Chapter 3 Working in Trusted Extensions (Tasks)
This chapter discusses how to work in Solaris Trusted Extensions workspaces. This chapter covers the following topics:
Visible Desktop Security in Trusted Extensions
Trusted Extensions offers two desktops, the Solaris Trusted Extensions (CDE) desktop and the Solaris Trusted Extensions (GNOME) desktop. Both desktops are labeled, but the labels might not be visible when you are working at a single label. To view an example of a system that is configured to display labels, see Figure 1–4.
A system that is configured with Trusted Extensions displays the trusted stripe except during login and screen lock. At all other times, the trusted stripe is visible. In Trusted CDE, the stripe is at the bottom of the screen. In Trusted GNOME, the stripe is at the top of the screen. The trusted symbol appears on the trusted stripe when you interact with the trusted computing base. When you change your password, for example, you interact with the TCB.
When the monitors of a multiheaded Trusted Extensions system are configured horizontally, one trusted stripe appears across the monitors. However, if the multiheaded system is configured to display vertically, or has separate desktops, one per monitor, then the trusted stripe appears on one monitor only.
If a second trusted stripe appears on a multiheaded system, the stripe is not generated by the operating system. You might have an unauthorized program on your system.
Contact your security administrator immediately. To determine the correct trusted stripe, see How to Regain Control of the Desktop’s Current Focus in Solaris Trusted Extensions Administrator’s Procedures.
For details about the applications, menus, labels, and features of the desktop, see Chapter 4, Elements of Trusted Extensions (Reference).
Trusted Extensions Logout Process
A workstation that is logged in to, but left unattended, creates a security risk. Make a habit of securing your workstation before you leave. If you plan to return soon, lock your screen. At most sites, the screen automatically locks after a specified period of idleness. If you expect to be gone for awhile, or if you expect someone else to use your workstation, log out.
Working on a Labeled System
If the trusted stripe is missing from your workspace, contact the security administrator. The problem with your system could be serious.
The trusted stripe should not appear during login, or when you lock your screen. If the trusted stripe shows, contact the administrator immediately.
 How to Lock and Unlock Your Screen
How to Lock and Unlock Your Screen
If you leave your workstation briefly, lock the screen.
-
To lock your screen, do one of the following:
-
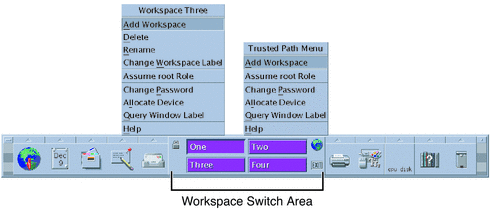
In Trusted CDE, click the screen lock icon in the workspace switch area of the Front Panel.
Figure 3–1 Front Panel Switch Area
-
In Trusted GNOME, choose Lock Screen from the Main menu.
The screen turns black. At this point, only you can log in again.
Note –The trusted stripe should not appear when the screen is locked. If the stripe does appear, notify the security administrator immediately.
-
 How to Log Out of Trusted Extensions
How to Log Out of Trusted Extensions
At most sites, the screen automatically locks after a specified period of idleness. If you expect to leave the workstation for awhile, or if you expect someone else to use your workstation, log out.
-
To log out, do one of the following:
-
In Trusted CDE, click the EXIT icon in the workspace switch area of the Front Panel.
For a picture of the Front Panel, see Figure 3–1.
The Logout Confirmation dialog box is displayed.
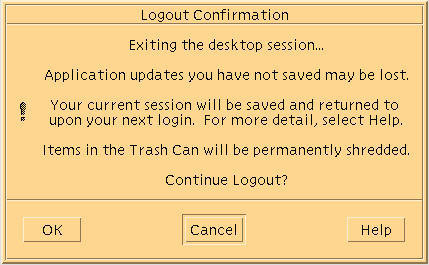
-
In Trusted GNOME, choose Log Out your-name from the Main menu.
-
-
Confirm that you want to continue to log out.
 How to Shut Down Your System
How to Shut Down Your System
Logging out is the normal way to end a Trusted Extensions session. Use the following procedure if you need to turn off your workstation.
Note –
If you are not on the console, you cannot shut down the system. For example, Sun RayTM clients cannot shut down the system.
