1 About the Connector
This chapter contains the following sections:
1.1 Introduction to the OID Connector
This guide discusses the procedures to deploy and use the OID connector, which integrates Oracle Identity Manager with LDAP directories such as Oracle Directory Server Enterprise Edition (ODSEE), Oracle Internet Directory (OID), Oracle Unified Directory (OUD), and Novell eDirectory.
The connector uses the LDAPv3 protocol, so you can also use the connector for an LDAPv3 compliant directory server.
Note:
At some places in this guide, ODSEE, OID, OUD, eDirectory, and an LDAPv3 compliant directory are referred to as the target system.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
Note:
It is recommended that you do not configure the target system as both an authoritative (trusted) source and a managed (target) resource.
1.2 Certified Components
These are the software components and their versions required for installing and using the connector.
Table 1-1 Certified Components
| Component | Requirement for AOB Application | Requirement for CI-Based Connector |
|---|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases:
|
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target systems |
The target system can be any one of the following:
|
The target system can be any one of the following:
|
|
Connector Server |
11.1.2.1.0 |
11.1.2.1.0 |
|
Connector Server JDK and JRE |
JDK or JRE 1.6 and above |
JDK or JRE 1.6 and above |
1.3 Usage Recommendations for the OID Connector
These are the recommendations for the OID connector versions that you can deploy and use depending on the Oracle Identity Manager version you are using.
-
If you are using an Oracle Identity Manager release that is earlier than Oracle Identity Manager 11g Release 1 (11.1.1), then depending on the target system that you are using, install and use one of the following connectors:
-
For Oracle Internet Directory, use the 9.0.4.x version of the Oracle Internet Directory connector.
-
For Novell eDirectory, use the 9.0.4.x version of the Novell eDirectory connector.
-
For Sun ONE Directory Server and Sun Java System Directory Server Enterprise Edition, use the 9.0.4.x version of the Sun Java System Directory connector.
-
-
If you are using Oracle Identity Manager 11g Release 1 (11.1.1.5.0) or later, Oracle Identity Manager 11g Release 2 (11.1.2.0.4) or later, or Oracle Identity Manager 11g Release 2 PS3 (11.1.2.3.0), then use the latest 11.1.1.x version of this connector for target systems Oracle Internet Directory, Sun Java System Directory Server Enterprise Edition, and Novell eDirectory.
1.4 Certified Languages for the OID Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English
-
Finnish
-
French
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
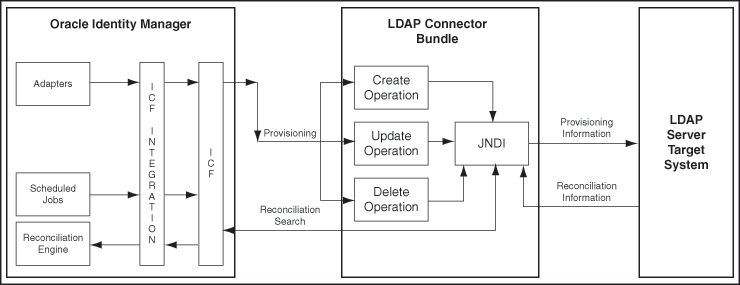
1.5 Architecture of the OID Connector
The OID connector is implemented by using the Identity Connector Framework (ICF). The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. The ICF is shipped along with Oracle Identity Manager. Therefore, you need not configure or modify the ICF.
The OID connector uses JNDI to access the target system.
This connector can be configured to run in one of the following modes:
-
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this form of reconciliation, OIM Users are created or updated corresponding to the creation of and updates to users on the target system. Note that the identity reconciliation mode supports reconciliation of user objects only.
See Reconciliation Scheduled Jobs for information about the LDAP Connector Trusted User Reconciliation scheduled job that is used in this mode.
-
Account Management
Account management is also known as target resource management. This mode of the connector enables the following operations:
-
Provisioning
Provisioning involves creating, updating, or deleting users, groups, roles, and organizational units (OUs) on the target system through Oracle Identity Manager.
When you allocate (or provision) a target system resource to an OIM User, the operation results in the creation of an account on the target system for that user. In the Oracle Identity Manager context, the term "provisioning" is also used to mean updates (for example enabling or disabling) made to the target system account through Oracle Identity Manager.
Users and organizations are organized in hierarchical format on the target system. Before you can provision users to (that is, create users in) the required organizational units (OUs) on the target system, you must fetch into Oracle Identity Manager the list of OUs used on the target system. This is achieved by using the LDAP Connector OU Lookup Reconciliation scheduled job for lookup synchronization.
Similarly, before you can provision users to the required groups or roles on the target system, you must fetch into Oracle Identity Manager the list of all groups and roles used on the target system. This is achieved by using the LDAP Connector Group Lookup Reconciliation and LDAP Connector Role Lookup Recon scheduled jobs for lookup synchronization.
-
Target resource reconciliation
To perform target resource reconciliation, the LDAP Connector User Search Reconciliation or LDAP Connector User Sync Reconciliation scheduled jobs is used. The connector applies filters to locate users to be reconciled from the target system and then fetches the attribute values of these users.
Depending on the data that you want to reconcile, you use different scheduled jobs. For example, you use the LDAP Connector User Search Reconciliation scheduled job to reconcile user data in the target resource mode. See Reconciliation Scheduled Jobs for more information about scheduled jobs used in this mode.
-
1.6 Features of the OID Connector
The features of the connector include support for connector server, support for high-availability configuration of the target system, support for bulk update of target systems, reconciliation of deleted user records, and support for groovy scripts, and so on.
The following are features of the connector:
1.6.1 Dependent Lookup Fields
If you have multiple installations of the target system, the entries in lookup definitions (used as an input source for lookup fields during provisioning) can be linked to the target system installation from which they are copied. Therefore, during a provisioning operation, you can select lookup field values that are specific to the target system installation on which the provisioning operation is being performed.
