2 Deploying the Google Apps Connector
The procedure to deploy the connector is divided across three stages namely preinstallation, installation, and postinstallation.
The following topics provide details on these stages:
Note:
Some of the procedures described in this chapter must be performed on the target system. To perform these procedures, you must use a Google Apps account with administrator privileges.
2.1 Preinstallation
Preinstallation involves copying third-party libraries to the computer hosting Oracle Identity Manager. It also involves registering the connector with Google Apps for accessing user management APIs and creating a target system account for the connector.
The following topics provide details on these preinstallation procedures:
2.1.1 Downloading and Copying Google Apps Third-Party Libraries
Perform the following steps to download and copy Google Apps third-party libraries:
2.1.2 Preinstallation on the Target System
This section provides a high-level summary about the preinstallation tasks to be performed on the target system.
The preinstallation process involves performing the following tasks:
Note:
The detailed instructions for performing each of these preinstallation tasks are available in the Google Cloud Platform Documentation at https://cloud.google.com/docs/
- Create a project and register your client application with the Google Apps Cloud platform in the Google Developers Console.
- Activate the associated API services such as adding custom information, enable billing, and page monitoring services, for your client application. While activating the associated API services ensure that the statuses of the Admin SDK and Group Settings APIs are set to ON.
- Create a service account and enable your client application to access the activated APIs. Additionally, create a Client ID, Public/Private key pair, and password for the earlier created service account. After the service account creation, note down the Client ID, Public/Private key pair and password information. This information is required while adding scopes and also while configuring the IT resource parameters.
- Add scopes and authorize the registered client application.
- Create a user account on the target system. The connector uses this account to connect to the target system during each connector operation. Post account creation, assign the Groups Admin and User Management Admin admin roles to the newly created account.
- Enable access to various Google administrative APIs available in the Google Apps Business Domain. The administrative API allows you to manage user accounts and synchronizes Google Apps user accounts with your own user account
- Enable external user access to groups in Google Apps. Perform this step only if you want external users to access groups in Google Apps.
2.2 Installation
You must install the connector in Oracle Identity Manager. If necessary, you can also deploy the connector in a Connector Server.
Installation information is divided across the following sections:
2.2.1 Understanding Installation of the Google Apps Connector
Depending on where you want to run the connector code (bundle), the connector provides installation options:
The following are the installation options:
-
Run the connector code locally in Oracle Identity Manager.
To run the connector code locally in Oracle Identity Manager, perform the procedure described in Installing the Connector in Oracle Identity Manager.
-
Run the connector code remotely in a Connector Server.
To run the connector code remotely in a Connector Server, perform the procedures described in Installing the Connector in Oracle Identity Manager and Deploying the Connector Bundle in a Connector Server.
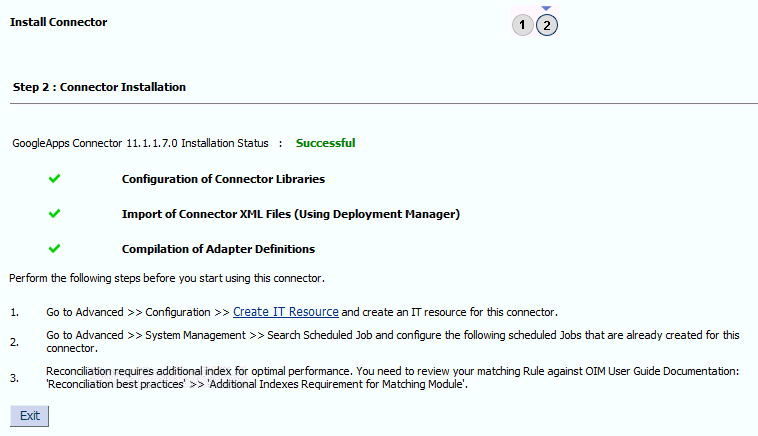
2.2.2 Installing the Connector in Oracle Identity Manager
Perform this procedure to install the Google Apps connector in Oracle Identity Manager.
Note:
In this guide, the term Connector Installer has been used to refer to the Install Connectors feature of the Administrative and User Console.
To run the Connector Installer:
2.2.3 Deploying the Connector Bundle in a Connector Server
You can deploy the Google Apps connector bundle into the Java Connector Server by performing the procedure mentioned here.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about installing and configuring connector server and running the connector server
If you want to deploy the Google Apps connector bundle into the Java Connector Server, then follow these steps:
2.3 Postinstallation
Postinstallation for the connector involves configuring Oracle Identity Manager, enabling logging to track information about all connector events, and configuring SSL. It also involves performing some optional configurations such as enabling request-based provisioning and localizing the user interface.