-
To shut down the system, do one of the following:
 How to View Your Files in a Labeled Workspace
How to View Your Files in a Labeled Workspace
To view your files, you use the same applications that you would use in Trusted CDE or Trusted GNOME on a Solaris system. If you are working at multiple labels, only the files that are at the label of the workspace are visible.
-
In a Trusted CDE workspace, open a terminal window or the File Manager.
-
Open a terminal window and list the contents of your home directory.
Click mouse button 3 over the background. From the Workspace menu, choose Programs –> Terminal.
-
On the Front Panel, click the File Manager.
Figure 3–2 A Labeled File Manager
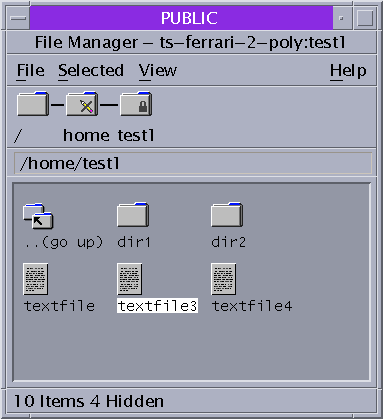
The File Manager appears with the contents of your home directory at that label.
The File Manager opens at the same label as the current workspace. The application provides access to only those files that are at its label. For details about viewing files at different labels, see Containers and Labels.
-
-
In a Trusted GNOME workspace, open a terminal window or the File Browser.
-
Open a terminal window and list the contents of your home directory.
Click mouse button 3 over the background. From the menu, choose Open Terminal.
-
Double-click the Documents folder or the This Computer folder on your desktop.
These folders open in a File Browser. The File Browser application opens at the same label as the current workspace. The application provides access to only those files that are at its label. For details about viewing files at different labels, see Containers and Labels.
-
 How to Access the Trusted Extensions Man
Pages
How to Access the Trusted Extensions Man
Pages
-
In the Solaris Express Community Edition release, review the trusted_extensions(5) man page in a terminal window.
% man trusted_extensions
For a list of user commands that are specific to Trusted Extensions, see Appendix E, List of Trusted Extensions Man Pages, in Solaris Trusted Extensions Administrator’s Procedures. The man pages are also available from Sun's documentation web site.
 How to Access Trusted Extensions Online Help
How to Access Trusted Extensions Online Help
-
In Trusted CDE, click the Help icon on the Front Panel.
Figure 3–3 Trusted Extensions Online Help
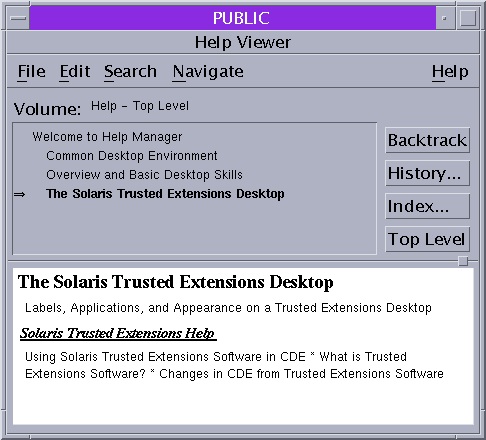
-
In Trusted GNOME, click Help from the Trusted Path menu.
 How to Customize the CDE
Workspace Menu
How to Customize the CDE
Workspace Menu
In Trusted CDE, users and roles can customize the Workspace menu for each distinct label.
-
In your current workspace, start to customize the Workspace menu.
-
If you are adding items to the Workspace menu, do the following:
-
If you are modifying the Workspace menu, do the following:
-
Confirm the menu changes, or cancel.
 How to Access Initialization Files at
Every Label
How to Access Initialization Files at
Every Label
Linking a file or copying a file to another label is useful when you want to make a file with a lower label visible at higher labels. The linked file is only writable at the lower label. The copied file is unique at each label and can be modified at each label. For more information, see .copy_files and .link_files Files in Solaris Trusted Extensions Administrator’s Procedures.
Before You Begin
You must be logged in to a multilevel session. Your site's security policy must permit linking.
Work with your administrator when modifying these files.
-
Decide which initialization files you want to link to other labels.
-
Create or modify the ~/.link_files file.
Type your entries one file per line. You can specify paths to subdirectories in your home directory, but you cannot use a leading slash. All paths must be within your home directory.
-
Decide which initialization files you want to copy to other labels.
