Messaging Server uses the Secure Sockets Layer protocol for encrypted communications and for certificate-based authentication of clients and servers. See Introduction to SSL (reproduced as an appendix to Managing Servers with Netscape Console) for background information on SSL. SSL itself is based on the concepts of public-key cryptography, described in Introduction to Public-Key Cryptography (also reproduced as an appendix to Managing Servers with Netscape Console).
If transmission of messages between a Messaging Server and its clients and between the server and other servers is encrypted, there is little chance for eavesdropping on the communications. If connecting clients and servers are authenticated, there is little chance for intruders to impersonate (spoof) them.
SSL functions as a protocol layer beneath the application layers of IMAP4, POP3, and SMTP. The SSL version of each of these three application protocols (IMAP/SSL, POP/SSL, SMTP/SSL) acts at a specific stage of message communication, as shown in Figure 6.2 for both outgoing and incoming messages.
Figure 6.2 Encrypted communications with Messaging Server
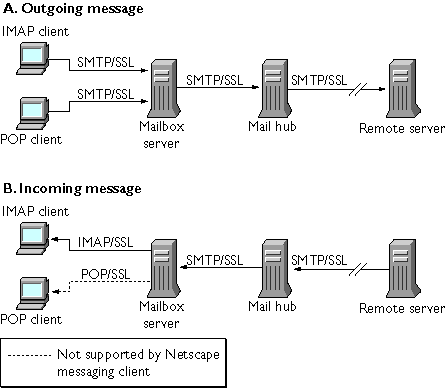
Complete end-to-end encryption of message transmission may require the use of all three SSL-related protocols. Netscape Messaging Server supports all three, but Netscape's messaging client software supports only SMTP/SSL and IMAP/SSL. As Figure 6.2 shows, the result is that Netscape POP clients can encrypt communication when sending messages, but not when receiving them.
Keep in mind that the extra performance overhead in setting up an SSL connection can put a performance burden on the server. In designing your messaging installation and in analyzing performance, you may need to balance security needs against server capacity.
Netscape Messaging Server 4.0 supports only SSL version 3.0.
Note: Because all Netscape servers support SSL, and the interface for
enabling and configuring SSL through Netscape Console is nearly identical
across all servers, several of the tasks described in this section are
documented more completely in the SSL chapter of Managing Servers with
Netscape Console. For those tasks, this chapter gives summary information
only.
Obtaining Certificates
Whether you use SSL for encryption or for authentication, you need to obtain a server certificate for your Messaging Server. The certificate identifies your server to clients and to other servers.
Managing Internal and External Modules
A server certificate establishes the ownership and validity of a key pair, the numbers used to encrypt and decrypt messages. Your server's certificate and key pair represent your server's identity. They are stored in a certificate database that can be either internal to the server or on an external, removable hardware card (smartcard).
Likewise, the software module that manages the keys and certificates database can be either internal or external. Netscape servers support both internal and external modules that conform to the Public-Key Cryptography System (PKCS) #11 protocol.
Setting up the server for a certificate involves creating a database for the certificate and its keys and installing a PKCS #11 module. If you do not use an external hardware token, you create an internal database on your server, and you use the internal, default module that is part of Messaging Server. If you do use an external token, you connect a hardware smartcard reader and install its PKCS #11 module.
You can manage PKCS #11 modules, whether internal or external, through Netscape Console. To install a PKCS #11 module, you
(For more complete instructions, see the chapter on SSL in Managing Servers with Netscape Console.)
Installing Hardware Encryption Accelerators.
If you use SSL for encryption, you may be able to improve server performance in encrypting and decrypting messages by installing a hardware encryption accelerator. An encryption accelerator typically consists of a hardware board, installed permanently in your server machine, plus a software driver. Netscape Messaging Server supports accelerator modules that follow the PKCS #11 protocol. (They are essentially hardware tokens that do not store their own keys; they use the internal database for that.) You install an accelerator by first installing the hardware and drivers as specified by the manufacturer, and then completing the installation--as with hardware certificate tokens--by installing the PKCS #11 module.
