2 Deploying the Connector
Deploying the connector involves the following steps:
Note:
In this guide, PeopleSoft HRMS is referred to as the target system.
2.1 Preinstallation
Preinstallation information is divided across the following sections:
2.1.1 Preinstallation on Oracle Identity Manager
This section contains the following topic:
2.1.1.1 Files and Directories on the Installation Media
Table 2-1 lists the files and directories on the installation media.
Table 2-1 Files and Directories on the Installation Media
| File in the Installation Media Directory | Description |
|---|---|
|
configuration/PSFT_Employee_Reconciliation-CI.xml |
This XML file contains configuration information that is used during connector installation. |
|
JavaDoc |
This directory contains information about the Java APIs used by the connector. |
|
lib/PSFT_ER-oim-integration.jar |
This JAR file contains the class files that are specific to integration of the connector with PeopleSoft target systems. During connector deployment, this file is copied to the Oracle Identity Manager database. |
|
lib/PSFTCommon.jar |
This JAR file contains PeopleSoft-specific files common to both Employee Reconciliation and User Management versions of the connector. During connector deployment, this file is copied to the Oracle Identity Manager database. |
|
The following files and directories in the listener directory: base directory lib/deploytool.jar build.xml deploy.properties README.txt |
The base directory contains the class files for the PeopleSoftOIMListener.ear file. This Enterprise Archive (EAR) file contains one or more entries representing the modules of the Web application to be deployed onto an application server. During connector deployment, the PeopleSoft listener is deployed as an EAR file. The deploytool.jar file contains the class files required for deploying the listeners. The build.xml file is the deployment script, which contains configurations to deploy the listener. The deploy.properties file contains Oracle Identity Manager connection details. The README.txt file contains instructions to deploy, remove, and redeploy the listener. |
|
The following project files in the peoplecode directory: OIM_ER OIM_ER_DELETE |
Each project file contains two files with .ini and .xml extension that has the same name as the project. They are listed as follows:
|
|
Files in the resources directory |
Each of these resource bundles contains language-specific information that is used by the connector. During connector deployment, this file is copied to the Oracle Identity Manager database. Note: A resource bundle is a file containing localized versions of the text strings that include GUI element labels and messages. |
|
test/config/reconConfig.properties test/config/log.properties |
These files are used by the InvokeListener.bat file. The reconConfig.properties file contains configuration information for running the InvokeListener.bat file. The log.properties file contains logger information. |
|
test/lib/PSFTTest.jar |
This JAR file is used by the testing utility for reconciliation. |
|
test/scripts/InvokeListener.bat test/scripts/InvokeListener.sh |
This BAT file and the UNIX shell script call the testing utility for reconciliation. |
|
xml/PeoplesoftHRMS-ConnectorConfig.xml |
This XML file contains definitions for the connector components.
|
2.1.2 Preinstallation on the Target System
Permission lists, roles, and user profiles are building blocks of PeopleSoft security. Each user of the system has an individual User Profile, which in turn is linked to one or more Roles. To each Role, you can add one or more Permission Lists, which defines what a user can access. So, a user inherits permissions through the role that is attached to a User Profile.
You must create limited rights users who have restricted rights to access resources in the production environment to perform PeopleSoft-specific installation or maintenance operations.
The preinstallation steps consist of creating a user account with limited rights. Permission lists may contain any number of accesses, such as the Web libraries permission, Web services permissions, page permissions, and so on. You attach this permission list to a role, which in turn is linked to a user profile.
This section describes the following procedures, which have to be performed on the target system to create a user account with limited rights:
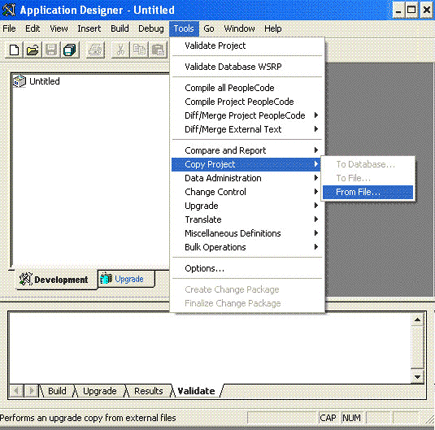
2.1.2.1 Importing a Project from Application Designer
A PeopleSoft Application Designer project is an efficient way to configure your application.
You can import the OIM_ER project created in Application Designer to automate the steps for creating a permission list. You can also create a permission list by manually performing the steps described in Creating a Permission List If you import the project, OIM_ER then you need not perform the steps mentioned in this section.
Note:
If you install, uninstall, or upgrade the same project repeatedly the earlier project definition will be overwritten in the database.
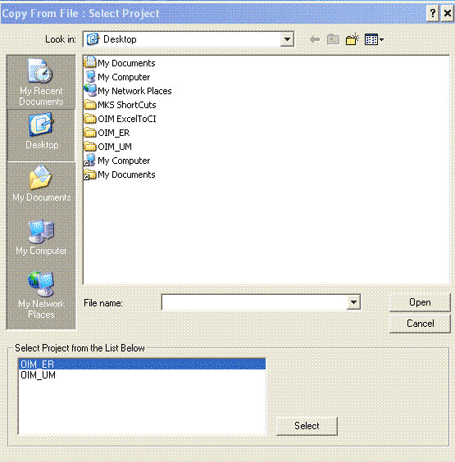
To import a project from Application Designer:
Note:
You can access the project files from the following directories:
OIM_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/peoplecode/OIM_ER
OIM_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/peoplecode/OIM_ER_DELETE
Copy these files to a directory on your computer from where you can access Application Designer.
Note:
You can remove the PeopleSoft project file and all its objects from the target system. To do so, repeat the steps described in the preceding procedure. When you reach Step 4, select OIM_ER_DELETE from the Select Project from the List Below region.
2.1.2.2 Creating a Target System User Account for Connector Operations
You must create a target system account with privileges required for connector operations. The user account created on the target system has the permission to perform all the configurations required for connector operations. This includes configuring the PeopleSoft Integration Broker for full reconciliation and incremental reconciliation. This account cannot access pages or components that are not required by the connector.
The following sections describe the procedures to create this target system account:
Note:
For creating the target system account, you must log into PeopleSoft Internet Architecture with administrator credentials.
2.1.2.2.1 Creating a Permission List
To create a permission list:
Note:
You can skip this section if you have imported a project from Application Designer. See Importing a Project from Application Designer for more information.
-
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=loginFor example:
http://172.21.109.69:9080/psp/ps/?cmd=login
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Security, Permissions & Roles, and then click Permission Lists.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Security, Permissions & Roles, and then click Permission Lists.
-
-
Click Add a new Value. On the Add a New Value tab, enter the permission list name, for example,
OIMER,and then click Add. -
On the General tab, enter a description for the permission list in the Description field.
-
On the Pages tab, click the search icon for Menu Name and perform the following:
-
Click the plus sign (+) to add a row for Menu Name. Click the search icon for Menu Name. In the Menu Name lookup, enter
IB_PROFILEand then click Lookup. From the list, select IB_PROFILE. The application returns to the Pages tab. Click Edit Components. -
On the Component Permissions page, click Edit Pages for each of the following component names:
IB_GATEWAY
IB_MESSAGE_BUILDER
IB_MONITOR_QUEUES
IB_NODE
IB_OPERATION
IB_QUEUEDEFN
IB_ROUTINGDEFN
IB_SERVICE
IB_SERVICEDEFN
IB_MONITOR
-
Click Select All, and then click OK for each of the components. Click OK on the Components Permissions page.
-
On the Pages tab, click the plus sign (+) to add another row for Menu Name.
-
In the Menu Name lookup, enter
PROCESSMONITORand then click Lookup. From the list, select PROCESSMONITOR. The application returns to the Pages tab. Click Edit Components. -
On the Component Permissions page, click Edit Pages for the PROCESSMONITOR component name.
-
Click Select All, and then click OK. Click OK on the Components Permissions page.
-
On the Pages tab, click the plus sign (+) to add another row for Menu Name.
-
In the Menu Name lookup, enter
PROCESS_SCHEDULERand then click Lookup. From the list, select PROCESS_SCHEDULER. The application returns to the Pages tab. Click Edit Components. -
On the Component Permissions page, click Edit Pages for the PRCSDEFN component name.
-
Click Select All, and then click OK. Click OK on the Components Permissions page.
-
On the Pages tab, click the plus sign (+) to add another row for Menu Name.
-
In the Menu Name lookup, enter
MANAGE_INTEGRATION_RULESand then click Lookup. From the list, select MANAGE_INTEGRATION_RULES. The application returns to the Pages tab. Click Edit Components. -
On the Component Permissions page, click Edit Pages for the EO_EFFDTPUB component name.
-
Click Select All, and then click OK. Click OK on the Components Permissions page. The application returns to the Pages tab.
-
-
On the People Tools tab, select the Application Designer Access check box and click the Definition Permissions link. The Definition Permissions page is displayed.
-
On this page, grant full access to the following object types by selecting Full Access from the Access list:
-
App Engine Program
-
Message
-
Component
-
Project
-
Application Package
-
-
Click OK.
-
Click the Tools Permissions link. The Tools Permissions page is displayed. On this page, grant full access to the SQL Editor tool by selecting Full Access from the Access list.
-
Click OK. The application returns to the People Tools tab.
-
On the Process tab, click the Process Group Permissions link. The Process Group Permission page is displayed.
-
In the Process Group lookup, click the search icon. From the list, select TLSALL.
-
On the Process Group Permission page, click the plus sign (+) to add another row for Process Group.
-
In the Process Group lookup, click the search icon. From the list, select STALL. The application returns to the Process Group Permission page.
-
Click OK.
-
On the Web Libraries tab, click the search icon for the Web Library Name field and perform the following:
-
In the Web Library Name lookup, enter
WEBLIB_PORTALand then click Lookup. From the list, select WEBLIB_PORTAL. The application returns to the Web Libraries tab. Click the Edit link. -
On the WebLib Permissions page, click Full Access(All).
-
Click OK and then click Save.
-
Click the plus sign (+) to add a row for the Web Library Name field and repeat Steps a through c for the WEBLIB_PT_NAV library.
-
Click Save to save all the settings specified for the permission list.
-
2.1.2.2.2 Creating a Role for a Limited Rights User
To create a role for a limited rights user:
-
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=loginFor example:
http:/172.21.109.69:9080/psp/ps/?cmd=login
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Security, Permissions & Roles, and then click Roles.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Security, Permissions & Roles, and then click Roles.
-
-
Click Add a new Value. On the Add a New Value tab, enter the role name, for example,
OIMER,and then click Add. -
On the General tab, enter a description for the role in the Description field.
-
On the Permission Lists tab, click the search icon and perform the following:
-
In the Permission Lists lookup, enter
OIMERand then click Lookup. From the list, select OIMER. -
Click the plus sign (+) to add another row.
-
In the Permission Lists lookup, enter
EOEI9000and then click Lookup. From the list, select EOEI9000.Note:
Permission list EOEI9000 is not available in PeopleTools 8.53 and above, and is hence not applicable.
-
Click the plus sign (+) to add another row.
-
In the Permission Lists lookup, enter
EOCO9000and then click Lookup. From the list, select EOCO9000.
-
-
Click Save.
2.1.2.2.3 Assigning the Required Privileges to the Target System Account
To assign the required privileges to the target system account:
-
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=loginFor example:
http://172.21.109.69:9080/psp/ps/?cmd=login
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Security, User Profiles, and then click User Profiles.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Security, User Profiles, and then click User Profiles.
-
-
Click Add a new Value. On the Add a New Value tab, enter the user profile name, for example,
OIMER,and then click Add. -
On the General tab, perform the following:
-
From the Symbolic ID list, select the value that is displayed. For example, SYSADM1.
-
Enter valid values for the Password and Confirm Password fields.
-
Click the search icon for the Process Profile permission list.
-
In the Process Profile lookup, enter
OIMERand then click Lookup. From the list, select OIMER. The application returns to the General tab.
-
-
On the ID tab, select none as the value of the ID type.
-
On the Roles tab, click the search icon:
-
In the Roles lookup, enter
OIMERand then click Lookup. From the list, select OIMER. -
Click the plus sign (+) to add another row.
-
In the Roles lookup, enter
ProcessSchedulerAdminand then click Lookup. From the list, select ProcessSchedulerAdmin. -
Click the plus sign (+) to add another row.
-
In the Roles lookup, enter
EIR Administratorand then click Lookup. From the list, select EIR Administrator.Note:
Role EIR Administrator is not available in PeopleTools 8.53, and is hence not applicable.
-
Click Save to save this user profile. This profile is also used for a person with limited rights in PeopleSoft for performing all reconciliation-related configurations.
-
2.2 Installation
Installation information is divided across the following sections:
2.2.1 Installation on Oracle Identity Manager
Installation on Oracle Identity Manager consists of the following procedures:
2.2.1.1 Running the Connector Installer
To run the Connector Installer:
-
Create a directory for the connector, for example, PSFT_ER-11.1.1.5.0, in the OIM_HOME/server/ConnectorDefaultDirectory directory.
-
Copy the contents of the connector installation media directory into directory created in Step 1.
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
-
For Oracle Identity Manager release 11.1.1.x:
-
Log in to the Administrative and User Console.
-
On the Welcome to Identity Manager Advanced Administration page, in the System Management region, click Manage Connector.
-
-
For Oracle Identity Manager release 11.1.2.x:
-
Log in to Identity System Administration.
-
In the left pane, under System Management, click Manage Connector.
-
-
-
In the Manage Connector page, click Install.
-
From the Connector List list, select PeopleSoft Employee Reconciliation 11.1.1.5.0. This list displays the names and release numbers of connectors whose installation files you copy into the default connector installation directory in Step 1.
If you have copied the installation files into a different directory, then:
-
In the Alternative Directory field, enter the full path and name of that directory.
-
To repopulate the list of connectors in the Connector List list, click Refresh.
-
From the Connector List list, select PeopleSoft Employee Reconciliation 11.1.1.5.0.
-
-
Click Load.
-
To start the installation process, click Continue.
