Chapter 11 PasswordSync
PasswordSync detects user password changes initiated on Windows domains and forwards those changes to Identity Manager. Identity Manager then synchronizes password changes with the other resources defined in Identity Manager.
This chapter is organized as follows:
What is PasswordSync?
The PasswordSync feature keeps user password changes made on Windows Active Directory domains synchronized with other resources defined in Identity Manager. PasswordSync must be installed on each domain controller in the domains that will be synchronized with Identity Manager. PasswordSync must be installed separately from Identity Manager.
PasswordSync consists of a DLL (lhpwic.dll) that resides on each domain controller. This DLL receives password update notifications from Windows, encrypts them, and sends them over HTTPS to the PasswordSync servlet. The PasswordSync servlet is located on the application server running Identity Manager.
Note –
Using HTTPS is preferred, but HTTP is also supported.
The PasswordSync servlet translates the notification into a format Identity Manager can understand. The servlet then sends the password change (still encrypted) to Identity Manager using one of the following methods:
-
Direct method. The servlet communicates the password change directly to Identity Manager using native Identity Manager classes. (See What is PasswordSync?.)
The direct connection method is only recommended for smaller, less complex environments that only require message delivery to one system, and that do not require guaranteed message delivery. (If direct message delivery fails for some reason, the message will be lost. Back up delivery is not possible.)
-
JMS method. The servlet sends the password information to Identity Manager using JMS (Java Message Service). With JMS, the servlet submits password changes to the JMS Message Queue. Separately, Identity Manager’s JMS Listener Resource Adapter checks the Queue for new messages. If a password change message is found waiting on the Queue, the JMS Listener Adapter takes the message off the Queue and imports it into Identity Manager. (See Figure 11–2.)
The JMS method is recommended for more complex environments that have a high volume requirement, need messages delivered to multiple systems, and require guaranteed message delivery. The JMS Message Queue can be made highly available. As long as a message gets into the queue, if message delivery to Identity Manager should fail, the queue will keep the change until the message can be delivered to Identity Manager.
You must install and configure JMS separately.
Figure 11–1 diagrams a direct connection. In this configuration the PasswordSync servlet sends update messages directly to Identity Manager.
Figure 11–1 PasswordSync Logical Diagram (Direct Connection)
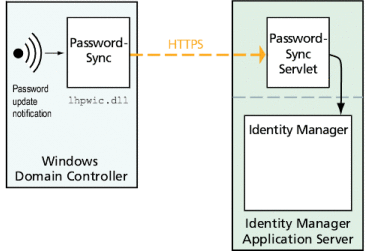
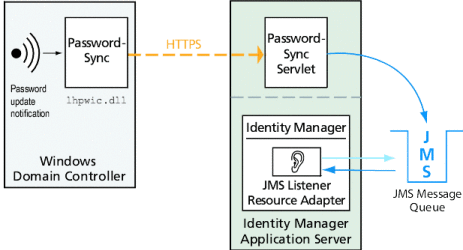
Figure 11–2 diagrams a JMS connection. In this configuration the PasswordSync servlet sends update messages to the JMS Message Queue. Identity Manager’s JMS Listener Resource Adapter periodically checks the Queue (indicated by the light blue arrow in the diagram) for new messages. The Queue responds by sending the messages to Identity Manager (indicated by the dark blue arrow).
Figure 11–2 PasswordSync Logical Diagram (JMS Connection).
When Identity Manager receives a password change notification, it decrypts it and processes the change using a workflow task. The password is updated on all of the user’s assigned resources, and an SMTP server sends an email to the user, notifying the user of the status of the password change.
Note –
Windows only sends out an update notification if a password change is successful. If a password change request does not meet the domain’s password policy, Windows will reject it and no synchronization data will be sent to Identity Manager.
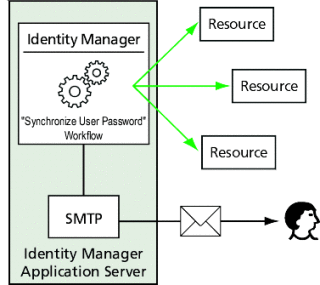
Figure 11–3 shows Identity Manager initiating a workflow and sending email to the user after receiving a password update notification.
Figure 11–3 PasswordSync Triggers a Workflow
Note –
PasswordSync discards all account change notifications for account names that end in a $ (dollar sign). Account names that end in a $ are assumed to be Windows computer accounts. Any user account names that end in a dollar sign will not be forwarded to Identity Manager.
Before You Install
The PasswordSync feature can be set up only on Windows 2008, Windows 2003, and Windows 2000 domain controllers. (Support for Windows NT domain controllers was discontinued in version 8.0 of Identity Manager.) You must install PasswordSync on each primary and backup domain controller in the domains that will be synchronized with Identity Manager. Configuring PasswordSync for HTTPS is highly recommended.
Note –
Versions of PasswordSync that are older than version 7.1.1 should be updated to at least version 7.1.1 on all domain controllers.
Support for the rpcrouter2 servlet has been deprecated in version 8.0, and will be removed in a future release. PasswordSync versions 7.1.1 and newer support the new protocol.
If using JMS, PasswordSync requires connectivity with a JMS server. See the JMS Listener resource adapter section in the Sun Identity Manager 8.1 Resources Referencefor more information about the requirements for the JMS system.
In addition, PasswordSync requires you to
-
Install at least Microsoft .NET 1.1 on each domain controller.
-
Remove any previous versions of PasswordSync.
These requirements are discussed in more detail in the following sections.
Install Microsoft .NET 1.1
To use PasswordSync, you must install at least the Microsoft .NET 1.1 Framework. This Framework is installed by default if you are using a Windows 2003 domain controller. The Microsoft .NET 2.0 Framework is installed by default on Windows 2008 domain controllers. If you are using a Windows 2000 domain controller, no Framework is installed by default. You can download the toolkit from the Microsoft Download Center at:
http://www.microsoft.com/downloads
Note –
-
Enter .NET Framework Redistributable in the Keywords search field to quickly locate the Framework toolkit.
-
The toolkit installs the .NET Framework.
