9 Extending the Functionality of the Connector
This chapter describes procedures that you can perform to extend the functionality of the connector for addressing your specific business requirements.
Note:
From Oracle Identity Manager Release 11.1.2 onward, lookup queries are not supported. See Managing Lookups of Oracle Fusion Middleware Administering Oracle Identity Manager for information about managing lookups by using the Form Designer in Identity System Administration.
This chapter discusses the following sections:
9.1 Adding Custom Fields for Target Resource Reconciliation
Note:
This section describes an optional procedure. Perform this procedure only if you want to add custom fields for target resource reconciliation.
By default, the fields listed in Table 1-5 are mapped for reconciliation between Oracle Identity Manager and the target system. If required, you can map additional fields for user reconciliation.
To add a custom field for target resource reconciliation, perform the following procedures:
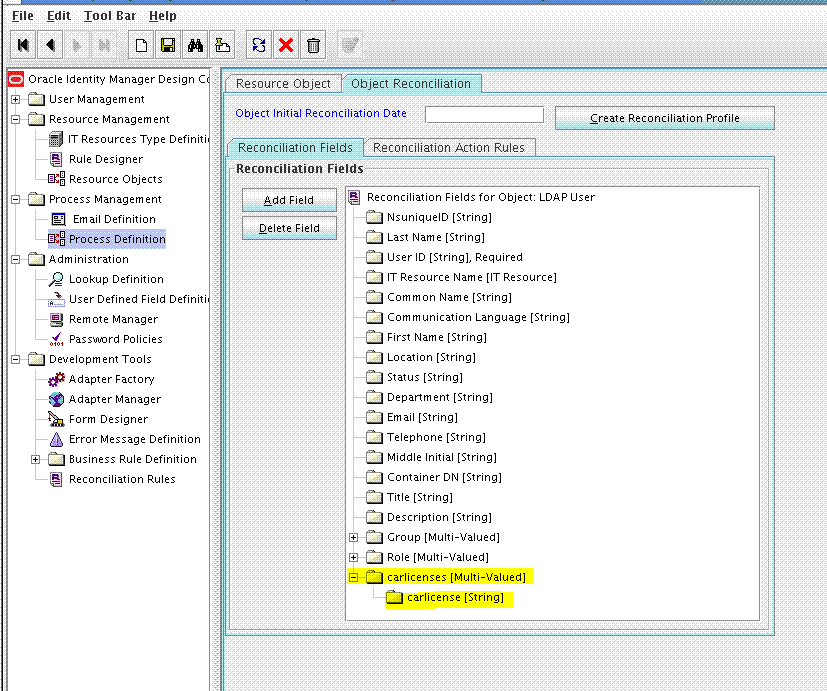
9.1.1 Adding the Custom Field to Resource Object Reconciliation Fields
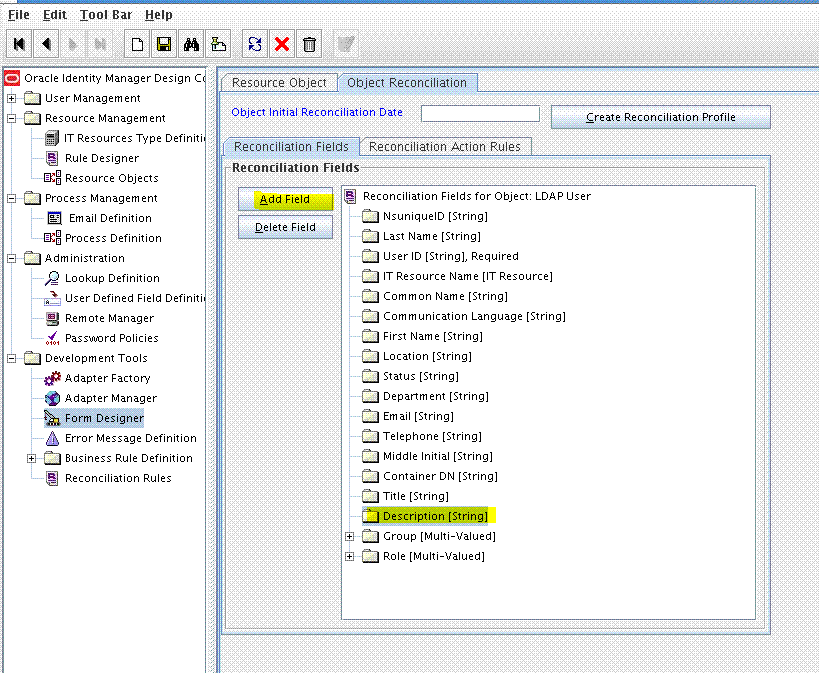
To add the custom field to the list of reconciliation fields in the resource object:
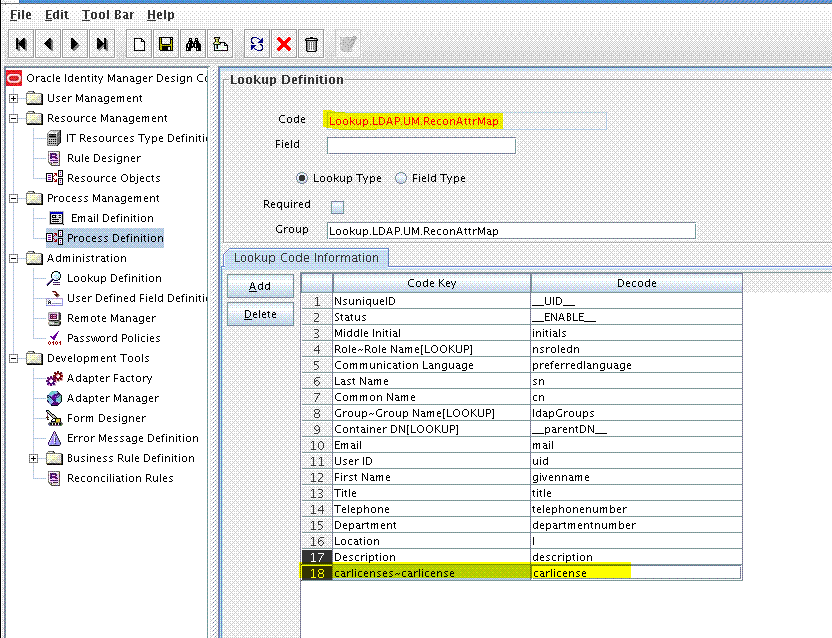
9.1.2 Creating an Entry for the Custom Field in the Lookup Definition for Reconciliation
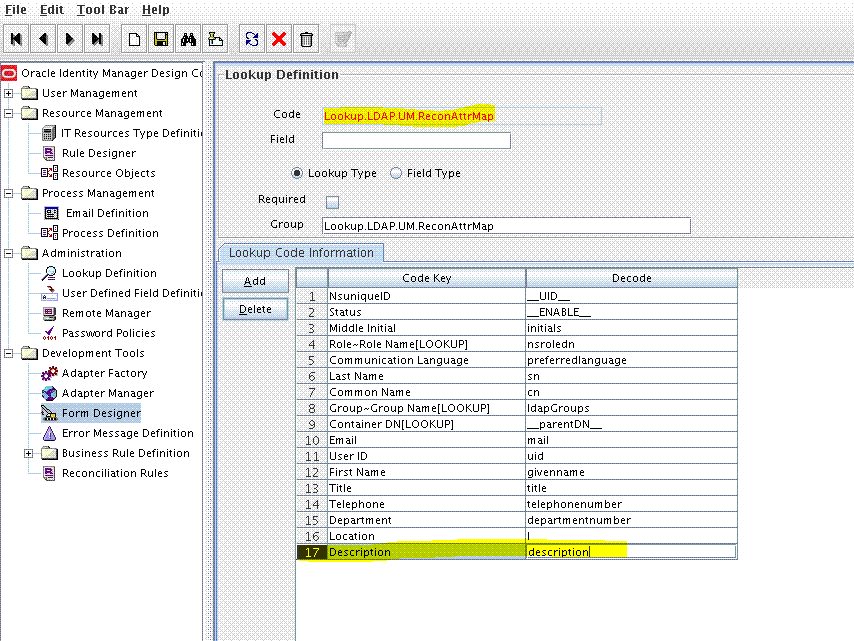
To create an entry for the field in the lookup definition for reconciliation:
9.1.4 Associating a New Form With the Application Instance
If you are using Oracle Identity Manager release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form as follows:
- Log in to Oracle Identity System Administration.
- Create and active a sandbox. See Creating and Activating a Sandbox for more information.
- Create a new UI form to view the newly added field along with the rest of the fields. See Creating a New UI Form for more information about creating a UI form.
- Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 5.c), and then save the application instance.
- Publish the sandbox. See Publishing a Sandbox for more information.
