| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Solaris Administration: Network Interfaces and Network Virtualization Oracle Solaris 11 Express 11/10 |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Solaris Administration: Network Interfaces and Network Virtualization Oracle Solaris 11 Express 11/10 |
2. NWAM Configuration and Administration (Overview)
3. NWAM Profile Configuration (Tasks)
4. NWAM Profile Administration (Tasks)
5. About the NWAM Graphical User Interface
Part II Administering Single Interfaces
6. Overview of the Networking Stack
7. Datalink Configuration and Administration
8. Configuring an IP Interface
9. Configuring Wireless Interface Communications on Oracle Solaris
Part III Administering Interface Groups
11. Administering Link Aggregations
Administering Virtual Local Area Networks
Consolidating the Network by Using VLANs
VLAN Administration (Task Map)
Planning for VLANs on a Network
How to Plan a VLAN Configuration
How to Configure VLANs Over a Link Aggregation
Performing Other Administrative Tasks on VLANs
How to Display VLAN Information
Combining Network Configuration Tasks While Using Customized Names
Part IV Network Virtualization and Resource Management
15. Introducing Network Virtualization and Resource Control (Overview)
16. Planning for Network Virtualization and Resource Control
17. Configuring Virtual Networks (Tasks)
18. Using Link Protection in Virtualized Environments
19. Managing Network Resources
A virtual local area network (VLAN) is a subdivision of a local area network at the datalink layer of the TCP/IP protocol stack. You can create VLANs for local area networks that use switch technology. By assigning groups of users to VLANs, you can improve network administration and security for the entire local network. You can also assign interfaces on the same system to different VLANs.
Consider dividing your local network into VLANs if you need to do the following:
Create a logical division of workgroups.
For example, suppose all hosts on a floor of a building are connected on one switched-based local network. You could create a separate VLAN for each workgroup on the floor.
Enforce differing security policies for the workgroups.
For example, the security needs of a Finance department and an Information Technologies department are quite different. If systems for both departments share the same local network, you could create a separate VLAN for each department. Then, you could enforce the appropriate security policy on a per-VLAN basis.
Split workgroups into manageable broadcast domains.
The use of VLANs reduces the size of broadcast domains and improves network efficiency.
Switched LAN technology enables you to organize the systems on a local network into VLANs. Before you can divide a local network into VLANs, you must obtain switches that support VLAN technology. You can configure all ports on a switch to serve a single VLAN or multiple VLANs, depending on the VLAN topology design. Each switch manufacturer has different procedures for configuring the ports of a switch.
The following figure shows a local area network that has the subnet address 192.168.84.0. This LAN is subdivided into three VLANs, Red, Yellow, and Blue.
Figure 12-1 Local Area Network With Three VLANs
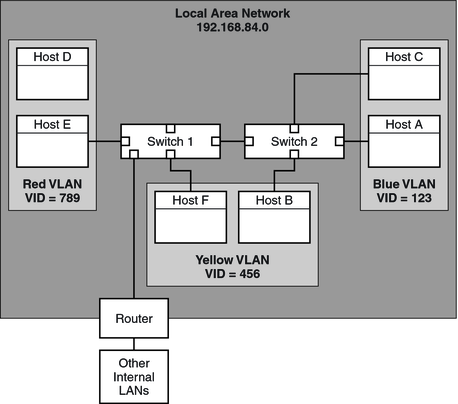
Connectivity on LAN 192.168.84.0 is handled by Switches 1 and 2. The Red VLAN contains systems in the Accounting workgroup. The Human Resources workgroup's systems are on the Yellow VLAN. Systems of the Information Technologies workgroup are assigned to the Blue VLAN.
VLANs on zones allow you to configure multiple virtual networks within a single network unit such as a switch. Consider the following illustration of a system with three physical NICs:
Figure 12-2 System With Multiple VLANs
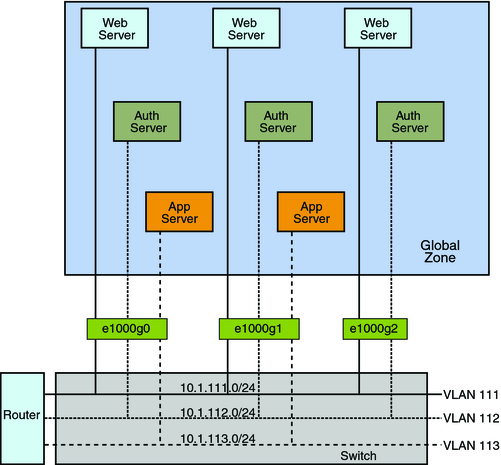
Without VLANs, you would configure different systems to perform specific functions and connect these systems to separate networks. For example, web servers would be connected to one LAN, authentication servers to another, and application servers to a third network. With VLANs and zones, you can collapse all eight systems and configure them as zones in a single system. Then you use VLAN tags, or VLAN IDs (VIDs) to assign a VLAN to each set of zones that performs the same functions. The information provided in the figure can be tabulated as follows:
|
To create the configuration shown in the figure, refer to Example 12-1.
