1 Introducing Oracle Database Firewall
This chapter contains:
Downloading the Latest Version of This Manual
You can download the latest version of this manual from the Oracle Database Firewall Web site, which is in the Database section of Oracle Technology Network. The URL is as follows:
http://www.oracle.com/technetwork/indexes/documentation/index.html
Oracle Database Firewall System Architecture
This section contains:
-
Ways to Connect Oracle Database Firewall to a Database Network
-
Integrating Oracle Database Firewall with Third-Party Products
About the Oracle Database Firewall System Architecture
The typical Oracle Database Firewall architecture has the following main components:
-
The database network, containing the database server and its clients: You are not required to install Oracle Database Firewall onto the database server or clients. However, if needed, you can install the Database Firewall Local Monitoring on the database server, which enables the Database Firewall to monitor SQL traffic originating from the users or processes that have direct access (for example, through the console) to the database computer.
-
The Database Firewall: This is a dedicated server that runs the Oracle Database Firewall software. Each Database Firewall collects SQL data from SQL databases, and then sends this SQL data to the Database Firewall Management Server to be analyzed in reports. After the Database Firewall sends the SQL data to the Management Server, it deletes it locally. The SQL data is then stored in the Management Server.
-
Database Firewall applications and other third-party applications: These applications perform system configuration, monitoring, and administration. If necessary, you can use a single computer to operate these applications. However, typically, there is a separate computer for each application, because applications are often used by different people or from different locations.
Examples of Database Firewall applications include the Oracle Database Firewall Administration Console and Oracle Database Analyzer. For details about the Analyzer, see the Oracle Database Firewall Security Guide.
You must use a Database Firewall Management Server to control one or more Database Firewall installations. Figure 1-1 shows an architecture for such a system. A Database Firewall Management Server is suitable for larger enterprise installations that protect multiple databases at different sites.
Figure 1-1 illustrates the position of the Management Server in the Database Firewall architecture.
Figure 1-1 Enterprise Architecture Using a Database Firewall Management Server
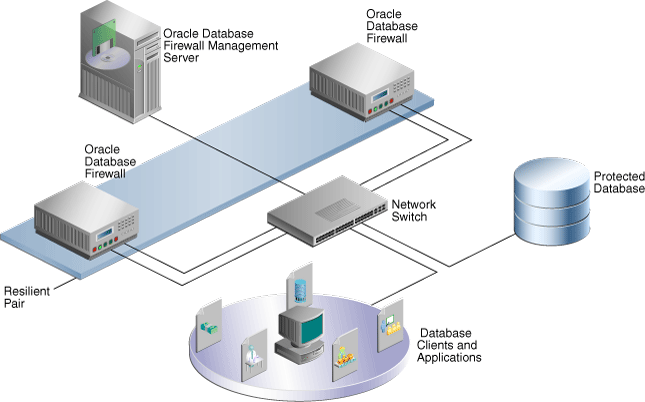
Description of "Figure 1-1 Enterprise Architecture Using a Database Firewall Management Server"
Note:
-
This figure shows only one protected database for simplicity. A typical architecture will have many protected databases.
-
Generally, Database Firewalls use different network ports (network devices and therefore, network paths) to connect to the Management Server. The Network Switch in this diagram shows two port connections for each of the Database Firewalls.
High-Availability Resilient Pairs
You can configure pairs of Database Firewalls or pairs of Database Firewall Management Servers, or both, to provide a high-availability system architecture. These pairs are known as resilient pairs. The resilient pair configuration works in Database Activity Monitoring (DAM) mode only.
During system configuration, one device is nominated as the primary device and the other as the secondary device. The primary device carries out all normal operations while the secondary device monitors traffic, but gives alerts only if the primary device fails.
Both primary and secondary Database Firewalls:
-
Receive the same span traffic
-
Have the same configuration (the Management Server synchronizes this)
-
Create log files according to the policy applied
Only the primary Database Firewall:
-
Sends out real-time alerts
-
Runs user role audits (URA) and stored procedure audits (SPA)
The Management Server collects logs from the Primary Database Firewall, and deletes the log files from both Database Firewalls.
