Secure Configuration Console
Overview
The Secure Configuration Console consolidates secure configuration checks in one dashboard. It ensures that high priority security configuration problems can be reviewed, understood, and remediated.
After you upgrade to the latest ATG_PF Release Update Pack, your system will be "locked down" until a local system administrator resolves or acknowledges the recommended security configurations in the Secure Configuration Console.
To access this console, a user must have a responsibility that includes the Applications System (OAM_APP_SYSTEM) function privilege, such as the seeded System Administration or System Administrator responsibilities, and must be registered as a local user with Oracle E-Business Suite. The administrator must log in to Oracle E-Business Suite using the local login page (http(s)://[host]:[port]/OA_HTML/AppsLocalLogin.jsp) to navigate to the console and unlock the system. If a user with local system administrator privileges is not available, you can access the Secure Configuration Console through a command line utility (described later in this section).
Once the system is unlocked for normal usage, the Secure Configuration Console is still available for administrators under the Functional Administrator responsibility.
Feature Overview
The Secure Configuration Console provides:
-
Restricted login
-
Login into the system is completely restricted in "Locked Down" mode.
-
Access to the system is provided by performing the recommended secure configuration or acknowledging secure configuration recommendations.
-
-
A single view of the system's security health
-
Consolidated view of all security recommendations for different layers such as network, database, and application.
-
View detailed descriptions of security configurations.
-
Review the current status, severity level, and type (autofixable/manual) of security configurations.
-
Provides complete picture of security health of the system.
-
-
Secure configuration management
-
Analyzes the current state of the configuration.
-
Resolves on-the-fly autofixable secure configurations as per Oracle E-Business Suite recommendations.
-
Mute or unmute the configurations as per administrator choice.
-
Benefits
Automating the high priority security configuration process provides the following benefits:
-
Security threats are prevented by ensuring secured configuration of the system.
-
Security vulnerabilities can be resolved as entry into the system is prevented until it is reviewed for security configuration.
-
All high-priority Oracle E-Business Suite secure configurations are available to review in one place.
-
Manual configurations, which are cumbersome and error-prone, are minimized.
-
Management of configurations is quick and easy.
Using the Secure Configuration Console
There are two methods to access the Secure Configuration Console home page.
-
Using the Functional Administrator responsibility:
On the Oracle E-Business Suite home page, select the Functional Administrator responsibility in the Navigator pane. Then, on the Functional Administrator page, select the Configuration Manager tab.
-
Using the OAM Security Dashboard:
On the Oracle E-Business Suite home page, select System Administrator in the Navigator pane. Then select Oracle Applications Manager, then OAM Security Dashboard. On the dashboard, under the Configuration Management section is a link to the Secure Configuration Console.
The Secure Configuration Console bases its recommendations on recommended security guidelines. They are listed in more detail in the following section, Checked Security Guidelines.
You can search for a recommendation by guideline, code, configuration type, status, or level of severity in the Search section or by perusing through the table itself.
The following actions are available:
-
Check - Discover the status of selected guideline check before configuring
-
Fix - Resolve the status of a selected failed guideline check
-
Suppress - Mute guidelines that are not relevant to your system
-
Unsuppress - Unmute previously suppressed guidelines
-
Check All - Discover the status of all unsuppressed guidelines
Checked Security Guidelines
The Secure Configuration Console currently checks the following high priority secure configuration guidelines.
Updates to the checks performed by the Secure Configuration Console are delivered with Oracle E-Business Suite ATG Release Updates (RUPs) or Critical Patch Updates (CPUs). We highly recommend that you apply the latest ATG RUP or latest CPU to ensure that all recommended secure configuration checks are available for your environment. See the following My Oracle Support knowledge documents for more information:
-
Document 1583092.1, Oracle E-Business Suite Release 12.2: Suite-Wide Release Update Pack and AD/TXK Delta Information
-
Document 2484000.1, Identifying the Latest Critical Patch Update for Oracle E-Business Suite Release 12.2
If you are not running the latest release of the Secure Configuration Console, see Obsolete Secure Configuration Console Checks for Security Guidelines for obsolete checks which may still be running in your environment.
