It is not always possible, however, to structure applications as a single distributed application because of their nature, geographical location, confidentiality, and potential growth. Also, an enterprise may want to expand their business by cooperating with other organizations that provide OLTP services under the control of different transaction processing monitors, such as BEA's TopEnd, Transarc's Encina, IBM's CICS, Bull's TDS, Bull's TP8, ICL's TPMS, and so forth.
The BEA TUXEDO system provides the basic framework for domain interoperability. This framework defines a set of processes, called gateways, that manage the communication between domains. These gateways run within a BEA TUXEDO server group. This is illustrated in Figure 1-1, which shows a BEA TUXEDO application that requires services (in this case, credit card authorizations) from a remote domain.
Figure 1-1 A Generalized View of Two Communicating Domains
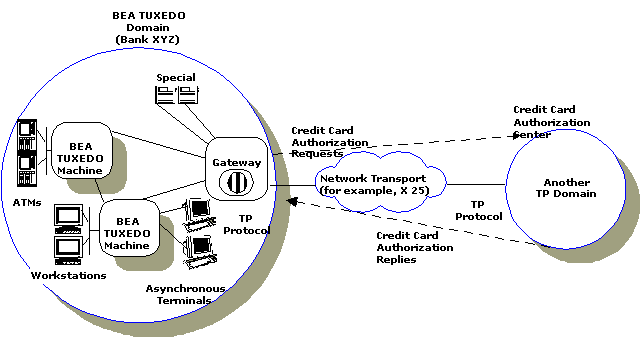
The application also accepts service requests (for example, balance inquiries) from remote domains. The gateway process provides bidirectional transaction control, and administrative tools that allow the configuration of the information required for interoperability of the local application with other domains. This configuration information includes the identification of a set of exported services, imported services, addressing, and access control. The BEA TUXEDO configuration of TDOMAIN is the subject of Chapter 2, "Configuring TDOMAIN."
Figure 1-2 shows a more detailed view of the environment associated with domains.
Figure 1-2 A Look at Domains Environments
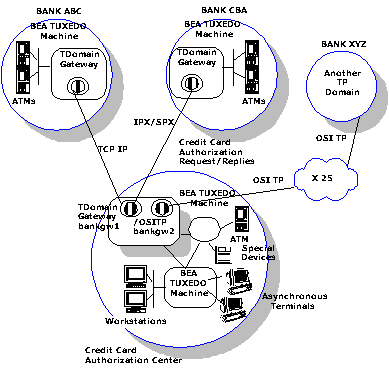
The example shows a credit card authorization center running under the control of the BEA TUXEDO system. The authorization center has two gateway groups: bankgw1 and bankgw2. bankgw1 provides access to two remote BEA TUXEDO domain; bankgw2 provides access to one remote domains (Bank XYZ) using the OSI TP protocol.
In this example, Bank ABC generates service requests to the credit card authorization center. These requests are received by a gateway running within group bankgw1. This gateway issues a service request on behalf of the remote domain to the credit card authorization service that is provided by a local server. The server processes the request and sends the reply to the gateway, and the gateway returns it to Bank ABC.
The credit card authorization center may also issue service requests, For example, the authorization center may send balance inquiries to Bank ABC. Domains makes this possible by behaving as a local server that advertises the services available on the other domains as if they were local services.
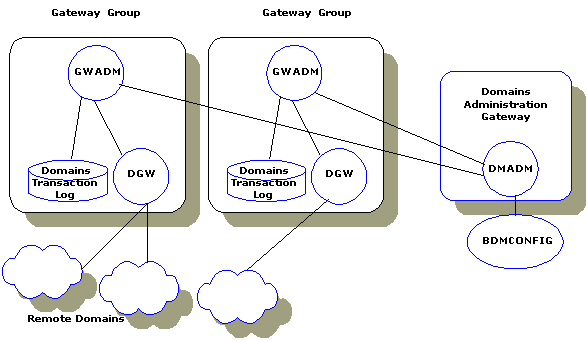
Domains provides the notion of a local domain to control incoming requests, and to provide a generic addressing framework for the application. Local domains help to provide partial views of an application, that is, a subset of the local services available to a set of remote domains. Each local domain is always represented by at most one gateway server group.
Cooperating with Other Applications
The main goal of the Domains feature is to allow the cooperation of BEA TUXEDO applications with dozens of applications running in other administrative domains. By meeting this goal, the BEA TUXEDO system provides a common framework for controlling very large applications that may include domains running other transaction processing systems.
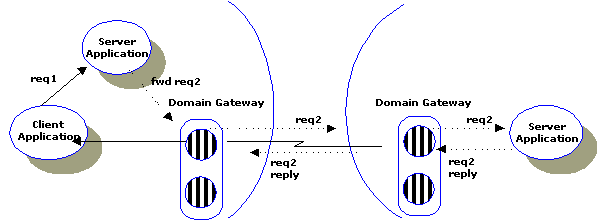
Domains maintains the BEA TUXEDO client/server model by making access to services on the remote TP System (or accepting service requests from a remote TP System) transparent to both the application programmer land the end-user (see Figure 1-3). Application programmers use the ATMI interface to access the services provided by remote domains, or to define services that can be executed by a remote domain. The following section discusses the implications of these interdomain communications on the different ATMI primitives.
Figure 1-3 Two-way Communication through a Gateway
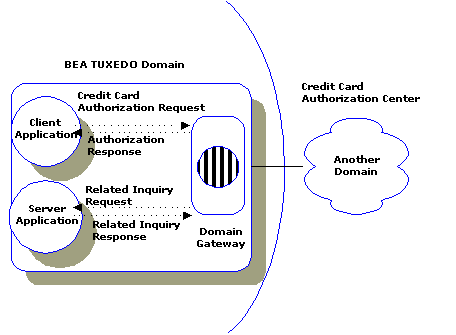
Domains provides an asynchronous multithreaded gateway able to process both requests going out to remote domains and requests coming in from remote domains. Any request can be processed within a transaction.
Security in Domains
The following four types of security are provided in Domains. These methods can be used separately or in combination with each other: