Chapter 3 User and Account Management
This chapter provides information and procedures for creating and managing users from the Identity Manager Administrator interface.
This information is organized into the following sections:
The Accounts Area of the Interface
A user is anyone who holds an Identity Manager system account. Identity Manager stores a range of data for each user. Collectively, this information forms a user’s Identity Manager identity.
The Identity Manager Accounts / User List page lets you manage Identity Manager users. To access this area, click Accounts on the Administrator interface menu bar.
The accounts list shows all Identity Manager user accounts. Accounts are grouped into organizations and virtual organizations, which are represented hierarchically in folders.
You can sort the accounts list by full name (Name), user last name (Last Name), or user first name (First Name). Click the header bar to sort by a column. Clicking the same header bar toggles between ascending and descending sort order. When you sort by full name (the Name column), then all items in the hierarchy, at all levels, are sorted alphabetically.
To expand the hierarchical view and see accounts in an organization, click the triangular indicator next to a folder. Collapse the view by clicking the indicator again.
Actions Lists in the Accounts Area
Use the actions lists (located at the top and bottom of the accounts area, as shown in Actions Lists in the Accounts Area), to perform a range of actions.
Actions list selections are divided among:
-
New Actions. Create users, organizations, and directory junctions.
-
User Actions. Edit, view, and change status of users; change and reset passwords; delete, enable, disable, unlock, move, update, and rename users; and run a user audit report.
-
Organization Actions. Perform a range of organization and user actions.
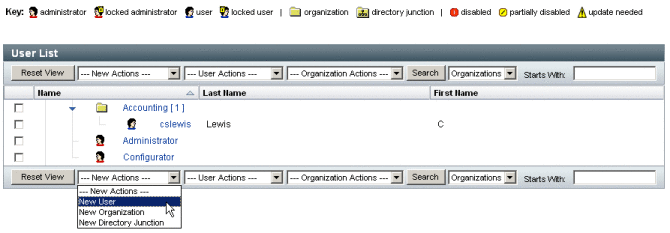
Searching in the Accounts List Area
Use the accounts area search feature to locate users and organizations. Select Organizations or Users from the list, enter one or more characters that the user or organization name starts with in the search area, and then click Search. For more information about searching in the accounts area, see Finding & Viewing User Accounts.
User Account Status
Icons that display next to each user account indicate current, assigned account status. Table 3–1 describes what each icon represents.
Table 3–1 User Account Status Icon Descriptions|
Indicator |
Status |
|---|---|
|
|
The user’s Identity Manager account is locked. Note that this icon only reflects the locked state of the Identity Manager account, not any of the user’s resource accounts. Users become locked after exceeding the maximum number of failed Identity Manager account login attempts as defined in the Identity Manager Account Policy. Only failed password or question logins to Identity Manager accounts are counted towards the maximum allowed. Therefore, if an Identity Manager login application (that is, the administrator interface, the end-user interface, and so on) does not include the Identity Manager Login Module in its login module group, then the Identity Manager failed password policy will not be considered. However, regardless of the stack of login modules configured for a given Identity Manager login application, failed question logins that exceed the maximum configured in the Identity Manager Account Policy can cause a user to become locked and this icon to be displayed. For information on how to unlock accounts see Unlocking User Accounts. |
|
|
The administrator Identity Manager account is locked. Note that this icon only reflects the locked state of the Identity Manager account, not any of the administrator’s resource accounts. For more information, see the description for the user lockout icon, above. |
|
|
The account is disabled on all assigned resources and on Identity Manager. (When an account is enabled, no icon appears.) For information about how to enable disabled accounts, see Disabling, Enabling, & Unlocking User Accounts. |
|
|
The account is partially disabled, meaning that it is disabled on one or more assigned resources. |
|
|
The system attempted but failed to create or update the Identity Manager user account on one or more resources. (When an account is updated on all assigned resources, no icon appears.) |
Note –
In the Manager column, a manager’s user name appears inside parentheses if Identity Manager cannot find an Identity Manager account that matches the name listed.
The User Pages (Create/Edit/View)
This section describes the Create User, Edit User, and View User pages that are available in the Administrator interface. Instructions on how to use these pages appear later in this chapter.
Note –
This documentation describes the default set of Create User, Edit User, and View User pages that ship with Identity Manager. To better reflect your business processes or specific administrator capabilities, however, you should create custom user forms specifically for your environment. For more information about customizing the user form, see Chapter 3, Identity Manager Forms, in Sun Identity Manager Deployment Reference.
The default Identity Manager user pages are organized into the following tabs or sections:
-
Identity
-
Assignments
-
Security
-
Delegations
-
Attributes
-
Compliance
Identity Tab
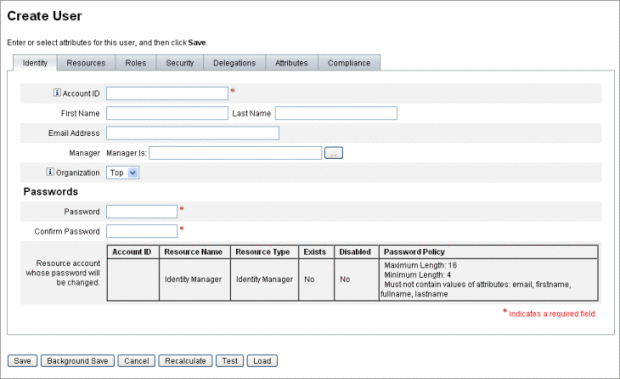
The Identity area defines a user’s account ID, name, contact information, manager, governing organization, and Identity Manager account password. It also identifies the resources to which the user has access, and the password policy governing each resource account.
Note –
For information about setting up account password policies, read the section in this chapter titled Managing Account Security and Privileges.
The following figure illustrates the Identity area of the Create User page.
Figure 3–1 Create User - Identity
Resources Tab
The Resources area provides for the direct assignment of resources and resource groups to a user. Resource exclusions can also be assigned.
Directly assigned resources supplement resources that are indirectly assigned to the user through role assignment. Role assignment profiles a class of users. Roles define user access to resources through indirect assignment.
Roles Tab
The Roles tab is used to assign one or more roles to a user, and manage those role assignments.
See To Assign Roles to a User for information about this tab.
Security Tab
In Identity Manager terminology, a user who is assigned extended capabilities is an Identity Manager administrator. Use the Security tab to assign a user administrator privileges.
For more information on using the Security tab to create administrators, see Creating and Managing Administrators.
The Security form consists of the following sections.
-
Admin roles. Assigns one or more administrative roles to the user. A role is a specific pairing of capabilities and controlled organizations that facilitates assigning administrative duties to users in a coordinated way.
-
Capabilities. Enables rights in the Identity Manager system. Each Identity Manager administrator is assigned one or more capabilities, frequently aligned with job responsibilities.
Capabilities are discussed on Understanding and Managing Capabilities. A list of task-based capabilities with definitions is included in Appendix D, Capabilities Definitions on Appendix D, Capabilities Definitions. This appendix also lists the tabs and subtabs that may be accessed with each capability.
-
Controlled organizations. Assigns organizations that this user has rights to manage as an administrator. He can manage objects in the assigned organization and in any organizations below that organization in the hierarchy.
Note –
To have administrator capabilities, a user must be assigned at least one Admin role, or one or more capabilities AND one or more controlled organizations. For more information about Identity Manager administrators, seeUnderstanding Identity Manager Administration.
-
User Form. Specifies the user form that the administrator will use when creating and editing users. If None is selected, the administrator will inherit the user form assigned to his organization.
-
View User Form. Specifies the user form that the administrator will use when viewing users. If None is selected, the administrator will inherit the view user form assigned to his organization.
-
Account policy. Establishes password and authentication limits.
Delegations Tab
The Delegations tab on the Create User page lets you delegate work items to other users for a specified length of time. For more information about delegating work items, read Delegating Work Items.
Attributes Tab
The Attributes tab on the Create User page defines account attributes associated with assigned resources. Listed attributes are categorized by assigned resource, and differ depending on which resources are assigned.
Compliance Tab
The Compliance tab:
-
Lets you select the attestation and remediation forms for the user account.
-
Specifies the assigned audit policies for the user account, including those in effect through the user’s Organization assignment. These policy assignments can be changed only by editing the user’s current organization or moving the user to another Organization.
-
Indicates the current status of policy scans, violations, and exemptions (as illustrated by the following figure), if applicable for the user account. The information includes the date and time of the last audit policy scan for the selected user.
