1 About the SAP SuccessFactors Connector
Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with the external and identity-aware applications. The SAP SuccessFactors connector integrates Oracle Identity Manager with the SuccessFactors target system.
This chapter contains the following sections:
1.1 Introduction to the SAP SuccessFactors Connector
Oracle Identity Manager is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premise or on the Cloud. The SAP SuccessFactors connector enables you to use SuccessFactors either as a managed (target) resource or as an authoritative (trusted) source of identity data for Oracle Identity Manager.
Note:
At some places in this guide, SAP SuccessFactors has been referred to either as the target system or as SuccessFactors.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. This data is used to add or modify resources (that is, accounts) allocated to Oracle Identity Manager Users. In addition, you can use Oracle Identity Manager to provision or update SuccessFactors resources (accounts) assigned to Oracle Identity Manager Users. These provisioning operations performed on Oracle Identity Manager translate into the creation or updates to target system accounts.
In the identity reconciliation (trusted source) mode of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
1.2 Certified Components for the SAP SuccessFactors Connector
These are the software components and their versions required for installing and using the SuccessFactors connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Manager:
|
|
Target systems |
SAP SuccessFactors |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or Later |
1.3 Certified Languages for the SAP SuccessFactors Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.4 Architecture of the SAP SuccessFactors Connector
The SuccessFactors connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that is required in order to use Identity Connector. ICF provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as, buffering, time outs, and filtering. ICF is distributed together with Oracle Identity Manager. Therefore, you do not need to configure or modify ICF.
Figure 1-1 shows the architecture of the SuccessFactors connector.
Figure 1-1 Architecture of the SuccessFactors Connector
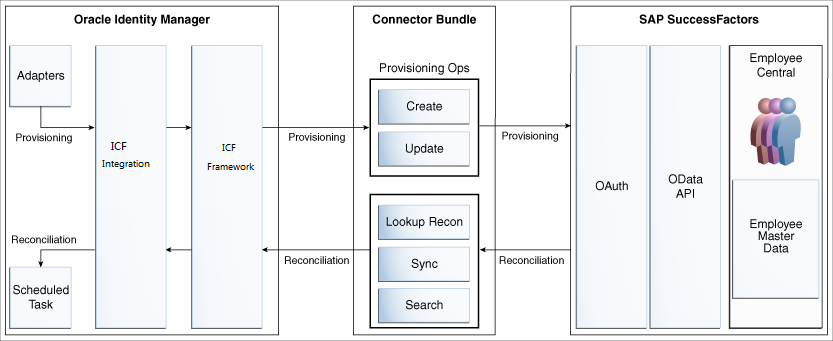
Description of "Figure 1-1 Architecture of the SuccessFactors Connector"
-
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this mode, the target system is used as the trusted source and users are directly created and modified on it. During reconciliation, a scheduled task invokes an ICF operation. ICF inturn invokes a search operation on the SuccessFactors Connector Bundle and then the bundle calls the OData API for reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Manager.
Each user record fetched from the target system is compared with existing Oracle Identity Manager Users. If a match is found between the target system record and the Oracle Identity Manager User, then the Oracle Identity Manager User attributes are updated with changes made to the target system record. If no match is found, then the target system record is used to create an Oracle Identity Manager User.
-
Account management
Account management is also known as target resource management. In this mode, the target system is used as a target resource and the connector enables the following operations:
-
Provisioning
Provisioning involves creating and updating users on the target system through Oracle Identity Manager. During provisioning, the adapters invoke ICF operation, ICF inturn invokes create operation on the SuccessFactors Identity Connector Bundle and then the bundle calls the target system API for provisioning operations. The API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters.
-
Target resource reconciliation
During reconciliation, a scheduled task invokes an ICF operation. ICF inturn invokes a search operation on the SuccessFactors Identity Connector Bundle and then the bundle calls the target system API for reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Manager.
Each record fetched from the target system is compared with SuccessFactors resources that are already provisioned to Oracle Identity Manager Users. If a match is found, then the update made to the SuccessFactors record from the target system is copied to the SuccessFactors resource in Oracle Identity Manager. If no match is found, then the user ID of the record is compared with the user ID of each Oracle Identity Manager User. If a match is found, then data in the target system record is used to provision a SuccessFactors resource to the Oracle Identity Manager User.
-
See Also:
Understanding the Identity Connector Framework in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager
1.5 Use Cases Supported by the Connector
The SAP SuccessFactors application uses the Software as a Service (SaaS) model and supports full human resource lifecycle functions on a single platform. The SAP SuccessFactors application allows an organization to make various data-driven people management decisions. The SAP SuccessFactors connector integrates Oracle Identity Manager with SuccessFactors application.
The SAP SuccessFactors connector standardizes service processes and implements automation to replace manual tasks. The SuccessFactors connector enables you to use SuccessFactors either as a managed (target) resource or as an authoritative (trusted) source of identity data for Oracle Identity Manager. Multiple instances of SuccessFactors solution can use a single connector bundle.