If any of the guidelines listed in the following tables fail the secure configuration check, you can either fix or suppress the failure. For a secure environment, Oracle recommends that you address all failures that are applicable to your environment.
The following tables, organized by severity, list the security checks made by the Secure Configuration Console and the releases in which they are made available. Full descriptions of each security check are found in the sections that follow.
| Security Check | Available as of the Listed Release and Later |
|---|---|
| Allowed Resources is enabled. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Application users default passwords have been changed to non-default values. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Attachment upload profiles are available and set correctly. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Clickjacking protection is configured. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Critical security profile values are set correctly. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Database users default passwords have been changed to non-default values. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Diagnostic web page protection is configured. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Forms blocking of bad characters on the web server is active. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| ModSecurity on the web server is active. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Oracle E-Business Suite CPU patch level is the expected level or later. | EBS Release 12.2.11 or R12.ATG_PF.C.Delta.10 |
| PUBLIC role privileges are restricted. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Site level server security profiles are available in the system. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| WebLogic Server default admin user password has been changed to non-default value. | EBS Release 12.2.9 or R12.ATG_PF.C.Delta.8 |
| Workflow generated emails that reference URLs in EBS require additional user authentication. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Security Check | Available as of the Listed Release and Later |
|---|---|
| Allowed Redirects is enabled. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Allowed Resources that are unused are denied. | EBS Release 12.2.11 or R12.ATG_PF.C.Delta.10 |
| Application users passwords have been migrated to hash passwords. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| APPLSYSPUB privileges are properly restricted. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Auditing profiles are correctly set. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Cookie Domain scoping is configured. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Database initialization parameters have been set to recommended values. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Database Network Access List (ACL) is configured. | EBS Release 12.2.10 or R12.ATG_PF.C.Delta.9 |
| Database profiles have been created in the EBS database for database user password management. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| FND Generic File Manager (FNDGFM) Authorization is properly configured. | EBS Release 12.2.11 or R12.ATG_PF.C.Delta.10 |
| HTTPS is enabled. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| iRecruitment file upload security profile value is set. | EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7 |
| Server security (Secure Flag in DBC file) is enabled. | EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6 |
| Unified Auditing is enabled. | EBS Release 12.2.15 or R12.ATG_PF.C.Delta.14 |
| Workflow Admin access is restricted. | EBS Release 12.2.9 or R12.ATG_PF.C.Delta.8 |
Security Check Details
The following sections provide more details on each Secure Configuration Console security check listed in the previous tables, including the security check name as found in the console, a description of the check, the internal code name, and so on. If any of the checks fail, you can either fix or suppress the failure. See the "Next Steps" listed in each check for further information and instructions.
For a secure environment, Oracle recommends that you address all failures that are applicable to your environment.
Allowed Resources is Enabled
-
Security Guideline: Allowed Resources Configuration
-
Description: Check whether the Allowed Resources feature is enabled.
-
Code: FND_JSP_UNRE ST_ACC
-
Severity: 1
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See Allowed Resources.
Application Users Default Passwords Have Been Changed to Non-Default Values
-
Security Guideline: Application Users Default Password
-
Description: Check whether all application users' default passwords have been changed to non-default values.
-
Code: FND_APPS_DEF_PSWD
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Changing Passwords for Seeded Application User Accounts.
Attachment Upload Profiles are Available and Set Correctly
-
Security Guideline: Attachment File Type Profiles
-
Description: Check whether attachment upload profiles are available and set correctly in the system.
-
Code: FND_MISS_ATT_PROF
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Securing Attachments.
Clickjacking Protection is Configured
-
Security Guideline: Clickjacking Protection
-
Description: Check whether clickjacking protection is configured.
-
Code: CLICKJACK_PROTECTION
-
Severity: 1
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See Using Certified HTTP Security Headers.
Critical Security Profile Values are Set Correctly
-
Security Guideline: Critical Security Profile Values
-
Description: Check whether critical security profile values are set correctly at all levels (for example: site, responsibility, user).
In addition to verifying that critical security profile values are set as recommended, as of EBS Release 12.2.15 or R12.ATG_PF.C.Delta.14 this check now confirms that the Developer Console is disabled.