See Lookup Definitions Synchronized with the Target System for more information about the format in which data is stored in dependent lookup definitions.
1.6.2 Full and Incremental Reconciliation
Full reconciliation involves reconciling all existing user records from the target system into Oracle Identity Manager. In incremental reconciliation, only records that are added or modified after the last reconciliation run are fetched into Oracle Identity Manager.
After you deploy the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, incremental reconciliation is automatically enabled. In incremental reconciliation, user accounts that have been added or modified since the last reconciliation run are fetched into Oracle Identity Manager.
After you create the application, you can first perform full reconciliation. After the first full reconciliation run, incremental reconciliation is automatically enabled.
See Full Reconciliation and Incremental Reconciliation for more information.
1.6.3 Limited Reconciliation
You can set a reconciliation filter as the value of the Filter attribute of a reconciliation scheduled job. This filter specifies the subset of added and modified target system records that must be reconciled.
See Limited Reconciliation for more information.
1.6.4 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation.
The following sections provide more information:
1.6.5 Support for the Connector Server
Connector Server is a component provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles. In other words, a connector server enables remote execution of an Oracle Identity Manager connector.
When you deploy the connector bundle in a connector server, the connector bundle code runs in the same Java Virtual Machine (JVM) as the connector server, rather than in the JVM used by Oracle Identity Manager. Running the Java connector server on a different host can provide performance benefits.
See the following sections for more information:
1.6.6 Support for High-Availability Configuration of the Target System
You can configure the connector for compatibility with high-availability target system environments.
It can read information about backup target system hosts from the failover parameter of the target system IT resource and apply this information when it is unable to connect to the primary host.
For more information about the Failover parameter of the IT resource, see Table 2-2 of Configuring the IT Resource for the Target System.
1.6.7 Support for Bulk Update of Attributes
The connector supports the bulk update of attributes. That is, the connector allows you to update multiple attributes in one operation. With earlier connectors, you could update only one attribute at a time. However, if you specify an invalid value for any of the attributes, none of the attributes are updated. The entire update operation is unsuccessful, and an error is returned. You must then correct any errors in the attribute values and repeat the bulk update operation.
1.6.8 Reconciliation of Deleted User Records
User records that are deleted on the target system are reconciled in Oracle Identity Manager.
1.6.9 Reconciliation of Deleted Groups, Roles, and Organizations
Groups, roles, and organizations that are deleted on the target system are also reconciled in Oracle Identity Manager.
1.6.10 Connection Pooling
A connection pool is a cache of objects that represent physical connections to the target. Oracle Identity Manager connectors can use these connections to communicate with target systems. At run time, the application requests a connection from the pool. If a connection is available, then the connector uses it and then returns it to the pool. A connection returned to the pool can again be requested for and used by the connector for another operation. By enabling the reuse of connections, the connection pool helps reduce connection creation overheads such as network latency, memory allocation, and authentication.
One connection pool is created for each IT resource. For example, if you have three IT resources for three installations of the target system, then three connection pools are created, one for each target system installation.
1.7 Security Considerations for the Connector
These are the security considerations and best practices for the connector.
1.7.1 Secure Communication to the Target System
To provide secure communication to the target system, SSL is required. You can configure SSL between Oracle Identity Manager and the Connector Server and between the Connector Server and the target system.
If you do not configure SSL, passwords can be transmitted over the network in clear text. For example, this problem can occur when you are creating a user or modifying a user's password.
For more information, see Configuring SSL for the Connector.
1.7.2 Administrator Account for the Target System
To connect to the target resource using the connector and to perform connector operations such as provisioning and reconciliation, you must specify a target system administrator with specific administrative permissions.
For more information, see Preinstallation on the Target System.
1.8 Lookup Definitions Used During Reconciliation and Provisioning
Lookup definitions used during connector operations are either preconfigured or can be synchronized with the target system.
Lookup definitions used during reconciliation and provisioning can be divided into the following categories:
-
Lookup definitions used with a specific target system:
1.8.1 Lookup Definitions Synchronized with the Target System
When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Group Name lookup field to select a group from the list of groups in the lookup field.
The following is the format in which data is stored after lookup definition synchronization:
Code Key: <IT_RESOURCE_KEY>~<LOOKUP_FIELD_VALUE>
In this format:
-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the value defined for the code key entry.
Sample value: 3~cn=marketing,ou=groups,dc=example,dc=com
Decode: <IT_RESOURCE_NAME>~<LOOKUP_FIELD_VALUE>
In this format:
-
IT_RESOURCE_NAME is the name of the IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the value defined for the decode entry.
Sample value: DSEE Server~marketing
For example, in the Lookup.LDAP.Role lookup definition, values will be stored in the following format:
Code Key: <IT_RESOURCE_KEY>~<DISTINGUISHED_NAME>
Decode: <IT_RESOURCE_NAME>~<DESCRIPTION>
During a provisioning operation, lookup fields are populated with values corresponding to the target system that you select for the operation.
