5 Configuring and Managing Oracle Privileged Account Manager
This chapter explains how to configure and manage Oracle Privileged Account Manager. This information is organized into the following topics:
-
Section 5.1, "Administering Oracle Privileged Account Manager"
-
Section 5.3, "Moving from a Test Environment to a Production Environment"
Note:
You can also use Oracle Privileged Account Manager's command line tool or Oracle Privileged Account Manager's RESTful interface to perform many of the tasks described in this chapter.
If you prefer using these interfaces instead of the Oracle Privileged Account Manager Console, see Appendix A, "Working with the Command Line Tool" or Appendix B, "Working with Oracle Privileged Account Manager's RESTful Interface" for instructions.
5.1 Administering Oracle Privileged Account Manager
This section provides instructions for administrators who must configure and maintain Oracle Privileged Account Manager.
The topics include:
You must be an Oracle Privileged Account Manager administrator with a particular Admin Role to perform the different configuration tasks described in this section.
The following list describes the basic workflow that is performed by Oracle Privileged Account Manager administrator users based on their different Admin Roles:
Note:
An administrator with the Application Configurator Admin Role should have already configured a connection to the Oracle Privileged Account Manager server. See Section 4.4.1, "Configuring a Connection to the Oracle Privileged Account Manager Server" for more information.
Table 5-1 Administrator Workflows Based on Admin Roles
| Administrator | Responsibility |
|---|---|
|
Security Administrator |
|
|
User Manager |
|
|
Security Auditor |
Reviews Oracle Privileged Account Manager reports. |
Note:
For more information about these Admin Roles, see Section 2.3.1, "Administration Role Types."
5.1.1 Working with Policies
This section provides information about working with Oracle Privileged Account Manager Usage Policies and Password Policies.
The topics include
5.1.1.1 Policies Overview
In Oracle Privileged Account Manager, there are two types of policies:
-
Password Policy. This policy type captures the password construction rules enforced by a specific target on an associated privileged account. For example, minimum and maximum number of numeric characters. You use a Password Policy to create a password value that Oracle Privileged Account Manager uses to reset a password for a privileged account.
-
Usage Policy. This policy type defines when and how a grantee can use a privileged account. (Default access is 24x7.)
Every privileged account that is managed by Oracle Privileged Account Manager must have an associated Password Policy. A Usage Policy only applies at the level of a grant. You can associate a single Password Policy with multiple privileged accounts and a single Usage Policy with multiple grants.
Oracle Privileged Account Manager provides a Default Password Policy and a Default Usage Policy. You can choose to use the default policies, to modify these policies, or to create your own, specialized policies.
To review the parameter settings for these policies, see Section 5.1.1.2, "Viewing Policies."
Note:
Only administrators with the Security Administrator Admin Role or the User Manager Admin Role can work with policies.
-
An administrator with the Security Administrator Admin Role can modify the Default Password Policy and Default Usage Policy, create new policies, or delete policies.
Administrators with the Security Administrator Admin Role can assign Password Policies, but they cannot assign Usage Policies.
-
An administrator with the User Manager Admin Role can only assign a Usage Policy to accounts at the grantee-account pair level. In other words, the User Manager can assign different Usage Policies to different grantees of the same account.
Administrators with the User Manager Admin Role cannot assign Password Policies.
5.1.1.2 Viewing Policies
To review the parameter settings for a Password Policy or a Usage Policy:
-
Select Password Policies or Usage Policies from the Home tree.
-
When the Policies page displays, use one of the following methods to open a policy:
-
Click the Row number next to the policy name and then click the Open icon located above the Search Results table.
-
Click the policy name (an active link) in the Search Results table.
For example, clicking the Default Password Policy link opens the Password Policy: Default Password Policy page.
A Password Policy page contains three tabs:
-
General. Contains parameters used to specify general information about the policy and Password Lifecycle Rules for the policy.
-
Password Complexity Rules. Contains parameters that govern the complexity requirements for account passwords.
-
Privileged Accounts. Provides information about the privileged accounts currently using the Default Password Policy.
A Usage Policy page also contains three tabs:
-
General Fields. Contains parameters used to specify general information about the policy.
-
Usage Rules. Contains parameters that govern when the account can be checked out and when the check out expires.
-
Grantees. Provides information about the grantees who are authorized to use that account.
-
5.1.1.3 Modifying the Default Password Policy
After evaluating the Default Password Policy, you may decide you want to modify the settings to better suit your environment.
To modify the Default Password Policy, use the following steps:
-
Select Password Policies from the Home tree.
-
When the Policies page displays, select the Default Password Policy link in the Search Results table to open the Password Policy: Default Password Policy page.
-
Select the General tab to edit the Policy Description field in the General Fields area or to modify any of the following Password Lifecycle Rules:
-
Password maximum age: Use the two menus to specify a duration period (number of days, hours, or minutes) after which Oracle Privileged Account Manager must automatically reset the account password.
For example, if your enterprise wants a security policy where account passwords must be changed every month, you would set this value to 30 days.
Every time the account is checked out and its password gets changed (if the policy is configured so that passwords must be changed on checkout/check-in) Oracle Privileged Account Manager tracks the password change time.
Note:
An administrator with the Security Administrator Admin Role can also manually reset a password by using the Reset Password option (described in Section 5.1.3.5.2, "Resetting an Account Password") and Oracle Privileged Account Manager tracks this password change time as well.
If Oracle Privileged Account Manager detects the account is idle and no password changes have occurred over the specified number of days, then Oracle Privileged Account Manager automatically resets the password to a new, randomized value, which helps the enterprise to automatically enforce the security policy without human intervention.
To disable this automatic reset option, set the numeric value to 0.
-
Reset password on check-in: Use this option to specify whether Oracle Privileged Account Manager must auto-generate and set a randomized password during a check-in operation.
Uncheck this box if you do not want the password to be reset during the check-in operation.
-
Reset password on check-out: Use this option to specify whether Oracle Privileged Account Manager must auto-generate and set a randomized password during a check-out operation.
Uncheck this box if you do not want the password to be reset during the check-out operation.
Note:
-
For higher security, the Password must be changed on check-in and Password must be reset on check-out options are both enabled by default to require password changes, but they can be disabled if required. For example, some enterprises may only require that passwords be reset every 30 days.