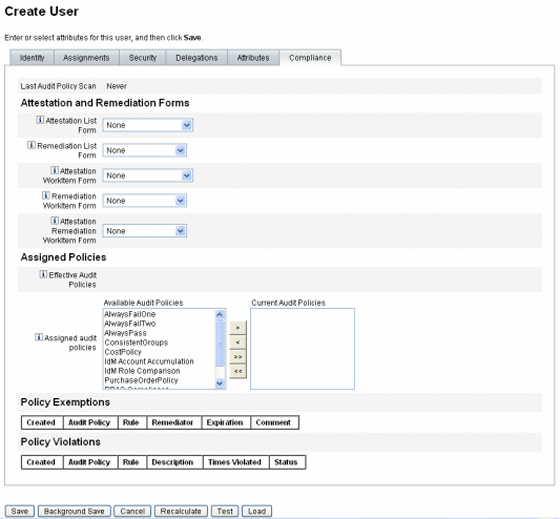
To assign audit policies, move selected policies from the Available Audit Policies list to the Current Audit Policies list.
Note –
You can view compliance violations logged for a user for a specific time period, by selecting View Compliance Violation Log from the User Actions list and specifying the range of entries to view.
Creating Users and Working with User Accounts
From the Accounts/User List page in the Administrator interface, you can perform a range of actions on the following system objects:
-
Administrators & Users. View, create, edit, move, rename, deprovision, enable, disable, update, unlock, delete, unassign, unlink, and audit.
For more information about creating and editing administrator accounts, see Understanding Identity Manager Administration.
-
Organizations. Create, edit, refresh, and perform user actions on members of the organization.
For more information on organizations, see Understanding Identity Manager Organizations.
-
Directory Junctions. Create a hierarchically related set of organizations to mirror a directory resource's actual set of hierarchical containers.
For more information about directory junctions, see Understanding Directory Junctions and Virtual Organizations.
Enabling Process Diagrams
Process diagrams depict the workflow that Identity Manager follows when it creates or otherwise acts on a user account. When enabled, process diagrams display on the results page or task summary page that is created when Identity Manager completes the task.
In Identity Manager version 8.0, process diagrams were disabled for both new and upgrade installations.
 To Enable Process Diagrams for Use in Identity Manager
To Enable Process Diagrams for Use in Identity Manager
-
Open the system configuration object for editing by following the procedure on Editing Identity Manager Configuration Objects.
-
Locate the following XML element:
<Attribute name=’disableProcessDiagrams’> <Boolean>true</Boolean> </Attribute>
-
Change the true value to false.
-
Click Save.
-
Restart your server (or servers) in order for the change to take effect.
Process diagrams can also be enabled in the end-user interface, but only if they are first enabled in the Administrator interface using the steps described above. For details, see To Enable Process Diagrams in the End-User Interface.
 To Create a User in Identity Manager
To Create a User in Identity Manager
You can create and manage users from the Accounts tab on the Administrator interface menu bar.
-
In the Administrator interface, click Accounts.
-
To create a user in a specific organization, select the organization, then select New User from the New Actions list.
Otherwise, to create a user account in the Top organization, select New User from the New Actions list.
-
Complete the information in the following tabs or sections.
-
Identity. Name, organization, password, and other details. (See Identity Tab.)
-
Resources. Individual resource and resource group assignments, as well as resource exclusions. (See Resources Tab.)
-
Roles. Role assignments. For information on roles, see Understanding and Managing Roles. See To Assign Roles to a User for instructions on completing the Roles tab.
-
Security. Admin roles, controlled organizations and capabilities. Also, user form settings and account policy. (See Security Tab.)
-
Delegations. Work item delegations. (See Delegations Tab.)
-
Attributes. Specific attributes for assigned resources. (See Attributes Tab.)
-
Compliance. Select attestation and remediation forms for the user account. The compliance area also lets you specify the assigned audit policies for the user account, including those in effect through the user’s organization assignment. Indicates the current status of policy scans, violations, and exemptions, and includes information about the user’s last audit policy scan. (See Attributes Tab.)
Note that selections available in one area may depend on selections you make in another.
To better reflect your business processes or specific administrator capabilities, you should customize the user form specifically for your environment. For more information about customizing the user form, see Customizing Forms in Sun Identity Manager Deployment Reference.
-
-
When you are finished, Save the account.
You have two options for saving a user account:
-
Save. Saves the user account. If you assign a large number of resources to the account, this process could take some time.
-
Background Save. This process saves a user account as a background task, which allows you to continue working in Identity Manager. A task status indicator displays on the Accounts page, the Find User Results page, and the Home page, for each save in progress.
Status indicators, as described in the following table, help you monitor the progress of the save process.
Status Indicator
Status

The save process is in progress.
The save process is suspended. Often, this means that the process is waiting for approval.

The process completed successfully. This does not mean that the user was successfully saved; rather that the process completed with no errors.
The process has not yet started.

The process completed with one or more errors.
By moving your mouse over the user icon that displays within the status indicator, you can see details about the background save process.
Note –If sunrise is configured, creating a user creates a work item that can be viewed from the Approvals tab. Approving this item overrides the sunrise date and creates the account. Rejecting the item cancels account creation. For more information about configuring sunrise, see Configuring the Sunrise and Sunset Tab.
-
Creating Multiple Resource Accounts for a User
Identity Manager provides the ability to assign multiple resource accounts to a single user. It does this by allowing multiple resource account types or types of accounts to be defined for each resource. Resource account types should be created as needed to match each functional account type on the resource. For example, AIX SuperUser or AIX BusinessAdmin.
Why Assign Multiple Accounts per User per Resource?
In some situations, an Identity Manager user may require more than one account on a resource. A user can have several different job functions related to the resource. For example, the user can be both a user and administrator of the resource. Best practice suggests using separate accounts for each function. That way, if one account is compromised, the access granted by the other accounts is still secure.
Configuring Types of Accounts
For a resource to support multiple accounts for a single user, the resource account types must first be defined in Identity Manager. To define resource account types for a resource, use the Resource Wizard. For information, see Managing the Resources List.
You must enable and configure resource account types before assigning them to users.
Assigning Types of Accounts
Once you have defined account types, you can assign them to a resource. Identity Manager treats each assignment of an account type as a separate account. As a result, each distinct assignment in a role can have different attributes set.
Similar to the single account per resource case, all assignments of a specific type create only one account, regardless of the number of assignments.
Although you can assign users to any number of different types of accounts on a resource, each user can be assigned one account of a given type on a resource. The exception to this rule is the built-in “default” type. Users can have any number of accounts of default type on a resource. It is not recommended that you do this however, as this leads to ambiguity when referencing accounts in forms and views.
Finding & Viewing User Accounts
The Identity Manager find feature lets you search for user accounts. After you enter and select search parameters, Identity Manager finds all accounts that match your selections.
To search for accounts, select Accounts -> Find Users from the menu bar. You can search for accounts by using one or more of these search types:
-
Account detail (such as user name, email address, or last name, or first name). These choices depend on your institution’s specific Identity Manager implementation.
-
User’s manager. The manager’s user name appears in parentheses if the user name does not match an existing account in Identity Manager.
-
Resource account status. Options include:
-
Disabled. User cannot access any Identity Manager or assigned resource accounts.
-
Partially Disabled. User cannot access one or more assigned resource accounts.
-
Enabled. User has access to all assigned resource accounts.
-
-
Assigned resource. Options include:
-
Role (see To Find Users Assigned to a Specific Role)
-
Organization
-
Organizational control
-
Capabilities
-
Admin role
-
-
User account status. Options include:
-
Locked. User account is locked because the maximum number of failed password or question login attempts exceeds the maximum allowed.
-
Not Locked. User account access is not restricted.
-
-
Update status. Options include:
-
no. User accounts that have not been updated on any resource.
-
some. User accounts that have been updated on at least one, but not all, assigned resources.
-
all. User accounts that have been updated on all assigned resources.
-
The search results list shows all accounts that match your search.
From the results page, you can:
-
Select user accounts to edit. To edit an account, click it in the search results list; or select it in the list, and then click Edit.
-
Perform actions (such as enable, disable, unlock, delete, update, or change/reset passwords) on one or more accounts. To perform an action, select one or more accounts in the search results list, and then click the appropriate action.
-
Create user accounts.