The following tasks are performed, in sequence:
-
Configuration of connector libraries
-
Import of the connector XML files (by using the Deployment Manager)
-
Compilation of adapter definitions
On successful completion of a task, a check mark is displayed for the task. If a task fails, then an X mark and a message stating the reason for failure is displayed. Depending on the reason for the failure, make the required correction and then perform one of the following steps:
-
Retry the installation by clicking Retry.
-
Cancel the installation and begin again from Step 1.
-
-
If all three tasks of the connector installation process are successful, then a message indicating successful installation is displayed. In addition, a list of steps that you must perform after the installation is displayed. These steps are as follows:
-
Configuring the IT resource for the connector
See Configuring the IT Resource for more information.
-
Configuring the scheduled tasks
See Configuring Scheduled Tasks for more information.
-
When you run the Connector Installer, it copies the connector files and external code files to destination directories on the Oracle Identity Manager host computer. These files are listed in Table 2-1.
2.2.1.2 Copying the Connector Files and External Code Files
Table 2-2 lists the files that you must copy manually and the directories on the Oracle Identity Manager host computer to which you must copy them.
If the connector files are extracted to the OIM_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/ directory on the Oracle Identity Manager host computer, then there is no need to copy these files manually.
Note:
-
The directory paths given in the first column of this table correspond to the location of the connector files in the PeopleSoft Employee Reconciliation directory on the installation media. See Files and Directories on the Installation Media for more information about these files.
If a particular destination directory does not exist on the Oracle Identity Manager host computer, then create it.
-
While installing Oracle Identity Manager in a cluster, you copy the contents of the installation directory to each node of the cluster. Then, restart each node. Similarly, after you install the connector, you must copy all the JAR files and the contents of the connectorResources directory into the corresponding directories on each node of the cluster.
Table 2-2 Files to Be Copied to the Oracle Identity Manager Host Computer
| File in the Installation Media Directory | Destination for Oracle Identity Manager |
|---|---|
|
lib/PeopleSoftOIMListener.ear |
OIM_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/listener |
|
Files in the test/scripts directory |
OIM_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/scripts |
|
Files in the test/config directory |
OIM_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/config |
2.2.1.3 Configuring the IT Resource
The IT resource for the target system contains connection information about the target system. Oracle Identity Manager uses this information during reconciliation.
When you run the Connector Installer, the PSFT HRMS IT resource is automatically created in Oracle Identity Manager. You must specify values for the parameters of this IT resource as follows:
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
-
For Oracle Identity Manager release 11.1.1.x:
Log in to the Administrative and User Console.
-
For Oracle Identity Manager release 11.1.2.x:
Log in to Identity System Administration.
-
-
If you are using Oracle Identity Manager release 11.1.1.x, then:
-
On the Welcome page, click Advanced in the upper-right corner of the page.
-
On the Welcome to Oracle Identity Manager Advanced Administration page, in the Configuration region, click Manage IT Resource.
-
-
If you are using Oracle Identity Manager release 11.1.2.x, in the left pane, then under Configuration, click IT Resource.
-
In the IT Resource Name field on the Manage IT Resource page, enter
PSFT HRMSand then click Search. -
Click the edit icon for the IT resource.
-
From the list at the top of the page, select Details and Parameters.
-
Specify values for the parameters discussed in Table 2-3. The remaining parameters of IT resource are not applicable for this connector.
-
To save the values, click Update.
2.2.1.4 IT Resource Parameters
Table 2-3 lists the IT resource parameters applicable to the connector.
Table 2-3 IT Resource Parameters
| Parameter | Description |
|---|---|
|
Configuration Lookup |
This parameter holds the name of the lookup definition that contains configuration information. Default value: Note: You must not change the value of this parameter. However, if you create a copy of all the connector objects, then you can specify the unique name of the copy of this lookup definition as the value of the Configuration Lookup Name parameter in the copy of the IT resource. |
|
IsActive |
This parameter is used to specify whether the specified IT Resource is in use or not. Enter one of the following as the value of the IsActive parameter: Enter Enter Default value: |
2.2.1.5 Deploying the PeopleSoft Listener
This section contains the following topics:
- Prerequisites for Deploying the PeopleSoft Listener
- Deploying the PeopleSoft Listener on Oracle Identity Manager
- Prerequisites for Deploying the PeopleSoft Listener on IBM WebSphere Application Server
- Deploying the PeopleSoft Listener on WebSphere Application Server
- Importing Oracle Identity Manager CA Root Certificate into PeopleSoft WebServer
2.2.1.5.1 Prerequisites for Deploying the PeopleSoft Listener
The PeopleSoft listener is a Web application that is deployed on an Oracle Identity Manager host computer. The PeopleSoft listener parses the XML message and creates a reconciliation event in Oracle Identity Manager.
Note:
-
If you have already deployed a listener for the PeopleSoft User Management connector, then you can skip this procedure.
A single listener is sufficient for both the connectors. You can configure the nodes to point to the same listener with different IT resource names.
-
The PeopleSoft Employee Reconciliation and PeopleSoft User Management connectors have different IT resources. Therefore, you must configure separate HTTP nodes for messages of the Employee Reconciliation and User Management connectors.
Even if an existing node is configured to the PeopleSoft listener on Oracle Identity Manager, a separate node is required for messages of the PeopleSoft Employee Reconciliation connector.
-
If you are using IBM WebSphere Application Server, then perform the procedure described in Deploying the PeopleSoft Listener on WebSphere Application Server.
-
If you are using Oracle Identity Governance 12c, then deploying and pinging PeopleSoft listener operations may not work as expected. Apply PeopleSoft Connector Patch 26419438 by using the following URL for these operations to work successfully:
https://support.oracle.com/
See Also:
Upgrading the PeopleSoft Listener for information about upgrading the listener
Before deploying the PeopleSoft listener, perform the following steps:
-
Ensure Apache Ant 1.7 or later and JDK 1.6 or later are installed.
-
Set the following environment values in ant.properties:
-
ORACLE_HOME maps to the Oracle Identity Manager installation directory. For example,
/ps1/beahome/Oracle_IDM1 -
ORACLE_COMMON maps to the oracle_common directory in MW_HOME, where MW_HOME is the directory in which Oracle Identity Management Suite is installed. For example,
/ps1/beahome/oracle_common -
WL_HOME maps to the WebLogic Server directory. For example,
/middleware/wlserver_10.3 -
JAVA_HOME maps to your JDK environment. For example,
C:\Program Files\Java\jdk1.6.0_24 -
PATH must include the JAVA_HOME/bin directory. You can set the PATH variable using the
SET PATH=$JAVA_HOME/bin:$PATHcommand.
-
-
Build the wlfullclient.jar file in Oracle WebLogic server, for example, in the WL_HOME/server/lib directory:
-
Change directories to WL_HOME/server/lib.
-
Run the following command:
java -jar ../../../modules/com.bea.core.jarbuilder_1.3.0.0.jar
Note:
The exact jar file version can be different based on the WebLogic Server. Use the corresponding file with the name as
com.bea.core.jarbuilderat the WL_HOME/../modules/ directory.
-
-
Start Oracle Identity Manager and the Admin Server.
2.2.1.5.2 Deploying the PeopleSoft Listener on Oracle Identity Manager
To deploy the PeopleSoft listener on Oracle Identity Manager:
Note:
If you need to deploy the listener in an Oracle Identity Manager cluster, then:
-
Specify the name of the cluster for the
oim.server.nameproperty in the listener/deploy.properties file. -
Update the following configurations appropriately with the URL of the listener, /PeopleSoftOIMListener:
-
Front-end web server
-
Load balancer
-
PeopleSoft nodes
-
-
Copy the connector package into the OIM_HOME/server/ConnectorDefaultDirectory directory of every node.
2.2.1.5.3 Prerequisites for Deploying the PeopleSoft Listener on IBM WebSphere Application Server
Before deploying the PeopleSoft listener, ensure Apache Ant 1.7 or later and JDK 1.6 or later are installed. Then, set the following environment values in the ant.properties file:
-
OIM_ORACLE_HOME maps to the Oracle Identity Manager installation directory. For example,
/ps1/was/Oracle_IDM1You can set this variable using the
setenv OIM_ORACLE_HOME <value>command. -
JAVA_HOME maps to your JDK environment. For example,
/usr/local/packages/jdk16/You can set this variable using the
setenv JAVA_HOME <value>command. -
PATH must include the JAVA_HOME/bin directory. You can set this variable using the
setenv PATH $JAVA_HOME/bin:$PATHcommand. -
Create the listener EAR file in listener directory. To do so:
-
Change directories to $OIM_ORACLE_HOME/server/ConnectorDefaultDirectory/PSFT_ER-11.1.1.5.0/listener.
-
Run the following commands:
rm -rf deployear mkdir deployear cp -rf base/PeopleSoftOIMListener.ear/META-INF deployear cp -rf base/PeopleSoftOIMListener.ear/PeopleSoftOIMListener.war/WEB-INF deployear cp -rf $OIM_ORACLE_HOME/server/client/oimclient.jar deployear/WEB-INF/lib cp -rf $OIM_ORACLE_HOME/server/platform/iam-platform-utils.jar deployear/WEB-INF/lib cp -rf $OIM_ORACLE_HOME/server/platform/iam-platform-auth-client.jar deployear/WEB-INF/lib cd deployear sed -i 's/OIM_ADMIN_USER/xelsysadm/g' WEB-INF/web.xml jar -cvf PeopleSoftOIMListener.war WEB-INF rm -rf WEB-INF/ jar -cvf PeopleSoftOIMListener.ear META-INF PeopleSoftOIMListener.war rm -rf META-INF rm -rf PeopleSoftOIMListener.war
-
2.2.1.5.4 Deploying the PeopleSoft Listener on WebSphere Application Server
To deploy the PeopleSoft listener on IBM WebSphere Application Server:
2.2.1.5.5 Importing Oracle Identity Manager CA Root Certificate into PeopleSoft WebServer
If you have configured SSL in Oracle Identity Manager, for the PeopleSoft listener to work in SSL you must import Oracle Identity Manager CA root certificate into PeopleSoft WebServer.
To do so, perform one of the following procedures depending on the PeopleSoft WebServer you are using:
-
For Oracle WebLogic Server:
-
Identity the certificate of issuing authority, the root CA for Oracle Identity Manager.
If you use the default demo certificate, then the root certificate is located in the following location:
MW_HOME/wlserver_10.3/server/lib/CertGenCA.der
If the certificate is issued by an external entity, then you must import the corresponding root certificate.
-
Use pskeymanager to import the root certificate into PeopleSoft WebServer keystore.
-
-
For IBM WebSphere Application Server:
-
Identity the certificate of issuing authority, the root CA for Oracle Identity Manager.
In the WebSphere Admin console, navigate to Security, SSL certificate and key management, Key stores and certificates, CellDefaultTrustStore, and Signer certificates. Then, select root and click Extract.
If the certificate is issued by a different entity, then you must import the corresponding root certificate.
-
Use pskeymanager to import the root certificate into PeopleSoft WebServer keystore.
-
2.2.1.6 Removing the PeopleSoft Listener
Note:
-
This section is not a part of installation on Oracle Identity Manager. You might need this procedure to extend the connector.
-
If you uninstall the connector, you must also remove the listener. Installing a new connector over a previously deployed listener creates discrepancies.
-
Do not remove the listener if the PeopleSoft User Management connector is installed and if it is using the listener.
See Also:
Upgrading the PeopleSoft Listener for information about upgrading the listener
To remove the PeopleSoft listener:
2.2.1.6.1 Removing the PeopleSoft Listener for BM WebSphere Application Server
To remove the PeopleSoft listener for IBM WebSphere Application Server:
2.2.2 Installation on the Target System
During this stage, you configure the target system to enable it for reconciliation. This information is provided in the following sections:
2.2.2.1 Configuring the Target System for Full Reconciliation
As described in About the Connector, full reconciliation is used to reconcile all existing person data into Oracle Identity Manager. The PeopleCode that is activated in response to these events extracts the required person data through the following components:
For PeopleSoft 9.0:
PERSONAL_DATA, JOB_DATA, JOB_DATA_EMP, JOB_DATA_CONCUR, and JOB_DATA_CWR
Configuring the target system for full reconciliation involves creation of XML files for full reconciliation by performing the following procedures:
2.2.2.1.1 Configuring the PeopleSoft Integration Broker
The following sections explain the procedure to configure PeopleSoft Integration Broker:
2.2.2.1.1.1 Configuring PeopleSoft Integration Broker Gateway
PeopleSoft Integration Broker is installed as part of the PeopleTools installation process. The Integration Broker Gateway is a component of PeopleSoft Integration Broker, which runs on the PeopleSoft Web Server. It is the physical hub between PeopleSoft and the third-party system. The integration gateway manages the receipt and delivery of messages passed among systems through PeopleSoft Integration Broker.
To configure the PeopleSoft Integration Broker gateway:
2.2.2.1.1.2 Configuring PeopleSoft Integration Broker
PeopleSoft Integration Broker provides a mechanism for communicating with the outside world using XML files. Communication can take place between different PeopleSoft applications or between PeopleSoft and third-party systems. To subscribe to data, third-party applications can accept and process XML messages posted by PeopleSoft using the available PeopleSoft connectors. The Integration Broker routes messages to and from PeopleSoft.
To configure PeopleSoft Integration Broker, create a remote node as follows:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier click, expand PeopleTools, Integration Broker, Integration Setup, and then click Nodes.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Nodes.
-
-
On the Add a New Value tab, enter the node name, for example,
OIM_FILE_NODE,and then click Add. -
On the Node Definition tab, provide the following values:
In the Description field, enter a description for the node.
In the Default User ID field, enter
PS. -
Make this node a remote node by deselecting the Local Node check box and selecting the Active Node check box.
-
Ensure that the Node Type is PIA.
-
For PeopleTools 8.56 or earlier, perform the following steps. If you are using PeopleTools 8.57, skip this step and perform step 7.
-
On the Connectors tab, search for the following information by clicking the Lookup icon:
Gateway ID: LOCAL
Connector ID: FILEOUTPUT
-
On the Properties page in the Connectors tab, enter the following information:
Property ID: HEADER
Property Name: sendUncompressed
Required value: Y
Property ID: PROPERTY
Property Name: Method
Required value: PUT
Property ID: PROPERTY
Property Name: FilePath
Required value: Any location writable by the Integration Broker. This location is used to generate the full data publish files.