-
Code: FND_PROF_ERRORS
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Setting Other Security-Related Profile Options.
Database Users Default Passwords Have Been Changed to Non-Default Values
-
Security Guideline: Database Users Default Passwords
-
Description: Check whether all database users default passwords have been changed.
As of EBS Release 12.2.15 or R12.ATG_PF.C.Delta.14, this check now validates password changes only for Oracle Database 11g Release 2 (11.2.0.4) and later. It no longer checks database releases prior to 11.2.0.4.
-
Code: FND_DB_DEF_PSWD
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See the following for more information.
-
My Oracle Support Knowledge Document 361482.1, Frequently Asked Questions about Oracle Default Password Scanner
Diagnostic Web Page Protection is Configured
-
Security Guideline: Diagnostic Web Pages Protected
-
Description: Check whether diagnostic web page protection is configured.
-
Code: DIAG_WEB_PAGE_PROTEC
-
Severity: 1
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See Protecting Diagnostic Pages.
Forms Blocking of Bad Characters on the Web Server is Active
-
Security Guideline: Forms Blocking of Bad Characters
-
Description: Check whether the Forms blocking of "bad" characters on the web server is active.
-
Code: FND_FORMS_BLOCK_CHR
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: If this check fails, log a Service Request (SR) in My Oracle Support. Reference the Secure Configuration Console and the failed Forms Blocking of Bad Characters check.
ModSecurity on the Web Server is Active
-
Security Guideline: ModSecurity Configuration
-
Description: Check whether ModSecurity on the web server is active.
-
Code: FND_MOD_SEC
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: If this check fails, log a Service Request (SR) in My Oracle Support. Reference the Secure Configuration Console and the failed ModSecurity Configuration check.
Oracle E-Business Suite CPU Patch Level is the Expected Level or Later
-
Security Guideline: Oracle E-Business Suite CPU Patch Level Check
-
Description: Check whether the Oracle E-Business Suite Critical Patch Update patch in the system is greater or equal to the configured value of the FND_SEC_MIN_CPU_PATCH_LEVEL (FND: Minimum CPU Patch Level) profile option.
As of EBS Release 12.2.15 or R12.ATG_PF.C.Delta.14, this check now defaults to verifying that the latest quarterly Critical Patch Update (CPU) has been applied to your environment.
-
Code: FND_MIN_CPU_LEVEL
-
Severity: 1
-
Availability: EBS Release 12.2.11 or R12.ATG_PF.C.Delta.10
-
Next Steps: See My Oracle Support Knowledge Document 2484000.1, Identifying the Latest Critical Patch Update for Oracle E-Business Suite Release 12.
PUBLIC Role Privileges are Restricted
-
Security Guideline: PUBLIC Privileges
-
Description: Check whether the PUBLIC role privileges are restricted.
-
Code: FND_APPS_IND_PUBLIC
-
Severity: 1
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: This checks whether unnecessary privileges to Oracle E-Business Suite object have been granted to the Oracle Database PUBLIC role. You should revoke unnecessary privileges from the PUBLIC role. Oracle E-Business Suite database objects should not have privileges granted to the PUBLIC role. Any privileges granted to the PUBLIC role from Oracle E-Business Suite objects should be revoked. Certain privileges, such as the ability to create indexes, can be leveraged for privilege escalation in the database and should be removed.
Site Level Server Security Profiles are Available in the System
-
Security Guideline: Missing Server Security Profile
-
Description: Check whether site level security profiles are available in the system.
-
Code: FND_MISS_PROF
-
Severity: 1
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: If this check fails, log a Service Request (SR) in My Oracle Support. Reference the Secure Configuration Console and the failed Missing Server Security Profile check.
WebLogic Server Default Admin User Password Has Been Changed to Non-Default Value
-
Security Guideline: WebLogic Server Default Password
-
Description: Check whether WebLogic Server default password has been changed to a non-default value.
-
Code: FND_WLS_DEF_PSWD
-
Severity: 1
-
Availability: EBS Release 12.2.9 or R12.ATG_PF.C.Delta.8
-
Next Steps: See Change Password for WebLogic Server Admin User.
