4 Adding and Managing an Oracle Privileged Account Manager Server
This chapter provides information that administrators must know to add, configure, and manage an Oracle Privileged Account Manager server.
The topics in this chapter include
-
Section 4.3, "Configuring an External Identity Store for Oracle Privileged Account Manager"
-
Section 4.4, "Managing an Oracle Privileged Account Manager Server"
Note:
-
Refer to "Oracle Fusion Middleware Directory Structure" in the Oracle Fusion Middleware Installation Planning Guide for information about directory structure.
-
For detailed information about starting WebLogic and Managed Servers, see "Starting or Stopping the Oracle Stack" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
-
You must have the Application Configurator Admin Role and credentials to start the Oracle Privileged Account Manager server.
4.1 Overview
The Oracle Privileged Account Manager server is a component that handles password requests, generates passwords, and protects the password keystore.
The Oracle Privileged Account Manager server implements the core functionality of Oracle Privileged Account Manager and makes authorization decisions that determine:
-
Which targets and privileged accounts are exposed to administrators and end-users
-
Which operations administrators and end-users can perform on targets, privileged accounts, and policies
In addition, the Oracle Privileged Account Manager server
-
Supports usage and password policies for accounts
-
Enforces the authorization decisions mentioned
-
Supports authentication by using the SAML-based Oracle Security Token from OPSS Trust Services and HTTP-Basic Authentication
-
Supports different Admin Roles for Oracle Privileged Account Manager server
Note:
For security purposes, the Oracle Privileged Account Manager server only responds to SSL traffic.
When you add the Oracle Privileged Account Manager server target to the Oracle Privileged Account Manager user interface or to the Oracle Privileged Account Manager command line tool (CLI), you must provide the SSL endpoint as https://hostname:sslport/opam.
By default, WebLogic responds to SSL using port 7002 on the Admin Server and port 18102 on the Managed Server. You can use the WebLogic console to check the port for your particular instance.
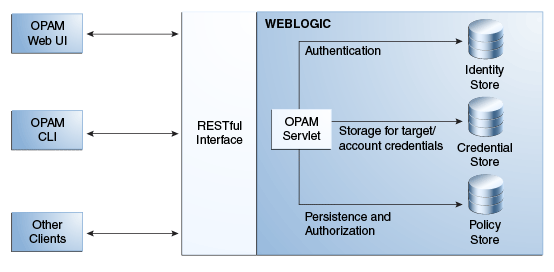
The following figure illustrates the Oracle Privileged Account Manager server architecture.
4.2 Before You Begin
You must be an Oracle Privileged Account Manager administrator with the Application Configurator Admin Role to add and manage an Oracle Privileged Account Manager server.
The procedures described in this chapter reference information and instructions contained in the following Oracle publications. If necessary, review the referenced concepts, terminology, and procedures before you begin configuring the Oracle Privileged Account Manager server:
Table 4-1 Reference Publications
| For Information About | Refer to |
|---|---|
|
Admin Roles |
|
|
Supported identity and policy store configurations for Oracle Privileged Account Manager and Oracle Identity Navigator |
Section 1.7, "System Requirements and Certification" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Navigator |
|
Oracle WebLogic Server concepts and terminology |
Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help and Oracle Fusion Middleware Securing Oracle WebLogic Server |
|
Creating a default authenticator in Oracle WebLogic Server |
Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help and Oracle Fusion Middleware Securing Oracle WebLogic Server |
|
Configuring an identity store in your environment |
Your vendor product documentation |
|
Configuring Oracle Virtual Directory with the LDAP-based server |
"Creating LDAP Adapters" in Oracle Fusion Middleware Administrator's Guide for Oracle Virtual Directory |
|
Configuring the OVD authenticator in Oracle WebLogic Server |
Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help |
|
Associating a policy store using WLST |
"Setting a Node in an Oracle Internet Directory Server" and "reassociateSecurityStore" sections in the Oracle Fusion Middleware Application Security Guide |
|
Associating a policy store using Enterprise Manager |
"Reassociating with Fusion Middleware Control" in the Oracle Fusion Middleware Application Security Guide |
|
Managing the Oracle Privileged Account Manager server |
Section 4.4, "Managing an Oracle Privileged Account Manager Server" |
Note:
Oracle Privileged Account Manager administrators and users will probably never have to use the Oracle Identity Navigator interface except during the initial set-up of Oracle Privileged Account Manager.
