Deploy Oracle E-Business Suite Cloud Manager on Oracle Cloud Infrastructure
This chapter covers the following topics:
- Overview of Deploying Oracle E-Business Suite Cloud Manager
- Create Oracle Cloud Infrastructure Accounts and Resources
- Create Network Resources for Deploying Oracle E-Business Suite Cloud Manager
- Create Oracle E-Business Suite Cloud Manager Compute Instance
- Configure Oracle E-Business Suite Cloud Manager Compute Instance
- Update to Latest Version of Oracle E-Business Suite Cloud Manager
- Set Up Notifications With OCI Email Delivery Service
- Oracle E-Business Suite Cloud Manager Deployment for Demo and Test Purposes (Commercial Cloud Regions Only)
Overview of Deploying Oracle E-Business Suite Cloud Manager
This chapter describes how to deploy Oracle E-Business Suite Cloud Manager on Oracle Cloud Infrastructure.
If you are performing a demo or test, you may be able to leverage the procedure provided in Oracle E-Business Suite Cloud Manager Deployment for Demo and Test Purposes (Commercial Cloud Regions Only) to simplify tenancy preparation, Oracle E-Business Suite Cloud Manager deployment and configuration by taking advantage of an Oracle Marketplace stack.
Note: If you have deployed a previous version of Oracle E-Business Suite Cloud Manager and wish to upgrade to the latest version, you do not need to perform the tasks in this chapter. Instead, follow the instructions described in Update Oracle E-Business Suite Cloud Manager to Latest Version. Oracle strongly recommends that you upgrade to the latest version at your earliest convenience.
Before you provision your Oracle E-Business Suite environments, you must follow the instructions in Set Up Your Tenancy to Host Oracle E-Business Suite Environments. Setting up the tenancy includes creating a compartment, groups, policies, users, and network resources to support a specific purpose. For example, the purpose could be to support a function (such as production, development or test), to support a region, or to create any other desired tenancy segmentation (such as a business unit).
Introduction to Users and Roles
The following are four distinct categories of users referenced throughout this procedure and their roles:
-
Tenancy administrator - Creates compartments, policies, groups, and users.
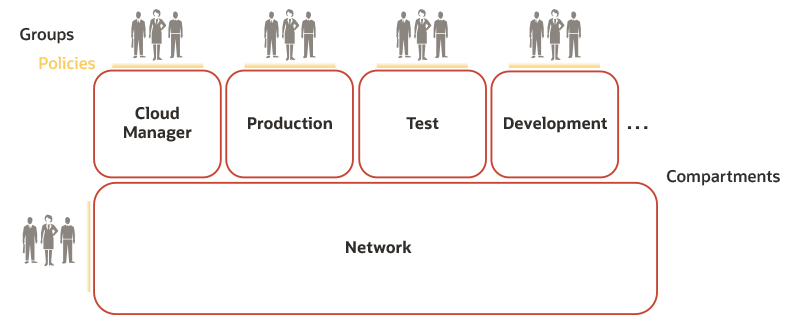
In the example shown in the following diagram, the tenancy administrator creates four compartments, one for the cloud manager deployment itself, and the other three for Oracle E-Business Suite production, test, and development environments. The tenancy administrator creates groups of users to serve as cloud manager administrators and Oracle E-Business Suite administrators for the production, test, and development environments in these compartments. Their access to these compartments is governed by the policies designed by the tenancy administrator.
These compartments will use network resources to be configured by the network administrator.
Example Tenancy Configuration Performed by Tenancy Administrators
-
Network administrator - Designs the network and implements the network design with the following cloud resources:
-
VCNs
-
Subnets
-
Gateways
-
Routing tables
-
Security lists/groups
-
Security rules
-
-
FastConnect
-
Mount targets, if you plan to use the File Storage service for a shared file system for your Oracle E-Business Suite environments
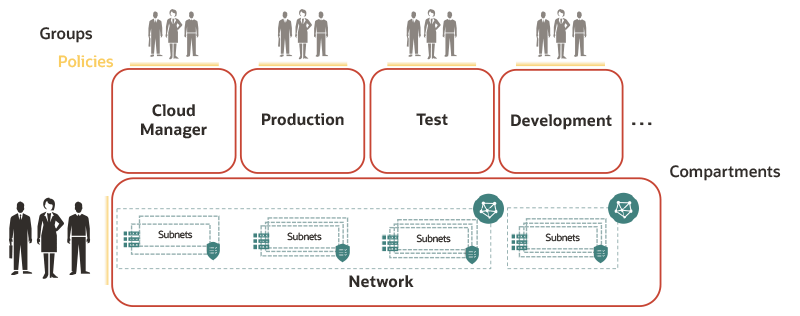
As shown in the following diagram, the network administrators create VCNs in the network, one or more subnet for each VCN, and create the security lists and security rules for the subnets.
Example Network Configuration by Network Administrators
-
-
Oracle E-Business Suite Cloud Manager administrator - Deploys Oracle E-Business Suite Cloud Manager and defines the network profiles to map compartments and network resources. The Oracle E-Business Suite Cloud Manager administrator also leverages the compartments and network resources.
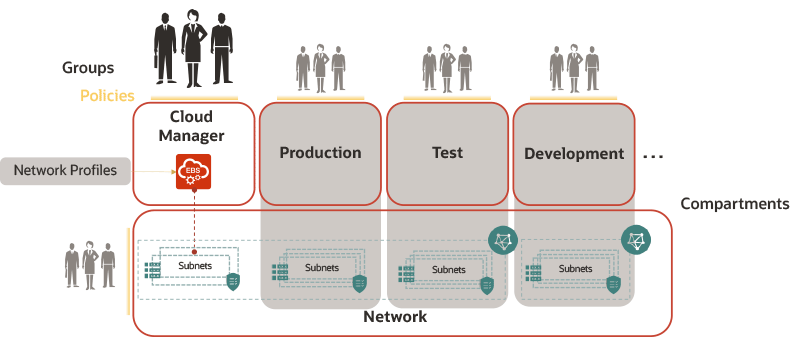
As shown in the following diagram, the Oracle E-Business Suite Cloud Manager administrator deploys Oracle E-Business Suite Cloud Manager in the designated compartment and defines network profiles for the production, test, and development compartments, mapping them to subnets and associated resources in the network.
Example Deployment and Network Profile Configuration by Oracle E-Business Suite Cloud Manager Administrators
-
Oracle E-Business Suite administrators - Also known as application administrators or DBAs, they provision and maintain the Oracle E-Business Suite environments. The Oracle E-Business Suite administrators also leverage the network profiles that are defined.
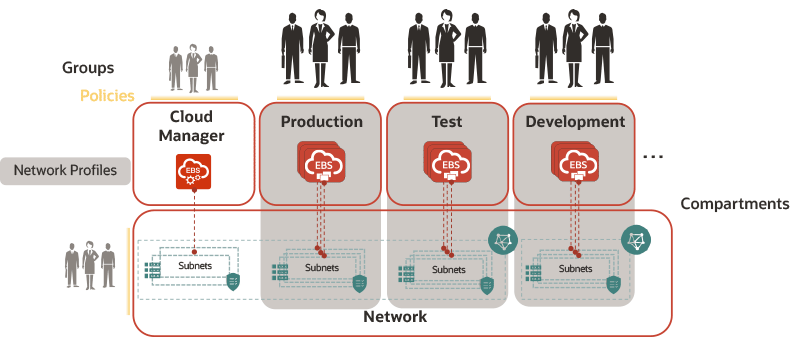
In the following diagram, the Oracle E-Business Suite administrators provision Oracle E-Business Suite environments in the production, test, and development compartments, leveraging the network profiles to designate the network resources used by those environments.
Example Provisioning and Management by Oracle E-Business Suite Administrators
Note: If you wish, an Oracle E-Business Suite Cloud Manager administrator can also perform the duties of the network administrator and an Oracle E-Business Suite administrator. This is appropriate if you are configuring the system for demonstration use, or in any other circumstance where a single database administrator (DBA) will be performing all these roles. To accomplish this, you will make this user a member of the network administrators group and Oracle E-Business Suite administrators group.
Note: Ensure you perform all the applicable instructions in each section before proceeding to the next section.
Create Oracle Cloud Infrastructure Accounts and Resources
In this section, the tenancy administrator performs all tasks as described.
Note: Your groups and users must be created in your tenancy's default domain.
Create Compartments
In this section, you will first map out your compartment topology and then create your compartment or compartments.
There are two types of compartments that we will refer to:
-
Cloud Manager Compartment - Compartment that holds the Oracle E-Business Suite Cloud Manager Compute instance.