Property ID: PROPERTY
Property Name: Password
Required value: Same value as of ig.fileconnector.password in the integrationGateway.properties file. If the password is not already encrypted, that you can encrypt it as follows:
i) In the Password Encrypting Utility region, enter the value of the ig.fileconnector.password property in the Password and Confirm Password fields.
ii) Click Encrypt.
iii) From the Encrypted Password field, copy the encrypted password to the Value field for the Password property.
Note:
To locate the intergrationGateway.properties file, perform the following steps using the PeopleSoft administrator credentials:
-
In PeopleSoft Internet Architecture:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Configuration, and then click Gateways.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Configuration, and then click Gateways
-
-
In the Integration Gateway ID field, enter
LOCAL,and then click Search. -
Click the Gateway Setup Properties link.
You are prompted to enter the user ID and password.
-
Specify the following values:
In the UserID field, enter the appropriate user ID.
In the Password field, enter the appropriate password.
-
-
-
For PeopleTools 8.57, perform the following steps:
-
On the Connectors tab of the PeopleSoft Internet Architecture window, search for the following information by clicking the Lookup icon:
Gateway ID: LOCAL
Connector ID: FTPTARGET
-
On the Properties page in the Connectors tab, enter the following information:
Property ID: HEADER
Property Name: sendUncompressed
Required value: Y
Property ID: FTPTARGET
Property Name: HOSTNAME
Required value: Enter the hostname of the computer on which you want to generate the files. You can also give OIM hostname if ftp port is open.
Property ID: FTPTARGET
Property Name: USERNAME
Required value: Enter the hostname of the computer on which you want to generate the files.
Property ID: FTPTARGET
Property Name: PASSWORD
Required value: Enter the password of the computer on which you want to generate the files. Password should be in encrypted form. If the password is not already encrypted, then you can encrypt it as follows:
i) In the Password Encrypting Utility region, enter the value of the ig.fileconnector.password property in the Password and Confirm Password fields.
ii) Click Encrypt.
iii) From the Encrypted Password field, copy the encrypted password to the Value field for the Password property.
Property ID: FTPTARGET
Property Name: TYPE
Required value: ASCII
Property ID: FTPTARGE
Property Name: METHOD
Required value: PUT
Property ID: FTPTARGET
Property Name: FTPS
Required value: N
Property ID: FTPTARGET
Property Name: FTPMODE
Required value: ACTIVE
Property ID: FTPTARGET
Property Name: DIRECTORY
Required value: Enter the location where you want to generate xmls.
Property ID: FTPTARGET
-
-
Click Save.
-
Click Ping Node to check whether a connection is established with the specified IP address.
2.2.2.1.2 Configuring the PERSON_BASIC_FULLSYNC Service Operation
The PERSON_BASIC_FULLSYNC message contains the basic personal information about all the persons. This information includes the Employee ID, First Name, Last Name, and Employee Type.
To configure the PERSON_BASIC_FULLSYNC service operation perform the following procedures:
Note:
The procedure remains the same for PeopleTools 8.49 with HRMS 9.0, PeopleTools 8.50 with HRMS 9.1, PeopleTools 8.53 through 8.57 with HRMS 9.2. The screenshots are taken on PeopleTools 8.49 version. Publishing Messages With VERSION_5 contains a summary of the procedure for PeopleTools 8.51 with HRMS 9.1.
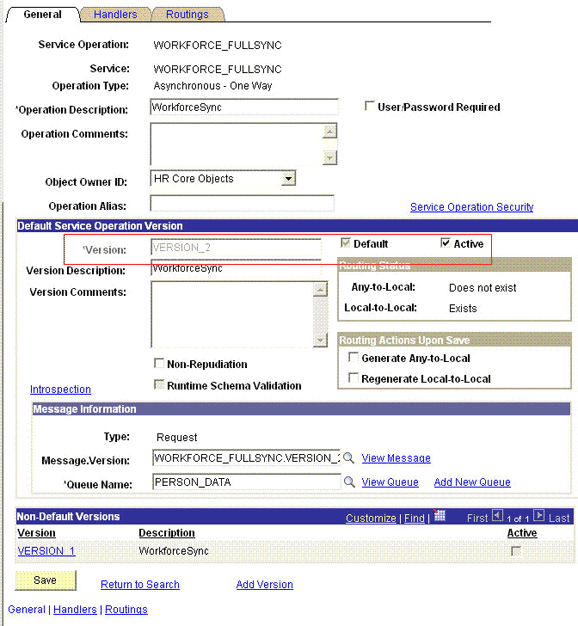
2.2.2.1.2.1 Activating the PERSON_BASIC_FULLSYNC Service Operation
The service operation is a mechanism to trigger, receive, transform, and route messages that provide information about updates in PeopleSoft or an external application. You must activate the service operation to successfully transfer or receive messages.
To activate the PERSON_BASIC_FULLSYNC service operation:
Note:
If the message version is not the same as specified, then you can change the message version as described in Changing Default Message Versions.
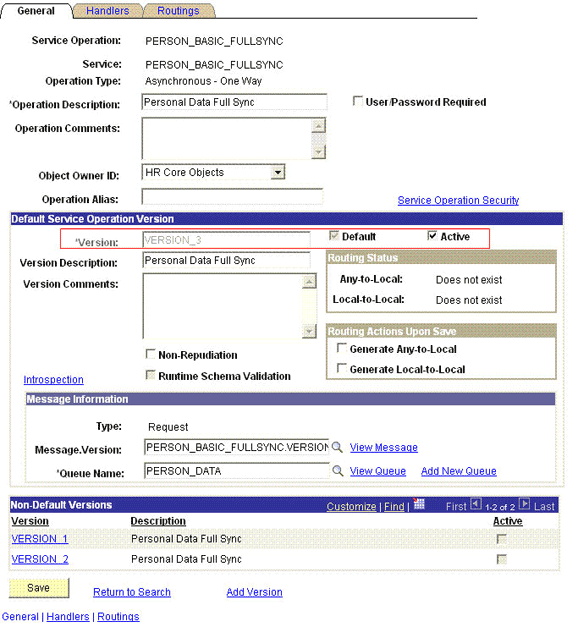
2.2.2.1.2.2 Verifying the Queue Status for the PERSON_BASIC_FULLSYNC Service Operation
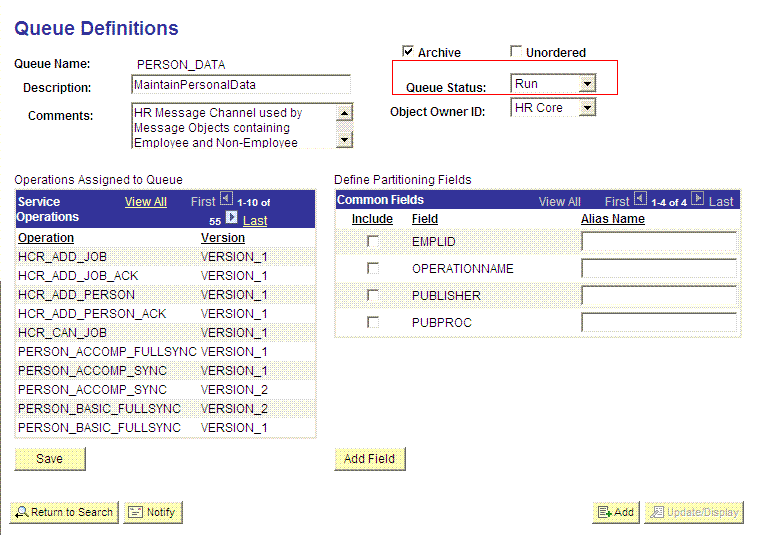
All messages in PeopleSoft are sent through a queue. This is done to ensure that the messages are delivered in a correct sequence. Therefore, you must ensure that the queue is in the Run status.
To ensure that the status of the queue for the PERSON_BASIC_FULLSYNC service operation is Run:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
-
Search for the PERSON_DATA queue.
-
In the Queue Status list, ensure that Run is selected.
Note:
If the queue status is not Run:
-
From the Queue Status list, select Run.
-
Click Save.
The queue status is highlighted in the following screenshot:
-
-
Click Return to Search.
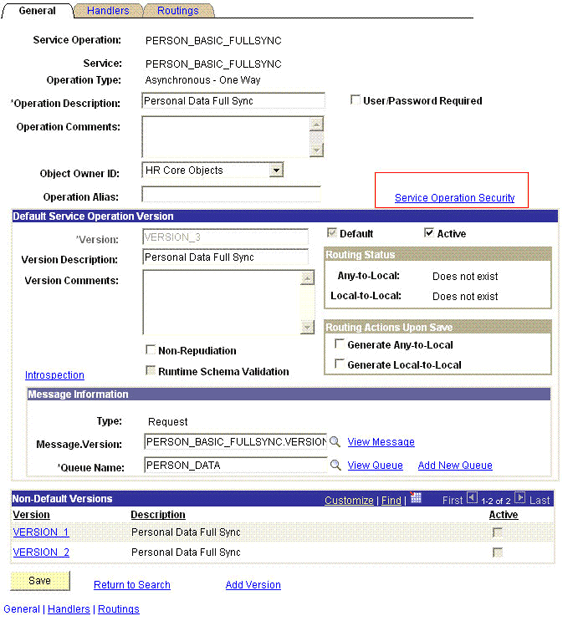
2.2.2.1.2.3 Setting Up the Security for the PERSON_BASIC_FULLSYNC Service Operation
A person on the target system who has permission to modify or add personal or job information of a person might not have access to send messages regarding these updates. Therefore, it is imperative to explicitly grant security to enable operations.
To set up the security for PERSON_BASIC_FULLSYNC service operation:
-
In PeopleSoft Internet Architecture, expand PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
-
Search for and open the PERSON_BASIC_FULLSYNC service operation.
-
On the General tab, click the Service Operation Security link.
The link is highlighted in the following screenshot:
-
Attach the OIMER permission list to the PERSON_BASIC_FULLSYNC service operation. This list is created in Step 3 of the preinstallation procedure discussed in Creating a Permission List.
To attach the permission list:
-
Click the plus sign (+) to add a row to the Permission List field.
-
In the Permission List field, enter
OIMERand then click the Look up Permission List icon.The OIMER permission list appears.
-
From the Access list, select Full Access.
The following screenshot displays the preceding steps:
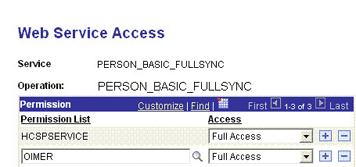
-
Click Save.
-
Click Return to Search.
-
2.2.2.1.2.4 Defining the Routing for the PERSON_BASIC_FULLSYNC Service Operation
Routing is defined to inform PeopleSoft about the origin and intended recipient of the message. You might have to transform the message being sent or received according to the business rules.
To define the routing for PERSON_BASIC_FULLSYNC service operation:
-
On the Routing tab, enter
PERSON_BASIC_FULLSYNC_HR_FILEas the routing name and then click Add. -
On the Routing Definitions tab, enter the following:
Sender Node:
PSFT_HRNote:
The Sender Node is the default active local node. To locate the sender node:
-
Click the Look up icon.
-
Click Default to sort the results in descending order.
The default active local node should meet the following criteria:
Local Node: 1
Default Local Node: Y
Node Type: PIA
Only one node can meet all the above conditions at a time.
-
Select the node.
-
Click Save.
Receiver Node:
OIM_FILE_NODEThe following screenshot displays the Sender and Receiver nodes:
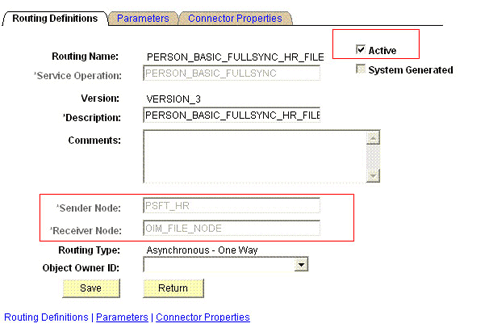
-
-
Click Save.
-
Click Return to go back to the Routings tab of the service operation, and verify whether your routing is active.
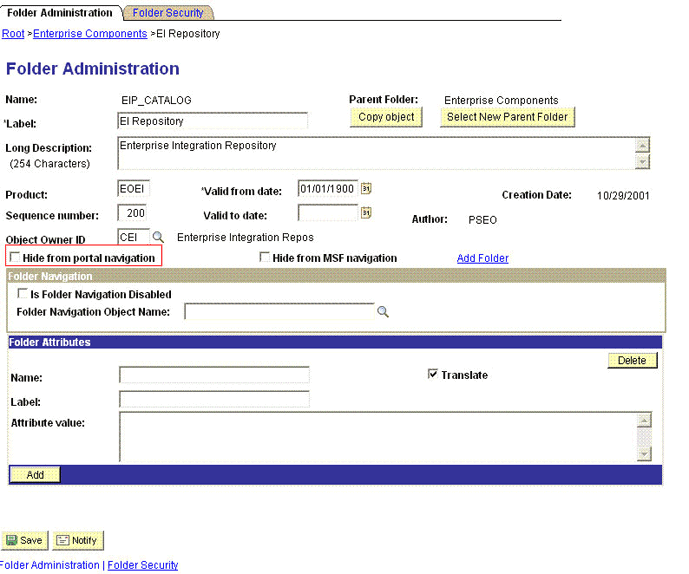
2.2.2.1.2.5 Displaying the EI Repository Folder
EI Repository is a hidden folder in PeopleSoft. Therefore, you must display this folder.
To display the EI Repository folder:
Note:
-
If you are using PeopleTools 8.53, PeopleTools 8.54, PeopleTools 8.55, PeopleTools 8.56, or PeopleTools 8.57 as the target system, then do not perform the procedure described in this section.
-
Perform this procedure using the PeopleSoft administrator credentials.