Copying an initialization file is useful when you have an application that always writes to a file with a specific name, and you need to separate the data at different labels.
-
Create or modify the ~/.copy_files file.
Type your entries one file per line. You can specify paths to subdirectories in your home directory, but you cannot use a leading slash. All paths must be within your home directory.
Example 3–1 Creating a .copy_files File
In this example, the user wants to customize several initialization files per label. In her organization, a company web server is available at the Restricted level. So, she sets different initial settings in the .mozilla file at the Restricted level. Similarly, she has special templates and aliases at the Restricted level. So, she modifies the .aliases and .soffice initialization files at the Restricted level. She can easily modify these files after creating the .copy_files file at her lowest label.
% vi .copy_files # Copy these files to my home directory in every zone .aliases .mozilla .soffice |
Example 3–2 Creating a .link_files File
In this example, the user wants her mail defaults and shell defaults to be identical at all labels.
% vi .link_files # Link these files to my home directory in every zone .cshrc .mailrc |
Troubleshooting
These files do not have safeguards for dealing with anomalies. Duplicate entries in both files or file entries that already exist at other labels can cause errors.
 How to Interactively Display a Window
Label
How to Interactively Display a Window
Label
This operation can be useful when your system is not configured to display labels in the window frames.
-
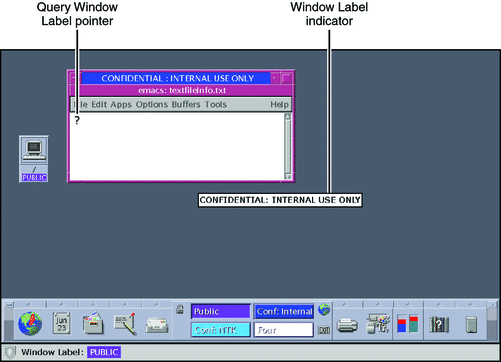
Choose Query Window Label from the Trusted Path menu.
The pointer changes to a question mark.
-
Move the pointer around the screen.
The label for the region under the pointer is displayed in a small rectangular box at the center of the screen.
Figure 3–4 Query Window Label Operation
-
Click the mouse button to end the operation.
 How to Perform Some Common Desktop Tasks in Trusted Extensions
How to Perform Some Common Desktop Tasks in Trusted Extensions
Some common tasks are affected by labels and security. In particular, the following tasks are affected by Trusted Extensions:
-
Emptying the trash
-
Finding calendar events
-
In Trusted CDE, restoring the Front Panel and using the Style Manager
-
Empty the trash.
The trash can contains files only at the label of the workspace. Delete sensitive information as soon as the information is in the trash can.
-
Find calendar events at every label.
Calendars show only the events at the label of the workspace that opened the calendar.
-
In Trusted CDE, restore the Front Panel by clicking the trusted stripe.
A minimized Front Panel is restored.
-
On both desktops, save a customized desktop at every label.
You can customize the workspace configuration for every label at which you log in.
-
Configure the desktop.
Arrange windows, establish the font size, and perform other customizations.
Note –Users can save desktop configurations. Roles cannot save desktop configurations.
-
Save the current workspace.
-
In Trusted CDE, open the Style Manager. Choose your settings in the Startup icon.
Note –The Style Manager requires the trusted path. Run the Style Manager from the Front Panel or from the Workspace menu, where the Style Manager has the trusted path.
Your desktop is restored in this configuration when you next log in at this label.
-
In Trusted GNOME, click the Main menu.
-
Click Preferences > Sessions.
-
Click the Session Options button.
-
Click Remember currently running applications, then close the dialog box.
Your desktop is restored in this configuration when you next log in at this label.
-
-
-
Performing Trusted Actions
The following security-related tasks require the trusted path.
If the trusted symbol is missing when you are attempting a security-related action, contact your security administrator at once. The problem on your system could be serious.
 How to Change Your Password in Trusted Extensions
How to Change Your Password in Trusted Extensions
Unlike the Solaris OS, Trusted Extensions provides a GUI for changing your password. The GUI grabs the pointer until the password operation is completed. To stop a process that has grabbed the pointer, see How to Regain Control of the Desktop’s Current Focus in Solaris Trusted Extensions Administrator’s Procedures.
-
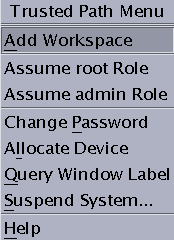
Choose Change Password from the Trusted Path menu.