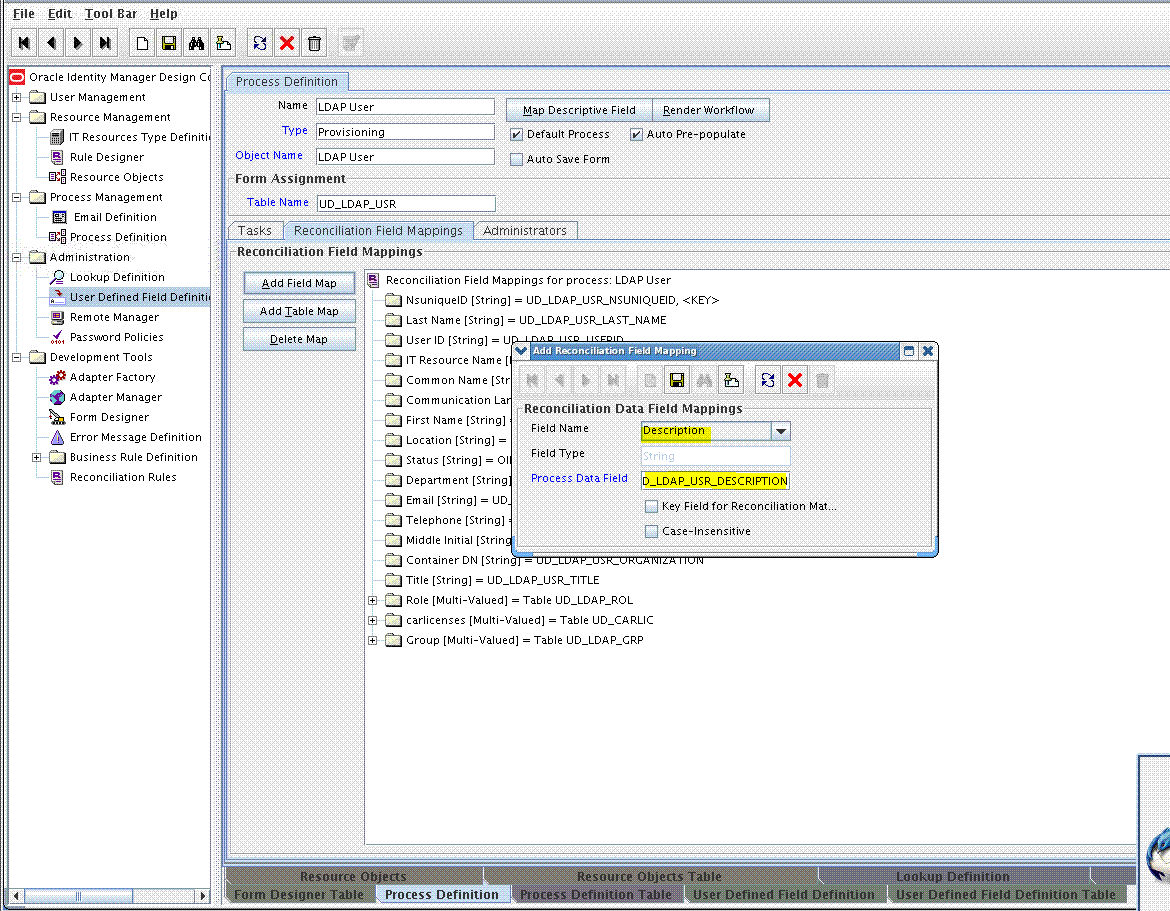
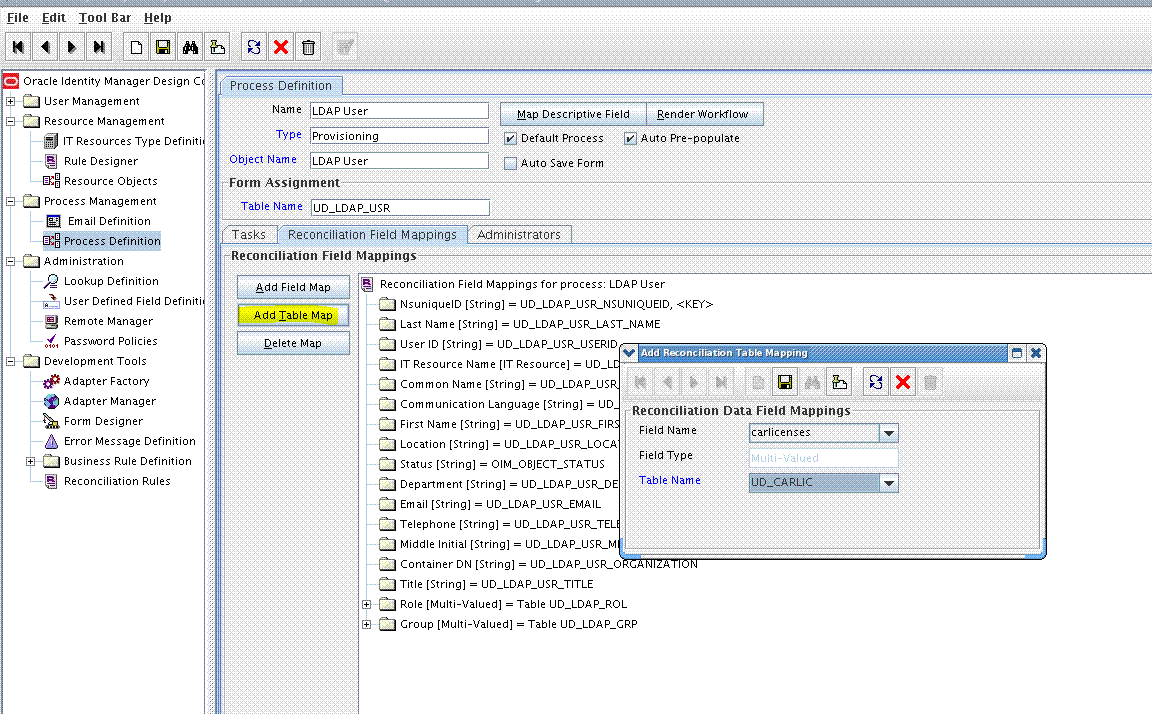
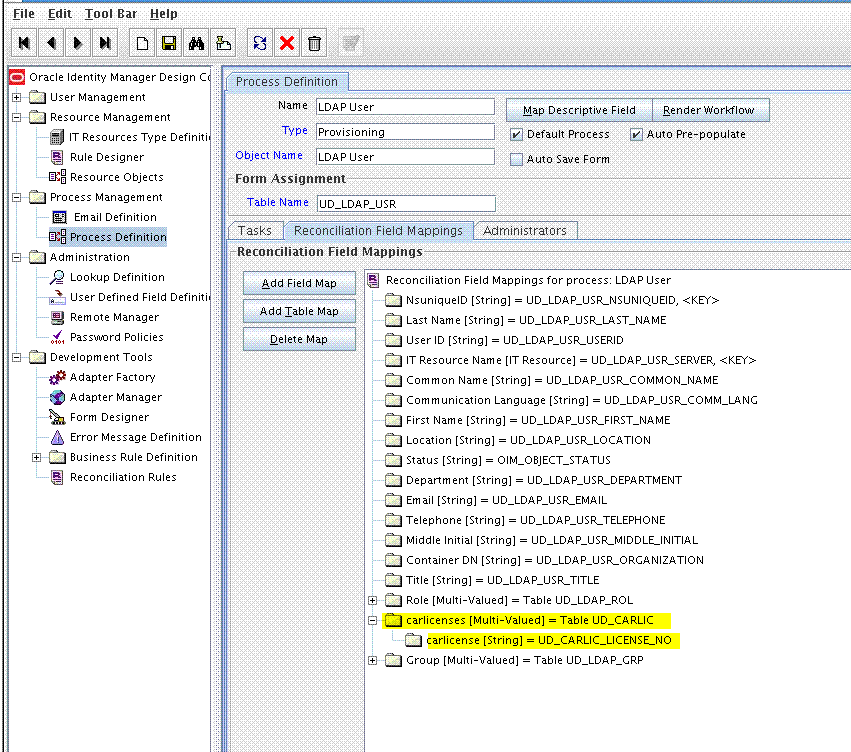
9.1.5 Creating a Reconciliation Field Mapping for the Custom Field in the Provisioning Process
Create a reconciliation field mapping for the custom field in the provisioning process as follows:
9.1.6 Creating the Reconciliation Profile
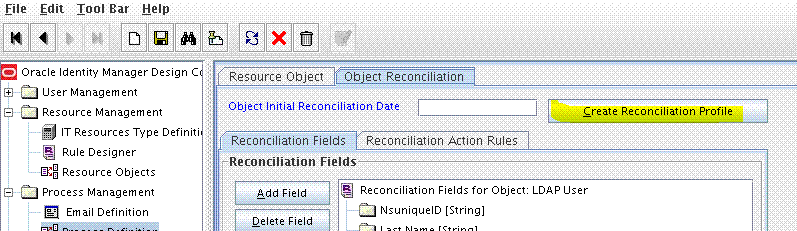
Create the Reconciliation Profile:
- Expand Resource Management and then double-click Resource Objects.
- Search for and open the LDAP User, OID User, or eDirectory User resource object.
- Click Create Reconciliation Profile. This copies changes made to the resource object into Oracle Identity Manager Meta Data Store (MDS).
9.2 Adding New Multivalued Fields for Target Resource Reconciliation
By default, the multivalued fields listed in the respective lookup definitions are mapped for reconciliation between Oracle Identity Manager and the target system. If required, you can add new multivalued fields for target resource reconciliation.
Note:
-
This section describes an optional procedure. Perform this procedure only if you want to add multivalued fields for target resource reconciliation.
-
You can apply this procedure to add either user, group, organizational unit, or role fields.
-
You must ensure that new fields you add for reconciliation contain only string-format data. Binary fields must not be brought into Oracle Identity Manager natively.