Postinstallation steps are divided across the following sections:
2.3.1 Configuring Oracle Identity Manager 11.1.2.x or Later
If you are using Oracle Identity Manager release 11.1.2.x or later, you must create additional metadata such as a UI form and an application instance. In addition, you must run entitlement and catalog synchronization jobs.
These procedures are described in the following sections:
2.3.1.1 Creating and Activating a Sandbox
Create and activate a sandbox as follows. For detailed instructions, see Managing Sandboxes in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
2.3.1.2 Creating a New UI Form
Create a new UI form as follows. For detailed instructions, see Managing Forms in Oracle Fusion Middleware Administering Oracle Identity Manager.
- In the left pane, under Configuration, click Form Designer.
- Under Search Results, click Create.
- Select the resource type for which you want to create the form.
- Enter a form name and click Create.
2.3.1.3 Creating an Application Instance
Create an application instance as follows. For detailed instructions, see Managing Application Instances in Oracle Fusion Middleware Administering Oracle Identity Manager.
- In the System Administration page, under Configuration in the left pane, click Application Instances.
- Under Search Results, click Create.
- Enter appropriate values for the fields displayed on the Attributes form and click Save.
- In the Form drop-down list, select the newly created form and click Apply.
- Publish the application instance for a particular organization.
Note:
If you are using access policy-based provisioning, then specify the Active Directory connector application instance as the value for the Parent AppInstance attribute.
2.3.1.4 Publishing a Sandbox
To publish the sandbox that you created in Creating and Activating a Sandbox:
- Close all the open tabs and pages.
- In the upper right corner of the page, click the Sandboxes link. The Manage Sandboxes page is displayed.
- From the table showing the available sandboxes in the Manage Sandboxes page, select the sandbox that you created in Creating and Activating a Sandbox.
- On the toolbar, click Publish Sandbox. A message is displayed asking for confirmation.
- Click Yes to confirm. The sandbox is published and the customizations it contained are merged with the main line.
2.3.1.5 Harvesting Entitlements and Sync Catalog
You can populate Entitlement schema from child process form table, and harvest roles, application instances, and entitlements into catalog. You can also load catalog metadata.
To harvest entitlements and sync catalog:
- Run the scheduled jobs for lookup field synchronization listed in –-----.
- Run the Entitlement List scheduled job to populate Entitlement Assignment schema from child process form table. See Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about this scheduled job.
- Run the Catalog Synchronization Job scheduled job. See for more information about this scheduled job. See Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about this scheduled job.
2.3.1.6 Updating an Existing Application Instance with a New Form
For any changes you do in the Form Designer, you must create a new UI form and update the changes in an application instance.
To update an existing application instance with a new form:
- Create a sandbox and activate it as described in Creating and Activating a Sandbox.
- Create a new UI form for the resource as described in Creating a New UI Form.
- Open the existing application instance.
- In the Form field, select the new UI form that you created.
- Save the application instance.
- Publish the sandbox as described in Publishing a Sandbox.
2.3.2 Enabling Request-Based Provisioning
In request-based provisioning, an end user creates a request for a resource or entitlement by using the Administrative and User Console.
Note:
Perform the procedure described in this section only if you are using Oracle Identity Manager release 11.1.1.x.
In request-based provisioning, an end user creates a request for a resource or entitlement by using the Administrative and User Console. Administrators or other users cannot create requests for a particular user. Requests can be viewed and approved by approvers designated in Oracle Identity Manager.
Note:
The direct provisioning feature of the connector is automatically disabled when you enable request-based provisioning. Therefore, do not enable request-based provisioning if you want to use the direct provisioning.
To enable request-based provisioning, perform the following procedures:
2.3.2.1 Importing Request Datasets
There are two ways of importing request datasets:
Note:
Request Datasets imported either into MDS or by using Deployment Manager are same.
2.3.2.1.1 Importing Request Datasets Using MDS Import Utility
To import a request dataset definition into the MDS:
2.3.2.1.2 Importing Request Datasets Using Deployment Manager
The request datasets (predefined or generated) can also be imported using Deployment Manager (DM), which are stored in xml/GoogleApps-Datasets.xml.
To import a request dataset definition using Deployment Manager:
- Log in to Oracle Identity Manager Administrative and User Console.
- Go to Advanced Administration.
- Click Import Deployment Manager File.
- Navigate to GoogleApps-Datasets.xml file and click Add to add it for import. The datasets available for import will be displayed.
