2 Using the Administrative Console to Configure Logon Manager
This section describes the procedures and settings in the Administrative Console, and how to use them to configure repositories, connections, and Logon Manager for your end-users.
In this chapter, you will learn about the following:
-
Section 2.3, "Considerations Before Deploying Logon Manager"
-
Section 2.16, "Configuring Logon Manager for Specific Environments"
-
Section 2.17, "Configuring the Agent with Global Agent Settings"
2.1 Overview
Logon Manager uses a patented process for detecting requests for credentials, analyzing the response necessary, responding reliably, logging events, and administering settings.
2.1.1 Architecture/Modules
The Logon Manager component architecture provides maximum flexibility to meet your organization's needs.
The Logon Manager architecture consists of seven areas:
In addition, administration is facilitated by the Administrative Console.
2.1.1.1 Authentication
Authentication is how the system validates users to gain access to Logon Manager. It consists of three layers:
-
The authenticator itself
-
The authentication service
-
The Logon Manager Authenticator API
After the system validates the user, it passes the users validation information to the core shell.
Logon Manager ships with these authenticators:
-
Windows Domain (same password used to log on to the network (deprecated as of version 11.1.2)
-
Windows Authentication v2
-
LDAP Directory Server
-
LDAP Directory Server v2
-
Authentication Manager
-
Entrust Entelligence
-
Proximity Card
-
Read-Only Smart Card
-
RSA SecurID
-
Smart Card
You determine which authenticators to support, which to install on each computer, and which to enable for each user. (Default: Windows Domain installs.)
For details, see Configuring the Agent for Windows Authentication.
2.1.1.2 Encryption
Encryption secures user credentials in the data store. The Agent requests that credentials be encrypted/decrypted based on the appropriate Crypto Library algorithm. The Agent automatically migrates credentials to a new algorithm/strength (for example, from Triple-DES to AES).
Logon Manager supports a variety of encryption algorithms and algorithm strengths to suit your corporate, legal, security, performance, and other requirements. The product ships with these popular algorithms:
-
AES (MS CAPI) (Default)
-
Cobra 128-bit (deprecated)
-
Blowfish 448-bit (deprecated)
-
Triple-DES 168-bit (deprecated)
-
AES 256-bit (deprecated)
-
Triple-DES (MS CAPI) (ALL OSs) (deprecated)
-
Triple-DES (MS CAPI) (XP/2003 only) (deprecated)
-
RC-4 (MS CAPI) (ALL OSs) (deprecated)
-
RC-4 (MS CAPI) (XP/2003 only) (deprecated)
Other algorithms can work as encryption modules.
You determine which encryption algorithms a user can use and which encryption new/modified credentials should use.
Note:
As of version 11.1.2, all encryption algorithms are being deprecated in favor of AES (MS CAPI). Other algorithms are listed for upgrade scenarios only.For details on setting the default algorithm and strength, see the Global Agent Security Settings.
2.1.1.3 Intelligent Agent Response
When an application presents a request for credentials, the Agent detects this event, determines the appropriate action, and responds with the correct credentials. The interface that performs these evaluations is the Intelligent Agent Response. It interfaces with Access Manager to supply the proper credentials to each application. Access Manager acquires the credentials from the Shell.
Windows support installs automatically. You determine whether to install support for Web and/or Host applications. (Default: All modules install, but Host support is disabled.) Logon Manager supports many host emulators. You determine which, if any, the Agent will recognize. (Default: The Agent works with all supported emulators but requires emulator configuration for some emulators.) Oracle recommends that you configure host emulators to work with the Agent before deploying Logon Manager.
For more information on adding additional application configurations, see Creating and Using Templates. For more information on host emulators, see Section 7.2.4, "Configuring Host Emulators."
Logon Manager ships with the configuration information for popular applications built in. It can work with its default installation settings; however, you have the flexibility to tailor its functionality to the specific needs of any organization. Some of the most commonly-customized functions are:
-
Application Templates, which improve usability by letting users select from a predefined logon list. Applications include Windows applications, host applications, and Web applications.
-
Mobility Support, to provide location transparency and automatic backup and restore.
-
Event Logging, which enables Logon Manager to log various events such as logons, password changes, and so on.
-
First-time use, which customize the user setup process to meet an organizations needs and improve usability.
-
Password policies, which propagate enterprise security policies, improve security, and (when automated) improve usability.
-
Logon Manager settings, which control the UI, implement security, enable, disable, and configure features, and more.
Each of these customization decisions impacts multiple stages of planning, deployment, use, and management.
2.1.1.4 Core (Including Storage)
Using your preferred encryption algorithm, the Agent encrypts and stores user credentials locally in the encrypted Local Credential Storage; it never maintains credentials unencrypted on disk or in memory. The credentials are stored in a user-specific secure database file. Within this file are the encrypted records for each set of user credentials, user settings, and additional configuration information.
2.1.1.5 Credential Synchronization
While the Agent stores user credentials and settings locally, it can synchronize the credentials and settings with remote file systems, directories, databases, devices, and so on. Synchronization can be of the entire user database file (which contains all user credentials) or of individual records within the database. The synchronization is triggered by a change to the Local Credential Storage or settings. Synchronization can be extended to any storage mechanism via the Synchronization API.
Agent administration is fully supported via the Synchronization component and allows the administrator to dynamically deliver updated settings and configuration data to the Agent through the central storage mechanism.
The Agent works with a variety of synchronization extensions, providing users access to their credentials from any desktop, and includes the following:
-
Microsoft Active Directory
-
Microsoft Active Directory Lightweight Directory Services (AD LDS), formerly Microsoft Active Directory Application Mode (ADAM), hereafter referred to as Microsoft AD LDS (ADAM)
-
Lightweight Directory Access Protocol (LDAP)
-
Database
-
File System
Logon Manager supports the most popular LDAP-compliant directory servers, including:
-
Oracle Directory Server Enterprise Edition
-
Oracle Internet Directory
-
Oracle Unified Directory
-
Oracle Virtual Directory
-
IBM Tivoli Directory Server
-
Microsoft Active Directory Server
-
Novell eDirectory
-
OpenLDAP Directory server
-
SQL-compliant relational database system, including:
-
Oracle Database
-
Microsoft SQL Server
-
IBM DB2
Note:
For information about required and supported versions, see the product certification matrix. -
Logon Manager also includes a synchronizer extension supporting a file system, such as can be found on a remote network drive share.
You determine which synchronization modules to install on each computer, which modules to enable for each user, and how to configure each extension. (Default: The synchronizer module installs but no synchronization extensions install.) See the following sections for more information about each feature:
2.1.1.6 Event Logging
When notified by the Shell, the Agent can log all SSO system events, including credential use, credential changes, global credential events, Agent events, and Agent feature use. The Agent can also log specified fields. Events can be logged locally or to any external destination through the Event Logging API. These destinations can include an SNMP service, a Windows server (for viewing via the Windows Event log), or even a local XML log file for simplified parsing and reporting.
The Agent can log all events through its Event Logging API.
Logon Manager works with a variety of Event Logging extensions and includes two Event Logging extensions writing to both local and remote servers:
-
Local File extension, to an XML file
-
Windows Event Logging extension, to a Windows Event Logging server
-
Logging events to a database
-
Logging events to a Syslog server
Oracle may release additional extensions (for example, Oracle and SNMP), and you can easily write your own extensions.
You determine which Event Logging modules to install on each computer, which modules to enable for each user, how to configure the extensions, how frequently the Agent writes to these extensions, how much data the Agent caches, where the Agent writes the log, and more. (Default: No Event Logging modules install, and no logging occurs)
See Event Logging for details.
2.1.1.7 Miscellaneous Components
Logon Manager also contains the following miscellaneous modules:
-
Backup/Restore. For users who do not perform any Credential Synchronization, the Backup/Restore component enables archiving and restoration of user credentials.
-
Citrix and Windows Terminal Services Tools. For environments that require using the Agent within a Citrix Server or Windows Terminal Services environment, additional components are supplied to allow Logon Manager to interact appropriately within each session.
-
Installer Package. Logon Manager ships within a Windows Installer package that supports the flexibility of that technology for easier deployment and customization.
2.1.2 Common Scenarios
-
First-Time Use. The Agent can prompt the user for current credentials for predefined applications. You determine which, if any, credentials to request. (Default: The Agent does not request credentials for any applications.)
For more information, see Bulk-Adding Applications for First-Time Use.
-
User Work Modes. Logon Manager supports work modes ranging from One Workstation, One or Multiple Users to Frequent Movement Among Many Workstations and from always-connected to frequently-disconnected.
For more information, see User Work Modes.
