3 Getting Started with Administering Oracle Privileged Account Manager
You can administer Oracle Privileged Account Manager from the Console and from the command line. This chapter describes how to perform basic administration tasks.
Note:
This chapter assumes you have installed and configured Oracle Privileged Account Manager as described in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
Reading the "Configuring Oracle Privileged Account Manager" chapter in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management might be particularly helpful.
In this guide, when you are instructed to start the Oracle WebLogic Administration Server (Admin Server) or various Managed Servers, refer to "Starting or Stopping the Oracle Stack" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management for instructions.
This chapter includes the following topics:
-
Section 3.1, "Getting Started after Installing 11g Release 2 (11.1.2)"
-
Section 3.2, "Deploying ICF Connectors in Oracle Privileged Account Manager"
-
Section 3.4, "Navigating Oracle Privileged Account Manager's Console"
3.1 Getting Started after Installing 11g Release 2 (11.1.2)
After installing 11g Release 2, Oracle recommends:
-
Reviewing Table 3-1 to understand the default application URLs for various interfaces that you use to manage Oracle Privileged Account Manager in this release:
Table 3-1 Default Application URLs
Interface Default URL Oracle Identity Navigator
http://adminserver_host:adminserver_port/oinav/
Oracle WebLogic Server Administrative Console
http://adminserver_host:adminserver_port/console/
Oracle Privileged Account Manager Console
http://adminserver_host:adminserver_port/oinav/opam
Oracle Privileged Account Manager Server
http://managedserver_host:managedserver_port/opam
-
Reviewing Table 3-2 to understand various default ports for Oracle Privileged Account Manager in this release:
Port Type Default Port Description Oracle Privileged Account Manager
18102
Default SSL-enabled port for the WebLogic Managed Server where the Oracle Privileged Account Manager server is deployed.
In a shiphome (such as an out-of-the-box environment) there are two WebLogic servers relevant to Oracle Privileged Account Manager:
-
The WebLogic Admin Server in the Oracle Privileged Account Manager domain runs Oracle Identity Navigator and the Oracle Privileged Account Manager Console.
-
An additional WebLogic Managed Server runs the Oracle Privileged Account Manager server.
WebLogic responds to SSL
7002
Default SSL-enabled port for the WebLogic Admin Server (where Oracle Identity Navigator and the Oracle Privileged Account Manager Console are deployed).
-
3.2 Deploying ICF Connectors in Oracle Privileged Account Manager
Oracle Privileged Account Manager enables you to secure, share, audit, and manage administrator-identified account credentials. To provide these capabilities, Oracle Privileged Account Manager must be able to access and manage privileged accounts on a target system.
Connectors enable Oracle Privileged Account Manager to interact with target systems, such as LDAP or Oracle Database, and to perform Oracle Privileged Account Manager-relevant administrative operations on those systems.
Oracle Privileged Account Manager leverages connectors that are compliant with the ICF standard.
This section describes how Oracle Privileged Account Manager consumes these ICF connectors. The topics include:
-
Locating the Oracle Privileged Account Manager Connector Bundles
-
Adding New Connectors to an Existing Oracle Privileged Account Manager Installation
For more information about the Identity Connector Framework, refer to "Understanding the Identity Connector Framework" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
3.2.1 About ICF Connectors
Oracle Privileged Account Manager ships with the following ICF-compliant connectors that were developed by Oracle:
-
Database User Management (DBUM) Connector
-
Generic LDAP Connector
-
Oracle Identity Manager Connector for UNIX
These connectors enable Oracle Privileged Account Manager to manage privileged accounts on a range of target systems belonging to the preceding types.
Oracle Privileged Account Manager can also use customer-created, ICF-compliant connectors, which empowers you to manage your proprietary systems by using Oracle Privileged Account Manager.
For more information about the Identity Connector Framework, refer to "Developing Identity Connectors" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
3.2.2 Locating the Oracle Privileged Account Manager Connector Bundles
Because ICF connectors are generic, and useful in numerous contexts, a given Oracle installation puts all connector bundles into a single location on the file system. All components (such as Oracle Privileged Account Manager) that rely on these connector bundles can access them from this location:
ORACLE_HOME/connectors
The connectors that are pushed into ORACLE_HOME/connectors are actually shipped with Oracle Identity Manager. Of all the connectors in this directory, only the following three connectors are certified with Oracle Privileged Account Manager for this release:
3.2.3 Consuming ICF Connectors
Oracle Privileged Account Manager consumes ICF connectors by using the opam-config.xml file. The contents of this file provide the following information to Oracle Privileged Account Manager:
-
Where to pick up the ICF connector bundle (on the file system)
-
Which configuration attributes are relevant for the Oracle Privileged Account Manager use-cases
-
How to render the Oracle Privileged Account Manager Console when configuring connectivity to a target system using a particular connector
You will find the opam-config.xml file in the ORACLE_HOME/opam/config directory. During domain creation, the opam-config.xml file is copied to the
DOMAIN_HOME/config/fmwconfig/opam directory, and this file is applicable for that domain. The out-of-the-box image is configured to pick up and use the connector bundles that ship with the Oracle Identity Management Suite.
The opam-config.xsd file (also located in the ORACLE_HOME/opam/config directory) describes the schema for opam-config.xml. If you make any changes to
DOMAIN_HOME/config/fmwconfig/opam/opam-config.xml file, verify them with the opam-config.xsd file.
3.2.4 Adding New Connectors to an Existing Oracle Privileged Account Manager Installation
This section describes the processes for adding new connectors to your existing Oracle Privileged Account Manager installation. The topics include:
3.2.4.1 Adding Connectors Supplied by Oracle
If you are adding new ICF connectors that are supplied by Oracle, then they will be accompanied by installation instructions. These instructions describe where to store the connector bundle and how to modify the installation specific opam-config.xml file.
3.2.4.2 Adding Custom Connectors
Oracle Privileged Account Manager can use custom connectors that you created or that were created by a third party. However, these connectors must strictly adhere to the ICF standard. After verifying that the connector is ICF-compliant, perform the following steps to deploy the connector for Oracle Privileged Account Manager consumption:
-
Put the connector bundle in a location on the file system where the bundle can be read by the Oracle Privileged Account Manager at run time.
-
Perform the following steps to create a configuration block for the connector and include that block in the installation specific
opam-config.xmlfile:-
Design and create a relevant configuration block.
Both the
opam-config.xmlandopam-config.xsdfiles contain documentation and an example at the beginning of the file describing how to create a configuration block. -
Ensure that this connector configuration block includes the file system location you specified for the connector bundle in step 1.
-
Add the new connector configuration block to the
opam-config.xmlfile by containing it in a<connectorConfig>block. -
Validate the modified
opam-config.xmlfile against theopam-config.xsdfile to ensure that the Oracle Privileged Account Manager server can read the modified file. You can use your favorite XML schema validation tool for this purpose.
-
-
Restart the Oracle Privileged Account Manager server.
-
Connect to Oracle Privileged Account Manager, and then add and configure a new target system using the newly added connector type.
3.3 Starting Oracle Privileged Account Manager
This section provides some high-level information about starting and working with Oracle Privileged Account Manager's Console. The topics include:
-
Configuring SSL Communication in Oracle Privileged Account Manager
-
Invoking Oracle Privileged Account Manager's Web-Based Console
Note:
Refer to Oracle Fusion Middleware Administrator's Guide for Oracle Identity Navigator for more detailed information.
3.3.1 Starting WebLogic
Before you start Oracle Privileged Account Manager, you must start the WebLogic servers and console.
Note:
-
For detailed information about starting WebLogic and managed servers, see "Starting or Stopping the Oracle Stack" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
-
You must have the appropriate Administration Role and credentials to start the server. Refer to Section 2.3.1, "Administration Role Types" for more information.
-
Connect the Node Manager to WLST by running the
nmConnectcommand.See "Node Manager Commands" in the Oracle Fusion Middleware WebLogic Scripting Tool Command Reference for instructions.
-
Start the WebLogic Admin Server. For example,
On UNIX, type
MIDDLEWARE_HOME/user_projects/domains/DOMAIN_NAME/bin/startWebLogic.sh
On Windows, type
MIDDLEWARE_HOME\user_projects\domains\DOMAIN_NAME\bin\startWebLogic.bat
-
Start the Oracle Privileged Account Manager managed server.