Workflow Generated Emails that Reference URLs in EBS Require Additional User Authentication
-
Security Guideline: Workflow Email Link Login
-
Description: Check whether Oracle Workflow generated emails that reference URLs in Oracle E-Business Suite require additional user authentication (login).
-
Code: WF_EMAIL_LOGIN
-
Severity: 1
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See Setting Workflow Notification Mailer SEND_ACCESS_KEY to N.
Allowed Redirects is Enabled
-
Security Guideline: Allowed Redirects
-
Description: Check whether the Allowed Redirects feature is enabled.
-
Code: FND_UNREST_REDIR
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See the following references for more information.
Allowed Resources that are Unused are Denied
-
Security Guideline: Unused Allowed Resources
-
Description: Check whether unused resources are denied.
As of EBS Release 12.2.15 or R12.ATG_PF.C.Delta.14, if the required access data has been collected, then the check will pass if all allowed resources have been accessed or fail if there are resources that are allowed but have never been accessed. If the required access data has not been collected because the Allowed Resources feature is not enabled in your environment, then the check is automatically disabled.
-
Code: SEC_UNUSED_RESOURCES
-
Severity: 2
-
Availability: EBS Release 12.2.11 or R12.ATG_PF.C.Delta.10
-
Next Steps: It is recommended to deny access to resources which have not been used in a year. These can be viewed in the Management by Resource tab on the Allowed Resources user interface. For more information, see Allowed Resources.
Application Users Passwords Have Been Migrated to Hash Passwords
-
Security Guideline: Hashed Passwords
-
Description: Check whether application user passwords have been migrated to hashed passwords.
-
Code: FND_PSWD_HASH
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Switching to Hashed Passwords.
APPLSYSPUB Privileges are Properly Restricted
-
Security Guideline: APPLSYSPUB Privileges
-
Description: Check whether APPLSYSPUB privileges are properly restricted.
-
Code: FND_APPLSYSPUB
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Revoking Unnecessary Grants Given to APPLSYSPUB.
Auditing Profiles are Correctly Set
-
Security Guideline: Auditing Profile Values
-
Description: Check whether the FND: Debug Log and Sign-on Audit profile values are set correctly.
-
Code: FND_AUDIT_PROF
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See the following references for more information.
-
"Using Oracle Application Object Library Profile Options to Configure Logging," Oracle E-Business Suite Maintenance Guide
-
"Page Access Tracking and Sign-On Audit," Oracle E-Business Suite Maintenance Guide
-
Cookie Domain Scoping is Configured
-
Security Guideline: Cookie Domain Scoping Configuration
-
Description: Check whether Cookie Domain Scoping is configured.
-
Code: FND_COOKIE_DOM
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See the following references for more information.
Database Initialization Parameters Have Been Set to Recommended Values
-
Security Guideline: Database Parameters (init*.ora)
-
Description: Check whether secure configuration recommended database initialization parameters have been set.
-
Code: FND_INIT_ORA
-
Severity: 2
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See the following references for more information.
Database Network Access List (ACL) is Configured
-
Security Guideline: Database Network Access Control List
-
Description: Check if Database Network Access Control List has been enabled.
-
Code: SEC_DB_NETWORK_ACL
-
Severity: 2
-
Availability: EBS Release 12.2.10 or R12.ATG_PF.C.Delta.9
-
Next Steps: See My Oracle Support Knowledge Document 2500511.1, Implementing Database Network Access Control Lists.
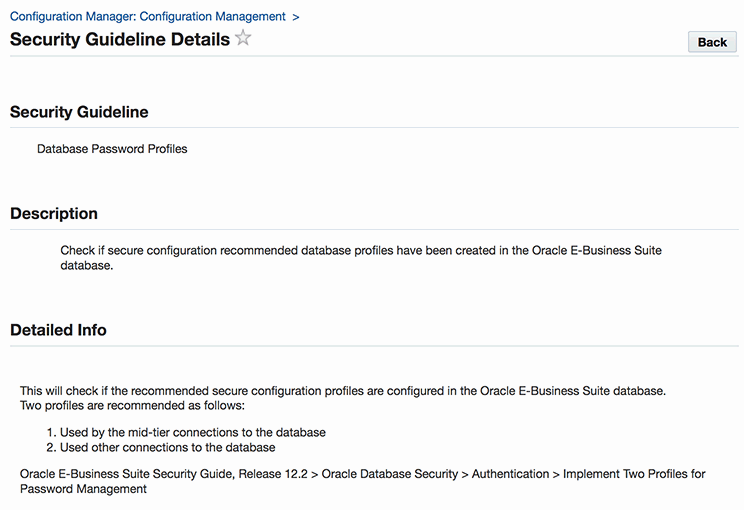
Database Profiles Have Been Created in the EBS Database for Database User Password Management
-
Security Guideline: Database Password Profiles
-
Description: Check if secure configuration recommended database profiles have been created in the Oracle E-Business Suite database.