Configure PasswordSync for SSL
Although sensitive data is encrypted before being sent to the Identity Manager server, Sun Microsystems recommends configuring PasswordSync to use a secure SSL connection (that is, an HTTPS connection).
For information on how to install imported SSL certificates, see this Microsoft Knowledge Base How-To article:
http://support.microsoft.com/kb/816794
Once you have installed PasswordSync, you can test that your SSL connection is properly configured by specifying an HTTPS URL in the PasswordSync Configuration dialog. See Testing Your Configuration for instructions.
Uninstall Previous Versions of PasswordSync
You must remove any previously installed instances of PasswordSync before installing a later version.
-
If the previously installed version of PasswordSync supports the IdmPwSync.msi installer, you can use the standard Windows Add/Remove Programs utility to remove the program.
-
If the previously installed version of PasswordSync does not support the IdmPwSync.msi installer, use the InstallAnywhere uninstaller to remove the program.
Installing and Configuring PasswordSync on Windows
This section contains information and instructions for installing and configuring PasswordSync.
This information is organized as follows:
 To Install the PasswordSync Configuration Application
To Install the PasswordSync Configuration Application
The following procedure describes how to install the PasswordSync configuration application.
Note –
You must install PasswordSync on each domain controller in the domains that will be synchronized with Identity Manager.
Be sure to uninstall any previously installed versions of PasswordSync before continuing.
-
From the Identity Manager installation media,
-
If you are installing to a 32-bit version of Windows, double-click pwsync\IdmPwSync_x86.msi.
-
If you are installing to a 64-bit version of Windows, double-click pwsync\IdmPwSync_x64.msi.
The installation wizard opens and the Welcome window displays with the following navigational buttons:
-
Cancel. Click to exit the wizard at any time without saving any of your changes.
-
Back. Click to return to a previous dialog box.
-
Next. Click to progress to the next dialog box.
-
-
Read the information provided on the Welcome screen, and then click Next to display the Choose Setup Type window.
-
Click either Typical or Complete to install the full PasswordSync package, or click Custom to control which parts of the package are installed. Click Next to continue.
-
When the Ready to Install window displays, click Install to install the product.
-
A final window displays. Enable the Launch Configuration Application box so that you can begin configuring Password Sync, and then click Finish to complete the installation process.
Instructions for configuring PasswordSync are provided in Chapter 11, PasswordSync.
Note –A dialog displays, stating that you must restart the system for the changes to take effect. It is not necessary to restart until after you have configured PasswordSync, but you must restart the domain controller before implementing PasswordSync.
Installing and Configuring PasswordSync on Windows describes the files that are installed on each domain controller.
Installed Component
Description
%$INSTALL_DIR$%\configure.exe
PasswordSync configuration program
%$INSTALL_DIR$%\configure.exe.manifest
Data file for the configuration program
%$INSTALL_DIR$%\passwordsyncmsgs.dll
DLL that handles PasswordSync messages
%SYSTEMROOT%\SYSTEM32\lhpwic.dll
Password Notification DLL that implements the Windows PasswordChangeNotify() function
 To Configure PasswordSync
To Configure PasswordSync
If you run the configuration application from the installer, the application displays the configuration screens as a wizard. After you have completed the wizard, each subsequent time you run the PasswordSync configuration application, you can navigate between screens by selecting a tab.
-
Start the PasswordSync configuration application (if it is not already running).
By default, the configuration application is installed at Program Files -> Sun Identity Manager PasswordSync -> Configuration.
Note –If you do not plan to use JMS, launch the configuration application from a command line, being sure to include the -direct flag as follows:
C:\InstallDir\Configure.exe -direct
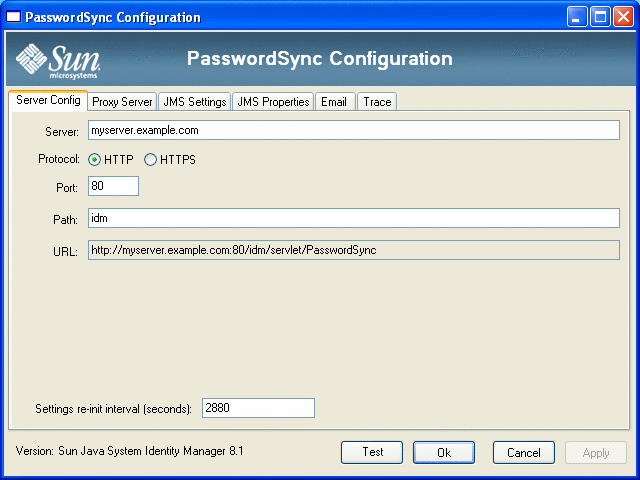
The PasswordSync Configuration wizard dialog is displayed (see Figure 11–4).
Figure 11–4 PasswordSync Configuration Wizard
-
Edit the fields on this dialog as necessary.
These fields include:
-
Server must be replaced with the fully-qualified host name or IP address where Identity Manager is installed.
-
Protocol indicate whether to make secure connections to Identity Manager.
PasswordSync supports the configuration of certificate check behavior for HTTPS connections. When you enable HTTPS, the following options display:
-
Allow revoked certificates. This setting maps to the securityIgnoreCertRevoke registry value on the connection. By default, PasswordSync does not ignore revocation issues and the securityIgnoreCertRevoke registry value is set to 0.
If you want PasswordSync to ignore revoked certificate messages, check this box (or set the SECURITY_FLAG_IGNORE_REVOCATION registry value to 1).
-
Allow invalid certificates. This setting affects the SECURITY_FLAG_IGNORE_CERT_CN_INVALID, SECURITY_FLAG_IGNORE_CERT_DATE_INVALID, and SECURITY_FLAG_IGNORE_UNKNOWN_CA options on the connection. By default, PasswordSync does not allow invalid certificates and the registry values are set to 0.
Checking this box, or setting the securityAllowInvalidCert registry value to 1, allows PasswordSync to use certificates that do not pass a number of safety checks. Enabling this option is not recommended for a production environment.
Note –These settings are not displayed for the HTTP protocol type, nor do they affect HTTP settings.
-
-
Port specify an available port for the server. For HTTP, the default port is 80. For HTTPS, the default port is 443.
-
Path specify the path to Identity Manager on the application server.