-
Open a browser and start the WebLogic Console from the following location:
http://adminserver_host:adminserver_port/console
3.3.2 Configuring SSL Communication in Oracle Privileged Account Manager
Oracle Privileged Account Manager can connect to target systems through Secure Socket Layer (SSL) or non-SSL options. The SSL option is more secure, but requires some additional configuration.
To communicate securely over SSL with a target system, the WebLogic instance running Oracle Privileged Account Manager must trust the SSL certificate used by the target system because Oracle Privileged Account Manager inherits its SSL configuration from the WebLogic container in which it runs. To have the WebLogic instance running Oracle Privileged Account Manager (and therefore Oracle Privileged Account Manager) trust the target system's SSL certificate, you must import the certificate into the truststore used by that WebLogic instance.
Use the following steps to enable SSL communication between the target system and Oracle Privileged Account Manager:
-
Export the SSL certificate from the target system host computer.
Note:
The steps for exporting an SSL certificate are different for each target system type. Refer to the product documentation provided for your target system for detailed instructions.
-
Copy the certificate to the machine where you have the WebLogic instance running Oracle Privileged Account Manager.
If you have the Oracle Privileged Account Manager/Oracle Identity Navigator Console and the Oracle Privileged Account Manager server running on different machines, you must copy the SSL certificate to the Oracle Privileged Account Manager server machine.
-
Run the following command to import the certificate into the JVM truststore of the WebLogic Server on which Oracle Privileged Account Manager is running:
JAVA_HOME\bin\keytool -import -file FILE_LOCATION -keystore TRUSTSTORE_LOCATION -storepass TRUSTSTORE_PASSWORD -trustcacerts -alias ALIAS
Where
-
JAVA_HOME is the location used by your WebLogic server. For example.
-
MIDDLEWARE_HOME/jrockit.. -
MIDDLEWARE_HOME/jdk.. -
The location where you installed the Java software
-
-
FILE_LOCATION is the full path and name of the certificate file.
-
TRUSTSTORE_LOCATION is one of the following truststore paths:
Table 3-3 Truststore Locations
If you are using: Import the Certificate into the Keystore in This Directory: Oracle jrockit_R27.3.1-jdk
JROCKIT_HOME/jre/lib/securityThe default Oracle WebLogic Server JDK
WEBLOGIC_HOME/java/jre/lib/security/cacertsA JDK other than Oracle
jrockit_R27.3.1-jdk or
Oracle WebLogic Server JDKJAVA_HOME/jre/lib/security/cacerts -
TRUSTSTORE_PASSWORD is the password for the truststore.
-
ALIAS is an alias for the certificate.
Note:
The default password for the
cacertskeystore is changeit. -
-
Restart all WebLogic servers.
Note:
For more information about WebLogic security concepts and how to create custom keystores, refer to "Configuring Identity and Trust" in the Oracle Fusion Middleware Securing Oracle WebLogic Server.
3.3.3 Assigning the Application Configurator Role to a User
After installation, you do not have any users present with administrator roles. You must select a user and grant that person the Application Configurator role by using Oracle Identity Navigator.
Note:
Refer to "Assigning a Common Admin Role" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Navigator for instructions.
The Application Configurator user can have other roles in addition to this role. For more information about other Admin Roles, see Section 2.3.1, "Administration Role Types."
When the Application Configurator user logs in by using the following URL, that user will see a empty screen with a Configure OPAM link.
http://adminserver_host:adminserver_port/oinav/opam
The Application Configurator user can use this link to let the Oracle Privileged Account Manager Console know where Oracle Privileged Account Manager server is running by providing the Oracle Privileged Account Manager server's host and port.
When the Oracle Privileged Account Manager Console can successfully communicate with the Oracle Privileged Account Manager server, the Oracle Privileged Account Manager Console will be populated with content.
Note:
Oracle Privileged Account Manager administrators and users will probably never have to use the Oracle Identity Navigator interface except during the initial set-up of Oracle Privileged Account Manager.
3.3.4 Invoking Oracle Privileged Account Manager's Web-Based Console
You can access Oracle Privileged Account Manager's Console by opening a browser window and entering the following URL:
http://adminserver_host:adminserver_port/oinav/opam
When the Oracle Privileged Account Manager page displays with the Sign In screen, log in with the appropriate administrator or end user credentials.