In Oracle Solaris, you can assign meaningful names to VLAN interfaces. VLAN names consist of a link name and the VLAN ID number (VID), such as sales0 You should assign customized names when you create VLANs. For more information about customized names, see Assigning Names to Datalinks. For more information about valid customized names, see Rules for Valid Link Names.
The following table links you to different tasks to administer VLANs.
|
Use the following procedure to plan for VLANs on your network.
For a basic example of such a topology, refer to Figure 12-1.
Note - A VLAN numbering scheme might already exist on the network. If so, you must create VIDs within the existing VLAN numbering scheme.
# dladm show-link
Note the VID of each interface and the switch port where each interface is connected.
Refer to the switch manufacturer's documentation for configuration instructions.
The following procedure shows how to create and configure a VLAN. In Oracle Solaris, all Ethernet devices can support VLANs. However, some restrictions exist with certain devices. For these exceptions, refer to VLANs on Legacy Devices.
Data links must already be configured on your system before you can create VLANs. See How to Configure an IP Interface.
For more information, see How to Obtain Administrative Rights in System Administration Guide: Security Services.
# dladm show-link
# dladm create-vlan -l link -v VID vlan-link
Specifies the link on which the VLAN interface is being created.
Indicates the VLAN ID number
Specifies the name of the VLAN, which can also be an administratively-chosen name.
# dladm show-vlan
# ipadm create-addr -T static -a IP-address addrobj
where interface takes the same name as the VLAN name and addrobj uses the naming convention interface/user-defined-string.
Example 12-1 Configuring a VLAN
This example creates the VLAN configuration that is illustrated in Figure 12-2. This example assumes that you have already configured the different zones in the system. For more information about configuring zones, see Part II, Oracle Solaris Zones, in System Administration Guide: Oracle Solaris Zones, Oracle Solaris 10 Containers, and Resource Management.
global# dladm show-link LINK CLASS MTU STATE BRIDGE OVER e1000g0 phys 1500 up -- -- e1000g1 phys 1500 up -- -- e1000g2 phys 1500 up -- -- global# dladm create-vlan -l e1000g0 -v 111 web1 global# dladm create-vlan -l e1000g0 -v 112 auth1 global# dladm create-vlan -l e1000g0 -v 113 app1 global# dladm create-vlan -l e1000g1 -v 111 web2 global# dladm create-vlan -l e1000g1 -v 112 auth2 global# dladm create-vlan -l e1000g1 -v 113 app2 global# dladm create-vlan -l e1000g2 -v 111 web3 global# dladm create-vlan -l e1000g2 -v 112 auth3 global# dladm show-vlan LINK VID OVER FLAGS web1 111 e1000g0 ---- auth1 112 e1000g0 ---- app1 113 e1000g0 ---- web2 111 e1000g1 ---- auth2 112 e1000g1 ---- app2 113 e1000g1 ---- web3 111 e1000g2 ---- auth3 113 e1000g2 ----
When link information is displayed, the VLANs are included in the list.
global# dladm show-link LINK CLASS MTU STATE BRIDGE OVER e1000g0 phys 1500 up -- -- e1000g1 phys 1500 up -- -- e1000g2 phys 1500 up -- -- web1 vlan 1500 up -- e1000g0 auth1 vlan 1500 up -- e1000g0 app1 vlan 1500 up -- e1000g0 web2 vlan 1500 up -- e1000g1 auth2 vlan 1500 up -- e1000g1 app2 vlan 1500 up -- e1000g1 web3 vlan 1500 up -- e1000g2 auth3 vlan 1500 up -- e1000g2
You assign the VLANs to their respective zones. For example, when you check for network information about individual zones, data similar to the following would be displayed for each zone:
global# zonecfg -z webzone1 info net
net:
address not specified
physical: web1
global# zonecfg -z authzone1 info net
net:
address not specified
physical: auth1
global# zonecfg -z appzone2 info net
net:
address not specified
physical: app2
The value of the property physical indicates the VLAN that is set for the given zone.
You log in to each non-global zone to configure the VLAN with an IP address.