-
Usability vs. Security. Logon Manager lets you choose the balance between usability and security that is appropriate for your organization. The default configuration guarantees your enterprise is secure, but you have the flexibility to adjust these settings as you need. See the Oracle Enterprise Single Sign-On Suite Secure Deployment Guide for a complete discussion of Oracle's security recommendations.
For more information, see Global Agent Settings for User Experience.
-
Packaging/Distribution/Installation. Logon Manager supports most deployment tools and methods. You determine which components deploy to which desktops.
For more information on deployment, see Deploying Logon Manager.
2.1.3 Resources
Logon Manager stores all program files, settings, and data in the following places:
-
The
%ProgramFiles%\Passlogix\v-GO SSOdirectory contains Logon Manager program files. (Default:C:\Program Files\Passlogix\Logon Manager). -
The
%ProgramFiles%\Passlogix\v-GO SSO\Consoledirectory contains Administrative Console program files. (Default:C:\Program Files\Passlogix\v-GO SSO\Console). -
The
%ProgramFiles%\Passlogix\SSO File Sync Servicedirectory contains SSO File Sync Service program files. (Default:C:\Program Files\Passlogix\SSO File Sync Service). -
The
%AppData%\Passlogixdirectory contains user data files. (Default: depends on OS; Windows 7:C:\Users\%Username%\AppData\Roaming\Passlogix). -
The
HKCUregistry tree stores user default settings. -
The
HKEY_LOCAL_MACHINE\SOFTWARE\Passlogixregistry tree stores overriding setting (settings that override user settings) and Logon Manager defaults. -
The
vGOLocatorobjects on a directory server point Logon Manager to where each users' credentials are stored (invGOConfigobject). -
The
vGOConfigobjects on directory servers and similar objects on File Systems store overriding settings and user data.Note:
Settings invGOConfigobjects override registry settings.vGOConfigis the default name, but this file can have any name.
2.2 Logon Manager Features
Logon Manager supports your enterprise users' secure single sign-on requirements with the following key features:
| Feature | Benefits |
|---|---|
| Single Sign-On | Requires one password to log on to networks, applications, and Web sites. |
| Authenticator Choice | Authenticate using a Windows logon or LDAP Directory Server logon. Logon Manager accepts strong authenticators for its primary authentication - including smart cards.) |
| Mobility Support | Users can log on from any workstation and use their Logon Manager credentials via directory servers, database systems, file systems, and Windows Roaming Profiles. (Logon Manager users can log on using smart cards.) |
| Workstation Sharing | Multiple users can share the same workstation securely using Kiosk Manager. |
| Automated Password Change | Users can choose a new password or the Agent can select one automatically using approved password rules (Password Policies). |
| Strong Authentication | Soft-token based, two-factor authentication protects against unauthorized access. |
| Event Logging | Automatically log events such as logons, password changes, and so on. |
| Auto Prompt | Automatically prompts users to configure logons when they encounter a new password-protected application. |
| Credential Sharing | Multiple applications can share the same credentials. |
| Central Administration | All configurations and settings are centrally manageable through the Administrative Console. |
| Automatic Backup/Restore | Automatically back up user credentials to a remote location including a directory server, relational database, or file system, and automatically restore user credentials after a system crash. |
| User Configuration of Logons | In addition to logons predefined by the administrator, users can add individual logons that they may have to other applications and Web sites. |
| Customization | Many aspects of the user experience, including user setup, are customizable to tailor the product to the security needs of the organization and technical sophistication of the user population. |
| Secure Architecture | The Agent is designed to be highly secure, including allowing the Administrator to prevent revealing of any passwords, calling modern encryption algorithms, and using tamper-resistant modules. |
2.3 Considerations Before Deploying Logon Manager
The topics in this section discuss important concepts and considerations regarding the deployment and administration of Logon Manager.
| Concept | Purpose |
|---|---|
| User Work Modes | Understanding the different ways to set up the Agent side of supporting users working in different configurations, and how to optimize your configuration for each set of scenarios. |
| System Configuration | Understanding the different ways to set up the server side of supporting users working in different configurations, and how to optimize your configuration for each set of scenarios. |
| Software Rollout Basics | Understanding the process and issues surrounding rolling out Logon Manager to an organization. |
| Administration and Management | Understanding the post-rollout issues for Logon Manager deployments. |
2.3.1 User Work Modes
Users access their computers in a variety of work modes:
-
Some users are always at a given workstation and are the sole user.
-
Some users move frequently among a limited number of workstations (for example, nurses in a department) or move to a different workstation every day or few hours (for example, a call center).
-
Multiple users may share a single workstation, for example, in shifts. Such a workstation may be used as a kiosk, that is, by multiple users who log on on using a smart card or other token.
-
Some users are not always connected to the network.
Logon Manager supports all these scenarios and can be optimized for each user's most common scenario. (Default: Users are always at a given workstation, but share with others.)
2.3.1.1 One Workstation, One User
When users are always at a given workstation, their credentials can be backed up to a remote location using an SSO synchronizer extension. See Synchronization for more information.
Alternately, the Backup/Restore facility module can store credentials on the workstation without the use of a remote repository. The Backup/Restore module is not installed by default. Users can perform backups manually, or the backup can be automated. See File-Based Backup/Restore for more information.
2.3.1.2 Frequent Movement Among Few Workstations
When users move frequently among a few workstations, but are always on those few workstations, you have two basic options for supporting their Logon Manager credentials.
The recommended option is to utilize a remote SSO repository. Both starting the Agent and any change to credentials force a record-level comparison (synchronization) of all records, ensuring that the user always has the most current credentials possible.
One other option is to configure Automatic Backup to a network file share. With proper configuration, the Agent will perform a silent backup to a remote store (network drive) with each change of credentials (Refresh Task). When the Agent first starts, it will see if the remote store is newer than the local store; if so, it will perform a silent restore; either way, the user will have the current credentials. Because this is a file-level (as opposed to record-level) comparison, this option is not safe if the user logs onto more than one computer at the same time.
2.3.1.3 Frequent Movement Among Many Workstations
When users move frequently among many workstations, you have two basic options for supporting their credentials.
The recommended option is to utilize a remote SSO synchronization repository. Both starting the Agent and any change to credentials force a record-level comparison (synchronization) of all records, ensuring that the user always has the most current credentials possible. In addition, to increase security and to reduce disk space use, enable the o increase security and to reduce disk space use, enable the Delete Local Cache (on Shutdown) option in Global Agent Synchronization Settings.
Alternately, if your Windows environment is already set up with Windows Roaming Profiles, user data is automatically available to the user since it is included in the %AppData% file directory. However, due to the bandwidth-intensive nature of Windows Roaming Profiles, it is not recommended for use with SSO credentials.
2.3.1.4 One Workstation, Many Users
A single workstation may be accessed by a number of users, such as a kiosk. A smart card (or other token) and a PIN can be used to log on to a kiosk (Authentication Manager only). To enable these users' access to the remote SSO repository the ssoSCDetect utility can be used to start the Logon Manager Agent and prompt for primary logon whenever a smart card is inserted in the reader. When the card is removed, the user is automatically logged out of the Agent. See Section 7.2.9, "Smart Card Monitor Utility (ssoSCDetect.exe)" for more information.
2.3.1.5 Disconnected
When users use laptops or are in remote locations, they often stay disconnected from the network for long periods of time.
The Logon Manager Agent stores credentials locally, providing full independence for mobile users who cannot rely on a network connection. Logon Manager modules like Storing User Credentials and Settings (see Storing Credentials in the User Object) and Event Logging support occasional reconnecting, ensuring reliability.
With File-Based Backup/Restore, users can save their own data to a floppy or zip drive.
The Logon Manager synchronizer extensions are configured for offline users using Synchronization options, including Disconnected Operation (see Global Agent Synchronization Settings).
2.3.1.6 Security Locked Down vs. User Freedom
You can customize Logon Manager to provide the balance of security appropriate to your organization's policies and risk/trust level. For example, some organizations need to insure that a user cannot deny having taken a given action, whereas others are not as security-conscious. See Oracle Enterprise Single Sign-On Suite Secure Deployment Guidelines for a complete discussion of Oracle's security recommendations.
2.3.1.7 Usability: User Flexibility vs. Simplicity
You can customize Logon Manager to provide the balance of usability appropriate to your organization's policies and user skill level. For example, some organizations largely employ users who are confused by all but the simplest user interface, whereas others are staffed by more experienced users and might wish to offer flexibility in their environment.
2.3.1.8 Other Settings
You can customize Logon Manager in many ways, and you can enforce these settings at the user, computer, or group level. (The group level can include the entire enterprise.) See Global Agent Settings in Depth for details.