The following tables list the Oracle Identity Manager lookup definitions that correspond to target system lookup fields and their description:
Table 1-2 Lookup Definitions Synchronized with the Target System
| Lookup Definition | Scheduled Task for Synchronization |
|---|---|
|
Lookup.LDAP.Group |
You use the LDAP Connector Group Lookup Reconciliation scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.LDAP.Role |
You use the LDAP Connector Role Lookup Recon scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.LDAP.Organization |
You use the LDAP Connector OU Lookup Reconciliation scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
Table 1-3 Lookup Definitions Synchronized with the Target System for Oracle Internet Directory
| Lookup Definition | Scheduled Task for Synchronization |
|---|---|
|
Lookup.OID.Group |
You use the OID Connector Group Lookup Reconciliation scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.OID.Organization |
You use the OID Connector OU Lookup Reconciliation scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
Table 1-4 Lookup Definitions Synchronized with the Target System for Novell eDirectory
| Lookup Definition | Scheduled Task for Synchronization |
|---|---|
|
Lookup.EDIR.UserGroup |
You use the eDirectory Connector Group Lookup Reconciliation scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.EDIR.AssignedRole |
You use the eDirectory Connector Role Lookup Recon scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.EDIR.DomainScope |
You use the eDirectory Connector Domain Scope Lookup Reconciliation scheduled job to synchronize this lookup definition. This lookup acts as the domain scope for role actions. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.EDIR.Organization |
You use the eDirectory Connector Org Lookup Reconciliation scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.EDIR.Profile |
You use the eDirectory Connector Profile Lookup Reconciliation scheduled job to synchronize this lookup definition. User can have pre-defined set of profiles in Novell eDirectory and they can be associated while user provisioning. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
Note:
Novell eDirectory has additional lookups such as profile, role containers, and domain scope. See Preconfigured Lookup Definitions for an eDirectory Target System.
1.8.2 Preconfigured Lookup Definitions for Languages
The connector comes with preconfigured values of supported languages.
The following lookup definitions contain the language values:
-
Lookup.LDAP.Language
-
Lookup.OID.Language
-
Lookup.EDIR.CommLang
See Certified Languages for the OID Connector for a list of supported languages.
1.9 Connector Objects Used During Target Resource Reconciliation
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to OIM Users.
This section discusses the following topics:
1.9.1 User Fields for Target Resource Reconciliation
The reconciliation attribute map lookup definitions map user resource object fields and target system attributes. These lookup definitions are used for performing target resource user reconciliation runs.
In these lookup definitions, entries are in the following format:
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 1-5 lists the LDAP attributes from which values are fetched during reconciliation. The LDAP Connector User Search Reconciliation or LDAP Connector User Sync Reconciliation scheduled job is used to reconcile user data.
Table 1-5 Entries in the Lookup.LDAP.UM.ReconAttrMap Lookup Definition
| Resource Object Field | Target System Field |
|---|---|
|
Common Name |
cn |
|
Communication Language |
preferredlanguage |
|
Container DN[LOOKUP] |
__parentDN__ |
|
Department |
departmentnumber |
|
|
|
|
First Name |
givenname |
|
Group~Group Name[LOOKUP] |
ldapGroups |
|
Last Name |
sn |
|
Location |
l |
|
Middle Initial |
initials |
|
NsuniqueID |
__UID__ |
|
Role~Role Name[LOOKUP] |
nsroledn |
|
Status |
__ENABLE__ |
|
Telephone |
telephonenumber |
|
Title |
title |
|
User ID |
uid |
Table 1-6 lists the Oracle Internet Directory attributes from which values are fetched during reconciliation. The OID Connector User Search Reconciliation or OID Connector User Sync Reconciliation scheduled job is used to reconcile user data.
Table 1-6 Entries in the Lookup.OID.UM.ReconAttrMap Lookup Definition
| Resource Object Field | Target System Field |
|---|---|
|
Common Name |
cn |
|
Container DN[LOOKUP] |
__parentDN__ |
|
Department |
departmentnumber |
|
|
|
|
End Date[Date] |
orclActiveEndDate=binding.variables.containsKey("orclActiveEndDate")&&orclActiveEndDate!=null?Date.parse('yyyyMMddHHmmss',orclActiveEndDate).getTime():null |
|
First Name |
givenname |
|
Last Name |
sn |
|
Location |
l |
|
manager |
manager |
|
Middle Name |
initials |
|
orclGuid |
__UID__ |
|
Preferred Language |
preferredlanguage |
|
Start Date[Date] |
orclActiveStartDate=binding.variables.containsKey("orclActiveStartDate")&&orclActiveStartDate!=null?Date.parse('yyyyMMddHHmmss',orclActiveStartDate).getTime():null |
|
Status |
__ENABLE__ |
|
Telephone |
telephonenumber |
|
TimeZone |
orclTimeZone |
|
Title |
title |
|
UserGroup~GroupName[LOOKUP] |
ldapGroups |
|
User ID |
uid |
Table 1-7 lists the Novell eDirectory attributes from which values are fetched during reconciliation. The eDirectory Connector User Search Reconciliation scheduled job is used to reconcile user data.
Table 1-7 Entries in the Lookup.EDIR.UM.ReconAttrMap Lookup Definition
| Resource Object Field | Target System Field |
|---|---|
|
Communication Language |
preferredLanguage |
|
Container DN[LOOKUP] |
__PARENTDN__ |
|
Department |
departmentNumber |
|
|
|
|
entryDN[IGNORE] |
entryDN |
|
First Name |
givenName |
|
Guid |
__UID__ |
|
Last Name |
sn |
|
Location |
l |
|
Logon Script |
loginScript |
|
Middle Initial |
initials |
|
parentDN[IGNORE] |
__PARENTDN__ |
|
Profile |
profile |
|
refid |
__UID__ |
|
Role~Inheritance |
rbsAssignedRoles~rbsRole~inheritable |
|
Role~Role Name[LOOKUP] |
rbsAssignedRoles~rbsRole~__NAME__ |
|
Role~Scope[LOOKUP] |
rbsAssignedRoles~rbsRole~domainScope |
|
Security Group~Group Name[LOOKUP] |
ldapGroups |
|
Status |
__ENABLE__ |
|
Telephone |
telephoneNumber |
|
TimeZone |
timezone |
|
Title |
title |
|
User ID |
entryDN |
1.9.2 Group Fields for Reconciliation
The group lookup definitions map group resource object fields and target system attributes. These lookup definitions are used for performing target resource group reconciliation runs.