-
Network Compartment - Compartment that holds network resources.
If you are giving a demonstration, you might choose to use one compartment for all components.
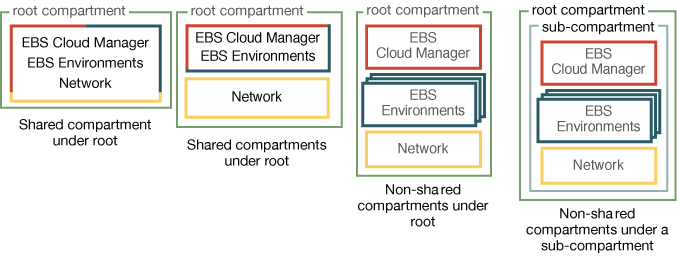
Oracle E-Business Suite Cloud Manager supports the use of nested compartments. The following depicts the compartment hierarchies that have been explicitly certified:
-
The first certified hierarchy consists of one shared compartment under the root compartment for Oracle E-Business Suite Cloud Manager, EBS environments, and the network.
-
Another certified hierarchy consists of multiple shared compartments under the root compartment including one compartment for Oracle E-Business Suite Cloud Manager and EBS environments, and another for the network.
-
Another certified hierarchy consists of separate non-shared compartments for Oracle E-Business Suite Cloud Manager, each EBS environment, and the network under the root compartment.
-
The final certified hierarchy consists of separate non-shared compartments for Oracle E-Business Suite Cloud Manager, each EBS environment, and the network within a subcompartment under the root compartment.
The following diagram depicts these compartment hierarchies:
Certified Compartment Hierarchies
To create each compartment, perform the following:
-
While signed in to the Oracle Cloud Infrastructure Service Console, open the navigation menu and click Identity & Security. Under Identity, click Compartments.
-
On the Compartments page, click Create Compartment.
-
In the dialog window, enter the required details:
-
Name: Enter the compartment name. For example,
network-compartmentorebscm-compartment. -
Description: Enter a description of your choice.
-
Parent Compartment: Select the root compartment under which the new compartment will be created.
-
Click Create Compartment.
-
Create Groups
The tenancy administrator is required to create the following groups:
-
The network administrators group, such as
netadmin-grp. -
The Oracle E-Business Suite Cloud Manager administrators group, such as
ebscmadmin-grp. This group will be used to configure the Oracle E-Business Suite Cloud Manager Compute instance in Configure Oracle E-Business Suite Cloud Manager Compute Instance.
Perform the following steps to create the two groups:
-
Open the navigation menu and click Identity & Security. Under Identity, click Domains.
-
Select the root compartment in the Compartment drop-down list.
-
Within the list of domains, click the link for the "Default" domain.
-
Click Groups.
-
Click Create group.
-
In the dialog window, enter the required details:
-
Name: Enter the name for the group. For example,
netadmin-grpandebscmadmin-grp. -
Description: Enter a description of your choice.
-
-
Click Create.
Assign Policies
In this section, you will assign policies that allow for the proper permissions for administrators to manage and use the necessary compartments.
-
Open the navigation menu and click Identity & Security. Under Identity, click Policies.
-
Create a policy for the network compartment to allow network administrators to manage it and for Oracle E-Business Suite Cloud Manager administrators to use it:
-
Select the network compartment from the Compartment drop-down list on the left.
-
Click Create Policy.
-
In the dialog window, enter the required details:
-
Name: Enter a name. For example,
networkcompartment-policy. -
Description: Enter a description of your choice.
-
In the Policy Builder section, click the Show manual editor toggle switch. In the provided text field, add each of the following policy statements, substituting appropriate values for the variables designated by angle brackets.
Allow group <network administrators group> to manage virtual-network-family in compartment <network compartment> Allow group <Oracle E-Business Suite Cloud Manager administrators group> to use virtual-network-family in compartment <network compartment>
If you plan to use the File Storage service for a shared file system for your Oracle E-Business Suite environments, then you must also add the following policy statement, substituting appropriate values for the variables designated by angle brackets.
Allow group <network administrators group> to manage mount-targets in compartment <network compartment>
-
-
Click Create.
-
-
Create a policy for the Oracle E-Business Suite Cloud Manager compartment to allow Oracle E-Business Suite Cloud Manager administrators to perform operations on Oracle Cloud Infrastructure resources within it:
-
Select the Cloud Manager compartment from the Compartment drop-down list.
-
Click Create Policy.
-
In the dialog window, enter the required details:
-
Name: Enter a name. For example,
ebscmcompartment-policy. -
Description: Enter a description of your choice.
-
In the Policy Builder section, click the Show manual editor toggle switch. In the provided text field, add each of the following policy statements, substituting appropriate values for the variables designated by angle brackets.
Allow group <Oracle E-Business Suite Cloud Manager administrators group> to manage instance-family in compartment <Oracle E-Business Suite Cloud Manager compartment> Allow group <Oracle E-Business Suite Cloud Manager administrators group> to manage load-balancers in compartment <Oracle E-Business Suite Cloud Manager compartment> Allow group <Oracle E-Business Suite Cloud Manager administrators group> to manage tag-namespaces in compartment <Oracle E-Business Suite Cloud Manager compartment>
-
-
Click Create Policy.
-
-
Create a policy for the tenancy to allow network administrators and Oracle E-Business Suite Cloud Manager administrators to perform operations on Oracle Cloud Infrastructure resources within it:
-
Select the root compartment from the Compartment drop-down list.
-
Click Create Policy.
-
In the dialog window, enter the required details:
-
Name: Enter a name. For example,
tenancy-policy. -
Description: Enter a description of your choice.
-
In the Policy Builder section, click the Show manual editor toggle switch. In the provided text field, add each of the following policy statements, substituting appropriate values for the variables designated by angle brackets.
Allow group <network administrators group> to inspect compartments in tenancy Allow group <Oracle E-Business Suite Cloud Manager administrators group> to inspect compartments in tenancy Allow group <Oracle E-Business Suite Cloud Manager administrators group> to inspect users in tenancy Allow group <Oracle E-Business Suite Cloud Manager administrators group> to inspect groups in tenancy Allow group <Oracle E-Business Suite Cloud Manager administrators group> to inspect dynamic-groups in tenancy Allow group <Oracle E-Business Suite Cloud Manager administrators group> to use domains in tenancy
-
-
Click Create Policy.
-
Create Users with Oracle E-Business Suite Cloud Manager Administrator Privileges
The tenancy administrator is required to create the users in this section.
While logged on to the Oracle Cloud Infrastructure Service Console as the tenancy administrator, create users who will have Oracle E-Business Suite Cloud Manager administrator privileges as follows.
Repeat these steps for all users of your Oracle E-Business Suite Cloud Manager administrator group and network administrator group.
-
Open the navigation menu, and click Identity & Security. Under Identity, click Domains.
-
Select the root compartment in the Compartment drop-down list.
-
Within the list of domains, click the link for the "Default" domain.
-
On the left hand side, click Users.
-
Click Create User.
-
In the Create User dialog box, enter the following:
-
First Name: First name of the user.
-
Last Name: Last name of the user.
-
Username / Email: A valid email ID.
-
Groups: Select the group that corresponds to the user you are creating. For example, if you are creating the Cloud Manager administrator, select the Cloud Manager administrators group. If you are creating the network administrator, select the network administrators group.
-
-
Click Create.
-
Grant the newly created user the Application Administrator role by following the steps in Assigning Users to Roles in the Oracle Cloud Infrastructure Documentation.
Create Network Resources for Deploying Oracle E-Business Suite Cloud Manager
Note: Regarding host name resolution, be aware of the following important notes:
-
All virtual machines created by Oracle E-Business Suite Cloud Manager will have oraclevcn.com as the physical (network) host name.
-
These physical host names will be resolvable within the VCN and subnet in which they were created.
-
You can set the logical name (domain name) for these virtual machines as desired; however, these will be resolvable through the use of the /etc/hosts file only.
In this section, the network administrator performs all tasks as described.
First, you will create a new Virtual Cloud Network (VCN) using the steps in Create a Virtual Cloud Network.
Then dependent on the type of subnet you intend to use, either public or private, you will create associated network resources that will be used by your Oracle E-Business Suite Cloud Manager Compute instance:
Oracle E-Business Suite Cloud Manager and associated load balancers work in regional and availability domain specific subnets. These subnets can be either public or private. Oracle recommends using regional and private subnets.