To add a new multivalued field for target resource reconciliation, perform the following procedures:
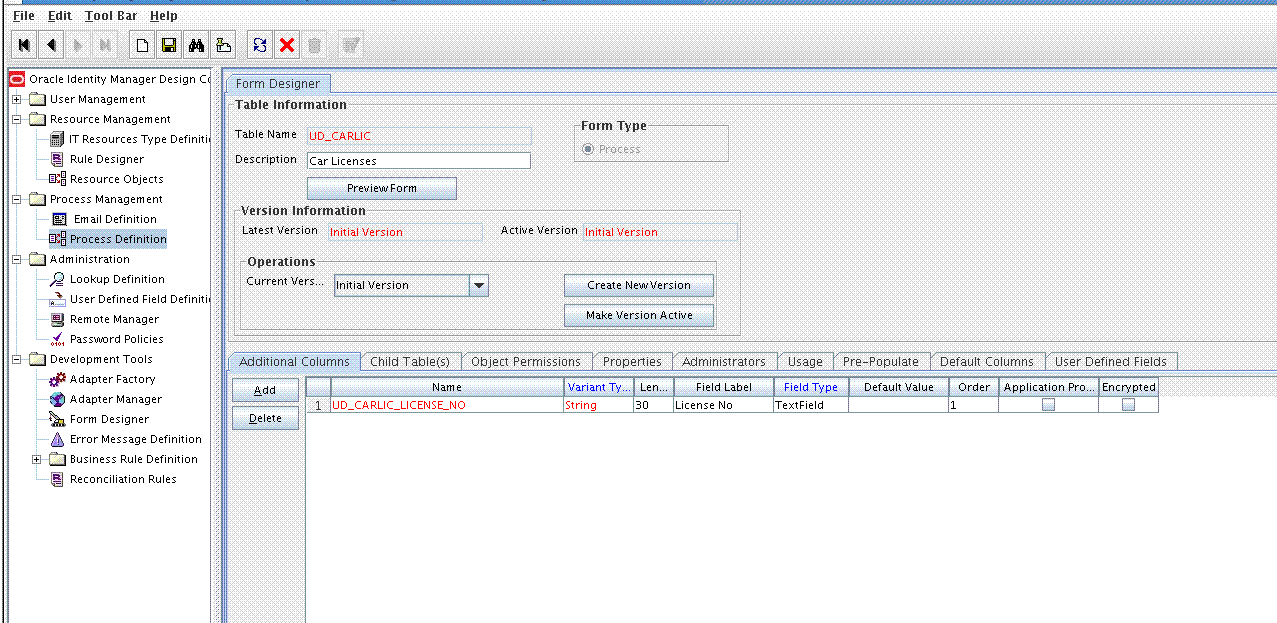
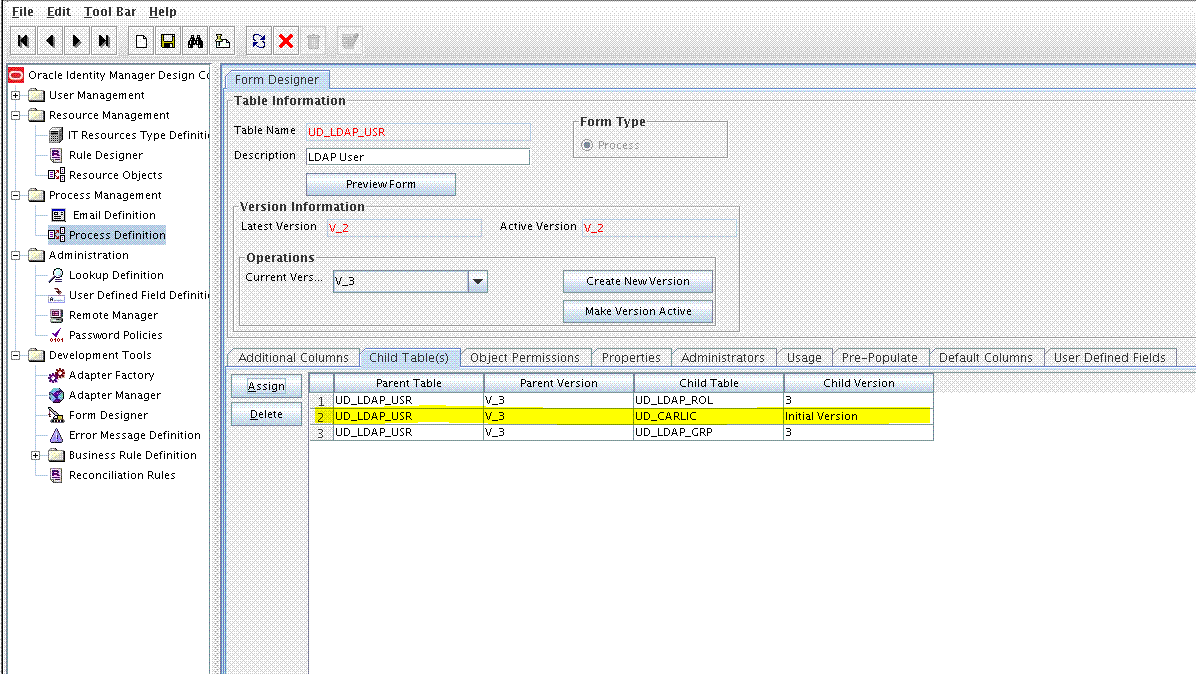
9.2.2 Adding the Form as a Child Form of the Process Form
Add the form created for the multivalued field as a child form of the process form as follows:
9.2.3 Associating a New Form With the Application Instance
If you are using Oracle Identity Manager release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form as follows:
- Log in to Oracle Identity System Administration.
- Create and active a sandbox. See Creating and Activating a Sandbox for more information.
- Create a new UI form to view the newly added field along with the rest of the fields. See Creating a New UI Form for more information about creating a UI form.
- Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 4.c), and then save the application instance.
- Publish the sandbox. See Publishing a Sandbox for more information.
9.2.4 Adding the New Multivalued Field to the Resource Object Reconciliation Fields
Add the new multivalued field to the list of reconciliation fields in the resource object as follows:
9.2.5 Creating an Entry for the Field in the Lookup Definition for Reconciliation
Create an entry for the field in the lookup definition for reconciliation as follows:
9.3 Adding Custom Fields for Provisioning
Note:
This section describes an optional procedure. Perform this procedure only if you want to add custom fields for provisioning.
By default, the attributes listed in User Fields for Provisioning are mapped for provisioning between Oracle Identity Manager and the target system. If required, you can map additional attributes for provisioning.
To add a custom field for provisioning, perform the following procedures:
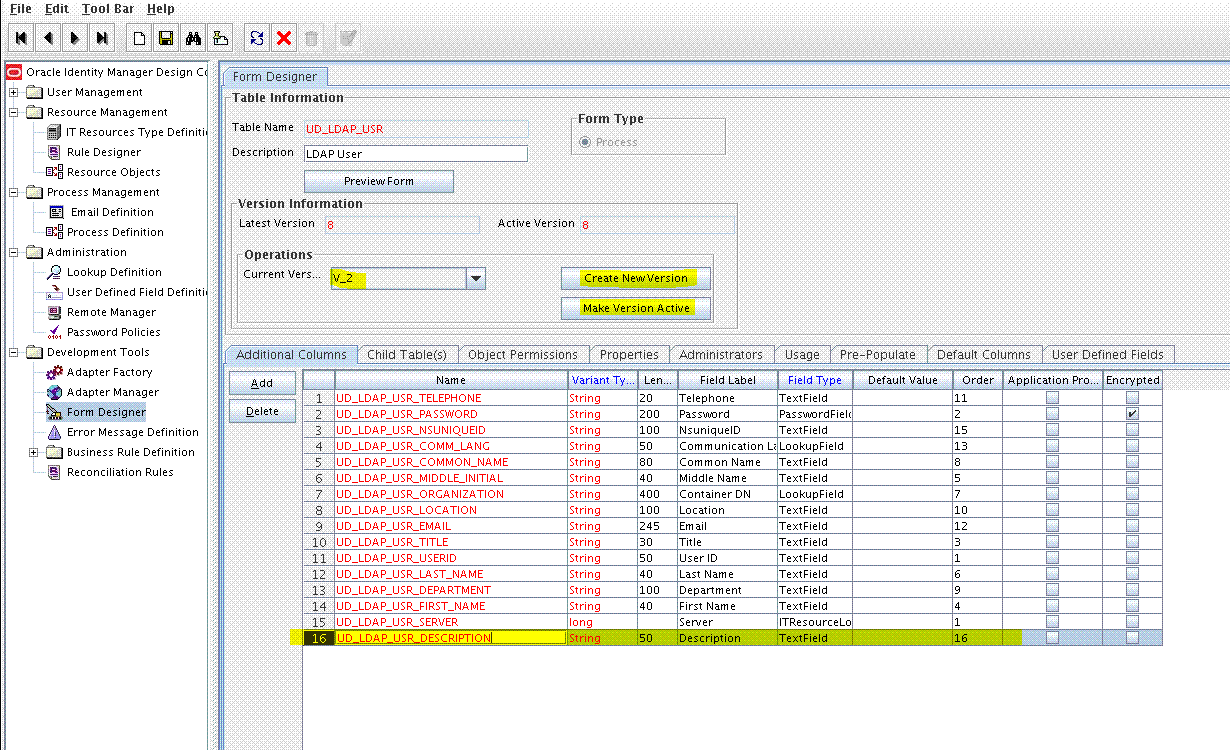
9.3.1 Adding the new Field to the Process Form
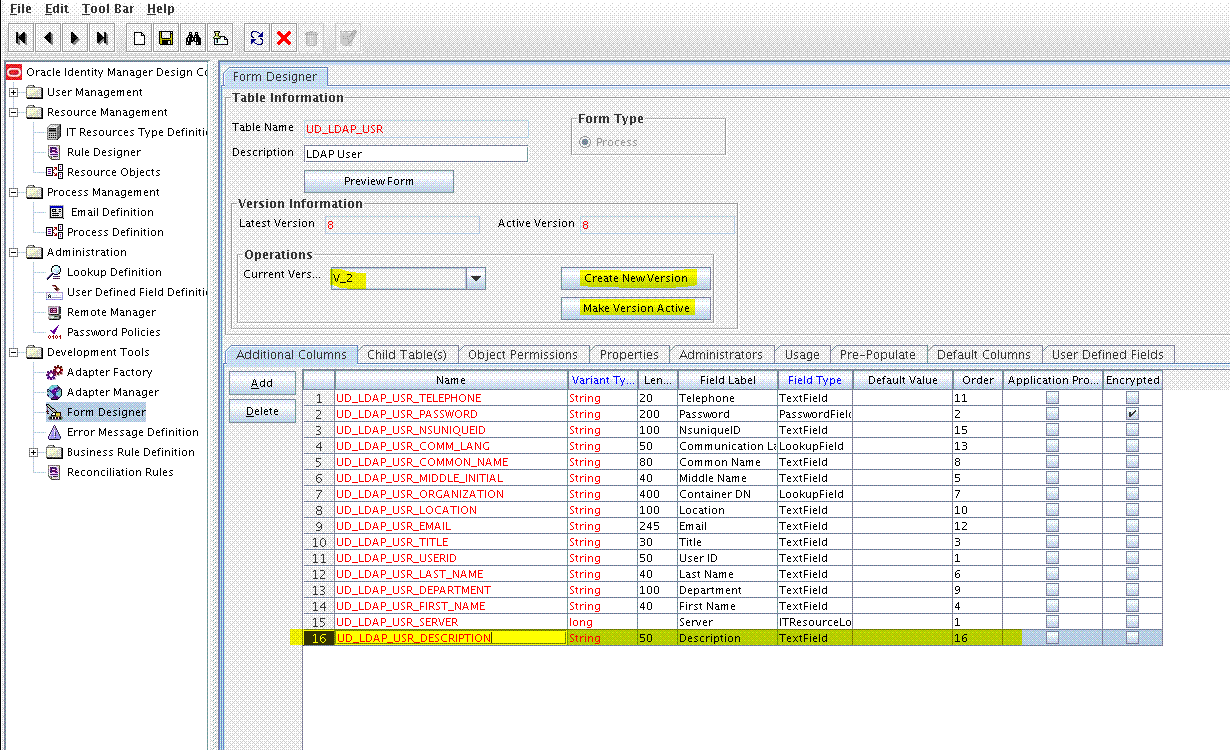
To add the new field to the process form:
-
Log in to Oracle Identity Manager Design Console.