Table 1-8 lists the LDAP attributes from which values are fetched during reconciliation. The LDAP Connector Group Search Reconciliation or LDAP Connector Group Sync Reconciliation scheduled job is used to reconcile group data.
Table 1-8 Entries in the Lookup.LDAP.Group.ReconAttrMap Lookup Definition
| Group Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[LOOKUP] |
__parentDN__ |
|
Group Name |
cn |
|
NsuniqueID |
__UID__ |
|
Org Name |
__PARENTRDNVALUE__ |
Table 1-9 lists the Oracle Internet Directory attributes from which values are fetched during reconciliation. The OID Connector Group Search Reconciliation or OID Connector Group Sync Reconciliation scheduled job is used to reconcile group data.
Table 1-9 Entries in the Lookup.OID.Group.ReconAttrMap Lookup Definition
| Group Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[LOOKUP] |
__parentDN__ |
|
Group Name |
cn |
|
OrclGuid |
__UID__ |
|
Org Name |
__PARENTRDNVALUE__ |
Table 1-10 lists the Novell eDirectory attributes from which values are fetched during reconciliation. The eDirectory Connector Group Search Reconciliation scheduled job is used to reconcile group data.
Table 1-10 Entries in the Lookup.EDIR.Group.ReconAttrMap Lookup Definition
| Group Field on Oracle Identity Manager | Target System Field |
|---|---|
|
GroupName |
cn |
|
Guid |
__UID__ |
|
Organization[LOOKUP] |
__PARENTDN__ |
1.9.3 Role Fields for Reconciliation
The role lookup definitions map role resource object fields and target system attributes. These lookup definitions are used for performing target resource role reconciliation runs.
Table 1-11 lists the LDAP role fields from which values are fetched during reconciliation. The LDAP Connector Role Search Reconciliation or LDAP Connector Role Sync Reconciliation scheduled job is used to reconcile role data.
Table 1-11 Entries in the Lookup.LDAP.Role.ReconAttrMap Lookup Definition
| Role Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[LOOKUP] |
__parentDN__ |
|
NsuniqueID |
__UID__ |
|
Org Name |
__PARENTRDNVALUE__ |
|
Role Name |
cn |
Table 1-12 lists the Novell eDirectory attributes from which values are fetched during reconciliation. The eDirectory Connector Role Search Reconciliation scheduled job is used to reconcile role data.
Table 1-12 Entries in the Lookup.EDIR.Role.ReconAttrMap Lookup Definition
| Role Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Guid |
__UID__ |
|
Organization[LOOKUP] |
__PARENTDN__ |
|
RoleName |
cn |
1.9.4 Organizational Unit (OU) Fields for Reconciliation
The organizational unit fields lookup definitions map organization resource object fields and target system attributes. These lookup definitions are used for performing target resource organization reconciliation runs.
Table 1-13 lists the LDAP organizational unit fields from which values are fetched during reconciliation. The LDAP Connector OU Search Reconciliation or LDAP Connector OU Sync Reconciliation scheduled job is used to reconcile organization data.
Table 1-13 Entries in the Lookup.LDAP.OU.ReconAttrMap Lookup Definition
| OU Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[LOOKUP] |
__parentDN__ |
|
NsuniqueID |
__UID__ |
|
Organisation Unit Name |
ou |
|
Org Name |
__PARENTRDNVALUE__ |
Table 1-14 lists the Oracle Internet Directory attributes from which values are fetched during reconciliation. The OID Connector OU Search Reconciliation or OID Connector OU Sync Reconciliation scheduled job is used to reconcile organization data.
Table 1-14 Entries in the Lookup.OID.OU.ReconAttrMap Lookup Definition
| OU Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[LOOKUP] |
__parentDN__ |
|
OrclGuid |
__UID__ |
|
Organization Unit Name |
ou |
|
Org Name |
__PARENTRDNVALUE__ |
Table 1-15 lists the Novell eDirectory attributes from which values are fetched during reconciliation. The eDirectory Connector Org Search Reconciliation scheduled job is used to reconcile organization data.
Table 1-15 Entries in the Lookup.EDIR.OU.ReconAttrMap Lookup Definition
| OU Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container |
__PARENTDN__ |
|
Guid |
__UID__ |
|
OrgName |
ou |
1.9.5 Reconciliation Rules for Target Resource Reconciliation
The connector uses reconciliation rules to determine the identity to which Oracle Identity Manager must assign a resource.
Reconciliation rules for target resource reconciliation are described in the following topics:
1.9.5.1 About Reconciliation Rules for Target Resource Reconciliation
See Also:
Reconciliation Engine in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about reconciliation matching and action rules
The reconciliation matching rules are primarily based on the unique identification attribute for the user in the directory. If this attribute match doesn't occur, second level matching is done based on User Login.