-
URL is generated by concatenating the other fields together. The value cannot be edited within the URL field.
-
Settings re-init interval (seconds) specify how often the PasswordSync dll should reread configuration settings from the registry. The default value is 2880 seconds or 8 hours.
Note –This PasswordSync Configuration wizard displays the value in seconds, but the registry value is actually stored in milliseconds.
The PasswordSync dll reads the configuration settings from the registry while the dll is active. This interval value is stored in the reinitIntervalMilli registry value.
Passwords cannot be synchronized while the settings are being updated, which can cause a small delay in processing a password change. Normally this delay is less than a second. PasswordSync processes any password changes received during an update directly after the update has completed. Also, PasswordSync does not process setting updates while a password synchronization is in progress. The update will be rescheduled and performed at a later time.
-
-
Click Next to display the Proxy Server Configuration page (Figure 11–5) and edit the fields as needed.
Figure 11–5 PasswordSync Wizard Proxy Server Dialog
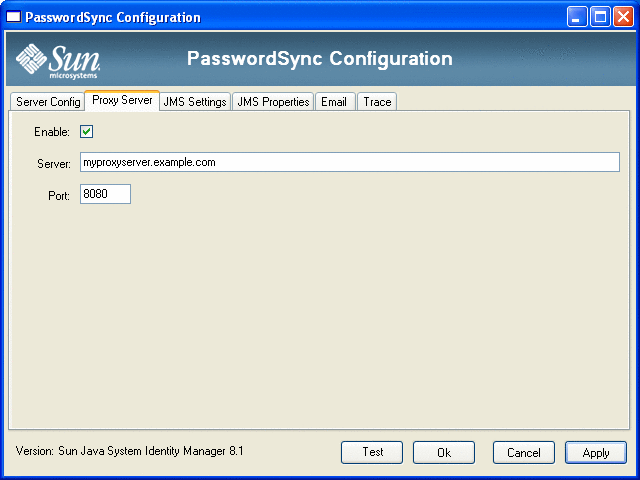
These fields include:
-
Enable. Select if a proxy server is required.
-
Server. You must enter the fully-qualified host name or IP address of the proxy server.
-
Port. Specify an available port number for the server. (The default proxy port is 8080 and the default HTTPS port is 443.)
-
-
Click Next.
Figure 11–6 PasswordSync Wizard JMS Settings Dialog
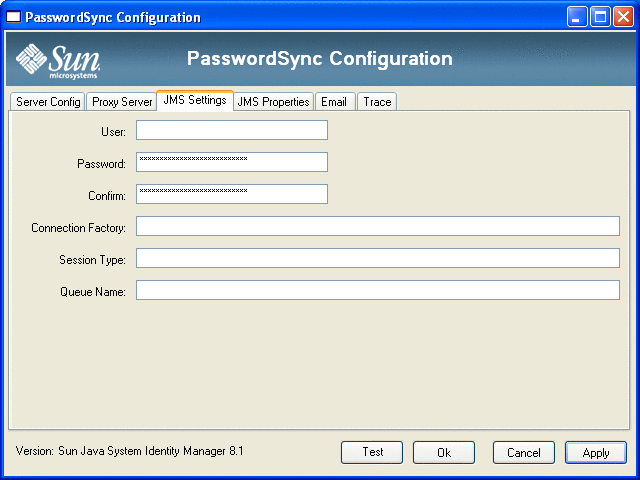
When the JMS Settings dialog (Figure 11–6) appears, perform one of the following actions:
-
Edit the following fields, as needed:
-
User specifies the JMS user name that places new messages on the queue.
-
Password and Confirm specify the password for the JMS user.
-
Connection Factory specifies the name of the JMS connection factory to be used. This factory must already exist on the JMS system.
-
In most cases, Session Type should be set to LOCAL, which indicates that a local session transaction will be used. The session will be committed after each message is received. Other possible values include AUTO, CLIENT, and DUPS_OK.
-
Queue Name specifies the Destination Lookup Name for the password synchronization events.
-
-
If you do not plan to use JMS and you launched the configuration wizard with the -direct flag, click Next to display the User dialog. Skip to step Figure 11–7.
-
-
Click Next to display the JMS Properties dialog (Figure 11–7).
Figure 11–7 PasswordSync Wizard JMS Properties Dialog
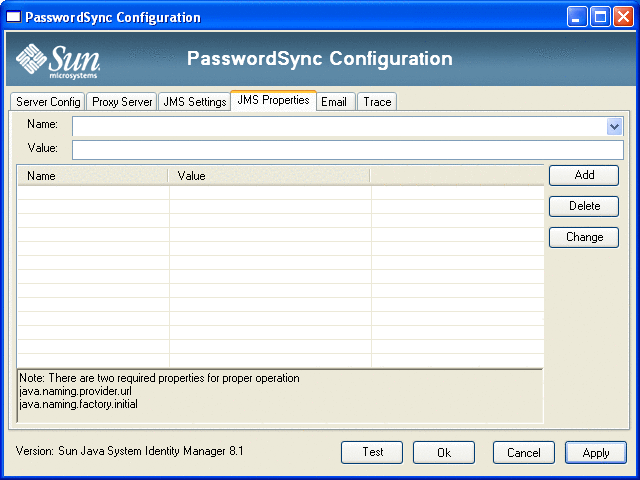
The JMS Properties dialog allows you to define the set of properties that are used to build the initial JNDI context. You must define the following name/value pairs:
-
java.naming.provider.url — Specify the URL of the machine running the JNDI service.
-
java.naming.factory.initial — Specify the classname (including the package) of the Initial Context Factory for the JNDI Service Provider.
The Name pull-down menu contains a list of classes from the java.naming package. Select a class or type in a class name, then enter its corresponding value in the Value field.
-
-
If you do not plan to use JMS and you launched the configuration wizard with the -direct flag, configure the User tab. Otherwise, skip this step and go to the next step.
To configure the User tab, edit the fields as necessary.
-
Account ID. Specify the user name that will be used to connect to Identity Manager.
-
Password. Specify the password that will be used to connect to Identity Manager.
-
-
Click Next to display the Email dialog (Figure 11–8) and edit the fields as necessary.