If the Primary Database Firewall is not available or cannot be contacted by the Management Server, it collects the log files from the Secondary Database Firewall and promotes the Secondary Database Firewall to be the Primary (so it will start sending out real-time alerts and running SPA/URA).
Figure 1-2 shows a pair of Oracle Database Firewalls and a pair of Database Firewall Management Servers being used to protect a single database.
Figure 1-2 Oracle Database Firewall High Availability
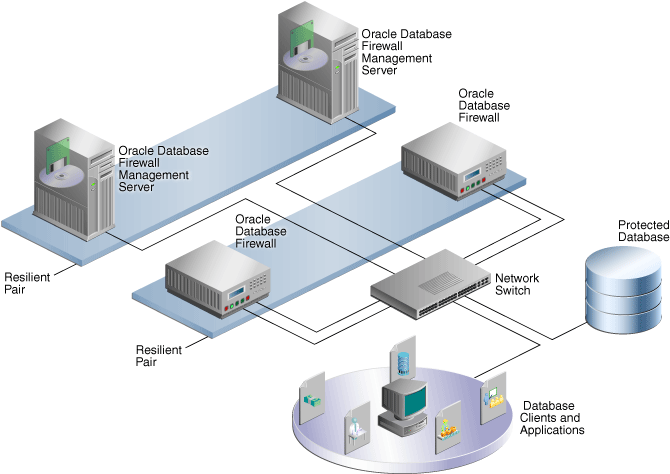
Description of "Figure 1-2 Oracle Database Firewall High Availability"
Ways to Connect Oracle Database Firewall to a Database Network
Oracle Database Firewall can connect to the database network in one of two ways:
-
Through a hub, tap or network switch configured with a "spanning port": This method sends a copy of all database traffic to the Database Firewall. This configuration enables a Database Firewall to operate as an off-line audit and monitoring system, and produce warnings of potential attacks, but it cannot block unwanted traffic.
For more information about connecting hubs, taps or switches, see the following Web site:
-
Inline between the database clients and database: This method enables Database Firewall to both block potential attacks and/or operating as an audit or monitoring system.
Integrating Oracle Database Firewall with Third-Party Products
You can integrate Oracle Database Firewall with the following third-party products:
-
BIG-IP Application Security Manager (ASM): This product from F5 Networks, Inc. is an advanced Web Application Firewall (WAF) that provides comprehensive edge-of-network protection against a wide range of Web-based attacks. It analyzes each HTTP and HTTPS request, and blocks potential attacks before they reach the Web application server. For more information, see Chapter 11, "Using Oracle Database Firewall with BIG-IP ASM."
-
ArcSight Security Information Event Management (SIEM): This product is a centralized system for logging, analyzing, and managing syslog messages from different sources. For more information, see Chapter 12, "Using Oracle Database Firewall with ArcSight SIEM."
Using the Oracle Database Firewall Administration Console
This section contains:
About the Oracle Database Firewall Administration Console
The Administration Console is a Web browser-based application that you use to configure, manage, and monitor Oracle Database Firewall. It is available on each Database Firewall (either standalone or managed) and Management Server.
The Administration Console is intended for use by network or system administrators who are responsible for IT systems deployment, maintenance, monitoring, and reporting.
Figure 1-3 shows the top portion of the status page of a managed Database Firewall Administration Console. (For a standalone Database Firewall, see "Step 1: Set the Database Firewall Date and Time".)