-
Add the new field to the process form.
If you have added the field on the process form by performing the procedure described in Adding the Custom Field on the Process Form, then you need not add the field again. If you have not added the field, then:
-
Expand Development Tools and then double-click Form Designer.
-
Search for and open the UD_LDAP_USR, UD_OID_USR, or UD_EDIR_USR process form.
-
Click Create New Version and then click Add.
-
Enter the details of the field.
For example, if you are adding the Description field, enter UD_LDAP_USR_DESCRIPTION or UD_OID_USR_DESCRIPTION in the Name field, and then enter the rest of the details of this field.
-
Click Save and then click Make Version Active. For example:
-
9.3.2 Associating a New Form With the Application Instance
If you are using Oracle Identity Manager release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form as follows:
- Log in to Oracle Identity System Administration.
- Create and active a sandbox. See Creating and Activating a Sandbox for more information.
- Create a new UI form to view the newly added field along with the rest of the fields. See Creating a New UI Form for more information about creating a UI form.
- Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 3.c), and then save the application instance.
- Publish the sandbox. See Publishing a Sandbox for more information.
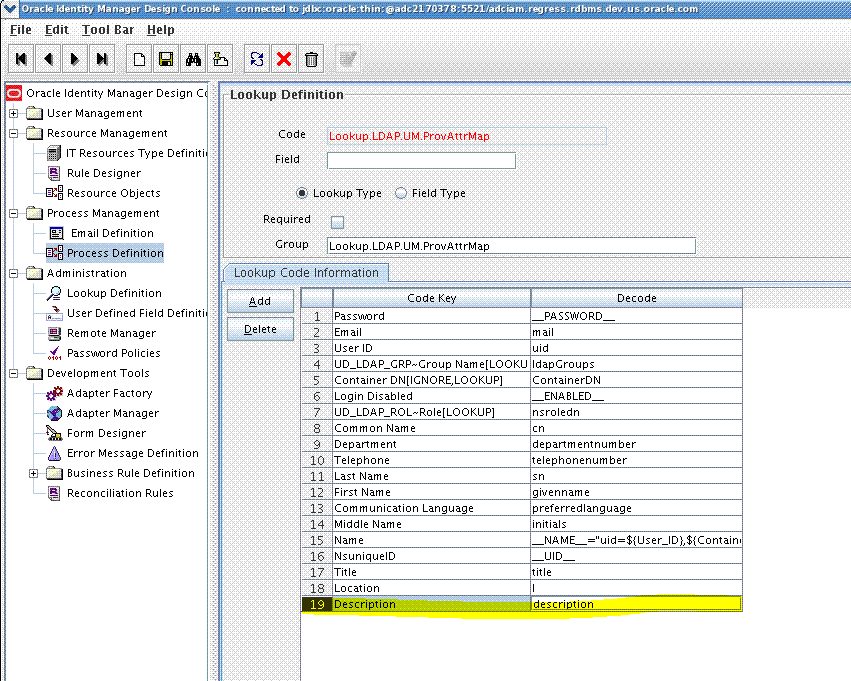
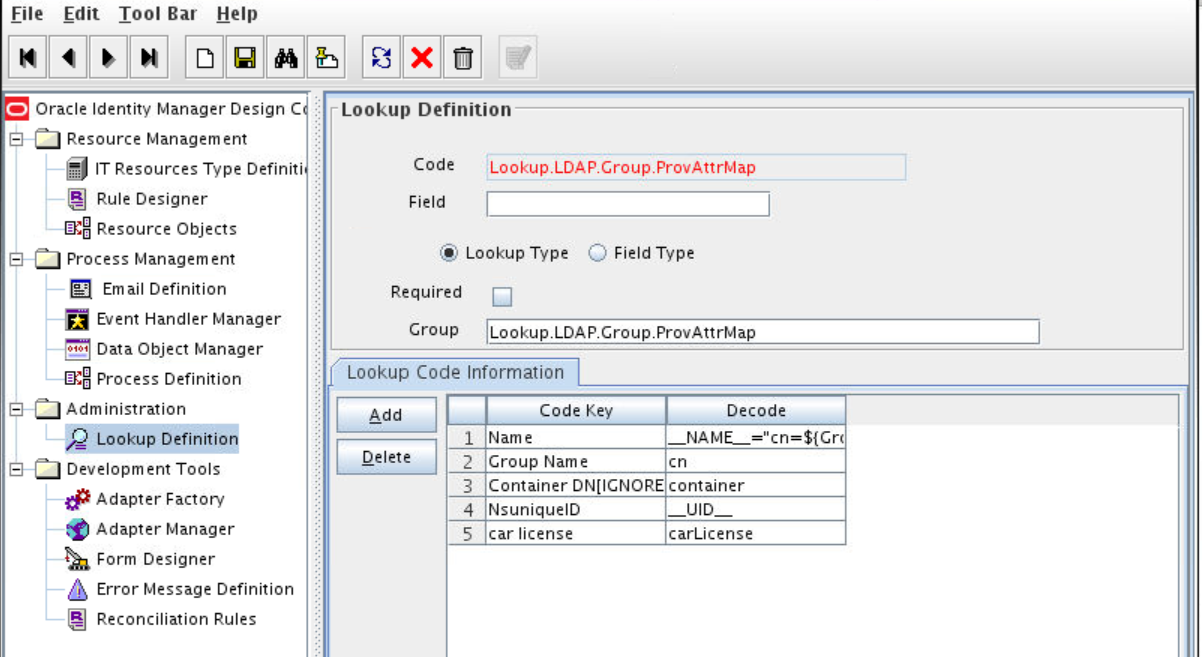
9.3.3 Creating an Entry for the Field in the Lookup Definition for Provisioning
Create an entry for the field in the lookup definition for provisioning as follows:
9.3.4 Enabling Update Provisioning Operations on the Custom Field
Enable update provisioning operations on the custom field as follows:
-
In the provisioning process, add a new task for updating the field as follows:
-
Expand Process Management and then double-click Process Definition.
-
Search for and open the LDAP User, OID User, or eDirectory User provisioning process.