Figure 11–8 PasswordSync Wizard Email Dialog
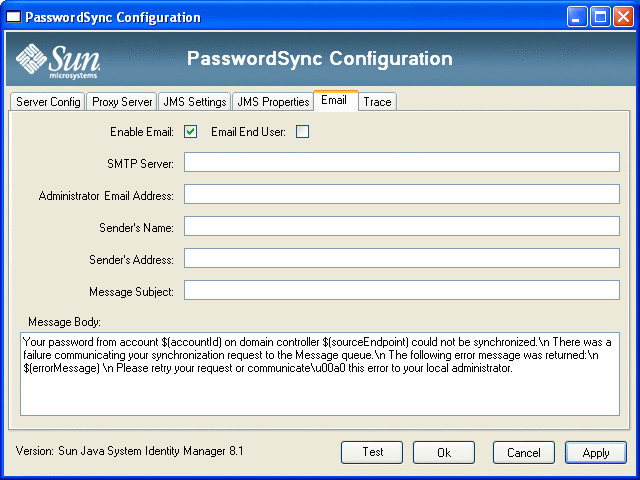
To send an email notification when a user’s password change does not synchronize successfully due to a communication error or other error outside of Identity Manager, use the following options on the Email dialog to set up the notification and configure the email.
-
Enable Email. Select to enable this feature.
-
Email End User. Select if the user is to receive notifications. Otherwise, only the administrator will be notified.
-
SMTP Server. Enter the fully qualified name or IP address of the SMTP server to be used when sending failure notifications.
-
Administrator Email Address. Enter the email address where you want to send the notifications.
-
Sender’s Name. Enter the sender's “friendly name.”
-
Sender’s Address. Enter the sender's email address.
-
Message Subject. Enter the subject line for all notifications
-
Message Body. Enter the text for the notification.
The message body might contain the following variables:
-
$(accountId) — The accountId of the user attempting to change password.
-
$(sourceEndpoint) — The host name of the domain controller where the password notifier is installed, to help locate troubled machines.
-
$(errorMessage) — The error message that describes the error that has occurred.
-
-
-
Click the Trace tab Figure 11–9.
Figure 11–9 Trace Tab
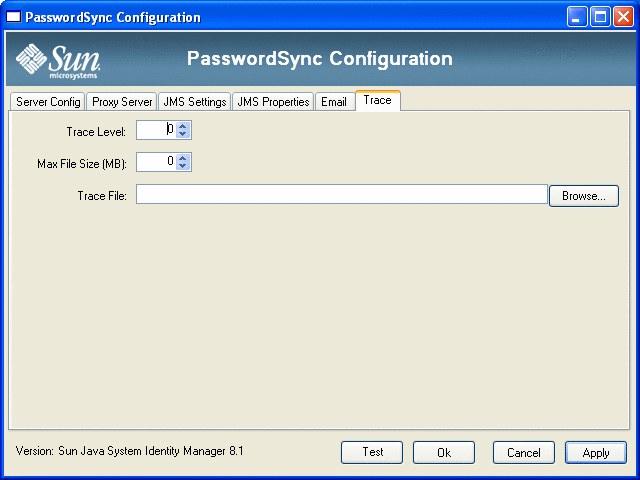
Set the following fields.
-
Trace Level.
-
Max File Size (MB).
-
Trace File.
-
-
Click Finish to save your changes.
If you run the configuration application again, a set of tabs is displayed instead of a wizard. If you want to display the application as a wizard, type the following command from the command line:
C:\InstallDir\Configure.exe -wizard
To test your PasswordSync configuration, see Testing Your Configuration.
Installing PasswordSync Silently
You can configure the PasswordSync installer for silent installation. To use this feature, you must first record configuration parameters to a file while installing PasswordSync. Future installations will reference the file and replay the configuration settings.
Note –
If you want to use the silent installation procedure then you must install the complete product on each server that will use it. Recording and replaying the configuration settings relies on the configuration application to be installed on the system.
The silent installation process utilizes a Windows utility calledmsiexec that installs .msi files from the command line.
Type msiexec /? at a command prompt to view usage information for this utility.
Documentation is also available on Microsoft's website. For example, for documentation on using msiexec on Windows Server 2003, see http://technet.microsoft.com/en-us/library/cc759262.aspx.
 To Capture Installation Parameters to a Configuration
File
To Capture Installation Parameters to a Configuration
File
Follow these instructions to install PasswordSync using the installation wizard. The configuration utility captures configuration parameters and writes them to an XML file.
Before You Begin
Remove older versions of PasswordSync before installing.
-
Go to the directory with the PasswordSync installation (.msi) file.
See To Install the PasswordSync Configuration Application for information.
-
Type the following at a command prompt. Arguments and values are case sensitive.
msiexec /i pwSyncInstallFile CONFIGARGS="-writexml fullPathToFile"
where:
-
pwSyncInstallFile is the PasswordSync installation file. (Either IdmPwSync_86.msi or IdmPwSync_x64.msi).
-
fullPathToFile specifies where to write the XML file.
For example:
msiexec /i IdmPwSync_x86.msi CONFIGARGS="-writexml c:\tmp\myconfig.xml"
-
-
Install the product.
 To Install PasswordSync Silently
To Install PasswordSync Silently
Before You Begin
-
You should have created an installation configuration XML file. See To Capture Installation Parameters to a Configuration File for instructions.
-
Remove older versions of PasswordSync before installing.
-
Copy your installation configuration XML file to a location where it can be read by the installer.
-
Type the following at a command prompt. Arguments and values are case sensitive.
msiexec /i pwSyncInstallFile ADDLOCAL="installFeature" CONFIGARGS="-readxml fullPathToFile" INSTALLDIR="installDir" /q
where:
-
pwSyncInstallFile is the PasswordSync installation file. (Either IdmPwSync_86.msi or IdmPwSync_x64.msi).
-
installFeature specifies which PasswordSync features to install. Choose one of the following:
-
MainProgram — Only install the interceptor .dll file
-
Configuration — Only install the configuration application
-
ALL — Install the complete product
If nothing is specified, MainProgram is used by default if the /q option is supplied.
-
-
fullPathToFile specifies the path to the configuration XML file.