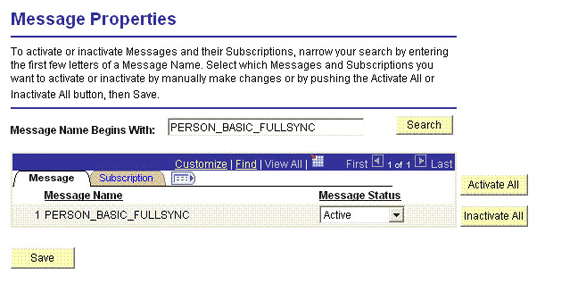
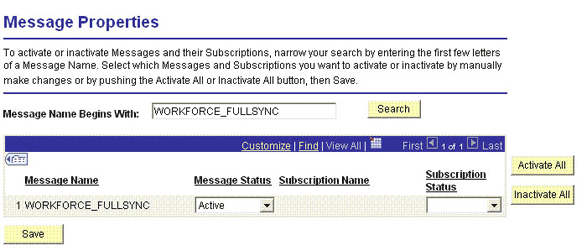
2.2.2.1.2.6 Activating the PERSON_BASIC_FULLSYNC Message
You must activate the PERSON_BASIC_FULLSYNC message so that it can be processed.
To activate the PERSON_BASIC_FULLSYNC message:
Note:
If you are using PeopleTools 8.53, PeopleTools 8.54, PeopleTools 8.55, PeopleTools 8.56, or PeopleTools 8.57 as the target system, then do not perform the procedure described in this section.
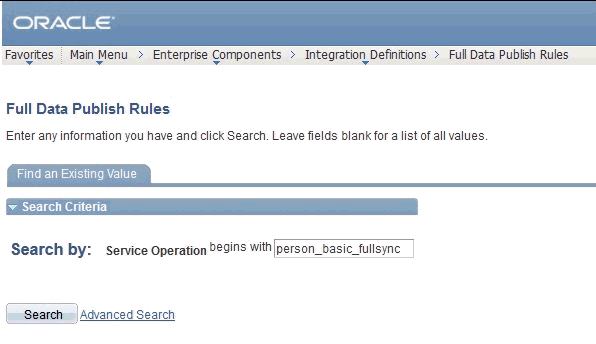
2.2.2.1.2.7 Activating the Full Data Publish Rule
You must define and activate the Full Data Publish rule, because it acts as a catalyst for the full reconciliation process. This rule provides the full reconciliation process the desired information to initiate reconciliation.
To activate the full data publish rule:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand Enterprise Components, Integration Definitions, and then click Full Data Publish Rules.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, Enterprise Components, Integration Definitions, and then click Full Data Publish Rules.
-
-
Search for and open the PERSON_BASIC_FULLSYNC message.
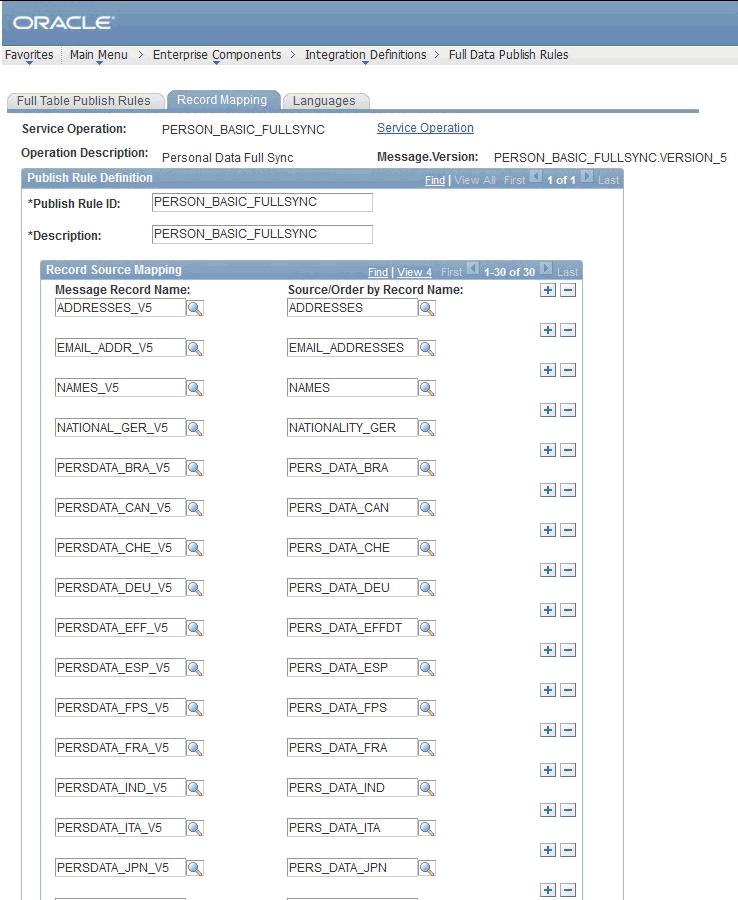
-
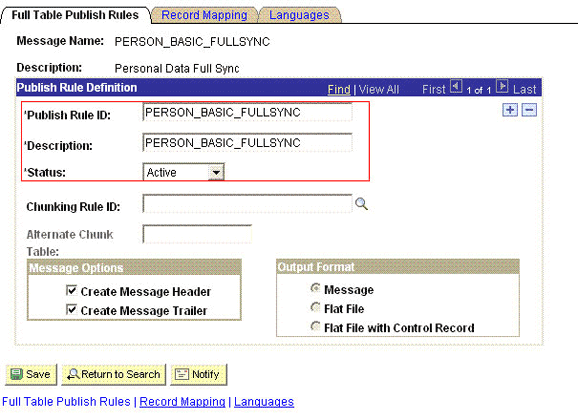
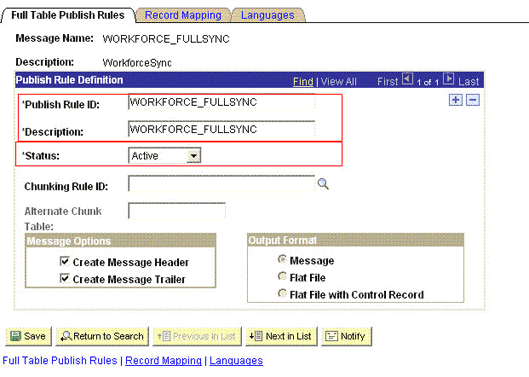
In the Publish Rule Definition region:
-
In the Publish Rule ID field, enter
PERSON_BASIC_FULLSYNC. -
In the Description field, enter
PERSON_BASIC_FULLSYNC. -
From the Status list, select Active.
The following screenshot displays the preceding steps:
-
-
Click Save.
2.2.2.1.3 Configuring the WORKFORCE_FULLSYNC Service Operation
The WORKFORCE_FULLSYNC message contains the job-related details of all persons. This information includes the Department, Supervisor ID, Manager ID, and Job Code.
To configure the WORKFORCE_FULLSYNC service operation perform the following procedures:
Note:
In PeopleSoft HRMS, there are many versions of the message associated with this service operation. But, when you integrate PeopleSoft HRMS and Oracle Identity Manager, you must send the following versions depending on the version of HRMS:
-
Use
WORKFORCE_FULLSYNC.INTERNALfor HRMS 8.9 Bundle 23 or later, HRMS 9.0 Bundle 14 or later, HRMS 9.1 Bundle 3 or later, and HRMS 9.2 Image 4 or later. -
Use
WORKFORCE_FULLSYNC.VERSION_3for other versions of HRMS.
-
Verifying the Queue Status for the WORKFORCE_FULLSYNC Service Operation
-
Setting Up the Security for the WORKFORCE_FULLSYNC Service Operation
-
Defining the Routing for the WORKFORCE_FULLSYNC Service Operation
Note:
The procedure remains the same for PeopleTools 8.49 with HRMS 9.0, PeopleTools 8.50 with HRMS 9.1, PeopleTools 8.53 through 8.57 with HRMS 9.2. The screenshots are taken on version PeopleTools 8.49.
2.2.2.1.3.1 Activating the WORKFORCE_FULLSYNC Service Operation
To activate the WORKFORCE_FULLSYNC service operation:
Note:
If the message version is not the same as specified, then you can change the message version as described in Changing Default Message Versions.
2.2.2.1.3.2 Verifying the Queue Status for the WORKFORCE_FULLSYNC Service Operation
To ensure that the status of the queue for the WORKFORCE_FULLSYNC service operation is Run:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
-
Search for the PERSON_DATA queue.
-
In the Queue Status list, ensure that Run is selected.
Note:
If the queue status is not Run:
-
From the Queue Status list, select Run.
-
Click Save.
The queue status is shown in the following screenshot:

-
-
Click Return to Search.
2.2.2.1.3.3 Setting Up the Security for the WORKFORCE_FULLSYNC Service Operation
To set up the security for the WORKFORCE_FULLSYNC service operation:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
-
-
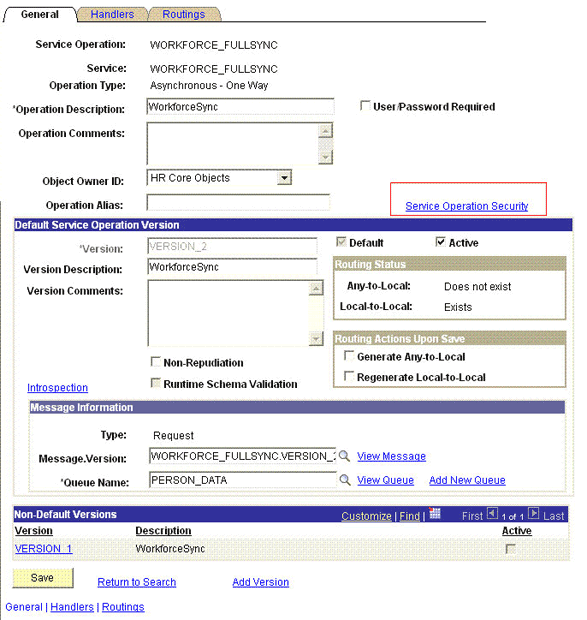
Search for an open the WORKFORCE_FULLSYNC service operation.
-
On the General tab, click the Service Operation Security link.
The link is shown in the following screenshot:
-
Attach the OIMER permission list to the WORKFORCE_FULLSYNC service operation. This list is created in Step 3 of the preinstallation procedure discussed in Creating a Permission List.
To attach the permission list:
-
Click the plus sign (+) to add a row to the Permission List field.
-
In the Permission List field, enter
OIMERand then click the Look up Permission List icon.The OIMER permission list appears.
-
From the Access list, select Full Access.
The following screenshot displays the Access list with Full Access:
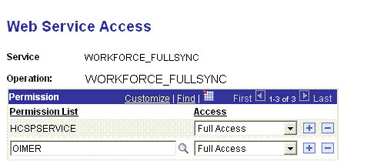
-
Click Save.
-
Click Return to Search.
-
2.2.2.1.3.4 Defining the Routing for the WORKFORCE_FULLSYNC Service Operation
To define the routing for the WORKFORCE_FULLSYNC service operation:
-
On the Routing tab, enter
WORKFORCE_FULLSYNC_HR_FILEas the routing name and then click Add. -
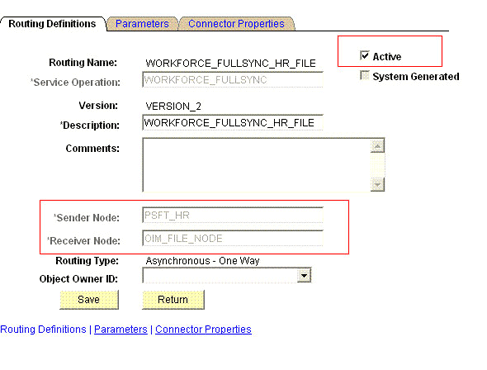
On the Routing Definitions tab, enter the following:
Sender Node:
PSFT_HRNote:
The Sender Node is the default active local node. To locate the sender node:
-
Click the Look up icon.
-
Click Default to sort the results in descending order.
The default active local node should meet the following criteria:
Local Node: 1
Default Local Node: Y
Node Type: PIA
Only one node can meet all the above conditions at a time.
-
Select the node.
-
Click Save.
Receiver Node:
OIM_FILE_NODEThe following graphic displays both the Sender and the Receiver nodes:
-
-
Click Save.
-
Click Return to go back to the Routings tab of the Service Operation, and verify whether your routing is active.
2.2.2.1.3.5 Displaying the EI Repository Folder
To display the EI Repository folder:
Note:
-
If you are using PeopleTools 8.53 or later, then do not perform the procedure mentioned in this section.
-
If you have performed this procedure as described in "Displaying the EI Repository Folder", then you can skip this section.
-
Perform this procedure using the PeopleSoft administrator credentials.
2.2.2.1.3.6 Activating the WORKFORCE_FULLSYNC Message
To activate the WORKFORCE_FULLSYNC message:
Note:
If you are using PeopleTools 8.53, PeopleTools 8.54, PeopleTools 8.55, PeopleTools 8.56, PeopleTools 8.57, then do not perform the procedure mentioned in this section.
2.2.2.1.3.7 Activating the Full Data Publish Rule
To activate the full data publish rule:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand Enterprise Components, Integration Definitions, and then click Full Data Publish Rules.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, Enterprise Components, Integration Definitions, and then click Full Data Publish Rules.
-
-
Search for and open the WORKFORCE_FULLSYNC message.
-
In the Publish Rule Definition region:
-
In the Publish Rule ID field, enter
WORKFORCE_FULLSYNC. -
In the Description field, enter
WORKFORCE_FULLSYNC. -
From the Status list, select Active.
The following screenshot displays the preceding steps:
-
-
Click Save.
2.2.2.2 Configuring the Target System for Incremental Reconciliation
Configuring the target system for incremental reconciliation involves configuring PeopleSoft Integration Broker and configuring the PERSON_BASIC_SYNC and WORKFORCE_SYNC messages.
A message is the physical container for the XML data that is sent from the target system. Message definitions provide the physical description of data that is sent from the target system. This data includes fields, field types, and field lengths. A queue is used to carry messages. It is a mechanism for structuring data into logical groups. A message can belong to only one queue.