2.3.1.8.1 Mobility Configuration
Some organizations configure their SSO repository components (directory servers, relational databases, file system share) in a very centralized fashion (for example, all user data store objects under one parent object). Other organizations use a decentralized structure (for example, a parent object for each department, location, level of employee). Each has its advantages and disadvantages, depending on your specific current and future network topology. Below are some general advantages and disadvantages.
| Centralized | |
|---|---|
Advantages
|
Disadvantages
|
| Decentralized | |
|---|---|
Advantages
|
Disadvantages
|
2.3.1.8.2 First-Time Use Scenarios
You can control users first-time use scenario from the Logon Manager repository. Determine your first-time use scenarios and then push the object to the Logon Manager repository. If using a centralized environment, only one object is needed; if using a decentralized environment, you can customize the first-time use scenario configuration to meet each group's needs. See Bulk-Adding Applications for First-Time Use for more information.
2.3.2 System Configuration
You can provide Logon Manager configuration settings to users from the Logon Manager repository. Determine your overriding settings and then push them to an object in the Logon Manager repository. If you are using a centralized environment, only one object is needed, providing ideal top-down security controls; if you are using a decentralized environment, you can customize the settings to meet each group's needs.
2.3.2.1 Application Configurations
You can provide application configurations to users from the Logon Manager repository. Determine your application configurations and then push to an object in the Logon Manager repository. If using a centralized environment, you need only one object; if you are using a decentralized environment, you can customize the list of supported applications to meet each groups needs. See Creating and Using Templates for more information.
2.3.3 Software Rollout Basics
You can introduce yourself to Logon Manager by accessing its basic functions; that is, log on to your computer and the Agent provides the logon to all other applications.
To see examples of this, observe the Agent responding to some predefined applications (for example, Microsoft Outlook and Lotus Notes) and some Web sites (for example, Yahoo! and Google.com). Install Logon Manager with its typical configuration and then start these applications.
2.3.4 Administration and Management
After the initial deployment, you can continue managing Logon Manager modules' deployment for updates and upgrades, using the Administrative Console or your own current deployment method.
| Logon Manager Configuration | |
|---|---|
| Directory Servers and Database Systems | Using the Administrative Console, modify the SSOAdminOverride objects. |
| File Systems | Using your current File System administration/management tool or the Administrative Console modify the overriding settings. |
| Local | Using a domain management tool, a deployment tool, RegEdit, and so on, modify the HKLM hive. |
| Application Configuration | |
|---|---|
| Directory Servers and Database Systems | Using the Administrative Console, modify the SSOentlist and (optionally) SSOftulist objects. |
| File Systems | Using the Administrative Console modify the entlist and (optionally) ftulist files. |
| Local | Using the Administrative Console, modify the entlist.ini and (optionally) ftulist.ini files. |
| Settings | |
|---|---|
| Change settings post-rollout | Using the Administrative Console, push overriding settings to the Logon Manager synchronization repository (for example, the directory server, database, file system).
Using a domain management tool, a deployment tool, RegEdit, and so on, deploy registry changes. |
| User Data | |
|---|---|
| Directory Services | Using your current directory administration/management tool, move the user object and (if needed) alter or add an SSOLocator object for the user. |
| File Systems | Using your current network administration/management tool (or even Windows Explorer), move the user file directory tree and (if needed) change the user files' storage location. |
| Local | Using a domain management tool, a deployment tool, RegEdit, and so on, change the user files' storage location. |
| Managing User Credentials | |
|---|---|
| Directory Servers | Deleting User Credentials. Using your current directory administration/management tool, delete the user object from the directory and delete user credentials by using Windows administrative access to delete the %AppData%\Passlogix file from the user's %AppData%\SSO file directory tree on all computers the user accesses.
Moving a user object. Using your current directory administration/management tool, move the user object using the directory administrative tool and (if needed) alter or add an |
| File Systems | Deleting User Credentials. Using your current network administration/management tool or Windows Explorer, delete the user files from the file system and delete user credentials by using Windows administrative access to delete the %UserName% AML.ini file from the user's %AppData%\Passlogix file directory tree on all computers the user accesses. |
| Local | Deleting User Credentials. Using a domain management tool, a deployment tool, Windows Explorer, and so on, delete the %AppData%\Passlogix file from the user's %AppData%\SSO directory on all computers the user accesses. |
2.4 Configuring the Server for Logon Manager
The topics below describe how to configure the server for Logon Manager deployment and support for synchronization, and event logging:
-
LDAP Directory Server Configuration, including:
-
Oracle Internet Directory
-
Oracle Directory Server Enterprise Edition
-
Oracle Unified Directory
-
Oracle Virtual Directory
-
IBM Tivoli Directory Server
-
Microsoft Active Directory and AD LDS (ADAM)
-
Novell eDirectory
-
Open LDAP Directory Server
-
Siemens Dirx
-
-
File Systems Configuration: for any UNC (Universal Naming Convention)-compliant network drive or device
-
Database Synchronization Configuration: for Oracle, Microsoft SQL Server, and IBM DB2 database systems
-
Syslog event logging: requires no special configuration of the Agent
2.4.1 LDAP Directory Server Configuration
This section describes how to extend LDAP directory servers to work with Logon Manager. Although this process simplifies some directory-related tasks, it assumes that the administrator has knowledge of the planning and deployment of directory services. This guide only covers concepts specific to Logon Manager deployments.
See Directory Server Synchronization Support for more information about how Logon Manager makes use of directory server resources. Also see Deploying Logon Manager with a Directory-Based Repository.
Configuring a directory server for Logon Manager entails using the Administrative Console to extend the schema and set up objects in the directory structure (also see Extending the Database Schema).
When you connect to a directory server, you must provide administrator-privileged authentication information. This information includes the directory type, server name or IP address (IP address may not be valid for Microsoft Active Directory Server), port, SSL-use selection, user ID and password.
Your user ID should be in DN format; for example:
uid=yourname,ou=Administrators,ou=TopologyManagement,o=NetscapeRoot
Note:
For AD LDS (ADAM) repositories:The AD LDS (ADAM) server instance must be installed and running before you begin the following procedure.
The naming context for the Application Directory Partition (step 2, below) must be an organization unit (ou). The example given in the AD LDS (ADAM) Setup Wizard panel shows a cn (container name).
-
Extend the directory schema.
Note:
It is considered a good practice to perform a backup of your directory before and after extending the schema. However, it is not necessary to disconnect users to extend the schema, or to reboot the server after the schema is extended. -
From the Repository menu, select Extend Schema.
-
In the Connect to Repository dialog, enter or select the required connection information, then click OK. The Administrative Console binds to the repository, adds attributes and object classes, and confirms successful server configuration.
-
Repeat for each additional server.
-
Create the container object.
A container object, typically named
SSOConfig(classorganizationUnit), holds overriding settings and a container object namedPeople. ThePeoplecontainer object (classorganizationUnit) holds a container object for each user (classSSOUserData, and each of these user container objects holds user credentials and settings (classSSOSecret).Note:
Use the Administrative Console to create container objects with the proper security, create thePeoplecontainer object with the proper security, and place overriding settings with the proper security in thePeoplecontainer object. -
In the left pane of the Administrative Console, right-click Repository and select Connect to from the shortcut menu.
-
Enter or select the required connection information, then click OK.
-
In the right pane, navigate to the container object where you will create the
Peopleobject and overriding settings. -
If necessary, create a new container object:
-
Right-click the parent container object, and select New Container from the shortcut menu.
-
Enter a name for the new container object and select it.
-
Right-click the container object (where the
Peoplecontainer object and overriding settings will exist) and choose Publish to Repository from the shortcut menu (also see Publishing to the Repository). -
Choose the Data Source of the overrides and provide the information requested:
o Administrative Console
o Data File
-
-
When you complete the configuration procedure, the newly-created
Peopleobject and entries for any overriding settings appear in the Repository pane. Right-click on any object and choose Refresh if necessary. -
Repeat this procedure for each additional container object.
-
-
In the left pane of the Administrative Console, right-click Repository and choose Connect To… from the shortcut menu.
-
Enter or select the required connection information, then click OK.
-
In the right pane, navigate to the container object where you will create the
Peopleobject and overriding setting. -
If necessary, create a new container object:
Right-click the parent container object, and choose New Container from the shortcut menu.
Enter a name for the new container object and select it.
-
In the right pane, navigate to the container in which you want to add the locator.
-
Right-click the container and choose Add Locator Object from the shortcut menu (also see Adding a Locator Object).
-
Specify the Locator Name (enter Default for all users unless there is one for a specific user).
-
Navigate to the parent container object of the target
Peoplecontainer object (or specify its path) and click OK. The newly-createdSSOLocatorobject appears with the name you specified. Right-click any object and choose Refresh if necessary. -
Repeat for each additional
SSOLocatorobject.