User Management is an example scenario which the SuccessFactors connector facilitates:
User Management
An organization using SuccessFactors wants to integrate with Oracle Identity Manager to manage the employee provisioning operations. The organization wants to manage its employee information (add and update functions) by creating them in the target system using Oracle Identity Manager. The organization also wants to synchronize employee updates performed directly in the target system with Oracle Identity Manager. In such a scenario, a quick and an easy way is to install the SuccessFactors connector and configure it with your target system by providing connection information in the IT resource.
The SuccessFactors connector is used to manage various employee attributes such as email id, hire-date, and job-level.
1.6 Features of the SAP SuccessFactors Connector
The features of the connector include support for connector server, full reconciliation, incremental reconciliation, limited reconciliation, and reconciliation of updates to account data.
1.6.1 Full and Incremental Reconciliation
After you create the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, you can configure your connector for incremental reconciliation. In incremental reconciliation, only records that are added or modified after the last reconciliation run are fetched into Oracle Identity Manager.
Note:
The connector supports incremental reconciliation if the target system contains an attribute that holds the timestamp at which an object is created or modified.See Full and Incremental Reconciliation for the SAP SuccessFactors Connector
1.6.2 Support for Trusted Source Reconciliation
The SuccessFactors connector can be configured as a trusted source for reconciliation of records into Oracle Identity Manager.
See Reconciliation Scheduled Jobs for the SAP SuccessFactors Connector.
1.6.3 Limited Reconciliation
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled.
You can set a reconciliation filter as the value of the Filter Suffix attribute of the user reconciliation scheduled job. The Filter Suffix attribute helps you to assign filters to the API based on which you get a filtered response from the target system.
See Limited Reconciliation for the SAP SuccessFactors Connector
1.6.4 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager
1.6.5 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation.
The following sections provide more information:
1.7 Lookup Definitions Used During Reconciliation and Provisioning
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
Lookup definitions used during connector operations can be categorized as follows:
1.7.1 Lookup Definitions Synchronized with the Target System
During a provisioning operation, you use a lookup field on the process form to select a single value from a set of values. For example, you may want to select a supervisor from the Supervisor lookup field to specify the supervisor being assigned to the user.
When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to specific fields in the target system to lookup definitions in Oracle Identity Manager.
After you deploy the connector, the following lookup definitions, which are used as an input source for lookup fields, are automatically created in Oracle Identity Manager:
-
Lookup.SuccessFactors.Joblevel
-
Lookup.SuccessFactors.Supervisor
-
Lookup.SuccessFactors.HR
These lookup definitions are empty by default. They are populated with values fetched from the target system when you run the scheduled jobs for lookup field synchronization. For example, when you run the scheduled job for Joblevel lookup field synchronization, all job levels on the target system are fetched to Oracle Identity Manager and populated in the Lookup.SuccessFactors.Joblevel lookup definition.
After lookup field synchronization, data in each of the lookup definitions for lookup field synchronization is stored in the following format:
-
Code Key: <IT_RESOURCE_KEY>~<LOOKUP_FIELD_VALUE>
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the connector attribute value defined for code.
101~VP-MKT. In this example,101is the numeric code assigned to the IT resource associated with the target system. -
-
Decode: <IT_RESOURCE_KEY>~<LOOKUP_FIELD_VALUE_ID>
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to an IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE_ID is the ID of the target system field value
For example, for the Lookup.SuccessFactors.HR lookup definition, the decode value for one of its entries is
121~fjones. In this example,121is the numeric code assigned to the IT resource associated with the target system andfjonesis the ID of the HR associate in the target system.
-
Table 1-2 Sample Entries in the Lookup.SuccessFactors.Joblevel Lookup Definition
| Code Key | Decode |
|---|---|
|
101~VP-MKT |
SuccessFactors~Vice President of Marketing |
|
101~SALES-ENG |
SuccessFactors~Sales Engineer |
|
101~STORE-MAN |
SuccessFactors~Store Manager |
|
101~FIN-DIR |
SuccessFactors~Director, Finance |
1.7.2 Preconfigured Lookup Definitions
Preconfigured lookup definitions are automatically created in Oracle Identity Manager after you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
The preconfigured lookup definitions are as follows:
1.7.2.1 Lookup.SuccessFactors.Configuration
The Lookup.SuccessFactors.Configuration lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
Table 1-3 Entries in the Lookup.SuccessFactors.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
| lookupUrl | /odata/v2/FOJobCode?$select=externalCode,name,jobFunction,jobLevel |
This the endpoint URL used to reconcile lookup data from the target system. Sample URL format: |
| upsertUrl |
/odata/v2/upsert |
This entry holds the value of endpoint URL that is used for performing any upsert operation on the user account. Sample URL format: |
| reconUrl |
/odata/v2/User?$format=JSON&$filter=status%20ne%20'p' |
This entry holds the value of endpoint URL that is used to reconcile users from the target resource. Sample URL format: |
| User Configuration Lookup |
Lookup.SuccessFactors.UM.Configuration |
This entry holds the name of the lookup definition that stores configuration information used during user management operations. |
| userUrl |
/odata/v2/User |
This entry holds the value of endpoint URL that is used to perform the create user operation. Sample URL format: |
| Bundle Name |
org.identityconnectors.successfactors |
This entry holds the name of the connector bundle. |
| Bundle Version |
1.0.11150 |
This entry holds the version of the connector bundle. |
| Connector Name |
org.identityconnectors.successfactors.SuccessFactorsConnector |
This entry holds the name of the connector. |
| customURIs | "EmpJob=/odata/v2/ EmpJob?$filter=userId%20eq %20'(Username)'", "PerPersonal=/odata/v2/ PerPersonal? $filter=personIdExternal %20eq%20'(Username)'", "UserEntity=/odata/v2/ User?$filter=status%20ne %20'p'%20and%20userId %20eq%20'(Username)'", "EmpEmployment=/ odata/v2/EmpEmployment? $filter=userId%20eq %20'(Username)'", "PerPerson=/odata/v2/ PerPerson? $filter=personIdExternal %20eq%20'(Username)'" | This entry holds a comma separated list of relative URLs for all object entities.
Sample URL format: Here the sample URI is used to filter information for a particular object, which in the above sample URL is the |
| objectMetadatas | "UserEntity={\""uri\"":\""User('Username')\""}",
"PerPerson={\""uri\"":\""PerPerson('Username')\"}", "EmpEmployment={\""uri\"":\""EmpEmployment(personIdExternal='Username',userId='Username')\"}", "EmpJob={\""uri\"":\""EmpJob(userId='Username',startDate=datetime'DateTime')\"}", "PerPersonal={\"uri\":\""PerPersonal(personIdExternal='Username',startDate=datetime'DateTime')\"}" |
This entry holds a comma separated list of object metadata information. During provisioning, each object requires a metadata entry in the payload. The metadata value is unique for each object entity. Sample objectMetadatas: For the
|
| childFields | "phone=phone~phoneType~phoneNumber~isPrimary" | To manage multi-valued attributes, you need to add this entry. This entry holds a comma separated list of child field entries. This field is an embedded object defined in the attribute mapping.
Note: This is an optional field. Syntax: Child Field name in Resource Object=Child Field Object Class~API names of child field attributes in process form seperated by ~ . |
1.7.2.2 Lookup.SuccesFactors.UM.Configuration
The Lookup.SuccesFactors.UM.Configuration lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during user management operations.
Table 1-4 Entries in the Lookup.SuccesFactors.UM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.SuccesFactors.UM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. This lookup definition is used during user provisioning operations. |
|
Recon Attribute Map |
Lookup.SuccesFactors.UM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. This lookup definition is used during reconciliation. |
1.7.2.3 Lookup.SuccessFactors.UM.ProvAttrMap
The Lookup.SuccessFactors.UM.ProvAttrMap lookup definitions hold mappings between process form fields and target system attributes.
This lookup definition is preconfigured and used during provisioning. Table 1-27 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Adding New Attributes for Provisioning.
Table 1-5 Entries in the Lookup.SuccessFactors.UM.ProvAttrMap Lookup Definition
| User Field on Oracle Identity Manager | SuccessFactors Field |
|---|---|
|
Supervisor[LOOKUP] |
EmpJob.managerId |
|
Business Unit |
EmpJob.businessUnit |
|
Citizenship |
UserEntity.citizenship |
|
City |
UserEntity.city |
|
Company |
EmpJob.company |
|
Country |
UserEntity.country |
|
HR[LOOKUP] |
UserEntity.hr |
|
Location |
EmpJob.location |
|
Married |
UserEntity.married |
|
Password |
UserEntity.password |
|
Hire Date[DATE] |
EmpEmployment.startDate |
|
State |
UserEntity.state |
|
Person Id |
__UID__ |
|
Username |
__NAME__ |
|
Status |
__ENABLE__ |
|
Department |
EmpJob.department |
|
Division |
EmpJob.division |
|
|
UserEntity.email |
|
Employee Id |
UserEntity.empId |
|
Event Reason |
EmpJob.eventReason |
|
First Name |
PerPersonal.firstName |
|
Gender |
PerPersonal.gender |
|
Job Classification |
EmpJob.jobCode |
|
Job Level |
UserEntity.jobLevel |
|
Last Name |
PerPersonal.lastName |
1.7.2.4 Lookup.SuccessFactors.UM.ReconAttrMap
The Lookup.SuccessFactors.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes.
This lookup definition is preconfigured and used during target resource reconciliation. Table 1-24 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for target resource reconciliation. See Adding New User Attributes for Reconciliation.
1.7.2.5 Lookup.SuccessFactors.UM.Configuration.Trusted
The Lookup.SuccessFactors.UM.Configuration.Trusted lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during trusted source user reconciliation runs.
Table 1-6 Entries in the Lookup.SuccessFactors.UM.Configuration.Trusted Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Recon Attribute defaults |
Lookup.SuccessFactors. UM.ReconAttrMap.TrustedDefaults |
This entry holds the name of the lookup definition that maps reconciliation fields to their default values. This lookup definition is discussed later in this guide. |
|
Recon Attribute Map |
Lookup.SuccessFactors. UM.ReconAttrMap.Trusted |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. This lookup definition is discussed later in this guide. |
1.7.2.6 Lookup.SuccessFactors.UM.ReconAttrMap.TrustedDefaults
The Lookup.SuccessFactors.UM.ReconAttrMap.Trusted.Defaults lookup definition holds mappings between reconciliation fields and their default values.
This lookup definition is used when there is a mandatory field on the Oracle Identity Manager User form, but no corresponding field in the target system from which values can be fetched during trusted source reconciliation. This is explained in the following example.
For example, Employee Type is a mandatory field on the Oracle Identity Manager User form. The target system contains no field that stores information about the employee type for a user account. During reconciliation, no value for the Employee Type field is fetched from the target system. However, as the Employee Type field cannot be left empty, the connector uses the decode value of the Employee Type entry of this lookup definition. This implies that the value of the Employee Type field on the Oracle Identity Manager User form displays Full-Time for all user accounts reconciled from the target system.
Table 1-7 lists the default entries in this lookup definition. Do not add or modify entries to this lookup definition.
Table 1-7 Entries in the Lookup.SuccessFactors.UM.ReconAttrMap.TrustedDefaults Lookup Definition
| Code Key (Resource Object Field) | Decode (SuccessFactors Field) |
|---|---|
|
Employee Type |
Full-Time |
|
Organization |
Xellerate Users |
|
User Type |
End-User |
1.7.2.7 Lookup.SuccessFactors.Configuration.Trusted
The Lookup.SuccessFactors.UM.Configuration.Trusted lookup definition holds configuration entries that are used during trusted source reconciliation.
Note:
Do not modify the entries in this lookup definition.Table 1-8 Entries in the Lookup.SuccessFactors.Configuration.Trusted
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.successfactors |
This entry holds the name of the connector bundle. |
|
Bundle Version |
1.0.11150 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.successfactors.SuccessFactorsConnector |
This entry holds the name of the connector. |
|
customURIs |
"EmpJob=/odata/v2/EmpJob?$filter=userId%20eq%20'(Username)'", "PerPersonal=/odata/v2/PerPersonal?$filter=personIdExternal%20eq%20'(Username)'", "UserEntity=/odata/v2/User?$filter=status%20ne%20'p'%20and%20userId%20eq%20'(Username)'", "EmpEmployment=/odata/v2/EmpEmployment?$filter=userId%20eq%20'(Username)'", "PerPerson=/odata/v2/PerPerson?$filter=personIdExternal%20eq%20'(Username)'" | This entry holds a comma separated list of relative URLs for all object entities.
Sample URL: Here the sample URI is used to filter information for a particular object, which in the above sample URL is the |
|
reconUrl |
/odata/v2/User?$format=JSON&$filter =status%20ne%20'p' |
This entry holds the value of endpoint URL that is used to reconcile users from the target resource. Sample URL Format: |
|
User Configuration Lookup |
Lookup.SuccessFactors.UM.Configuration.Trusted |
This entry holds the name of the lookup definition that stores configuration information used during user management operations. |
1.7.2.8 Lookup.SuccessFactors.UM.ReconAttrMap.Trusted
The Lookup.SuccessFactors.UM.ReconAttrMap.Trusted lookup definition holds mappings between resource object fields and target system attributes.
This lookup definition is preconfigured and used during trusted source user reconciliation runs. Table 1-9 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for trusted source reconciliation.
Table 1-9 Entries in the Lookup.SuccessFactors.UM.ReconAttrMap.Trusted
| Code Key | Decode |
|---|---|
|
|
UserEntity.email |
|
First Name |
PerPersonal.firstName |
|
Hire Date[DATE] |
EmpEmployment.startDate |
|
Last Name |
PerPersonal.lastName |
|
Person Id |
__UID__ |
|
Status |
__ENABLE__ |
|
Termination Date[DATE] |
EmpEmployment.endDate |
|
Username |
__NAME__ |
1.7.2.9 Lookup.SuccessFactors.Division
The Lookup.SuccessFactors.Division lookup definition holds values of all divisions that you can select for a user account.
Note:
Do not modify the entries in this lookup definition.Table 1-10 Entries in the Lookup.SuccessFactors.Division
| Code Key | Decode |
|---|---|
|
ENT |
Enterprises (ENT) |
|
HC |
Healthcare (HC) |
|
IND |
Industries (IND) |
|
SVC |
Professional Service (SVC) |
1.7.2.10 Lookup.SuccessFactors.Department
The Lookup.SuccessFactors.Department lookup definition contains information about department that you can select for a user account.
Table 1-11 Entries in the Lookup.SuccessFactors.Department
| Code Key | Decode |
|---|---|
|
CLNC-CR |
Community Relations (CLNC-CR) |
|
CLNC |
Clinical (CLNC) |
|
ALNCE |
Alliances (ALNCE) |
|
IND |
Industries (IND) |
|
CORP |
Enterprises (CORP) |
|
TALENT |
Talent Management (TALENT) |
1.7.2.11 Lookup.SuccessFactors.Married
The Lookup.SuccessFactors.Married lookup definition contains information about martial status (true or false) for a user account that you create through Oracle Identity Manager. You cannot add or modify entries in this lookup definition.