Setting the PeopleSoft Integration Broker gateway is mandatory when you configure PeopleSoft Integration Broker. To subscribe to XML data, Oracle Identity Manager can accept and process XML messages posted by PeopleSoft by using PeopleSoft connectors located in the PeopleSoft Integration Broker gateway. These connectors are Java programs that are controlled by the PeopleSoft Integration Broker gateway.
This gateway is a program that runs on the PeopleSoft Web server. It acts as a physical hub between PeopleSoft and PeopleSoft applications (or third-party systems, such as Oracle Identity Manager). The gateway manages the receipt and delivery of messages to external applications through PeopleSoft Integration Broker.
To configure the target system for incremental reconciliation, perform the following procedures:
Note:
You must use an administrator account to perform the following procedures.
2.2.2.2.1 Configuring PeopleSoft Integration Broker
The following sections explain the procedure to configure PeopleSoft Integration Broker:
2.2.2.2.1.1 Configuring PeopleSoft Integration Broker Gateway
Section "Configuring PeopleSoft Integration Broker Gateway" describes the procedure to configure the PeopleSoft Integration Broker gateway.
2.2.2.2.1.2 Configuring PeopleSoft Integration Broker
To configure PeopleSoft Integration Broker:
Note:
-
The PeopleSoft Employee Reconciliation and PeopleSoft User Management connectors have different IT resources. Therefore, you must configure separate HTTP nodes for messages of the Employee Reconciliation and User Management connectors.
Even if an existing node is configured to the PeopleSoft listener on Oracle Identity Manager, a separate node is required for messages of the PeopleSoft User Management connector.
-
A single listener is sufficient for both the connectors. You can configure the nodes to point to the same listener with different IT resource names.
-
Create a remote node by performing the following steps:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Integration Setup, and then click Nodes.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Nodes.
-
-
On the Add a New Value tab, enter the node name, for example,
OIM_NODE,and then click Add. -
On the Node Definition tab, enter a description for the node in the Description field. In addition, specify the SuperUserID in the Default User ID field. For example,
PS. -
Make this node a remote node by deselecting the Local Node check box and selecting the Active Node check box.
-
Ensure Node Type is PIA.
-
On the Connectors tab, search for the following information by clicking the Lookup icon:
Gateway ID: LOCAL
Connector ID: HTTPTARGET
-
On the Properties page in the Connectors tab, enter the following information:
Property ID: HEADER
Property Name: sendUncompressed
Required value: Y
Property ID: HTTP PROPERTY
Property Name: Method
Required value: POST
Property ID: HEADER
Property Name: Location
Required value: Enter the value of the IT Resource name as configured for PeopleSoft HRMS
Sample value: PSFT HRMS
Property ID: PRIMARYURL
Property Name: URL
Required value: Enter the URL of the PeopleSoft listener that is configured to receive XML messages. This URL must be in the following format:
http://ORACLE_IDENTITY_MANAGER_SERVER_IPADDRESS:PORT/PeopleSoftOIMListener
The URL depends on the application server that you are using. For an environment on which SSL is not enabled, the URL must be in the following format:
For IBM WebSphere Application Server:
http://10.121.16.42:9080/PeopleSoftOIMListener
For Oracle WebLogic Server:
http://10.121.16.42:7001/PeopleSoftOIMListener
For an environment on which SSL is enabled, the URL must be in the following format:
https://COMMON_NAME:PORT/PeopleSoftOIMListener
For IBM WebSphere Application Server:
https://example088196:9443/PeopleSoftOIMListener
For Oracle WebLogic Server:
https://example088196:7002/PeopleSoftOIMListener
Note:
The ports may vary depending on the installation that you are using.
-
Click Save to save the changes.
-
Click the Ping Node button to check whether a connection is established with the specified IP address.
Note:
Ping also validates the target authentication, in this case, the IT resource name.
-
Before the XML messages are sent from the target system to Oracle Identity Manager, you must verify whether the PeopleSoft node is running. You can do so by clicking the Ping Node button in the Connectors tab. To access the Connectors tab, click PeopleTools, Integration Broker, Integration Setup, and then Nodes.
Note:
You might encounter the following error when you send a message from PeopleSoft Integration Broker over HTTP PeopleTools 8.50 target system:
HttpTargetConnector:PSHttpFactory init or setCertificate failed
This happens because the Integration Broker Gateway Web server tries to access the keystore even if SSL is not enabled using the parameters defined in the integrationgateway.properties file as follows:
secureFileKeystorePath=<path to pskey>
secureFileKeystorePasswd=password
If either the <path to pskey> or the password (unencrypted) is incorrect, you will receive the preceding error message. Perform the following steps to resolve the error:
-
Verify if
secureFileKeystorePathin the integrationgateway.properties file is correct. -
Verify if
secureFileKeystorePasswdin the integrationgateway.properties file is correct. -
Access the pskeymanager to check the accuracy of the path and the password. You can access pskeymanager from the following location:
<PIA_HOME>\webserv\peoplesoft\bin
Usually, a new PeopleTools 8.50 instance throws the preceding error when you message over the HTTP target connector. The reason is that the default password is not in the encrypted format in the integrationgateway.properties file.
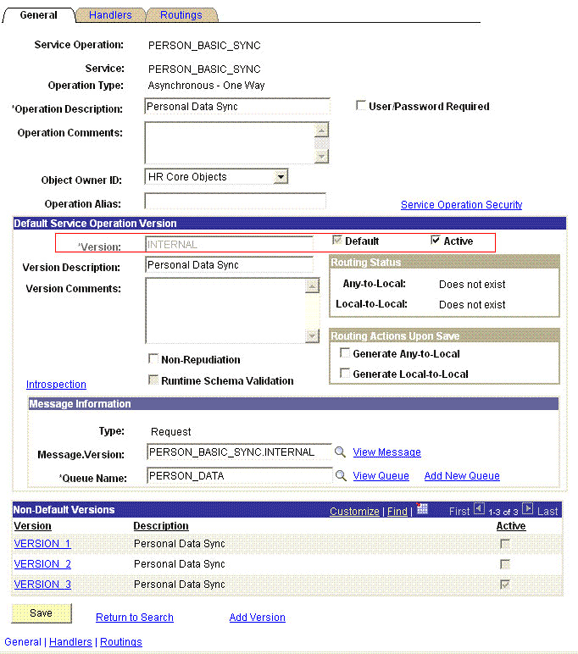
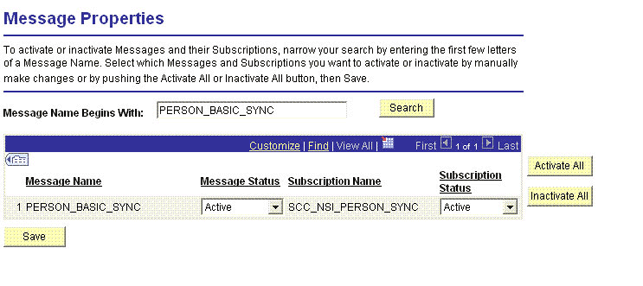
2.2.2.2.2 Configuring the PERSON_BASIC_SYNC Service Operation
The PERSON_BASIC_SYNC message contains the updated information about a particular person. This information includes the Employee ID and the information that is added or modified.
To configure the PERSON_BASIC_SYNC service operation perform the following procedures:
Note:
The procedure remains the same for PeopleTools 8.49 with HRMS 9.0, PeopleTools 8.50 with HRMS 9.1, PeopleTools 8.53 through 8.57 with HRMS 9.2. The screenshots are taken on PeopleTools 8.49 version.
2.2.2.2.2.1 Activating the PERSON_BASIC_SYNC Service Operation
To activate the PERSON_BASIC_SYNC service operation:
Note:
If the message version is not the same as specified, then you can change the message version as described in Changing Default Message Versions.
2.2.2.2.2.2 Verifying the Queue Status for the PERSON_BASIC_SYNC Service Operation
To ensure that the status of the queue for the PERSON_BASIC_SYNC service operation is Run:
-
In the PeopleSoft Internet Architecture window:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
-
Search for the PERSON_DATA queue.
-
In the Queue Status list, ensure that Run is selected.
Note:
If the queue status is not Run:
-
From the Queue Status list, select Run.
-
Click Save.
The queue status is shown in the following screenshot:

-
-
Click Return to Search.
2.2.2.2.2.3 Setting Up the Security for the PERSON_BASIC_SYNC Service Operation
To set up the security for the PERSON_BASIC_SYNC service operation:
-
In PeopleSoft Internet Architecture:
-
For PeopleTools 8.54 and earlier releases, expand PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
-
For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup and then click Service Operations.
-
-
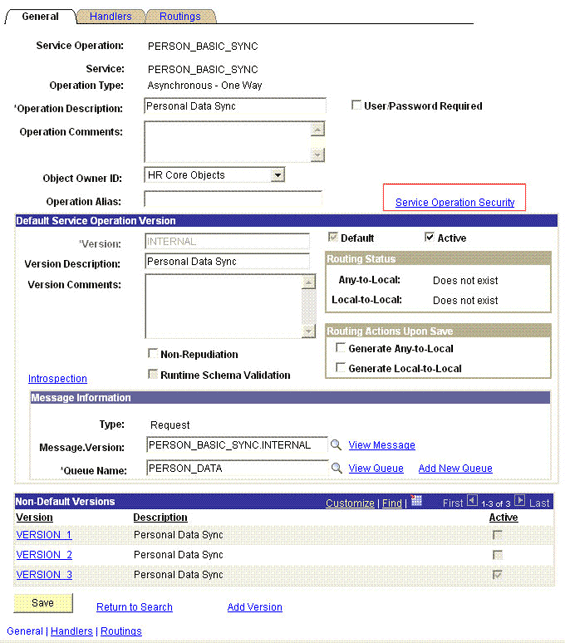
Search for an open the PERSON_BASIC_SYNC service operation.
-
On the General tab, click the Service Operation Security link.
The link is shown in the following screenshot:
-
Attach the OIMER permission list to the PERSON_BASIC_SYNC service operation. This list is created in Step 3 of the preinstallation procedure discussed in Creating a Permission List.
To attach the permission list:
Note:
This procedure describes how to grant access to the OIMER permission list. The OIMER permission list is used as an example. But, to implement this procedure you must use the permission list (attached through a role) to the user profile that has the privilege to modify personal data in the target system.
-
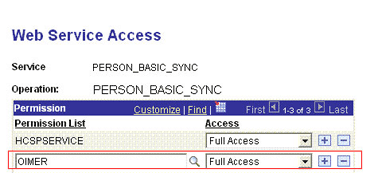
Click the plus sign (+) to add a row for the Permission List field.
-
In the Permission List field, enter
OIMERand then click the Look up Permission List icon.The OIMER permission list appears.
-
From the Access list, select Full Access.
The following screenshot displays the permission list with Full Access:
-
Click Save.
-
Click Return to Search.
-
-
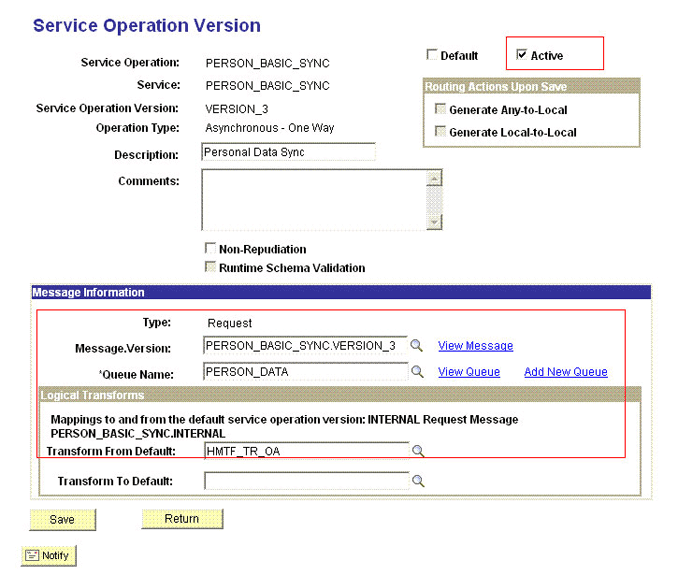
In the Non-Default Version region, click the VERSION_3 link to view the details.
Note:
Skip this step for version type INTERNAL.
-
Click Active.
-
Enter
HMTF_TR_OAin the Transform From Default field.Note:
If the Transform From Default field is not available in the region, you can ignore this step.
The following screenshot displays the preceding steps:
-
Click Save, and then click Return.
-
-
On the Handlers Tab, ensure that the Status is Active for the Type column that contains OnNotify PeopleCode.
-
Click Save.
2.2.2.2.2.4 Defining the Routing for the PERSON_BASIC_SYNC Service Operation
To define the routing for the PERSON_BASIC_SYNC service operation:
-
On the Routing tab, enter
PERSON_BASIC_SYNC_HR_OIMas the routing name and then click Add. -
On the Routing Definitions tab, enter the following:
Sender Node:
PSFT_HRNote:
The Sender Node is the default active local node. To locate the sender node:
-
Click the Look up icon.
-
Click Default to sort the results in descending order.
The default active local node should meet the following criteria:
Local Node: 1
Default Local Node: Y
Node Type: PIA
Only one node can meet all the above conditions at a time.
-
Select the node.
-
Click Save.
Receiver Node:
OIM_NODEThe following screenshot displays the Sender and Receiver nodes:
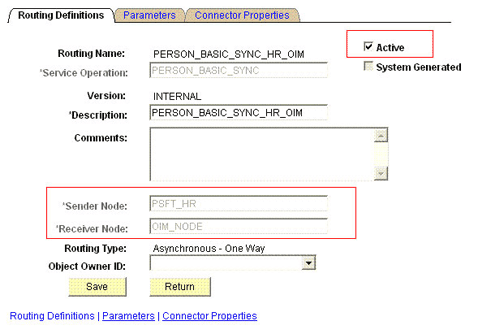
-
-
On the Parameters tab, enter the following information:
Note:
Skip this step for version type
INTERNAL.-
In the External Alias field, enter
PERSON_BASIC_SYNC.VERSION_3. -
In the Message.Ver into Transform 1 field, enter
PERSON_BASIC_SYNC.INTERNAL.Here, you specify the name of the default message that you must convert.