Note:
As described in Directory Structure, Logon Manager looks for anSSOLocatorobject when it connects to the Directory Server, which points to where the Agent can store user credentials. An object namedDefaultis required somewhere in the tree. You can create specificSSOLocatorClassobjects for specific users as needed. -
2.4.2 File Systems Configuration
This section describes how to extend File Systems to work with Logon Manager. Although this process simplifies some tasks, it assumes that the administrator has knowledge of the planning and deployment of file system shares. This guide only covers concepts specific to Logon Manager deployments.
Note:
See File System Synchronization Support for more information about how Logon Manager makes use of file system resources.Configuring a File System share for Logon Manager entails using the Administrative Console to set up objects in the directory structure.
Note:
When you connect to a File System, you may need to provide Administrator-privileged authentication information. This information includes the synchronizer extension type, UNC path, user ID, and password.Your user ID should be in domain name format, for example, yourdomain\yourname.
2.4.2.1 Creating the Container Object
A container object is typically a file system share in UNC format, for example:
\\Server\Share
Or it can be a share with a path, for example:
\\Server\Share\Path\subPath
The container object holds overriding settings and a container object named People.
-
The
Peoplecontainer object is a file folder that holds a container object for each user (rights:User=Full; Server\Administrators=Full), -
Each of these user container objects holds a container object named
SSOUserData. -
Each
SSOUserDatacontainer object holds user settings in anSSOSecretDataobject (a file) and container objects for each application credential. -
Each of these container objects contains a user's credentials for one application (a file named
SSOSecretData).
Use the Administrative Console to create container objects with the proper security, to create the People container object with the proper security, and to place overriding settings with the proper security in the People container object.
-
In the left pane of the Administrative Console, right-click Repository and choose Connect To… from the shortcut menu.
-
Enter or select the required connection information, then click OK.
-
In the right pane, navigate to the container object where you will create the
Peopleobject and overriding settings. -
If necessary, create a new container object:
-
Right-click the parent container object, and choose New Container from the shortcut menu.
-
Enter a name for the new container object and select it.
-
-
Right-click the container object (where the
Peoplecontainer object and overriding settings will exist) and choose Publish to Repository from the shortcut menu (also see Publishing to the Repository). -
Choose the Data Source of the overrides and provide the information requested:
-
Administrative Console
-
Data File
-
-
When you complete the configuration procedure, the newly-created
Peopleobject and entries for any overriding settings appear in the Repository pane. Right-click on any object and choose Refresh if necessary. -
Repeat this procedure for each additional container object.
2.4.3 Database Synchronization Configuration
This section describes how to configure a relational database server to work with Logon Manager. It assumes that you have basic knowledge of relational database administration and operation. This guide only covers concepts specific to Logon Manager deployments.
Note:
See Database Synchronization Support for more information about how Logon Manager makes use of database resources.Configuring Logon Manager for database synchronization requires using the Administrative Console to extend the database schema and to create the container objects.
-
Extend the database schema.
Note:
Perform a backup of your database before and after extending the schema.-
Choose Extend Schema from the Repository menu.
-
In the Connect to Repository dialog, enter or select the required connection information, then click OK. You must use administrator-level authentication to connect the Administrative Console to the database server. The Administrative Console connects to the database, creates the necessary objects, and confirms successful configuration.
Note:
For SQL Server, when extending the schema, if the database does not exist, the extend schema function will create the database for you. For IBM DB2 Setup instructions, see IBM DB2 Configuration.
-
-
Repeat for each additional server.
-
Create the container objects.
A container object, typically named SSOConfig, holds a default set of overriding settings and a container object named People. The People container object contains a container object for each user, and each of these user container objects holds user credentials and settings.
Use the Administrative Console to create container objects, to create the People container object, and to place overriding settings with the proper security in the People container object.
-
In the left pane of the Administrative Console, right-click Repository and select Connect To… from the shortcut menu.
-
Enter or select the required connection information, then click OK.
-
In the right pane, navigate to the container object where you will create the
Peopleobject and overriding settings. -
If necessary, create a new container object:
-
Right-click the parent container object, and choose New Container from the shortcut menu.
-
Enter a name for the new container object and select it.
-
-
Right-click the container object (where the
Peoplecontainer object and overriding settings will exist) and choose Publish to Repository from the shortcut menu (also see Publishing to the Repository). -
Choose the Data Source of the overrides and provide the information requested:
-
Data File
-
Administrative Console
-
-
When you complete the configuration procedure, the newly-created
Peopleobject, and entries for any overriding settings, appear in the Repository pane. Right-click on any object and choose Refresh if necessary. -
Repeat this procedure for each additional container object.
2.4.4 IBM DB2 Configuration
To extend the central repository schema for Logon Manager and prepare IBM DB2 as the central repository, follow the steps in this section.
2.4.4.1 IBM DB2 Setup Requirements
-
You must install the IBM DB2 Client on the local machine.
-
The DB2 client must have OLE DB (Object Linking and Embedding Database) support installed and configured. This support provides a set of interfaces that allow applications to uniformly access data stored in different data sources. To install OLE DB support, run the DB2 setup wizard and navigate to Client support > Interfaces > OLE DB Support. See your DB2 documentation for more information.
-
The currently logged-on user (to Windows) who is extending the schema must have the appropriate rights to the database in order to connect to the repository and extend the schema. The DB2 User Account must have "Database Administrator Authority" rights.
-
A DB2 administrator must create a database named "
vGOSSO."Refer to the IBM DB2 instructions for detailed information on any of these instructions.
2.4.4.2 Extending the Database Schema
-
Open the Administrative Console.
-
From the Repository menu, select Extend Schema.
-
From the Connect to Repository menu, enter or select the required IBM DB2 connection information:
-
Server name. Enter the server name.
-
Repository Type. Select DB2 Database.
-
Port. The port number needs to be entered only if it is not the default port (normally 50000). If the port is the default, you can leave this field blank.
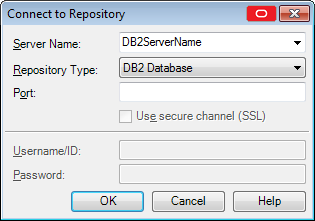
-
-
Click OK.
Note:
You must have administrator-level authentication to connect the Administrative Console to the database server. The Administrative Console connects to the database, creates the necessary objects, and confirms successful configuration.The Extend Schema function uses the following SQL commands to extend the schema:
CREATE SCHEMA vGOSSO;CREATE TABLE vGOSSO.SSO_ADMIN (ConfigType VARCHAR(128) NOT NULL, Data CLOB, PRIMARY KEY(ConfigType));CREATE TABLE vGOSSO.SSO_USERS (UserID VARCHAR(128) NOT NULL, ObjectID VARCHAR(255) NOT NULL, Data CLOB, PRIMARY KEY (UserID, ObjectID)); -
After schema extension, in the DB2 database, grant full rights to SSO_USERS table and its indexes and read-only rights to SSO_ADMIN table and its indexes.
2.4.4.3 Publishing to the Repository
-
In the left pane of the Administrative Console, right-click Repository and select Connect To… from the shortcut menu.
-
Enter or select the required connection information, then click OK.
-
In the right pane, navigate to the root (server name).
-
Right-click on the root and select Publish to Repository from the shortcut menu. The
Peoplecontainer object will already exist under the root. -
Choose the Data Source of the Administrative Overrides and provide the information requested:
-
Administrative Console. Use this wizard page to export an Agent configuration to a selected synchronizer container using the current Administrative Console settings as the source.
-
Data File. Use this wizard page to export an Agent configuration to a selected synchronizer container using one or more data files as the source.
-
-
When you complete the configuration procedure, entries for any overriding settings appear in the Repository pane. Right-click on any object and choose Refresh if necessary.
2.4.4.4 Required Settings for Connecting to IBM DB2 Database
You must set the Required Database Synchronization settings for all database synchronizer extensions.
To add the synchronizer and configure it for IBM DB2:
-
Open the Administrative Console and select a set of Global Agent Settings.
-
Expand Synchronization > DBExt > Required.
-
Enter the following information:
-
Extension location. Make sure this is checked. It is the
path\filenameof the IBM DB2 database synchronizer extension. Default:C:\Program Files\LocalDirectory\v-GO SSO\Plugin\SyncMgr\DBEXT\DBExt.dll) -
Servers. Specify the connection string for the database server in the order to attempt connection for synchronization. Select the checkbox and click the ellipsis ("…") button to open the Edit List dialog. Enter the full connection string for one database server on each line; end each line by pressing Enter. Do not use any other delimiter characters.