Table 1-12 Entries in the Lookup.SuccessFactors.Married
| Code Key | Decode |
|---|---|
| 1 | True |
| 0 | False |
1.7.2.12 Lookup.SuccessFactors.Citizenship
The Lookup.SuccessFactors.Citizenship lookup definition provides citizenship information for a user account that you create through Oracle Identity Manager.
Table 1-13 Entries in the Lookup.SuccessFactors.Citizenship
| Code Key | Decode |
|---|---|
| US | US |
| Canada | Canada |
| France | France |
| Germany | Germany |
1.7.2.13 Lookup.SuccessFactors.Gender
The Lookup.SuccessFactors.Gender lookup definition contains information about gender (female or male) information that you can select for a user account.
Table 1-14 Entries in the Lookup.SuccessFactors.Gender
| Code Key | Decode |
|---|---|
| F | Female |
| M | Male |
1.7.2.14 Lookup.SuccessFactors.Country
The Lookup.SuccessFactors.Country lookup definition contains information about countries that you can select for a user account.
Table 1-15 Entries in the Lookup.SuccessFactors.Country
| Code Key | Decode |
|---|---|
|
Australia |
Australia |
|
Canada |
Canada |
|
France |
France |
|
Germany |
Germany |
|
Italy |
Italy |
|
USA |
USA |
1.7.2.15 Lookup.SuccessFactors.State
The Lookup.SuccessFactors.State lookup definition contains information about various states which can be assigned for a user account created through Oracle Identity Manager.
Table 1-16 Entries in the Lookup.SuccessFactors.State
| Code Key | Decode |
|---|---|
| Alberta | Alberta |
| British Coloumbia | British Coloumbia |
| California | California |
1.7.2.16 Lookup.SuccessFactors.BussinessUnit
The Lookup.SuccessFactors.BussinessUnit lookup definition contains information about various business units (within an organization) that you create through Oracle Identity Manager.
Table 1-17 Entries in the Lookup.SuccessFactors.BussinessUnit
| Code Key | Decode |
|---|---|
| ACE_HC | Corporate Healthcare |
| ACE_IND | Corporate Industries |
1.7.2.17 Lookup.SuccessFactors.Company
The Lookup.SuccessFactors.Company lookup definition contains information about different companies (within an organization) that you create through Oracle Identity Manager.
Table 1-18 Entries in the Lookup.SuccessFactors.Company
| Code Key | Decode |
|---|---|
|
ACE_BRA |
Ace Brazil |
| ACE_CAN | Ace Canada Corp |
| ACE_USA | Ace USA |
1.7.2.18 Lookup.SuccessFactors.EventReason
The Lookup.SuccessFactors.EventReason lookup definition contains information regarding reasons for a certain event.
Table 1-19 Entries in the Lookup.SuccessFactors.EventReason
| Code Key | Decode |
|---|---|
|
HIRACQRE |
Acquired employee |
|
HIRAFFIL |
Hired from Affiliate |
1.7.2.19 Lookup.SuccessFactors.JobClassification
The Lookup.SuccessFactors.JobClassification lookup definition contains information about various job classification available for a user account that you create through Oracle Identity Manager.
Table 1-20 Entries in the Lookup.SuccessFactors.JobClassification
| Code Key | Decode |
|---|---|
| ACC-MGR | Account Manager |
| ADMIN-1 | Administrative Assistant |
|
ANALYST-IT |
Analyst |
1.7.2.20 Lookup.SuccessFactors.BooleanValues
The Lookup.SuccessFactors.BooleanValues lookup definition maps boolean values that are used for some of the fields in the target system with the corresponding boolean values to be displayed in the fields of Oracle Identity Manager User form.
Table 1-21 Entries in the Lookup.SuccessFactors.BooleanValues Lookup Definition
| Code Key (Resource Object Field) | Decode (SuccessFactors Field) |
|---|---|
|
T |
True |
|
F |
False |
1.7.2.21 Lookup.SuccessFactors.Location
The Lookup.SuccessFactors.Location lookup definition contains information about locations that you can select for a user account.
Table 1-22 Entries in the Lookup.SuccessFactors.Location
| Code Key | Decode |
|---|---|
|
US_SFO |
San Mateo (US_SFO) |
|
US_NYC |
New York (US_NYC) |
|
US_DCM |
Arlington, Virginia (US_DCM) |
|
US_ATL |
Atlanta (US_ATL) |
|
CN_BJS |
Beijing (CN_BJS) |
|
BR_SAO |
Sao Paolo (BR_SAO) |
1.7.2.22 Lookup.SuccessFactors.City
The Lookup.SuccessFactors.City lookup definition contains information about cities that you can select for a user account.