-
installDir specifies the full path to a custom installation directory. Optional.
-
/q specifies a non-GUI install that automatically reboots the server when finished. If not included, the installation wizard will display but the configuration will run with the predefined settings. Optional.
Examples:
msiexec /i IdmPwSync_x86.msi CONFIGARGS="-readxml c:\tmp\myconfig.xml"
msiexec /i IdmPwSync_x86.msi ADDLOCAL="MainProgram" CONFIGARGS="-readxml c:\tmp\myconfig.xml" /q
msiexec /i IdmPwSync_x64.msi ADDLOCAL="Complete" CONFIGARGS="-readxml c:\tmp\myconfig.xml" INSTALLDIR="C:\Program Files\Sun Microsystems\MyCustomInstallDirectory" /q
-
Deploying PasswordSync on the Application Server
Once PasswordSync is installed on your Windows domain controllers, you must take additional steps on the application server running Identity Manager.
You do not need to install the PasswordSync servlet on the application server. It is automatically installed when you installed Identity Manager.
To finish deploying PasswordSync, however, you do need to perform the following actions in Identity Manager:
-
Add and configure the JMS Listener Adapter (if using JMS)
-
Implement the “Synchronize User Password” Workflow
-
Set up notifications
Adding and Configuring a JMS Listener Adapter
If the PasswordSync servlet is using JMS to send messages to Identity Manager, you need to add Identity Manager’s JMS Listener resource adapter. The JMS Listener resource adapter periodically checks the JMS Message Queue for messages placed there by the PasswordSync servlet. If the Queue contains a new message, it sends it to Identity Manager for processing.
 To Add the JMS Listener Resource Adapter
To Add the JMS Listener Resource Adapter
-
Log on to the Identity Manager Administrator Interface (Identity Manager Administrator Interface).
-
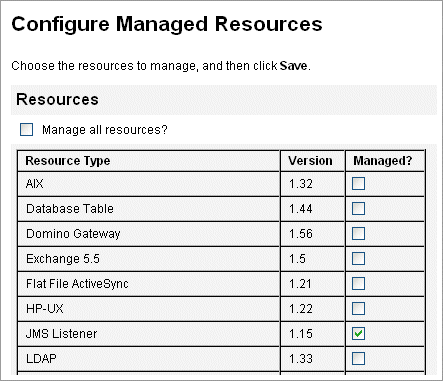
Select Resources -> Configure Types from the main menu.
The Configure Managed Resources page opens as shown in Figure 11–10.
Figure 11–10 The Configure Managed Resources Page.
-
Verify that the JMS Listener checkbox in the Managed? column is selected as shown in Figure 11–10.
If the box is not selected, select it and click Save.
-
Click List Resources in the secondary menu.
-
Locate the Resource Type Actions drop-down menu and select New Resource.
The New Resource page is displayed.
-
To add the JMS Listener Adapter, select JMS Listener from the drop-down menu (as shown in Figure 11–11) and click New.
Figure 11–11 The New Resource Wizard

-
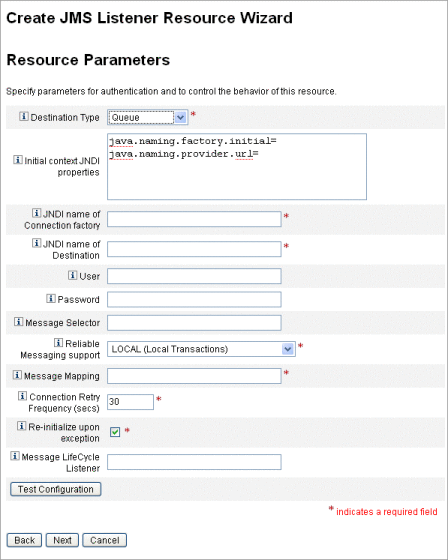
Configure the following settings on the Resource Parameters page, and then click Next.
-
Destination Type. Specify the This value is typically set to Queue. (Topics are not usually relevant because there is one subscriber and potentially multiple publishers.)
-
Initial context JNDI properties. Define the set of properties that are used to build the initial JNDI context.
You must define the following name/value pairs:
-
java.naming.factory.initial. Specify the classname (including the package) of the Initial Context Factory for the JNDI Service Provider.
-
java.naming.provider.url. Specify the URL of the machine running the JNDI service.
You might have to define additional properties. The list of properties and values should match those specified on the JMS settings page on the JMS server. For example, to provide the credentials and bind method, you might need to specify the following sample properties:
-
java.naming.security.principal — Bind DN (for example, cn=Directory manager)
-
java.naming.security.authentication — Bind method (for example, simple)
-
java.naming.security.credentials — Password
-
-
-
JNDI name of Connection factory. Enter the name of a connection factory, as defined on the JMS server.
-
JNDI name of Destination. Enter the name of a destination, as defined on the JMS server.
-
User and Password. Enter the account name and password of the administrator that requests new events from the queue.
-
Reliable Messaging Support. Select LOCAL (Local Transactions). The other options are not applicable for password synchronization.
-
Message Mapping. Enter java:com.waveset.adapter.jms.PasswordSyncMessageMapper. This class transforms messages from the JMS server into a format that can be used by the Synchronize User Password workflow.
-
-
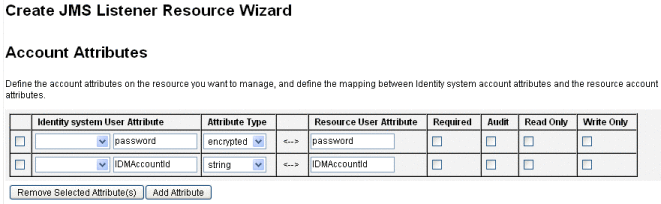
On the Account Attributes wizard page (Figure 11–12), click Add Attribute and map the following attributes, which are made available to the JMS Listener Adapter by PasswordSyncMessageMapper.
-
IDMAccountId — This attribute is resolved by the PasswordSyncMessageMapper, based on the resourceAccountId and resourceAccountGUID attributes passed in the JMS message.
-
password — The encrypted password forwarded in the JMS message.
Figure 11–12 The Account Attributes Page of the Create JMS Listener Resource Wizard
-
-
Click Next.