-
If your enterprise prefers that passwords not be automatically managed at all; that they are only changed through human intervention, disable all three of these Password Lifecycle Rules options.
After disabling these three options, the only way to manually change passwords is by using the Reset Password option (described in Section 5.1.3.5.2, "Resetting an Account Password"). Oracle Privileged Account Manager is still useful in this case, as you can reset and centrally manage passwords for multiple systems from one place by using Oracle Privileged Account Manager.
-
-
Select the Password Complexity Rules tab to change one or more of the parameters that define the default password requirements.
Parameter Description Characters for Password
Specify the minimum and maximum number of characters required.
Alphabetic Characters
Specify the minimum number of alphabetic characters required.
Numeric Characters
Specify the minimum number of numeric characters required.
Alphanumeric Characters
Specify the minimum number of alphanumeric characters required.
Special Characters
Specify the minimum and maximum number of special characters (such as
*or@) required.Repeated Characters
Specify the minimum and maximum number of repeated characters allowed.
Unique Characters
Specify the minimum number of unique characters required.
Uppercase Characters
Specify the minimum number of uppercase characters required.
Lowercase Characters
Specify the minimum number of lowercase characters required.
Start with Character (not digit)
Specify the first character required to start a password.
Required Characters
Specify characters that are required in a password.
Allowed Characters
Specify which characters are permitted in a password.
Disallowed Characters
Specify which characters are not permitted in a password.
Disallowed as Password
Enable (check) the Account Name box to prohibit the use of an account name in the password.
-
Select the Privileged Accounts tab to review which accounts are currently using the Default Password Policy.
Note:
To specify a different Password Policy for any account listed in the table, click the Account Name link. When the Account page displays, select a different policy name from the Password Policy menu.
-
When you are finished editing the policy, click Apply to save your changes.
5.1.1.4 Modifying the Default Usage Policy
To modify the default Usage Policy,
-
Select Usage Policies from the Home tree.
-
When the Policies tab displays, select the Default Usage Policy link in the Search Results table to open the Usage Policy: Default Password Policy page with three tabs.
-
On the General Fields tab, you can only change content in the Description field.
-
Select the Usage Rules tab to change one of more of following parameter settings:
Parameter Description Timezone
Select a different time zone from the menu.
Permitted Usage Dates
Use the checkboxes and drop menus to change when grantees are allowed to use the account. Select one or more days of the week and the periods of time when grantees can access this account. (Default access is 24x7.)
Expiration Dates
Enable one of the following options to change when grantees' access to the account expires:
-
Automatically check in account. Use the counter to specify the number of minutes after last check out.
-
Automatically check in account on this date. Click the Calendar icon to open a Select Date and Time dialog.
Use the month and year menus or click a day in the calendar to specify an expiration date.
Use the hours, minutes, and seconds menus and enable the AM or PM buttons to specify an expiration time.
Note:
If you are configuring a Usage Policy for a shared privileged account, it is prudent to configure an Automatic check-in option to ensure the account gets checked-in and the password gets cycled in a timely manner.
In addition, consider limiting how many users can access the shared account and further segregate these users by specifying when they can access the account. By specifying which days of the week and what times of the day each user can access the account, you minimize overlapping checkouts and improve Oracle Privileged Account Manager's auditing ability.
For more information about shared accounts, see Section 2.4.2, "Securing Shared Accounts."
-
-
Select the Grantees tab to view which grantees this policy is assigned.
Note:
To specify a different Usage Policy for any grantee listed in the table, click the Account Name link. When the Account page displays, select a different policy name from the Usage Policy menu.
Tip:
Clicking the active links in Grantee Name or Account Name columns enable you to navigate to other screens for additional information.
-
When you are finished editing the policy, click Apply to save your changes.
5.1.1.5 Creating a Password Policy
To create a Password Policy, use the following steps:
-
Select the Password Policies node from the Home tree.
-
When the Policies tab displays, click Create Password Policy at the top of the Search Results table.
A new, Password Policy: Untitled page displays with three tabs.
-
Provide the following information on the General tab:
-
Policy Name: Enter a name for the new policy.
-
Policy Status: Click the button to specify whether the policy is Active or Disabled.
Disabling a policy applies the Default Password Policy to all accounts and grants associated with that disabled policy. If you simply assigned a different policy to those accounts and grants, you would lose all information about the old policy assignment.
Making the policy Active puts that policy into effect for the associated accounts and grants.
-
Configure the Password Lifecycle Rules to allow Oracle Privileged Account Manager to auto-generate and set a randomized account password under certain conditions, as described in step 3.
-
-
Use the parameters on the Password Complexity Rules tab to define the complexity rules requirements for passwords. Refer to the table provided in step 4 for a description of these parameter settings.
-
Assign the policy to accounts or grantees using the instructions provided in Section 5.1.1.8, "Assigning Policies."
After you assign this policy, you can select the Privileged Accounts tab to review which accounts are using this policy.
-
Click Save.
5.1.1.6 Creating a Usage Policy
To create a Usage Policy, use the following steps:
-
Select Usage Policies node from the Home tree.
-
When the Policies tab displays, click Create Usage Policy at the top of the Search Results table.
A new, Usage Policy: Untitled page displays with three tabs.
-
Provide the following information on the General tab:
-
Policy Name: Enter a name for the new policy.
-
Policy Status: Click the button to specify whether the policy status is Active or Disabled.
Disabling a policy applies the Default Usage Policy to all accounts and grants associated with that disabled policy. If you simply assigned a different policy to those accounts and grants, you would lose all information about the old policy assignment.
Making the policy Active puts that policy into effect for the associated accounts and grants.
-
Description: Enter a description of the policy.
-
-
Select the Usage Rules tab. Use the options on this page to define rules for using a privileged account. Refer to the table provided in step 4 for a description of these parameter settings.
-
Assign the policy to accounts or grantees using the instructions provided in Section 5.1.1.8, "Assigning Policies."
After you assign this policy, you can select the Grantees tab to review which users or groups are using this policy.
-
Click Save.
5.1.1.7 Searching for Policies
Use the following steps to search for a policy:
-
In the Home tree,
-
Select Policies to search all policies.
-
Select the Password Policies node or the Usage Policies node to search for policies that are the selected policy type.
-
-
When the Search Policies portlet displays, enter your search criteria into one or more of the following fields.