-
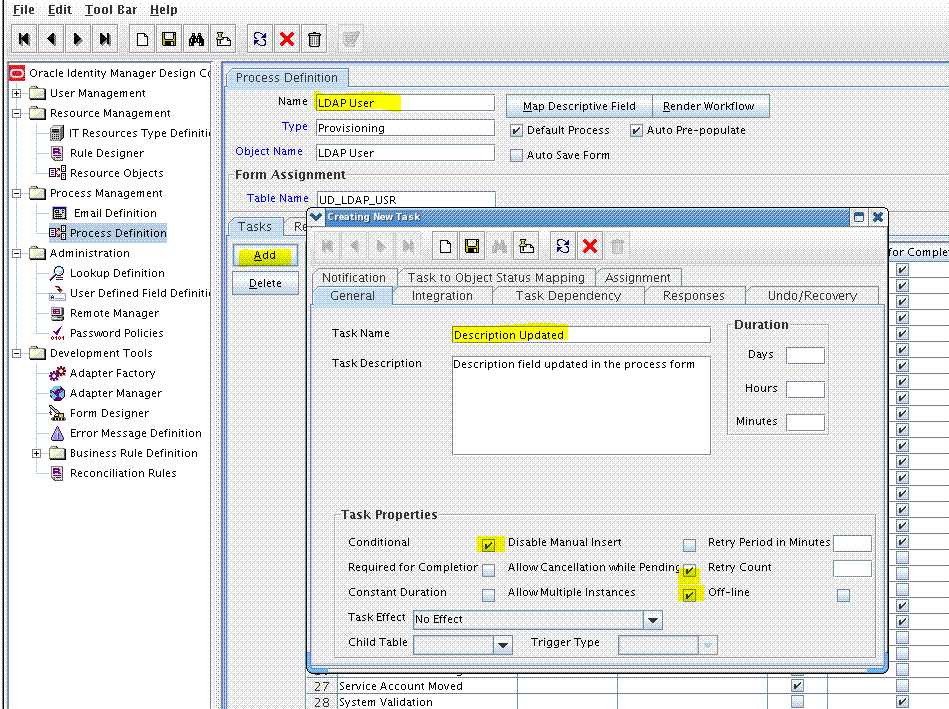
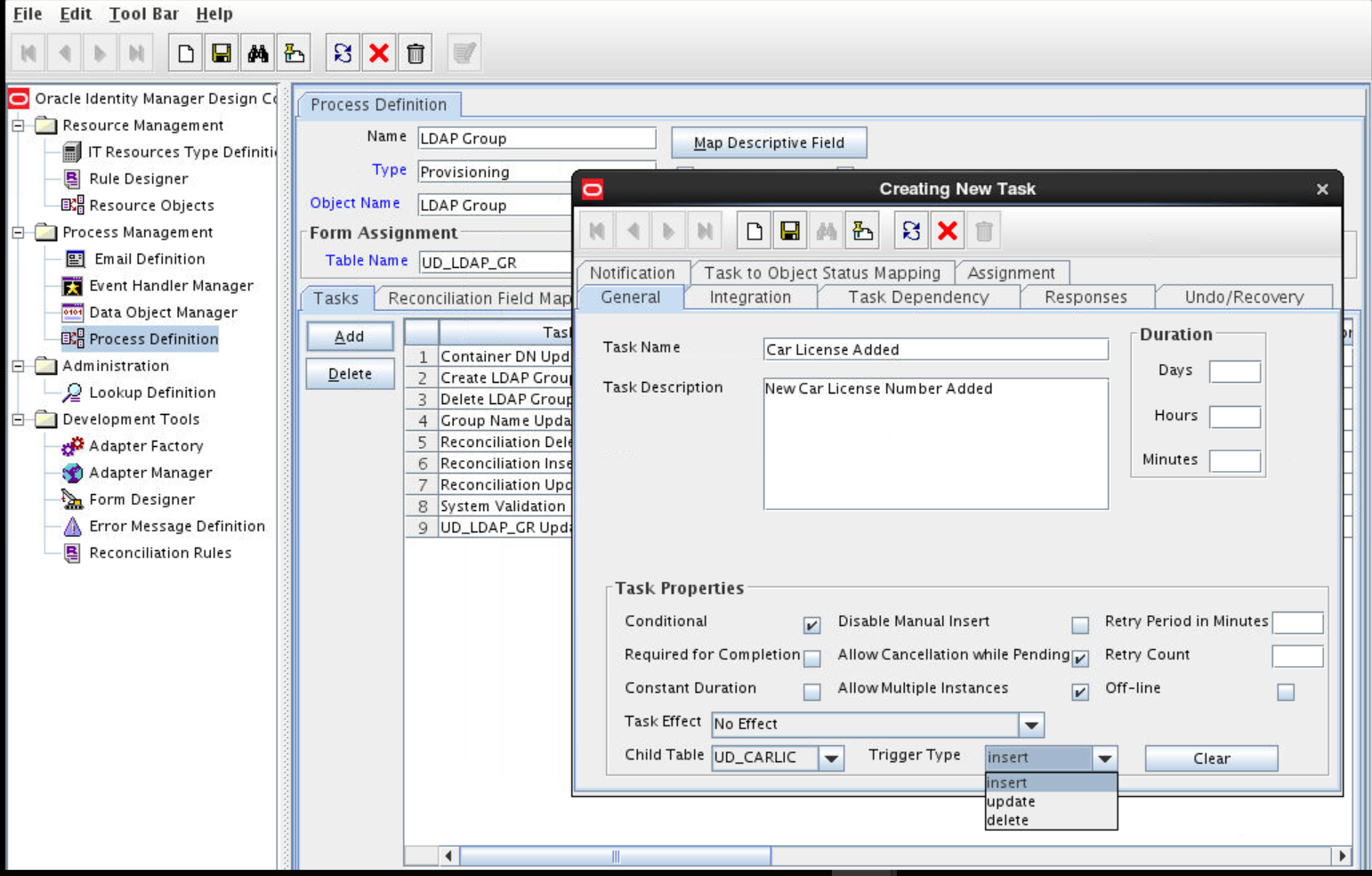
Click Add and enter the task name and task description. The following are sample values:
Task Name:
Description UpdatedTask Description:
Process Task for handling update of the description field. -
In the Task Properties section, select the following fields:
- Conditional
- Allow Cancellation while Pending
- Allow Multiple Instances
-
Insert to add the data from the Trigger Type list.
-
Click Save. For example:
-
-
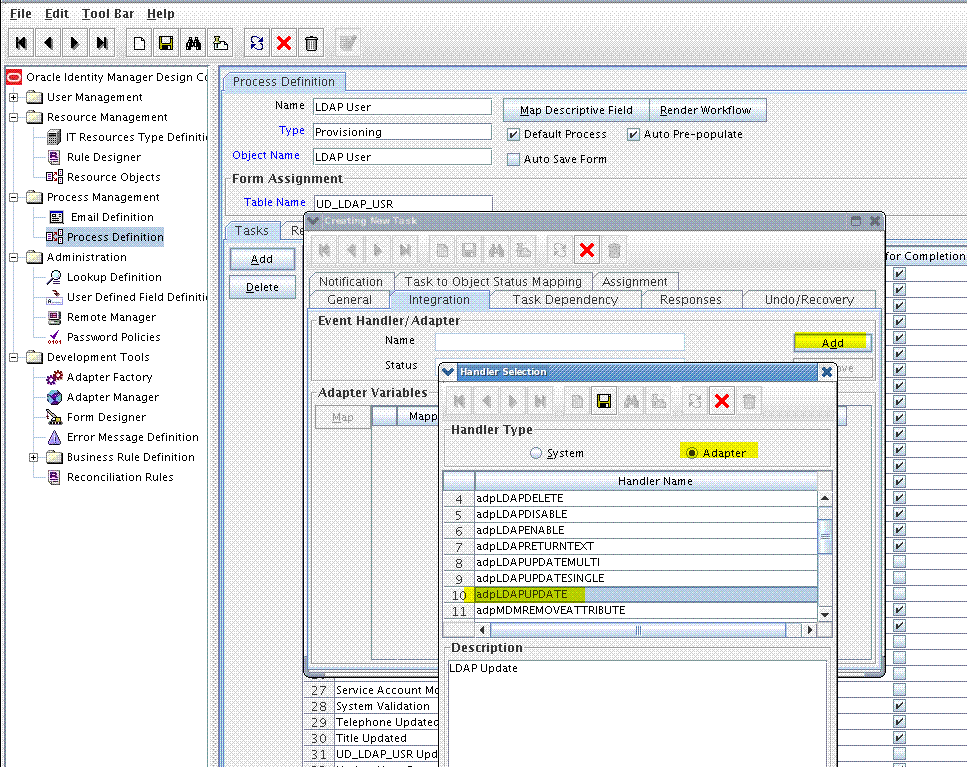
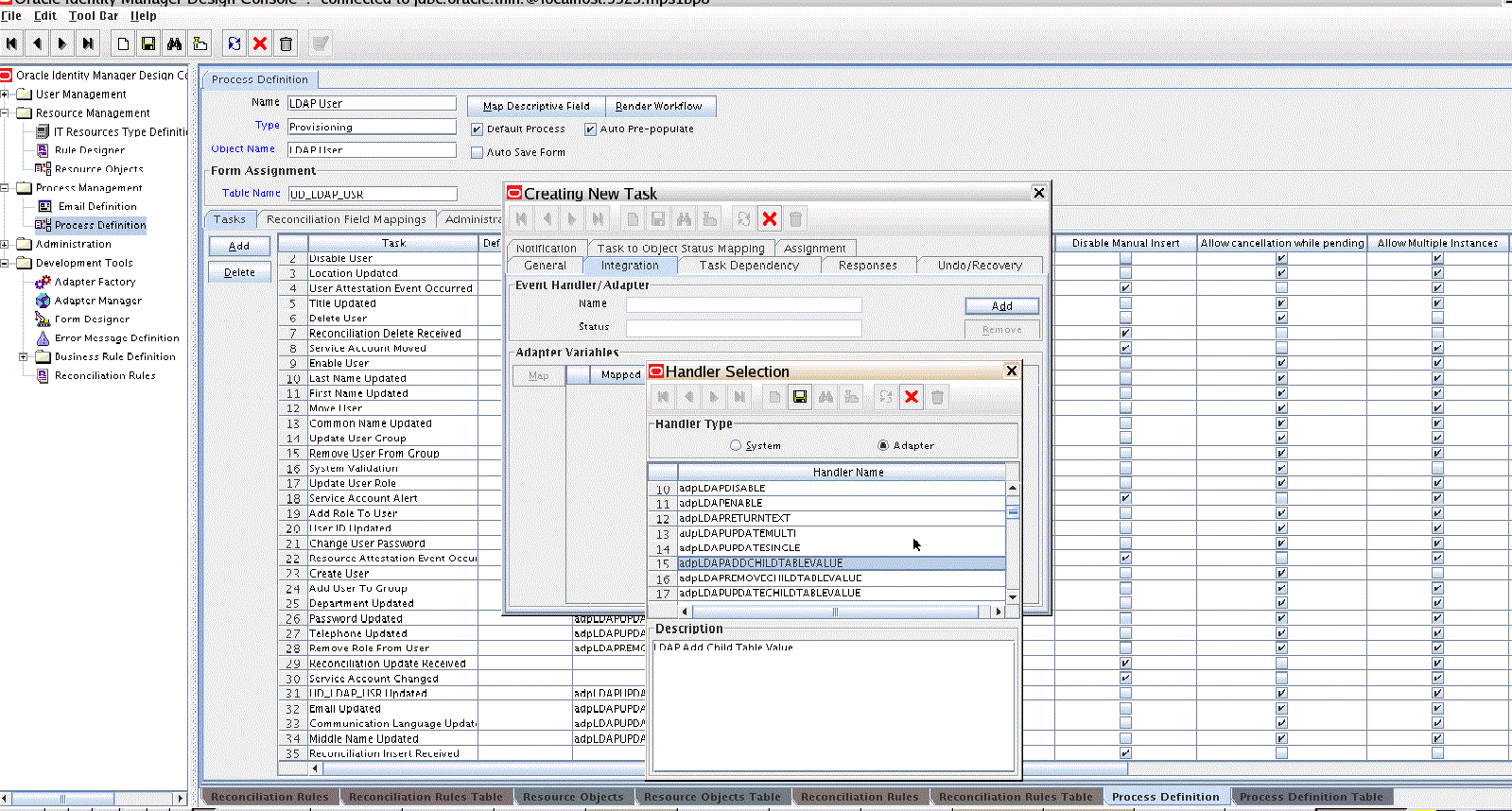
In the provisioning process, select the adapter name in the Handler Type section as follows:
-
Go to the Integration tab, and click Add.