In a production environment, if you are not using FastConnect or IPsec VPN we recommend you deploy a dedicated bastion server. Use of a dedicated bastion server is strongly recommended when deploying Oracle E-Business Suite in government cloud regions. This bastion server will be associated with a specific subnet that will be used as a bridge between the resources outside and inside Oracle Cloud Infrastructure. See Bastion Hosts: Protected Access for Virtual Cloud Networks for more information about the architecture of the bastion server.
Create a Virtual Cloud Network
Note: If you have an existing Virtual Cloud Network you want to use, skip this section and proceed to Create Network Resources for Use with Public Subnets if you intend to use public subnets. If you intend to use private subnets, proceed to Create Network Resources for Use with Private Subnets.
To create a new Virtual Cloud Network (VCN):
-
Open the navigation menu. Click Networking, then click Virtual Cloud Networks.
-
Click Create VCN and enter the required details for your VCN:
-
Name: Enter a name, such as
ebscm-vcn. -
Create in Compartment: Select your network compartment, created in Create Compartments.
-
IPv4 CIDR Blocks: Specify your choice of CIDR. For example,
10.0.0.0/16. -
Under DNS Resolution, select Use DNS hostnames in this VCN.
-
-
Click Create VCN.
-
Now, you must review and potentially modify the default DHCP options for your VCN.
If your EBS environments need to contact a server in your local network that requires DNS name resolution, you must ensure your DHCP options include a custom DNS resolver. To do so, perform the following steps:
-
Navigate to the DHCP options for your VCN and click on the name of the VCN you have just created.
-
Under Resources, select DHCP Options.
-
Review the Default DHCP Options for your VCN.
If the DNS type for your default DHCP Options is Internet and VCN Resolver, perform the following steps:
-
Click Edit DHCP Options.
-
Change to Custom Resolver.
-
Enter
169.254.169.254for the IP address of the DNS Server (Note: This IP address corresponds to Oracle's VCN resolver.) -
Select DNS Search Domain Type.
If you set your DNS Search Domain Type to "Customer Search Domain", you must confirm that when querying for host names, your DNS search domain returns fully qualified domain names (FQDN).
To do so, use the command
hostname -fon any of your Oracle E-Business Suite nodes to validate the host names.If your DNS search domain configuration does not result in FQDNs, you must set your DNS Search Domain Type to "Subnet Search Domain".
-
-
Create Network Resources for Use with Public Subnets (Conditional)
Note: If you want to use private subnets for Oracle E-Business Suite Cloud Manager and load balancer, skip this section and proceed to Create Network Resources for Use with Private Subnets.
Create an Internet Gateway
To create an internet gateway:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Internet Gateways.
-
Click Create Internet Gateway and enter the required details for your internet gateway:
-
Name: Enter a name, such as
ebscm-igw. -
Create in Compartment: Select your network compartment, created in Create Compartments.
-
-
Click Create Internet Gateway.
Create Route Tables
In this section, you will create two separate route tables, one for the Oracle E-Business Suite Cloud Manager Compute instance and one for the load balancer. In the following examples, we will use the names ebscm-RouteTable and lbaas-RouteTable, respectively.
Perform these steps twice: once for the Oracle E-Business Suite Cloud Manager Compute instance route tables and once for the load balancer route tables.
To create the route tables:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Route Tables.
-
Click Create Route Table and enter the required details for your route table:
-
Name: Specify a name, such as
ebscm-RouteTableorlbaas-RouteTable. -
Create in Compartment: Select your network compartment, created in Create Compartments.
-
-
Click + Another Route Rule and enter the route rule details as follows:
-
Target Type: Select Internet Gateway.
-
Destination CIDR Block:
0.0.0.0/0 -
Compartment: Select your network compartment, created in Create Compartments.
-
Target Internet Gateway: Select the previously created gateway.
-
-
Click Create.
Configure Network Security
In this section, you will establish network security either using network security groups (NSGs) or security lists.
Both NSGs and security lists use security rules to control traffic at the packet level. NSGs let you define a set of security rules that applies to a group of virtual network interface cards (VNICs) of your choice, while security lists let you define a set of security rules that applies to all the VNICs in an entire subnet.
Oracle recommends using NSGs instead of security lists because NSGs let you separate the VCN's subnet architecture from your application security requirements.
Follow the instructions in the applicable section to configure your method of network security:
Network Security Groups
To use network security groups (NSGs), create two separate NSGs. Their roles and some example names are shown in the following table:
| Component NSG Needed For | Example NSG Name |
|---|---|
| EBS Cloud Manager Load Balancer | ebscmlbaas-nsg |
| EBS Cloud Manager Virtual Machine | ebscmvm-nsg |
For more information, see Network Security Groups in the Oracle Cloud Infrastructure Documentation.
To create an NSG:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Under Resources on the navigation menu at the left, select Network Security Groups.
-
Click Create Network Security Group:
-
Name: Specify a name such as
ebscmlbaas-nsgorebscmvm-nsg. -
Create in Compartment: Select your compartment name, such as network-compartment.
-
-
Click Create.
Create Security Lists (Optional If Not Using NSGs)
If you are not using NSGs, in this section you will create two separate security lists: one for the Oracle E-Business Suite Cloud Manager Compute instance and one for the load balancer. In the following examples, we will use the names ebscmvm-seclist and ebscmlbaas-seclist, respectively.
To use security lists, create two separate security lists. Their roles and some example names are shown in the following table:
| Component Security List Needed For | Example Security List Name |
|---|---|
| EBS Cloud Manager Virtual Machine | ebscmvm-seclist |
| EBS Cloud Manager Load Balancer | ebscmlbaas-seclist |
Create the Oracle E-Business Suite Cloud Manager Virtual Machine Security List
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Security Lists.
-
Click Create Security List and enter the required details for the security list:
-
Name: Specify a name such as
ebscmvm-seclist. -
Create in Compartment: Select your network compartment, created in Create Compartments.
-
Create the Load Balancer Security List
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Security Lists.
-
Click Create Security List and enter the required details of your security list:
-
Name: Specify a name such as
ebscmlbaas-seclist. -
Create in Compartment: Select your network compartment, created in Create Compartments.
-
Create Security Rules
In this section, you will add the mandatory security rules shown in the following tables to the chosen security mechanism --either network security group or security list-- created in Configure Network Security.
Create Security Rules for the EBS Cloud Manager Virtual Machine
-
Under Allow Rules for Ingress:
-
Click + Another Ingress Rule.
-
For the first ingress rule that is needed, modify the default rule as follows:
-
Source Type:
CIDR -
Source CIDR: Enter the CIDR of your choice.
-
IP Protocol:
TCP -
Source Port Range:
All -
Destination Port Range:
22
-
-
For the second ingress rule that is needed, click + Another Ingress Rule and enter the following values:
-
Source Type:
CIDR -
Source CIDR:
0.0.0.0/0 -
IP Protocol:
ICMP -
Type:
3 -
Code:
4
-
-
For the third ingress rule that is needed, click + Another Ingress Rule and enter the following values:
-
Source Type:
CIDR -
Source CIDR: Enter the CIDR of your LBaaS subnet, lbaas-subnet-ad1. For example,
10.0.1.0/24. Note that the subnet is created in the next step. -
IP Protocol:
TCP -
Source Port Range:
All -
Destination Port Range:
8081
-
-
For the fourth ingress rule that is needed, click + Another Ingress Rule and enter the following values:
Note: Note that the fourth ingress rule is not required if a regional subnet is chosen for your public load balancer or if you are in a single availability domain region.
-
Source Type:
CIDR -
Source CIDR: Enter the CIDR of your LBaaS subnet, lbaas-subnet-ad2. For example,
10.0.1.0/24. Note that the subnet is created in the next step. -
IP Protocol:
TCP -
Source Port Range:
All -
Destination Port Range:
8081
-
-
-
Under Allow Rules for Egress, click + Another Egress Rule and modify the default rule as follows.
-
Destination Type:
CIDR -
Destination CIDR:
0.0.0.0/0 -
IP Protocol:
TCP -
Source Port Range:
All -
Destination Port Range:
All
-
-
Click Create Security List.
Create Security Rules for the EBS Cloud Manager Load Balancer
-
Under Allow Rules for Ingress, click + Another Ingress Rule and enter the following values for the ingress rule that is needed:
-
Source Type:
CIDR -
Source CIDR: Enter the CIDR corresponding to the IP addresses of your client machines that will access the Cloud Manager UI.
-
IP Protocol:
TCP -
Source Port Range:
All -
Destination Port Range:
443or other port of your choice. This port will be used in step 5 of Run Oracle E-Business Suite Cloud Manager Configure Script for the First Time, when prompting for the Load Balancer Listener Port.