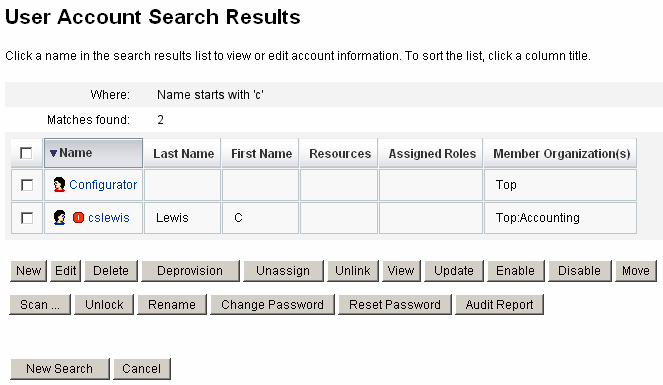
Editing Users
The information in this section covers viewing, editing, reassigning, and renaming user accounts.
 To View User Accounts
To View User Accounts
Use the View User page and perform the following steps to view account information.
-
In the Administrator interface, click Accounts in the menu.
The User List page opens.
-
Select the box next to the user whose account you want to view.
-
In the User Actions drop-down menu, select View.
The View User page displays a subset of the user’s identity, assignments, security, delegations, attributes, and compliance information. The information on the View User page is view-only and cannot be edited.
-
Click Cancel to return to the Accounts list.
 To Edit User Accounts
To Edit User Accounts
Use the Edit User page and perform the following steps to edit account information.
-
In the Administrator interface, click Accounts in the menu.
-
Select the box next to the user whose account you want to edit.
-
In the User Actions drop-down menu, select Edit.
-
Make and save your changes.
Identity Manager displays the Update Resource Accounts page. This page shows resource accounts assigned to the user and the changes that will apply to the account.
-
Select Update All resource accounts to apply changes to all assigned resources, or individually select none, one, or more resource accounts associated with the user to update.
-
Click Save again to complete the edit, or click Return to Edit to make further changes.
Figure 3–2 Edit User (Update Resource Accounts)
Reassigning Users to Another Organization
The move action allows you to remove one or more users from one organization and reassign, or move, the users to a new organization.
 To Move a User
To Move a User
-
In the Administrator interface, click Accounts in the menu.
The User List page opens.
-
Select the box next to the user (or users) to be moved.
-
In the User Actions drop-down menu, select Move.
The Change Organization of Users task page opens.
-
Select the organization that you want to reassign the user to and click Launch.
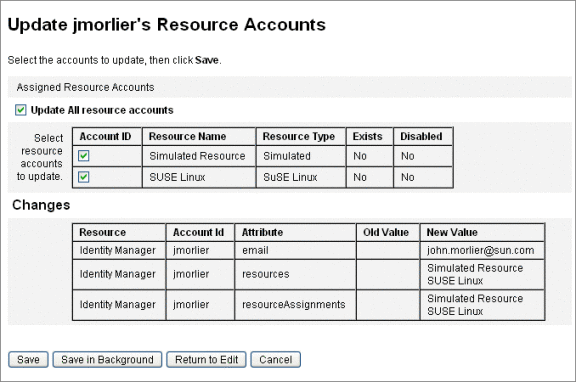
Renaming Users
Typically, renaming an account on a resource is a complex action. Because of this, Identity Manager provides a separate feature to rename a user’s Identity Manager account, or one or more resource accounts, that are associated with that user.
To use the rename feature, select a user account in the list, and then select the Rename option from the User Actions list.
The Rename User page allows you to change the user account name, associated resource account names, and resource account attributes associated with the user’s Identity Manager account.
Note –
Some resource types do not support account renaming.
As shown in the following figure, the user has an assigned Active Directory resource.
During the renaming process, you can change:
-
Identity Manager user account name
-
Active Directory resource account name
-
Active Directory resource attribute (fullname)
Updating Resources Associated with an Account
In an update action, Identity Manager updates the resources that are associated with a user account. Updates performed from the accounts area send any pending changes that were previously made to a user to the resources selected.
This situation may occur if:
-
A resource was unavailable when updates were made.
-
A change was made to a role or resource group that needed to be pushed to all users assigned to that role or resource group. In this case, you should use the Find User page to search for users, and then select one or more users on which to perform the update action.
When you update the user account, you have the following options:
-
Choose whether assigned resource accounts will receive the updated information.
-
Update all resource accounts, or select individual accounts from a list.
Updating Resources on a Single User Account
To update a user account, select it in the list, and then select Update from the User Actions list.
On the Update Resource Accounts page, select one or more resources to update, or select Update All resource accounts to update all assigned resource accounts. When finished, click OK to begin the update process. Alternatively, click Save in Background to perform the action as a background process.
A confirmation page confirms the data sent to each resource.
Figure 3–3 illustrates the Update Resource Accounts page.
Figure 3–3 Update Resource Accounts

Updating Resources on Multiple User Accounts
You can update two or more Identity Manager user accounts at the same time. Select more than one user account in the list, and then select Update from the User Actions list.
Note –
When you choose to update multiple user accounts, you cannot select individually assigned resource accounts from each user account. Rather, this process updates all resources on all user accounts you select.
Deleting Identity Manager User Accounts
In Identity Manager, an Identity Manager user account is deleted in the same way that a remote resource account is deleted. Follow the steps for deleting a resource account, but instead of selecting a remote resource account for deletion, select the Identity Manager account.
Note –
If a user has outstanding work items, or if a user has outstanding work items that have been delegated to another user, Identity Manager will not allow the user’s Identity Manager account to be deleted. The delegated work items either need to be resolved or forwarded to another user before the user’s Identity Manager account can be deleted.
For more information, see Deleting Resources from a Single User Account and Deleting Resources from Multiple User Accounts.
Deleting Resources from User Accounts
Identity Manager provides several deletion operations that can be used to remove Identity Manager user account access from a resource:
-
Delete. For each resource selected, Identity Manager deletes the user’s account on the remote resource. (To delete a user from Identity Manager, select Identity Manager as the resource.)
-
Deleted resource accounts are automatically unlinked from the Identity Manager user.
-
Deleted resource accounts are not unassigned from the user. The resource remains assigned to the user unless the unassign action is also selected.
-
-
Unassign. For each resource selected, Identity Manager removes the resource from the user’s list of assigned resources.
-
Unassigned resource accounts are automatically unlinked from the Identity Manager user.
-
The user account on the remote resource is not deleted. The account remains intact unless the delete action is also selected.
-
-
Unlink. For each resource selected, the user’s resource account information is removed from Identity Manager.
-
The user’s account on the remote resource remains intact unless a delete action is also selected.
-
The resource remains on the user’s list of assigned resources unless an unassign action is also selected.
-
If you unlink an account that has been indirectly assigned to the user through a role or resource group, the link may be restored when the user is updated.
-
Although deprovision appears as a user-action in the User List page menus, there are actually only three Deletion actions in Identity Manager: delete, unassign, and unlink.
To deprovision a remote resource, use the delete and unassign actions on the resource.
Deleting Resources from a Single User Account
Use the following procedure to perform a delete operation on a single Identity Manager user. By working with one user account at a time, you can specify different delete, unassign, and/or unlink operations for individual resource accounts.
 To Start a Delete, Unassign, or Unlink Action for
a Single User Account
To Start a Delete, Unassign, or Unlink Action for
a Single User Account
-
In the Administrator interface, click Accounts in the main menu.
The User List page displays on the List Accounts tab.
-
Select a user and click the User Actions drop-down menu.
-
Select any of the Deletion actions (Delete, Deprovision, Unassign, or Unlink) from the list.
Identity Manager displays the Delete Resource Accounts page (Figure 3–4).
-
Complete the form. For more information on the Delete, Unassign, and Unlink actions, see Deleting Resources from User Accounts.
-
Click OK.
Figure 3–4 shows the Delete Resource Accounts page. In the screen capture, the user jrenfro has one active account on a remote resource (the Simulated Resource). The Delete action is selected, which means that when the form is submitted, jrenfro’s account on the resource will be deleted. Because deleted accounts are automatically unlinked, the account information for this resource will be removed from Identity Manager. The Simulated Resource will remain assigned to jrenfro because the Unassign action is not selected.
To delete jrenfro’s Identity Manager account, the Delete action should be selected for Identity Manager.