4.3 Configuring an External Identity Store for Oracle Privileged Account Manager
This section describes how to configure a new, external identity store for Oracle Privileged Account Manager.
The topics in this section include:
4.3.1 Configuring the External Identity Store
You must configure a domain identity store before you can view users when searching from the Oracle Identity Navigator Access Privileges pane. To configure the identity store as the main authentication source, you must configure the Oracle WebLogic Server domain where Oracle Identity Navigator is installed.
This section describes how to configure the domain identity store using Oracle Internet Directory or Oracle Virtual Directory with a supported LDAP-based directory server. You configure the identity store in the WebLogic Server Administration Console.
Note:
-
Theoretically, you can configure any LDAP server as an external identity store to WebLogic.
For more information about configuring an identity store, see "Configuring the Identity Store Service" in the Oracle Fusion Middleware Application Security Guide.
-
For information about other supported identity stores, see "System Requirements and Certification" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Navigator.
To configure the Oracle Internet Directory authenticator in Oracle WebLogic Server:
-
Log in to Oracle WebLogic Server Administration Console, and click Lock & Edit in the Change Center.
-
In Oracle WebLogic Server Administration Console, select Security Realms from the left pane and click the realm you are configuring. For example, the default realm is
myrealm. -
Select the Providers tab, then select the Authentication subtab.
-
Click New to launch the Create a New Authentication Provider page and complete the fields as follows:
-
Name: Enter a name for the authentication provider. For example,
MyOIDDirectory. -
Type: Select OracleInternetDirectoryAuthenticator from the list.
Click OK to update the authentication providers table.
-
-
In the authentication providers table, click the newly added authenticator.
-
In Settings, select the Configuration tab, then select the Common tab.
-
On the Common tab, set the Control Flag to SUFFICIENT.
Setting the Control Flag attribute for the authenticator provider determines the ordered execution of the Authentication providers. The possible values for the Control Flag attribute are:
-
REQUIRED - This LoginModule must succeed. Even if it fails, authentication proceeds down the list of LoginModules for the configured Authentication providers. This setting is the default.
-
REQUISITE - This LoginModule must succeed. If other Authentication providers are configured and this LoginModule succeeds, authentication proceeds down the list of LoginModules. Otherwise, control is returned to the application.
-
SUFFICIENT - This LoginModule need not succeed. If it does succeed, return control to the application. If it fails and other Authentication providers are configured, authentication proceeds down the LoginModule list.
-
OPTIONAL - This LoginModule can succeed or fail. However, if all Authentication providers configured in a security realm have the JAAS Control Flag set to
OPTIONAL, the user must pass the authentication test of one of the configured providers.
-
-
Click Save.
-
Select the Provider Specific tab and enter the following required settings using values for your environment:
-
Host: The host name of the Oracle Internet Directory server.
-
Port: The port number on which the Oracle Internet Directory server is listening.
-
Principal: The distinguished name (DN) of the Oracle Internet Directory user to be used to connect to the Oracle Internet Directory server. For example: cn=OIDUser,cn=users,dc=us,dc=mycompany,dc=com.
-
Credential: Password for the Oracle Internet Directory user entered as the Principal.
-
Group Base DN: The base distinguished name (DN) of the Oracle Internet Directory server tree that contains groups.
-
User Base DN: The base distinguished name (DN) of the Oracle Internet Directory server tree that contains users.
-
All Users Filter: LDAP search filter. Click More Info for details.
-
User From Name Filter: LDAP search filter. Click More Info for details.
-
User Name Attribute: The attribute that you want to use to authenticate (for example, cn, uid, or mail). For example, to authenticate using a user's email address you set this value to mail.
-
-
Click Save.
-
From the Settings for myrealm page, select the Providers tab, then select the Authentication tab.
-
Click Reorder.
-
Select the new authenticator and use the arrow buttons to move it into the first position in the list.
-
Click OK.
-
Click DefaultAuthenticator in the Authentication Providers table to display the Settings for DefaultAuthenticator page.
-
Select the Configuration tab, then the Common tab, and select SUFFICIENT from the Control Flag list.
-
In the Change Center, click Activate Changes.
-
Restart Oracle WebLogic Server.
-
Verify your configuration and set-up by confirming that the users present in the LDAP directory (Oracle Internet Directory or Oracle Virtual Directory) can log in to Oracle Privileged Account Manager with no issues.