Note:
If you prefer using Oracle Privileged Account Manager's command line tool or Oracle Privileged Account Manager's RESTful interface, refer to Appendix A, "Working with the Command Line Tool" or Appendix B, "Working with Oracle Privileged Account Manager's RESTful Interface" (respectively) for detailed information about using those interfaces.
3.4 Navigating Oracle Privileged Account Manager's Console
This section provides a high-level overview of the Oracle Privileged Account Manager Console.
Note:
Access to certain features in the Console is based on your administration role (Admin Role) and credentials. For example, the Reports and Administration accordions described in this section are not available to users with the Security Administrator role.
Refer to Section 2.3, "Understanding Oracle Privileged Account Manager Authorization" for more information about Admin Roles.
The topics in this section include:
Tip:
Hover your mouse over elements in the Oracle Privileged Account Manager interface (such as nodes in the Home accordion or parameter fields) to see helpful prompts.
3.4.1 Working with the Home Accordion
When you log in to Oracle Privileged Account Manager, the Home accordion is displayed and expanded by default. Based on your Admin Role and credentials, this area gives you access to a tree containing some or all of the following nodes:
-
Accounts: Search, open, add, and remove accounts
-
Targets: Search, open, add, and remove targets
-
Policies: Search, open, create, and delete Password Policies and Usage Policies
-
Grantees: Search, open, add, and remove grantees (users and groups)
-
My Checked-out Accounts: View, check out, and check in accounts
Note:
For detailed information about Admin Roles, see Section 2.3.1, "Administration Role Types."
You can expand these nodes to view the target types, domains, Password and Usage Policies, and Users and Groups Grantees.
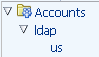 |
For example, in this figure, the ldap node is the Target Type, and us is the Domain. So, if you are looking for an account and know that it is managed by an LDAP target in the us Domain, simply click the us node to view a list of the accounts in that domain. The results display in the Search Results table. |
Selecting the nodes or subnodes on this accordion causes a new page to display. You use parameters on these pages to configure and manage Oracle Privileged Account Manager.
Above the Home accordion are two menus that you can use to control how the Home accordion is displayed:
-
View: Use the options on this drop-down menu to expand or collapse all nodes at once, expand or collapse all subnodes below a selected node, or scroll to the first or last node.
-
Perspective: Use this drop-down menu to control whether information is displayed from a Target Type or from a Domain perspective.
3.4.2 Working with the Reports Accordion
Expand the Reports accordion and click a Report link to access different reports about the targets and privileged accounts in your deployment. The information is displayed in the Reports page on the right side of the Console.
Note:
For detailed information about these Reports, see Section 5.1.5, "Working with Reports."
3.4.3 Working with the Administration Accordion
Expand the Administration accordion and click Server Configuration to open a Server Configuration tab. You use the Server Configuration tab to set up and test a connection to your Oracle Privileged Account Manager server.
Note:
For detailed information about managing an Oracle Privileged Account Manager server, see Section 4.4, "Managing an Oracle Privileged Account Manager Server."
3.4.4 Working with the Search Portlet
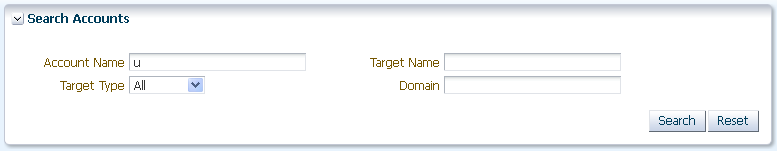
You use Oracle Privileged Account Manager's Search portlet to search for targets, accounts, policies, users, and groups.
You can configure searches by using one or more of the parameters displayed in a Search portlet. The available parameters depend on the type of search. The following table describes the different search parameters:
Table 3-4 Search Portlet Parameters
| Parameter Name | Description | Search Type |
|---|---|---|
|
Account Name |
Enter one or more letters of the account name for which you are searching. |
Accounts, Users, Groups |
|
Target Name |
Specify one or more letters of the target name on which to search. |
Accounts, Targets, Users, Groups |
|
Target Type |
Specify All (to search all target types), ldap, unix, or database. |
Accounts, Targets |
|
Domain |
Specify the domain on which to search. |
Accounts, Targets |
|
Host Name |
Specify the name of the host on which to search. |
Targets |
|
Policy Name |
Specify one or more letters of the policy name for which you are searching. |
Policies |
|
Policy Status |
Specify whether to search for All policies or limit the search to only Active or only Disabled policies. |
Policies |
|
Policy Type |
Specify whether to search for All policy types or limit the search to only Password Policies or only Usage Policies. |
Policies |
|
User Name |
Specify one or more letters of the user's name for which you are searching. |
Users |
|
First Name |
Specify one or more letters of the user's first name. |
Users |
|
Last Name |
Specify one or more letters of the user's last name. |
Users |
|
Group Name |
Specify one or more letters of the group name for which you are searching. |
Groups |
|
Description |
Provide the group description. |
Groups |
The general steps for performing a search are as follows:
-
Select the appropriate node in the Home tree.
For example, to search for an account, select the Accounts node.
-
Enter one or more of the search parameters available in the Search portlet and then click Search.
For example, to search for a list of all the accounts on a particular LDAP target, enter one or more letters of the target's name, select LDAP from Target Type menu, and then click Search.
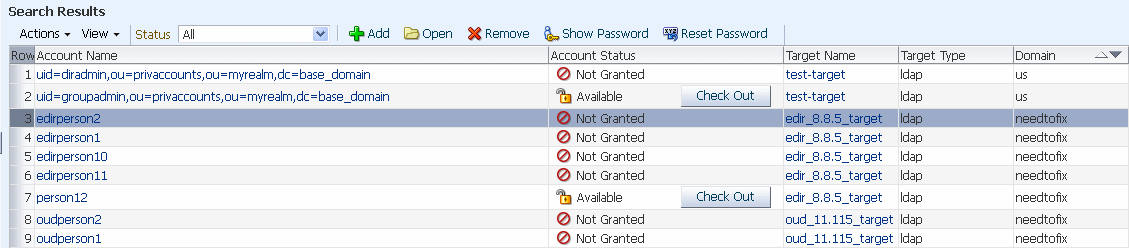
The results are displayed in the Search Results table.
Note:
You can use the Status menu, located above the Search Results table, to control the search results based on the account status. See the table in Section 3.4.5, "Working with a Search Results Table" for more information.
-
To perform another search, click Reset.
3.4.5 Working with a Search Results Table
You can use the drop-down menus and icons located along the top of the different Search Results tables to perform various tasks.
The following table describes these features:
Note:
The availability of these features change, based on your role (privileges) and what type of search was performed. See Section 2.3.1, "Administration Role Types" for more information.
Table 3-5 Search Results Table Features
| Feature Name | Search Type | Description |
|---|---|---|
|
Actions |
Accounts, Targets, Policies, Users, Groups, and My Checked-out Accounts |
Click to select an action from a drop-down menu. Note: The Actions menu options duplicate the task icons displayed above the table. |
|
View |
Accounts, Targets, Policies, Users, Groups, and My Checked-out Accounts |
Use this drop-down menu to control how the columns are displayed in the Search Results table.
|
|
Status |
Accounts only |
Choose an option from the menu to control how the search results are displayed:
|
|
Add |
Accounts, Targets, Users, and Groups |
Click to add a new target, account, user, or group to the Oracle Privileged Account Manager repository. |
|
Open |
Accounts, Targets, Policies, Users, and Groups |
Click to open the selected account, target, policy, user, or group. |
|
Remove |
Accounts, Targets, Policies, Users, and Groups |
Click to remove the selected account, target, policy, user, or group from the Oracle Privileged Account Manager repository. |
|
Show Password |
Accounts only |
Click to open a message listing the account name and the password for that account. |
|
Reset Password |
Accounts only |
Click to open the Reset Password dialog where you can enter a new password for the selected account. |
|
Create Password Policy |
Policies only |
Click to create a Password Policy. See Section 5.1.2.2, "Adding Targets to Oracle Privileged Account Manager" for more information. |
|
Create Usage Policy |
Policies only |
Click to create a Usage Policy. See Section 5.1.2.2, "Adding Targets to Oracle Privileged Account Manager" for more information. |
|
Delete |
Policies only |
Click to delete a selected policy from the Oracle Privileged Account Manager repository. |
|
Check-In |
My Checked-out |
Click to check in the selected checked-out account. See Section 5.1.3.7, "Checking In Accounts" for more information. |