-
In the Handler Selection dialog box, select Adapter.
-
From the Handler Name column, select adpLDAPUPDATE or adpLDAPCHILDUPDATE.
For an eDirectory target, select adpEDIRUPDATE or adpEDIRCHILDUPDATE.
-
Click Save and close the dialog box. For example:
-
-
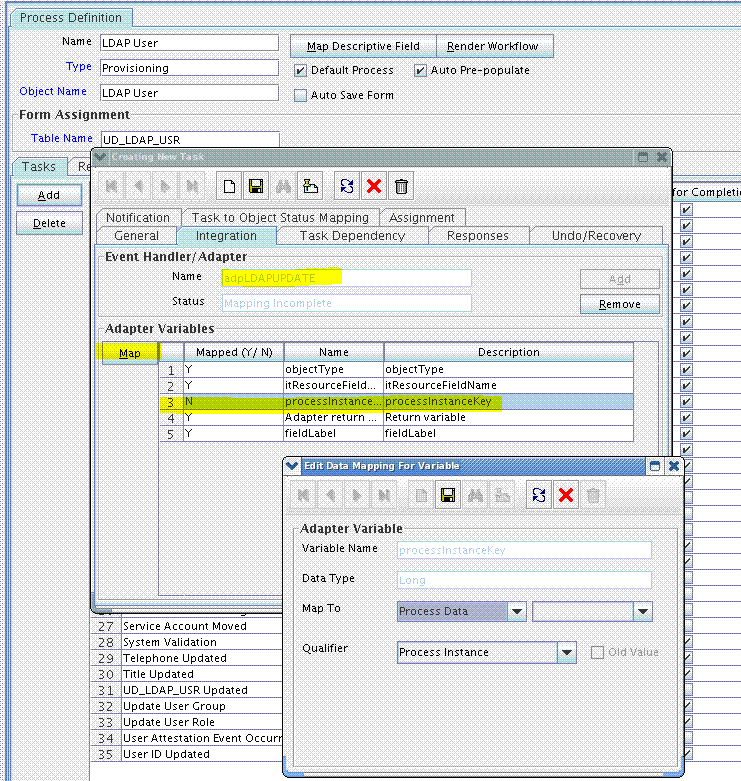
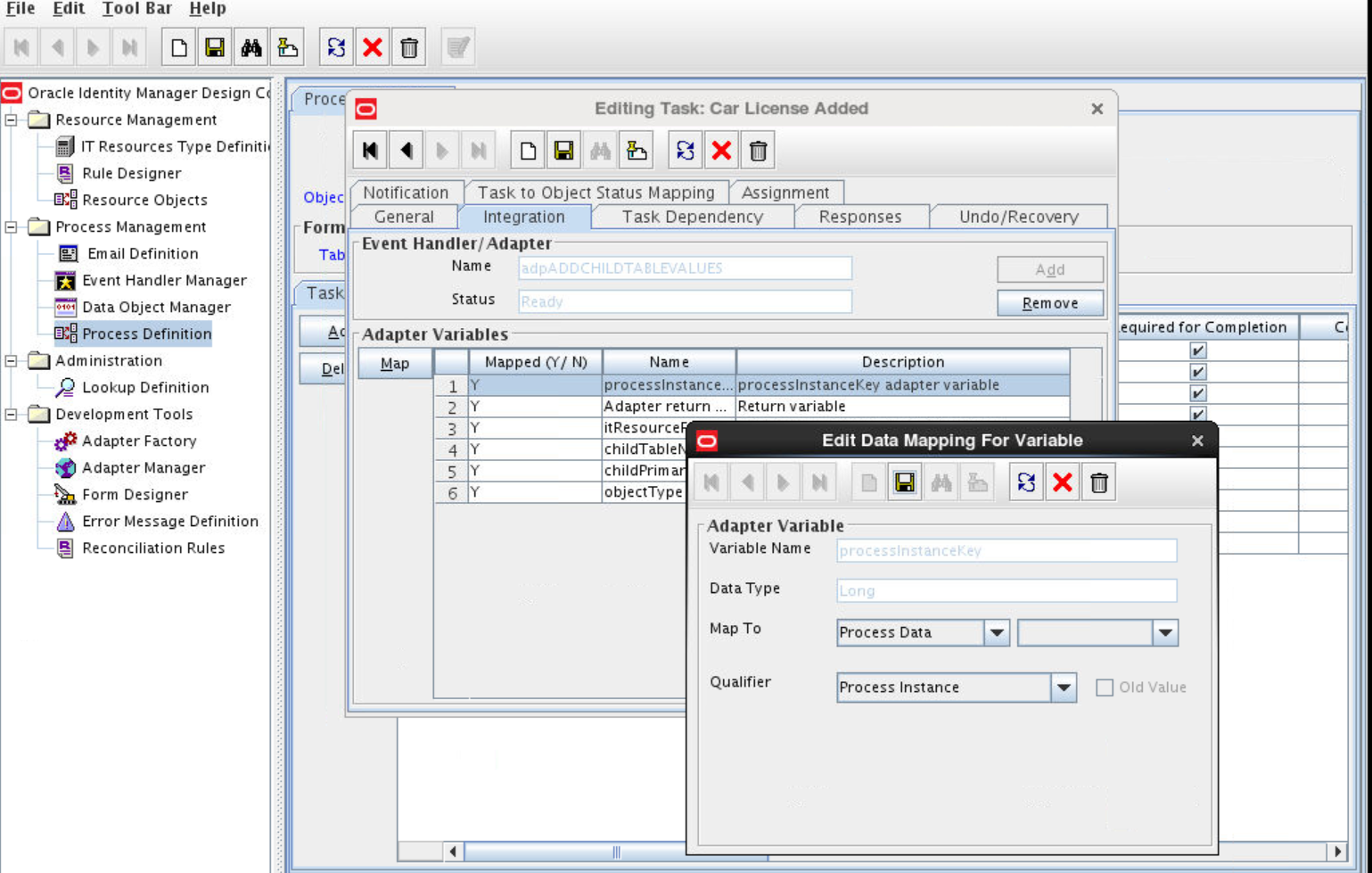
In the Adapter Variables region, click the procInstanceKey variable.
-
In the dialog box that is displayed, create the following mapping:
Variable Name:
procInstanceKeyMap To:
Process DataQualifier:
Process Instance -
Click Save and close the dialog box. For example:
-
Repeat Steps 3 through 5 in Enabling Update Provisioning Operations on the Custom Field for the remaining variables listed in the Adapter Variables region. The following table lists values that you must select from the Map To, Qualifier, and Literal Value lists for each variable:
Variable Map To Qualifier Literal Value Adapter Return Variable
Response Code
NA
NA
processInstanceKey
Process Data
Process Instance
NA
itResourceName or itresourceFieldname for an OID target
Literal
String
UD_LDAP_USR_SERVER, UD_OID_USR_SERVER, or UD_EDIR_USR_SERVER
attrFieldName
Literal
String
Description
objectType
Literal
String
User
-
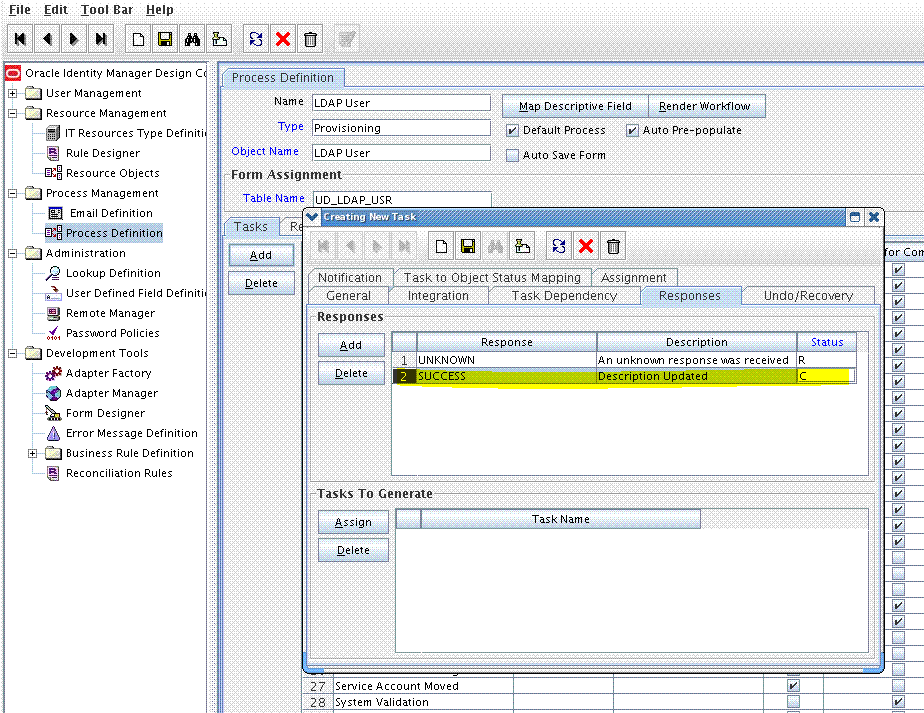
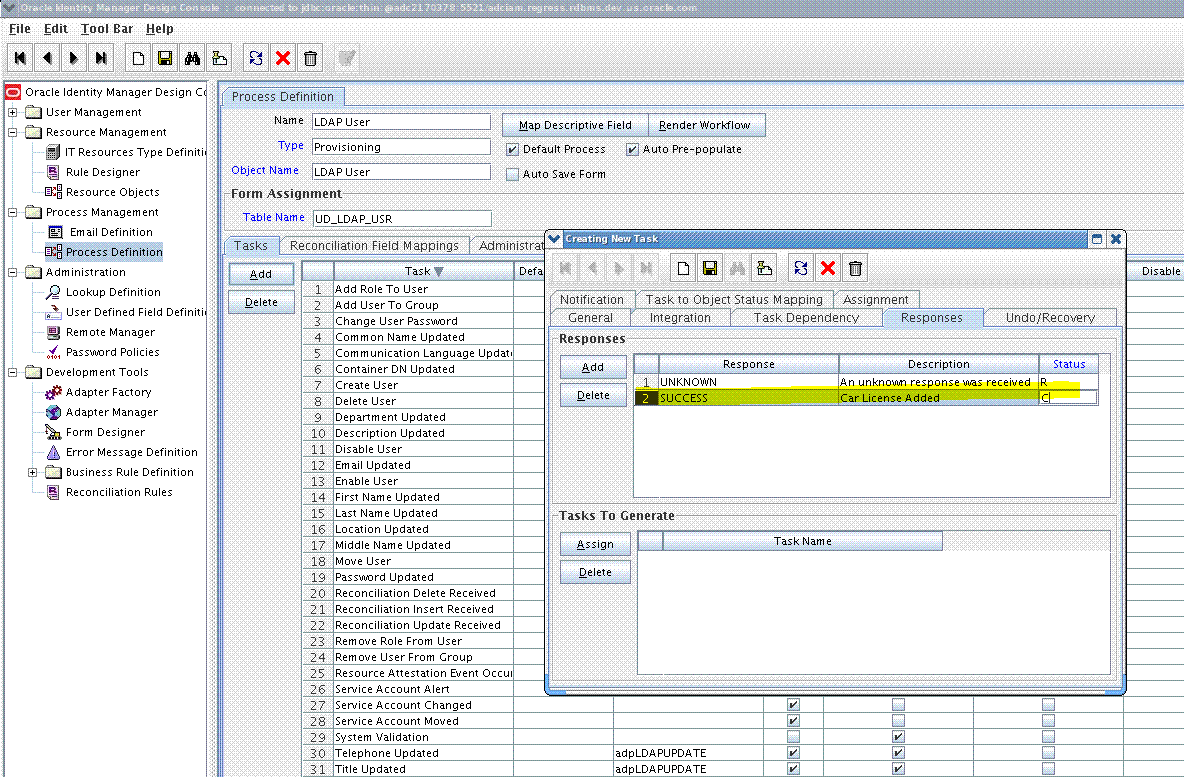
On the Responses tab, click Add to add at least the SUCCESS response code, with Status
C.This ensures that if the custom task is successfully run, then the status of the task is displayed asCompleted. For example: -
Click the Save icon and close the dialog box, and then save the process definition.