-
Code: SEC_DB_PSWD_PROF
-
Severity: 2
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See Implementing Two Profiles for Password Management.
FND Generic File Manager (FNDGFM) Authorization is Properly Configured
-
Security Guideline: FND Generic File Manager (FNDGFM) Authorization Configuration
-
Description: Check whether the system is compliant with the recommended configuration for FND Generic File Manager (FNDGFM) authorization.
-
Code: FNDGFM_AUTH_CONFIG
-
Severity: 2
-
Availability: EBS Release 12.2.11 or R12.ATG_PF.C.Delta.10
-
Next Steps: See My Oracle Support Knowledge Document 1357849.1, Security Configuration Mechanisms in the Attachments Feature in Oracle E-Business Suite.
HTTPS is Enabled
-
Security Guideline: HTTPS Configuration
-
Description: Check whether HTTPS is enabled.
-
Code: FND_SSL_ENABLED
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Using TLS to Encrypt Oracle E-Business Suite Connections.
iRecruitment File Upload Security Profile Value is Set
-
Security Guideline: iRecruitment File Upload Profile
-
Description: Check whether the iRecruitment File Upload profile (IRC: XSS Filter) value is set.
-
Code: IREC_FILE_UPLOAD
-
Severity: 2
-
Availability: EBS Release 12.2.7 or R12.ATG_PF.C.Delta.7
-
Next Steps: See Oracle iRecruitment Implementation and User Guide, Release 12.2.
Server Security (Secure Flag in DBC File) is Enabled
-
Security Guideline: Activate Server Security
-
Description: Check whether server security (Secure Flag in DBC file) is enabled.
-
Code: FND_SERVER_SEC
-
Severity: 2
-
Availability: EBS Release 12.2.6 or R12.ATG_PF.C.Delta.6
-
Next Steps: See Activating Server Security.
Unified Auditing is Enabled
-
Security Guideline: Unified Auditing
-
Desscription: Check for whether Unified Auditing is supported and enabled.
This check fails if Unified Auditing and the recommended default EBS Unified Auditing policies are not enabled.
-
Code:
-
Severity: 2
-
Availability: EBS Release 12.2.15 or R12.ATG_PF.C.Delta.14
-
Next Steps: See the following resources for more information:
-
Database Auditing in Oracle E-Business Suite Security Guide
-
My Oracle Support Knowledge Document 2777404.1, Enabling Unified Auditing in Oracle E-Business Suite Release 12.2 with Oracle Database 23ai, 19c, or 12c
-
Workflow Admin Access is Restricted
-
Security Guideline: Workflow Admin Access
-
Description: Check whether Oracle Workflow Admin access is restricted.
-
Code: WF_ADMIN_NOT_PUBLIC
-
Severity: 2
-
Availability: EBS Release 12.2.9 or R12.ATG_PF.C.Delta.8
-
Next Steps: See Ensuring You Know Who is a Workflow Admin.
Navigating Through the Secure Configuration Console
On the main screen of the console are four predefined filtered criteria in tiles added in Oracle E-Business Suite Release 12.2.10. Click on each tile to view the filtered guidelines in the table displayed.
-
Failed Guidelines - By default, this filter provides all Severity 1 and Severity 2 level failures, but not guideline checks that have been suppressed.
-
Passed Guidelines - This shows all guideline checks that have passed, but not those that have been suppressed.
-
Suppressed Guidelines - This shows all guideline checks that have been suppressed (or muted).