Note:
You must specify at least one connection string for the extension to work.To connect to an IBM DB2 database, use the following connection string:
Provider=IBMDADB2;Data Source=vGOSSO;CurrentSchema=vGOSSO;Location= <DB2ServerName>[:port];Extended Properties="trusted_connection=yes";Where
<DB2ServerName>is the name of the server and[:port]is the optional port.
-
-
Expand Synchronization>DBExt>. The Advanced Database Synchronization settings control special-case options for all database synchronizer extensions. This setting is not required.
Append Domain when naming objects enables appending of the user's domain to the username in naming the user's container.
Example: For the domain
companyand useruser1, the container is nameduser1with this flag disabled anduser1.companywith this flag enabled. Default is set to Disable. Select Enable to activate this feature.
2.4.5 Repositories
This section discusses working with repositories that have already been configured for use with Logon Manager. For a full discussion about planning and configuring your repository, see Deploying Logon Manager with a Directory-Based Repository.
2.4.5.1 Displaying and Connecting to a Repository
-
To display an established connection to a synchronization repository:
Click Repository in the left pane to display the current Logon Manager synchronization repository.
-
Or, if no connection is active:
Right-click Repository in the left pane and choose Connect To… from the shortcut menu.
2.4.5.2 Repository Actions and Options
Right-click an object in the Repository window in the right pane to display one of the following shortcut menus of commands and options.
| With a Container Selected | |
|---|---|
| Publish SSO Objects Here | Opens the Publish to Repository dialog, which allows you to publish configuration objects, such as application templates and Agent setting overrides to the repository. |
| Bring Multiple Objects to Console | Displays a list that allows you to select multiple configuration objects that you wish to import into the current Administrative Console settings. |
| Add Locator Object | Create locator objects (directory servers only). |
| Create People Container | Creates the ou=People container used for application credential storage on directory systems other than Microsoft Active Directory. |
| New Container | Create a new container within the selected container. |
| Delete | Remove a container and all objects within. |
| Refresh | Update the Directory window. |
| Filter Subnodes… | Opens the Subnodes Filtering Options dialog, which allows you to refine the criteria that the Administrative Console uses to display the subnodes of the repository. |
| With an Override Object Selected | |
|---|---|
| Configure | Create Administrative Override objects from Administrative Console settings or a data file. |
| View | Quickly view the selected object, with an option to save it to an INI file. |
| Bring to Console | Import the object to the current Administrative Console settings.
|
| Save as File | Save the object to a local INI file. |
| Delete | Remove the object from the repository. |
2.4.5.3 Add User or Group (for Active Directory Role/Group Support)
Use this dialog to select the individual users or user groups to add to the access list for the current configuration item (application logon, password policy, Global Agent Settings, or passphrase set).
| Controls | |
|---|---|
| List Names From | Select an Active Directory domain or server. |
| Names | Lists the names of users and groups for the selected domain or server. Select one or more names to add to the access list. |
| Add | Copies user(s) and group(s) selected in the Names list to the Add Names list. Use Ctrl+click or Shift+click to select multiple entries. |
| Members | When a group is selected, the Names list displays the Global Group Membership dialog, which lists the members of the selected group. |
| Search | Displays the Find Account dialog for searching one or more domains for a specific user or group. |
| Add Names | Display the names of the user(s) or group(s) that you have already selected. Click OK to add these names to the access list for the current configuration item.
Note: You can type or edit user names in this list. However, your entries are checked for invalid account names, and duplicate account selections are automatically removed when you click OK. |
2.4.5.4 Viewing Global Group Membership (for AD Role/Group Support)
The Global Group Membership dialog lists the members of a group selected in the Add User or Group dialog. Use this dialog to select the individual members to add to the access-control list for the current configuration item. (Use Ctrl+click or Shift+click to select multiple entries). Click Add to copy the selected names to the Add Names list in the Add User or Group dialog.
2.4.5.5 Searching for Specific Users or Groups (for AD Role/Group Support)
Use the Find Account dialog to search for a specific individual user account or user group in a specific domain or across multiple domains, then add any or all of the search results to the access-control list for the current configuration item (application logon, password policy, Global Agent Settings or passphrase set).
| Search for names | |
|---|---|
| Find a User or Group | Enter the name of a user or group to search for. Only exact user/group name matches are allowed. |
| Search All/Search Only in | Search all available domains (displayed in the list box below) or select specific domains to search. Use Ctrl+click or Shift+click to select multiple entries. |
| Search | Begin searching for the user/group name. |
| Add results to list | |
|---|---|
| Search Results | Lists the user and group accounts that match the search criteria. |
| Add | Add user(s) and group(s) selected in the Search Results list to the Add Names list in the Add User or Group dialog. Use Ctrl+click or Shift+click to select multiple entries. |
2.4.5.6 Adding Users or Groups (for LDAP Role/Group Support)
Use this dialog to select the individual users or user groups that are to be added to the access list for the current configuration item (application logon, password policy, Global Agent Settings or passphrase set).
| Controls | |
|---|---|
| Search Base | The base (highest-level) directory to begin searching for user/group accounts. All subdirectories of the base directory are searched. Enter a location or click Change to browse the directory tree. |
| Change | Displays the Select Search Base dialog to browse for a base directory for the search. |
| Search | Begin searching the base directory for users and groups. |
| Users and Groups | Lists the search results. Select the names to be added to the access list for the current configuration item. Use Ctrl+click or Shift+click to select multiple entries. Click OK when finished to copy your selections to the access list. |
2.4.5.7 Selecting a Search Base (for LDAP Role/Group Support)
Use this dialog to browse to and select the base (highest-level) directory to search for user/group names. Click OK when finished to return to the Select Users or Groups dialog.
2.4.5.8 Browsing for a Repository
This dialog allows you to navigate to a specific target repository container within the currently connected directory server's hierarchy. It also allows you to connect to a different server, if necessary.
To select the target repository container:
-
(Optional) If the directory server to which the Administrative Console is currently connected is not the desired target server, click Change Server, fill in the connection information, and click OK to connect to the desired server.
-
In the directory tree, navigate to and select the target container.
-
Click OK.
2.4.5.9 Connecting to the Repository
To connect the Administrative Console to a synchronization repository:
-
Right-click Repository and select Connect To… from the shortcut menu.
-
Enter or select the required connection information, then click OK.
2.4.5.10 Connection Controls
| Menu Option | Description |
|---|---|
| SyncPath or Server Name | Either:
Note: Select Edit List to remove directories/servers from the drop-down list. For SQL Server, if the database server is the only instance on the computer that you are connecting to, then enter the computer name only. If there is more than one database server instance on the target computer, then enter the full connection address ( You must specify a file system server as a UNC path, not as a drive-letter and directory path. For example: |
| Repository Type | Select File System Sync, a directory service, or a database server from the drop-down list.
If you select OpenLDAP Directory Server, and an Extend Schema Status error appears, extend the schema manually |
| Port | (Directory server only) Enter the port number. |
| Database | (Database server only) The name of the database to connect to; enter the name of an existing database (default vGOSSO). |
| Use secure channel (SSL) | Select to enable secure socket layer (directory server only). |
| User ID | Enter your username. |
| Password | Enter your password. |
2.4.5.11 Creating a New Container
Use the New Container prompt to name a new container object at the selected node in the current repository.
To name a new container, enter a container name, then click OK.
See Repositories for more information.
2.4.5.12 Editing a Server List
Use this dialog to remove servers that are listed in the Server Name drop-down list on the Connect to Repository dialog. Select a server and click Delete. Click OK when finished.
2.4.5.13 Editing a Repository List
The dialog, Select Objects to Bring to Console, displays the list of most recently used target repositories and allows you to delete unwanted entries from the list.
To delete an unwanted entry from the list:
-
Select the entry in the list.
-
Click Delete.
-
Repeat steps 1-2 for any other unwanted list entries.
-
When you have finished, click OK.
2.4.5.14 Subnodes Filtering Options
The subnodes filtering settings control the number of items that display in repository trees. Using filtering, you can refine the criteria that the Administrative Console uses to display the subnodes of these trees, so that they display more manageable results.
You can limit displayed subnodes in two ways:
-
Filter list. Uses the asterisk (*) and question mark (?) wild cards.
The wildcard filter is node-specific. You can use a different wildcard for each node that you want to filter. The wildcard filter is discarded when you switch repository nodes and expires at the end of the Administrative Console session.
-
Truncate list. Limits the number of nodes to display.
Specify a threshold for the maximum number of child nodes to display in a tree. This number governs all repository nodes and remains in effect between Administrative Console sessions. The minimum value is 1; the maximum value is 65,535; and the default value is 1,000. This means that the Administrative Console will display no more than 1,000 entries in a subnode unless you configure it differently.