The following are the process matching rules:
-
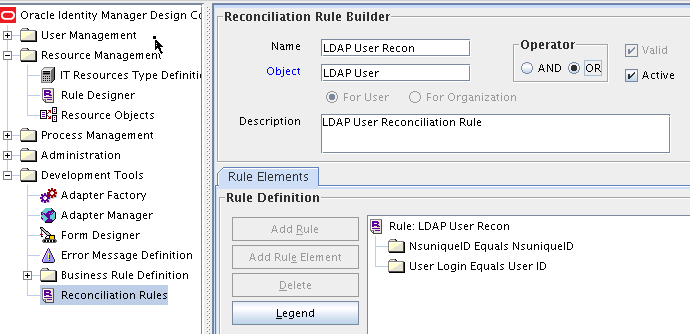
LDAP Rule element: (NsuniqueID Equals NsuniqueID) OR (User Login Equals User ID)
-
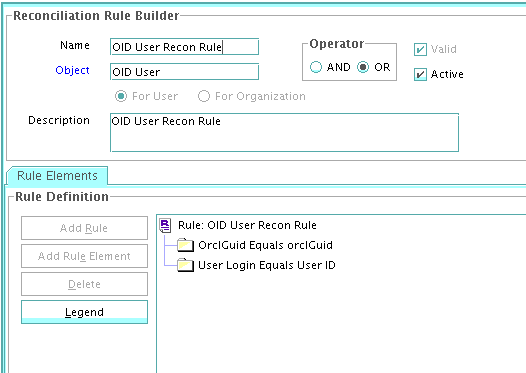
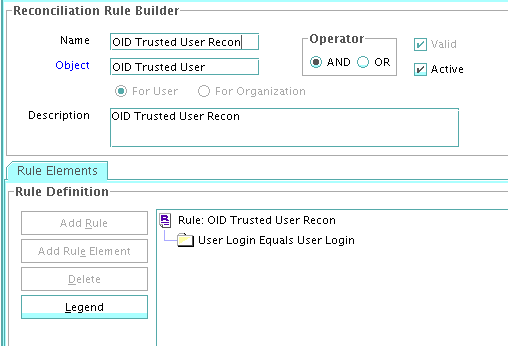
OID Rule element: (OrclGuid Equals orclGuid) OR (User Login Equals User ID)
-
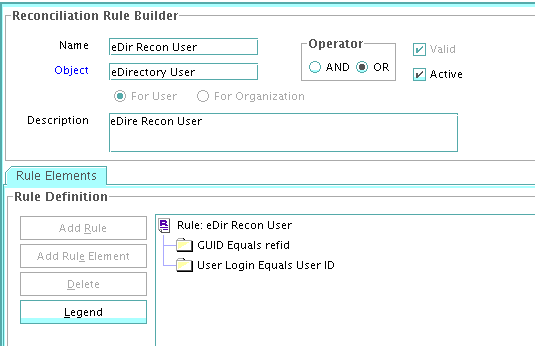
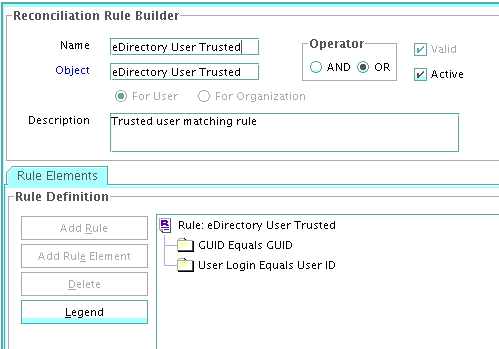
eDirectory Rule element: (GUID Equals refid) OR (User Login Equals User ID)
In the first rule component:
-
GUID on the left of Equals is the unique ID of the user.
-
refid on the right of Equals is the reference ID of the user on the target system.
In the second rule component:
-
User Login is the User Login field on the OIM User form.
-
User ID is the uid field of the target system.
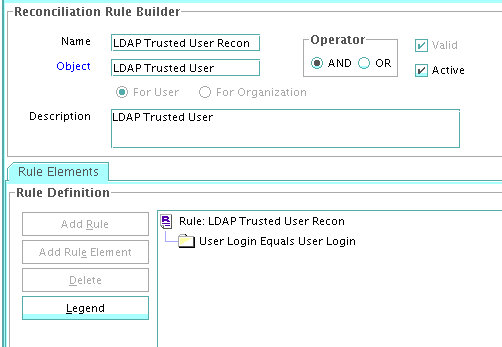
1.9.5.2 Viewing the Reconciliation Rule for Target Resource Reconciliation
After you deploy the connector, you can view the reconciliation rule for target resource reconciliation by performing the following steps:
Note:
Perform the following procedure only after the connector is deployed.
-
Log in to Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for LDAP User Recon. For OID, use OID User Recon Rule and for eDirectory, use eDir Recon User.
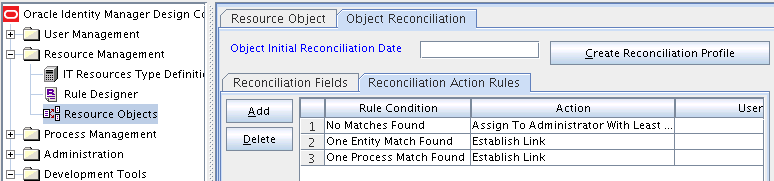
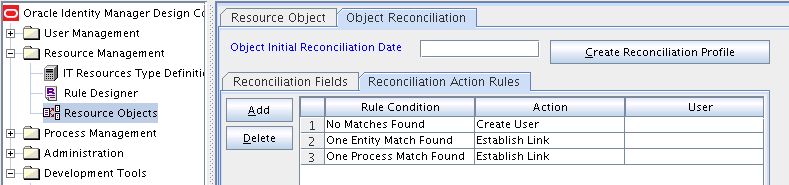
The following screenshots show the reconciliation rules for target resource reconciliation.
1.9.6 Reconciliation Action Rules for Target Resource Reconciliation
Reconciliation action rules define the actions the connector must perform based on the reconciliation rules defined for users.
Reconciliation action rules for target resource reconciliation is described in the following topics:
1.9.6.1 About Reconciliation Actions Rules for Target Resource Reconciliation
Table 1-16 lists the action rules for target resource reconciliation.
Table 1-16 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Assign to Administrator With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. See
in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about setting a reconciliation action rule.
1.10 Connector Objects Used During Provisioning
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
This section discusses the following topics:
Note:
The following characters have special considerations for an LDAP DN: , (comma), = (equals), + (plus), < (less than), > (greater than), # (number sign), ; (semicolon), \ (backslash), and " " (quotation marks). If you use any of these characters in User, Group, Organization, or Role process forms, you must escape the character with a backslash (\).