Figure 1-3 Dashboard Page of the Management Server Administration Console
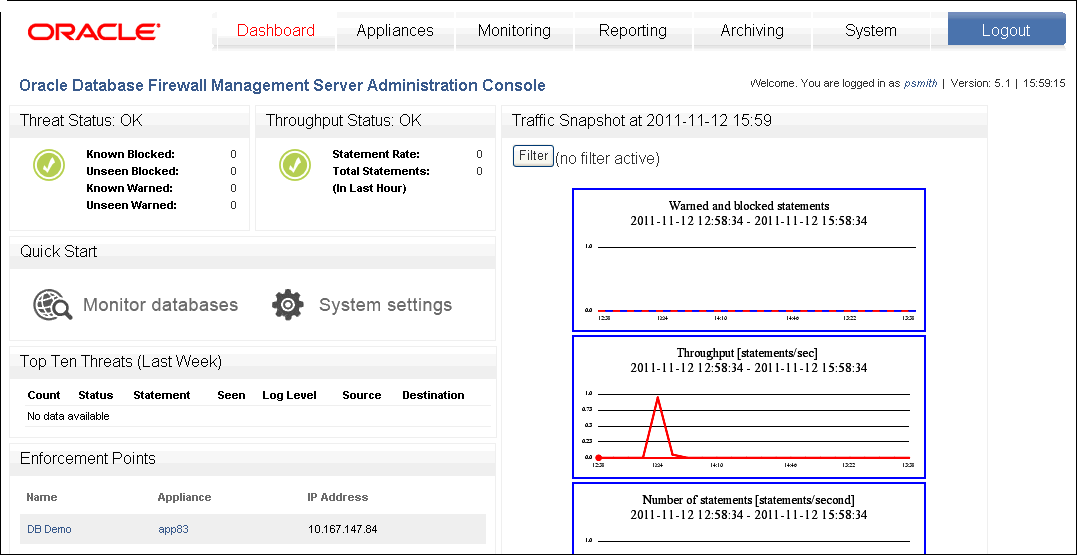
Description of "Figure 1-3 Dashboard Page of the Management Server Administration Console"
You use the Administration Console to:
-
Deploy policies that were created in the Analyzer, by creating enforcement points for your site's protected databases
-
Configure system settings for the Oracle Database Firewall.
-
Configure ArcSight SIEM connectors.
-
Create, find, and configure password security policies for users.
-
View and capture logged data.
All users of the Administration Console must enter a valid login ID and password before access is granted.
Because the Administration Console is a browser-based application, you can use it from any computer that has a supported Web browser, such as Internet Explorer. You can restrict this access by IP address.
Which Administration Console Should I Use?
There are three possible Administration Consoles that you can use: one for a standalone Database Firewall, one for a Database Firewall that is managed by a Management Server, or one used by the Management Server itself.
The tasks that you perform in each are as follows:
-
Tasks Performed in a Standalone Database Firewall Administration Console
-
Tasks Performed in a Managed Database Firewall Administration Console
Tasks Performed in a Standalone Database Firewall Administration Console
Tasks performed in a standalone Database Firewall Administration Console are as follows:
-
Using the Dashboard to view the overall system behavior
-
Management functions such as suspending, resuming, and changing Database Firewall controls or restarting a Database Firewall
-
System settings, such as changing the IP address, time, and keyboard settings
-
Checking the status of the standalone Database Firewall server
-
Configuring e-mail setup, such as the SMTP server address
-
Time synchronization and time offsets
-
Configuring public key synchronization
-
Configuring the Management Server certificate (this determines whether this is a standalone or managed Database Firewall)
-
Managing log files
-
Viewing system events
-
Summarizing traffic log files
-
Viewing and filtering the administration log
-
Repairing log files
-
Configuring, viewing, and approving changes found in stored procedure or user role auditing
-
Managing syslog and ArcSight SEIM connectors, and e-mail alerts
-
Creating and managing user accounts
-
Showing network traffic and capturing it to a file; finding traffic sources
-
Creating enforcement points and configuring protected databases
-
Uploading policies
-
Scheduling reports
-
Archiving jobs
Tasks Performed in a Managed Database Firewall Administration Console
Tasks performed in a managed Database Firewall Administration Console are as follows:
-
Viewing and updating system settings
-
Checking the status of the managed Database Firewall
-
System and network settings, such as changing the IP address, time, and keyboard settings
-
Time synchronization and time offsets
-
Configuring public key synchronization
-
Configuring the Management Server certificate (this determines whether this is a standalone or managed Database Firewall)
-
Configuring the ArcSight connector
-
Creating and managing user accounts
-
Showing network traffic and capturing it to a file
Tasks Performed in a Management Server
Tasks performed in a Management Server:
-
Using the Dashboard to view the overall system behavior
-
Management functions such as suspending, resuming, and changing Database Firewall controls or restarting a Database Firewall
-
Configuring resilient pairs of Management Servers
-
System settings, such as changing the IP address, time, and keyboard settings
-
Checking the status of the Management Server server
-
Configuring e-mail setup, such as the SMTP server address and so on
-
Time synchronization and time offsets
-
Configuring public key synchronization
-
Managing log files
-
Viewing system events
-
Summarizing traffic log files
-
Viewing and filtering the administration log
-
Repairing log files
-
Managing log files
-
Configuring, viewing, and approving changes found in stored procedure or user role auditing
-
Managing syslog and ArcSight SEIM connectors, and e-mail alerts
-
Creating and managing user accounts
-
Creating enforcement points and configuring protected databases
-
Uploading policies
-
Scheduling reports
-
Archiving jobs
Logging in to the Administration Console
To log in to the Administration Console:
-
Open a Web browser from any computer that has network access to Oracle Database Firewall.