The Identity Template wizard page opens as shown in Figure 11–13. Note that the attributes you added in the previous step are available in the Attribute Mappings section of the Resource Wizard (Figure 11–13).
Figure 11–13 JMS Listener Resource Wizard Attribute Mappings
-
Click Next and configure the options on Identity System Parameters page as needed.
See Sun Identity Manager 8.1 Resources Referencefor more information about setting up the JMS Listener resource adapter.
Implementing the Synchronize User Password Workflow
When Identity Manager receives a password change notification, it starts the Synchronize User Password workflow. The default Synchronize User Password workflow checks out the ChangeUserPassword viewer, and then checks it back in again. Next, the workflow processes all of the resources accounts (except the Windows resource that sent the initial password change notification). Finally, Identity Manager sends the user email indicating whether the password change was successful on all resources.
If you want to use the default implementation of the Synchronize User Password workflow, assign it as the process rule for the JMS Listener adapter instance. Process rules may be assigned when you configure the JMS Listener for synchronization (see Configuring Active Sync).
If you want to modify the workflow, copy the $WSHOME/sample/wfpwsync.xml file and make your modifications. Then, import the modified workflow into Identity Manager.
Some of the modifications you might want to make to the default workflow include:
-
Which entities are notified when a password is changed.
-
What happens if an Identity Manager account cannot be found.
-
How resources are selected in the workflow.
-
Whether to allow password changes from Identity Manager.
For detailed information about using workflows, see Chapter 2, Workflow, in Sun Identity Manager Deployment Reference.
Setting Up Notifications
Identity Manager provides two email templates that can inform users whether a password change was successful across all resources.
These templates are:
-
Password Synchronization Notice
-
Password Synchronization Failure Notice
Both templates should be updated to provide company-specific information about what users should do if they need further assistance. For more information see Customizing Email Templates in Chapter 4, Configuring Business Administration Objects.
Configuring PasswordSync with a Sun JMS Server
Identity Manager can use Java Message Service (JMS) to receive password change notifications from the PasswordSync servlet. In addition to guaranteed delivery, JMS can deliver messages to multiple systems.
Note –
See the Sun Identity Manager 8.1 Resources Reference for more information about this adapter.
Using a sample scenario, this section provides instructions for configuring PasswordSync with a Sun JMS server.
The information is organized as follows:
Sample Scenario
A typical (simple) use case for configuring PasswordSync with a JMS server is to enable users to change their passwords on Windows, have Identity Manager pick up the new password, and then update the user accounts with the new passwords on a Sun Directory Server.
The following environment was configured for this scenario:
-
Windows Server 2003 Enterprise Edition– Active Directory
-
Sun JavaTM System Identity Manager 6.0 2005Q4M3
-
MySQL running on SUSE Linux 10.0
-
Tomcat 5.0.28 running on SUSE Linux 10.0
-
Sun Java System Message Queue 3.6 SP3 2005Q4 running on SUSE Linux 10.0
-
Sun Java System Directory Server 5.2 SP4 running on SUSE Linux 10.0
-
Java 1.5 (Java 5.0)
The following files were copied to the Tomcat common/lib directory to enable JMS and JNDI:
-
jms.jar (from Sun Message Queue)
-
fscontext.jar (from Sun Message Queue)
-
imq.jar (from Sun Message Queue)
-
jndi.jar (from Java JDK)
Creating and Storing Administered Objects
This section provides instructions for creating and storing the following administered objects, which are required for the sample scenario to work successfully:
-
Connection factory objects
-
Destination objects
You can store administered objects in an LDAP directory or in a file. If you are using a file, all instances of the file must be the same.
For instructions, see
Note –
-
The instructions in this section assume you have installed Sun Java System Message Queue. (The necessary tools are located in the bin/ directory of your Message Queue installation.)
-
You can use the Message Queue administrative GUI (imqadmin) or the command-line tool (imqobjmgr) to create these administered objects. The following instructions use the command-line tool.
Storing Administered Objects in an LDAP Directory
PasswordSync and the JMS Listener can be configured to use administered objects stored in an LDAP directory. Figure 11–14 illustrates the process. Both the PasswordSync Servlet and the JMS Listener adapter must retrieve connection factory and destination settings from the LDAP Directory in order to send and receive messages.
Figure 11–14 Retrieving Connection Factory and Destination Objects from the LDAP Directory
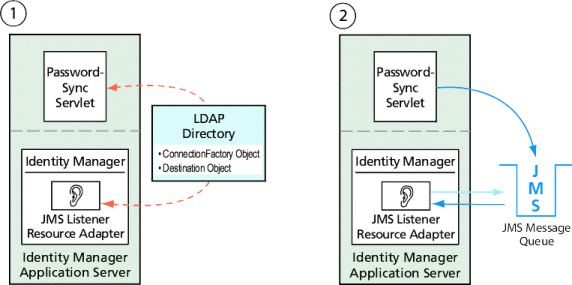
Using the Message Queue Command-Line Tool
This section explains how to use the Message Queue command-line tool (imqobjmgr) to store administered objects in an LDAP directory.
Storing Connection Factory Objects
Open the Message Queue command-line tool (imqobjmgr) and type the commands in Storing Connection Factory Objects to store the connection factory objects.
Example 11–1 Storing Connection Factory Objects
#> ./imqobjmgr add -l "cn=mytestFactory" -j "java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory" -j "java.naming.provider.url=ldap://gwenig.coopsrc.com:389/ou=sunmq,dc=coopsrc,dc=com" -j "java.naming.security.principal=cn=directory manager" -j "java.naming.security.credentials=password" -j "java.naming.security.authentication=simple" -t qf -o "imqAddressList=mq://gwenig.coopsrc.com:7676/jms" Adding a Queue Connection Factory object with the following attributes: imqAckOnAcknowledge [Message Service Acknowledgement of Client Acknowledgements] ... imqSetJMSXUserID [Enable JMSXUserID Message Property] false Using the following lookup name: cn=mytestFactory The object’s read-only state: false To the object store specified by: java.naming.factory.initial com.sun.jndi.ldap.LdapCtxFactory java.naming.provider.url ldap://gwenig.coopsrc.com:389/ou=sunmq,dc=coopsrc,dc=com java.naming.security.authentication simple java.naming.security.credentials netscape java.naming.security.principal cn=directory manager Object successfully added. |
In Storing Connection Factory Objects imqAddressList defines the JMS server/broker hostname (gwenig.coopsrc.com), port (7676), and the access method (jms).