For the Change password menu item in Trusted GNOME, click Trusted Path in the trusted stripe.
The following figure shows the Trusted Path menu in Trusted CDE.
-
Type your current password.
This action confirms that you are the legitimate user for this user name. For security reasons, the password is not displayed as you type.
 Caution –
Caution – When you type your password, make sure that the cursor is over the Change Password dialog box and that the trusted symbol is displayed. If the cursor is not over the dialog box, you might inadvertently type your password into a different window where the password could be seen by another user. If the trusted symbol is not displayed, then someone might be attempting to steal your password. Contact your security administrator at once.
-
Type the new password.
-
Confirm the password by retyping it.
 How to Log In at a Different Label
How to Log In at a Different Label
The label of the first workspace that appears in subsequent login sessions after the first login can be set to any label within your label range.
Users can configure the startup session characteristics for every label at which they log in..
Before You Begin
You must be logged in to a multilevel session.
-
Create workspaces at every label.
For details, see How to Add a Workspace at a Particular Label.
-
Configure each workspace as you want the workspace to appear.
-
Go to the workspace that you want to see when you log in.
-
Save this current workspace.
For details, see How to Perform Some Common Desktop Tasks in Trusted Extensions.
 How to Allocate a Device in Trusted Extensions
How to Allocate a Device in Trusted Extensions
The Allocate Device menu item enables you to mount and allocate a device for your exclusive use. If you try to use a device without allocating it, you get the error message “Permission Denied”.
Before You Begin
You must be authorized to allocate a device.
-
Choose Allocate Device from the Trusted Path menu
Or, in Trusted CDE, open the Device Allocation Manager from the Tools subpanel in the Front Panel.
Figure 3–5 Device Allocation Icon in Trusted CDE
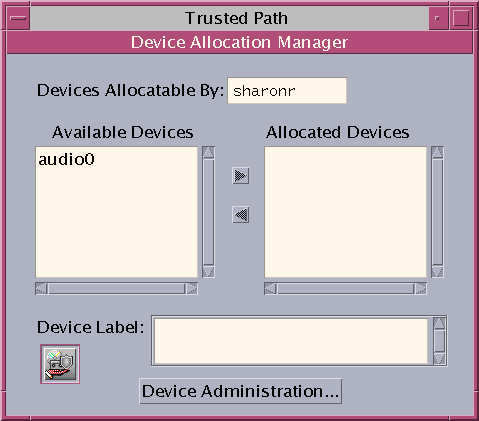
The Device Allocation Manager is displayed. In Solaris Trusted Extensions (GNOME), this GUI is called the Device Manager.
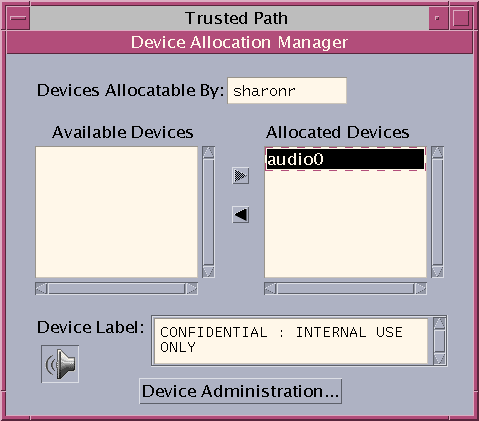
Figure 3–6 Device Allocation Manager
-
Double-click the device that you want to use.
The devices that you are permitted to allocate at your current label appear under Available Devices:.
-
audion – Indicates a microphone and speaker
-
cdromn – Indicates a CD-ROM drive
-
floppyn – Indicates a diskette drive
-
mag_tapen – Indicates a tape drive (streaming)
-
rmdiskn – Indicates a removable disk, such as a JAZ or ZIP drive, or USB hot-pluggable media
-
-
Select the device.
Move the device from the Available Devices list to the Allocated Devices list.
-
Double-click the device name in the Available Devices list.
-
Or, select the device and click the Allocate button that points to the right.
This step starts the clean script. The clean script ensures that no data from other transactions remains on the media.
Note that the label of the current workspace is applied to the device. Any data transferred to or from the device's media must be dominated by this label.
-
-
Follow the instructions.
The instructions ensure that the media has the correct label. Then, the device is mounted. The device name now appears in the Allocated Devices list. This device is now allocated for your exclusive use.