-
Enter the following URL:
https://ip_address/user/loginProvide the IP address for the server on which Oracle Database Firewall is installed. For example:
https://192.0.2.206/user/login
If you change the user interface port number (by using the System Settings page of the Administration Console), then you must also include this port number in the URL. Use the following syntax:
https://ip_address:port/user/login
For example:
https://192.0.2.206:444/user/login
Add this address to your Favorites to make it easy to access.
-
If you see the following prompt in Internet Explorer, click OK.
Description of the illustration image007.gif
-
If you see the following message, click Continue to this website:
Description of the illustration image009.gif
-
Enter the user name and password for an account that has System Administrator privileges.
The Administration Console appears. The following screen shows how the Administration Console appears for a managed Database Firewall.
Description of the illustration image011.jpg
When you log into the Management Server, the Administration Console appears as follows. You use the Appliances tab to manage individual Database Firewalls.

Description of the illustration mgmt_adm_con.gif
Administration Console Tabs
The Administration Console contains a collection of tab along the top of the page, which contains the following options:
-
Dashboard. (Management Server and standalone Database Firewall only) Provides a high-level view of important information about the databases being protected, such as the threat status, throughput, and top ten threats (see Chapter 13, "System Administration"). Key indicators are shown in charts, which are intended to be used by IT and security managers who are responsible for the day-to-day monitoring of the system.
The Dashboard also provides Quick Start options that allow the system's configuration settings to be set up with ease.
-
Appliances. (Management Server only) Enables you to define each Oracle Database Firewall that the Oracle Database Firewall Management Server is required to manage (see "Configuring Oracle Database Firewalls").
-
Monitoring. (Management Server and standalone Database Firewall only) Allows you to configure enforcement points, set up the details of the protected databases, and deploy policies. See the following sections for more information:
-
Oracle Database Firewall Security Guide for information about listing and uploading policies
-
Reporting. (Management Server and standalone Database Firewall only) Allows you to generate a wide variety of different types of reports. The reports can be generated and displayed as Adobe Acrobat PDF documents or Microsoft Excel (XLSX) spreadsheets.
You can schedule reports to run automatically at defined intervals, such as every day, week or month. Scheduled reports are automatically forwarded to named e-mail addresses. See the Oracle Database Firewall Security Guide for how to schedule reports.
Oracle Database Firewall provides a large number of data access, management, security, system, Sarbanes-Oxley (SOX), Payment Card Industry (PCI), Data Protection Act (DPA), Gramm-Leach-Bliley Act (GLBA) and Health Insurance Portability and Accountability Act (HIPAA) report types by default, giving full traceability of all essential information over a selected date and time range.
-
Archiving. (Management Server and standalone Database Firewall only) Provides options that enable important data to be archived to prevent loss of data in the unlikely event of a disk or other system error (see "Archiving Data").
-
System. (Management Server, standalone Database Firewall, and managed Database Firewall) Allows initial configuration of Oracle Database Firewall, such as IP addresses and time settings. These options are used during initial deployment of Oracle Database Firewall (see "Configuring the System").
Most pages accessed from the top bar contain a menu of further sub-options along the left side of the page.
Security Guidelines
Consult the Oracle Database Firewall Security Guide for information on protecting your data and general recommendations about deploying Database Firewall in a network and in special configurations.