23 Upgrading OIM-OAM Integrated Highly Available Environments
This chapter describes how to upgrade Oracle Identity Manager (OIM), Oracle Access Management Access Manager (Access Manager), and Oracle Adaptive Access Manager (OAAM) integrated split domain highly available environments to 11g Release 2 (11.1.2.3.0) using the manual upgrade procedure.
Note:
If your existing Oracle Identity and Access Management environment was deployed using the Life Cycle Management (LCM) Tools, you must use the automated upgrade procedure to upgrade to Oracle Identity and Access Management 11g Release 2 (11.1.2.3.0).For information about automated upgrade procedure, supported starting points and topologies, see Chapter 2, "Understanding the Oracle Identity and Access Management Automated Upgrade".
This chapter includes the following sections:
-
Section 23.1, "Understanding the Integrated HA Upgrade Topology"
-
Section 23.3, "Supported Starting Points for an Integrated, HA Upgrade"
-
Section 23.4, "Roadmap for Upgrading OIM/OAM/OAAM Integrated Highly Available Environments"
-
Section 23.7, "Creating Necessary Schemas and Upgrading the Existing Schemas"
23.1 Understanding the Integrated HA Upgrade Topology
This chapter describes how to upgrade the topology shown in Figure 23-1. This topology is based on the split domain topology described in the Enterprise Deployment Guide for Oracle Identity and Access Management 11g Release 2 (11.1.2.1). It has been modified to include Oracle Adaptive Access Manager (OAAM).
This topology and the accompanying procedures in this chapter are provided to serve as an example for upgrading a highly available, integrated Oracle Identity and Access Management environment. Your specific Oracle Identity and Access Management installation will vary, but this topology and upgrade procedure demonstrates the key elements of the upgrade process, which can be applied to your specific environment.
For a complete description of the topology diagram, refer to the Enterprise Deployment Guide in the Oracle Identity and Access Management 11g Release 2 (11.1.2.1) Documentation Library.
Figure 23-1 Starting Point for the OIM/OAM/OAAM Integrated HA Upgrade
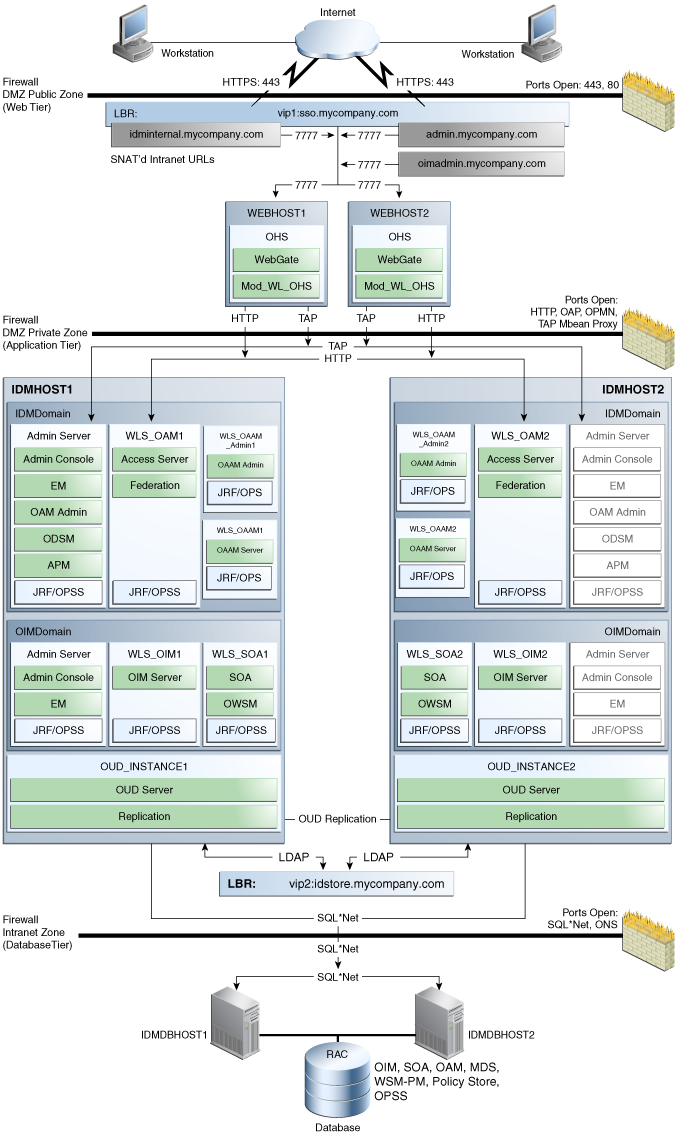
Description of ''Figure 23-1 Starting Point for the OIM/OAM/OAAM Integrated HA Upgrade''
23.2 Upgrade Overview
The procedure for upgrading the OIM-OAM-OAAM integrated highly available environments involves the following high level tasks:
-
Pre-Upgrade Tasks: This step includes reviewing system requirements, reviewing the customizations that are lost as part of the upgrade, generating the pre-upgrade reports and completing the necessary tasks specified in the pre-upgrade report, backing up the existing environment, and stopping the servers.