Figure 3–4 The Delete Resource Accounts page
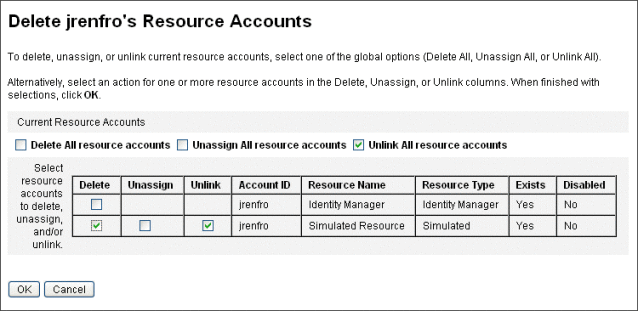
Deleting Resources from Multiple User Accounts
You can perform a delete operation on more than one Identity Manager user account at a time, however, you can only perform the selected delete operation on all of the users’ resource accounts.
Delete operations can also be performed using Identity Manager’s Bulk Account Actions feature. See Delete, DeleteAndUnlink, Disable, Enable, Unassign, and Unlink Commands.
 To Start A Delete, Unassign, or Unlink Action for
Multiple Users
To Start A Delete, Unassign, or Unlink Action for
Multiple Users
-
In the Administrator interface, click Accounts in the main menu.
The User List page displays on the List Accounts tab.
-
Select one or more users and click the User Actions drop-down menu.
-
Select any of the Deletion actions (Delete, Deprovision, Unassign, or Unlink) from the list.
Identity Manager displays the Confirm Delete, Unassign, or Unlink page (Figure 3–5).
-
Specify the action to be performed.
The options include:
-
Delete user only. Deletes the users’ Identity Manager accounts. This option does not delete or unassign the users’ resource accounts.
-
Delete user and resource accounts. Deletes the users’ Identity Manager accounts and all of the users’ resource accounts.
-
Delete resource accounts only. Deletes all of the users’ resource accounts. This option does not unassign the resource accounts, nor does it delete the users’ Identity Manager accounts.
-
Delete resource accounts and unassign directly assigned resources from user. Deletes and unassigns all of the users’ resource accounts, but does not delete the users’ Identity Manager accounts.
-
Unassign directly assigned resource accounts from user. Unassigns directly assigned resource accounts. This option does not delete the users’ accounts on the remote resources. Resource accounts assigned through a role or resource group are not affected.
-
Unlink resource accounts from user. The users’ resource account information is removed from Identity Manager. The users’ accounts on the remote resources are not deleted and are not unassigned. Accounts that are indirectly assigned to the users through a role or resource group may be restored when the users are updated.
-
-
Click OK.
Figure 3–5 shows the Confirm Delete, Unassign, or Unlink page. The top portion of the page displays the six available actions that can be carried out for multiple users. The bottom portion of the page displays the users who will be affected by the selected action.
Figure 3–5 The Confirm Delete, Unassign, or Unlink Page
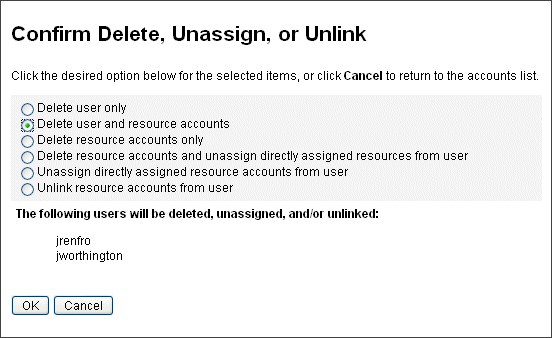
Changing User Passwords
All Identity Manager users are assigned a password. When set, the Identity Manager user password is used to synchronize the user’s resource account passwords. If one or more resource account passwords cannot be synchronized (for example, to comply with required password policies), you can set them individually.
Note –
For information about account password policies, as well as general information about user authentication, see Managing Account Security and Privileges.
 Changing Passwords from the User List Page
Changing Passwords from the User List Page
You can use the Change Password User Action from the User List page (Accounts -> List Accounts) to change a user account password from the User List page. Follow these steps:
-
In the Administrator interface, click Accounts in the main menu.
The User List page displays on the List Accounts tab.
-
Select a user and click the User Actions drop-down menu.
-
To change the password, select Change Password.
The Change User Password page opens.
-
Type the new password and click the Change Password button.
 To Change Passwords from the Main Menu
To Change Passwords from the Main Menu
To change a user account password from the main menu, follow these steps:
-
In the Administrator interface, click Passwords in the main menu.
The Change User Password page appears by default.
Figure 3–6 Change User Password
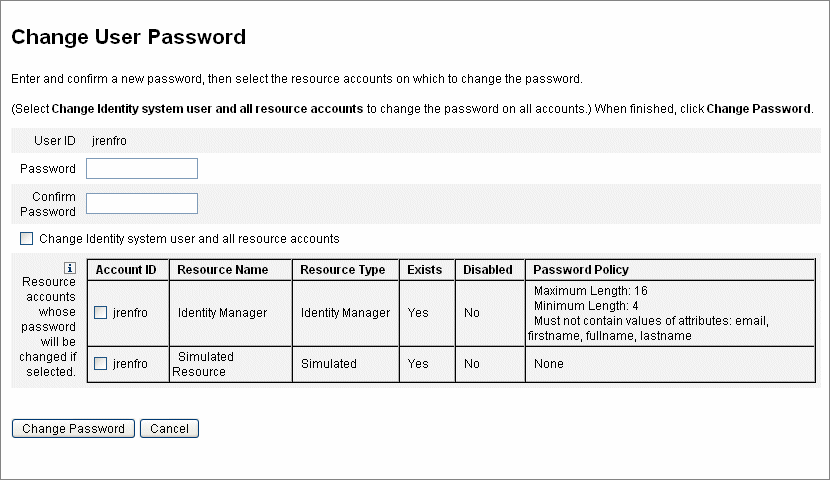
-
Select a search term (such as account name, email address, last name, or first name), and then a search type (starts with, contains, or is).
-
Type one or more letters of a search term in the entry field, and then click Find. Identity Manager returns a list of all users whose IDs contain the entered characters. Click to select a user and return to the Change User Password page.
-
Enter and confirm new password information, and then click Change Password to change the user password on the listed resource accounts. Identity Manager displays a workflow diagram that shows the sequence of actions taken to change the password.
Resetting User Passwords
The process for resetting Identity Manager user account passwords is similar to the change process. The reset process differs from a password change in that you do not specify a new password. Rather, Identity Manager randomly generates a new password (depending on your selections and password policies) for the user account, resource accounts, or a combination of these.
The policy assigned to the user (by direct assignment or through the user’s organization) controls several reset options, including:
-
How often a password can be reset before resets are disabled
-
Where the new password is displayed or sent
Depending on the Reset Notification Option selected for the role, Identity Manager emails the new password to the user or displays it (on the Results page) to the Identity Manager administrator requesting the reset.
 Resetting Passwords from the User List Page
Resetting Passwords from the User List Page
The Reset Password user action is available on the User List page (Accounts > List Accounts).
To reset a password from the User List page, follow these steps:
-
In the Administrator interface, click Accounts in the main menu. The User List page displays on the List Accounts tab.
-
Select a user and click the User Actions drop-down menu.
-
To reset the password, select Reset Password.
The Reset User Password page opens.
-
Click the Reset Password button.
 To Expire Passwords Using the Identity Manager Account
Policy
To Expire Passwords Using the Identity Manager Account
Policy
When you reset a user password, the password is immediately expired by default. Consequently, the first time users log in after a password reset, they must select a new password to gain access. You can use the Edit the Reset User Password form to override this default, so that the user’s password will expire according to the expire password policy set in the Identity Manager Account Policy associated with that user.
Use the following process to override the default change-password requirement:
-
Edit the Reset User Password Form and set the following value to false.
resourceAccounts.currentResourceAccounts[Lighthouse].expirePassword
-
Use the Reset option in the Identity Manager Account Policy to specify when a password expires.
The settings include
-
permanent. Identity Manager uses the time period specified in the passwordExpiry policy attribute to calculate the relative date from the current date when the password is reset, and then set that date on the user. If no value is specified, the changed or reset password never expires.
-
temporary. Identity Manager uses the time period specified in the tempPasswordExpiry policy attribute to calculate the relative date from the current date when the password is reset, and then set that date on the user. If no value is specified, the changed or reset password never expires. If tempPasswordExpiry is set to a value of 0, then the password is expired immediately.
The tempPasswordExpiry attribute applies only when passwords are reset (randomly changed). It does not apply to password changes.