-
Policy Name: Enter all or any part of a policy name.
-
Policy Status: Select All to search all policies. Select Active or Inactive to limit the search to just active or inactive policies.
-
Policy Type: Select All to search all policies, or specify Password Policy or Usage Policy to limit the search to just the selected policy type.
Note:
Selecting Password Policies or Usage Policies in step 1, automatically enters that policy type into the Policy Type field.
-
-
Click Search.
Review your search results in the Search Results table.
5.1.1.8 Assigning Policies
As previously stated, when you add a new privileged account, the Default Password Policy and Default Usage Policy are automatically assigned to that account.
To assign a different Password Policy or Usage Policy, you must first create the policy as described in Section 5.1.1.5, "Creating a Password Policy" or in Section 5.1.1.6, "Creating a Usage Policy."
Note:
-
Administrators with the Security Administrator Admin Role can assign a Password Policy or a Usage Policy to an account. However, this role can only apply a Usage Policy at the account level.
-
Administrators with the User Manager Admin Role can assign a Usage Policy to accounts at the grantee-account pair level. In other words, the User Manager can assign different Usage Policies to different grantees of the same account.
The User Manager Admin Role cannot assign Password Policies.
5.1.1.8.1 Assigning Password Policies to Accounts
You can assign Password Policies to an account from the Accounts page, from the Targets page, or from the Policies page.
To assign a Password Policy from the Accounts page,
-
Use one of the following methods to locate the account:
-
Select the Accounts node in the Home tree, and then use the Search Accounts portlet to search for the account. See Section 5.1.3.3, "Searching for Privileged Accounts" for instructions.
-
Select the account's Target Type node or Domain node in the Home tree.
For example, if you know the account is assigned to an LDAP target, select the ldap node.
-
-
When the Search Results display, click the account's Account Name link in the table to open the Account: AccountName page.
-
On the General tab, select a different policy name from the Password Policy menu.
-
After selecting the new policy, click Test to verify that the account can be managed by Oracle Privileged Account Manager. You should see a Test Succeeded dialog confirming the test was successful.
-
Click Apply to finish assigning the policy to the selected account.
To assign a Password Policy from the Targets page,
-
Use one of the following methods to locate the account:
-
Select the Targets node in the Home tree, and then use the Search Targets portlet to search for the account target. See Section 5.1.2.3, "Searching for Targets" for instructions.
-
Select the account's Target Type node or Domain node in the Home tree.
For example, if you know the account is assigned to a UNIX target, select the unix node.
-
-
Click the account's Target Name link in the Search Results table to open the Target: TargetName page.
-
Click the Privileged Accounts tab to view a list of the accounts currently managed on the target.
Notice that the table lists the Password Policy that is currently assigned to each account.
-
Locate the account and click the Account Name link.
-
When the General tab displays, select a different policy name from the Password Policy menu.
-
After selecting the new policy, click Test to verify that the account can be managed by Oracle Privileged Account Manager. You should see a Test Succeeded dialog confirming the test was successful.
-
Click Apply to finish assigning the policy to the selected account.
To assign a Password Policy from the Policies page,
-
Select the Password Policies node in the Home tree.
-
Locate the policy you want to assign in the Search Results table. Click the Policy Name link to open the Password Policy: PolicyName page.
-
Select the Privileged Accounts tab.
-
Locate the account and click the Account Name link to open the Account: AccountName page.
-
When the General tab displays, select a different policy name from the Password Policy menu.
-
After selecting the new policy, click Test to verify that the account can be managed by Oracle Privileged Account Manager. You should see a Test Succeeded dialog confirming the test was successful.
-
Click Apply to finish assigning the policy to the selected account.
5.1.1.8.2 Assigning a Usage Policy to Users and Groups
When you add grantees to an account, as described in Section 5.1.4.2, "Granting Accounts to Users" or Section 5.1.4.3, "Granting Accounts to Groups," Oracle Privileged Account Manager adds the user or group name to the Users or Groups table on the Grants tab and automatically assigns the Default Usage Policy.
You can assign a different Usage Policy from the Accounts page or from the Usage Policies page.
Note:
When you create a new Usage Policy for an account, the new policy will not automatically be assigned to the existing grantees on that account. Oracle Privileged Account Manager allows you to assign customized policies to individual grantees, so you do not want the new policy to override those other policy assignments.
However, if you create a new policy for an account and then add new grantees, those (and future) grantees will automatically be associated with that policy because it has become the new default Usage Policy for the account.
To assign a Usage Policy from the Accounts page,
-
Use one of the following methods to locate the account:
-
Select the Accounts node in the Home tree, and then use the Search Accounts portlet to search for the account. See Section 5.1.3.3, "Searching for Privileged Accounts" for instructions.
-
Select the account's Target Type node or Domain node in the Home tree.
For example, if you know the account is assigned to an LDAP target, select the ldap node.
-
-
Locate the account's Account Name link to open the Account: AccountName page.
-
Select the Grants tab.
-
Locate the grantee in the Users or Groups table, and use the Usage Policy menu in that row to select a different policy.
-
Click Apply to add your changes.
To assign a Usage Policy from the Targets page,
-
Use one of the following methods to locate the account:
-
Select the Targets node in the Home tree, and then use the Search Targets portlet to search for the account target. See Section 5.1.2.3, "Searching for Targets" for instructions.
-
Select the account's Target Type node or Domain node in the Home tree.
For example, if you know the account is assigned to an UNIX target, select the unix node.
-
-
Click the account's Target Name in the Search Results table to open that target.
-
When the Target: TargetName page displays, click the Grants tab to view a list of the grantees currently granted access to that account.
Notice that the table lists the Usage Policy that is currently assigned to each grantee.
-
Locate the grantee in the Users or Groups table, and use the Usage Policy menu in that row to select a different policy.
-
Click Apply to finish assigning the policy to the selected account.
To assign a Usage Policy from the Policies page,
-
Select the Usage Policies node in the Home tree.
-
When the search results display, locate the policy you want to assign in the Search Results table. Click the Policy Name link to open the Usage Policy: PolicyName page.
-
Select the Grantees tab.
-
Locate the user or group name in the Grantees table and then click that grantee's Account Name link to open the account.
-
When the Account: AccountName page displays, click the Grants tab.
-
Locate the grantee in the Users or Groups table, and use the Usage Policy menu in that row to select a different policy.