If you enter a value less than the minimum or greater than the maximum allowable values, Administrative Console uses whichever limit is closer.
To filter a subnode:
-
Connect to a repository.
-
Right-click on a node in the repository and select Filter Subnodes…
-
In the Subnodes Filtering Options dialog, do either or both of the following:
-
In the Filter List field, enter a wildcard expression.
-
In the Truncate list field, select the maximum number of nodes to display. The maximum number that you can specify is 65,535. The default is 1,000.
-
-
Click OK.
-
Expand the subnode to view the results.
2.4.5.15 Working with Filtered Subnodes
The icon of a filtered subnode contains an F next to its standard icon to indicate a filtered state:
If you choose to expand a node containing a number of subnodes greater than the threshold that you set in the Truncate list setting, the Subnodes Filtering Options dialog appears, displaying the following:
Warning: The number of items to be displayed is XXXX (the number you specified), which exceeds the limit defined below.
Click OK to expand the subnode using the limit that you previously set, or change the maximum number of nodes to accommodate the list, and then click OK.If you did not set a threshold for this subnode, the Administrative Console uses the system default of 1,000.
2.4.5.16 Importing Multiple Objects to the Administrative Console
The Bring Multiple Objects to Console dialog displays, in a flat list, all objects residing in the selected container and all of its child containers, and allows you to select multiple objects for import to the current Administrative Console settings
To select multiple objects from the list and bring them to the Administrative Console:
-
Ctrl+click each desired object.
or
-
Shift+click the first and last objects in the desired range.
-
Click OK.
2.4.5.17 Publish to Repository
This screen allows you to publish configuration objects of your choice to the selected target container, either in a directory-style hierarchy (default), or as a flat configuration file.
Note:
For considerations when publishing an Exclusion list, refer to Working with User Exclusions.To select and publish the desired objects to the repository:
-
Do one of the following:
-
From the tree, right-click on the configuration object that you want to publish, and select Publish or Publish To….
or
-
Select a configuration object from the tree and select Tools > Publish to Repository.
-
-
In the Available configuration objects list of the Publish to Repository dialog, navigate to and select the desired objects.
Note:
Only categories for which objects have been configured will appear in this list. For example, if no password generation policies exist, the corresponding category will not appear in this list. -
Click >> to move the selected objects to the Selected objects to be published list. (To remove an object from this list and not publish it, select the object and click <<.)
-
(Optional) If you did not invoke the Publish SSO Objects Here command by right-clicking on the target container, select the desired container from the Target repository drop-down list.
Note:
If the target container path does not appear in the list, click Browse to find and select the desired container.To remove unwanted entries from this list, select the Edit list option from the list.
-
(Optional) If your environment calls for storing configuration objects in flat-format, check the box, Store selected items in configuration files, rather than as individual objects.
Note:
Selecting this option will overwrite all items stored in existing configuration files, if present, in the target container. -
(Optional) If you want to create the first-time-use object (
FTUList), select the corresponding check box.Note:
This option only becomes active if you choose to store your configuration objects in flat format in step 4. -
Click Publish. The Administrative Console publishes the selected objects to the target repository.
Note:
Do not attempt to dismiss the dialog or close the Administrative Console until the publishing process completes. The dialog disappears automatically when the objects have been published.To quickly publish an object or a group of objects, select it in the left-hand tree, right-click it, and select Publish (single objects and groups) or Publish To (single objects only) from the context-menu.
This will invoke the Publish to Repository dialog and automatically add the object(s) to the list of objects to be published. Keep in mind that:
-
If you select the Publish option, the Publish to Repository dialog appears.
-
If you select the Publish To option and select a repository, the selected object is automatically published to that repository and the Publish to Repository dialog is not displayed. (If you are not currently connected to the selected repository, you will be prompted to authenticate to the directory server.)
-
2.4.5.18 Publishing to the Repository from the Administrative Console
Use this window to export an Agent configuration to a selected synchronizer container using the current Administrative Console settings as the source. You can export:
-
One or more application logons
-
A first-time use (bulk-add) object
-
A set of Global Agent Settings
2.4.5.19 Exporting Administrative Overrides from the Administrative Console
To export administrative overrides from the Administrative Console:
-
Do one of the following:
-
Select Send All Applications.
or
-
Select Send Some Applications, then:
-
Click Select Apps.
or
-
From the Select Applications dialog, select the applications to send, and click OK.
-
Choose Send No Apps.
-
-
Optionally, select Create First-Time-Use (FTUList) object.
-
Optionally, choose a set of Global Agent Settings from the Admin Overrides drop-down list.
-
Select Next. The wizard displays a summary of the Override configuration.
-
Select Finish to complete the export.
2.4.5.20 Displaying the Publish to Repository Window
-
Connect to the Logon Manager repository.
-
In the right pane, right-click a container object and select Publish to Repository from the shortcut menu to open the Publish to Repository dialog.
-
Select Administrative Console.
2.4.5.21 Publishing to the Repository from a Data File
Use this window to export an Agent configuration to a selected synchronizer container using one or more data files as the source. You can export:
-
One or more application logons.
-
A first-time use (bulk-add) object.
-
A set of Global Agent Settings (from an
.inior.regfile).
Note:
The Console produces a.REG file compatible only with 32-bit systems. If you are merging the.REG file on a 64-bit system, you must run the following command to move the merged registry data to the correct location within the registry (otherwise, Universal Authentication Manager will not function):
reg.exe COPY HKLM\Software\Passlogix HKLM\Software\Wow6432Node\Passlogix /s
2.4.5.22 Exporting Administrative Overrides from Data Files
-
Enter the file names (or select Browse to select a data file) as the source for each administrative override object you want to export. You can export:
-
First-Time Use (from an
ftulist.inifile). -
Administrative overrides (from a valid
INIorREGfile). -
Applications (from an
entlist.inifile).
-
-
Click Next. The wizard displays a summary of the override configuration.
-
Click Finish to complete the export.
2.4.6 Configuring Logon Manager Support
Use the Publish to Repository dialog to deploy administrative overrides and application configurations to end users using file-system, database, or directory service synchronizers. The objects you can export include:
-
One or more application logons.
-
A first-time use (bulk-add) object.
-
A set of Global Agent Settings.
The Publish to Repository dialog helps you export the overrides, from current Administrative Console settings or from one or more data files, to a selected synchronizer container object.
See Synchronization for more information.
2.4.7 Exporting Administrative Overrides to a Synchronizer Container
-
Connect to the Logon Manager synchronizer repository.
-
In the right pane, right-click a container object and select Publish to Repository from the shortcut menu to open the window.
-
Choose the Data Source of the administrative overrides and provide the information requested:
-
Administrative Console
-
Data File
-
2.4.8 Select Applications, Password Policies, and Session Lists to Publish to Repository
Use the Publish to Repository dialog to select application logons, password policies, and Kiosk Manager lists from the current Administrative Console session to deploy to the current synchronization repository. You can choose all applications and policies, select applications and policies individually, or remove items from either list. When your selection is complete, select Next to continue.
| Lists | Definitions |
|---|---|
| Applications | Lists the application logon configurations to be deployed. |
| Password Generation Policies | Lists the password policies to be deployed. |
| Kiosk Manager Application List | Lists the Kiosk Manager applications lists to be deployed. |
2.4.9 Selecting Global Agent Settings to Publish to Repository
Use the Publish to Repository dialog to select a set of Global Agent Settings from the current Administrative Console session to deploy to the current Logon Manager synchronization repository.
-
From the list, select a set of Global Agent Settings.
-
Select Next to continue.
2.4.10 Including Passphrase Questions to Publish to the Repository
Use the Publish to Repository dialog to deploy the passphrase questions from the current Administrative Console session to the current synchronization repository. See Using Passphrase Sets for more information.
| Control | Function |
|---|---|
| Send the Passphrase questions | Select this checkbox to deploy the current set of passphrase questions. Select Next to continue. |
2.4.11 Selecting Role/Group Support Mode When Publishing to a Repository
The Publish to Repository dialog offers the option to apply role/group access control support for Logon Manager configuration information.
If Standard mode (the default) is selected, configuration information is stored on the directory as standard Logon Manager objects: EntList (for logons and policies), FTUList (for bulk-add and passphrase questions), and AdminOverride (global Agent settings).
Select Advanced mode to enable role/group support. All application logons, password policies, global Agent settings, and passphrase question sets are added to the current synchronization repository as individual objects.
| Control | Function |
|---|---|
| Enable Role/Group Support | Select this checkbox to enforce role/group access-control settings for all logons, policies, global Agent settings, and passphrases.
