Understanding EPM Security and Setups
This topic discusses:
PeopleSoft application security
EPM security
Setting up EPM security
EPM security views
PeopleSoft Application Security
PeopleSoft applications use multilevel security to enable you to successfully manage shared data environments. You set up data access at different entry points within your system and define the most efficient path to data across business groups, tables, departments, pages, and so forth. You have full control over security definitions, selecting options to create a matrix that enables or restricts user access to data through a series of authorizations.
Security access covers three areas: networks, databases, and applications. Network security controls the overall point of entry into your system hardware and software resources. Database security narrows the scope of a user's information access. At the application level, security extends to the field level. This diagram illustrates PeopleSoft application security levels:
Image: Levels of security in PeopleSoft applications
This example illustrates the Levels of security in PeopleSoft applications.
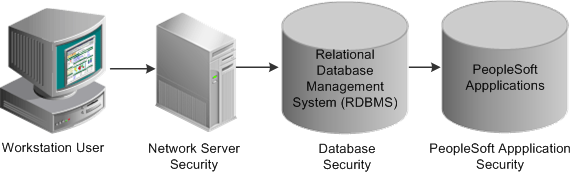
Application Security Terms
This table describes the various types of PeopleSoft application security:
|
Security Type |
Location |
Function |
|---|---|---|
|
Network |
Network software |
Controls entry into the network and authorizes rights to use shared resources. |
|
Relational Database Management System (RDBMS) |
Operating system |
Controls access to the database. |
|
User |
PeopleTools |
Controls access to application pages, functions, and business components. |
|
Object |
PeopleTools |
Controls access to objects or object groups that are used in application development. |
|
Query |
PeopleTools |
Defines table row sets that are accessed for performing system queries. |
|
Row-level |
PeopleTools and PeopleSoft applications |
Controls access to the subset of data rows within tables that the user is authorized to review or update. |
|
Field-level |
PeopleCode |
Controls access to individual fields on pages. |
EPM Security
EPM security controls access to specific data within the EPM database and enables you to grant users access to specific rows, columns, or fields in an EPM database table. Data-access privileges within the warehouse can be defined for both Operational Warehouse - Enriched (OWE) and Multidimensional Warehouse (MDW) tables, and for dimension and fact tables.
You can specify EPM security access using any of the following methods:
Field-level security
Ledger security
Dimension (row-level) security
Metric (column-level) security
EPM security provides a single point of entry for defining and maintaining data access rules across all the EPM Warehouses and Analytical Applications.
Setting Up EPM Security
EPM security is extremely flexible and enables you to restrict user access to EPM database tables in a variety of ways, including field level, row level, and column level restrictions. PeopleSoft-delivered ETL jobs move security data from your source transaction system to EPM target warehouse tables. You must set up PeopleTools and IBM WebSphere DataStage security, but you need only use the security pages documented in this topic to redefine or modify your existing security data.
You have the option of implementing only one type of EPM security restriction or all four types:
Field-level security.
Ledger security.
Row-level security.
Column-level security.
Image: EPM Security Setup Process Flow
The following security setup process flow demonstrates the different security setup options:
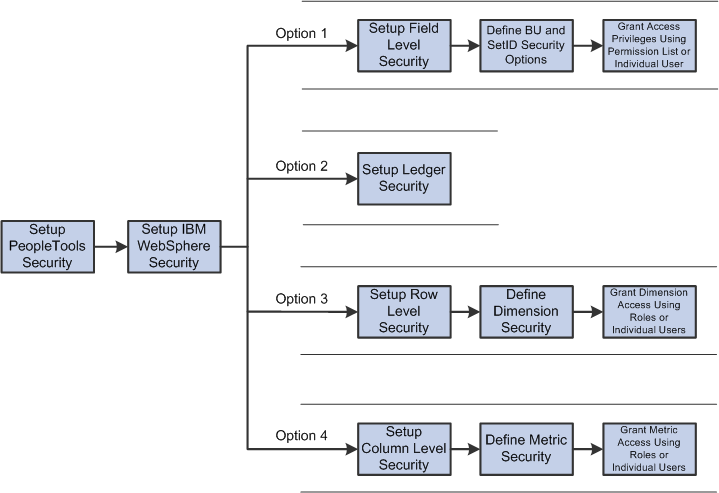
As demonstrated in the diagram, you can implement any combination of field level, ledger, row level, and column level security restrictions.
Note: Refer to your EPM Warehouse and Analytical Application documentation for any special security setups required for those products.
PeopleTools security
PeopleTools security provides user authentication and application-level security. Users are authorized to access the EPM database using Peopletools login security. Users may be granted or denied access to each application and components therein. EPM security works together with PeopleTools security, so you must properly define PeopleTools security prior to setting up EPM security.
See PeopleSoft PeopleTools: Security Administration
IBM WebSphere DataStage Security
PeopleSoft EPM delivers the IBM WebSphere extract, transform, and load (ETL) tool to load your source data into the Operational Warehouse - Staging (OWS) and migrate the data to the OWE and the MDW. The tool builds three layers of security into the repository and its objects. Access is granted through groups and users.
The three layers of security are:
A user role that is created by the EPM Production Manager.
The Production Manager assigns Windows user groups to one of four DataStage user categories. For example, if you belong to the Windows Administrators user group, you might be assigned to the DataStage Production Manager category and have full access to all areas of a DataStage project. This is the default for DataStage users.
Project privileges that range from browse-only to full Production Manager privileges.
Object-level safeguards that prevent users from jointly accessing or overwriting the same object.
For example, if a user is working on a job, that object is locked so that no other user can access it. Locks are automatically created to avoid repository contamination.
The following DataStage user categories are defined in PeopleSoft EPM: the EPM Production Manager, Developer, Operator, and None. The Production Manager has full access to all areas of a DataStage project, including repository objects, and can create and manipulate protected projects. The Production Manager grants access to all other groups and users. Developers have full access to all areas of a DataStage project and can create and modify ETL jobs. This is the default setting. Operators have permission to run and manage DataStage jobs. Users who are assigned to None do not have permission to sign in to DataStage.
See IBM Information Server: Administration Guide
Field Level Security
Field level security enables you to restrict users to specific fields on your EPM database tables based on business units and SetIDs (because the tables are keyed by SetID or business unit).
To set up field level security you must:
Enable field level security and specify related options.
Associate security views with specific users, permission lists, business units, or SetIDs.
Apply the aforementioned field level security parameters.
Associate specific users or permission lists with the business unit and/or SetID restrictions (data group restrictions) you defined in the previous steps.
Ledger Security
Ledger security enables you to restrict users to specific EPM ledger tables. You can restrict access to the tables by user or permission list.
Dimension (Row Level) and Metric (Column Level) Security
Row level security enables you to secure individual rows of an EPM dimension table. Column level security enables you to secure individual columns of an EPM database table. Usually, these are measures on fact tables, but may also be attributes on a dimension table that contain sensitive data, such as Employees' Salary or the Social Security Number columns. With row level and metric level support, you can restrict access by individual user or security roles.
To set up row level security you must:
Define dimension security.
Associate the dimension with a security join table.
Security join tables are EPM database tables that store the security profiles for users along with the corresponding dimension values for which they have access.
Define users and security roles.
Assign dimension rows to the user or security role.
To set up column level security you must:
Define metric security.
Define users and security roles.
Assign metric to the user or security role.
See Defining Dimension and Metric Security.
See Understanding Role and User Based Security for Dimensions and Metrics.
EPM Security Views
Security views are SQL SELECT statements that filter out data rows whose key values are not needed as valid access parameters. The result is that users who are authorized to access SetIDs or business units see only a subset of values from these edit table values. PeopleSoft EPM delivers prepackaged security views for most securable objects in EPM and the views tell the system which table views to reference. To use these security views in PeopleTools, use the views as a search view.
|
Object |
Delivered EPM Security View |
|---|---|
|
Personal Data |
PERSONAL_SRCH |
|
Job Data |
JOB_SRCH |
|
Job Code |
JOBCODE_SRCH |
|
Location |
LOCATION_SRCH |
|
Scenario |
SCENARIO_SRCH |
You can alter these prepackaged views or build your own.