-
Disabling, Enabling, & Unlocking User Accounts
This section describes how to disable and enable Identity Manager user accounts. It also describes how to help users who have become locked out of their Identity Manager accounts.
 To Disable User Accounts
To Disable User Accounts
When you disable a user account, you alter that account so that the user can no longer log in to either Identity Manager or to his assigned resource accounts.
Note that administrators can disable user accounts from the Administrator interface, but they cannot lock user accounts. Accounts can only become locked if the user exceeds the allowable number of unsuccessful login attempts defined by the Identity Manager account policy
Note –
If an assigned resource does not have native support for account disabling, but does support password changes, then Identity Manager can be configured to disable user accounts on that resource by assigning new, randomly generated passwords.
Use the following steps to ensure that this functionality works correctly:
-
Open the “Identity System Parameters” page in the Edit Resource Wizard. (See Managing Resources for instructions on how to open the wizard.)
-
In the “Account Features Configuration” table verify that both the Password feature and the Disable feature do not have check marks in the Disable? column. (To display the Disable feature, select Show All Features.)
If the Disable feature does have a check mark in the Disable? column, accounts in the resource cannot be disabled.
Disabling Single User Accounts
To disable a user account, select it in the User List, and then select Disable from the User Actions drop-down menu.
On the displayed Disable page, select the resource accounts to disable, and then click OK. Identity Manager displays the results of disabling the Identity Manager user account and all associated resource accounts. The accounts list indicates that the user account is disabled.
Disabling Multiple User Accounts
You can disable two or more Identity Manager user accounts at the same time. Select more than one user account in the list, and then select Disable from the User Actions list.
Note –
When you choose to disable multiple user accounts, you cannot select individually assigned resource accounts from each user account. Rather, this process disables all resources on all user accounts you select.
 To Enable User Accounts on a Resource Through Password
Resets
To Enable User Accounts on a Resource Through Password
Resets
User account enabling reverses the disabling process.
Depending on selected notification options, Identity Manager also displays the password on the administrator’s results page.
The user can then reset his password (through the authentication process), or a user with administrator privileges can reset it.
Note –
If an assigned resource does not have native support for account enabling, but does support password changes, then Identity Manager can be configured to enable user accounts on that resource through password resets.
To ensure that this functionality works correctly, do the following:
-
Open the “Identity System Parameters” page in the Edit Resource Wizard. (See Managing Resources for instructions on how to open the wizard.)
-
In the “Account Features Configuration” table, verify that both the Password feature and the Enable feature do not have check marks in the Disable? column. (To display the Enable feature, select Show All Features.)
If the Enable feature does have a check mark in the Disable? column, accounts in the resource cannot be enabled.
Enabling Single User Accounts
To enable a user account, select it in the list, and then select Enable from the User Actions list.
On the displayed Enable page, select the resources to enable, and then click OK. Identity Manager displays the results of enabling the Identity Manager account and all associated resource accounts.
Enabling Multiple User Accounts
You can enable two or more Identity Manager user accounts at the same time. Select more than one user account in the list, and then select Enable from the User Actions list.
Note –
When you choose to enable multiple user accounts, you cannot select individually assigned resource accounts from each user account. Rather, this process enables all resources on all user accounts you select.
Unlocking User Accounts
Users become locked out if they are unsuccessful at logging in to Identity Manager. To become locked out, the user has to exceed the allowable number of unsuccessful login attempts defined by the Identity Manager account policy.
Note –
Only login attempts on an Identity Manager user interface are counted towards an Identity Manager lockout (that is, either the administrator interface, the end-user interface, the command-line interface, or the SPML API interface). Failed login attempts on resource accounts are not counted and will not cause the user to be locked out of their Identity Manager account.
The Identity Manager account policy establishes the maximum number of failed password or question login attempts that can be made.
-
Users who exceed the maximum number of failed password login attempts are locked out of all Identity Manager application interfaces, including the Forgot My Password interface.
-
Users who exceed the maximum number of failed question login attempts can authenticate to any Identity Manager application interface except Forgot My Password.
Failed Password Login Attempts
Users who are locked out of Identity Manager due to excessive failed password login attempts will not be able to log in until an administrator unlocks the account or until the lock expires.
-
An administrator can unlock an account if the administrator has administrative control of the user’s member organization, as well as the Unlock User capability.
-
If a Lock Timeout value is set in the Identity Manager Account Policy, a lock placed on an account will eventually expire. The Lock Timeout value for failed password login attempts is set by the Account lock created by failed password-logins expires in value.
Failed Question Login Attempts
Users who are locked out of the Forgot My Password interface due to excessive failed question login attempts will not be able to log in to that interface until an administrator unlocks the account, or until the locked user (or a user with appropriate capabilities) changes or resets the user’s password, or until the lock expires.
-
An administrator can unlock an account if the administrator has administrative control of the user’s member organization, as well as the Unlock User capability.
-
If a Lock Timeout value is set in the Identity Manager Account Policy, a lock placed on an account will eventually expire. The Lock Timeout value for failed question login attempts is set by the Account lock created by failed question-logins expires in value.
An administrator with appropriate capabilities can perform the following operations on a user in locked state:
-
Update (including resource reprovisioning)
-
Change or reset password
-
Disable or enable
-
Rename
-
Unlock
To unlock accounts, select one or more user accounts in the list, and then select Unlock Users from the User Actions or Organization Actions list.
Bulk Account Actions
You can perform several bulk actions on Identity Manager accounts, which allow you to act on multiple accounts at the same time.
You can initiate the following Bulk actions:
-
Delete. Deletes, unassigns, and unlinks selected resource accounts. Select the “Target the Identity Manager Account” option to also delete each user’s Identity Manager account.
-
Delete and Unlink. Deletes any selected resource accounts and unlinks the accounts from the users.
-
Disable. Disables any selected resource accounts. Select the “Target the Identity Manager Account” option to also disable each user’s Identity Manager account.
-
Enable. Enables any selected resource accounts. Select the “Target the Identity Manager Account” option to enable each user’s Identity Manager account.
-
Unassign, Unlink. Unlinks any selected resource accounts and removes the Identity Manager user account’s assignments to those resources. Unassigning does not remove the account from the resource. You cannot unassign an account that has been indirectly assigned to the Identity Manager user through a role or resource group.
-
Unlink. Removes a resource account’s association (link) with the Identity Manager user account. Unlinking does not remove the account from the resource. If you unlink an account that has been indirectly assigned to the Identity Manager user through a role or resource group, the link may be restored when the user is updated.
Bulk actions work best if you have a list of users in a file or application, such as an email client or spreadsheet program. You can copy and paste the list into a field on this interface page, or you can load the list of users from a file.
Many of these actions can be performed on the results of a user search. Use the Find Users page (Accounts -> Find Users) to search for users.
You can save the results of a bulk account operation to a CSV file by clicking Download CSV when the task results appear upon completion of the task.
Launching Bulk Account Actions
 To Launch Bulk Account Actions
To Launch Bulk Account Actions
-
In the Administrator interface, click Accounts in the main menu.
-
Click Launch Bulk Actions in the secondary menu.
-
Complete the form and then click Launch.
Identity Manager launches a background task to perform the bulk actions.
To monitor the status of the bulk actions task, click Server Tasks in the main menu, and then click All Tasks.
Using Action Lists
You can specify a list of bulk actions using comma-separated values (CSV) format. This allows you to provide a mix of different action types in a single action list. In addition, you can specify more complicated creation and update actions.
The CSV format consists of two or more input lines. Each line consists of a list of values separated by commas. The first line contains field names. The remaining lines each correspond to an action to be performed on an Identity Manager user, the user’s resource accounts, or both. Each line should contain the same number of values. Empty values will leave the corresponding field value unchanged.
Two fields are required in any bulk action CSV input:
-
user. Contains the name of the Identity Manager user.
-
command. Contains the action taken on the Identity Manager user. Valid commands are:
-
Delete. Deletes, unassigns, and unlinks resource accounts, the Identity Manager account, or both.
-
DeleteAndUnlink. Deletes and unlinks resource accounts.
-
Disable. Disables resource accounts, the Identity Manager account, or both.
-
Enable. Enables resource accounts, the Identity Manager account, or both.
-
Unassign. Unassigns and unlinks resource accounts.
-
Unlink. Unlinks resource accounts.
-
Create. Creates the Identity Manager account. Optionally creates resource accounts.
-
Update. Updates the Identity Manager account. Optionally creates, updates, or deletes resource accounts.