-
-
Under Allow Rules for Egress, click + Another Egress Rule and enter the following values for the egress rule that is needed:
-
Destination Type:
CIDR -
Destination CIDR:
0.0.0.0/0 -
IP Protocol:
TCP -
Source Port Range:
All -
Destination Port Range:
All
-
-
Click Create Security List.
Create Subnets
In this section, you will create the following new subnets:
-
One regional or availability domain-specific public subnet where the Oracle E-Business Suite Cloud Manager Compute instance will be created. This may be referred to as the "provisioning VM subnet."
-
Either one or two subnets for creating the load balancer for Oracle E-Business Suite Cloud Manager.
-
Create only one subnet for the load balancer if any of the following are true:
-
You are using a regional subnet.
-
You are in a single availability domain region.
-
-
Alternatively, if you choose to deploy using availability domain-specific subnets in a multiple availability domain region, you will create two subnets.
-
You will need to specify your own names and parameters, but you can use the examples in the following two tables for guidance.
If you choose to use regional subnets, refer to the following example.
Note: The Security Lists column in the following table is labeled "optional" as it is not applicable if you are using NSGs.
| Subnet Name | CIDR Block | Route Table | Subnet Access | Security List (Optional) |
|---|---|---|---|---|
| ebscm-subnet-phx | 10.0.0.0/24 | ebscm-RouteTable | Public subnet | ebscmvm-seclist |
| lbaas-subnet-phx | 10.0.1.0/24 | lbaas-RouteTable | Public subnet | lbaas-seclist |
If you choose to use availability domain-specific subnets, refer to the following example.
Note: The Security Lists column in the following table is labeled "optional" as it is not applicable if you are using NSGs.
| Subnet Name | Availability Domain (AD) | CIDR Block | Route Table | Subnet Access | Security List (Optional) |
|---|---|---|---|---|---|
| ebscm-subnet-ad1 | AD-1 | 10.0.0.0/24 | ebscm-RouteTable | Public subnet | ebscmvm-seclist |
| lbaas-subnet-ad1 | AD-1 | 10.0.1.0/24 | lbaas-RouteTable | Public subnet | lbaas-seclist |
| lbaas-subnet-ad2 | AD-2 | 10.0.2.0/24 | lbaas-RouteTable | Public subnet | lbaas-seclist |
To create a new subnet:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Subnets.
-
Click Create Subnet, specifying your choice for the following parameters:
-
Name
-
Create in Compartment
-
Subnet Type: Select either the Regional (Recommended) or Availability Domain-Specific option. If you choose Availability Domain-Specific, select your availability domain.
-
IPv4 CIDR Block
-
Route Table: Ensure you choose a route table that has a target type of Internet Gateway.
-
Subnet Access: Select the Public Subnet option.
-
Security Lists: Select the security list that matches the subnet you are defining based on Table 2-3.
Note: This parameter is not applicable if you are using NSGs.
-
-
Click Create Subnet.
Create Network Resources for Use with Private Subnets (Conditional)
Note: If you plan to use public subnets for Oracle E-Business Suite Cloud Manager and a load balancer, do not perform the steps in this section. Instead, follow the steps in Create Network Resources for Use with Public Subnets.
When using private subnets, you could either:
-
Define a DRG (Dynamic Routing Gateway) to establish communication between your on-premises network and the VCN.
-
Leverage a public subnet associated with a bastion server to access the VMs in the private subnet.
Create a Network Address Translation (NAT) Gateway (Conditional)
This step is mandatory when running Oracle E-Business Suite Cloud Manager in a commercial cloud region. When running in a government cloud region, to prevent any resource in the VCN from accessing the internet, skip this step.
To create a Network Address Translation, or NAT, gateway, perform the following steps:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select NAT Gateways.
-
Click Create NAT Gateway and specify the following:
-
Name: Enter a name, such as
ebscm-natgw. -
Create in Compartment: Select your network compartment, created in Create Compartments.
-
-
Click Create NAT Gateway.
Create a Service Gateway
To create a service gateway, perform the following steps:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Service Gateways.
-
Click Create Service Gateway and specify the following:
-
Create in Compartment: Select your network compartment created in Create Compartments.
-
Name: Enter a name, such as
ebscm-srvgw. -
Select "All <XXX> Services In Oracle Services Network" from the Services drop-down list. Note that XXX is a region-specific code such as IAD or LHR.
-
-
Click Create Service Gateway.
Create Route Tables
In this section, you will create two separate route tables, one for the Oracle E-Business Suite Cloud Manager Compute instance and one for the load balancer. In the following examples, we will use the names ebscm-RouteTable and lbaas-RouteTable, respectively
Create the Route Table for Oracle E-Business Suite Cloud Manager Compute Instance
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Route Tables.
-
Click Create Route Table and specify the following:
-
Create in Compartment: Select your network compartment, created in Create Compartments.
-
Name: Enter a name, such as
ebscm-rtbl.
-
-
(Conditional) Enable connectivity to public object storage if you plan to allow internet connectivity from your EBS environments. This is required in case you want to perform new installations using the Advanced Provisioning feature.
-
Establish connectivity to object storage in required regions and home region.
Oracle E-Business Suite Cloud Manager requires access to object storage in the following two regions, in addition to your home region:
-
US West (Phoenix)
-
US East (Ashburn)
You have two options to establish this connectivity:
-
Enable the connectivity using the NAT gateway by performing the following steps to add a route rule:
Click + Another Route Rule and enter the route rule details as follows:
-
Target Type: Select NAT Gateway.
-
Destination CIDR Block:
134.70.0.0/16. Note that the 134.70.0.0/16 CIDR is required in order to connect to object storage. -
Compartment: Select your network compartment created in Create Compartments.
-
Target NAT Gateway: Select the previously created NAT gateway.
-
-
Alternatively, work with your network administrator to add a route rule in your private network to enable connectivity to the following CIDR block:
134.70.0.0/16. You may also need to add firewall rules to allow connections to the following locations:-
https://objectstorage.us-phoenix-1.oraclecloud.com/ -
https://swiftobjectstorage.us-phoenix-1.oraclecloud.com/ -
https://objectstorage.us-ashburn-1.oraclecloud.com/
-
-
-
Click + Another Route Rule and enter route rule details as follows:
-
Target Type: Select NAT Gateway.
-
Destination CIDR Block: The CIDR for the Oracle Identity Cloud Service host being used. Note that the Oracle Identity Cloud Service host is of the format "idcs-xxxxxxxxxxxxxxxxxxxxxx.identity.oraclecloud.com". Use
nslookupfor getting the IP address of the Identity Cloud Service and derive the CIDR for the IP address to add the same here. In case the Oracle Identity Cloud Service CIDR changes, this rule must be updated as well. -
Compartment: Select your network compartment created in Create Compartments.
-
Target NAT Gateway: Select the previously created NAT gateway.
-
-
-
Click + Another Route Rule and enter route rule details as follows:
-
Target Type: Select Service Gateway.
-
Destination CIDR Block: Select "All <XXX> Services In Oracle Services Network". Note that XXX is a region-specific code such as IAD or LHR.
-
Compartment: Select your network compartment, created in Create Compartments.
-
Target Service Gateway: Select the previously created service gateway.
-
-
Click Create.
Create the Route Table for Oracle E-Business Suite Cloud Manager Load Balancer
For this route table for the load balancer, no route rules will be added to this route table as it will be used as a placeholder in case we need to define any additional route rules at a later time. Note that for communication within the VCN, no route rules are needed.
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Route Tables.
-
Click Create Route Table and specify the following:
-
Create in Compartment: Select your network compartment created in Create Compartments.
-
Name: Enter a name, such as
ebscm-RouteTable.
-
-
Click Create.
Configure Network Security
In this section, you will establish network security either using network security groups (NSGs) or security lists when using private subnets.
Both NSGs and security lists use security rules to control traffic at the packet level. NSGs let you define a set of security rules that applies to a group of virtual network interface cards (VNICs) of your choice, while security lists let you define a set of security rules that applies to all the VNICs in an entire subnet.
Oracle recommends using NSGs instead of security lists because NSGs let you separate the VCN's subnet architecture from your application security requirements.
Follow the instructions in the applicable section to configure your method of network security:
Network Security Groups
To use network security groups (NSGs), create two NSGs. Their roles and some example names are shown in the following table:
| Component NSG Needed For | Example NSG Name |
|---|---|
| EBS Cloud Manager Load Balancer | ebscmlbaas-nsg |
| EBS Cloud Manager Virtual Machine | ebscmvm-nsg |
For more information, see Network Security Groups in the Oracle Cloud Infrastructure Documentation.
To create an NSG:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Under Resources on the navigation menu at the left, select Network Security Groups.