Table 1-23 Entries in the Lookup.SuccessFactors.City
| Code Key | Decode |
|---|---|
|
Sydney |
Sydney |
|
Sydney |
Seoul |
|
San Mateo |
San Mateo |
|
New York |
New York |
|
London |
London |
|
Beijing |
Beijing |
1.8 Connector Objects Used During Target Resource Reconciliation
Connector objects such as reconciliation rules, reconciliation action rules, and scheduled jobs are used for reconciling user records from the target system into Oracle Identity Manager.
The SuccessFactors Target Resource User Reconciliation scheduled job is used to initiate a reconciliation run. This scheduled job is discussed in Reconciliation Scheduled Jobs for the SAP SuccessFactors Connector.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for generic information about connector reconciliation
This section contains the following topics related to connector objects::
1.8.1 User Fields for Target Resource Reconciliation
The Lookup.SuccessFactors.UM.ReconAttrMap lookup definition maps resource object fields with target system attributes. This lookup definition is used for performing target resource user reconciliation runs.
In this lookup definition, entries are in the following format:
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system user attribute at the OData API level
Table 1-24 lists the entries in this lookup definition.
Table 1-24 Entries in the Lookup.SuccessFactors.UM.ReconAttrMap Lookup Definition
| Code Key (Resource Object Field) | Decode (SuccessFactors Field) |
|---|---|
|
Business Unit |
EmpJob.businessUnit |
|
Citizenship |
UserEntity.citizenship |
|
City |
UserEntity.city |
|
Company |
EmpJob.company |
|
Country |
UserEntity.country |
|
Department |
EmpJob.department |
|
Division |
EmpJob.division |
|
|
UserEntity.email |
|
Employee Id |
UserEntity.empId |
|
Event Reason |
EmpJob.eventReason |
|
First Name |
PerPersonal.firstName |
|
Gender |
PerPersonal.gender |
|
Hire Date[DATE] |
EmpEmployment.startDate |
|
HR[LOOKUP] |
UserEntity.hr |
|
Job Classification |
EmpJob.jobCode |
|
Job Level[LOOKUP] |
UserEntity.jobLevel |
|
Last Name |
PerPersonal.lastName |
|
Location |
EmpJob.location |
|
Married |
UserEntity.married |
|
Payroll End Date[DATE] |
EmpEmploymentTermination.payrollEndDate |
|
Person Id |
__UID__ |
|
State |
UserEntity.state |
|
Status |
__ENABLE__ |
|
Supervisor[LOOKUP] |
EmpJob.managerId |
|
Termination Date[DATE] |
EmpEmployment.endDate |
|
Username |
__NAME__ |
1.8.2 Reconciliation Rules for Target Resource Reconciliation
Reconciliation rules for target resource reconciliation involves target resource reconciliation rules for users and viewing of reconciliation rules for the target resource.
The following topics related to reconciliation rule for target resource reconciliation are discussed in this is section:
1.8.2.1 Target Resource Reconciliation Rules for Users
Reconciliation rules for target resource reconciliation are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
The following is the process-matching rule for users:
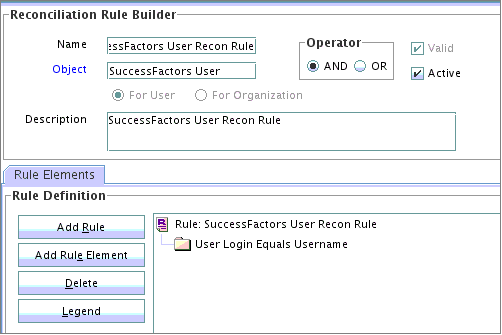
Rule name: SuccessFactors User Recon Rule
Rule element: User Login Equals Username
-
User Loginis the attribute of a user having a SuccessFactors account. -
Usernameis the unique ID attribute of the SuccessFactors user account.
1.8.2.2 Viewing Reconciliation Rules for Target Resource Reconciliation
After you deploy the connector, you can view the reconciliation rules for users on the Reconciliation Rule Builder form in Oracle Identity Manager Design Console.
1.8.3 Reconciliation Action Rules for Target Resource Reconciliation
Reconciliation action rules define the actions the connector must perform based on the reconciliation rules defined for users.
The following topics related to reconciliation action rules for target resource reconciliation are discussed in this section:
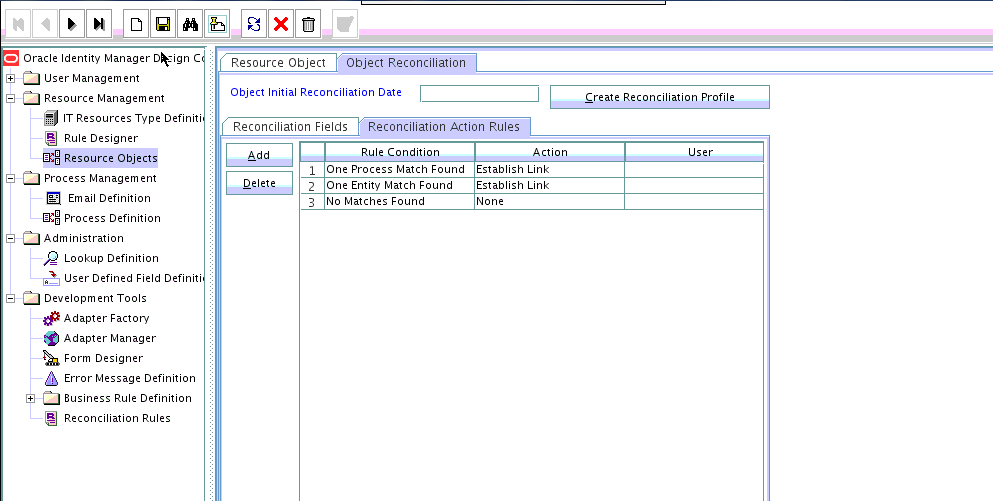
1.8.3.1 Target Resource Reconciliation Action Rules for Users
Reconciliation action rules specify the actions the connector must perform based on the result of the processing of a reconciliation event.