-
Click Apply to add your changes.
5.1.1.9 Deleting Policies
To delete a policy, use the following steps:
-
Locate and select the policy to be deleted.
-
Click the Delete icon.
-
When the Confirm Remove dialog displays, click the Remove button.
The policy will be deleted and all accounts using that policy will revert to using the applicable Default Policy.
5.1.2 Working with Targets
This section describes the different tasks you can perform when working with targets in Oracle Privileged Account Manager.
Note:
You must be an Oracle Privileged Account Manager administrator with the Security Administrator Admin Role to add, edit, or remove targets.
The topics in this section include:
5.1.2.1 What Are Targets?
A target is a software system that contains, uses, and relies on user, system, or application accounts.
You cannot create targets in, or delete targets from, your environment by using Oracle Privileged Account Manager. Rather, Oracle Privileged Account Manager manages existing targets that were provisioned using other mechanisms.
When you "add" a target in Oracle Privileged Account Manager, you are creating a reference to that target. In effect, you are registering the target and asking Oracle Privileged Account Manager to manage it. When you "remove" a target from Oracle Privileged Account Manager, you are only removing that reference.
5.1.2.2 Adding Targets to Oracle Privileged Account Manager
Note:
When adding a target of any Target Type, you must configure a service account (also called an unattended account) with privileges that enable that account to
-
Search for accounts on the target system
-
Modify the passwords of accounts on the target system
For additional information about service accounts, see the description on page 1-3.
Use the following steps to add a target for Oracle Privileged Account Manager to manage:
-
Log in to Oracle Privileged Account Manager and expand the Home accordion.
-
Select the Targets node to open the Targets page.
-
Click Add, located in the Search Results table toolbar to open a new Target: Untitled page displays with two tabs:.
-
General. Contains two areas with parameters used to specify Basic Configuration and Advanced Configuration information for the target.
-
Privileged Accounts. Lists the privileged accounts currently being managed on the target and enables you to add, open, and remove the accounts that are managed by that target.
-
-
Select a target type (ldap, unix, or database) from the Target Type menu.
The Target: Untitled page refreshes and the target configuration parameters change, based on the selected target type. You must specify all of the required attributes (indicated by an asterisk
*symbol).The following parameters are common to all target types:
-
Target Name: Enter a name for the new target.
-
Description: Enter a description for this target.
-
Organization: Enter the name of an organization to associate with the target.
-
Domain: Enter the domain of the target server.
-
Host: Enter the host name of the target server.
The following table describes the remaining Basic Configuration parameters that are unique to each target type.
Table 5-2 Basic Configuration Parameters for Targets
For ldap Target Types For unix Target Types For database Target Types TCP Port: Enter the TCP/IP port to use when communicating with the LDAP server.
You can use the up/down arrow icons to increment this value.
Port: Enter the port used to connect with the UNIX server.
For example, use port 22 for ftp, and port 23 for telnet.
You can use the up/down arrow icons to increment this value.
Database Connection URL: Enter the JDBC URL used to identify the target system location. For example,
Oracle:jdbc:oracle:thin:@<host>: <port>:<sid>
Refer to the Oracle Identity Manager Connector Guide for Database User Management for information about which special options are supported.
SSL: Enable this box to use Secure Socket Layer (SSL) when connecting to the LDAP server.
Note: For SSL connectivity, you must import an SSL certificate to the WebLogic server running Oracle Privileged Account Manager. For more information, see Section 3.3.2, "Configuring SSL Communication in Oracle Privileged Account Manager."
Login User: Enter the user name to use when connecting to this target.
Admin User Name: Enter the administrator's name to use when connecting to this target.
Note: If you are using the
sysuser name, you must enterinternal_logon=sysdbain the Connection Properties field located in the Advanced Configuration area. This entry is not required for "system."Principal: Enter the distinguished name (DN) to use when authenticating to the LDAP server.
For example, cn=admin
Login User Password: Enter the user's password.
Admin User Password: Enter the user's password.
Password: Enter the user's password.
Login Shell Prompt: Enter the shell prompt to display when you log in to the target. For example,
$or#.Database Type: Select the type of database (Oracle or MSSQL) for which the connector will be used.
This connector supports the Oracle MSSQL, MySQL, DB2, and Sybase database types.
You can also configure this connector to work with custom database types.
Base Contexts: Enter one or more starting points in the LDAP tree to use when searching the tree for users on the LDAP server or when looking for groups where the user is a member. Use a pipe (|) to separate values.
Sudo authorization: Enable this box if the user requires sudo authorization.
Do not enable this box for the
rootuser.Account User Name Attribute: Enter the attribute to be used as the account's user name. (Default is uid.)
-
-
You can also specify these optional, advanced configuration parameters.
Table 5-3 Advanced Configuration Parameters for Targets
For ldap Target Types For unix Target Types For database Target Types Uid Attribute: Enter the name of the LDAP attribute that is mapped to the
Uidattribute.Command timeout: Specify how long (in milliseconds) to wait for the command to complete before terminating that command.
Connection Properties: Enter connection properties to use while configuring a secured connection. These properties must be name-value pairs given in following format:
prop1=val1#prop2=val2.LDAP Filter for Retrieving Accounts: Enter an optional LDAP filter to control which accounts are returned from the LDAP resource. If you do not specify a filter, Oracle Privileged Account Manager returns only those accounts that include all of the specified object classes.
Password Attribute: Enter the name of the LDAP attribute that holds the password.
When changing a user's password, Oracle Privileged Account Manager sets the new password to this attribute.
Account Object Classes: Enter one or more object classes to use when creating new user objects in the LDAP tree.
Type each object class on its own line. Do not use commas or semicolons to separate entries.
Some object classes require that you specify them in their class hierarchy, using a pipe (
|) to separate the values. -
When you are finished, click Test to check the target's configuration.
If the target's configuration settings are valid, a Test Succeeded message displays.
-
Click Save to add your new target on the Oracle Privileged Account Manager server.
You can now associate this target with a privileged account. For instructions, proceed to Section 5.1.3.2, "Adding Privileged Accounts into Oracle Privileged Account Manager."
5.1.2.3 Searching for Targets
If you have administrator privileges, you can search for targets using the following criteria or a combination of these items:
-
Target Name
-
Target Type
-
Host Name
-
Domain
To search for a target,
-
Select the Targets node, a target type node, or a domain node in the Home tree.