-
Click Create Network Security Group:
-
Name: Specify a name such as
ebscmlbaas-nsgorebscmvm-nsg. -
Create in Compartment: Select your compartment name, such as network-compartment.
-
-
Click Create.
Security Lists (Optional If Not Using NSGs)
In this section, you will create two separate security lists, one for the Oracle E-Business Suite Cloud Manager Compute instance and one for the load balancer. In the following examples, we will use the names ebscmvm-seclist and lbaas-seclist, respectively.
To use security lists, create two separate security lists. Their roles and some example names are shown in the following table:
| Component Security List Needed For | Example Security List Name |
|---|---|
| EBS Cloud Manager Virtual Machine | ebscmvm-seclist |
| EBS Cloud Manager Load Balancer | ebscmlbaas-seclist |
Create the Oracle E-Business Suite Cloud Manager Virtual Machine Security List
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Security Lists.
-
Click Create Security List and specify the following:
-
Create in Compartment: Select your network compartment, as created in Create Compartments.
-
Name: Specify a name such as
ebscmvm-seclist.
-
Create the Load Balancer Security List
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Open the navigation menu. Under Resources, select Security Lists.
-
Click Create Security List:
-
Create in Compartment: Select your network compartment created in Create Compartments.
-
Name: Specify a name, such as
lbaas-seclist.
-
Create Security Rules for the EBS Cloud Manager Virtual Machine and Load Balancer
Create Security Rules for the EBS Cloud Manager Virtual Machine
In this section, you will add the mandatory security rules shown in the following steps to the chosen security mechanism --either network security group or security list-- created in Configure Network Security When Using Private Subnets.
-
Under Allow Rules for Ingress, click + Another Ingress Rule:
-
For the first rule that is needed, modify the default rule as follows:
-
Source Type:
CIDR -
Source CIDR: The CIDR matching the IP address of the machine from which you plan to connect to Oracle E-Business Suite Cloud Manager, such as a bastion server.
-
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range:
22
-
-
For the second rule that is needed, click + Another Ingress Rule and enter the following values:
-
Source Type:
CIDR -
Source CIDR: VCN CIDR
-
IP Protocol: ICMP
-
Type: All
-
Code: All
-
-
For the third rule that is needed, click + Another Ingress Rule and enter the following values:
-
Source Type: CIDR
-
Source CIDR: Enter the CIDR of your LBaaS subnet, lbaas-subnet-ad1. For example,
10.0.1.0/24. Note that the subnet is created in the next step. -
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range:
8081
-
-
-
Under Allow Rules for Egress:
-
(Conditional) If you plan to allow public internet connectivity from your EBS environments, click + Another Egress Rule to add an egress rule to public object storage. Enter the following values:
-
Destination Type:
CIDR -
Destination CIDR:
134.70.0.0/16. This particular CIDR is required to connect to object storage. -
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range: All
-
-
Click + Another Egress Rule and enter the following values:
-
Destination Type: Service
-
Destination CIDR: "All <XXX> Services In Oracle Services Network". Note that XXX is a region-specific code, such as IAD or LHR.
-
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range: All
-
-
Click + Another Egress Rule and enter the following values:
-
Destination Type: CIDR
-
Destination CIDR: VCN CIDR
-
IP Protocol: ICMP
-
Type: Leave this field blank.
-
Code: Leave this field blank.
-
-
Click + Another Egress Rule and enter the following values:
-
Destination Type: CIDR
-
Destination CIDR: VCN CIDR
-
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range: 22
-
-
Click Create Security List.
-
Create Security Rules for the Load Balancer Subnet
In this section, you will add the mandatory security rules shown in the following steps to the chosen security mechanism --either network security group or security list-- created in Configure Network Security
-
Under Allow Rules for Ingress, click + Another Ingress Rule and enter the following values for the ingress rule that is needed:
-
Source Type: CIDR
-
Source CIDR: The CIDR matching the IP address of the machine from which you plan to connect to Oracle E-Business Suite Cloud Manager, such as a bastion server.
-
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range:
443or other port of your choice. This port will be used in step 5 of Run Oracle E-Business Suite Cloud Manager Configure Script for the First Time, when prompting for the Load Balancer Listener Port.
-
-
Under Allow Rules for Egress, click + Another Egress Rule and enter the following values for the egress rule that is needed:
-
Destination Type: CIDR
-
Destination CIDR: The CIDR matching the private IP of the Oracle E-Business Suite Cloud Manager VM's subnet.
-
IP Protocol: TCP
-
Source Port Range: All
-
Destination Port Range:
8081
-
-
Click Create Security List.
Create Subnets
In this section, you will create the following new subnets:
-
One regional or availability domain-specific private subnet where the Oracle E-Business Suite Cloud Manager Compute instance will be created. This may be referred to as the "provisioning VM subnet."
-
One regional or availability domain-specific private subnet for creating the load balancer for Oracle E-Business Suite Cloud Manager.
You will need to specify your own names and parameters, but you can use the examples in the following two tables for guidance.
If you choose to use regional subnets, refer to the following example.
Note: The Security Lists column in the following table is labeled "optional" as it is not applicable if you are using NSGs.
| Subnet Name | CIDR Block | Route Table | Subnet Access | Security List (Optional) |
|---|---|---|---|---|
| ebscm-subnet-phx | 10.0.0.0/24 | ebscm-RouteTable | Private subnet | ebscmvm-seclist |
| lbaas-subnet-phx | 10.0.1.0/24 | lbaas-RouteTable | Private subnet | lbaas-seclist |
If you choose to use availability domain-specific subnets, refer to the following example.
Note: The Security Lists column in the following table is labeled "optional" as it is not applicable if you are using NSGs.
| Subnet Name | Availability Domain (AD) | CIDR Block | Route Table | Subnet Access | Security List (Optional) |
|---|---|---|---|---|---|
| ebscm-subnet-ad1 | AD-1 | 10.0.0.0/24 | ebscm-RouteTable | Private subnet | ebscmvm-seclist |
| lbaas-subnet-ad1 | AD-1 | 10.0.1.0/24 | lbaas-RouteTable | Private subnet | lbaas-seclist |
For each of the subnets you create, perform the following steps:
-
On the Virtual Cloud Networks screen, click the link with the name of your VCN, such as ebscm-vcn.
-
Under Resources in the navigation menu on the left, select Subnets.
-
Click Create Subnet, specifying your choice for the following parameters:
-
Name
-
Subnet Type: Select either Regional (Recommended) or Availability Domain-Specific. If you choose Availability Domain-Specific, select your availability domain.
-
IPv4 CIDR Block
-
Route Table
-
Subnet Access: Select Private Subnet or Public Subnet for the subnet you wish to create.
-
Security Lists: Select the security list that matches the subnet you are defining.
Note: Specifying a security list is not necessary if you are using NSGs.
-
-
Click Create Subnet.
Create Oracle E-Business Suite Cloud Manager Compute Instance
In this section, the Oracle E-Business Suite Cloud Manager administrator performs all tasks as described.
Follow the steps in this section to create and connect to a Compute instance (created using an image in the Oracle Cloud Infrastructure Console Marketplace) that will be used to host Oracle E-Business Suite Cloud Manager.
-
Log in to the Oracle Cloud Infrastructure Service Console.
-
Open the navigation menu. Under Marketplace, click All Applications.
-
If prompted for the compartment, select the compartment where you wish to install Oracle E-Business Suite Cloud Manager.
-
Then, select the Oracle E-Business Suite Cloud Manager image.
-
In the Version drop-down list, ensure that the default, which reflects the latest available version, is selected. The version appears in the form of "Oracle-EBS-Cloud-Manager-<version>-<date>".
-
Select the compartment where you plan to install Oracle E-Business Suite Cloud Manager. For example,
ebscm-compartment. -
Review and accept the Oracle Standard Terms and Restrictions.
-
Click Launch Instance.
-
In the Create Compute Instance dialog box, specify the following:
-
Under Name, enter your choice of name for your instance. For example,
ebscm-instance. -
In Create in compartment, choose your compartment for your instance in the drop-down list.
-
Under Availability Domain, make a suitable selection, based on the subnets you created previously, from the displayed options.
-
Under Image, you will see the name of the Oracle Cloud Infrastructure Console Marketplace image: Oracle E-Business Suite Cloud Manager.
-
Under Shape, you can use the default shape or click Change Shape to select another shape. We recommend that you use a flexible shape, such as "VM.Standard.E4.Flex", starting with 2 OCPUs and 4 GB of memory and tailoring capacity as your needs become clear.