Storing Destination Objects
In the Message Queue command-line tool (imqobjmgr), type the commands in Storing Destination Objects to store the destination objects.
Example 11–2 Storing Destination Objects
#> ./imqobjmgr add -l "cn=mytestDestination" -j "java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory" -j "java.naming.provider.url=ldap://gwenig.coopsrc.com:389/ou=sunmq,dc=coopsrc,dc=com" -j "java.naming.security.principal=cn=directory manager" -j "java.naming.security.credentials=password" -j "java.naming.security.authentication=simple" -t q -o "imqDestinationName=mytestDestination" Adding a Queue object with the following attributes: imqDestinationDescription [Destination Description] A Description for the Destination Object imqDestinationName [Destination Name] mytestDestination Using the following lookup name: cn=mytestDestination The object’s read-only state: false To the object store specified by: java.naming.factory.initial com.sun.jndi.ldap.LdapCtxFactory java.naming.provider.url ldap://gwenig.coopsrc.com:389/ ou=sunmq,dc=coopsrc,dc=com java.naming.security.authentication simple java.naming.security.credentials netscape java.naming.security.principal cn=directory manager Object successfully added. |
You can check the newly created object with an ldapsearch or an LDAP browser.
This concludes the section on Storing Administered Objects on an LDAP Server. Skip the next section, which describes how to store Administered Objects in a file, and go to the section on Configuring the JMS Listener Adapter for this Scenario.
Storing Administered Objects in a File
PasswordSync and the JMS Listener can be configured to use administered objects stored in a file. If you are not storing administered objects on an LDAP server (Storing Administered Objects in an LDAP Directory), follow the instructions in this section.
Storing Connection Factory Objects
Open the Message Queue command-line tool (imqobjmgr) and type the commands in Storing Connection Factory Objects to store connection factory objects and specify a lookup name.
Example 11–3 Storing Connection Factory Objects and Specifying Lookup Names
#> ./imqobjmgr add -l "mytestFactory" -j "java.naming.factory.initial= com.sun.jndi.fscontext.RefFSContextFactory" -j "java.naming.provider.url=file:///home/gael/tmp" -t qf -o "imqAddressList=mq://gwenig.coopsrc.com:7676/jms" Adding a Queue Connection Factory object with the following attributes: imqAckOnAcknowledge [Message Service Acknowledgement of Client Acknowledgements] ... imqSetJMSXUserID [Enable JMSXUserID Message Property] false Using the following lookup name: mytestFactory The object’s read-only state: false To the object store specified by: java.naming.factory.initial com.sun.jndi.fscontext.RefFSContextFactory java.naming.provider.url file:///home/gael/tmp Object successfully added. To specify a destination: #> ./imqobjmgr add -l "mytestQueue" -j "java.naming.factory.initial=com.sun.jndi.fscontext.RefFSContextFactory" -j "java.naming.provider.url=file:///home/gael/tmp" -t q -o "imqDestinationName=myTestQueue" Adding a Queue object with the following attributes: imqDestinationDescription [Destination Description] A Description for the Destination Object imqDestinationName [Destination Name] myTestQueue Using the following lookup name: mytestQueue The object’s read-only state: false To the object store specified by: java.naming.factory.initial com.sun.jndi.fscontext.RefFSContextFactory java.naming.provider.url file:///home/gael/tmp Object successfully added. |
Creating the Destination on the Broker
By default, the Sun Message Queue broker allows auto-creation of the queue destination (see config.properties, where the default value for imq.autocreate.queue is true).
If the queue destination is not created automatically, you must create the destination object on the broker using the command shown in Creating the Destination on the Broker (where myTestQueue is the destination).
Example 11–4 Creating a Destination Object on the Broker
name (Queue name): #> cd /opt/sun/mq/bin #>./imqcmd create dst -t q -n mytestQueue Username: <admin> Password: <admin> Creating a destination with the following attributes: Destination Name mytestQueue Destination Type Queue On the broker specified by: ------------------------- Host Primary Port ------------------------- localhost 7676 Successfully created the destination. |
You can store administered objects in a directory or in a file:
-
In a directory: Using a directory is a centralized way of storing the Connection Factory and the Destination objects.
When you use a directory, these administered objects are stored as directory entries.
Note –If the Identity Manager PasswordSync servlet and the Identity Manager server are not on the same machine, then each of them must be able to access the .bindings file. You can repeat the administered object creation twice (on each machine) or you can copy the .bindings file to the proper location on each machine.
-
In a file: If the Identity Manager PasswordSync servlet and Identity Manager server are both running on the same server (or if you do not have a directory available), you can store the administrative objects in a file.
When you use a file, both administered objects are stored in a single file (called .bindings on both Windows and UNIX), under the directory you specified for the java.naming.provider.url (for example, file:///c:/temp on Windows or file:///tmp on UNIX).
Configuring the JMS Listener Adapter for this Scenario
Configure the JMS listener adapter on the application server. Follow the instructions in the section Adding and Configuring a JMS Listener Adapter.
Configuring Active Sync
Next, configure the JMS Listener for synchronization. Active Sync is required if you are using JMS, but it is not used for direct connections.
 To Configure the JMS Listener for Synchronization
To Configure the JMS Listener for Synchronization
-
In the Administrator interface, click Resources in the menu.
-
In the Resource List, select the JMS Listener checkbox.
-
In the Resource Actions list, select Edit Synchronization Policy.
