|
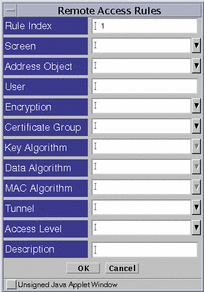
Rule Index
|
(Optional) Assigns a number to a rule.
By default, this field displays a number one greater than the last rule (indicating
this rule will be placed bottom of the list). If you type a lower number,
the new rule is inserted into the specified position in the list, and the
rules currently in the configuration are renumbered.
|
|
Screen
|
(Optional) Specifies the Screen for
which you want the rule to apply. Type a specific Screen name in this field
if you use centralized management and want a rule to apply to a specific Screen.
The default All applies to all Screens.
|
|
Address Object
|
Specifies from where users may initiate
a connection.
|
|
User
|
Lists the user names of SunScreen
administrators. Use the names that you defined for the Administrative User
object.
|
|
Encryption
|
Specifies the version of SunScreen
SKIP being used to encrypt traffic between the Screen and the Administration
Station.
|
|
Certificate Group
|
Specifies the name of
the certificate group, which can correspond to a single certificate or a certificate
group, allowed over this interface.
|
|
Key Algorithm
|
Identifies the algorithm used to encrypt
traffic-encrypting keys. The algorithms available depend on the strength of
encryption (128 bit, or 56 bit) that you are using with SunScreen.
|
|
Data Algorithm
|
Identifies the algorithm used to encrypt
message traffic between the Screen and the Administration Station. The algorithms
available depend on the strength of encryption (128 bit or 56 bit) that you
are using with SunScreen.
|
|
MAC Algorithm
|
Identifies the algorithm used to authenticate
traffic.
|
|
Tunnel
|
Identifies the tunnel address used
for the communication between the remote Administration Station and the Screen.
|
|
Access Level
|
Specifies what actions the designated
user can perform:
-
ALL - The administrator can display and modify all settings
for the Screen.
-
WRITE - The administrator can perform all operations
except modifying the Administration Access rules for any Policy.
-
READ - The administrator can view both the Information
and Policy. This level also allows the user to save and clear logs on the
information page. With this access level users cannot modify any Policy data.
-
STATUS - The administrator can display status information
(logs, statistics, status) but cannot display or modify management settings.
-
NONE - The administrator does not have access.
|
|
Description
|
(Optional) Provides a brief description
of the remote administrative access rule.
|
|
Move
|
Enables you to assign a new rule index
number for the rule that you highlighted in the Access Rules for Remote Administration
panel of the Administrative Access tab.
|
|
Delete
|
Deletes the access rule that you highlighted
in the Access Rules for Remote Administration panel of the Administrative
Access tab.
|
|
Help
|
Displays the online help.
|