Requesting a Server Certificate
You request a server certificate by opening your server in Netscape Console and running the Certificate Setup Wizard, accessed through the Console menu. Using the Wizard, you
When the email response from the CA arrives, you save it as a text file.
(For more complete instructions, see the chapter on SSL in Managing Servers with Netscape Console.)
Creating a Password File
On any Netscape server, when you use the Certificate Setup Wizard to request a certificate, the wizard creates a key pair to be stored in either the internal module's database or in an external database (on a smartcard). The wizard then prompts you for a password, which it uses to encrypt the stored key pair. Only that same password can later be used to decrypt the keys. The wizard does not retain the password nor store it anywhere.
On most Netscape servers for which SSL is enabled, the administrator is prompted at startup to supply the password required to decrypt the key pair. On Messaging Server 4.0, however, to alleviate the inconvenience of having to enter the password multiple times (it is need by at least three server processes), and to facilitate unattended server restarts, the password is read from a password file.
The password file must be named sslpassword.conf and must be in the directory installDirectory/config/. Entries in the file are individual lines with the format
moduleName:password
where moduleName is the name of the (internal or external) PKCS #11 module to be used, and password is the password that decrypts that module's key pair. The password is stored as clear (unencrypted) text.
Messaging Server 4.0 provides a default version of the password file, with the following single entry (for the internal module and default password):
Communicator Certificate DB:netscape!
If you specify anything but the default password when you install an internal certificate, you need to edit the above line of the password file to reflect the password you specified. If you install an external module, you need to add a new line to the file, containing the module name and the password you specified for it.
Important: Because the administrator is not prompted for the module
password at server startup, it is especially important that you ensure proper
administrator access control to the server and proper physical security of
the server host machine and server backups.
Installing the Certificate
Installing is a separate process from requesting. Once the email response to your request for a certificate has arrived and been saved as a text file, run the Certificate Setup Wizard once more to install the file as a certificate. When you run the wizard, you
(For more complete instructions, see the chapter on SSL in Managing Servers with Netscape Console.)
Note: This is also the process you follow to install a CA certificate
(described next), which your server uses to determine whether to trust the
certificates presented by clients.
Installing Certificates of Trusted CAs
You also use the Certificate Setup Wizard to install the certificates of certificate authorities. A CA certificate validates the identity of the CA itself. Your server uses these CA certificates in the process of authenticating clients and other servers.
If, for example, you set up your enterprise for certificate-based client authentication in addition to password-based authentication (see Setting Up Certificate-Based Login), you need to install the CA certificates of all CAs that are trusted to issue the certificates that your clients may present. These CAs may be internal to your organization or they may be external, representing commercial or governmental authorities or other enterprises. (See Introduction to Cryptography for more details on the use of CA certificates for authentication.)
When installed, Messaging Server initially contains CA certificates for several commercial CAs. If you need to add other commercial CAs or if your enterprise is developing its own CA for internal use (using Netscape Certificate Server), you need to obtain and install additional CA certificates.
Note: The CA certificates automatically provided with Messaging Server are
not initially marked as trusted. You need to edit the trust settings before
your server can trust client certificates issued by these CAs. See Managing
Certificates and Trusted CAs for instructions.
To request and install a new CA certificate, you
(For more complete instructions, see the chapter on SSL in Managing Servers with Netscape Console.)
Managing Certificates and Trusted CAs
Your server can have more than one server certificate with which it identifies itself. It can also have any number of certificates of trusted CAs that it uses for authentication of clients.
You can view, edit the trust settings of, or delete any of the certificates installed in your Messaging Server by opening your server in Netscape Console and choosing the Certificate Management Command in the Console menu. For instructions, see the chapter on SSL in Managing Servers with Netscape Console.
Enabling SSL
You can use Netscape Console to enable SSL and to select the set of encryption ciphers that Messaging Server can use in its encrypted communications with clients.