Table 1-25 Action Rules for Target Resource Reconciliation of Users
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Process Match Found |
Establish Link |
|
One Entity Match Found |
Establish Link |
1.8.3.2 Viewing Reconciliation Action Rules for Target Resource Reconciliation
After you deploy the connector, you can view reconciliation action rules on the Object Reconciliation tab of a resource object in Oracle Identity Manager Design Console.
1.9 Connector Objects Used During Provisioning
Connector objects such as adapters are used for performing provisioning operations on the target system. These adapters perform provisioning functions on the fields defined in the lookup definition for provisioning.
The following topics are discussed in this section:
1.9.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the SuccessFactors connector.
The Adapter column in Table 1-26 gives the name of the adapter that is used when the function is performed.
Table 1-26 User Provisioning Functions
| Function | Adapter |
|---|---|
|
Create User |
SuccessFactors Create Object |
|
Update User |
SuccessFactors Update Object |
| Enable User | SuccessFactors Enable Object |
| Disable User | SuccessFactors Disable Object |
See Also:
Types of Adapters in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about process tasks and adapters
1.9.2 User Fields for Provisioning
The Lookup.SuccessFactors.UM.ProvAttrMap lookup definition holds the user fields for provisioning. This lookup definition holds mapping between process form fields and target system attributes.
In this lookup definition, entries are in the following format:
-
Code Key: Name of the process form field
-
Decode: Name of the target system user attribute at the OData API level
Table 1-27 lists the entries in this lookup definition.
Table 1-27 Entries in the Lookup.SuccessFactors.UM.ProvAttrMap Lookup Definition
| Code Key (Process Form Field) | Decode (SuccessFactors Field) |
|---|---|
|
Supervisor [LOOKUP] |
EmpJob.managerId |
|
Business Unit |
EmpJob.businessUnit |
|
Citizenship |
UserEntity.citizenship |
|
City |
UserEntity.city |
|
Company |
EmpJob.company |
|
Country |
UserEntity.country |
|
HR[LOOKUP] |
UserEntity.hr |
|
Location |
EmpJob.location |
|
Password |
UserEntity.password |
|
Hire Date[DATE] |
EmpEmployment.startDate |
|
State |
UserEntity.state |
|
Time Zone |
UserEntity.timeZone |
|
Person Id |
__UID__ |
|
Username |
__NAME__ |
|
Status |
UserEntity.status |
|
Department |
EmpJob.department |
|
Division |
EmpJob.division |
|
|
UserEntity.email |
|
Employee Id |
UserEntity.empId |
|
Event Reason |
EmpJob.eventReason |
|
First Name |
PerPersonal.firstName |
|
Gender |
PerPersonal.gender |
|
Job Classification |
EmpJob.jobClassification |
|
Job Level |
UserEntity.jobLevel |
|
Last Name |
PerPersonal.lastName |
For information about understanding and customizing the OData API Dictionary, see Understanding OData API Dictionary.
1.10 Connector Objects Used During Trusted Source Reconciliation
Connector objects such as reconciliation rules, reconciliation action rules, and scheduled jobs are used for reconciling user records from the target system into Oracle Identity Manager.
The SuccessFactors Trusted User Reconciliation scheduled task is used to initiate a trusted source reconciliation run. This scheduled task is discussed in SAP SuccessFactors User Reconciliation.
The following connector objects are discussed in this section:
1.10.1 User Fields for Trusted Source Reconciliation
The Lookup.SuccessFactors.UM.ReconAttrMap.Trusted lookup definition maps user fields of the Oracle Identity Manager User form with corresponding field names in the target system. This lookup definition is used for performing trusted source reconciliation runs. Values for the user identity fields in this lookup definition are fetched from the target system during a trusted source reconciliation run.
Table 1-28 Entries in the Lookup.SuccessFactors.UM.ReconAttrMap.Trusted Lookup Definition
| Code Key (Resource Object Field) | Decode (SuccessFactors Field) |
|---|---|
|
|
UserEntity.email |
|
First Name |
PerPersonal.firstName |
|
Hire Date[DATE] |
EmpEmployment.startDate |
|
Last Name |
PerPersonal.lastName |
|
Person Id |
__UID__ |
|
Status |
__ENABLE__ |
|
Termination Date[DATE] |
EmpEmployment.endDate |
|
Username |
__NAME__ |
1.10.2 Reconciliation Rule for Trusted Source Reconciliation
Reconciliation rule for trusted source reconciliation is invoked when Oracle Identity Manager tries to determine the user record that is associated with a change on your target system (a trusted source).