To use Oracle Virtual Directory as the domain identity store, you must do the following:
-
Configure Oracle Virtual Directory with an LDAP-based server as described in "Creating LDAP Adapters" in Oracle Fusion Middleware Administrator's Guide for Oracle Virtual Directory.
-
Configure the OVD authenticator in Oracle WebLogic Server as described in Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help.
-
You must enable the Use Retrieved User Name As Principal option when configuring authenticators in Oracle WebLogic Server, as described in the preceding step 9.
4.3.2 Configuring Enterprise Roles
You must create enterprise roles in the domain identity store to support the Common Admin Roles. Templates are provided for both Oracle Internet Directory and Oracle Virtual Directory configured with an LDAP-based directory server. You use these templates with the Oracle Internet Directory Migration Tool (ldifmigrator), which enables you to convert LDIF files output from other directories or application-specific repositories into a format recognized by Oracle Internet Directory.
Before you configure enterprise roles for the Common Admin Roles, you must configure the domain identity store as described in Section 4.3.1, "Configuring the External Identity Store."
Note:
For more information about supported identity store configurations for Oracle Privileged Account Manager and Oracle Identity Navigator, see Section 1.7, "System Requirements and Certification" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Navigator.
To configure enterprise roles in the domain identity store:
-
Select the template for your environment from
ORACLE_HOME/common/templates.-
For Oracle Internet Directory, use
oinav_template_oid.ldif -
For Oracle Virtual Directory, use
oinav_template_ovd.ldif
-
-
To use the
ldifmigratortool, setJAVA_HOMEand includeJAVA_HOME/bininPATH. -
Use the
ldifmigratortool to create the enterprise roles in the identity store under<GroupBase>as follows:Run java -cp MIDDLEWARE_HOME/oracle_common/modules/oracle.ldap_11.1.1 /ldapjclnt11.jar -DORACLE_HOME=ORACLE_HOME/oracle_common oracle.ldap.util.LDIFMigration input_file=<ldif template> output_file=<outputfile> namespace=<GroupBase> -load dn=<bindDn> password=<> host=<hostName> port=<portNumber>
Where ldif template is the template name.
Note:
-
When using Oracle Virtual Directory with an LDAP-based directory server, the host, port, dn, and groupbase refer to Oracle Virtual Directory and not the LDAP server.
-
For more information about using the
ldifmigratortool, refer to the Oracle Fusion Middleware Reference for Oracle Identity Management.
-
Note:
To configure Single Sign On, see Section 7.2.2, "Enabling Single Sign-On."
4.4 Managing an Oracle Privileged Account Manager Server
This section provides information administrators need to manage an Oracle Privileged Account Manager server, which includes the following topics:
-
Configuring a Connection to the Oracle Privileged Account Manager Server
-
Managing Oracle Privileged Account Manager Server Properties
4.4.1 Configuring a Connection to the Oracle Privileged Account Manager Server
Use the following steps to configure a connection to the Oracle Privileged Account Manager server from the Oracle Privileged Account Manager Console:
-
Open Oracle Privileged Account Manager by logging in to:
http://adminserver_host:adminserver_port/oinav/opam
Note:
You must log in as a user with the Application Configurator Admin Role, or the Server Configuration page will not be accessible.
For more information about this, and other, Admin Roles see Section 2.3.1, "Administration Role Types" and Section 3.3.3, "Assigning the Application Configurator Role to a User."
-
Expand the Administration accordion and select Server Configuration.
-
When the Server Configuration page displays, enter the Host name and SSL Port number.
Notice the URL displayed below the SSL Port field.
-
Click the Test button to test the connection settings.
You should see a message display, stating the configuration tested successfully.
-
Click the Apply button to save this connection information.
4.4.2 Managing Oracle Privileged Account Manager Server Properties
You can use properties in the OPAM Global Config configuration entry to control how often the Oracle Privileged Account Manager server
-
Checks accounts and then automatically checks-in the accounts that have exceeded the expiration time defined in the Usage Policy.
-
Checks accounts and then resets the password for any accounts that have exceeded the maximum password age defined in the password policy.
To access the OPAM Global Config configuration entry and modify these server properties, use the getglobalconfig and the modifyglobalconfig commands from the command line.
Note:
Refer to Section A.2.13, "getglobalconfig Command" and Section A.2.16, "modifyglobalconfig Command" for detailed information about using these commands.