1.10.1 Provisioning Functions
Table 1-17 and Table 1-18 list the supported user provisioning functions and the adapters that perform these functions. The functions listed in the table correspond to either a single or multiple process tasks.
Table 1-17 Provisioning Functions for LDAP and OID Users
| Function | Adapter |
|---|---|
|
Create a user account |
LDAP CREATE OBJECT |
|
Update a user account |
LDAP Update Single - for updating only a single attribute LDAP Update Multi - for updating two or more attributes |
|
Delete a user account |
LDAP Delete |
|
Enable a disabled user account |
LDAP Enable |
|
Disable a user account |
LDAP Disable |
|
Change or reset the password |
LDAP Return Text |
Table 1-18 Provisioning Functions for eDirectory Users
| Function | Adapter |
|---|---|
|
Create a user account |
EDIR CREATE OBJECT |
|
Update a user account |
EDIR Update Single - for updating only a single attribute EDIR Update Multi - for updating two or more attributes |
|
Delete a user account |
EDIR Delete |
|
Enable a disabled user account |
EDIR Enable |
|
Disable a user account |
EDIR Disable |
|
Child table operations |
EDIR Child Update |
Table 1-19 and Table 1-20 list the provisioning functions for groups, roles, and organizational units and the adapters that perform these functions.
Table 1-19 Provisioning Functions for LDAP and OID Groups, Roles, and Organizational Units
| Function | Adapter |
|---|---|
|
Create Group, Create Role, and Create Organization |
LDAP CREATE OBJECT |
|
Delete Group, Delete Organization, and Delete Role |
LDAP Delete |
|
Group Name Update, Role Name Update, and Organization Name Update |
LDAP Update |
|
Container DN Update |
LDAP Update Single |
Table 1-20 Provisioning Functions for eDirectory Groups, Roles, and Organizational Units
| Function | Adapter |
|---|---|
|
Create Group, Create Role, and Create Organization |
EDIR CREATE OBJECT |
|
Delete Group, Delete Organization, and Delete Role |
EDIR Delete |
|
Group Name Update, Role Name Update, and Organization Name Update |
EDIR Update |
|
Container DN Update |
EDIR Update Single |
1.10.2 User Fields for Provisioning
This section discusses the following topics:
1.10.2.1 User Fields for Provisioning an ODSEE Target System
The Lookup.LDAP.UM.ProvAttrMap lookup definition maps process form fields with ODSEE attributes. This lookup definition is used for performing user provisioning operations.
Table 1-21 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-21 Entries in the Lookup.LDAP.UM.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Common Name |
cn |
|
Communication Language |
preferredlanguage |
|
Container DN[IGNORE,LOOKUP] |
ContainerDN |
|
Department |
departmentnumber |
|
|
|
|
First Name |
givenname |
|
Last Name |
sn |
|
Location |
l |
|
Login Disabled |
__ENABLED__ |
|
Middle Name |
initials |
|
Name |
__NAME__="uid=${User_ID},${Container_DN}" |
|
NsuniqueID |
__UID__ |
|
Password |
__PASSWORD__ |
|
Telephone |
telephonenumber |
|
Title |
title |
|
UD_LDAP_GRP~Group Name[LOOKUP] |
ldapGroups |
|
UD_LDAP_ROL~Role[LOOKUP] |
nsroledn |
|
User ID |
uid |
1.10.2.2 User Fields for Provisioning an OUD Target System
The Lookup.LDAP.UM.ProvAttrMap lookup definition maps process form fields with OUD target system attributes. This lookup definition is used for performing user provisioning operations.
Table 1-22 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-22 Entries in the Lookup.LDAP.UM.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Common Name |
cn |
|
Communication Language |
preferredlanguage |
|
Container DN[IGNORE,LOOKUP] |
ContainerDN |
|
Department |
departmentnumber |
|
|
|
|
First Name |
givenname |
|
Last Name |
sn |
|
Location |
l |
|
Login Disabled |
__ENABLED__ |
|
Middle Name |
initials |
|
Name |
__NAME__="uid=${User_ID},${Container_DN}" |
|
NsuniqueID |
__UID__ |
|
Password |
__PASSWORD__ |
|
Telephone |
telephonenumber |
|
Title |
title |
|
UD_LDAP_GRP~Group Name[LOOKUP] |
ldapGroups |
|
UD_LDAP_ROL~Role[LOOKUP] |
nsroledn |
|
User ID |
uid |
1.10.2.3 User Fields for Provisioning an OID Target System
The Lookup.OID.UM.ProvAttrMap lookup definition maps process form fields with OID attributes. This lookup definition is used for performing user provisioning operations.
Table 1-23 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-23 Entries in the Lookup.OID.UM.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Common Name |
cn |
|
Container DN[IGNORE,LOOKUP] |
ContainerDN |
|
Department |
departmentnumber |
|
Email ID |
|
|
EndDate |
orclActiveEndDate=End_Date!=null&&!End_Date.startsWith("1969-12-31")?Date.parse('yyyy-MM-dd', End_Date).format('yyyyMMddHHmmss') + 'Z':null |
|
End Date[IGNORE] |
enddate |
|
First Name |
givenname |
|
Last Name |
sn |
|
Location |
l |
|
Login Disabled |
__ENABLED__ |
|
manager |
manager |
|
Middle Name |
initials |
|
Name |
__NAME__="uid=${User_ID},${Container_DN}" |
|
orclGuid |
__UID__ |
|
Password |
__PASSWORD__ |
|
Preferred Language |
preferredLanguage |
|
StartDate |
orclActiveStartDate=Start_Date!=null&&!Start_Date.startsWith("1969-12-31")?Date.parse('yyyy-MM-dd', Start_Date).format('yyyyMMddHHmmss') + 'Z':null |
|
Start Date[IGNORE] |
startdate |
|
Telephone |
telephonenumber |
|
Time Zone |
orclTimeZone |
|
Title |
title |
|
UD_OID_GRP~Group Name[LOOKUP] |
ldapGroups |
|
User ID |
uid |
1.10.2.4 User Fields for Provisioning an eDirectory Target System
The Lookup.EDIR.UM.ProvAttrMap lookup definition maps process form fields with eDirectory attributes. This lookup definition is used for performing user provisioning operations.