Clear this checkbox to deploy configurations information without enforcing access control. Click Next to continue. |
2.4.12 Configuring Applications for an EntList
Use the Configure Applications dialog to select the application logons to include in an EntList object for synchronization.
-
Do one of the following:
-
Choose Send All Applications.
or
-
Choose Send Some Applications.
Note:
Either of these options overwrites all applications in the selected directory. To create a First-Time-Use list object without overwriting applications in the directory, select Do not send apps.
-
-
Click Select Apps.
-
In the Select Application dialog, select the applications to package and click OK.
-
If desired, select Create First-Time-Use (FTUList) object.
-
Click OK.
To display this dialog for an EntList object, connect to a synchronizer repository, right-click an Entlist object, then select Configure from the shortcut menu.
2.4.13 Adding a Locator Object
Use the Add Locator Object dialog to create a locator—a directory object that points the Agent to the container in which user credentials are (or can be) stored. You can create a default locator for all end users or a locator for a specific end user.
See Create locator objects for more information.
| Control | Function |
|---|---|
| Locator Name | Enter default to create a locator for all users. To create a locator for a specific end user, enter the user's distinguished name. |
| Forwarding Location | Navigate to the container where user credentials are stored and click OK. |
| Store data under the user objects (AD only) | (Active Directory only) Select this checkbox to store the user's credentials (or all users if Locator Name is "default") in the container under the respective user object, rather than in a specific Forwarding Location.
This setting requires updating the directory schema and modifying the directory-root security settings. To do this, use the Enable Storing Credentials under User Object command on the Repository menu. You can use this setting to specify individual users whose credentials are to be stored under their respective User objects. All other user credentials will be stored as specified by the default locator. To store all users' credentials under their respective user objects without using a locator object, use the Enable Storing Credentials under User Object setting (under |
To display this dialog:
-
Connect to the synchronizer directory.
-
In the right pane, select the container in which you want to add the locator.
-
Right-click the container and choose Add Locator Object from the shortcut menu.
2.4.14 View Object
Use this dialog to view the contents of the selected configuration object. To save the object to an INI (text) file, click Save To. See Repositories for more information.
Note:
You can edit the displayed configuration information, but your changes can only be saved to anINI file, not to the object itself.2.5 Synchronization
Synchronizer extensions allow you to synchronize credentials between an end user's local store (on a workstation) and a store in a remote SSO repository (file system share, relational database or directory server). You can also use these extensions to deploy Administrative Overrides of local Agent settings, application logon configurations (overriding entlist.ini and to be merged with applist.ini), and bulk-add lists (overriding ftulist.ini). See Overriding Configuration Objects for more information.
Synchronizer extensions communicate with directory servers, database servers, file systems, and other storage devices. Each type of extension has its own configuration requirements.
2.5.1 Supported Synchronizers
Logon Manager supports the following synchronizer extensions:
-
Microsoft Active Directory Server, including AD LDS (ADAM).
Note:
If users will be synchronizing with an Active Directory or AD LDS (ADAM) repository from outside of the corporate network, you must allow RPC protocol-based connections through the corporate firewall; otherwise, users will be unable to synchronize with the repository. -
LDAP-compliant directory servers, including Oracle Internet Directory, Oracle Directory Server Enterprise Edition, OpenLDAP Directory Server, IBM Tivoli Directory Server, and Novell eDirectory.
-
Relational databases, including Oracle DB, Microsoft SQL Server, and IBM DB2.
-
Network file systems.
Synchronizer extensions are capable of performing the following tasks:
-
Connecting to (or binding with) a destination device/resource/store.
-
Retrieving any overriding settings (administrative overrides, application configuration information, and first-time use configuration information).
-
Synchronizing the local user store (credentials) with the remote store.
Logon Manager supports using each extension multiple times, which allows you to support multiple configurations. For example, if the LDAP Directory Server and File System synchronizer extensions are installed, the Agent will synchronize credentials with, and download overriding settings from, both an LDAP Directory Server and a File System.) See Multiple Synchronizer Extensions for more information.
2.5.2 Directory Server Synchronization Support
The Administrative Console supports any LDAP directory server, including:
-
Oracle Internet Directory
-
Oracle Directory Server Enterprise Edition
-
Oracle Unified Directory
-
Oracle Virtual Directory
-
Open LDAP Directory Server
-
IBM Tivoli Directory Server
-
Microsoft Active Directory
-
Microsoft AD LDS (ADAM)
-
Novell eDirectory
-
Siemens Dirx
Logon Manager uses directory server resources for administrative configuration, mobility, and backup. Administrators can deploy configuration overrides to provide new registry, entlist.ini, and ftulist.ini (bulk-add) settings or to update existing settings. Users can store credentials (for backup) and move among multiple computers (for mobility). When Logon Manager connects to a directory server, it utilizes a specific directory structure to determine where the user's credentials and overriding settings reside.
Note:
Each Directory Server presents platform-specific configuration issues. These are addressed in the individual configuration topics.2.5.3 Directory Structure
Within each directory, Logon Manager utilizes the following object structure:
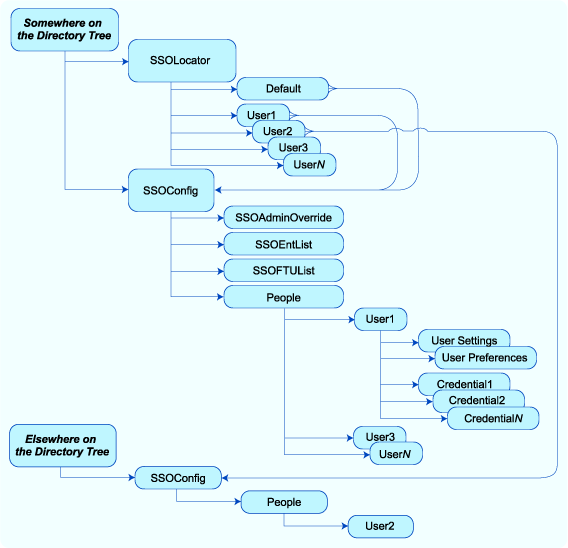
When a user first connects to a directory server, the system is configured to locate a specific path on the directory tree. Using the process described in the next section, the Agent is able to find the SSOConfig object, which contains overriding settings, and a People object, which contains the user's settings, preferences, and credentials.
2.5.4 Finding and Creating User Objects
The Agent must locate the specific object in which to store and retrieve the user's credentials. After the first successful connection, the Agent records the objects DN in the user's registry at:
HKCU\…\Extensions\SyncManager\%Extension%:Root
where %Extension% can be any name as specified in the synchronizer's Global Agent Setting for Sync Order. However, for the first connection from a given workstation, if the user's object is moved, or if the user registry does not contain this information, the Agent must search for the user's object.
Logon Manager uses three methods to search for the proper location to store user credentials on a directory server. Each method looks at the specified distinguished name; the latter two then each walk the directory tree toward the root, to look for a parent object with relevant information.
-
The first method is to look for the user object (
CN=%UserName%,OU=People) in a specified place. -
The second method is to look for a user-specific pointer object (
CN=%UserName%,OU=SSOLocator) to the right place; and if the object is not present, walk the tree until the Agent finds the object or checks the root. -
The third method is to look for a default pointer (
CN=default,OU=SSOLocator) to the right place; and if the object is not present, walk the tree until the Agent finds the pointer to the object or checks the root.
If none of these methods succeeds, the user cannot store credentials on the Directory Server (any existing local credentials will be usable).
Note:
The%UserName% variable is set automatically in Microsoft Active Directory from the users system username/ID. For LDAP Directory Servers, the %UserName% variable is set from the username/ID with which the user performs a bind to the Directory Server.2.5.4.1 Method 1: Logon Manager Looks for the User Object
Logon Manager first looks for the user object, CN=%UserName%, inside an OU=People object, specified by the Root registry key (see above).
If that registry key is set to:
OU=SSOConfig,OU=QA,OU=Eng,OU=Company,DC=com,
then the Agent looks for:
CN=%UserName%,OU=People,OU=SSOConfig,OU=QA,OU=Eng,OU=Company,DC=com.
If the Root registry key is not set, the Agent looks in:
HKLM\…\Extensions\SyncManager\%Extension%
for User Paths (see LDAP Synchronization Settings) or Naming Attribute string (see LDAP Special Purpose Synchronization Settings), which points to where the Agent should look.