-
When the Targets tab displays, use the parameter fields in the Search Targets portlet to specify your search criteria.
Note:
If you started by selecting a target type node or a domain node, notice that Oracle Privileged Account Manager automatically inserts that information in the Target Type field or the Domain field.
-
Click Search.
Review your search results in the Search Results table.
5.1.2.4 Opening a Target
You can open a target to review and edit the target's configuration parameters and its associated privileged account parameters.
Use one of the following methods to open a target:
-
Click the target name (an active link) in the Search Results table.
-
Select the target row and then click the Open icon.
The Target: targetname page opens where you can access the target and privileged account information.
5.1.3 Working with Privileged Accounts
This section describes the different tasks you can perform when working with privileged accounts in Oracle Privileged Account Manager.
Note:
Administrators determine which accounts are privileged within a particular deployment, and they must configure Oracle Privileged Account Manager to manage those accounts.
You must be an Oracle Privileged Account Manager administrator with the Security Administrator Admin Role to add and manage accounts.
The topics in this section include:
-
Adding Privileged Accounts into Oracle Privileged Account Manager
-
Removing Privileged Accounts from Oracle Privileged Account Manager
5.1.3.1 What is a Privileged Account?
An account on a target is considered privileged in a deployment when that account
-
Is associated with elevated privileges
-
Is used by multiple end-users on a task-by-task basis
-
Requires its usage to be controlled and audited
You cannot create accounts in, or delete accounts from, your environment by using Oracle Privileged Account Manager. Oracle Privileged Account Manager only manages existing accounts that were provisioned using other mechanisms.
When you "add" an account in Oracle Privileged Account Manager, you are creating a reference to that account. In effect, you are registering the account and asking Oracle Privileged Account Manager to manage it. When you "remove" the account from Oracle Privileged Account Manager, you are only removing the reference to that account.
Oracle Privileged Account Manager enables you to manage both system and application accounts. As described in the following Managing System Accounts and Managing Application Accounts sections.
5.1.3.1.1 Managing System Accounts
Oracle Privileged Account Manager's primary purpose is to manage privileged system accounts on a supported target system. Oracle Privileged Account Manager does not mandate what constitutes a privileged system account — it can manage any account on a target system. Administrators are responsible for identifying which accounts are privileged. A privileged account is typically a system account that allows a user to perform administration tasks.
Privileged accounts are suitable for management through Oracle Privileged Account Manager if they are used and shared by multiple individuals in the organization and administrators are required to track the use of these accounts.
Administrators perform the following steps to register an account as a privileged account to be managed by Oracle Privileged Account Manager:
-
Add the target to Oracle Privileged Account Manager (if this has not already been done). See Section 5.1.2.2, "Adding Targets to Oracle Privileged Account Manager" for instructions.
-
Add the identified privileged account to the target and assign a Password Policy. See Section 5.1.3.2, "Adding Privileged Accounts into Oracle Privileged Account Manager" and Section 5.1.1, "Working with Policies" for instructions.
-
Grant access to end users directly or by using LDAP roles/groups and assign a Usage Policy. See Section 5.1.4.2, "Granting Accounts to Users" and Section 5.1.1, "Working with Policies" for instructions.
5.1.3.1.2 Managing Application Accounts
Applications use application accounts to connect to target systems at run time. Traditionally, administrators set up these accounts once during installation and then they are forgotten. Consequently, application accounts can potentially cause hidden vulnerabilities in your deployment. For example, passwords might become less secure over time because they were created using outdated policies or commonly used deployment passwords might be compromised.
Oracle Privileged Account Manager enables you to better manage application accounts. In particular, for applications that store their application accounts in the Credential Store. These applications consume the account credentials at run time from the Credential Store through the Credential Store Framework.
For example, because an application account is essentially a special version of a system account, you can register an application account in Oracle Privileged Account Manager as described in Section 5.1.3.1.1, "Managing System Accounts." You can then add the corresponding CSF mappings for every application that depends on that account, which is how CSF uniquely identifies a credential stored within CSF, and how an application finds its credential in CSF. For more information about CSF mapping, see "Guidelines for the Map Name" in the Oracle Fusion Middleware Application Security Guide.
If you register an account's CSF mappings with Oracle Privileged Account Manager, then every time the account's password changes, Oracle Privileged Account Manager can update the CSF entries that correspond to the registered mappings to reflect the new password and the applications continue to work without service interruption.
Note:
Oracle Privileged Account Manager updates, or synchronizes, CSF only when a password change occurs.
Additionally, you can apply a Password Policy to these applications that periodically cycles the account password. Cycling the password ensures that the application accounts are always compliant with the latest corporate policies and they remain secure. Oracle Privileged Account Manager performs this task with no service interruption.
Finally, its useful to note that Oracle Privileged Account Manager can support an account as both a system account (shared and used by multiple end-users) and as an application account (only used by an application at run time) at the same time. In this configuration, a human end-user who's been granted access can "check-out" the application account to perform manual administrative operations as that application without disrupting application functionality.
For more information about application accounts, review Section 1.2.4, "Oracle Privileged Account Manager-Managed CSF Credentials."
5.1.3.1.3 Sharing Accounts
Oracle Privileged Account Manager enables you to specify whether an account is shared or not shared.
-
Shared accounts enable multiple users to check out the account at the same time.
-
Unshared accounts (Default) enable only one user to check out an account at a time.
Because unshared accounts are more secure, Oracle recommends that you designate an account as shared only if there are compelling business reasons to do so. If sharing is necessary, be sure to read Section 2.4.2, "Securing Shared Accounts."
5.1.3.2 Adding Privileged Accounts into Oracle Privileged Account Manager
Note:
Accounts are always added to a target, so you must add a target object before you can add an account. Refer to Section 5.1.2.2, "Adding Targets to Oracle Privileged Account Manager" for more information.
To add a new privileged account
-
Expand the Home accordion.
-
Use one of the following methods to locate the target where you want to add the account.
-
Expand the Targets node and select the target from the subtree.
-
Click the Targets node and search for the target by providing search criteria in the Search Targets pane.
-
-
Open the target by clicking the Target Name link in the Search Results table.
-
Select the Privileged Accounts tab.
-
Click Add in the Search Results table toolbar.