-
In the Transform Program 1 field, enter the name of the transformation program,
HMTF_TR_OA.Note:
For PeopleSoft HRMS 9.2 Image 4 or later, the value for the Transform program 1 field must be
HCM_MSG_XFRMinstead ofHMTF_TR_OA. -
In the Message.Ver out of Program field, enter
PERSON_BASIC_SYNC.VERSION_3.Here, you specify the name into which you want to transform the message mentioned in Step b.
The following screenshot displays the preceding steps:
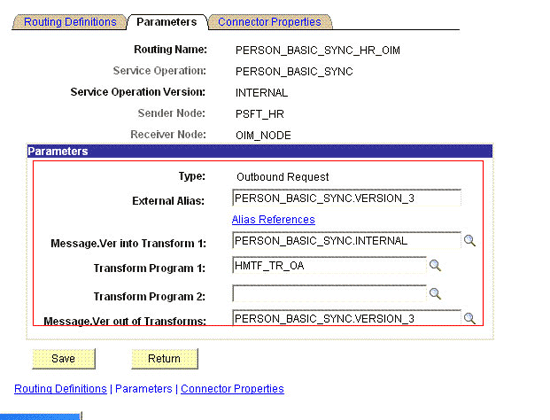
-
Click Save.
-
Click Return to go back to the Routings tab of the Service Operation, and verify whether your routing is active.
The following graphic displays the routing PERSON_BASIC_SYNC_HR_OIM and its transformation:
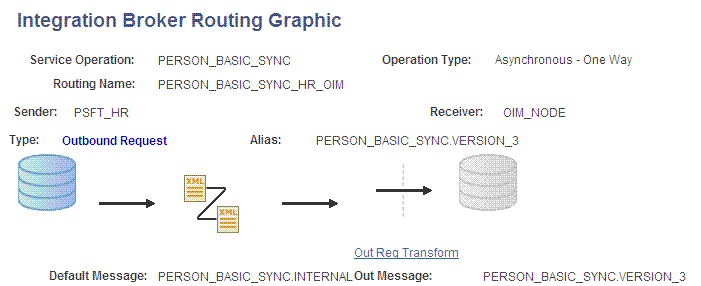
-
2.2.2.2.2.5 Displaying the EI Repository Folder
To display the EI Repository folder:
Note:
-
If you are using PeopleTools 8.53, then do not perform the procedure described in this section.
-
If you have performed this procedure as described in "Displaying the EI Repository Folder", then you can skip this section.
-
Perform this procedure using the PeopleSoft administrator credentials.
2.2.2.2.3 Configuring the WORKFORCE_SYNC Service Operation
This message contains the job-related details of a particular person. This information includes Employee ID and the information that is added or modified.
To configure the WORKFORCE_SYNC service operation, perform the following procedures:
Note:
The procedure remains the same for PeopleTools 8.49 with HRMS 9.0, PeopleTools 8.50 with HRMS 9.1, PeopleTools 8.53 through 8.57 with HRMS 9.2. The screenshots are taken on version PeopleTools 8.49.
For PeopleTools 8.57, configure WORKFORCE_SYNC with default version type INTERNAL. Skip the steps for other version types.
2.2.2.2.3.1 Activating the WORKFORCE_SYNC Service Operation
To activate the WORKFORCE_SYNC service operation:
Note:
If the message version is not the same as specified, then you can change the message version as described in Changing Default Message Versions.
2.2.2.2.3.2 Verifying the Queue Status for the WORKFORCE_SYNC Service Operation
To ensure that the status of the queue for the WORKFORCE_SYNC service operation is Run:
-
In PeopleSoft Internet Architecture, expand PeopleTools, Integration Broker, Integration Setup, and then click Queues.
-
Search for the PERSON_DATA queue.
-
In the Queue Status list, ensure that Run is selected.
Note:
If the queue status is not Run:
-
From the Queue Status list, select Run.
-
Click Save.
The queue status is shown in the following screenshot:

-
-
Click Return to Search.
2.2.2.2.3.3 Setting Up the Security for the WORKFORCE_SYNC Service Operation
To set up the security for the WORKFORCE_SYNC service operation:
-
In PeopleSoft Internet Architecture, expand PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
-
Search for an open the WORKFORCE_SYNC service operation.
-
On the General tab, click Service Operation Security link.
The following screenshot displays the link:
-
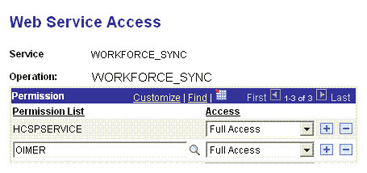
Attach the OIMER permission list to the WORKFORCE_SYNC service operation. This list is created in Step 3 of the preinstallation procedure discussed in Creating a Permission List.
To attach the permission list:
Note:
This procedure describes how to grant access to the OIMER permission list. The OIMER permission list is used as an example. But, to implement this procedure you must use the permission list (attached through a role) to the user profile that has the privilege to modify job data in the target system.
-
Click the plus sign (+) to add a row to the Permission List field.
-
In the Permission List field, enter
OIMERand then click the Look up Permission List icon.The OIMER permission list appears.
-
From the Access list, select Full Access.
The following screenshot displays the permission list with Full Access:
-
Click Save.
-
Click Return to Search.
-
2.2.2.2.3.4 Defining the Routing for the WORKFORCE_SYNC Service Operation
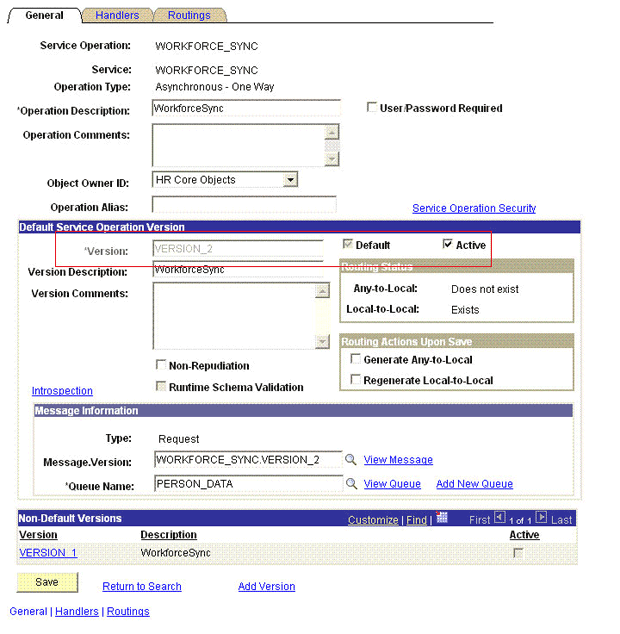
To define the routing for the WORKFORCE_SYNC service operation:
-
On the Routing tab, enter
WORKFORCE_SYNC_HR_OIMas the routing name and then click Add. -
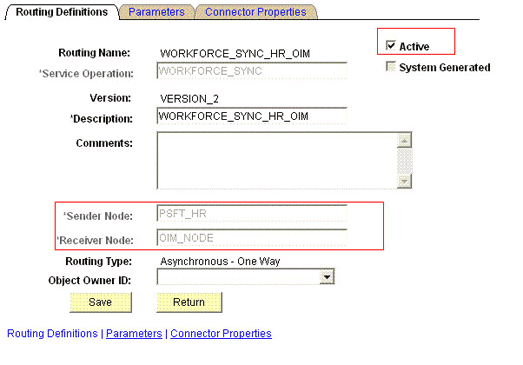
On the Routing Definitions tab, enter the following:
Sender Node:
PSFT_HRNote:
The Sender Node is the default active local node. To locate the sender node:
-
Click the Look up icon.
-
Click Default to sort the results in descending order.
The default active local node should meet the following criteria:
Local Node: 1
Default Local Node: Y
Node Type: PIA
Only one node can meet all the above conditions at a time.
-
Select the node.
-
Click Save.
Receiver Node:
OIM_NODEThe following screenshot displays the Sender and Receiver nodes:
-
-
Click Save.
-
Click Return to go back to the Routings tab of the Service Operation, and verify whether your routing is active.
2.2.2.2.3.5 Displaying the EI Repository Folder
To display the EI Repository folder:
Note:
-
If you are using PeopleTools 8.53, then do not perform the procedure described in this section.
-
If you have performed this procedure as described in "Displaying the EI Repository Folder", then you can skip this section.
-
Perform this procedure using the PeopleSoft administrator credentials.
2.2.2.2.4 Preventing Transmission of Unwanted Fields During Incremental Reconciliation
By default, Peoplesoft messages contain fields that are not needed in Oracle Identity Manager. If there is a strong use case that these fields should not be published to Oracle Identity Manager, then do the following:
-
Locate if there are any local-to-local or local-to-third party PeopleSoft active routings for the service operations using the message under study.
-
If none, then you can safely remove the unwanted fields at message level. See below for more information on removing unwanted fields at the message level.
-
If active routings exist, analyze the subscription or handler code of the routing to determine the fields they are utilizing and the ones not needed in Oracle Identity Manager. If so, remove the unwanted fields at message level. See below for more information on removing unwanted fields at the message level.
-
Lastly, if there are active routings that use these sensitive fields that you do not want to transmit to Oracle Identity Manager, then you need to write a transformation.
For more information about implementing transformation, refer to Chapter 21 of Integration Broker PeopleBook on Oracle Technology Network at the following location
http://download.oracle.com/docs/cd/E13292_01/pt849pbr0/eng/psbooks/tibr/book.htmIn addition, refer to Chapter 43 of PeopleCode API Reference PeopleBook on Oracle Technology Network at the following location
http://download.oracle.com/docs/cd/E13292_01/pt849pbr0/eng/psbooks/tpcr/book.htm
-
-
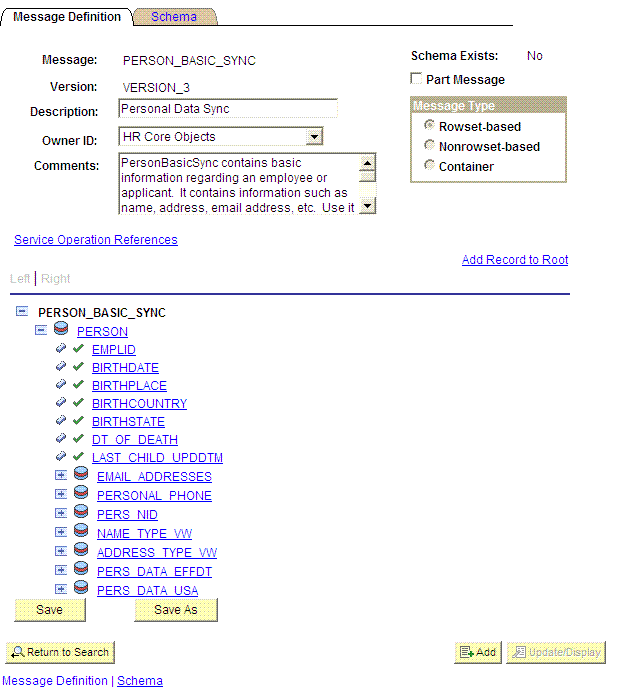
Remove unwanted fields at the message level. To do so:
-
Expand PeopleTools, Integration Broker, Integration Setup, and then click Messages.
-
Search for and open the desired message, for example, PERSON_BASIC_SYNC.VERSION_3 used for incremental reconciliation.
-
Expand the message.
-
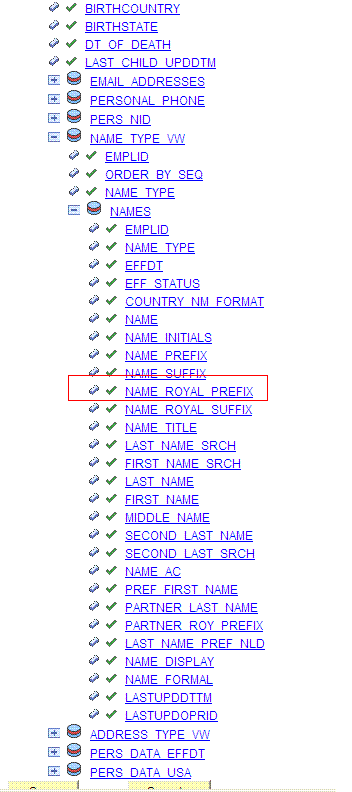
Navigate to the field that you do not want to transmit to Oracle Identity Manager, for example, NAME_ROYAL_PREFIX.
-
Click the field and clear the Include check box.
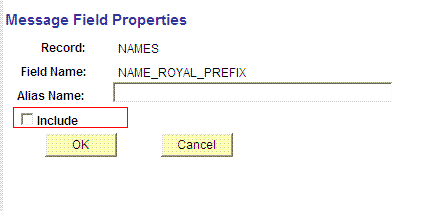
-
Click OK, return and save the message.
-
2.3 Postinstallation
Postinstallation information is divided across the following sections:
2.3.1 Configuring Oracle Identity Manager
Note:
In an Oracle Identity Manager cluster, you must perform this step on each node of the cluster.
2.3.1.1 Enabling Logging
This section contains the following topics:
2.3.1.1.1 Log Levels and Message Types
Oracle Identity Manager uses Oracle Java Diagnostic Logging (OJDL) for logging. OJDL is based on java.util.logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that may allow Oracle Identity Manager to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These message types are mapped to ODL message type and level combinations as shown in Table 2-4.
Table 2-4 Log Levels and ODL Message Type:Level Combinations
| Java Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
2.3.1.1.2 Enabling Logging on Oracle WebLogic Server
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SEVER are the domain name and server name specified during the installation of Oracle Identity Manager.
To enable logging on Oracle WebLogic Server:
-
Edit the logging.xml file as follows:
-
Add the following blocks in the file:
<log_handler name='psft-er-handler' level='[LOG_LEVEL]' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='[FILE_NAME]'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="ORACLE.IAM.CONNECTORS.PSFT" level="[LOG_LEVEL]" useParentHandlers="false"> <handler name="psft-er-handler"/> <handler name="console-handler"/> </logger><logger name="ORACLE.IAM.CONNECTORS.PSFT.HRMS" level="[LOG_LEVEL]" useParentHandlers="false"> <handler name="psft-er-handler"/> <handler name="console-handler"/> </logger> -
Replace all occurrences of [LOG_LEVEL] with the ODL message type and level combination that you require. Table 2-4 lists the supported message type and level combinations.