-
Under Primary VNIC Information:
-
Locate the Network subsection, click the "Change Compartment" hyperlink, and select the compartment where your VCN resides. For instance, following our example in Create Compartments, you would select the compartment network-compartment.
-
Also within the Network subsection, choose your VCN from the Select a Virtual Cloud Network drop-down list. For example, ebscm-vcn.
-
Locate the Subnet subsection, click the "Change Compartment" hyperlink, and select the compartment where your VCN resides. For example, network-compartment.
-
Also within the Subnet subsection, specify the Oracle E-Business Suite Cloud Manager subnet from the Select a subnet drop-down list. For example, ebscm-subnet-ad1.
-
If the VM is associated with a public subnet and you want to assign a public IP address, select the Assign a public IPv4 address option.
-
If you plan to use NSGs, perform the following steps to define the EBS Cloud Manager NSGs:
-
Click Show advanced options.
-
Under Advanced Options, select the Use network security groups to control traffic checkbox.
-
Select the EBS Cloud Manager NSGs (for example, ebscmvm-nsg).
-
-
-
Under Add SSH Keys, choose one of the following options for this procedure:
-
Select the Generate a key pair for me option, then click the "Save Private Key" link to download the private key. Doing so allows the SSH connection to be established.
-
Alternatively, select the Upload public key files (.pub) option and then drag and drop the file or browse to specify the file containing your SSH public key generated previously.
-
Another choice is to select the Paste public keys option and paste the SSH public key content in the text field provided, using the content of the public key generated previously.
-
-
Leave the values in the Configure Boot Volume section unselected in order to accept the default volume size.
-
-
Click Create.
Once the instance is created (provisioned), details of the new instance will appear on the screen. Full details, including IP addresses, can also be viewed by clicking on the instance name in the instance list.
When the Oracle E-Business Suite Cloud Manager instance is fully provisioned and running, you can connect to it by following the instructions in Connecting to an Instance in the Oracle Cloud Infrastructure Documentation.
Configure Oracle E-Business Suite Cloud Manager Compute Instance
In this section, the Oracle E-Business Suite Cloud Manager administrator and tenancy administrator perform all the tasks as described.
Follow the instructions in this section to configure your Oracle E-Business Suite Cloud Manager Compute instance. You will perform many of these operations from the Oracle Cloud Infrastructure Service Console.
-
Run Oracle E-Business Suite Cloud Manager Configure Script For the First Time
-
Register Oracle E-Business Suite Cloud Manager as a Confidential Application
-
Run Oracle E-Business Suite Cloud Manager Configure Script For the Second Time
-
Configure Oracle Cloud Infrastructure Email Delivery Service (Optional)
Configure Authentication API Keys
-
If you do not have one already, generate an API signing key and associated fingerprint that will be used by the configuration and networking scripts in subsequent sections. Oracle E-Business Suite Cloud Manager does not support API signing keys with passphrases, so you must generate an API signing key with no passphrase. Reference the Oracle Cloud Infrastructure Documentation site, following the instructions under To Generate an API Signing Key Pair.
-
Add the public key for the Oracle E-Business Suite Cloud Manager administrator user by performing the following steps:
-
Log in to the Oracle Cloud Infrastructure Service Console as the Oracle E-Business Suite Cloud Manager administrator user created previously in Create Users with Oracle E-Business Suite Cloud Manager Administrator Privileges.
-
Click the user avatar icon.
-
Select My Profile from the context menu.
-
Open the navigation menu. Under Resources, click API Keys. Then, click Add Public Key.
-
Select the Paste Public Keys option.
-
Paste the contents of the API public key in the dialog box and click Add. The key's fingerprint is displayed.
-
Copy the Oracle Cloud Infrastructure API private PEM key file to the Oracle E-Business Suite Cloud Manager Compute instance. The file must be placed in a directory owned by the
oracleuser, for example/u01/install/APPS/.oci. The fully qualified path to the Oracle Cloud Infrastructure API private PEM key file will be needed for runningconfigure.plin Run Oracle E-Business Suite Cloud Manager Configure Script for the First Time.
-
Identify Credential Required for Configuration Steps
While still logged into the Oracle Cloud Infrastructure Service Console, identify and record the OCID of your tenancy. You will need to provide this credential when you run the Oracle E-Business Suite Cloud Manager configure.pl script.
-
Open the navigation menu and select Governance & Administration. Under Account Management, click Tenancy Details.
-
Click Copy to copy the OCID of the tenancy into your clipboard, and record this value for use in the next section.
Run Oracle E-Business Suite Cloud Manager Configure Script for the First Time
The Oracle E-Business Suite Cloud Manager administrator performs the tasks in this section.
-
Connect to your Oracle E-Business Suite Cloud Manager Compute instance using SSH.
-
As the
oracleuser, run theconfigure.plscript:$ sudo su - oracle $ cd /u01/install/APPS/apps-unlimited-ebs/bin $ perl configure.pl
Note the creation of the session-specific log file, which will have the format shown in the following example:
Log File : /u01/install/APPS/apps-unlimited-ebs/out/configure_<date>_<time>.log
-
When prompted, enter an Oracle E-Business Suite Cloud Manager admin password and enter your user details required for authentication:
Enter New Oracle E-Business Suite Cloud Manager Admin Password : Re-enter New Oracle E-Business Suite Cloud Manager Admin Password : Enter Oracle E-Business Suite Cloud Manager Admin User OCID (Default Domain) : ocid1.user.oc1..xxxxxxxxxx Enter Full path to API Private Signing Key : /u01/install/APPS/.oci/oci_api_key.pem Enter Tenancy OCID : ocid1.tenancy.oc1..xxxxxxxxxx
Note: The password should contain at least one of these special characters: _ (underscore), # (hash), or $ (dollar). This password is used by the Oracle E-Business Suite Cloud Manager administrator to connect to the Cloud Manager database, and to run subsequent scripts.
-
You will now be prompted for the Oracle E-Business Suite Cloud Manager Administrator Group. This example shows a group called ebscmadmin-grp being selected from the list of available choices.
Available Groups from OCI for provided User: Group Name Description ---------- ----------- 1: ebsdevdba-grp EBS Dev DBA Group 2: ebscmadmin-grp EBS Cloud Manager Admin Group 3: ebsdemodba-grp EBS Test DBA Group 4: ebsqadba-grp EBS QA DBA Group Choose Oracle E-Business Suite Cloud Manager Administration group from above list: 2
-
You will now be asked if you wish to use an existing load balancer:
Do you wish to use an existing load balancer? 1: Yes 2: No Enter your choice: 1
-
If you choose option 1 (Yes), you will be asked to choose a load balancer from a list such as shown in this example. Note that the available load balancers reside in the same VCN and the same compartment as the Oracle E-Business Suite Cloud Manager VM.
Available Load Balancers 1: demolbaas1 2: demolbaas2 Choose a load balancer from the above list: 1
Note: If you choose an existing load balancer, then the
configure.plscript creates the necessary new resources under that load balancer, including "listener", "backend set", "backend", and "certificate". The creation of the new resources will not affect any existing resources under that load balancer. -
Otherwise, if you choose option 2 (No), indicating that you wish to create a new load balancer, you will need to choose a load balancer visibility type, shape, and the subnets in which to place the load balancer. Example screens are shown as follows.
-
Choose the load balancer visibility type:
Choose Load Balancer Visibility Type: 1: Public 2: Private Enter your choice: 1
Select option 1 (Public) or option 2 (Private) for the load balancer visibility type.
-
Enter the bandwidth for the flexible shape load balancer:
Choose Size of Bandwidth for Flexible Shape Load Balancer: Enter Minimum Bandwidth in Mbps : 10 Enter Maximum Bandwidth in Mbps : 10
-
Subnets in which to place the load balancer (as defined in Create Network Resources for Use with Public Subnets or Create Network Resources for Use with Private Subnets):
Available List of Subnets Regional ( recommended ): ------------------------------ 1: lbaas-subnet-phx Availability Domain: CQIl:PHX-AD-1 ------------------------------ 2: lbaas-subnet-ad1 Availability Domain: CQIl:PHX-AD-2 ------------------------------ 3: lbaas-subnet-ad2 4: othersubnet1 Availability Domain: CQIl:PHX-AD-3 ------------------------------ 5: othersubnet2 6: othersubnet3 7: othersubnet4 Choose subnet from above list: 1
-
If you are in a single availability domain region, your screen will show only two subnet groupings, one for regional subnets and one for your single availability domain.
-
When creating a public load balancer, only public subnets are listed.
If you are in a multiple availability domain region and you choose an availability domain-specific public subnet (options 2 to 7 in the previous example), and not a regional subnet (option 1 in the previous example), you will be prompted for a second availability domain-specific subnet for the HA load balancer, as shown.