Table 1-24 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-24 Entries in the Lookup.EDIR.UM.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Password |
__PASSWORD__ |
|
UD_EDIR_ROL~Role Name[LOOKUP] |
rbsAssignedRoles~rbsRole~__NAME__ |
|
UD_EDIR_ROL~Inheritable |
rbsAssignedRoles~rbsRole~inheritable |
|
Logon Script |
loginScript |
|
Timezone |
timezone |
|
Title |
title |
|
Department |
departmentNumber |
|
UD_EDIR_ROL~Scope[LOOKUP] |
rbsAssignedRoles~rbsRole~domainScope |
|
First Name |
givenName |
|
Communication Language |
preferredLanguage |
|
Profile[LOOKUP] |
profile |
|
Last Name |
sn |
|
Guid |
__NAME__="cn=${User_ID},${Container_DN}" |
|
User ID |
cn |
|
Container DN[IGNORE,LOOKUP] |
ContainerDN |
|
|
|
|
Location |
l |
|
Telephone |
telephonenumber |
|
Reference ID |
__UID__ |
|
UD_EDIR_GRP~Group Name[LOOKUP] |
ldapGroups |
|
Middle Name |
initials |
1.10.3 Group Fields for Provisioning
The Lookup.LDAP.Group.ProvAttrMap lookup definition maps process form fields for groups and target system attributes from an LDAP target system. This lookup definition is used for performing group provisioning operations.
Table 1-25 lists the group fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-25 Entries in the Lookup.LDAP.Group.ProvAttrMap Lookup Definition
| Group Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[IGNORE,LOOKUP] |
container |
|
Group Name |
cn |
|
Name |
__NAME__="cn=${Group_Name},${Container_DN}" |
|
NsuniqueID |
__UID__ |
The Lookup.OID.Group.ProvAttrMap lookup definition maps process form fields for groups and target system attributes for an Oracle Internet Directory target system. This lookup definition is used for performing group provisioning operations.
Table 1-26 lists the group fields of the OID target system for which you can specify or modify values during provisioning operations.
Table 1-26 Entries in the Lookup.OID.Group.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Container DN[IGNORE,LOOKUP] |
container |
|
Group Name |
cn |
|
Name |
__NAME__="cn=${Group_Name},${Container_DN}" |
|
OrclGuid |
__UID__ |
The Lookup.EDIR.Group.ProvAttrMap lookup definition maps process form fields for groups and target system attributes for an eDirectory target system. This lookup definition is used for performing group provisioning operations.
Table 1-27 lists the group fields of the eDirectory target system for which you can specify or modify values during provisioning operations.
Table 1-27 Entries in the Lookup.EDIR.Group.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Reference ID |
__UID__ |
|
Container DN[IGNORE,LOOKUP] |
ContainerDN |
|
Group Name |
cn |
|
Guid |
__NAME__="cn=${Group_Name},${Container_DN}" |
1.10.4 Role Fields for Provisioning
The Lookup.LDAP.Role.ProvAttrMap lookup definition maps process form fields for roles and target system attributes from an LDAP target system. This lookup definition is used for performing role provisioning operations.
Table 1-28 lists the role fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-28 Entries in the Lookup.LDAP.Role.ProvAttrMap Lookup Definition
| Role Field on Oracle Identity Manager | Target System Field |
|---|---|
|
Container DN[IGNORE,LOOKUP] |
not used |
|
Name |
__NAME__="cn=${Role_Name},${Container_DN}" |
|
NsuniqueID |
__UID__ |
|
Role Name |
cn |
The Lookup.EDIR.Role.ProvAttrMap lookup definition maps process for fields for roles and target system attributes for an eDirectory target system. This lookup definition is used for performing role provisioning operations.
Table 1-29 lists the role fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-29 Entries in the Lookup.EDIR.Role.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Role Container[IGNORE,LOOKUP] |
ContainerDN |
|
Reference ID |
__UID__ |
|
Guid |
__NAME__="cn=${Role_Name},${Role_Container}" |
|
Role Name |
cn |
1.10.5 Organizational Unit Fields for Provisioning
The Lookup.LDAP.OU.ProvAttrMap lookup definition maps process form fields for organizations and target system attributes for an LDAP target system. This lookup definition is used for performing organizational unit provisioning operations.
Table 1-30 lists the organizational unit fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-30 Entries in the Lookup.LDAP.OU.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Container DN[IGNORE,LOOKUP] |
not used |
|
Name |
__NAME__="ou=${Organisation_Unit_Name},${Container_DN}" |
|
NsuniqueID |
__UID__ |
|
Organisation Unit Name |
ou |
The Lookup.OID.OU.ProvAttrMap lookup definition maps process form fields for organizations and target system attributes for an Oracle Internet Directory target system. This lookup definition is used for performing group provisioning operations.
Table 1-31 lists the organizational unit fields of the OID target system for which you can specify or modify values during provisioning operations.
Table 1-31 Entries in the Lookup.OID.OU.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Container DN[IGNORE,LOOKUP] |
not used |
|
Name |
__NAME__="ou=${Organisation_Unit_Name},${Container_DN}" |
|
OrclGuid |
__UID__ |
|
Organisation Unit Name |
ou |
The Lookup.EDIR.OU.ProvAttrMap lookup definition maps process form fields for organizations and target system attributes for an eDirectory target system. This lookup definition is used for performing organizational unit provisioning operations.