-
Unsuppressed Guidelines - This shows all guidelines that have not been suppressed. These are the security guidelines that are being checked.
The "Guidelines were last checked on" date above the left most tile is the date in which the security guidelines were checked against using the Secure Configuration Console.
Secure Configuration Console Main Page
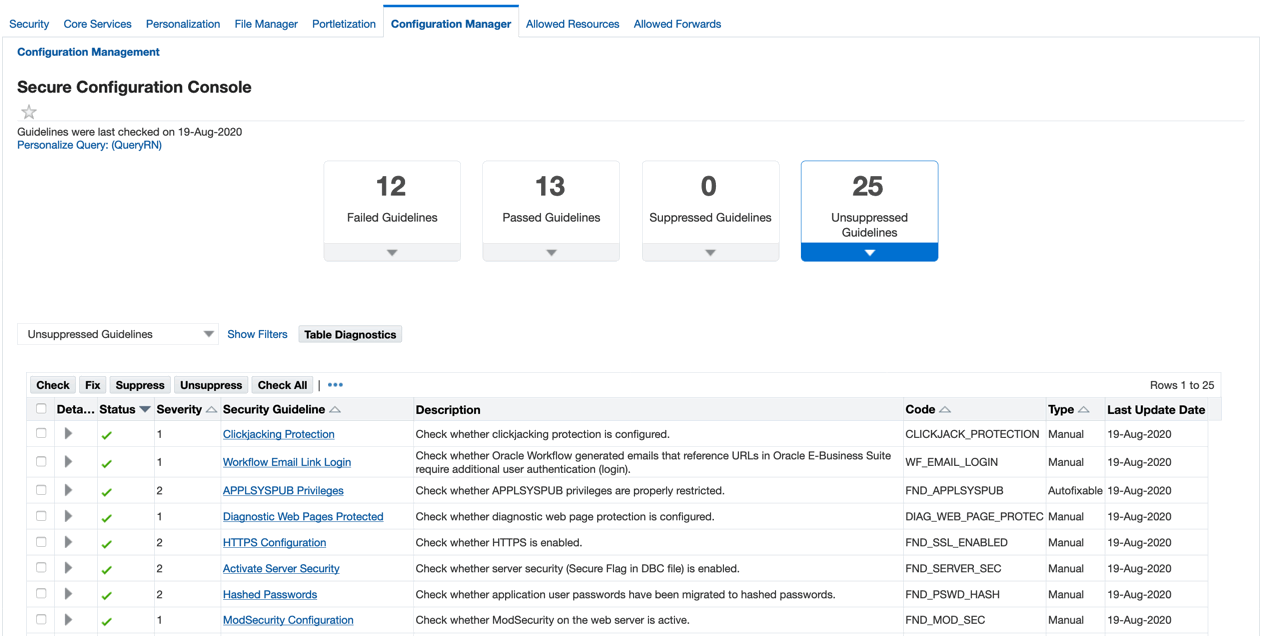
You can further refine each tile's criteria by utilizing the Saved Search drop-down. The drop-down allows you to add additional filter criteria which displays in the Filter section on the left, where you can save your search for future use.
In the table on the main console page, click Check to compute the status of all configurations on your system against the selected guidelines. Click Check All to select and check all guidelines.
Once the status is computed, the guideline will display as either as Pass or Fail (green check mark or red X, respectively) in the Status column.
Click on the arrow in the Details column for more information as to why a certain configuration passed, failed, or produced an error during the configuration check.