The Account: Untitled page displays with three subtabs:
-
General: Use to specify information needed to add the account.
-
Grants: Use to associate users and groups (grantees) with the account.
-
Credential Store Framework: Use to add or remove Credential Store Framework (CSF) mappings for the account.
Use these tabs and the instructions provided in the following sections to add an account:
-
-
When you are finished, click Save.
5.1.3.2.1 Adding the Account
To add a new account you must complete the Step 1: Set Target and Step 2: Add Account sections on the General tab as follows:
-
If the Target Name is undefined, click the search icon.
-
When the Set Target dialog displays, enter a value in the Target Name field and click the Search button to locate the target where you want to add the account.
For example, if you know the target name begins with "r," you can type an
rinto the Target Name field and click the Search button. -
When the search results display in the Search Results table, select (check) the Row box next to a target name and then click Set.
Note that the selected Target Name and its Target Type are displayed on the General tab.
-
In the Step 2: Add Account section, if the Account Name is undefined, click the search icon.
-
When the Set Account dialog displays, enter a value in the Account Name field and click the Search button to locate the account you want to add.
For example, if you know the account name begins with "s," you can type an
sinto the Account Name field and click the Search button. -
When the search results display in the Search Results table, select (check) the Row box next to an account name and then click Set.
Note that the selected account is displayed as the Account Name on the General tab.
-
Enable the Shared Account box to allow multiple users to check out this account at the same time.
Note:
See Section 5.1.3.1.3, "Sharing Accounts" and Section 5.1.3.6, "Checking Out Accounts" for more information.
-
Specify a Usage Policy and a Password Policy.
Note:
Oracle Privileged Account Manager automatically assigns the Default Usage Policy and Default Password Policy to new accounts.
However, Oracle Privileged Account Manager administrators with the Security Administrator or the User Manager Admin Role can create new policies.You can leave the default policies set or choose a different policy from the Usage Policy and Password Policy drop-down menus.
For more information about policies, refer to Section 5.1.1, "Working with Policies."
-
Click Test to confirm that the account can be managed by Oracle Privileged Account Manager with these settings.
If the account configuration settings are valid, a Test Succeeded message displays.
You can now add grantees and CSF mappings to the account. Continue to the following sections for more information.
5.1.3.2.2 Adding Grantees
this section provides instructions for adding grantees to a privileged account.
Note:
Adding a new account does not automatically grant you access to that account. You must complete the process for adding yourself as a grantee.
You must be an Oracle Privileged Account Manager administrator with the User Manager Admin Role to add, edit, or delete grantees.
To associate users and groups with a new account, select the Grants tab and then complete the following steps:
-
To associate users, click Add from the Users table toolbar.
-
In the Add Users dialog, enter a name into the User Name field and click the arrow icon to search for that user.
-
When the search results display, select (check) each user you want to associate with this account.
-
When you are finished adding users, click Add and then click Close.
Oracle Privileged Account Manager adds those user names to the Users table on the Grants tab.
-
-
To associate groups, click Add from the Groups table toolbar.
-
In the Add Group dialog, enter a name into the Group Name field and click the arrow icon to search for that group.
-
When the search results display, select (check) each group you want to associate with this account.
-
When you are finished adding groups, click Add and then click Close.
Oracle Privileged Account Manager adds those group names to the Groups table on the Grants tab.
-
5.1.3.2.3 Adding CSF Mappings
Oracle Privileged Account Manager enables you to securely store and synchronize account credentials with the Oracle Credential Store Framework (CSF). This capability is useful for managing the lifecycle of application passwords stored in CSF.
When you configure CSF synchronization for an account, Oracle Privileged Account Manager changes the account password based on the assigned Usage Policy.
Note:
Oracle Privileged Account Manager updates, or synchronizes, CSF only when a password change occurs.
To add CSF mappings to an account, complete the following steps:
-
Select the Account Name link from the Search Results table.
-
When the Account: AccountName page displays, select the Credential Store Framework tab and click Add.
-
Enter the following information:
-
Administration Server URL. Enter the server URL in this format, protocol://listen-address:listen-port
-
Username and Password. Enter the user's credentials.
-
Mapping. Enter a map name.
-
Key. Enter a unique key to identify the credential.
-
-
Click Add again to create another mapping. You can create as many CSF mappings as needed.
5.1.3.3 Searching for Privileged Accounts
You can search for accounts by using one or more of the following parameters:
-
Account name
-
Target name
-
Target type
-
Domain
To search for accounts, use the following steps:
-
Select the Accounts node in the Home tree.
-
When the Accounts tab displays, enter your search criteria in the Search Accounts pane and then click Search.
For example, to search for a list of all the accounts on a particular target, enter the Target Name and click Search. Your search results are displayed in the Search Results table.
Note:
You can use the Status menu, located above the Search Results table, to control the search results based on the account status. See the table in Section 3.4.5, "Working with a Search Results Table" for more information.
-
To perform another search, click Reset.
5.1.3.4 Opening an Account
You can open an account to view or edit the configuration parameters for that account.
Use one of the following methods to open an account:
-
Click the account name (an active link) in the Search Results table.
-
Select the account row and then click Open Account.
The Account: accountname page opens where you can access information about the associated target, general account parameters, the grantees, and the CSF mapping.
5.1.3.5 Managing Account Passwords
Oracle Privileged Account Manager provides two options for managing account passwords:
-
Show Password. Displays the password for an account.
If you forget the password for a checked- out account, you can use this feature to view that password again.
Any user can use Show Password to review the current password for a account they have checked out. However, they cannot access passwords after the account is checked back in or view passwords for accounts that are checked out by other users. In these cases, clicking Show Password will cause an error.
Administrators with the Security Administration or User Manager Admin Role, who can access all system and target service accounts, can use this feature to view current the password for both checked out and checked in privileged accounts.
-
Reset Password. Resets the existing account password.
If Security Administrators do not want to use randomized password generation, they can manually set a password of their choosing. For example, administrators might prefer to set a simple, easy-to-type password for one time use, such as during a system upgrade.
Only administrators with the Security Administration Admin Role can reset account passwords.
See Section 5.1.3.5.1, "Showing an Account Password" and Section 5.1.3.5.2, "Resetting an Account Password" for instructions.