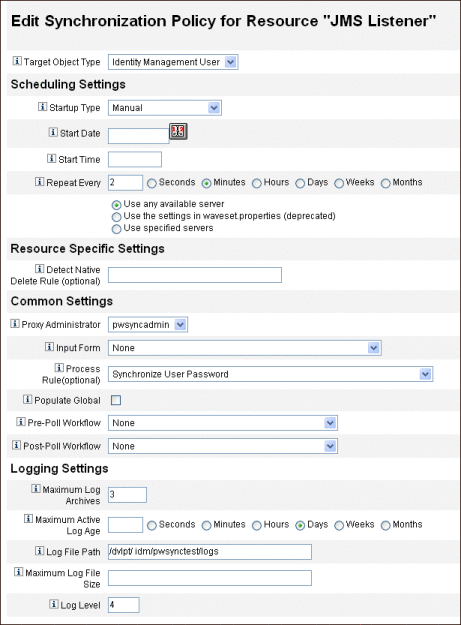
The Edit Synchronization page for the JMS Listener resource opens (Figure 11–15).
Figure 11–15 Configuring Active Sync for the JMS Listener
-
Under Common Settings, locate Proxy Administrator and select pwsyncadmin. (This administrator is associated with an empty form.)
-
Under Common Settings, locate Process Rule and select Synchronize User Password from the list. The default Synchronize User Password workflow takes each request that comes in from the JMS Listener adapter, checks out the ChangeUserPassword viewer, and then checks the ChangeUserPassword viewer back in.
-
In the Log File Path box, specify a path to a directory where the active and archived log files should be created.
-
For debugging purposes, set the Log Level to 4 to generate a verbose log.
-
Click Save.
Testing Your Configuration
-
Start the PasswordSync configuration application, if it is not already running.
By default, the configuration application is installed at Program Files -> Sun Java System Identity Manager PasswordSync -> Configuration.
-
When the PasswordSync Configuration dialog displays, click the Test button.
-
If using JMS, the Test Connection dialog displays, with a message stating whether the test connection completed successfully.
-
Click Close to close the Test Connection dialog.
-
Click OK to close the PasswordSync Configuration dialog.
The JMS Listener adapter then runs in debug mode, and generates debug information in a file, similar to the one in the following figure.
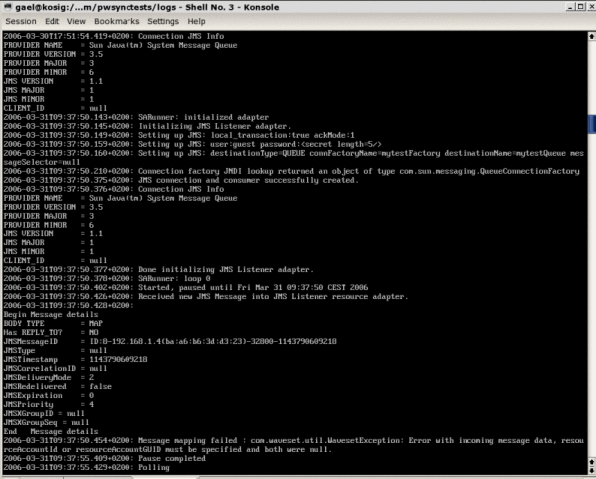
You can use the Windows PasswordSync Configuration application to debug the Windows side of your configuration.
Debugging PasswordSync on Windows
PasswordSync writes all failures to the Windows Event Viewer. (For help using Event Viewer, see Windows Help.) The source name for error log entries is PasswordSync.
See the Sun Identity Manager 8.1 System Administrator’s Guide for information on troubleshooting PasswordSync on Windows.
Uninstalling PasswordSync on Windows
To uninstall the PasswordSync application, go to the Windows Control Panel and select Add or Remove Programs. Then select Sun Java System Identity Manager PasswordSync and click Remove.
Note –
PasswordSync can also be uninstalled (or reinstalled) by loading the Identity Manager installation media and clicking on the pwsync\IdmPwSync.msi icon.
You must restart your system to complete the process.
Frequently Asked Questions about PasswordSync
This section answers some frequently asked questions about PasswordSync.
Question:Can PasswordSync be implemented without a Java Messaging Service?
Answer:Yes, but doing so eliminates the advantages of using a JMS to track password change events.
To implement PasswordSync without a JMS, launch the configuration application with the following flag:
Configure.exe -direct
When the -direct flag is specified, the configuration application displays the User tab.
If you implement PasswordSync without a JMS, you do not need to create a JMS Listener adapter. Therefore, you should omit the procedures listed in Deploying PasswordSync on the Application Server. If you want to set up notifications, you may need to alter the Change User Password workflow.
Note –
If you subsequently run the configuration application without specifying the -direct flag, PasswordSync will require a JMS to be configured. Relaunch the application with the -direct flag to bypass the JMS again.
Question:
Can PasswordSync be used in conjunction with other Windows password filters that are used to enforce custom password policies?
Answer:Yes, you can use PasswordSync in conjunction with other _WINDOWS_ password filters. It must, however, be the last password filter listed in the Notification Package registry value.
You must use this Registry path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Notification Packages (value of type REG_MULTI_SZ)
By default, the installer places the Identity Manager password intercept at the end of the list, but if you installed the custom password filter after the installation, you will be required to move lhpwic to the end of the Notification Packages list.
You can use PasswordSync in conjunction with other Identity Manager password policies. When policies are checked on the Identity Manager server side, all resource password policies must pass in order for the password synchronization to be pushed out to other resources. Consequently, you should make the Windows native password policy as restrictive as the most restrictive password policy defined in Identity Manager.
Note –
The password intercept DLL does not enforce any password policies.
Question:
Can the PasswordSync servlet be installed on a different application server than Identity Manager?
Answer:Yes. The PasswordSync servlet requires the spml.jar and idmcommon.jar jar files, in addition to any jar files required by the JMS application.
Question:Does the PasswordSync service send passwords over to the lh server in clear text?
Answer:Although best practice is to run PasswordSync over SSL, all sensitive data is encrypted before being sent to the Identity Manager server.
For information, see Configure PasswordSync for SSL.
Question:Why do some password changes result in com.waveset.exception.ItemNotLocked?
Answer:If you enable PasswordSync, a password change (even one initiated from the user interface), will result in a password change on the resource, which causes the resource to contact Identity Manager.
If you configure the passwordSyncThreshold workflow variable correctly, Identity Manager examines the user object and decides that it has already handled the password change. However, if the user or the administrator makes another password change for the same user, at the same time, the user object could be locked.
- © 2010, Oracle Corporation and/or its affiliates