Choose AD Specific HA subnet from above list: 6
-
-
When prompted, enter the load balancer listener port:
Enter Load Balancer Listener Port : 443
-
When prompted, enter the CIDR range information to access the load balancer port:
Enter CIDR Block (Range) from which Client can Access Load Balancer Listener Port: 192.0.2.0/24
-
-
-
Review the summary screen containing the information you specified earlier for Oracle E-Business Suite Cloud Manager.
---------------------------------------------------------------------------------------- Summary of Inputs ---------------------------------------------------------------------------------------- Oracle E-Business Suite Cloud Manager User Name ( Non Federated ) : xxxx.xxxxx@example.com Oracle E-Business Suite Cloud Manager User OCID ( Non Federated ) : ocid1.user.oc1..xxxxxxxxxxx Fingerprint of API Public Key : xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx Path to Private PEM key file : /u01/install/APPS/.oci/oci_api_key.pem Tenancy OCID : ocid1.tenancy.oc1..xxxxxxxxxxxxxx Region: xx-xxxxxx-1 Oracle E-Business Suite Cloud Manager VM Compartment Name : ebscm-compartment Oracle E-Business Suite Cloud Manager VM Compartment OCID : ocid1.compartment.oc1..xxxxxxxxxxxxxxx Oracle E-Business Suite Cloud Manager Administration Group Name : ebscmadmin-grp Oracle E-Business Suite Cloud Manager Administration Group OCID : ocid1.group.oc1..xxxxxxxxxxxxxxxxxxxx Network Compartment Name : network-compartment Network Compartment OCID : ocid1.compartment.oc1..xxxxxxxxxxxxxxxxxxxx Network VCN Name : ebscm-vcn Network VCN OCID : ocid1.vcn.oc1.phx-subnet.xxxxxxxxxxxxxxxxxxxxxxxxxx Use an existing Load Balancer : false Load Balancer Listener Port : 443 CIDR Block (Range) from which Client can Access Load Balancer Listener Port : 192.0.2.0/24 Load Balancer Visibility Type : Public Load Balancer Shape : flexible Load Balancer Minimum Bandwidth in Mbps: 10 Load Balancer Maximum Bandwidth in Mbps: 10 Load Balancer Subnet Name : Public Load Balancer Subnet OCID : ocid1.subnet.oc1.phx-subnet1.xxxxxxxxxxxxxxxxxxxx Load Balancer Subnet CIDR : 10.0.3.16/28 ---------------------------------------------------------------------------------------- Do you wish to continue? 1: Yes 2: No Enter your choice: 1
If you are satisfied with the values shown, enter option 1 to proceed.
-
You will then see a screen containing a success message, similar to the following example, plus the load balancer URL you will need later.
======================================================================================================== Load Balancer demolbaas1 configuration completed. Review screen messages above to determine if security rules are missing and must be added in order to access the load balancer URL. ======================================================================================================== ======================================================================================================== Register confidential application in IDCS with the URL: https://xxx.xxx.xx.xxx:xxx and then re-run this script to update your IDCS configuration. ========================================================================================================
Register Oracle E-Business Suite Cloud Manager as a Confidential Application
In this section, you will register Oracle E-Business Suite Cloud Manager as a confidential application.
As an Oracle E-Business Suite Cloud Manager administrator who has been previously granted the Application Administrator role (in Create Users with Oracle E-Business Suite Cloud Manager Administrator Privileges), register Oracle E-Business Suite Cloud Manager as a confidential application using the following steps.
-
Open the navigation menu and click Identity & Security. Under Identity, click Domains.
-
Select the root compartment in the Compartment drop-down list.
-
Within the list of domains, click the link for the "Default" domain.
-
Click Integrated applications in the menu on the left.
-
Click Add application.
-
Select Confidential Application in the dialog box.
-
Click Launch Workflow.
-
Under Add application details, enter the following:
-
Name: Enter a name.
-
Description: Enter a description.
-
-
Click Next.
-
Under Configure OAuth:
-
Click Configure this application as a client now.
-
Under Allowed Grant Types, select the following options:
-
Client Credentials
-
Refresh Token
-
Authorization Code
Additionally, if you plan to create standby environments or to upgrade environments from Oracle E-Business Suite Release 12.1 to Release 12.2, select the Resource Owner option.
-
-
Redirect URL: This is the load balancer URL from step 7 of Run Oracle E-Business Suite Cloud Manager Configure Script for the First Time in the following format:
<Your Load Balancer URL>/cm/auth/callback. For example:https://xxx.xxx.xx.xxx:xxx/cm/auth/callback -
Post-Logout Redirect URL:
<Your Load Balancer URL>/cm/ui/index.html?root=login. For example:https://xxx.xxx.xxx.xxx:xxx/cm/ui/index.html?root=login -
Logout URL: Leave this field empty.
-
Under Client Type, ensure that the Confidential option is selected.
-
Select the Introspect option for Allowed Operations.
-
Under Token Issuance Policy, select the Add app roles checkbox.
-
Click Add roles.
-
Select Authenticator Client and Me.
-
Click Add, and then click Next.
-
-
-
Under Configure policy, click Finish.
-
Make a note of the following values under General Information:
-
Client ID
-
Client secret (In order to view, click Show secret.)
-
-
Click Activate and confirm to activate the confidential application.
-
Record the Domain URL found in the Overview page for the domain.
Run Oracle E-Business Suite Cloud Manager Configure Script for the Second Time
-
Connect to your Oracle E-Business Suite Cloud Manager Compute instance using SSH.
-
As the
oracleuser, run theconfigure.plscript again:$ sudo su - oracle $ cd /u01/install/APPS/apps-unlimited-ebs/bin $ perl configure.pl
Note the creation of the session-specific log file, which will have the format shown in the following example:
Log File : /u01/install/APPS/apps-unlimited-ebs/out/configure_2019-07-11_10_02_09.log
-
When prompted, enter the Oracle E-Business Suite Cloud Manager administrator password and your Oracle Identity Domain application details, as shown in the following example.
Enter Oracle E-Business Suite Cloud Manager Admin Password : Enter IDCS Client ID : <client id> (In a format similar to xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx) Enter IDCS Client Secret : <client secret> (In a format similar to xxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx) Enter IDCS URL : <client url> (Instructions for determining the IDCS URL found in the content that follows)
The values you will need to enter for client ID and client secret were established when you registered Oracle E-Business Suite Cloud Manager as a confidential application in Register Oracle E-Business Suite Cloud Manager as a Confidential Application.
To find the IDCS URL:
-
In the OCI Console menu, navigate to Identity & Security, then Domains.
-
Select the root compartment.
-
Click on Default domain.
-
The IDCS URL can be found in the Identity Domain settings page under Domain URL. Copy the URL and remove ":443" to get your IDCS URL.
For commercial cloud regions, the format is similar to
https://idcs-xxxxxxxxx.identity.oraclecloud.com. For government cloud regions, the formatting is similar tohttps://idcs-xxxxxxxx.<regional-idcs-instance>.identity.oci.<realm>.com.
-
-
You will see a summary screen containing the information you specified earlier. The following is example output for a tenancy in a commercial cloud region:
---------------------------------------------------------------------------------------- Summary of Inputs ---------------------------------------------------------------------------------------- IDCS Client ID : xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx IDCS Client Secret : xxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx IDCS URL : https://idcs-xxxxxxxxxxxxxxxxxxxxxx.identity.oraclecloud.com ---------------------------------------------------------------------------------------- Do you wish to continue? 1: Yes 2: No Enter your choice: 1
Choose option 1 to continue.
-
A Login URL is then displayed on the screen, as shown in the following example. This is the URL by which users will access the Oracle E-Business Suite Cloud Manager UI.
======================================================================================== Finished Configuring Oracle E-Business Suite Cloud Manager VM. Login URL : https://xxx.xxx.xx.xxx:xxx Ensure the confidential application is correctly configured in IDCS as per the documentation. ========================================================================================
Note: If you wish to update the URL by which users will access the Oracle E-Business Suite Cloud Manager UI, you can do so using your own DNS registered host name and certificate by following the instructions described in "Update Oracle E-Business Suite Cloud Manager URL" in Update the Oracle E-Business Suite Cloud Manager Load Balancer URL.
Configure Oracle Cloud Infrastructure Email Delivery Service (Optional)
This section provides instructions on how to set up the Oracle Cloud Infrastructure Email Delivery Service to send notifications.