Note:
You can also perform both password management actions by using the Oracle Privileged Account Manager command line tool. Refer to Section A.2.31, "showpassword Command" and Section A.2.21, "resetpassword Command" for instructions.
Oracle Privileged Account Manager audits both types of password management actions to keep track of password access.
5.1.3.5.1 Showing an Account Password
To view the password for a selected account,
-
Select the account's row in the Search Results table.
Note:
Do not click an active link in the table, such as the account name, or you will open the account
-
Click the Show Password icon located above the table.
A message displays with the name of the selected account and its password.
5.1.3.5.2 Resetting an Account Password
If necessary, you can manually reset the password for a selected account as follows:
-
Ensure the privileged account is checked in.
You cannot perform a manual password reset if the account is in a checked-out state.
-
Select the account row in the Search Results table.
Note:
Do not click an active link in the table, such as the account name, or you will open the account
-
Click the Reset Password icon located above the table.
The Reset Password dialog displays.
-
Type a password into the New Password field and click Save.
You can use a password string of your choosing. The string does not have comply with the Oracle Privileged Account Manager Password Policy because the Password Policy is used for randomized password generation.
A message displays with the name of the selected account and its password.
5.1.3.6 Checking Out Accounts
Any administrator or end user can check out an account if they have been granted access to that account. (See Section 5.1.4, "Working with Grantees" for more information.)
Note:
You must be an administrator with the Security Administration Admin Role to modify or remove an account.
Privileged accounts are not shared by default, which means when one user checks out the account, it becomes unavailable to other users and prevents conflicting actions. However, administrators can configure shared accounts, which enables multiple users to check out the account at the same time. (Refer to Section 5.1.3.1.3, "Sharing Accounts" for more information.)
The steps for checking out an account are as follows:
-
Expand the Accounts node on the Home accordion, and select the account target.
-
When the Accounts tab displays, locate the account you want to check out in the Search Results table.
-
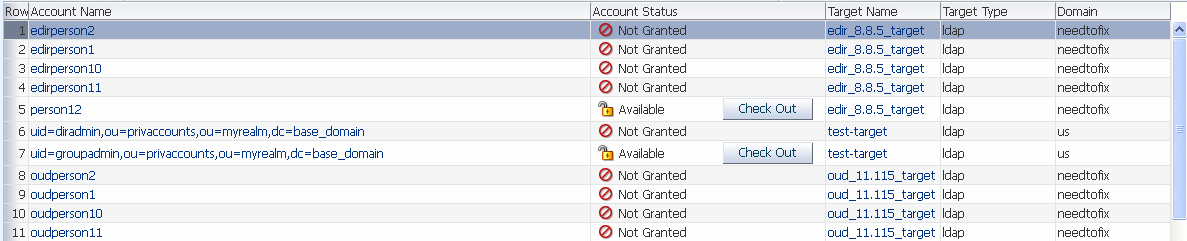
If the account is available for check out, the Account Status is Available and the Check-out button is displayed.
-
If the account is not available for check out, then the Account Status is Not Granted.
-
-
Click the Check-out button.
When the Check-Out Account dialog displays, you can enter a comment in the Comments field, and then click Checkout.
If the check-out is successful,
-
For an unshared account, the Account Status changes to Checked-Out, the Check Out button changes to a Check In button, and Oracle Privileged Account Manager lists the account on the My Checked-out Accounts page.
-
For a shared account, the Account Status remains Available, the Check Out button remains, and Oracle Privileged Account Manager lists the account on the My Checked-out Accounts page.
-
5.1.3.7 Checking In Accounts
Any administrator or end user can check in accounts.
Note:
You can also use the Search Accounts page, the Oracle Privileged Account Manager command line tool, or the RESTful interface to check-in accounts.
The steps for checking in an account are as follows:
-
Select My Checked-out Accounts on the Home accordion.
The My Checked-out Accounts page displays with all of your checked-out accounts listed in the Search Results table.
-
Select (check) the account(s) you want to check in.
-
Click the Check-in icon located above the table.
-
When the Check-in Accounts dialog displays, click the Check In button.
If the check-in is successful, Oracle Privileged Account Manager removes the account name(s) from the My Checked-out Accounts table and the account becomes Available for check-out again.
5.1.3.8 Removing Privileged Accounts from Oracle Privileged Account Manager
You can remove a privileged account from Oracle Privileged Account Manager by using the Targets page or the Search Accounts page.
To remove an account from a target,
-
Expand the Home accordion.
-
Locate the target from which you want to remove the account.
-
Expand the Targets node and select the target from the subtree.
-
Click the Targets node and search for the target by providing search criteria in the Search Targets pane.
-
-
Click the target name in the Search Results table to open the target.
-
Select the Privileged Accounts tab.
-
In the Search Results table, select the account to be removed and then click Remove.
-
When you are finished, click the Apply button located at the top of the page.
To remove an account from the Search Accounts page,
-
Expand the Home accordion.
-
Click the Accounts node, target type node, or domain node in the Home tree to open the Search Accounts page.
-
Locate the account to be removed.
-
If you selected the Accounts node, use the fields in the Search Accounts section to search for the account. Your search results are displayed in the Search Results table.
-
If you selected a target type or domain node, the account displays in the Search Results table.
-
-
In the Search Results table, select the account to be removed, and then click Remove.
-
When you are finished, click the Apply button located at the top of the page.
5.1.4 Working with Grantees
This section describes the different tasks you can perform when working with grantees in Oracle Privileged Account Manager.
Note:
You must be an Oracle Privileged Account Manager administrator with the User Manager Admin Role to add, edit, or delete grantees.
The topics in this section are:
5.1.4.1 What Are Grantees?
Grantees are users or groups in the ID Store that have been granted access to a privileged account managed by an Oracle Privileged Account Manager administrator. Users cannot check out a privileged account unless they have been granted access to that account.
5.1.4.2 Granting Accounts to Users
Use the following steps to grant access to a privileged account:
-
Expand the Home accordion.
-
Click Accounts or a sub-node to locate the account to which you want to grant access.
If necessary, use the Search Accounts portlet to search for the account as described.
-
Select the account name in the Search Results table.
The General, Grants, and Credential Store Framework tabs display.
-
Select the Grants tab.
If any users are already associated with this account, their names are listed in the table in the Users area.
-
Click Add to open the Add Users dialog.