Example 3–3 Loading Removable Media to Read a File System
In this example, a user wants to load information onto her system from a CD-ROM that is labeled SECRET. She is authorized to allocate the CD-ROM.
First, she creates a workspace at the label SECRET. In this workspace, she opens the Device Allocation Manager, and allocates the CD-ROM drive. Then, she inserts the CD and responds yes to the mount query.
The software mounts the CD and the File Manager appears. The current directory is set to the mount point.
Example 3–4 Loading Removable Media to Format the Media
In this example, a user wants to format a diskette to contain SECRET data. She is authorized to allocate the CD-ROM drive.
First, she creates a workspace at the label SECRET. In this workspace, she opens the Device Allocation Manager, and allocates the CD-ROM drive. Then, she inserts the CD and responds no to the mount query. The CD can now be formatted.
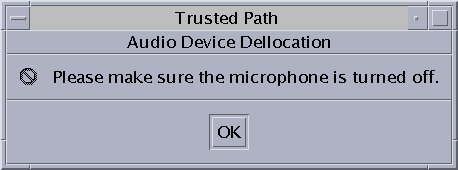
Example 3–5 Allocating an Audio Device
In this example, a user allocates the audio device on her system. When she moves the audio device to the Allocated Device list, the following message appears:

The device is allocated at the label Confidential : Internal Use Only. She views the label when she selects the device in the Allocated Device list.
When the user is finished with the audio device, she deallocates it. The system reminds her to turn off the microphone.
Troubleshooting
If the device that you want to use does not appear in the list, check with your administrator. The device could be in an error state or in use by someone else. Or, you might not be authorized to use the device.
If you switch to a different role workspace or to a workspace at a different label, the allocated device cannot work at that label. To use the device at the new label, you need to deallocate the device at the initial label, and then allocate the device at the new label. In Trusted CDE, when you use the Occupy Workspace command from the window menu to move the Device Allocation Manager to the new workspace, the Available and Allocated Devices lists change to reflect the correct context. The Device Manager in Trusted GNOME works similarly when you move the GUI to a workspace at a different label.
If a File Manager or File Browser window does not appear, open the window manually, then navigate to the root directory, /. In this directory, navigate to the allocated device to see its contents.
 How to Deallocate a Device in Trusted Extensions
How to Deallocate a Device in Trusted Extensions
-
Deallocate the device.
-
Remove the media.
-
Click OK in the Deallocation dialog box.
The device is now available for use by another authorized user.
 How to Assume a Role in Trusted Extensions
How to Assume a Role in Trusted Extensions
Unlike the Solaris OS, Trusted Extensions provides a GUI for assuming a role.
-
-
In Solaris Trusted Extensions (CDE), click the center of the Front Panel.
If you have been assigned a role by the security administrator, the Trusted Path menu includes the Assume rolename Role menu item.
Choose Assume rolename Role.
-
In Solaris Trusted Extensions (GNOME), click your user name at the right of the trusted symbol.
Choose the role name from the menu.
-
-
Type the role password and press Return.
This action confirms that you can legitimately assume this role. For security reasons, the password is not displayed as you type.
 Caution –
Caution – When you type your password, make sure that the cursor is over the Change Password dialog box and that the trusted symbol is displayed. If the cursor is not over the dialog box, you might inadvertently type your password into a different window where the password could be seen by another user. If the trusted symbol is not displayed, then someone might be attempting to steal your password. Contact your security administrator at once.
After the role password is accepted, the software places you in a role workspace. In Trusted GNOME, the current workspace becomes the role workspace. In Trusted CDE, a new workspace is created for the role. You are in the global zone. You can perform the tasks that are permitted by the rights profiles in your role.
 How to Change the Label
of a Workspace
How to Change the Label
of a Workspace
The ability to set workspace labels in Trusted Extensions provides a convenient means of working at different labels within the same session.
Use this procedure to work in the same workspace at a different label. To create a workspace at a different label, see How to Add a Workspace at a Particular Label.
Before You Begin
You must be logged in to a multilevel session.
-
Click mouse button 3 over the workspace button.
-
From the menu, choose Change Workspace Label.
-
Choose a label from the label builder.