-
CreateOrUpdate. Performs a create action if the Identity Manager account does not already exist. Otherwise, it performs an update action.
-
Delete, DeleteAndUnlink, Disable, Enable, Unassign, and Unlink Commands
If you are performing Delete, DeleteAndUnlink, Disable, Enable, Unassign, or Unlink actions, the only additional field you need to specify is resources. Use the resources field to specify which accounts on which resources will be affected.
The resources field can have the following values:
-
all. Process all resource accounts including the Identity Manager account.
-
resonly. Process all of the resource accounts excluding the Identity Manager account.
-
resource_name [ | resource_name ... ]. Process the specified resource accounts. Specify Identity Manager to process the Identity Manager account.
The following is an example of the CSV format for several of these actions:
command,user,resources Delete,John Doe,all Disable,Jane Doe,resonly Enable,Henry Smith,Identity Manager Unlink,Jill Smith,Windows Active Directory|Solaris Server
Create, Update, and CreateOrUpdate Commands
If you are performing Create, Update, or CreateOrUpdate commands, you can specify fields from the User View in addition to the user and command fields. The field names used are the path expressions for the attributes in the views. See User View Attributes in Sun Identity Manager Deployment Reference for information about the attributes that are available in the User View. If you are using a customized User Form, then the field names in the form contain some of the path expressions that you can use.
Some of the more common path expressions used in bulk actions are:
-
waveset.roles. A list of one or more role names to assign to the Identity Manager account.
-
waveset.resources. A list of one or more resource names to assign to the Identity Manager account.
-
waveset.applications. A list of one or more role names to assign to the Identity Manager account.
-
waveset.organization. The organization name in which to place the Identity Manager account.
-
accounts[resource_name].attribute_name. A resource account attribute. The names of the attributes are listed in the schema for the resource.
The following example illustrates the CSV format for create and update actions:
command,user,waveset.resources,password.password, password.confirmPassword,accounts[Windows Active Directory].description, accounts[Corporate Directory].location Create,John Doe, Windows Active Directory|Solaris Server,changeit,changeit,John Doe - 888-555-5555, Create,Jane Smith,Corporate Directory,changeit,changeit,,New York CreateOrUpdate,Bill Jones,,,,,California
The CreateOrUpdate command allows you to specify a specific account-type on a resource that supports multiple account-types. So if a user has multiple accounts on a specific resource, with each account being a different account type, the following example shows how to update the admin account type for the userAye user:
command,user,accounts[Sim1|admin].emailAddress CreateOrUpdate,userAye,bbye8@example.com
Note –
Although the CreateOrUpdate command allows you to set account-specific attributes for a user's accounts, be aware that the following values in the global section of the User's View will be applied to all specified accounts:
-
accountId
-
email
-
password
-
disable
-
All extended attributes
Consequently, a BulkOps command of the following form might not do what you expect.
command,user,accounts[Sim1].email CreateOrUpdate,userAye,bbye8@example.com
If userAye already has a value for email, that value will be applied to the email attribute on the Sim1 resource. You have no way to override this behavior.
Fields with More Than One Value
Some fields can have multiple values. These are known as multivalued fields. For example, the waveset.resources field can be used to assign multiple resources to a user. You can use the vertical bar (|) character (also known as the “pipe” character) to separate multiple values in a field. The syntax for multiple values can be specified as follows:
value0 | value1 [ | value2 ... ]
When updating multivalued fields on existing users, replacing the current field’s values with one or more new values may not be what you want. You may want to remove some values or add to the current values. You can use field directives to specify how to treat the existing field’s values. Field directives go in front of the field value and are surrounded by the vertical bar character, as follows:
|directive [ ; directive ] | field values
You can choose from the following directives:
-
Replace. Replace the current values with the specified values. This is the default if no directive (or just the List directive) is specified.
-
Merge. Add the specified values to the current values. Duplicate values are filtered.
-
Remove. Remove the specified values from the current values.
-
List. Force the field’s value to be handled as if it had multiple values, even if it only has a single value. This directive is not usually needed as most fields are handled appropriately regardless of the number of values. This is the only directive that can be specified with another directive.
Note –
Field values are case-sensitive. This is important when specifying the Merge and Remove directives. The values must match exactly to correctly remove values or avoid having multiple similar values when merging.
Special Characters in Field Values
If you have a field value with a comma (,) or double quote (") character, or you want to preserve leading or trailing spaces, you must embed your field value within a pair of double quotes ("field_value"). You then need to replace double quotes in the field value with two double quote (") characters. For example, "John ""Johnny"" Smith" results in a field value of John "Johnny" Smith.
If you have a field value with a vertical bar (|) or backslash (\) character in it, you must precede it with a backslash (\| or \\).
Bulk Action View Attributes
When the Create, Update, or CreateOrUpdate actions are performed, there are additional attributes in the User View that are only used or available during bulk action processing. These attributes can be referenced in the User Form to allow behavior specific to bulk actions.
The attributes are as follows:
-
The waveset.bulk.fields.field_name attributes contain the values for the fields that were read in from the CSV input, where field_name is the name of the field. For example, the command and user fields are in the attributes with path expressions waveset.bulk.fields.command and waveset.bulk.fields.user, respectively.
-
The waveset.bulk.fieldDirectives.field_name attributes are only defined for those fields for which a directive was specified. The value is the directive string.
-
Set the waveset.bulk.abort Boolean attribute to true to abort the current action.
-
Set the waveset.bulk.abortMessage attribute to a message string to display when waveset.bulk.abort is set to true. If this attribute is not set, a generic abort message is displayed.
Correlation and Confirmation Rules
Use correlation and confirmation rules when you do not have the Identity Manager user name available to put in the user field of your actions. If you do not specify a value for the user field, then you must specify a correlation rule when launching the bulk action. If you do specify a value for the user field, then the correlation and confirmation rules will not be evaluated for that action.
A correlation rule looks for Identity Manager users that match the action fields. A confirmation rule tests an Identity Manager user against the action fields to determine whether the user is a match. This two-stage approach allows Identity Manager to optimize correlation by quickly finding possible users (based on name or attributes), and by performing expensive checks only on the possible users.
Create a correlation or confirmation rule by creating a rule object with a subtype of SUBTYPE_ACCOUNT_CORRELATION_RULE or SUBTYPE_ACCOUNT_CONFIRMATION_RULE, respectively.
For more information about correlation and confirmation rules, see Chapter 4, Data Loading and Synchronization, in Sun Identity Manager Deployment Guide.
Correlation Rules
Input for any correlation rule is a map of the action fields. Output must be one of the following:
-
String (containing user name or ID)
-
List of String elements (each a user name or ID)
-
List of WSAttribute elements
-
List of AttributeCondition elements
A typical correlation rule generates a list of user names based on values of the fields in the action. A correlation rule may also generate a list of attribute conditions (referring to queryable attributes of Type.USER) that will be used to select users.
A correlation rule should be relatively inexpensive but as selective as possible. If possible, defer expensive processing to a confirmation rule.
Attribute conditions must refer to queryable attributes of Type.USER. These are configured in the Identity Manager configuration object named IDM Schema Configuration.
Correlating on an extended attribute requires special configuration:
The extended attribute must be specified as queryable.
 To Set an Extended Attribute as Queryable
To Set an Extended Attribute as Queryable
-
Open IDM Schema Configuration. You must have the IDM Schema Configuration capability to view or edit IDM Schema Configuration.
-
Locate the <IDMObjectClassConfiguration name=’User’> element.
-
Locate the <IDMObjectClassAttributeConfiguration name=’ xyz ’> element, where xyz is the name of the attribute that you want to set as queryable.
-
Set queryable=’true’
In Correlation Rules the email extended attribute is defined as queryable.
Example 3–1 XML Excerpt That Defines the Email Extended Attribute as Queryable
<IDMSchemaConfiguration>
<IDMAttributeConfigurations>
<IDMAttributeConfiguration name=’email’ syntax=’STRING’/>
</IDMAttributeConfiguration>
</IDMAttributeConfigurations>
<IDMObjectClassConfigurations>
<IDMObjectClassConfiguration name=’User’ extends=’Principal’ description=’User description’>
<IDMObjectClassAttributeConfiguration name=’email’ queryable=’true’/>
</IDMObjectClassConfiguration>
</IDMObjectClassConfigurations>
</IDMSchemaConfiguration>
You must restart the Identity Manager application (or the application server) for the IDM Schema Configuration change to take effect.