-
In the Add Users dialog, enter all or part of a user name and then click the arrow icon to browse for the user name to add.
For example, to grant access to the sec_admin user, you can type
secinto this field and the search results will include any existing user name containing those letters. -
Select (check) the user name and then click Add to add the selected user as a grantee.
-
Click Close to close the dialog.
The new user's name displays in the table.
Note:
At this point, the Default Usage Policy is automatically assigned to the user. However, you can use the Usage Policy menu to select a different policy for that user.
5.1.4.3 Granting Accounts to Groups
Use the following steps to grant access to a privileged account:
-
Expand the Home accordion.
-
Click Accounts or a sub-node to locate the account to which you want to grant access.
If necessary, use the Search Accounts portlet to search for the account as described.
-
Select the account name in the Search Results table.
The General, Grants, and Credential Store Framework tabs display.
-
Select the Grants tab.
If any groups are already associated with this account, their names are listed in the table in the Groups area.
-
Click Add to open the Add Groups dialog.
-
In the Add Groups dialog, enter all or part of a group name and then click the arrow icon to browse for the group name to add.
For example, to grant access to the OPAM_USER_MANAGER group, you can type
opaminto this field and the search results will include any existing group names containing those letters. -
Select (check) the group name and then click Add to add the selected group as a grantee.
-
Click Close to close the dialog.
The new group name displays in the table.
Note:
At this point, the Default Usage Policy is automatically assigned to the group. However, you can use the Usage Policy menu to select a different policy for that group.
5.1.4.4 Searching for Grantees
If you have administrator privileges, you can search for grantees by using the following criteria or a combination of these items.
-
For a user grantee
-
User Name
-
First Name
-
Last Name
-
Target Name
-
Account Name
-
-
For a group grantee
-
Name
-
Description
-
Target Name
-
Account Name
-
Use the following steps to search for a grantee:
-
Select Users or Groups under the Grantees node on the Home tree.
-
When the Search User or Search Group portlet displays on the right, enter your search criteria into one or more of the fields provided.
-
Click Search.
Review your search results in the Search Results table.
5.1.4.5 Opening a Grantee
You can open a grantee to view information about that user or group grantee.
Use one of the following methods to open a grantee:
-
Click the User name or the Group name (an active link) in the Search Results table.
-
Select the User or Group row and then click the Open icon.
The User: username or the Group: groupname page opens where you can review the information about that grantee.
5.1.4.6 Removing Grantees from an Account
To remove one or more grantees from an account
-
Open the account and select the Grants tab.
-
Select the user or group row in the Search Results table.
-
Click the Remove icon.
-
When you are prompted to confirm the removal, click the Remove button to continue, (or Cancel to terminate the operation).
The prompt closes and the user or group is removed from the table.
5.1.5 Working with Reports
Oracle Privileged Account Manager reports are real-time reports that provide information about the current status of accounts and targets being managed by Oracle Privileged Account Manager.
Note:
You must be an Oracle Privileged Account Manager administrator with the Security Auditor Admin Role to open and review Oracle Privileged Account Manager reports.
The topics in this section include:
To view a report, expand the Reports accordion and click a Report link. The report information is displayed in the Reports page on the right.
5.1.5.1 Working with Deployment Reports
Select the Deployment Report link to view information about how targets and privileged accounts are currently deployed.
Information about the deployment is organized into three portlet:
-
Target and Accounts Deployment table. Provides a list of targets, including their target type and host names. Expand the arrow icon next to a target name to view the accounts associated with that target.
Tip:
You can click a link in the Target/Account column to open the configuration page for that target or account.
-
Target Distribution. This portlet illustrates how targets are distributed within your deployment.
-
Account Distribution. This portlet illustrates how accounts are distributed within your deployment, by Organization.
Use the Show and Filter drop-down menus to control how the report content is displayed. For example, use the Show menu to view all targets or filter the results to view a particular target. You can use the Filter menu to view the target and account distribution in bar chart, pie chart or tabular format.
5.1.5.2 Working with Usage Reports
Select the Usage Report link to view information about how privileged accounts are currently being used in your deployment. This information displays in the following portlets:
-
Account Usage. This portlet provides a list of targets, the target types, host names, and the last checked out date. Expand the arrow icon next to a target name to view the accounts associated with that target.
-
Checked Out Accounts. This portlet illustrates which targets are checked out within your deployment.
Use the Show and Filter drop-down menus to control how the report content is displayed. For example, select Show to view just currently checked out accounts or accounts that were checked out in the last hour, day, or week. You can use the Filter menu to view the report information as a bar chart, pie chart, or in tabular format.
5.1.5.3 Working with Failure Reports
The Failure Report provides information about the current state of target and account failures. This information displays in the following portlets:
-
Targets and Accounts Failures. This portlet provides a list of targets, the target status, last error message, and the last failure date. Expand the arrow icon next to a target to view the accounts associated with that target.
-
Target Failures. This portlet illustrates the target failures within your deployment.
-
Account Failures. This portlet illustrates the account failures within your deployment.
Use the Show and Filter drop-down menus to control how the report content is displayed. For example, select Show to view the errors that occurred during the last 24 or 48 hours, the last week, or the last 30 days. You can use the Filter menu to view the report information as a bar chart, pie chart, or in tabular format.
5.2 Working with Self-Service
This section provides instructions for users working with Oracle Privileged Account Manager.
The topics include:
5.2.1 Self-Service Workflow
This section describes the basic workflow for self-service users:
-
Searching for an account
-
Checking out the account
-
Viewing checked-out accounts
-
Checking in accounts
5.2.2 Searching for Accounts
You can search for an account by following the instructions provided in Section 5.1.3.3, "Searching for Privileged Accounts."
5.2.3 Checking Accounts Out and In
To check out a privileged account granted to you, see Section 5.1.3.6, "Checking Out Accounts."
To check an account back in again, follow the instructions provided in Section 5.1.3.7, "Checking In Accounts."
5.3 Moving from a Test Environment to a Production Environment
For information about moving Oracle Fusion Middleware components from one environment to another, see "Moving from a Test to a Production Environment" in Oracle Fusion Middleware Administrator's Guide.
For information about moving Identity Management components, including Oracle Privileged Account Manager, from a test environment to a production environment, see "Moving Identity Management Components to a Target Environment" in Oracle Fusion Middleware Administrator's Guide.