Configuring the Screen to Use Preshared Keys
This sections describes how you set up SunScreen to use IKE preshared Keys.
Set Up the Screen
-
Select and edit the appropriate policy.
-
Define an IPsec Key Common Object.
Note -This is an optional step as you can also enter a preshared key directly into a field on the Rule Definition Action Details window.
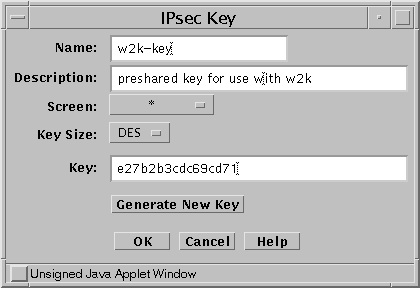
In the Common Object panel select IPsec Key and New; the IPsec Key dialog appears (see Figure 9-2).
Figure 9-2 IPsec Key Dialog Window
-
Fill in the required fields
Provide a Name and Description for the object as well as selecting the desired key size from the Key Size list. If you were using a preshared key generated by another system, you could type the key into the Key field. If you were using SunScreen to generate the key, you would click the Generate New Key button. The key does not have to be numeric, so you could for instance use a phrase.
-
Define the required Address objects.
In this example, you would define HOST type Address objects for the following systems: bos-host5, sf-w2kremote, and sf-w2k1.
-
Create a Packet Filtering rule that allows encrypted communication between the systems using the IKE preshared key.
In this example, telnet is the required service but it could be any service. The way you define the rule is similar to other IKE encryption rules except that the Authentication Method is PRE-SHARED (for more details on defining Packet Filtering IKE rules, see "Create Packet Filtering Rules with the ENCRYPT action".) See Figure 9-3 for an example of what the Rule Definition and Action Details windows would look like.
Figure 9-3 Rule Definition Windows for PreShared Key
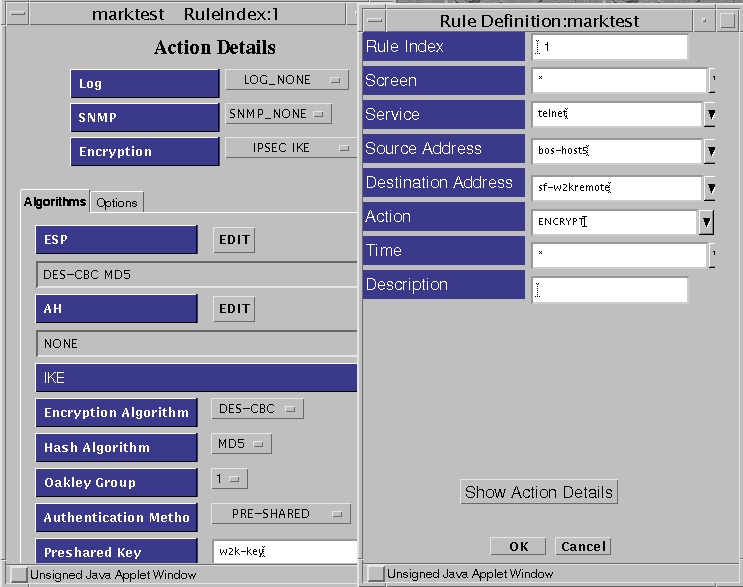
Note -The Oakley Group field on the Screen and the DH Group field on the Windows 2000 system must use the same value.
-
Click the Options tab and select the IKE mode.
Your choices are Tunnel or Transport mode. Tunnel mode encapsulates and encrypts the entire packet including the IP header for maximum security. Transport mode encapsulates and encrypts only the data portion of the IP packet resulting in smaller packets and potentially better throughput as the Screen is relieved of the overhead of decrypting the IP header. SunScreen and Windows 2000 both support IKE Transport and Tunnel modes.
If you choose Tunnel mode, you can supply the Source and Destination Tunnel addresses. You can also supply Source and Destination Screens. If you choose Transport mode, you can only specify Source and Destination Screens.
If the Source Address is the Screen, specify the Screen object in the Source Screen field. If the Destination Address is the Screen, specify the Screen object in the Destination Screen field.
-
Save and activate the policy.
- © 2010, Oracle Corporation and/or its affiliates