Steps to Perform Prior to Enabling Mailer
Before enabling the mailer, you must perform these steps:
-
Generate SMTP credentials by following the instructions in Generate SMTP Credentials for a User in the Oracle Cloud Infrastructure Documentation.
-
Create an Approved Sender by following the instructions in Managing Approved Senders in the Oracle Cloud Infrastructure Documentation.
Enable and Disable the Mailer
In order to enable and disable the mailer, use the command provided in Enable Mailer Configuration and Disable Mailer Configuration.
Update to Latest Version of Oracle E-Business Suite Cloud Manager
To obtain the latest fixes, update to the latest version by following the instructions in Update Oracle E-Business Suite Cloud Manager to the Latest Version.
Set Up Notifications With OCI Email Delivery Service
There are certain points within the deployment process in which you must provide the CIDR for the Oracle Cloud Infrastructure Email Delivery service SMTP server. In order to obtain this CIDR, perform the following steps:
-
See Configure SMTP Connection for the list of SMTP endpoints. Contact your tenancy administrator to determine the SMTP endpoint being used.
-
Run
nslookupon the endpoint. For example:$ nslookup smtp.us-phoenix-1.oraclecloud.com
-
The resulting output will be the public IP address for the SMTP endpoint. The CIDR for the IP address obtained will be <IP address>/32. For example:
138.1.38.16/32.
Oracle E-Business Suite Cloud Manager Deployment for Demo and Test Purposes (Commercial Cloud Regions Only)
You can leverage the procedure provided in this section to simplify tenancy preparation, Oracle E-Business Suite Cloud Manager deployment, and configuration by taking advantage of available automation. Doing so will streamline portions of the procedure documented in this chapter, as well as the instructions in Set Up Your Tenancy to Host Oracle E-Business Suite Environments.
This simplified procedure is most appropriate for demo purposes, as it has the following restrictions:
-
The automation deploys a new VCN and subnets for Oracle E-Business Suite Cloud Manager, load balancers, and the first set of Oracle E-Business Suite environments. The subnets are public regional subnets.
-
The automation creates a new compartment for all the assets. An existing compartment cannot be used, and multiple compartments are not supported.
Identify or Create a Tenancy and Obtain Tenancy Administrator User Credentials
If you have an existing tenancy, you must have a user with tenancy administrator privileges to run this procedure.
If you do not have an existing tenancy, you can sign up for a free trial account using the following steps:
-
Go to https://www.oracle.com/cloud/free/ and click Start for free.
-
On the Oracle Cloud Sign Up page, enter the requested information including your desired tenancy name and tenancy password.
-
Review your details and click Submit.
Note: Ensure that you use the same email address that was used when you registered.
You will be directed to the Oracle Cloud Infrastructure Console where you will perform the remainder of the procedure.
-
Record your trial user name and password for future reference.
Prepare Your Tenancy for Oracle E-Business Suite Cloud Manager Stack for Demos
Follow the instructions detailed in Register Oracle E-Business Suite Cloud Manager as a Confidential Application. After completing these instructions, continue with the steps in Oracle E-Business Suite Cloud Manager Deployment and Configuration.
Oracle E-Business Suite Cloud Manager Deployment and Configuration
In this section you will deploy and configure an Oracle E-Business Suite Cloud Manager Compute instance using an Oracle Marketplace stack.
Sign in to the Oracle Cloud Infrastructure Console
Use the tenancy administrator credentials to sign in to Oracle Cloud Infrastructure Console.
Sign in to the Oracle Cloud Infrastructure Console using the following:
-
User Name: Tenancy Admin User
-
Password: Tenancy Admin Password
Deploy and Configure Oracle E-Business Suite Cloud Manager
You will now deploy and configure Oracle E-Business Suite Cloud Manager using a Marketplace stack. The stack creates the following cloud resources:
-
A compartment to contain resources required by Oracle E-Business Suite Cloud Manager.
-
An Oracle E-Business Suite Cloud Manager Administrators IAM (Identity and Access Management) user and group, as well as the policies required to manage the compartment.
-
Network resources - including a VCN, an internet gateway, subnets, route tables, security lists, and security rules.
-
A Compute instance for running Oracle E-Business Suite Cloud Manager.
Then, the stack will configure Oracle E-Business Suite Cloud Manager to work with your Oracle Cloud Infrastructure tenancy and the newly created Oracle Cloud Infrastructure resources.
Perform the following steps:
-
While signed in to the Oracle Cloud Infrastructure Service Console, open the navigation menu. Click Marketplace and then All Applications.
-
In the Search field, search for
Oracle E-Business Suite Cloud Manager Stack for Demosand then click the Oracle E-Business Suite Cloud Manager Stack for Demos listing. -
In the Version drop-down list, ensure that the default is selected. For example, Oracle-EBS-Cloud-Manager-RM-XX.X.X.X-XXXX.XX.XX.
-
In the Compartment drop-down list, select the parent compartment of the compartment where the Oracle E-Business Suite Cloud Manager Compute instance will be deployed. For example, mycompanytenancy(root).
-
Review and accept the Oracle standard Terms and Restrictions.
-
Click Launch Stack.
-
On the Configure Variables screen, enter the following values:
-
Under Setup Details:
-
Resource Prefix: A prefix that will be added to names of all the cloud resources created by the stack.
-
Leave the Single Compartment Setup checkbox selected.
-
Select the compartment under which the new compartment will be created.
-
-
Under EBS Cloud Administrator Details:
-
Enter the user name corresponding to the EBS Cloud Manager administrator created in step 5 of Prepare Your Tenancy for Oracle E-Business Suite Cloud Manager Stack for Demos.
-
Enter the email address of the EBS Cloud Manager administrator.
-
Make sure the Create new REST API Key checkbox is selected.
-
-
Under EBS Cloud Manager Instance Details:
-
Enter the load balancer URL you provided in step 10 (3) of Register Oracle E-Business Suite Cloud Manager as a Confidential Application.
-
Select VM.Standard.E2.2 for EBS Cloud Manager Shape.
-
Enter a password which matches the following criteria: 8 to 30 characters, at least one lowercase character, one uppercase character, one special character from _#$.
-
Enter the contents of a public key file that will be used to connect using SSH to your Oracle E-Business Suite Cloud Manager Compute instance. For more details on how to generate the key, see Creating a Key Pair in the Oracle Cloud Infrastructure Documentation.
-
Choose the availability domain that ends in -1 from the list under EBS Cloud Manager Availability Domain.
-
-
Under EBS Cloud Manager Network Details:
-
Leave the Custom CIDR Ranges checkbox deselected.
-
Enter a CIDR block that corresponds to the IP range of the clients you plan to use to connect to Oracle E-Business Suite Cloud Manager. For the whole internet, use 0.0.0.0/0.
-
Enter the values corresponding to Client ID, Client Secret, and IDCS Client Tenant from Register Oracle E-Business Suite Cloud Manager as a Confidential Application.
-
-
-
On the Review screen, verify the information and click Create.
-
This takes you to the Stack Details page for your newly created stack. On this page, click the Terraform Actions drop-down list and select Apply.
-
In the Apply dialog window, leave the default settings as-is and click Apply.
-
On the Job Details page, you will see the job status which will cycle through Accepted, In Progress, and Succeeded. After the job succeeds, you will have all the network resources (VCN, load balancer, subnets, and so on) required to deploy the Oracle E-Business Suite Cloud Manager Compute instance.
-
On the Application Information tab are details related to the Oracle E-Business Suite Cloud Manager instance and load balancer.
Make a note of the Private IP, Public IP, Login URL, and LB Public IP. These variables are needed for the remainder of the procedures in this section.
Ensure You are on the Latest Cloud Manager Version
Check to make sure you are on the latest cloud manager version by following the instructions in Update Oracle E-Business Suite Cloud Manager to the Latest Version (Conditional).
Log in to Oracle E-Business Suite Cloud Manager
Before logging in to the Oracle E-Business Suite Cloud Manager web application, you need to add the host name in the Login URL to your local computer hosts file. Follow these instructions to perform this configuration:
-
Edit the local hosts file on your laptop and add an entry.
For Windows Users
-
Navigate to Notepad in your start menu.
-
Right-click on Notepad and select the option to run as administrator.
-
In Notepad, click File, then click Open.
-
Browse to
C:\\Windows\System32\drivers\etc. -
Find the file hosts.
-
In the hosts file, scroll down to the end of the content.
-
Add the following entry to the very end of the file:
<LB Public IP> <Cloud-Manager-web-entry>
-
Save the file.
-
-
Using the Login URL found in the Application Information tab, log in to Oracle E-Business Suite Cloud Manager using your Oracle Identity Cloud Service credentials.
Once logged in, you are on the Environments page.