In webzone1:
webzone1# ipadm create-addr -T static -a 10.1.111.0/24 web1/v4
In webzone2:
webzone2# ipadm create-addr -T static -a 10.1.111.0/24 web2/v4
In webzone3:
webzone3# ipadm create-addr -T static -a 10.1.111.0/24 web3/v4
In authzone1:
authzone1# ipadm create-addr -T static -a 10.1.112.0/24 auth1/v4
In authzone2:
autzone2# ipadm create-addr -T static -a 10.1.112.0/24 auth2/v4
In authzone3:
authzone3# ipadm create-addr -T static -a 10.1.112.0/24 auth3/v4
In appzone1:
appzone1# ipadm create-addr -T static -a 10.1.113.0/24 app1/v4
In appzone2:
appzone2# ipadm create-addr -T static -a 10.1.113.0/24 app2/v4
In the same manner as configuring VLANs over an interface, you can also create VLANs on a link aggregation. Link aggregations are described in Chapter 11, Administering Link Aggregations. This section combines configuring VLANs and link aggregations.
Create the link aggregation first and configure it with a valid IP address. To create link aggregations, refer to How to Create a Link Aggregation.
# dladm show-link
# dladm create-vlan -l link -v VID vlan-link
where
Specifies the link on which the VLAN interface is being created. In this specific case, the link refers to the link aggregation.
Indicates the VLAN ID number
Specifies the name of the VLAN, which can also be an administratively-chosen name.
# ipadm create-addr -T static -a IP-address addrobj
where addrobj must follow the naming convention vlan-int/user-defined-string
Example 12-2 Configuring Multiple VLANs Over a Link Aggregation
In this example, two VLANs are configured on a link aggregation. The VLANs are assigned VIDs 193 and 194, respectively.
# dladm show-link LINK CLASS MTU STATE BRIDGE OVER subvideo0 phys 1500 up -- ---- subvideo1 phys 1500 up -- ---- video0 aggr 1500 up -- subvideo0, subvideo1 # dladm create-vlan -l video0 -v 193 salesregion1 # dladm create-vlan -l video0 -v 194 salesregion2 # ipadm create-addr -T static -a 192.168.10.5/24 salesregion1/v4static # ipadm create-addr -T static -a 192.168.10.25/24 saelsregion2/v4static
Certain legacy devices handle only packets whose maximum frame size is 1514 bytes. Packets whose frame sizes exceed the maximum limit are dropped. For such cases, follow the same procedure listed in How to Configure a VLAN. However, when creating the VLAN, use the -f option to force the creation of the VLAN.
The general steps to perform are as follows:
Create the VLAN with the -f option.
# dladm create-vlan -f -l link -v VID [vlan-link]
Set a lower size for the maximum transmission unit (MTU), such as 1496 bytes.
# dladm set-linkprop -p default_mtu=1496 vlan-link
The lower MTU value allows space for the link layer to insert the VLAN header prior to transmission.
Perform the same step to set the same lower value for the MTU size of each node in the VLAN.
For more information about changing link property values, refer to Configuration of Datalinks (Tasks).
This section describes the usage of new dladm subcommands for other VLAN tasks. These dladm commands also work with link names.
For more information, see How to Obtain Administrative Rights in System Administration Guide: Security Services.
# dladm show-vlan [vlan-link]
If you do not specify a VLAN link, the command displays information about all configured VLANs.
Example 12-3 Displaying VLAN Information
The following example is based on the system with multiple VLANs illustrated by Figure 12-2 and shows the available VLANs in the system.
# dladm show-vlan LINK VID OVER FLAGS web1 111 e1000g0 ---- auth1 112 e1000g0 ---- app1 113 e1000g0 ---- web2 111 e1000g1 ---- auth2 112 e1000g1 ---- app2 113 e1000g1 ---- web3 111 e1000g2 ---- auth3 113 e1000g2 ----
Configured VLANs also appear when you issue the dladm show-link command. In the command output, the VLANs are appropriately identified in the CLASS column.
# dladm show-link LINK CLASS MTU STATE BRIDGE OVER e1000g0 phys 1500 up -- -- e1000g1 phys 1500 up -- -- e1000g2 phys 1500 up -- -- web1 vlan 1500 up -- e1000g0 auth1 vlan 1500 up -- e1000g0 app1 vlan 1500 up -- e1000g0 web2 vlan 1500 up -- e1000g1 auth2 vlan 1500 up -- e1000g1 app2 vlan 1500 up -- e1000g1 web3 vlan 1500 up -- e1000g2 auth3 vlan 1500 up -- e1000g2
For more information, see How to Obtain Administrative Rights in System Administration Guide: Security Services.
# dladm show-vlan
# ipadm delete-if vlan-interface
where vlan-interface is the IP interface that is configured over the VLAN.
Note - You cannot remove a VLAN that is currently in use.
To delete the VLAN temporarily, use the -t option as follows:
# dladm delete-vlan -t vlan
To make the deletion persist, perform the following:
Remove the VLAN.