Table 1-32 lists the organizational unit fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-32 Entries in the Lookup.EDIR.OU.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field |
|---|---|
|
Organisation Name |
ou |
|
Reference ID |
__UID__ |
|
Guid |
__NAME__="ou=${Organisation_Name},${Container_DN}" |
|
Container DN[LOOKUP,IGNORE] |
Not used |
1.11 Connector Objects Used During Trusted Source Reconciliation
Trusted source reconciliation involves fetching data about newly created or modified accounts on the target system and using that data to create or update OIM Users.
The LDAP Connector Trusted User Reconciliation scheduled job is used to initiate a trusted source reconciliation run. This scheduled task is discussed in Scheduled Jobs for Reconciliation of User Records.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for conceptual information about trusted source reconciliation.
This section discusses the following topics:
1.11.1 User Fields for Trusted Source Reconciliation
The Lookup.LDAP.UM.ReconAttrMap.Trusted lookup definition maps user fields of the OIM User form with corresponding field names in the LDAP target system. This lookup definition is used for performing trusted source reconciliation runs.
Table 1-33 lists the user identity fields whose values are fetched from the LDAP target system during a trusted source reconciliation run.
Table 1-33 Entries in the Lookup.LDAP.UM.ReconAttrMap.Trusted Lookup Definition
| OIM User Form Field | Target System Field |
|---|---|
|
|
|
|
First Name |
givenname |
|
Last Name |
sn |
|
Middle Name |
initials |
|
NsuniqueID |
__UID__ |
|
Status[TRUSTED] |
__ENABLE__ |
|
User Login |
uid |
The Lookup.OID.UM.ReconAttrMap.Trusted lookup definition maps user fields of the OIM User form with corresponding field names in the Oracle Internet Directory target system. This lookup definition is used for performing trusted source reconciliation runs.
Table 1-34 lists the user identity fields whose values are fetched from the OID target system during a trusted source reconciliation run.
Table 1-34 Entries in the Lookup.OID.UM.ReconAttrMap.Trusted Lookup Definition
| OIM User Form Field | Target System Field |
|---|---|
|
|
|
|
First Name |
givenname |
|
Last Name |
sn |
|
Manager |
manager=matcher=java.util.regex.Pattern.compile("uid=(\\w*).*").matcher(manager==null?"":manager);matcher.matches()?matcher[0][1]:null |
|
Middle Name |
initials |
|
OrclGuid |
__UID__ |
|
Status[TRUSTED] |
__ENABLE__ |
|
User Login |
uid |
The Lookup.EDIR.UM.ReconAttrMap.Trusted lookup definition maps user fields of the OIM User form with corresponding field names in the Novell eDirectory target system. This lookup definition is used for performing trusted source reconciliation runs.
Table 1-35 lists the user identity fields whose values are fetched from the eDirectory target system during a trusted source reconciliation run.
Table 1-35 Entries in the Lookup.EDIR.UM.ReconAttrMap.Trusted Lookup Definition
| OIM User Form Field | Target System Field |
|---|---|
|
Department Number |
departmentNumber |
|
|
|
|
entryDN[IGNORE] |
entryDN |
|
Fax |
facsimileTelephoneNumber |
|
First Name |
givenName |
|
GUID |
__UID__ |
|
Last Name |
sn |
|
location |
l |
|
Pager |
pager |
|
parentDN[IGNORE] |
__PARENTDN__ |
|
Postal Address |
postalAddress |
|
Postal Code |
postalCode |
|
Status[TRUSTED] |
__ENABLE__ |
|
Street |
street |
|
Telephone |
telephoneNumber |
|
Title |
title |
|
User ID |
entryDN |
1.11.2 Reconciliation Rule for Trusted Source Reconciliation
Reconciliation rule for trusted source reconciliation is described in the following topics:
See Also:
Reconciliation Engine in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about reconciliation matching and action rules
1.11.2.1 About Reconciliation Rule for Trusted Source Reconciliation
The following are the process matching rules:
-
LDAP Rule element: User Login Equals User Login
-
OID Rule element: User Login Equals User Login
-
eDirectory Rule element: (GUID Equals GUID) OR (User Login Equals User ID)
For eDirectory, if the attribute match does not occur, second level matching is done based on User Login.
In this rule element:
-
User Login is the User Login field on the OIM User form.
-
User Login is the uid field of the target system.
1.11.3 Reconciliation Action Rules for Trusted Source Reconciliation
Reconciliation actions rules for trusted source reconciliation is described in the following topics:
1.11.3.1 About Reconciliation Action Rules for Trusted Source Reconciliation
Table 1-36 lists the action rules for trusted source reconciliation.
Table 1-36 Action Rules for Trusted Source Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. See
in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about setting a reconciliation action rule.
1.12 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Deploying the Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the Connector provides information that is common to all target systems.
-
Using the Connector with Oracle Directory Server Enterprise Edition provides information about using the connector with Oracle Directory Server Enterprise Edition (ODSEE).
-
Using the Connector with Oracle Unified Directory provides information about using the connector with Oracle Unified Directory (OUD).
-
Using the Connector with Oracle Internet Directory provides information about using the connector with Oracle Internet Directory (OID).
-
Using the Connector with Novell eDirectory provides information about using the connector with Novell eDirectory.
-
Using the Connector with an LDAPv3 Compliant Directory provides information about using the connector with an with an LDAPv3 compliant directory.
-
Extending the Functionality of the Connector describes procedures that you can perform if you want to extend the functionality of the connector.
-
Troubleshooting lists solutions to errors that you may encounter while using the connector.
-
Known Issues and Workarounds lists known issues associated with this release of the connector.