- Click Import. A message with the successful import of the datasets is displayed.
2.3.2.2 Enabling the Auto Save Form Feature
To enable the Auto Save Form feature:
- Log in to the Design Console.
- Expand Process Management, and then double-click Process Definition.
- Search for and open the GoogleApps User process definition.
- Select the Auto Save Form check box.
- Click Save.
2.3.2.3 Running the PurgeCache Utility
Run the PurgeCache utility to clear content belonging to the Metadata category from the server cache. See Clearing Content Related to Connector Resource Bundles from the Server Cache for instructions.
The procedure to enable request-based provisioning ends with this step.
2.3.3 Changing to the Required Input Locale
Changing to the required input locale (language and country setting) involves installing the required fonts and setting the required input locale.
You may require the assistance of the system administrator to change to the required input locale.
2.3.4 Clearing Content Related to Connector Resource Bundles from the Server Cache
When you deploy the connector, the resource bundles are copied from the resources directory on the installation media into the Oracle Identity Manager database.
Whenever you add a new resource bundle to the connectorResources directory or make a change in an existing resource bundle, you must clear content related to connector resource bundles from the server cache.
To clear content related to connector resource bundles from the server cache:
2.3.5 Managing Logging
Oracle Identity Governance uses Oracle Java Diagnostic Logging (OJDL) for recording all types of events pertaining to the connector. OJDL is based on java.util.logger.
The following topics provide detailed information about logging:
2.3.5.1 Understanding Log Levels
Note:
In an Oracle Identity Manager cluster, perform this procedure on each node of the cluster. Then, restart each node.
When you enable logging, Oracle Identity Manager automatically stores in a log file information about events that occur during the course of provisioning and reconciliation operations.