9.3.5 Updating the Request Dataset
Note:
Perform steps in this section and Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS only if you want to perform request-based provisioning.
When you add an attribute on the process form, you also update the XML file containing the request dataset definitions. To update a request dataset:
9.3.6 Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS
Run the PurgeCache utility to clear content related to request datasets from the server cache.
See Purging Cache in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about the PurgeCache utility.
Import into MDS, the request dataset definitions in XML format.
See Importing Request Datasets for detailed information about the procedure.
9.4 Adding New Multivalued Fields for Provisioning
Note:
This section describes an optional procedure. Perform this procedure only if you want to add multivalued fields for provisioning.
To add new multivalued fields for provisioning, perform the following procedures:
-
Creating an Entry for the Field in the Lookup Definition for Provisioning
-
Adding the Task for Provisioning Multivalued Attributes in the Process Definition
-
Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS
Note:
Before starting the following procedure, perform the procedures described in Creating a Form for the Multivalued Field through Adding the New Multivalued Field to the Resource Object Reconciliation Fields. If these steps have been performed while adding new multivalued fields for target resource reconciliation, then you need not repeat the steps.
9.4.1 Creating an Entry for the Field in the Lookup Definition for Provisioning
Create an entry for the field in the lookup definition for provisioning as follows:
9.4.2 Adding the Task for Provisioning Multivalued Attributes in the Process Definition
To add the task for provisioning multivalued attributes in the process definition, perform the following procedures:
9.4.2.1 Updating the Process Definition
In the process definition, add the task for provisioning multivalued attributes as follows:
9.4.3 Updating the Request Dataset
Update the request dataset.
Note:
Perform the steps in this section and Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS only if you enabled request-based provisioning.
When you add an attribute on the process form, you also update the XML file containing the request dataset definitions. To update a request dataset:
9.4.4 Running the PurgeCache Utility and Importing the Request Dataset Definition to MDS
Run the PurgeCache utility to clear content related to request datasets from the server cache.
See Purging Cache in Oracle Fusion Middleware Administering Oracle Identity Governance for more information about the PurgeCache utility.
Import into MDS the request dataset definitions in XML format.
9.5 Adding New Fields for Trusted Source Reconciliation
Note:
This section describes an optional procedure. Perform this procedure only if you want to add new fields for trusted source reconciliation.
By default, the attributes listed in Table 1-33 are mapped for reconciliation between Oracle Identity Manager and the target system. If required, you can add new fields for trusted source reconciliation. To do so, perform the following procedures:
9.5.1 Adding the New Field on the OIM User Process Form
To add the new field to the OIM User process form:
-
Log in to Oracle Identity Manager Design Console.
-
If you are using a release prior to Oracle Identity Manager release 11.1.1.5.3, then add the new field on the OIM User process form as follows:
-
Expand Administration.
-
Double-click User Defined Field Definition.
-
Search for and open the Users form.
-
Click Add and enter the details of the field.
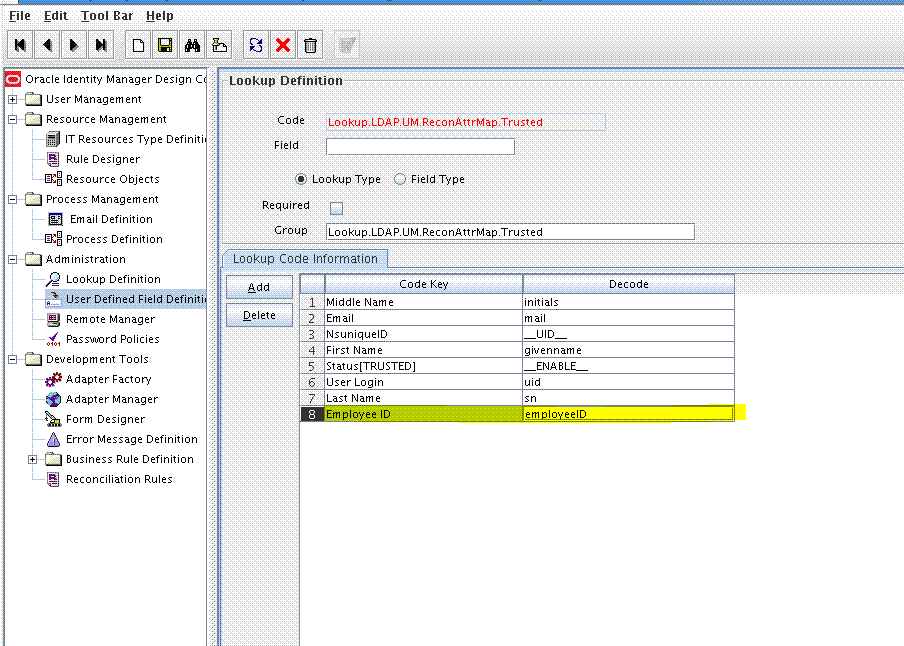
For example, if you are adding the Employee ID field, then enter
Employee IDin the Name field, set the data type to String, enterUSR_UDF_EMPLOYEE_IDas the column name, and enter a field size value. -
Click Save.
-
-
If you are using Oracle Identity Manager release 11.1.1.5.3, then add the new field on the OIM User process form by using the Oracle Identity Advanced Administration interface.
-
If you are using Oracle Identity Manager release 11.1.2 or later, then add the new field on the OIM User process form by performing the procedure described in Configuring Custom Attributes of Oracle Fusion Middleware Administering Oracle Identity Manager.