# dladm delete-vlan vlan
Example 12-4 Removing a VLAN
# dladm show-vlan LINK VID OVER FLAGS web1 111 e1000g0 ---- auth1 112 e1000g0 ---- app1 113 e1000g0 ---- web2 111 e1000g1 ---- auth2 112 e1000g1 ---- app2 113 e1000g1 ---- web3 111 e1000g2 ---- auth3 113 e1000g2 ---- # ipadm delete-if web1 # dladm delete-vlan web1
This section provides an example that combines all the procedures in the previous chapters about configuring links, link aggregations, and VLANs while using customized names. For a description of other networking scenarios that use customized names, see the article in http://www.sun.com/bigadmin/sundocs/articles/vnamingsol.jsp.
Example 12-5 Configuring Links, VLANs, and Link Aggregations
In this example, a system that uses 4 NICs needs to be configured to be a router for 8 separate subnets. To attain this objective, 8 links will be configured, one for each subnet. First, a link aggregation is created on all 4 NICs. This untagged link becomes the default untagged subnet for the network to which the default route points.
Then VLAN interfaces are configured over the link aggregation for the other subnets. The subnets are named by basing on a color-coded scheme. Accordingly, the VLAN names are likewise named to correspond to their respective subnets. The final configuration consists of 8 links for the eight subnets: 1 untagged link, and 7 tagged VLAN links.
To make the configurations persist across reboots, the same procedures apply as in previous Oracle Solaris releases. For example, IP addresses need to be added to configuration files like /etc/inet/ndpd.conf or /etc/hostname.interface. Or, filter rules for the interfaces need to be included in a rules file. These final steps are not included in the example. For these steps, refer to the appropriate chapters in System Administration Guide: IP Services, particularly TCP/IP Administration and DHCP.
# dladm show-link LINK CLASS MTU STATE BRIDGE OVER nge0 phys 1500 up -- -- nge1 phys 1500 up -- -- e1000g0 phys 1500 up -- -- e1000g1 phys 1500 up -- -- # dladm show-phys LINK MEDIA STATE SPEED DUPLEX DEVICE nge0 Ethernet up 1000Mb full nge0 nge1 Ethernet up 1000Mb full nge1 e1000g0 Ethernet up 1000Mb full e1000g0 e1000g1 Ethernet up 1000Mb full e1000g1 # ipadm delete-if nge0 # ipadm delete-if nge1 # ipadm delete-if e1000g0 # ipadm delete-if e1000g1 # dladm rename-link nge0 net0 # dladm rename-link nge1 net1 # dladm rename-link e1000g0 net2 # dladm rename-link e1000g1 net3 # dladm show-link LINK CLASS MTU STATE BRIDGE OVER net0 phys 1500 up -- -- net1 phys 1500 up -- -- net2 phys 1500 up -- -- net3 phys 1500 up -- -- # dladm show-phys LINK MEDIA STATE SPEED DUPLEX DEVICE net0 Ethernet up 1000Mb full nge0 net1 Ethernet up 1000Mb full nge1 net2 Ethernet up 1000Mb full e1000g0 net3 Ethernet up 1000Mb full e1000g1 # dladm create-aggr -P L2,L3 -l net0 -l net1 -l net2 -l net3 default0 # dladm show-link LINK CLASS MTU STATE BRIDGE OVER net0 phys 1500 up -- -- net1 phys 1500 up -- -- net2 phys 1500 up -- -- net3 phys 1500 up -- -- default0 aggr 1500 up -- net0 net1 net2 net3 # dladm create-vlan -v 2 -l default0 orange0 # dladm create-vlan -v 3 -l default0 green0 # dladm create-vlan -v 4 -l default0 blue0 # dladm create-vlan -v 5 -l default0 white0 # dladm create-vlan -v 6 -l default0 yellow0 # dladm create-vlan -v 7 -l default0 red0 # dladm create-vlan -v 8 -l default0 cyan0 # dladm show-link LINK CLASS MTU STATE BRIDGE OVER net0 phys 1500 up -- -- net1 phys 1500 up -- -- net2 phys 1500 up -- -- net3 phys 1500 up -- -- default0 aggr 1500 up -- net0 net1 net2 net3 orange0 vlan 1500 up -- default0 green0 vlan 1500 up -- default0 blue0 vlan 1500 up -- default0 white0 vlan 1500 up -- default0 yellow0 vlan 1500 up -- default0 red0 vlan 1500 up -- default0 cyan0 vlan 1500 up -- default0 # dladm show-vlan LINK VID OVER FLAGS orange0 2 default0 ----- green0 3 default0 ----- blue0 4 default0 ----- white0 5 default0 ----- yellow0 6 default0 ----- red0 7 default0 ----- cyan0 8 default0 ----- # ipadm create-addr ... orange0/v4 # ipadm create-addr ... green0/v4 # ipadm create-addr ... blue0/v4 # ipadm create-addr ... white0/v4 # ipadm create-addr ... yellow0/v4 # ipadm create-addr ... red0/v4 # ipadm create-addr ... cyan0/v4