The following topics related to reconciliation rule for trusted source reconciliation are discussed in this section:
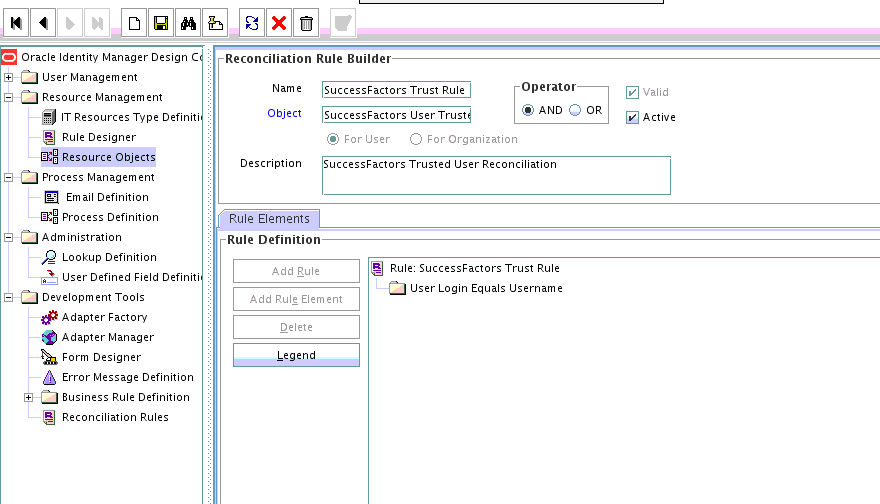
1.10.2.1 Trusted Source Reconciliation Rule for Users
Reconciliation rule for trusted source reconciliation is invoked when Oracle Identity Manager tries to determine the user record that is associated with a change on your target system (a trusted source).
The following is the entity matching rule for users:
Rule name: SuccessFactors User Trust Rule
Rule element: (User Name Equals User Login) OR (SuccessFactors GUID Equals Object Id)
-
User Nameis the Person Id field of the OIM user form. -
User Loginis the unique login name of a user.
-
SuccessFactors GUIDis UDF (user-defined field) for mapping target object ID with an OIM User -
Object Idis the Object Id for a SuccessFactors user.
1.10.3 Reconciliation Action Rules for Trusted Source Reconciliation
Reconciliation action rules specify the actions the connector must perform based on the result of the processing of a reconciliation event.
The following topics related to reconciliation action rules are discussed in this section:
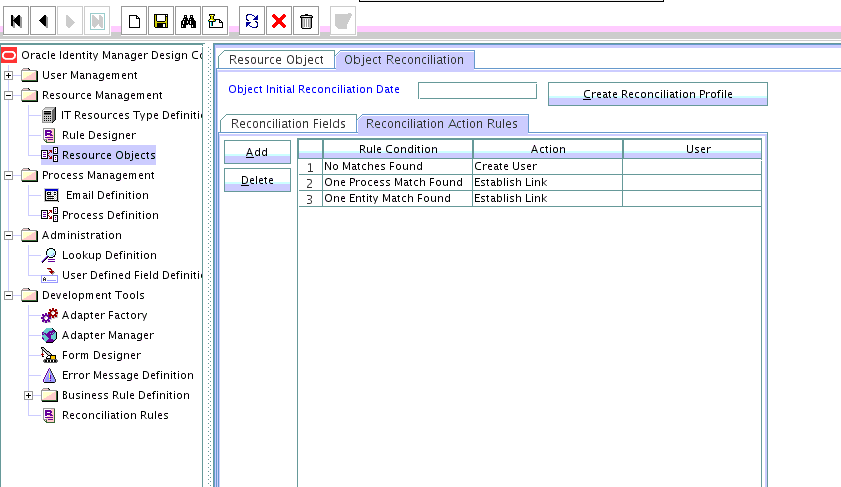
1.10.3.1 Trusted Source Reconciliation Action Rules for Users
Reconciliation action rules specify the actions the connector must perform based on the result of the processing of a reconciliation event.
Table 1-29 Action Rules for Trusted Source Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
1.10.3.2 Viewing Reconciliation Action Rules for Trusted Source Reconciliation
After you deploy the connector, you can view reconciliation action rules on the Object Reconciliation tab of a resource object in Oracle Identity Manager Design Console.
1.11 Roadmap for Deploying and Using the SAP SuccessFactors Connector
This is the organization of information available in this guide for deploying and using the connector.
The rest of this guide is divided into the following chapters:
-
Deploying the SAP SuccessFactors Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the SAP SuccessFactors Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the SAP SuccessFactors Connector describes procedures that you can perform if you want to extend the functionality of the connector.
-
Known Issues and Workarounds for the SAP SuccessFactors Connector lists known issues associated with this release of the connector.
-
Files and Directories on the SAP SuccessFactors Connector Installation Media lists the files and directories that comprise the connector installation media.