The workspace label is changed to the new label. Windows and applications that were invoked before the label change continue to run at the previous label. The trusted stripe indicates the new label. In a system where labels are color-coded, new windows are marked with the new color. In Trusted CDE, the workspace button is color-coded.
 How to Add a Workspace at a Particular
Label
How to Add a Workspace at a Particular
Label
The ability to set workspace labels in Trusted Extensions provides a convenient means of working at different labels within the same session. On both desktops, you can add a workspace at your minimum label. In Trusted CDE, you can add a workspace at the label of an existing workspace.
Tip –
In Trusted CDE, rename each workspace button to reflect the label of the workspace.
To change the label of the current workspace, see How to Change the Label of a Workspace.
Before You Begin
You must be logged in to a multilevel session.
-
In Trusted GNOME, to create a workspace at your minimum label, do the following:
-
Click mouse button 3 over a workspace box in the panel display.
-
From the menu, choose Preferences.
-
Increase the number in the Number of Workspaces field.
The new workspaces are created at your minimum label. You can also use this dialog box to name the workspaces.
Note –In Trusted GNOME, to add a workspace at a different label, you select a workspace box and change its label. For details, see How to Change the Label of a Workspace.
-
-
In Trusted CDE, to create a workspace at your minimum label, do the following:
-
In Trusted CDE, to create a workspace at the label of an existing workspace, do the following:
 How to Switch to a Workspace at a Different Label
How to Switch to a Workspace at a Different Label
-
In Trusted CDE, click the workspace switch at that label.
Figure 3–7 Front Panel With Switches at Different Labels

-
In Trusted GNOME, click the workspace box on the panel display.
You are now in that labeled workspace.
Troubleshooting
If you are logged in to a single-level session, you must log out to work at a different label. Then, log in at the desired label. If you are permitted, you can also log in to a multilevel session.
 How to Move a Window to a Different Workspace
How to Move a Window to a Different Workspace
Windows that are moved to a different workspace retain their original label. Any actions that are done in those windows are done at the label of the window, not at the label of the containing workspace. Moving a window is useful when you want to compare information. You might also want to use applications at different labels without moving between workspaces.
-
In Trusted CDE, use the Occupy Workspace menu to move a window to a different workspace.
-
From the application's window menu, choose Occupy Workspace.
Figure 3–8 Selecting Occupy Workspace
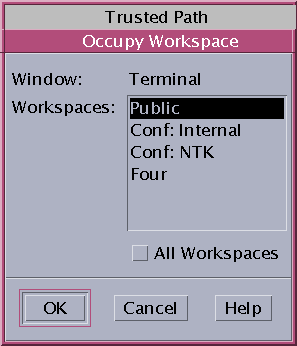
-
Choose a workspace at a different label, then click OK.
This action moves the application to a workspace that has a different label. Note that the Occupy Workspace dialog box has the label Trusted Path. This label indicates that occupying a workspace affects the trusted computing base.
The following figure shows two terminal windows at different labels in one workspace.
Figure 3–9 Differently Labeled Windows in One Workspace
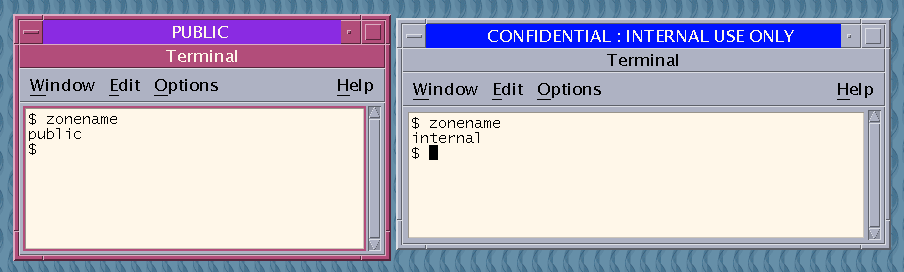
-
-
In Trusted GNOME, in the panel display, drag the window from its original workspace box to a different workspace box.
The dragged window now appears in the second workspace.
 How to Determine the Label of a File
How to Determine the Label of a File
Usually, the label of a file is obvious. However, if you are allowed to view files at a lower label than your current workspace, the label of a file might not be obvious. In particular, the label of a file can be different from the label of the File Manager.
-
In Trusted CDE, use the File Manager to determine the label of the file.
-
In Trusted GNOME, use the File Browser.
Tip –You can also use the Query Label menu item from the Trusted Path menu.