Confirmation Rules
Inputs to any confirmation rule are as follows:
-
Use userview for a full view of an Identity Manager user.
-
Use account for a Map of action fields.
A confirmation rule returns a string-form Boolean value of true if the user matches the action fields; otherwise, it returns a value of false.
A typical confirmation rule compares internal values from the user view to the values of the action fields. As an optional second stage in correlation processing, the confirmation rule performs checks that cannot be expressed in a correlation rule (or that are too expensive to evaluate in a correlation rule).
In general, you need a confirmation rule only for the following situations:
-
The correlation rule may return more than one matching user.
-
User values that must be compared are not queryable.
A confirmation rule is run once for each matching user returned by the correlation rule.
Managing Account Security and Privileges
This section discusses actions you can take to provide secure access for user accounts and to manage user privileges in Identity Manager.
Setting Password Policies
Resource password policies establish the limitations for passwords. Strong password policies provide added security to help protect resources from unauthorized login attempts. You can edit a password policy to set or select values for a range of characteristics.
To begin working with password policies, click Security on the main menu, and then click Policies.
To edit a password policy, click it in the Policies list. To create a password policy, select String Quality Policy from the New list of options.
Note –
For more information on policies, see Configuring Identity Manager Policies.
Creating a Policy
Password policies are the default type for string quality policies. After naming and providing an optional description for the new policy, select options and parameters for the rules that define it.
Length Rules
Length rules set the minimum and maximum required character length for a password. Select this option to enable the rule, and then enter a limit value for the rule.
Policy Type
Choose one of the policy type buttons . If you choose the Other option, you must enter the type in the text field provided.
Character Type Rules
Character type rules establish the minimum and maximum characters of certain types and number that can be included in a password.
These include:
-
Minimum and maximum alphabetic, numeric, uppercase, lowercase, and special characters
-
Minimum and maximum embedded numeric characters
-
Maximum repetitive and sequential characters
-
Minimum beginning alphabetic and numeric characters
Enter a numeric limit value for each character type rule; or enter All to indicate that all characters must be of that type.
Minimum Number of Character Type Rules
You can also set the minimum number of character type rules that must pass validation, as illustrated in Figure 3–7. The minimum number that must pass is one. The maximum cannot exceed the number of character type rules that you have enabled.
Note –
To set the minimum number that must pass to the highest value, enter All.
Figure 3–7 Password Policy (Character Type) Rules
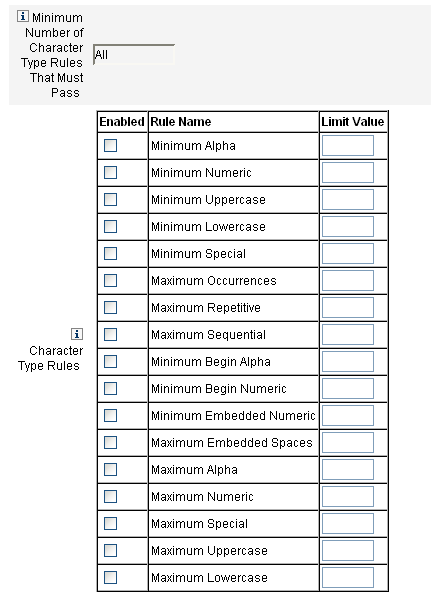
Dictionary Policy Selection
You can choose to check passwords against words in a dictionary to guard against simple dictionary attacks.
Before you can use this option, you must:
-
Configure the dictionary
-
Load dictionary words
You configure the dictionary from the Policies page. For more information about how to set up the dictionary, see What is a Dictionary Policy?.
Password History Policy
You can prohibit re-use of passwords that were used immediately preceding a newly selected password.
In the Number of Previous Passwords that Cannot be Reused field, enter a numeric value greater than one to prohibit re-use of the current and preceding passwords. For example, if you enter a numeric value of 3, the new password cannot be the same as the current password or the two passwords used immediately before it.
You can also prohibit re-use of similar characters from passwords used previously. In the Maximum Number of Similar Characters from Previous Passwords that Cannot be Reused field, enter the number of consecutive characters from the previous password or passwords that cannot be repeated in the new password. For example, if you enter a value of 7, and the previous password was password1, then the new password cannot be password2 or password3.
If you enter a value of 0, then all characters must be different regardless of sequence. For example, if the previous password was abcd, then the new password cannot include the characters a, b, c, or d.
The rule can apply to one or more previous passwords. The number of previous passwords checked is the number specified in the Number of Previous Passwords that Cannot be Reused field.
Must Not Contain Words
You can enter one or more words that the password may not contain. In the entry box, enter one word on each line.
You can also exclude words by configuring and implementing the dictionary policy. For more information, see What is a Dictionary Policy?.
Must Not Contain Attributes
You can enter one or more attributes that the password may not contain.
You can specify the following attributes:
-
accountID
-
email
-
firstname
-
fullname
-
lastname
You can change the allowed set of “must not contain” attributes for passwords in the UserUIConfig configuration object. See Must Not Contain Attributes in Policies for more information.
Implementing Password Policies
Password policies are established for each resource. To put a password policy in place for a specific resource, select it from the Password Policy list of options, which is located in the Policy Configuration area of the Create or Edit Resource Wizard: Identity Manager Parameters pages.
User Authentication
If a user forgets his password or his password is reset, the user can answer one or more account authentication questions to gain access to Identity Manager. You establish these questions, and the rules that govern them, as part of an Identity Manager account policy. Unlike password policies, Identity Manager account policies are assigned to the user directly or through the organization assigned to the user (on the Create and Edit User pages).
 To Set Up Authentication in an Account Policy
To Set Up Authentication in an Account Policy
-
Click Security in the main menu, and then click Policies.
-
Select “Default Identity Manager Account Policy” from the list of policies.
Authentication selections are offered in the Secondary Authentication Policy Options area of the page.
Important! When first set up, the user should log in to the User interface and provide initial answers to his authentication questions. If these answers are not set, the user cannot successfully log in without his password.
The authentication question policy determines what happens when a user clicks on the Forgot Your Password? button on the login page or when accessing the Change My Answers page. User Authentication describes each option.
Option
Description
All
Requires the user to answer all policy-defined and personalized questions.
Any
Identity Manager displays all policy-defined and personalized questions. You must specify how many questions the user must answer.
Next
Requires the user to answer all possible policy-defined questions the first time that user logs in.
If the user clicks the Forgot Your Password? button during login, Identity Manager displays the first question. If the user answers incorrectly, Identity Manager displays the next question, and so on until the user answers an authentication question correctly and logs in, or is locked out based on the specified failure attempts limit. User-generated questions are not supported for this policy.
Random
Allows the administrator to specify how many questions the user must answer. Identity Manager randomly selects and displays the specified number of questions from the list of questions defined in the policy as well as those the user has defined. The user must answer all questions displayed.
Round robin
Identity Manager selects the next question from the list of configured questions and assigns this question to the user. The first user is assigned the first question in the list of authentication questions, and the second user is assigned the second question. This pattern continues until the number of questions is exceeded. At that point, questions are assigned to users in sequential order. For example, if there are 10 questions, the 11th and 21st users are assigned the first question.
The selected question is the only one that is displayed. If you want the user to answer a different question every time, use the Random policy and set the number of questions to 1.
Users cannot define their own authentication questions. See Personalized Authentication Questions for more information about this feature.
You can verify your authentication choices by logging in to the Identity Manager User interface, clicking the Forgot Your Password? button, and answering the presented question or questions.
Figure 3–8 shows an example of the User Account Authentication screen.
Figure 3–8 User Account Authentication

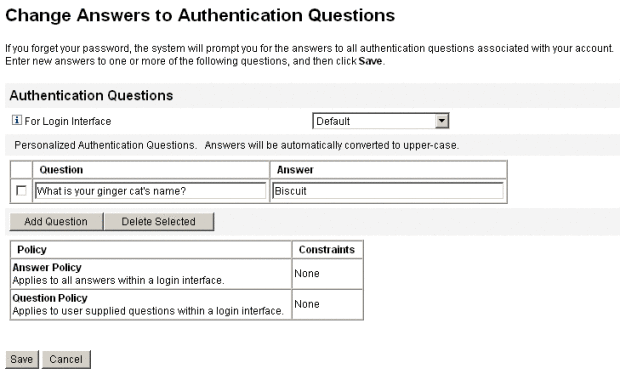
Personalized Authentication Questions
In the Identity Manager account policy, you can select an option to allow users to supply their own authentication questions in the User and Administrator interfaces. You can additionally set the minimum number of questions that the user must provide and answer to be able to log in successfully by using personalized authentication questions.