-
Upgrading Oracle Home: This step includes upgrading the binaries of Oracle WebLogic Server (if necessary), Oracle SOA Suite, Oracle Identity Manager, Oracle Access Manager, and Oracle Adaptive Access Manager using the Oracle Universal Installer.
-
Creating Necessary Schemas and Upgrading the Existing Schemas: This step includes creating new schemas like Oracle Mobile Security Manager (OMSM) schema, Oracle BI Publisher (BIP) schema and upgrading the existing schemas like Oracle Identity Manager schema, Oracle Access Manager schema, Oracle Platform Security Services schema and so on.
-
Upgrading Oracle Identity Manager Domain: This step includes tasks like upgrading the Oracle Identity Manager middle tier, scaling out Oracle Business Publisher, upgrading Oracle Remote Manager and Oracle Design Console and so on.
-
Upgrading Oracle Access Management Domain Which Also Contains Oracle Adaptive Access Manager: This step includes tasks like upgrading Oracle Access Management system configurations, extending the Oracle Access Management domain to include Oracle Mobile Security Suite and Policy Manager and so on. The Oracle Access Management domain also contains Oracle Adaptive Access Manager (OAAM). Therefore, you must redeploy OAAM applications as part of the Access Manager domain upgrade.
-
Seeding the Oracle Identity Manager 11.1.2.3.0 Resources in Oracle Access Management: If you upgraded Oracle Identity Manager domain prior to upgrading Oracle Access Management domain, you must run the
-configOIMcommand to seed the Oracle Identity Manager 11.1.2.3.0 resources in Oracle Access Management.This step is not required if you upgraded Oracle Access Management domain first.
-
Verifying the Upgraded Environment: This step includes tasks for verifying if the upgrade was successful.
Note:
It is assumed that you are running Oracle HTTP Server (OHS) 11g Release 1 (11.1.1.6.0), WebGate 11g Release 2 (11.1.2.1.0), and Oracle Unified Directory (OUD) 11g Release 2 (11.1.2.1.0) installed with Oracle Identity and Access Management 11g Release 2 (11.1.2.1.0).Oracle Identity and Access Management 11g Release 2 (11.1.2.3.0) is compatible with Oracle HTTP Server 11g Release 1 (11.1.1.6.0), WebGate 11g Release 2 (11.1.2.1.0), and Oracle Unified Directory (OUD) 11g Release 2 (11.1.2.1.0). Therefore, it is not mandatory to upgrade these components. However, if you wish to upgrade them, refer to the following document:
For information about upgrading Oracle HTTP Server to 11g Release 1 (11.1.1.9.0), see "Task 4: Upgrading the Oracle HTTP Server Oracle Home Using the Oracle Web Tier Patch Set Installer" in the Oracle Fusion Middleware Patching Guide for 11g Release 1 (11.1.1.9.0). When you run the Patch Set Installer for upgrading Oracle HTTP Server, select Install Software and Do Not configure option on the Select Installation Type screen.
For information about upgrading WebGate to 11g Release 2 (11.1.2.3.0), use the instructions described in the Oracle Fusion Middleware Installing WebGates for Oracle Access Manager. During the process, ensure that you point to the existing 11g Release 2 (11.1.2.1.0) WebGates, when prompted.
For information about upgrading Oracle Unified Directory (OUD) to 11g Release 2 (11.1.2.3.0), see "Updating the Oracle Unified Directory Software" in the Oracle Fusion Middleware Installing Oracle Unified Directory.
23.3 Supported Starting Points for an Integrated, HA Upgrade
Table 23-1 lists the starting points that are supported for upgrade of an integrated highly available environments.
Table 23-1 Supported Starting Points for Upgrade of an Integrated Environment
| Component | Supported Starting Point |
|---|---|
|
Oracle Identity Manager |
11g Release 2 (11.1.2.1.0) |
|
Oracle Access Management |
11g Release 2 (11.1.2.1.0) |
|
Oracle Adaptive Access Manager |
11g Release 2 (11.1.2.1.0) |
|
Oracle SOA Suite |
11g Release 1 (11.1.1.6.0) |
|
Oracle WebLogic Server |
10.3.6 Oracle Identity and Access Management 11.1.2.3.0 is compatible with Oracle WebLogic Server 10.3.6. Therefore, you do not have to upgrade Oracle WebLogic Server if you are already using 10.3.6 version. |
23.4 Roadmap for Upgrading OIM/OAM/OAAM Integrated Highly Available Environments
Table 23-2 lists the tasks that you must complete to upgrade an integrated high availability environment.
| Task | For more information, | |
|---|---|---|
|
1 |
Review the topology that can be upgraded using the procedure described in this chapter. |
|
|
2 |
Review the supported starting points for upgrading integrated environments. |
See, Supported Starting Points for an Integrated, HA Upgrade |
|
3 |
Complete the necessary pre-upgrade tasks before you start the upgrade process. |
|
|
4 |
Upgrade Oracle Home by upgrading the binaries of Oracle Identity and Access Management, Oracle WebLogic Server, and Oracle SOA Suite. |
|
|
5 |
Create necessary database schemas using the Repository Creation Utility (RCU), and upgrade the existing schemas using the Patch Set Assistant (PSA). |
See, Creating Necessary Schemas and Upgrading the Existing Schemas |
|
6 |
Upgrade the Oracle Identity Manager domain. |
|
|
7 |
Upgrade the Oracle Access Management domain. This domain also includes Oracle Adaptive Access Manager. |
See, Upgrading Oracle Access Management Domain Which Also Contains Oracle Adaptive Access Manager |
|
8 |
If you upgraded Oracle Identity Manager domain prior to upgrading Oracle Access Management domain, you must run the |
See, Seeding the Oracle Identity Manager 11.1.2.3.0 Resources in Oracle Access Management |
|
9 |
Verify the OIM-OAM-OAAM integrated upgrade. |
23.5 Performing the Required Pre-Upgrade Tasks
Before you start with the upgrade, you must complete the following pre-upgrade tasks:
-
Review the Oracle Fusion Middleware System Requirements and Specifications and Oracle Fusion Middleware Supported System Configurations documents to ensure that your system meets the minimum requirements for the products you are installing or upgrading to. For more information see Section 24.1.1, "Verifying Certification, System Requirements, and Interoperability".
-
Ensure that you are using a Java Development Kit (JDK) version that is supported and certified with Oracle Identity and Access Management 11.1.2.3.0.
You can verify the required JDK version by reviewing the certification information on the Oracle Fusion Middleware Supported System Configurations page.
The JDK can be downloaded from the Java SE Development Kit 7 Downloads page on Oracle Technology Network (OTN).
Note:
For more information about JDK version requirements, see the "Oracle WebLogic Server and JDK Considerations" topic in the Oracle Fusion Middleware System Requirements and Specifications for Oracle Identity and Access Management 11g Release 2 (11.1.2) document. -
Review the Oracle Identity Manager customizations that are lost or overwritten as part of the upgrade process.
For more information, see Section 10.2.4, "Reviewing the Customizations that are Lost or Overwritten as Part of Upgrade".
-
Generate the pre-upgrade report for Oracle Identity Manager by running the pre-upgrade utility, and analyze all the reports generated. The pre-upgrade report utility analyzes your existing Oracle Identity Manager environment, and provides information about the mandatory prerequisites that you must complete before you upgrade the existing Oracle Identity Manager environment.
For information about generating and analyzing the pre-upgrade report for Oracle Identity Manager, see Section 24.2.2, "Generating and Analyzing Pre-Upgrade Report for Oracle Identity Manager".
-
Stop all the servers on
IDMHOST1andIDMHOST2in the following order:-
Stop the Oracle Adaptive Access Manager Managed Server(s) on
IDMHOST1andIDMHOST2. -
Stop the Access Manager Managed Server(s) on
IDMHOST1andIDMHOST2. -
Stop the Oracle Identity Manager Managed Server(s) on
IDMHOST1andIDMHOST2. -
Stop the Oracle SOA Suite Managed Server(s) on
IDMHOST1andIDMHOST2. -
Stop the WebLogic Administration Server on
IDMHOST1.
-
-
Back up your existing environment after stopping the servers. To do this, complete the following steps:
-
Back up the
MW_HOMEdirectory including the Oracle Home directories inside Middleware home on bothIDMHOST1andIDMHOST2. -
Back up the Access Manager Domain Home directory which also contains Oracle Adaptive Access Manager, on both
IDMHOST1andIDMHOST2. -
Back up the Oracle Identity Manager Domain Home directory on both
IDMHOST1andIDMHOST2. -
Back up the following database schemas:
- Oracle Access Manager schema
- Oracle Identity Manager schema
- Oracle Adaptive Access Manager schema
- Oracle Platform Security Services schema
- MDS schema
- ORASDPM schema
- SOAINFRA schema
- Audit schema
- IAU schema
For more information about backing up schemas, see Oracle Database Backup and Recovery User's Guide.
-
23.6 Upgrading Oracle Home
You must upgrade Oracle SOA Suite to 11g Release 1 (11.1.1.9.0) on both IDMHOST1 and IDMHOST2, as Oracle Identity Manager 11.1.2.3.0 is certified with Oracle SOA Suite 11.1.1.9.0. Also, you must update the binaries of Oracle Identity Manager, Oracle Access Management Access Manager, and Oracle Adaptive Access Manager to 11g Release 2 (11.1.2.3.0) on both IDMHOST1 and IDMHOST2. To do this, complete the following steps:
-
Upgrade Oracle WebLogic Server to 10.3.6 on both
IDMHOST1andIDMHOST2, if you are using an earlier version. This involves running the Oracle WebLogic Server 10.3.6 upgrade installer to upgrade the existing Oracle WebLogic Server.Note:
If you are already using Oracle WebLogic Server 10.3.6, ensure that you apply the mandatory patches to fix specific issues with Oracle WebLogic Server 10.3.6.To identify the required patches that you must apply for Oracle WebLogic Server 10.3.6, see "Downloading and Applying Required Patches" in the Oracle Fusion Middleware Infrastructure Release Notes.
The patches listed in the release notes are available from My Oracle Support. The patching instructions are mentioned in the
README.txtfile that is provided with each patch.For more information about upgrading Oracle WebLogic Server to 10.3.6, see Section 24.1.5, "Upgrading Oracle WebLogic Server to 11g Release 1 (10.3.6)".
-
Upgrade Oracle SOA Suite to 11g Release 1 (11.1.1.9.0). This involves running the Oracle SOA Suite 11.1.1.9.0 installer to update the binaries on
IDMHOST1andIDMHOST2, and performing required post-patching tasks for Oracle SOA Suite.For more information about upgrading Oracle SOA Suite, see Section 24.2.3, "Upgrading Oracle SOA Suite to 11g Release 1 (11.1.1.9.0)".
-
Update the binaries of Oracle Identity Manager, Oracle Access Management Access Manager, and Oracle Adaptive Access Manager to 11g Release 2 (11.1.2.3.0) by running the Oracle Identity and Access Management 11.1.2.3.0 Oracle Universal Installer.
For more information about upgrading the Oracle Identity and Access Management binaries, see Section 24.1.6, "Updating Oracle Identity and Access Management Binaries to 11g Release 2 (11.1.2.3.0)".
23.7 Creating Necessary Schemas and Upgrading the Existing Schemas
In order to upgrade to Oracle Identity and Access Management 11.1.2.3.0, you must upgrade the existing database schemas before you upgrade the domain. Also, it is recommended that you create the new Oracle Mobile Security Manager (OMSM) schema to enable the new feature of Oracle Access Management - Oracle Mobile Security Services. You must also create Oracle BI Publisher schema to enable the embedded BIP feature available in Oracle Identity Manager 11.1.2.3.0.
To create new schemas, you must run the Repository Creation Utility (RCU) 11.1.1.9.0, and to upgrade the existing schemas, you must run the Patch Set Assistant (PSA). To do this, complete the following steps on IDMHOST1:
-
Create the following schemas by running the Repository Creation Utility 11.1.1.9.0:
-
Oracle BI Publisher (BIP) schema
-
Oracle Mobile Security Manager (OMSM) Schema
For information about running the RCU to create new schemas, see Section 24.1.3, "Creating Database Schemas Using Repository Creation Utility".
-
-
Upgrade the following database schemas by running the Patch Set Assistant:
-
Oracle Access Manager schema
-
Oracle Identity Manager schema
-
Oracle Adaptive Access Manager schema
-
Oracle Platform Security Services schema
-
MDS schema
-
ORASDPM schema
-
SOAINFRA schema
-
Audit schema
-
IAU schema
For more information about upgrading schemas, see Section 24.1.4, "Upgrading Schemas Using Patch Set Assistant".
-
23.8 Upgrading Oracle Identity Manager Domain
To upgrade the Oracle Identity Manager domain, complete the following steps:
-
If you are using Windows 64-bit machine, perform the additional tasks described in Section 24.2.4.1, "Additional Task for Windows 64-Bit Users Before Upgrading Middle Tier" on
IDMHOST1before proceeding with the middle tier upgrade. -
If you are upgrading an SSL enabled middleware, that is, if you would be specifying SSL ports for WebLogic Administration Server and SOA Managed Servers during middle tier upgrade, you must create a truststore that contains the public certificates for all SSL enabled servers (which can be WebLogic Administration Server, SOA Managed Servers, OIM Managed Servers) irrespective of the node on which the server is running. This truststore will be used a client side store by the upgrade script to communicate with various servers during upgrade.
For information about creating a truststore, see Section 24.2.4.2, "Creating a Truststore for Upgrading SSL Enabled Middleware".
-
Update the
oim_upgrade_input.propertiesfile located atOIM_HOME/server/bin/onIDMHOST1, with the values for the properties required for Oracle Identity Manager middle tier upgrade.For information about the properties that you must update in the
oim_upgrade_input.propertiesfile, see Section 24.2.4.3, "Updating the Properties File". -
Performing the Oracle Identity Manager middle tier upgrade offline on
IDMHOST1. This is done by runningOIMUpgradeoffline utility.For more information about performing Oracle Identity Manager middle tier upgrade offline, see Section 24.2.4.4, "Performing Oracle Identity Manager Middle Tier Upgrade Offline".
-
Replicate the domain configuration on
IDMHOST2by packing the Oracle Identity Manager domain onIDMHOST1and unpacking it onIDMHOST2.For more information about replicating the domain configuration using
packandunpackcommands, see Section 20.7, "Replicating Domain Configuration on OIMHOST2". -
Start the WebLogic Administration Server and SOA Managed Server(s) on both
IDMHOST1andIDMHOST2. Make sure that you do not start the Oracle Identity Manager Managed Server(s).For information about starting the servers, see Section 24.1.8, "Starting the Servers".
-
Performing the Oracle Identity Manager middle tier upgrade online on
IDMHOST1. This is done by runningOIMUpgradeonline utility. When you perform this step, ensure that the Administration Server for Oracle Access Manager is up and running.For more information about performing Oracle Identity Manager middle tier upgrade online, see Section 24.2.4.6, "Performing Oracle Identity Manager Middle Tier Upgrade Online".
-
Start the Oracle Identity Manager Managed Server(s) and Oracle BI Publisher Server on
IDMHOST1andIDMHOST2.For more information about starting the servers, see Section 24.1.8, "Starting the Servers".
-
If you wish to scale out Oracle BI Publisher, you can do so by creating a new BIP Server on
IDMHOST2, setting the location of the shared BI Publisher configuration folder, setting the scheduler configuration options, and configuring JMS for BI Publisher. This step is optional.For more information about scaling out Oracle BI Publisher, see Section 20.9, "Scaling out Oracle BI Publisher".
-
Upgrade Oracle Identity Manager Design Console and Oracle Identity Manager Remote Manager to 11.1.2.3.0 on
IDMHOST1.For more information, see Section 24.2.5, "Upgrading Other Oracle Identity Manager Installed Components".
-
Complete the necessary Oracle Identity Manager post-upgrade steps described in Section 24.2.6, "Performing Oracle Identity Manager Post-Upgrade Tasks".
Note:
The section Section 24.2.6, "Performing Oracle Identity Manager Post-Upgrade Tasks" contains the post-upgrade tasks for various Oracle Identity Manager starting points. You must perform only those tasks that are applicable to your starting point and your environment. -
If you do not plan to upgrade Oracle Access Management domain to 11.1.2.3.0, then you must manually create the resources
/soa/**and/xmlpserver/**with protection levelEXCLUDEDunder the IAM Suite Application domain.Note:
If you plan to upgrade Oracle Access Management domain to 11.1.2.3.0, post-OIM upgrade, skip this step.To manually create the resources
/soa/**and/xmlpserver/**with protection levelEXCLUDED, complete the following steps:-
Log in to the Oracle Access Management console using the following URL:
http://WLS_Admin_Host:WLS_Admin_Port/oamconsole -
Click Application Domains.
-
Search for IAM Suite and open IAM Suite Application Domain.
-
Click Resources, and then click New Resource.
-
Specify the following details for creating
/soa/**resource:Select Type:
HTTPHost Identifier:
IAMSUiteAgentResource URL:
/soa/**Protection Level:
ExcludedClick Apply to apply the changes.
-
Specify the following details for creating
/xmlpserver/**resource:Select Type:
HTTPHost Identifier:
IAMSUiteAgentResource URL:
/xmlpserver/**Protection Level:
ExcludedClick Apply to apply the changes.
-
Specify the following details for creating
/soa-infra/**resource:Select Type:
HTTPHost Identifier:
IAMSUiteAgentResource URL:
/soa-infra/**Protection Level:
ExcludedClick Apply to apply the changes.
-
23.9 Upgrading Oracle Access Management Domain Which Also Contains Oracle Adaptive Access Manager
To upgrade the Oracle Access Management domain, complete the following steps:
-
Stop the Oracle Access Management Access Manager Managed Servers on both
IDMHOST1andIDMHOST2. Also, stop the WebLogic Administration Server onIDMHOST1.For more information, see Section 24.1.9, "Stopping the Servers".
-
Upgrade Oracle Platform Security Services (OPSS) by running the WLST command
upgradeOpss()onIDMHOST1. This is required to upgrade the configuration and policy stores of Oracle Access Manager and Oracle Adaptive Access Manager to 11.1.2.3.0.For more information, see Section 24.1.7, "Upgrading Oracle Platform Security Services".
-
Undeploy the
coherence#3.7.1.1library, as it is not shipped with Access Manager 11.1.2.3.0.For information about undeploying coherence#3.7.1.1 library, see Section 8.8, "Undeploying coherence#3.7.1.1 Library".
-
Restart the WebLogic Administration Server and the Access Manager Managed Servers on
IDMHOST1andIDMHOST2. -
Upgrade the Oracle Access Management system configuration by running the
upgradeConfig()command onIDMHOST1.For more information, see Section 8.10, "Upgrading System Configuration".
-
Extend the Oracle Access Management domain to include Oracle Mobile Security Suite and Policy Manager. Using the functionality of Oracle Mobile Security Suite is optional. However, you must perform this step to enable the Policy Manager.
For more information, see Section 24.3.1, "Extending the 11.1.2.3.0 Access Manager Domain to Include Mobile Security Suite and Policy Manager".
Note:
To start using the features of Oracle Mobile Security Suite, you must enable Oracle Mobile Security Suite as described in Section 24.3.2, "Enabling Oracle Mobile Security Suite". -
Start the WebLogic Administration Server on
IDMHOST1, and the Oracle Access Manager Managed Servers on bothIDMHOST1andIDMHOST2. If you have configured Oracle Adaptive Access Manager, you must start the Oracle Adaptive Access Manager Managed Servers on bothIDMHOST1andIDMHOST2.For more information, see Section 24.1.8, "Starting the Servers".
-
Perform the required post-upgrade tasks for Oracle Access Management as described in Performing the Required Post-Upgrade Tasks.
-
Redeploy the Oracle Adaptive Access Manager applications on Oracle Adaptive Access Manager 11.1.2.3.0 Server.
For more information, see Section 9.10, "Redeploying Oracle Adaptive Access Manager Applications".
23.10 Seeding the Oracle Identity Manager 11.1.2.3.0 Resources in Oracle Access Management
This step is required only if you upgraded Oracle Identity Manager domain before upgrading Oracle Access Management domain.
Note:
If you upgraded Oracle Access Management domain prior to upgrading Oracle Identity Manager domain, skip this task.If Oracle Identity Manager domain is upgraded first, then you must seed the Oracle Identity Manager 11.1.2.3.0 resources in Oracle Access Management, after upgrading Oracle Access Management domain. To do this, you must run the idmConfigTool -configOIM command.
For information about running the -configOIM command, see "configOIM Command" in the Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite.
Note:
- In the 11.1.2.3.0 property file for
-configOIM, ensure that the value specified for the attributeIDSTORE_WLSADMINUSERis the user who has access to the Oracle Access Management console (oamconsole).For example:
IDSTORE_WLSADMINUSER:oamAdminUser -
Ensure that the values specified for various attributes in the 11.1.2.3.0 property file for
-configOIMis same as the values provided when you ran-configOIMin the base environment (11g Release 2 (11.1.2.1.0)). -
The following are the newly added properties for
-configOIMproperty file in 11.1.2.3.0:IDSTORE_WLSADMINUSEROIM_MSM_REST_SERVER_URL
After you successfully run the -configOIM command, restart all the servers in IDMDomain and OIMDomain on both IDMHOST1 and IDMHOST2.
23.11 Verifying the Upgraded Environment
Verify the upgraded environment by completing the following steps:
-
Verify the Oracle Identity Manager upgrade by completing the steps described in Section 10.8, "Verifying the Oracle Identity Manager Upgrade".
-
Verify the Oracle Access Management upgrade by completing the steps described in Section 8.14, "Verifying the Oracle Access Management Upgrade".
-
Verify the Oracle Adaptive Access Manager upgrade by completing the steps described in Section 9.12, "Verifying the Oracle Adaptive Access Manager Upgrade".
23.12 Troubleshooting
If you encounter any issue during upgrade, refer to the following sections:
-
For issues and workaround specific to Oracle Identity Manager upgrade, see Section 25.1, "Troubleshooting Oracle Identity Manager Upgrade Issues".
-
For issues and workaround specific to Oracle Access Management upgrade, see Section 25.2, "Troubleshooting Oracle Access Management Upgrade Issues".
-
For the list of known issues related to upgrade, and their workaround, see "Upgrade and Migration Issues for Oracle Identity and Access Management" in the Oracle Fusion Middleware Release Notes for Identity Management.