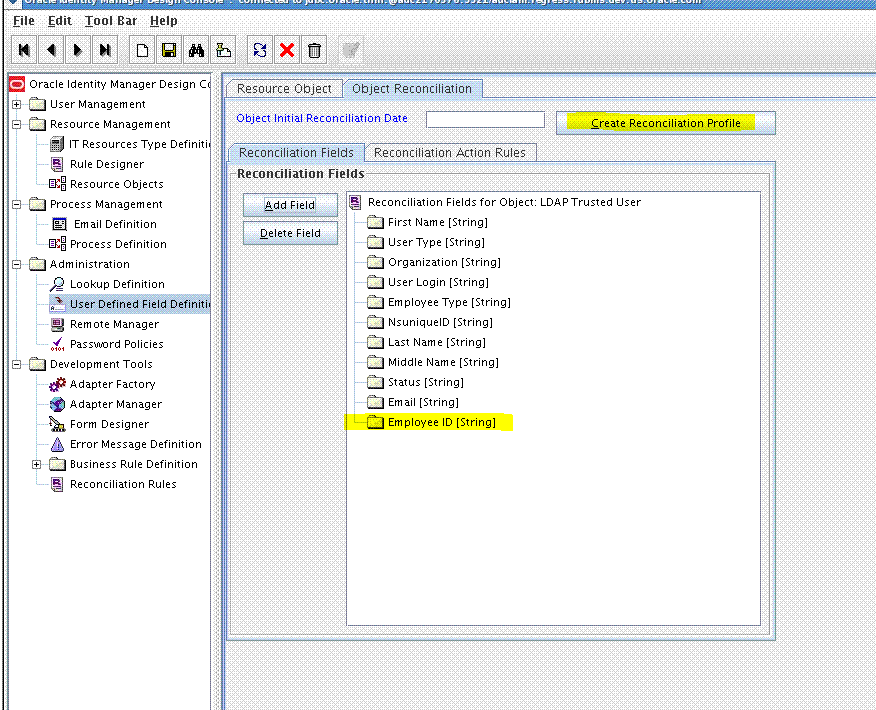
9.5.2 Adding the New Field to the Resource Object Reconciliation Fields
Add the new field to the list of reconciliation fields in the resource object as follows:
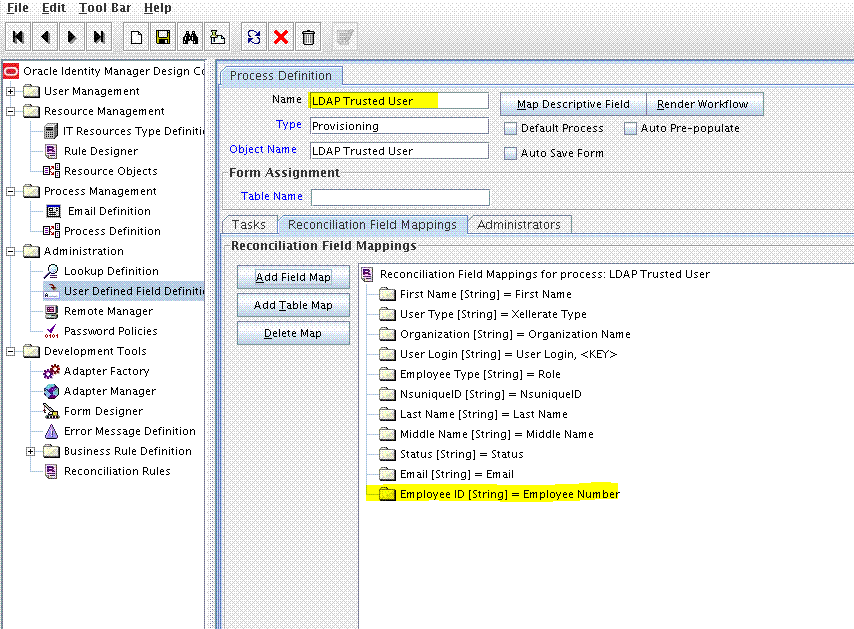
9.5.3 Creating a Reconciliation Field Mapping
Create a reconciliation field mapping for the new field as follows:
9.6 Configuring Transformation of Data During Reconciliation
Note:
This section describes an optional procedure. Perform this procedure only if you want to configure transformation of data during reconciliation.
You can configure transformation of reconciled single-valued user data according to your requirements. For example, you can use First Name and Last Name values to create a value for the Full Name field in Oracle Identity Manager.
To configure transformation of single-valued user data fetched during reconciliation:
9.7 Configuring Validation of Data During Reconciliation and Provisioning
Note:
This section describes an optional procedure. Perform this procedure only if you want to configure validation of data during reconciliation and provisioning.
You can configure validation of reconciled and provisioned single-valued data according to your requirements. For example, you can validate data fetched from the First Name attribute to ensure that it does not contain the number sign (#). In addition, you can validate data entered in the First Name field on the process form so that the number sign (#) is not sent to the target system during provisioning operations.
To configure validation of data:
9.8 Configuring the Connector for User-Defined Object Classes
Note:
This section describes an optional procedure. Perform this procedure only if you want to configure the connector for user-defined object classes.
To configure the connector for user-defined object classes:
9.9 Configuring the Connector to Use Custom Object Classes
If you want to use a custom object class, you need to perform the following procedure. Note that the procedure in this section has been described by using User object class as an example.
-
Modify the LDAP User process definition as follows:
-
Log in to the Design Console.
-
Expand Process Management and then double-click Process Definition.
-
Search for and open the LDAP User process definition.
-
On the Tasks tab, double-click the Create LDAP User process task.
-
Change the value of the objectType adapter variable, to the name of the custom object class.
-
Click Save
-
Repeat steps 'd' through 'g' to edit and update each of the process tasks associated with the User object class. For example, Delete LDAP User and UD_LDAP_USR Updated.
-
-
Before you run any of the following scheduled jobs, set the value of the Object Type attribute of the scheduled jobs to the custom object class value:
-
LDAP Connector User Search Delete Reconciliation
-
LDAP Connector User Search Reconciliation
-
LDAP Connector User Sync Reconciliation
-
LDAP Connector Trusted User Reconciliation
-
LDAP Connector Trusted User Delete Reconciliation
-
9.10 Configuring the Connector for Multiple Trusted Source Reconciliation
Note:
This section describes an optional procedure. Perform this procedure only if you want to configure the connector for multiple trusted source reconciliation.
The following are examples of scenarios in which there is more than one trusted source for user data in an organization:
-
One of the target systems is a trusted source for data about employees. The second target system is a trusted source for data about contractors. The third target system is a trusted source for data about interns.
-
One target system holds the data of some of the identity fields that constitute an OIM User. Two other systems hold data for the remaining identity fields. In other words, to create an OIM User, data from all three systems would need to be reconciled.
If the operating environment of your organization is similar to that described in either one of these scenarios, then this connector enables you to use the target system as one of the trusted sources of user data in your organization.
9.11 Configuring the Connector to Support POSIX Groups and Accounts
This procedure allows the connector to support POSIX groups (posixGroups) and POSIX accounts (posixAccounts).
After you complete this configuration:
-
The connector will support POSIX groups.
-
The sync reconciliation operation will not return the POSIX group membership changes. You must use the full search reconciliation task to get these changes.
To configure the connector to support POSIX groups and accounts:
-
Log in to Oracle Identity Manager Design Console.
-
Modify the Lookup.LDAP.Configuration, Lookup.LDAP.OUD.Configuration, or Lookup.OID.Configuration lookup definition as follows:
-
Set maintainPosixGroupMembership to true.
-
For accountObjectClasses, add "posixGroup","posixAccount".
-
For objectClassesToSynchronize, add "posixGroup","posixAccount".
-
Set groupObjectClasses to "top", "posixGroup".
-
Set readSchema to true.
-
-
In the Lookup.LDAP.UM.ProvAttrMap and Lookup.LDAP.UM.ReconAttrMap lookup definitions, replace "ldapGroups" with "posixGroups".
For OID, update the Lookup.OID.UM.ProvAttrMap and Lookup.OID.UM.ReconAttrMap lookup definitions.
For eDirectory, update the Lookup.EDIR.UM.ProvAttrMap and Lookup.EDIR.UM.ReconAttrMap lookup definitions.
-
In the Lookup.LDAP.Group.ProvAttrMap and Lookup.LDAP.Group.ReconAttrMap lookup definitions, add the following mapping as a String:
GID NUMBER to gidNumber
For OID, update the Lookup.OID.Group.ProvAttrMap and Lookup.OID.Group.ReconAttrMap lookup definitions.
For OID, update the Lookup.EDIR.Group.ProvAttrMap and Lookup.EDIR.Group.ReconAttrMap lookup definitions.
-
In the LDAP Group, OID Group, or eDirectory Group resource object, add the GID NUMBER field as follows:
Select the group (LDAP Group, OID Group, or eDirectory Group), Object Reconciliation, Add Field, and then add GID NUMBER.
-
In the LDAP Group, OID Group, or eDirectory Group process form, add the GID NUMBER field.
-
In the LDAP Group, OID Group, or eDirectory Group process definition, add the mapping as a String for GID Number.
-
In the Lookup.LDAP.UM.ProvAttrMap and Lookup.LDAP.UM.ReconAttrMap lookup definitions, add the following mappings as Strings:
-
GID NUMBER to gidNumber
-
UID NUMBER to uidNumber
-
HOME DIRECTORY to homedirectory
For OID, update the Lookup.OID.UM.ProvAttrMap and Lookup.OID.UM.ReconAttrMap lookup definitions.
For eDirectory, update the Lookup.EDIR.UM.ProvAttrMap and Lookup.EDIR.UM.ReconAttrMap lookup definitions.
-
-
In the LDAP User, OID User, or eDirectory User resource object, add mappings as Strings for these fields:
-
GID NUMBER
-
UID NUMBER
-
HOME DIRECTORY
-
-
In the LDAP User, OID User, or eDirectory User process form, add mappings as Strings for these fields:
-
GID NUMBER
-
UID NUMBER
-
HOME DIRECTORY
-
-
In the LDAP User, OID User, or eDirectory User process definition, add mappings as Strings for these fields:
-
GID NUMBER
-
UID NUMBER
-
HOME DIRECTORY
-
-
After you are finished, click Create Reconciliation Profile.
9.12 Configuring the Connector to Support Provisioning of Custom Object Classes while Provisioning Organizational Unit
Provisioning of custom object-classes while provisioning Organizational Unit (OU) to target systems is supported. In order to change the object classes used for OU, you need to add the Key OU ObjectClasses in the appropriate lookup definitions.
This section contains the following topics:
9.12.1 Modifying the Configuration Lookup Definition
In the Design Console, modify the configuration lookup definition by performing the following procedure:
9.12.2 About Adding Custom Object Classes
If you are adding custom object classes, then the scheduled task (LDAP Connector OU Lookup Reconciliation) used to reconcile the OU container lookup populates those OUs that have the objectClasses specified as the decode value of the ouObjectClasses code key in the configuration lookup definition.
However, the scheduled task (LDAP Connector OU Lookup Reconciliation) does not update the lookup if the OU container in LDAP does not have the custom objectclass associated with it. To reconcile the default OU container loopkup, enter organizationalUnit as the value of the Object Type parameter in the LDAP Connector OU Lookup Reconciliation scheduled job. This will populate the lookup with all the OUs. This because, the default ObjectClass for OU is organizationalUnit.
Similar behavior is observed with the scheduled task LDAP/OID/eDirectory OU search reconciliation operation and synchronized reconciliation operation. These operations will fetch those OUs having objectClasses provided in decode key of the ouObjectClasses.
In order to get the default behavior, you must specify the decode key value as top or organizationalUnit for the code key ouObjectClasses.