About Ciphers
A cipher is the algorithm used to encrypt and decrypt data in the encryption process. Some ciphers are stronger than others, meaning that a message they have scrambled is more difficult for an unauthorized person to unscramble.
A cipher operates on data by applying a key--a long number--to the data. Generally, the longer the key the cipher uses during encryption, the harder it is to decrypt the data without the proper decryption key.
When a client initiates an SSL connection with a Messaging Server, the client lets the server know what ciphers and key lengths it prefers to use for encryption. In any encrypted communication, both parties must use the same ciphers. Because there are a number of cipher-and-key combinations in common use, a server should be flexible in its support for encryption. Netscape Messaging Server 4.0 can support up to 6 combinations of cipher and key length.
Table 6.1 lists the ciphers that Messaging Server supports for use with SSL 3.0. The table summarizes information that is available in more detail in Introduction to SSL; please consult that document before making final decisions on what ciphers to support
.
Unless you have a compelling reason for not using a specific cipher, you should support them all. However, note that export laws restrict the use of certain encryption ciphers in certain countries. Basically, key lengths of greater than 40 bits can be used only in the United States and Canada. See Export Restrictions on International Sales on the Netscape DevEdge Web site for details. In general, Messaging Server cannot use the higher-strength encryption for any communication with international versions of client software.
Turning On SSL and Selecting Ciphers
If your Messaging Server has an installed server certificate, SSL is enabled as long as one or more encryption ciphers is selected. (Most are on by default.) Thus you can effectively enable or disable SSL communications by selecting or deselecting encryption ciphers. Follow these steps:
In Netscape Console, open the Messaging Server whose cipher settings you want to modify.
Click the Configuration tab in the left pane.
Select the Services folder.
Select the Encryption tab in the right pane. The Encryption Configuration form opens.
Click the boxes to select the encryption cipher or ciphers that you want your server to support. To disable SSL completely, deselect all ciphers.
See Encryption Configuration Tab for a complete description of the contents of that form.
Setting Up Certificate-Based Login
In addition to password-based authentication, Netscape servers support authentication of users through examination of their digital certificates. In certificate-based authentication, the client establishes an SSL session with the server and submits the user's certificate to the server. The server then evaluates whether the submitted certificate is genuine. If the certificate is validated, the user is considered authenticated.
To set up your Messaging Server for certificate-based login:
Obtain a server certificate for your server. (See Obtaining Certificates for details.)
Run the Certificate Setup Wizard to install the certificates of any trusted certificate authorities that will issue certificates to the users your server will authenticate. (See Installing Certificates of Trusted CAs for details.)
Note that, as long as there is at least one trusted CA in the server's database, the server requests a client certificate from each connecting client.
Turn on SSL. (See Enabling SSL for details.)
(Optional) Edit your server's certmap.conf file so that the server appropriately searches the LDAP user directory based on information in the submitted certificates.
Editing the certmap.conf file is not necessary if the email address in your users' certificates matches the email address in your users' directory entries, and if you do not need to optimize searches or validate the submitted certificate against a certificate in the user entry.
For details of the format of certmap.conf and the changes you can make, see the SSL chapter of Managing Servers with Netscape Console.
Once you have taken these steps, when a client establishes an SSL session so that the user can log in to IMAP, the Messaging Server requests the user's certificate from the client. If the certificate submitted by the client has been issued by a CA that the server has established as trusted, and if the identity in the certificate matches an entry in the user directory, the user is authenticated and access is granted (depending on access-control rules governing that user).
There is no need to disallow password-based login (see Password-Based Login) to enable certificate-based login. If password-based login is allowed (which is the default state), and if you have performed the tasks described in this section, both password-based and certificate-based login are supported. In that case, if the client establishes an SSL session and supplies a certificate, certificate-based login is used. If the client does not use SSL or does not supply a certificate, the server requests a password.
For more details on setting up your entire installation of Netscape servers and clients to use certificate-based authentication, see Single Sign-On Deployment Guide.