Similarly, replace [FILE_NAME] with the full path and name of the log file in which you want log messages to be recorded.
The following blocks show sample values for [LOG_LEVEL] and [FILE_NAME]:
<log_handler name='psft-er-handler' level='NOTIFICATION:1' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='F:\MyMachine\middleware\user_projects\domains\base_domain1\servers\oim_server1\logs\oim_server1-diagnostic-1.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="ORACLE.IAM.CONNECTORS.PSFT" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="psft-er-handler"/> <handler name="console-handler"/> </logger><logger name="ORACLE.IAM.CONNECTORS.PSFT.HRMS" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="psft-er-handler"/> <handler name="console-handler"/> </logger>With these sample values, when you use Oracle Identity Manager, all messages generated for this connector that are of a log level equal to or higher than the NOTIFICATION:1 level are recorded in the specified file.
Note:
The logging level for console-handler must be as fine as the level set in the loggers.For example, if the
NOTIFICATION:1level is specified in theORACLE.IAM.CONNECTORS.PSFTlogger, and the console-handler hasERROR:1level, then only logs atERROR:1or coarser levels would be available.
-
-
Save and close the file.
-
Set the following environment variable to redirect the server logs to a file:
-
For Microsoft Windows:
set WLS_REDIRECT_LOG=FILENAME
-
For UNIX:
export WLS_REDIRECT_LOG=FILENAME
Replace FILENAME with the actual name of the file to which you want to redirect the output.
-
-
Restart the application server.
2.3.1.2 Setting Up the Lookup.PSFT.HRMS.ExclusionList Lookup Definition
In the Lookup.PSFT.HRMS.ExclusionList lookup definition, enter the user IDs of target system accounts for which you do not want to perform reconciliation. See Lookup.PSFT.HRMS.ExclusionList for more information about this lookup definition.
2.3.1.3 Setting Up the Lookup.PSFT.HRMS.Configuration Lookup Definition
Every standard PeopleSoft message has a message-specific configuration defined in the Lookup.PSFT.HRMS.Configuration lookup definition. See Lookup.PSFT.HRMS.Configuration for more information about this lookup definition.
For example, the mapping for the PERSON_BASIC_SYNC message in this lookup definition is defined as follows:
Code Key: PERSON_BASIC_SYNC
Decode: Lookup.PSFT.Message.PersonBasicSync.Configuration
You can configure the message names, such as PERSON_BASIC_SYNC, WORKFORCE_SYNC, PERSON_BASIC_FULLSYNC, and WORKFORCE_FULLSYNC defined in this lookup definition.
Consider a scenario in which the target system sends the PERSON_BASIC_SYNC.VERSION_3 message. You must change the Code Key value in this lookup definition to implement the message sent by the target system.
To modify or set the Code Key value:
2.3.1.4 Configuring SSL
The following sections describe the procedure to configure SSL connectivity between Oracle Identity Manager and the target system:
2.3.1.4.1 Configuring SSL on IBM WebSphere Application Server
You can configure SSL connectivity on IBM WebSphere Application Server with either a self-signed certificate or a CA certificate. Perform the procedure described in one of the following sections:
2.3.1.4.1.1 Configuring SSL on IBM WebSphere Application Server with a Self-Signed Certificate
To configure SSL connectivity between Oracle Identity Manager on IBM WebSphere Application Server and the target system with a self-signed certificate, you must perform the following tasks:
2.3.1.4.1.2 Configuring SSL on IBM WebSphere Application Server with a CA Certificate
To configure SSL connectivity between Oracle Identity Manager on IBM WebSphere Application Server and the target system with a CA certificate:
-
Log in to the WebSphere Integrated Solutions Console. The URL may be similar to the following:
https://localhost:9043/ibm/console/logon.jsp
-
Click Security, SSL certificate and key management, Related items, Key stores and certificates, NodeDefaultKeyStore.
-
On the Additional Properties tab, click Personal certificate requests.
-
Click New.
-
In the File for certificate request field, enter the full path where the certificate request is to be stored, and a file name. For example:
c:\servercertreq.arm(for a computer running on Microsoft Windows). -
In the Key label field, enter an alias name. You specify the alias name to identify the certificate request in the keystore.
-
In the CN field, enter a value for common name. The common name must be the fully-qualified DNS host name or the name of the computer. The CN of the certificate must match the domain name of your community. For example, if the name of your domain is us.example.com, then the CN of the SSL certificate that you create for your community must also be us.example.com.
-
In the Organization field, enter an organization name.
-
In the Organization unit field, specify the organization unit.
-
In the Locality field, enter the locality.
-
In the State or Province field, enter the state.
-
In the Zip Code field, enter the zip code.
-
From the Country or region list, select the country code.
-
Click Apply and then Save. The certificate request is created in the specified file location in the keystore. This request functions as a temporary placeholder for the signed certificate until you manually receive the certificate in the keystore.
Note:
Keystore tools such as iKeyman and keyTool cannot receive signed certificates that are generated by certificate requests from IBM WebSphere Application Server. Similarly, IBM WebSphere Application Server cannot accept certificates that are generated by certificate requests from other keystore utilities.
-
Send the certification request arm file to a CA for signing.
-
Create a backup of your keystore file. You must create this backup before receiving the CA-signed certificate into the keystore. The default password for the keystore is WebAS. The Integrated Solutions Console contains the path information for the location of the keystore. The path to the NodeDefaultKeyStore is listed in the Integrated Solutions Console as:
was_profile_root\config\cells\cell_name\nodes\node_name\key.p12Now you can receive the CA-signed certificate into the keystore to complete the process of generating a signed certificate for IBM WebSphere Application Server.
-
To receive a signed certificate issued by a CA, perform the following tasks:
-
In the WebSphere Integrated Solutions Console, click Security, SSL certificate and key management, Related items, Key stores and certificates, NodeDefaultKeyStore, and then click Personal Certificates.
-
Click Receive a certificate from a certificate authority.
-
Enter the full path and name of the certificate file.
-
Select the default data type from the list.
-
Click Apply and then Save.
-
The keystore contains a new personal certificate that is issued by a CA. The SSL configuration is ready to use the new CA-signed personal certificate.
2.3.1.4.2 Configuring SSL on Oracle WebLogic Server
You can configure SSL connectivity on Oracle WebLogic Server with either a self-signed certificate or a CA certificate. Perform the procedure described in one of the following sections:
See Also:
2.3.1.4.2.1 Configuring SSL on Oracle WebLogic Server with a Self-Signed Certificate
To configure SSL connectivity between Oracle Identity Manager on Oracle WebLogic Server and the target system with a self-signed certificate, you must perform the following tasks:
To generate the keystore:
-
Run the following command:
keytool -genkey -keystore ABSOLUTE_KEYSTORE_PATH -alias ALIAS_NAME -keyalg KEY_ALGORITHM -storepass KEYSTORE_PASSWORD -keypass PRIVATE_KEY_PASSWORD
For example:
keytool -genkey -keystore c:\temp\keys\keystore.jks -alias example088196 -keyalg RSA -storepass example1234 -keypass example1234
Note:
- The keystore password and the private key password must be the same.
- Typically, the alias is the name or the IP address of the computer on which you are configuring SSL.
- The alias used in the various commands of this procedure must be the same.
-
When prompted, enter information about the certificate. This information is displayed to persons attempting to access a secure page in the application. This is illustrated in the following example:
keytool -genkey -keystore c:\temp\keys\keystore.jks -alias example088196 -keyalg RSA -storepass example1234 -keypass example1234 What is your first and last name? [Unknown]: Must be the name or IP address of the computer What is the name of your organizational unit? [Unknown]: example What is the name of your organization? [Unknown]: example What is the name of your City or Locality? [Unknown]: New York What is the name of your State or Province? [Unknown]: New York What is the two-letter country code for this unit? [Unknown]: US Is <CN=Name or IP address of the computer, OU=example, O=example, L=New York, ST=New York, C=US> correct? [no]: yes
When you enter yes in the last line of the preceding example, the keystore.jks file is created in the c:\temp\keys\directory.
-
Export the keystore to a certificate file by running the following command:
keytool -export -alias ALIAS_NAME -keystore ABSOLUTE_KEYSTORE_PATH -file CERTIFICATE_FILE_ABSOLUTE_PATH
For example:
keytool -export -alias example088196 -keystore c:\temp\keys\keystore.jks -file c:\temp\keys\keystore.cert
-
When prompted for the private key password, enter the same password used for the keystore, for example,
example1234. -
Import the keystore by running the following command:
keytool -import -alias ALIAS_NAME -keystore NEW_KEYSTORE_ABSOLUTE_PATH -file CERTIFICATE_FILE_ABSOLUTE_PATH
For example:
keytool -import -alias example088196 -keystore c:\temp\keys\new.jks -file c:\temp\keys\keystore.cert
When you run this command, it prompts for the keystore password, as shown in the following example:
Enter keystore password: example1234 [Enter] Trust this certificate? [no]: yes [Enter] Certificate was added to keystore
In this example, the instances when you can press Enter are shown in bold.
After generating and importing the keystore, start Oracle WebLogic Server. To configure Oracle WebLogic Server:
-
Log in to the Oracle WebLogic Server console at
http://localhost:7001/consoleand perform the following:-
Expand the servers node and select the oim server instance.
-
Select the General tab.
-
Select the SSL Listen Port Enabled option.
-
Ensure that a valid port is specified in the SSL Listen Port field. The default port is 7002.
-
Click Apply to save your changes.
-
-
Click the Keystore & SSL tab, and then click Change.
-
From the Keystores list, select Custom identity And Java Standard Trust, and then click Continue.
-
Configure the keystore properties. To do so:
-
In the Custom Identity Key Store File Name column, specify the full path of the keystore generated in Step 1 of generating the keystore, for example,
c:\temp\keys\keystore.jks. In the Custom Identity Key Store Type column, specify the type of keystore, for example,JKS. In the Custom Identity Key Store Pass Phrase and Confirm Custom Identity Key Store Pass Phrase columns, specify the keystore password. -
Provide the Java standard trust keystore pass phrase and the Confirm Java standard trust keystore pass phrase. The default password is
changeit, unless you change the password. -
Click Continue.
-
-
Specify the private key alias, pass phrase and the confirm pass phrase as the keystore password. Click Continue.
-
Click Finish.
-
Restart Oracle WebLogic Server. If the server starts successfully with the SSL configuration, then lines similar to the following are recorded in the startup log:
<Apr 21, 2008 2:35:43 PM GMT+05:30> <Notice> <WebLogicServer> <BEA-000355> <Thread "ListenThread.Default" listening on port 7001, ip address *.*> <Apr 21, 2008 2:35:43 PM GMT+05:30> <Notice> <WebLogicServer> <BEA-000355> <Thread "SSLListenThread.Default" listening on port 7002, ip address *.*>
Note:
7002 is the default SSL port for Oracle WebLogic Server.
2.3.1.4.2.2 Configuring SSL on Oracle WebLogic Server with a CA Certificate
To configure SSL connectivity between Oracle Identity Manager on Oracle WebLogic Server and the target system with a CA certificate, you must perform the following tasks:
Note:
Although this is an optional step in the deployment procedure, Oracle strongly recommends that you configure SSL communication between the target system and Oracle Identity Manager.
The connector requires Certificate Services to be running on the host computer. To generate the keystore:
-
Run the following command:
keytool -genkey -keystore ABSOLUTE_KEYSTORE_PATH -alias ALIAS_NAME -keyalg KEY_ALGORITHM -storepass KEYSTORE_PASSWORD -keypass PRIVATE_KEY_PASSWORD
For example:
keytool -genkey -keystore c:\temp\keys\keystore.jks -alias example088196 -keyalg RSA -storepass example1234 -keypass example1234
Note:
The keystore password and the private key password must be the same.
Typically, the alias name is the name or the IP address of the computer on which you are configuring SSL.
-
When prompted, enter the information about the certificate. This information is displayed to persons attempting to access a secure page in the application. This is illustrated in the following example:
keytool -genkey -keystore c:\temp\keys\keystore.jks -alias example088196 -keyalg RSA -storepass example1234 -keypass example1234 What is your first and last name? [Unknown]: Must be the name or IP address of the computer What is the name of your organizational unit? [Unknown]: example What is the name of your organization? [Unknown]: example What is the name of your City or Locality? [Unknown]: New York What is the name of your State or Province? [Unknown]: New York What is the two-letter country code for this unit? [Unknown]: US Is <CN=Name or IP address of the computer, OU=example, O=example, L=New York, ST=New York, C=US> correct? [no]: yes
When you enter yes in the last line of the preceding example, the keystore.jks file is created in the c:\temp\keys\directory.
-
Generate the certificate signing request by running the following command:
keytool -certreq -keystore ABSOLUTE_KEYSTORE_PATH -alias ALIAS_NAME -keyalg KEY_ALGORITHM -file CERTIFICATE_FILE_ABSOLUTE_PATH
For example:
keytool -certreq -keystore c:\temp\keys\keystore.jks -alias example088196 -keyalg RSA -file c:\temp\keys\keystore.cert
When prompted for the keystore password, enter the same password used for the keystore in Step 1, for example
example1234. This stores a certificate request in the file that you specified in the preceding command. -
Get the certificate from a CA by using the certificate request generated in the previous step and store the certificate in a file.
-
Export the keystore generated in Step 1 to a new certificate file, for example, myCert.cer, by running the following command:
keytool –export –keystore ABSOLUTE_KEYSTORE_PATH -alias alias-name specified in step 1 -file CERTIFICATE_FILE_ABSOLUTE_PATH
For example:
keytool –export –keystore c:\temp\keys\keystore.jks -alias example088196 -file c:\temp\keys\myCert.cer
-
Import the CA certificate to a new keystore by running the following command:
keytool -import -alias ALIAS_NAME -file CERTIFICATE_FILE_ABSOLUTE_PATH -keystore NEW_KEYSTORE_ABSOLUTE_PATH -storepass KEYSTORE_PASSWORD generated in Step 1
For example:
keytool -import -alias example088196 -file c:\temp\keys\rootCert.cert -keystore c:\temp\keys\rootkeystore.jks
When you run this command, it prompts for the keystore password, as shown:
Enter keystore password: example1234 [Enter] Trust this certificate? [no]: yes [Enter] Certificate was added to keystore
In this example, the instances when you can press Enter are shown in bold.