To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Manager to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These message types are mapped to ODL message type and level combinations as shown in Table 2-1.
Table 2-1 Log Levels and ODL Message Type:Level Combinations
| Java Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SEVER are the domain name and server name specified during the installation of Oracle Identity Manager.
2.3.6 Configuring the IT Resource for the Target System
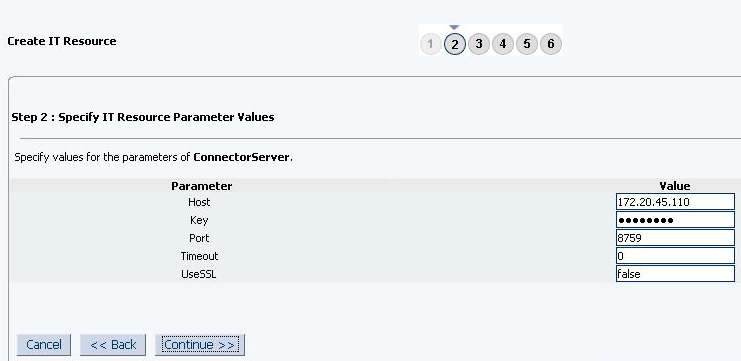
The GoogleApps IT resource is automatically created when you run the Connector Installer. You must specify values for the parameters of the IT resource.
The following section describes the parameters of the IT resource:
To specify values for the parameters of the IT resource:
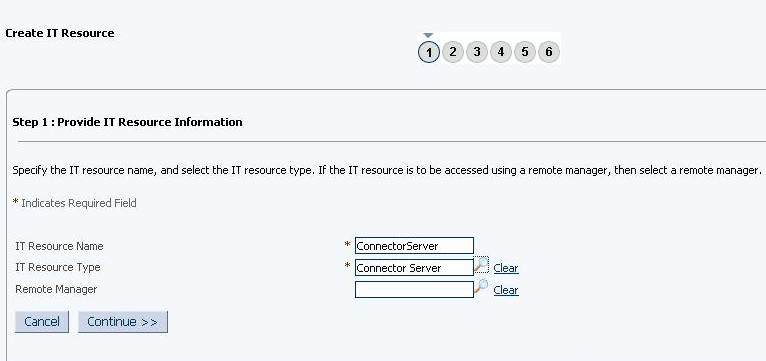
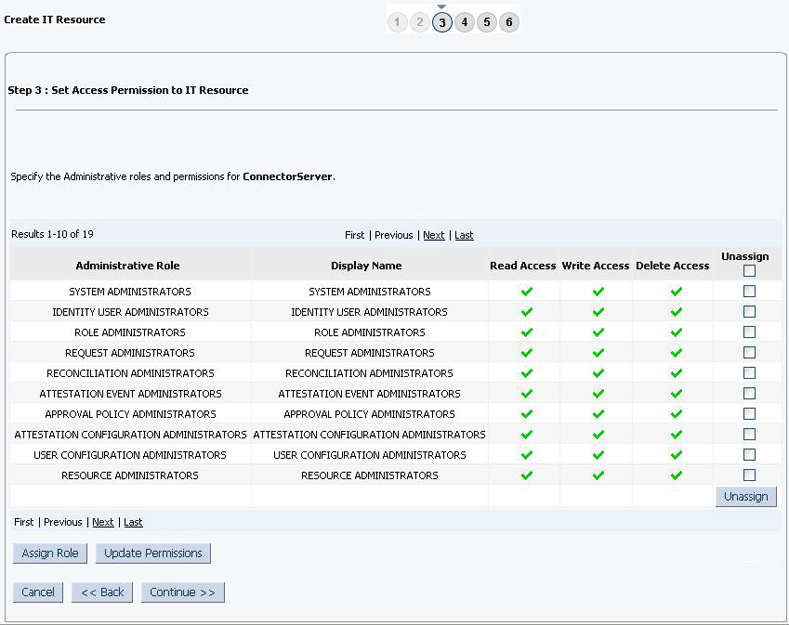
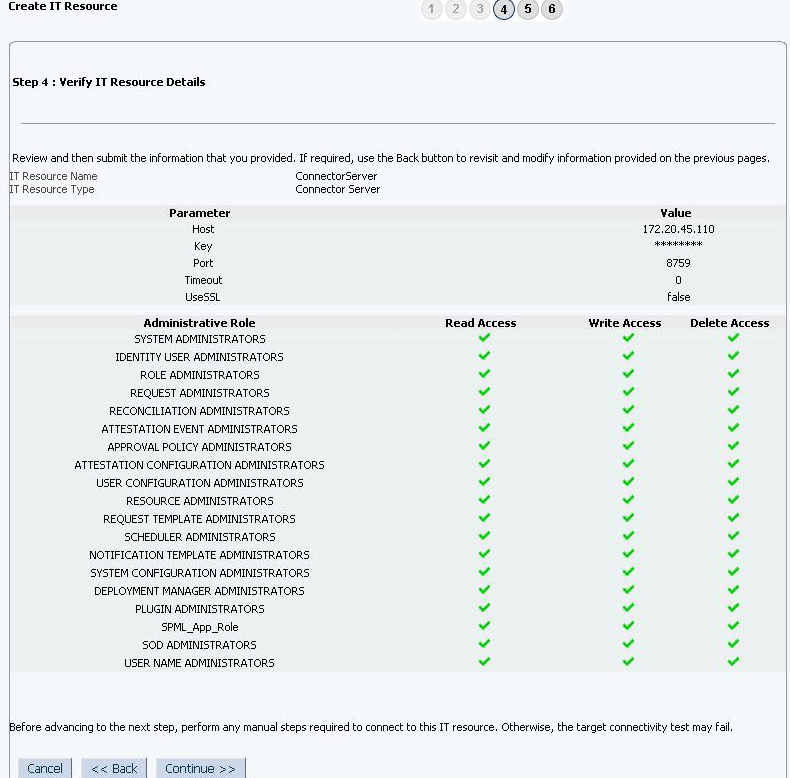
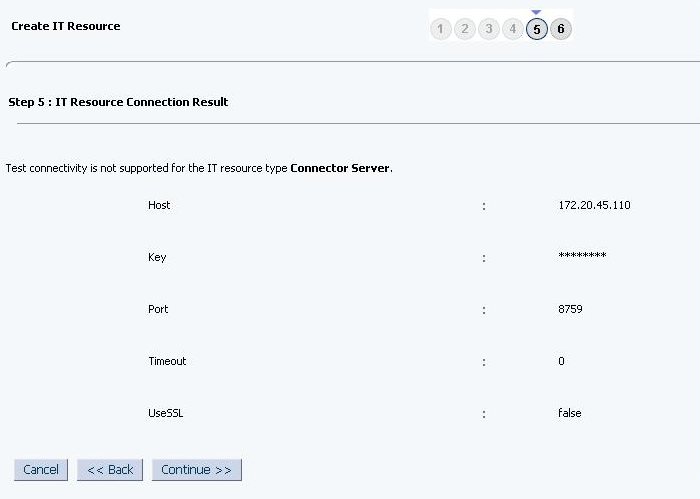
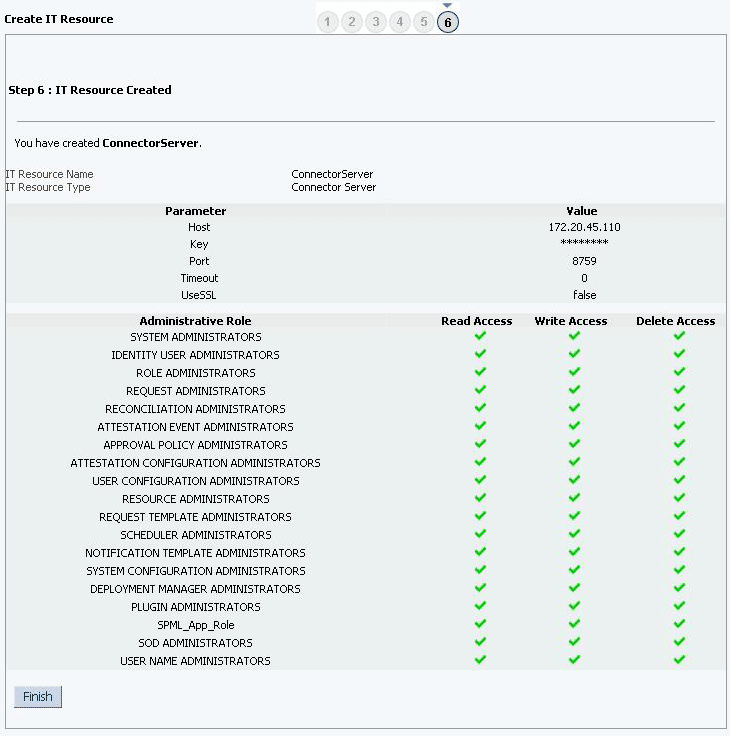
2.3.7 Creating the IT Resource for the Connector Server
Perform the procedure described in this section only if you have deployed the connector bundle remotely in a Connector Server.
Note:
Before you deploy the connector bundle remotely in a Connector Server, you must deploy the connector in Oracle Identity Manager by performing the procedures described in Installation.
To create the IT resource for the Connector Server:
2.3.8 Localizing Field Labels in UI Forms
You can localize UI form field labels by using the resource bundle corresponding to the language you want to use. The resource bundles are available in the connector installation media.
Note:
Perform the procedure described in this section only if you are using Oracle Identity Manager release 11.1.2.x or later and you want to localize UI form field labels.
2.4 Upgrading the Connector
If you have already deployed the Google Apps Connector versions 11.1.1.5.0 or 11.1.1.6.0, then you can upgrade the connector to version 11.1.1.7.0. The following sections discuss the procedure to upgrade the connector:
The following sections discuss the procedure to upgrade the connector:
Note:
Before you perform the upgrade procedure:
- It is strongly recommended that you create a backup of the Oracle Identity Manager database and the connector JARs before you perform an upgrade operation. Refer to the database documentation for information about creating a backup.
- Upgrade the Google Apps connector.
- As a best practice, first perform the upgrade procedure in a test environment.
2.4.1 Preupgrade Steps
Preupgrade steps for the connector involves performing a reconciliation run to fetch records from the target system, defining the source connector in Oracle Identity Manager, creating copies of the connector if you want to configure it for multiple installations of the target system, and disabling all the scheduled jobs.
Perform the following preupgrade steps:
- Perform a reconciliation run to fetch all latest updates to Oracle Identity Manager.
- Perform the preupgrade procedure documented in Managing Connector Lifecycle in Oracle Fusion Middleware Administering Oracle Identity Manager.
- Define the source connector (an earlier release of the connector that must be upgraded) in Oracle Identity Manager. You define the source connector to update the Deployment Manager XML file with all customization changes made to the connector. See Managing Connector Lifecycle in Oracle Fusion Middleware Administering Oracle Identity Manager for more information.
2.4.2 Upgrade Steps
This is a summary of the procedure to upgrade the connector for both staging and production environments.
-
Staging Environment
Perform the upgrade procedure by using the wizard mode.
Note:
Do not upgrade IT resource type definition. In order to retain the default setting, you must map the IT resource definition to "None".
-
Production Environment
Perform the upgrade procedure by using the silent mode.
See Managing Connector Lifecycle in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed information about the wizard and silent modes.
2.4.3 Postupgrade Steps
Postupgrade steps involve uploading new connector jars, running the Form Version Control (FVC) utility to manage data changes on a form, running the PostUpgradeScript.sql script to upgrade the IT resource, configuring the upgraded IT resource of the source connector, and so on.
Perform the following procedure: