


|

|
|
|
|
Auditing
Auditing provides a means to collect, store, and distribute information about operating requests and their outcomes. Audit-trail records may be used to determine which principals performed, or attempted to perform, actions that violated BEA Tuxedo security. They may also be used to determine which operations were attempted, which ones failed, and which ones successfully completed.
How auditing is done (that is, how information is collected, processed, protected, and distributed) depends on the auditing plug-in.
Auditing Plug-in Architecture
A fanout is an umbrella plug-in to which individual plug-in implementations are connected. As shown in the following diagram, the auditing plug-in interface is implemented as a fanout.
Auditing Plug-in Architecture
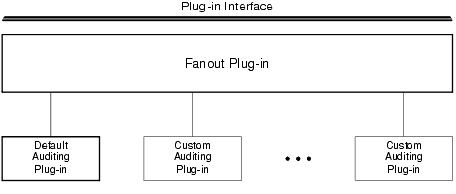
The default auditing implementation consists of a fanout plug-in and a default auditing plug-in. A custom implementation consists of the fanout plug-in, the default auditing plug-in, and one or more custom auditing plug-ins.
In a fanout plug-in model, a caller sends a request to the fanout plug-in. The fanout plug-in passes the request to each of the subordinate plug-ins, and receives a response from each. Finally, the fanout plug-in forms a composite response from the individual responses, and sends the composite response to the caller.
The purpose of an auditing request is to record an event. Each auditing plug-in returns one of two responses: success (the audit succeeded-logged the event) or failure (the audit failed-did not log the event). The auditing fanout plug-in forms a composite response in the following manner: if all responses are success, the composite response is success; otherwise, the composite response is failure.
For default auditing, the composite response is determined solely by the default auditing plug-in. For custom auditing, the composite response is determined by the fanout plug-in after collecting the responses of the subordinate plug-ins. For more insight into how fanouts work, see Authorization Plug-in Architecture.
How the Auditing Plug-in Works
Auditing decisions are based partly on user identity, which is stored in an auditing token. Because auditing tokens are generated by the authentication security plug-in, providers of authentication and auditing plug-ins need to ensure that these plug-ins work together.
A BEA Tuxedo system process or server (such as /Q server TMQUEUE(5) or EventBroker server TMUSREVT(5)) calls the auditing plug-in when it receives a client request. Because it is called before an operation begins, the auditing plug-in can audit operation attempts and store data if that data will be needed later for a post-operation audit. In response, the auditing plug-in performs a pre-operation audit and returns whether the audit succeeded.
The BEA Tuxedo system process or server may call the auditing plug-in after the client operation is performed. In response, the auditing plug-in performs a post-operation audit and returns whether the audit succeeded.
In addition, a BEA Tuxedo system process or server may call the auditing plug-in when a potential security violation occurs. (Suspicion of a security violation arises when a pre-operation or post-operation authorization check fails, or when an attack on security is detected.) In response, the auditing performs a post-operation audit and returns whether the audit succeeded.
These calls are system-level calls, not application-level calls. A BEA Tuxedo application cannot call the auditing plug-in.
The auditing process is somewhat different for (1) users of the default auditing plug-in provided by the BEA Tuxedo system and (2) users of one or more custom auditing plug-ins. The default plug-in does not support pre-operation audits. If the default auditing plug-in receives a pre-operation audit request, it returns immediately and does nothing.
The custom plug-ins support both pre-operation and post-operation audits.
Default Auditing
The default auditing implementation consists of the BEA Tuxedo EventBroker component and userlog (ULOG). These utilities report only security violations; they do not report which operations were attempted, which ones failed, and which ones successfully completed.
When default auditing is called by a BEA Tuxedo process to perform a post-operation audit when a security violation is suspected, the auditing plug-in performs the following tasks.
Because the auditing token is created by the authentication plug-in, the auditing plug-in has no record of the token's content. This information is necessary for the auditing process.
The auditing plug-in examines the client's auditing token and the security violation delivered in the post-operation audit request.
The auditing fanout plug-in receives a decision (success or failure) from the default auditing plug-in and operates on its behalf.
Custom Auditing
Users of one or more custom auditing plug-ins may take advantage of additional functionality offered by the BEA Tuxedo system. Specifically, the custom plug-ins may perform an additional audit before an operation occurs.
When custom auditing is called by a BEA Tuxedo process to perform a pre-operation audit in response to a client request, the auditing plug-in performs the following tasks.
The auditing plug-in examines the client's auditing token and may store user data if that data will be needed later for a post-operation audit.
The auditing fanout plug-in makes the ultimate decision by checking the individual responses (success or failure) from its subordinate plug-ins.
Custom auditing may be called by the BEA Tuxedo process to perform a post-operation audit after the client operation is performed. If so, the auditing plug-in performs the following tasks.
The auditing plug-in examines the client's auditing token, the completion status delivered in the post-operation audit request, and any data stored during the pre-operation audit.
The auditing fanout plug-in decides if the post-operation audit succeeded or failed by checking the individual responses (success or failure) from its subordinate plug-ins.
An operation is considered successful if it passes both pre- and post-operation audits, and the operation itself is successful. Some companies collect and store both pre- and post-operation auditing data, even though such data can occupy a lot of disk space.
Implementing Custom Auditing
You can provide auditing for your application by using the default plug-in or adding one or more custom plug-ins. You choose a plug-in by configuring the BEA Tuxedo registry, a tool that controls all security plug-ins.
If you want to use the default auditing plug-in, you do not need to configure the registry. If you want to add one or more custom auditing plug-ins, however, you must configure the registry for your additional plug-ins before you can install them. For more detail about the registry, see Setting the BEA Tuxedo Registry.

|

|

|
|
|
|
Copyright © 2000 BEA Systems, Inc. All rights reserved.
|