After creating and importing the keystore to the system, start Oracle WebLogic Server. To configure Oracle WebLogic Server:
-
Log in to the Oracle WebLogic Server console ((http://localhost:7001/console) and perform the following:
-
Expand the server node and select the server instance.
-
Select the General tab.
-
Select the SSL Port Enabled option.
-
Ensure that a valid port is specified in the SSL Listen Port field. The default port is 7002.
-
Click Apply to save your changes.
-
-
Click the Keystore & SSL tab, and click the Change link.
-
From the Keystores list, select Custom Identity And Custom Trust, and then click Continue.
-
Configure the keystore properties. To do so:
-
In the Custom Identity Key Store File Name column, specify the full path of the keystore generated in Step 1 of generating the keystore, for example,
c:\temp\keys\keystore.jks. In the Custom Identity Key Store Type column, specify the type of keystore, for example,JKS. In the Custom Identity Key Store Pass Phrase and Confirm Custom Identity Key Store Pass Phrase columns, specify the keystore password. -
In the Custom Trust and Custom Trust Key Store File Name column, specify the full path of the keystore generated in Step 1 of generating the keystore, for example,
c:\temp\keys\rootkeystore.jks. In the Custom Trust Key Store Type column, specify the type of keystore, for example,JKS. In the Custom Trust Key Store Pass Phrase and Confirm Custom Trust Key Store Pass Phrase columns, specify the keystore password. -
Provide the Java standard trust keystore password. The default password is
changeit, unless you change the password. -
Click Continue.
-
-
Specify the alias name and private key password. Click Continue.
-
Click Finish.
-
Restart Oracle WebLogic Server. If the server starts successfully with the SSL configuration, then lines similar to the following are recorded in the startup log:
<Apr 21, 2008 2:35:43 PM GMT+05:30> <Notice> <WebLogicServer> <BEA-000355> <Thread "ListenThread.Default" listening on port 7001, ip address *.*> <Apr 21, 2008 2:35:43 PM GMT+05:30> <Notice> <WebLogicServer> <BEA-000355> <Thread "SSLListenThread.Default" listening on port 7002, ip address *.*>
Note:
7002 is the default SSL port for Oracle WebLogic Server.
2.3.1.5 Creating an Authorization Policy for Job Code
Note:
Perform this procedure only if you are using Oracle Identity Manager release 11g R1 (11.1.1.x). You must configure the authorization policy for Supervisor ID if you want to use PeopleSoft HRMS Manager Reconciliation scheduled task.
The following instructions are specific to individual steps of the procedure described in the "Creating an Authorization Policy for User Management" section of that chapter:
-
When you reach Step 3, then:
In the Policy Name field, enter
Job Code Authorization Policy. -
When you reach Step 4, then:
In the Description field, enter
Job Code Authorization Policy. -
When you reach Step 7, then:
In the Permissions table, select the following check boxes in the Enable column:
-
Modify User Profile
-
Search User
-
View User Details
Click Edit Attributes.
On the Attribute Settings page, clear all the check boxes and select Job Code.
-
-
When you reach Step 14 c, then:
From the Available Roles list, select System Administrator, and then click the Move button to move the selected role to the Organizations to Add list.
Note:
Perform the preceding steps to create an authorization policy for any user-defined field that you want to add, for example Supervisor ID, Department, and so on.
2.3.1.6 Displaying UDFs in Oracle Identity Manager 11.1.2.x or Later
In Oracle Identity Manager release 11.1.2.x or later, some user attributes (UDFs) such as Department, Job Code, and Supervisor ID are not displayed after running the reconciliation for the WORKFORCE_FULLSYNC message. If you want to display these attributes as form fields in the Oracle Identity Manager user interface, then you must customize the associated pages on the interface to add the custom form fields. To do so:
2.4 Upgrading the Connector
You can upgrade the PeopleSoft Employee Reconciliation connector while in production, and with no downtime. Your customizations will remain intact and the upgrade should be transparent to your users. Form field names are preserved from the legacy connector.
To upgrade the PeopleSoft Employee Reconciliation connector from release 9.1.1.6 to this release of the connector, perform the following procedures:
See Also:
Upgrading Connectors in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed information of these steps
2.4.1 Prerequisites for Upgrading the Connector
Before you perform the upgrade procedures:
-
It is strongly recommended that you create a backup of the Oracle Identity Manager database. Refer to the database documentation for information about creating a backup.
-
As a best practice, first perform the upgrade procedure in a test environment.
2.4.2 Re-defining the Connector
The upgrade process of the connector must not include IT resource. Therefore, you must re-define the connector to exclude IT resource.
To re-define the connector to exclude IT resource:
-
Add the Peoplesoft HRMS resource. To do so:
-
Log in to the Administrative and User Console.
-
On the Welcome to Identity Manager Advanced Administration page, under the System Management section, click Manage Connector.
-
Click Define.
-
In Step 1 of the Connector Management Wizard, select Resource from the drop-down box and search for
Peoplesoft HRMS. -
In the Search Results region, select the Peoplesoft HRMS check box and click Select Children, as shown in the following screenshot.
-
In Step 2, in the Select Children region, ensure the Peoplesoft HRMS Person check box is selected. Click Select Dependencies, as shown in the following screenshot.
-
In Step 3, in the Select Dependencies region, ensure the Peoplesoft HRMS and the Peoplesoft HRMS Person check boxes are selected. Click Confirmation, as shown in the following screenshot.
-
In Step 4, click Add For Define, as shown in the following screenshot.
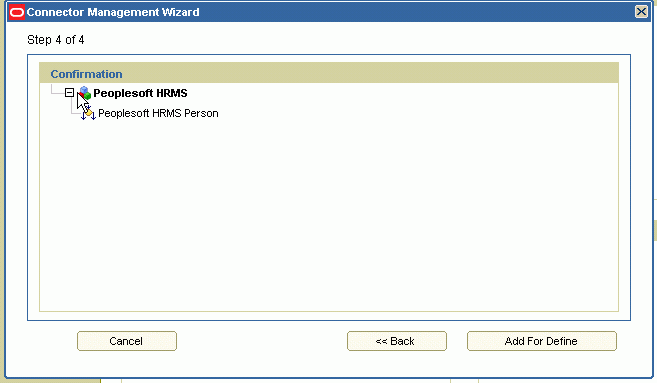
-
On the next page, select Add more (Go to Step 1) to add Peoplesoft HRMS scheduled tasks, and click OK, as shown in the following screenshot.
-
-
Add the Peoplesoft HRMS scheduled tasks. To do so:
-
In Step 1 of the Connector Management Wizard, select Scheduled Task from the drop-down box and search for the Peoplesoft HRMS tasks.
-
In the Search Results region, select the Peoplesoft HRMS Manager Reconciliation and the Peoplesoft HRMS Trusted Reconciliation check boxes. Then, click Select Children, as shown in the following screenshot.
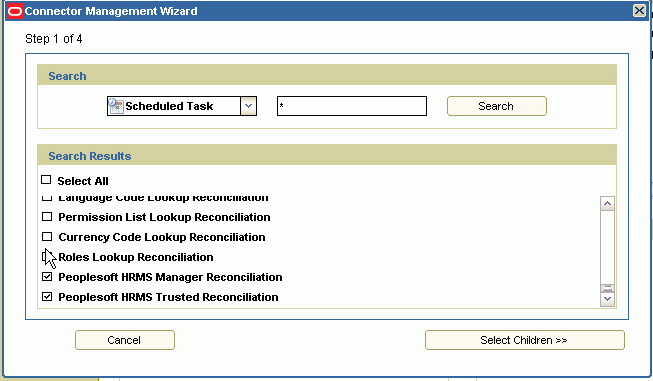
-
In Step 2, in the Select Children region, ensure the Peoplesoft HRMS scheduled tasks are selected, as shown in the following screenshot. Click Select Dependencies.
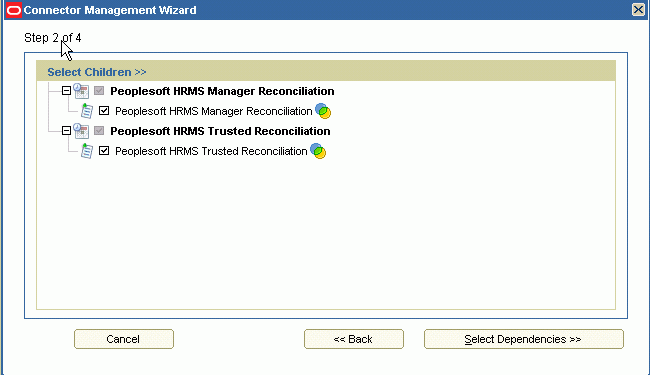
-
In Step 3, in the Select Dependencies region, ensure the Peoplesoft HRMS scheduled tasks are selected, as shown in the following screenshot. Click Confirmation.
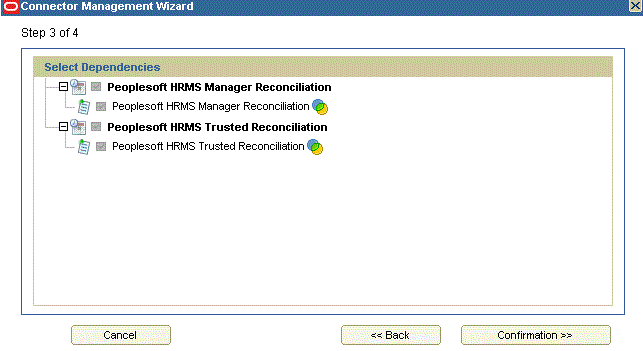
-
In Step 4, click Add For Define.
-
On the next page, select Exit wizard and show full selection, and click OK, as shown in the following screenshot.

-
-
On the Summary page, verify the objects added in the preceding steps, as shown in the following screenshot. Then, click Define.
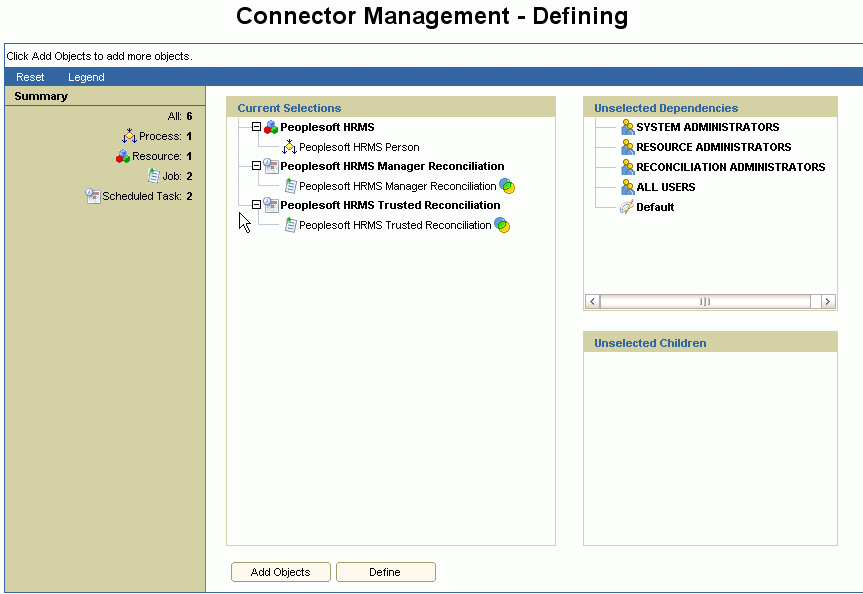
-
Select Peoplesoft Employee Reconciliation in the Connector Name drop-down box, and enter a new version in the Connector Release field, as shown in the following sample screenshot. Then, click Define.
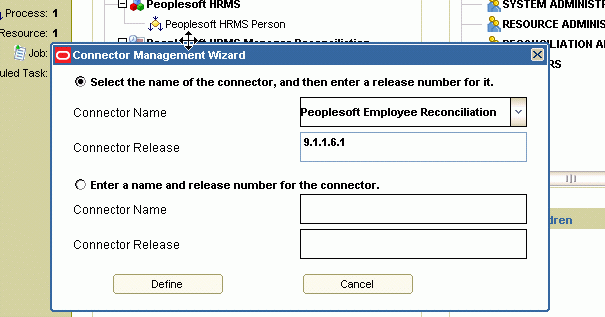
2.4.4 Upgrading the Connector Files and External Code Files
To upgrade the connector files and external code files:
2.4.5 Upgrading the PeopleSoft Listener
Note:
-
If you have already deployed a listener for the PeopleSoft User Management connector, then you can skip this procedure.
A single listener is sufficient for both the connectors. You can configure the nodes to point to the same listener with different IT resource names.
-
If you upgrade the connector, you must also upgrade the listener. Installing a new connector over a previously deployed listener creates discrepancies.
To upgrade the PeopleSoft listener:
- Remove the existing PeopleSoft listener by performing the procedure described in Removing the PeopleSoft Listener.
- Deploy the new PeopleSoft listener by performing the procedure described in Deploying the PeopleSoft Listener.
If there are any validation or transformation JARs, you must add the JARs to the deployable connector bundle JAR and re-deploy the listener. See Configuring Validation of Data During Reconciliation and Configuring Transformation of Data During Reconciliation for more information.
2.4.7 Updating the PeopleSoft Target System
The PeopleSoft Employee Reconciliation and PeopleSoft User Management connectors have different IT resources. Therefore, you must configure separate HTTP nodes for messages of the Employee Reconciliation and User Management connectors.
Even if an existing node is configured to the PeopleSoft listener on Oracle Identity Manager, a separate node is required for messages of the PeopleSoft Employee Reconciliation connector.
Configure a new node, for example, OIM_ER_NODE, and configure routings from the PERSON_BASIC_SYNC and WORKFORCE_SYNC service operations.
See Configuring the Target System for Full Reconciliation and Configuring the Target System for Full Reconciliation for more information.