 How to Move Data Between Labels
How to Move Data Between Labels
As on a Solaris system, you can move data between windows in Trusted Extensions. However, the data must be at the same label. When you transfer information between windows with different labels, you are upgrading or downgrading the sensitivity of that information.
Before You Begin
Your site's security policy must permit this type of transfer, the containing zone must permit relabeling, and you must be authorized to move data between labels.
Therefore, your administrator must have completed the following tasks:
You must be logged in to a multilevel session.
-
Create workspaces at both labels.
For details, see How to Add a Workspace at a Particular Label.
-
Confirm the label of the source file.
For details, see How to Determine the Label of a File.
-
Move the window with the source information to a workspace at the target label.
For details, see How to Move a Window to a Different Workspace. The following figure shows two editors at different labels in the same workspace.
Figure 3–10 Differently Labeled Applications in One Workspace
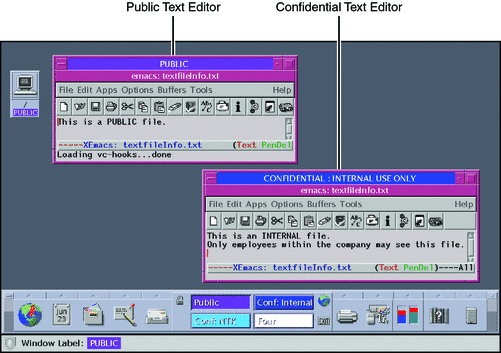
-
Highlight the information to be moved, and paste the selection in the target window.
-
Review the Selection Manager Confirmation dialog box.
This dialog box:
-
Describes why confirmation of the transaction is needed.
-
Identifies the label and the owner of the source file.
-
Identifies the label and the owner of the destination file.
-
Identifies the type of data that was selected for transfer, the type of the target file, and the size of the data in bytes. By default, the selected data is visible in text format.
-
Indicates the time that remains for you to complete the transaction. The amount of time and the use of the timer depends on your site's configuration.
Figure 3–11 Selection Manager Confirmation Dialog Box
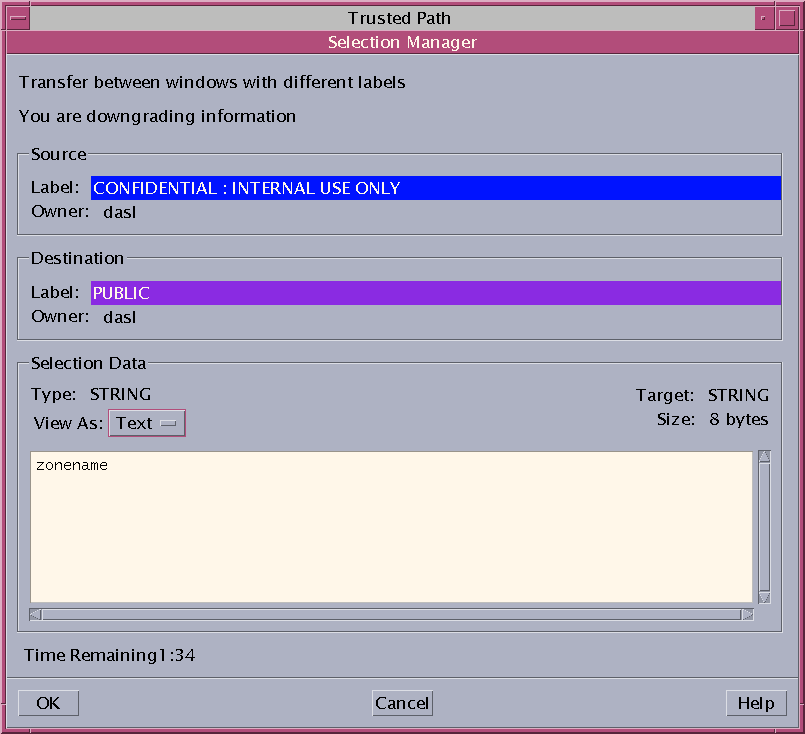
-
-
(Optional) In the View As menu, choose how to view the source information.
-
Confirm that you want the label of the data to change.
 How to Move Files Between Labels in Trusted CDE
How to Move Files Between Labels in Trusted CDE
As on a standard Solaris system, you can move files in Trusted Extensions. When you move a file to a different label, you are upgrading or downgrading the sensitivity of the information that is in the file.