Secure Configuration Console Checked Guidelines Table
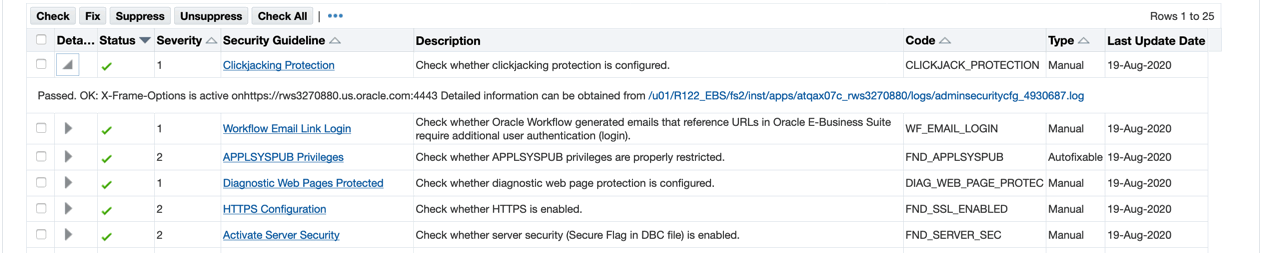
To automatically remediate failed configuration checks, select guideline checks with a Failed status and of the type Autofixable and click Fix located at the top of the table to resolve the reported issues.
Click Suppress to mute selected guideline checks that are NOT applicable to your system. Suppressed guidelines will no longer be displayed, nor will they require further review in the console when deselecting the Muted Security Configuration checkbox.
Click Unsuppress to unmute the previously muted guideline checks.
Each security guideline is a link, which when clicked, opens a new page with a detailed description of the configuration requirement.
If the configuration requirement involves a manual fix, more information on the necessary manual steps can be found by clicking the link. For example, when clicking the "Database Password Profiles" link, the Security Guideline Details page is displayed, providing the security guideline description and detailed information about the check.
Security Guideline Details Page
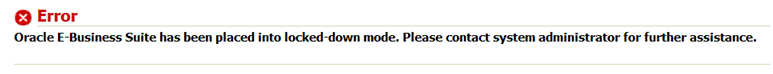
As mentioned previously, until the recommended security configurations have been implemented or acknowledged by a local system administrator, the Secure Configuration Console will prevent entry into the system. Until then, users will see an error message when trying to log in which says: "Oracle E-Business Suite has been placed into locked-down mode. Please contact system administrator for further assistance."
Locked-Down Mode Error Message
When an Oracle E-Business Suite instance has been placed into locked-down mode, as soon as a user with system administrator privileges logs in the Secure Configuration Console will appear.
At this point, the system administrator should resolve or address any failed security guideline checks. When ready to unlock the instance, the system administrator should select either of the following options prior to clicking Proceed:
-
I am done with the security configurations.
-
Ignore the security configurations.
Once you click Proceed, the Oracle E-Business Suite instance is unlocked.
Command Line Utility
If a user with local system administrator privileges is not available, you can access the Secure Configuration Console by using the AdminSecurityCfg utility.
This utility is provided for the following tasks:
-
To take the system out of locked down mode.
-
To compute the status of a certain configuration or all configurations.
-
To configure a certain configuration or all configurations of type Autofixable.
-
To view the status of a certain configuration or all configurations.
To use the AdminSecurityCfg utility, use the following syntax which will then will prompt you for your <APPS Username> and <APPS password>. Note that all parameters can, if desired, be entered on the same command line; they are shown here on different lines (using the UNIX '\' continuation character) for clarity.
java oracle.apps.fnd.security.AdminSecurityCfg \ <-check|-fix|-status|-lock|-unlock> \ DBC=<DBC File Path> \ [CODES=<code1>,<code2>,<code3>...]
Where:
-check - Runs the utility in check mode. You can specify the configurations to check by adding [CODES=<code1>,<code2>,<code3>...] to the command. These correspond to the security guideline codes found in Security Guidelines.
For example: java oracle.apps.fnd.security.AdminSecurityCfg -check DBC=<DBC File Path> CODES=FND_DB_DEF_PSWD,FND_PROF_ERRORS
If you do not specify a CODES attribute, then the utility will check all configurations.
-fix - Runs the utility in fix mode. You can specify the configurations to fix by adding [CODES=<code1>,<code2>,<code3>...] to the command.
For example: java oracle.apps.fnd.security.AdminSecurityCfg -fix DBC=<DBC File Path> CODES=FND_UNREST_REDIR,FND_AUDIT_PROF
If you do not specify a CODES attribute, then the utility will fix all configurations of type Autofixable.
-status - Determines the status of all configurations. Specifying the CODES attribute is not necessary for this mode.
-lock - Places the system in locked down mode.
-unlock - Takes the system out of locked down mode.