Users then can add and change questions from the Change Answers to Authentication Questions page. An example of this page is shown in Figure 3–9.
Figure 3–9 Change Answers: Personalized Authentication Questions
Bypassing the Change Password Challenge after Authentication
When a user successfully authenticates by answering one or more questions, by default he is challenged by the system to provide a new password. You can configure Identity Manager to bypass the change password challenge, however, by setting the bypassChangePassword system configuration property for one or more Identity Manager applications.
For instructions on editing the system configuration object, see Editing Identity Manager Configuration Objects.
To bypass the change password challenge for all applications following successful authentication, set the bypassChangePassword property as follows in the system configuration object.
Example 3–2 Setting the Attribute to Bypass the Change Password Challenge
<Attribute name="ui"
<Object>
<Attribute name="web">
<Object>
<Attribute name=’questionLogin’>
<Object>
<Attribute name=’bypassChangePassword’>
<Boolean>true</Boolean>
</Attribute>
</Object>
</Attribute>
...
</Object>
...
To disable this password challenge for a specific application, set it as follows.
Example 3–3 Setting the attribute to Disable the Change Password Challenge
<Attribute name="ui">
<Object>
<Attribute name="web">
<Object>
<Attribute name=’user’>
<Object>
<Attribute name=’questionLogin’>
<Object>
<Attribute name=’bypassChangePassword’>
<Boolean>true</Boolean>
</Attribute>
</Object>
</Attribute>
</Object>
</Attribute>
...
</Object>
...
|
Assigning Administrative Privileges
You can assign Identity Manager administrative privileges, or capabilities, to users as follows:
-
Admin Roles. Users assigned an Admin Role inherit the capabilities and controlled organizations defined by the role. By default, all Identity Manager user accounts are assigned the User Admin Role when created. For detailed information about Admin Roles and creating an Admin Role, see Understanding and Managing Identity Manager Resources in Chapter 5, Roles and Resources.
-
Capabilities. Capabilities are defined by rules. Identity Manager provides sets of capabilities grouped into functional capabilities that you can select from. Assigning capabilities allows for more granularity in assigning administrative privileges. For information about capabilities and creating capabilities, seeUnderstanding and Managing Capabilities in Chapter 6, Administration.
-
Controlled organizations. Controlled organizations grant administrative control privileges over specified organizations. For more information, see Understanding Identity Manager Organizations in Chapter 6, Administration.
For more information about Identity Manager Administrators and administrative duties, see Chapter 6, Administration
User Self-Discovery
The Identity Manager end-user interface allows end-users to discover resource accounts. This means that a user with an Identity Manager identity can associate it with an existing, but unassociated, resource account.
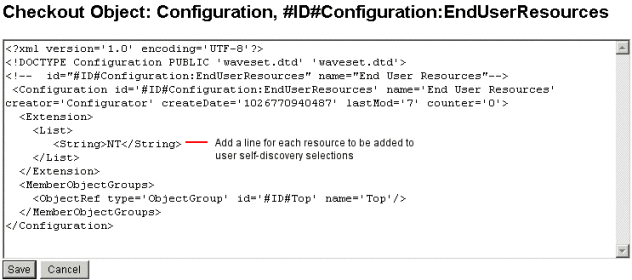
Enabling Self-Discovery
To enable self-discovery, you must edit a special configuration object (End User Resources) and add to it the name of each resource on which the user will be allowed to discover accounts.
 To Enable Self-Discovery
To Enable Self-Discovery
-
Edit the “End User Resources” configuration object.
For instructions on editing Identity Manager configuration objects, see Editing Identity Manager Configuration Objects.
-
Add <String>Resource</String>, where Resource matches the name of a resource object in the repository, as illustrated in Figure 3–10.
Figure 3–10 End User Resources Configuration Object
-
Click Save.
When self-discovery is enabled, the user is presented with a new selection under the Profile menu tab on the Identity Manager User interface (Self Discovery). This area allows the user to select a resource from an available list, and then enter the resource account ID and password to link the account with his Identity Manager identity.
Note –To give end-users access to Identity Manager configuration objects, administrators can also use the “End User” organization. See The End User Organization for details.
Anonymous Enrollment
The anonymous enrollment feature allows a user without an Identity Manager account to obtain one by request.
Enabling Anonymous Enrollment
By default, the anonymous enrollment feature is disabled.
 To Enable the Anonymous Enrollment Feature
To Enable the Anonymous Enrollment Feature
-
In the Administrator interface, click Configure, and then click User Interface.
-
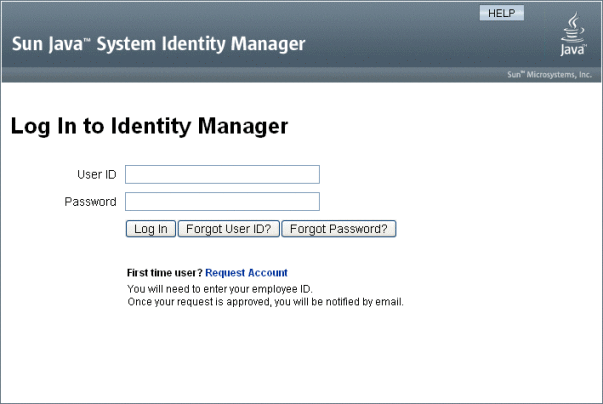
In the Anonymous Enrollment area, select the Enable option, and then click Save.
When a user logs in to the User interface, the login page will display the text First time user? followed by a Request Account link.
Note –The text First time user? Request Account is customizable. See the Sun Identity Manager Deployment Guidefor details.
Figure 3–11 The User Interface Page With the “Request Account” Link Enabled
Configuring Anonymous Enrollment
From the Anonymous Enrollment area on the User Interface page, you can configure the following options for the anonymous enrollment process:
-
Notification Template. Specify the ID of an email template to use to send notifications to the user requesting an account.
-
Require Privacy Policy. If selected, then the user must accept the privacy policy before he can request an account. This is enabled by default.
-
Enable Validation. If selected, then the user must validate his employment before he can request an account. This is enabled by default.
-
Process Launch URL. Enter a URL to specify which workflow will be used for the anonymous enrollment process.
-
Enable Notifications. If selected, then a notification email will be sent to the user when his account has been created.
-
Email Domain. Enter the name of the email domain to use to construct the user’s email address.
Click Save when finished.
User Enrollment Process
When a user logs on to the User interface, that user can request an account by clicking Request Account on the login page.
Identity Manager displays the first of two registration pages, which requests a first name, last name, and employee ID. If the Enable Validation attribute is set to yes (the default), then this information must be validated before the user can proceed to the next page.
The verifyFirstname, verifyLastname, verifyEmployeeId, and verifyEligibility rules in EndUserLibrary validate the information for each attribute.
Note –
You may need to modify one or more of these rules. In particular, you should modify the rule that verifies the employee ID to use a Web services call or Java class to verify the information.
If the Enable Validation attribute is disabled, then the initial registration page does not display. In this case, you must modify the End User Anonymous Enrollment Completion form to allow the user to enter information normally captured by the initial validation form.
From the information provided on the Registration page, Identity Manager generates:
-
An account ID (following the convention of first initial, last initial, employee ID).
-
An email address in the form:
FirstName.LastName@EmailDomain
Where EmailDomain is the domain set by the Email Domain attribute in anonymous enrollment configuration.
-
The manager attribute (idmManager). You can set this attribute by modifying the EndUserRuleLibrary:getIdmManager rule. By default, the manager is set to Configurator. The administrator designated as the manager must approve the user request before his account is provisioned.
-
The organization attribute. You can set this attribute by customizing the EndUserRuleLibrary:getOrganization rule. By default, users are assigned to the top of the organizational hierarchy (“Top”).
If the information provided by the user on the Registration page validates correctly, then Identity Manager presents the user with the second Registration page. Here the user must enter a password and password confirmation. If the Require Privacy Policy attribute is set to yes, then the user must also select an option to accept the terms of the privacy policy.
When the user clicks Register, Identity Manager presents a confirmation page. If the Enable Notifications attribute is set to yes, then the page indicates the user will receive email notification when he account has been created.
The account is created after the standard Create User process (including approvals required by the idmManager attribute and policy settings) is complete.
- © 2010, Oracle Corporation and/or its affiliates