Before You Begin
Your site's security policy must permit this type of transfer, the containing zone must permit relabeling, and you must be authorized to move files between labels.
Therefore, your administrator must have completed the following tasks:
You must be logged in to a multilevel session in Trusted CDE. The file that you want to move must be closed. Verify that no one else is using this file.
-
Create workspaces at both labels.
For details, see How to Add a Workspace at a Particular Label.
-
Open File Managers at both labels.
For details, see How to View Your Files in a Labeled Workspace.
-
In the source File Manager, navigate to the file whose label is to change.
-
In the target File Manager, navigate to the file's new directory.
-
Move the File Managers into one workspace.
For details, see How to Move a Window to a Different Workspace.
Figure 3–12 Differently Labeled File Managers in One Workspace
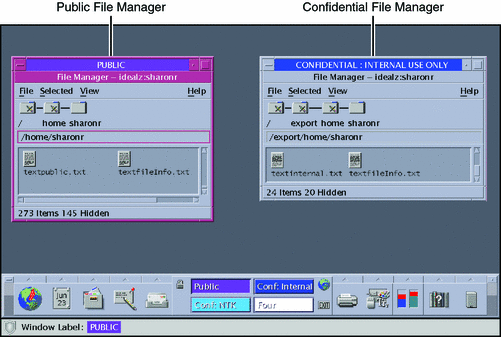
-
Drag and drop the file to the target directory.
Figure 3–13 Dragging a File Between File Managers at Different Labels
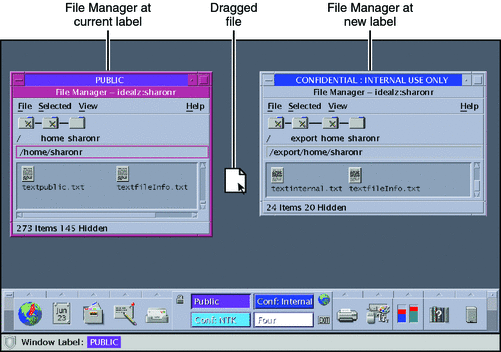
The File Manager Confirmation dialog box is displayed, as shown in Figure 3–14.
This dialog box is similar to the Selection Manager Confirmation dialog box, but does not include a timer. This dialog box:
-
Describes why confirmation of the transaction is needed.
-
Identifies the label and the owner of the source file.
-
Identifies the label and the owner of the destination file.
-
Identifies the type of data that was selected for transfer, the type of the target file, and the size of the data in bytes.
Figure 3–14 File Manager Confirmation Dialog Box
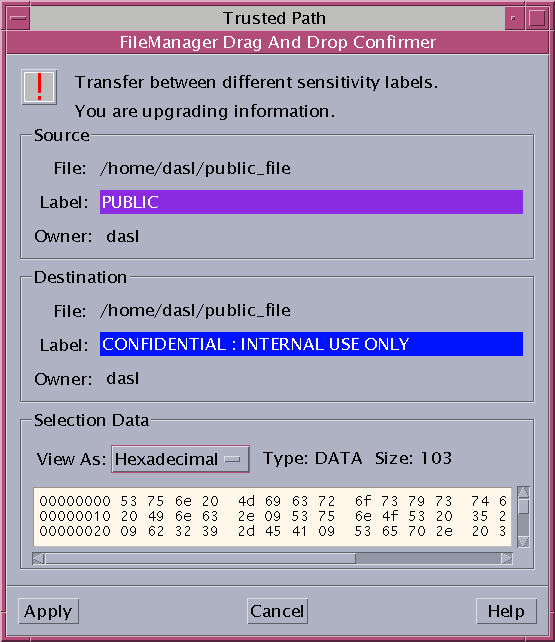
-
-
Confirm that you want the label of the file to change.
Example 3–6 Linking a File to a Different Label
The linking of a file to another label is useful when you want to view a file with a lower label at a higher label. The file is writable only at the lower label.
To link a file, the user presses Shift-Control while dragging the file icon from the source File Manager to the target File Manager. Then, the user confirms the link, or cancels the operation.
Troubleshooting
If your system is not configured to permit the upgrading or downgrading of labels, a dialog box that states that the transfer is not authorized is displayed. Check with your administrator.
- © 2010, Oracle Corporation and/or its affiliates