For example, if UserPath1 is set to:
CN=users,DC=Company,DC=com
then the Agent looks for:
CN=%UserName%,OU=People,OU=SSOConfig,OU=QA,OU=Eng,OU=Company,DC=com
2.5.4.2 Method 2: Logon Manager Looks for a User Pointer
If the user object is not present, Logon Manager next looks for an SSOLocator object in the same object as the SSOConfig object. Therefore, continuing the example above, the Agent looks for:
CN=%UserName%,OU=SSOLocator,OU=QA,OU=Eng,DC=Company,DC=com
If the user pointer is not present, then the Agent walks the tree, toward the root, looking first in:
CN=%UserName%,OU=SSOLocator,OU=Eng,DC=Company,DC=com
and then
CN=%UserName%,OU=SSOLocator,DC=Company,DC=com
If an SSOLocator object exists with the users CN, it points to where the user's credentials will be stored; the Agent records this information in the user's Root registry key, and future logons look in that location.
Note that the pointer can indicate any location in the Directory Tree; for example, a pointer at:
CN=%UserName%,OU=SSOLocator,OU=Eng,DC=Company,DC=com
can point to a user object at:
CN=%UserName%,OU=People,OU=SSOConfig,OU=Sales,DC=Company,DC=com.
2.5.4.3 Method 3: Logon Manager Looks for a Default Pointer
If a user pointer object is not present, Logon Manager next looks for a default object inside each SSOLocator object. Continuing the example above, the Agent looks for
CN=default,OU=SSOLocator,OU=QA,OU=Eng,DC=Company,DC=com
If an SSOLocator object exists with the CN=default object, it points to where the user's credentials will be stored by default; the Agent records this information in the user's Root registry key, and future logons look in that location. An example of a default object is:
OU=People,OU=SSOConfig,OU=Sales,DC=Company,DC=com.
2.5.5 File System Synchronization Support
The Administrative Console supports file system synchronization with any network drive/device that can be addressed by UNC (Universal Naming Convention). File system synchronization can also be used to support a kiosk user scenario, where multiple users share a single workstation.
2.5.5.1 File System Structure
When a user first connects to the file system, the computer is configured to locate a specific path. The Agent is then directed to find the vGOConfig object, which contains overriding settings and a People object, which contains the user's settings, preferences, and credentials.
2.5.6 Database Synchronization Support
The Administrative Console supports synchronization of user credentials, application logons, and Global Agent Settings between client workstations and a relational database server. Supported servers include Oracle Database, Microsoft SQLServer, and IBM DB2. For a full list of supported servers, see the Oracle certification matrix.
In this type of synchronization, Logon Manager configuration objects and user data containers are stored on the server as database records in Logon Manager-specific tables:
-
SSO_ADMIN stores, as records, the configuration objects you create in the Administrative Console:
-
EntList(application logons),FTUList(Setup Wizard configurations) -
AdminOverride(Global Agent Settings)During synchronization, all workstation users read their logons and overrides from this table; only the administrator, using the Administrative Console, can write to it. These configuration object are depicted in the Administrative Console in the same hierarchal layout as for file system and directory server synchronizers.
-
-
SSO_USERSstores user credentials, preferences, and synchronization states as records. During synchronization, users read and write to their own records. Only the record for the user currently logged on can be accessed. In the Administrative Console, the records for each user are depicted within the user container.When Logon Manager connects to the database server, it reads the configuration objects and overriding settings (from
SSO_ADMIN) and synchronizes the user data (inSSO_USERS).
The procedure for configuring database synchronization is similar to that for other synchronization methods:
-
Extend the database schema to create the two tables described above.
-
Create the container objects:
-
An
SSOConfigobjectThis object contains overriding settings.
-
A
PeopleobjectThis object holds the user containers for each user's settings, preferences, and credentials.
-
2.5.7 Multiple Synchronizer Support
Logon Manager supports synchronizing to multiple synchronizer extensions and multiple configurations of the same extension. In either scenario, the Agent attempts to complete synchronization with the first extension and then with each subsequent extension.
Overriding settings can exist on each extension. See Working with Multiple Sets of Overriding Settings for an explanation of how the Agent handles multiple extensions with overriding settings.
Note:
Instances to%AD%, %LDAP%, and %File% refer to the respective extensions, and %Extension% refers to any of those extensions.2.5.8 Multiple Synchronizer Extensions
Logon Manager supports using multiple synchronizer extensions simultaneously. For example, the Agent could first synchronize with a Microsoft Active Directory Server, then with an Oracle Directory Server Enterprise Edition, and then with the File System synchronizer. With Authentication Manager, the Agent could then synchronize with a smart card.
To enable this:
-
Install Logon Manager with the desired synchronizer extensions.
-
In the Administrative Console, select an existing set of Global Agent Settings or create a new set.
-
In the left pane, expand Global Agent Settings, right-click Synchronization, and select Manage Synchronizers.
-
In the Synchronizers dialog, select Add, name this extension, select the extension type (for example, Active Directory, File System, or LDAP), then click OK.
-
Repeat the previous step for additional synchronizer extensions, and reorder as desired.
-
For each synchronizer: select it in the left pane and confirm in the right pane that Path is selected and the location specified is correct.
Note:
Oracle recommends that you set theDisplayNameregistry entry to help users distinguish between the multiple extensions.
2.5.9 Multiple Configurations of the Same Synchronizer Extension
Logon Manager supports using a given extension with multiple configurations. For example, one LDAP Directory Server configuration could be for an Oracle Directory Server Enterprise Edition, and another LDAP Directory Server configuration could be for Novell eDirectory.
To enable this:
-
Install Logon Manager with the desired synchronizer extensions.
-
In the Administrative Console, select an existing set of Global Agent Settings or create a new set.
-
In the left pane, expand Global Agent Settings, right-click Synchronization, and select Manage Synchronizers.
-
In the Synchronizers dialog, select Add, name this extension, select the extension type LDAP, then click OK.
-
Repeat the previous step for additional synchronizer extensions, and reorder as desired.
-
For each synchronizer: select it in the left pane and confirm in the right pane that Path is selected and the location specified is correct.
Note:
Oracle recommends that you set theDisplayNameregistry entry to help users distinguish between the multiple extensions.
2.5.10 Overriding Configuration Objects
Synchronizer extensions can download overriding configurations for Global Agent Settings (administrative overrides), application configuration information (EntList), and first-time use scenarios (FTUlist). Each of these objects has a local equivalent, as detailed in the following table.
| Settings Type | Local Equivalent | Directory Server/ Database Object Name | File System Object Name |
|---|---|---|---|
| Administrative Overrides | Registry entries under HKLM |
SSOAdminOverride |
AdminOverride |
| Application logon configuration information | The entlist.ini file |
SSOentlist |
entlist |
| First-time-use configuration information (including bulk-add information) | The ftulist.ini file |
SSOftulist |
ftulist |
The latter two types of objects are similar in format and layout to their local equivalents, entlist.ini and ftulist.ini. The first type of object has the following syntax:
[HKLM\Software\Passlogix]
REQUIRED: RegistryPath\RegistryPath:KeyName=TYPE:Value
This format is exported by the Administrative Console.
- Example 1
-
[HKLM\Software\Passlogix] Shell:AutoBackupPath=STRING:\\FS\Home Shell:ShowAccessBtn=DWORD:1 Extensions\AccessManager:ReauthOnReveal=DWORD:0
Note:
In directory server installations, this configuration information can be enabled with support for role group-based access.Certain settings, such as server URLs, must not be overridden and are thus permanently excluded from administrative override objects. See Configuring the Agent with Global Agent Settings for a complete list of entries that are excluded from being overridden.
2.5.11 Working with Multiple Sets of Overriding Settings
The Agent attempts to retrieve each type of overriding settings from each extension until it finds an extension that has at least one of each. After an overriding setting is downloaded, the Agent does not query other extensions for that overriding setting.
2.5.11.1 Sample Scenarios
Example
-
Order: Ext1,Ext2,Ext3,Ext4.
-
Ext1 has Admin Overrides.
-
Ext2 has Admin Overrides, an
entlist.inifile, and an first-time use information file. -
Ext3 has no Admin Overrides.
-
Ext4 has Admin Overrides, and an first-time use information file.
Scenario A
-
Ext1 connects; downloads Admin Overrides; and synchronizes.
-
Ext2 connects; downloads application configuration information and first-time use configuration information; and synchronizes.
-
Ext3 connects and synchronizes.
-
Ext4 connects and synchronizes.
Scenario B
-
Ext1 fails.
-
Ext2 connects; downloads Admin Overrides, application configuration information, and first-time use configuration information; and synchronizes.
-
Ext3 connects and synchronizes.
-
Ext4 connects and synchronizes.
Scenario C
-
Ext1 fails.
-
Ext2 fails.
-
Ext3 connects and synchronizes.
-
Ext4 connects; downloads Admin Overrides and first-time use configuration information; and synchronizes.
2.5.12 Selective Backup/Restore
The Agent can be configured to compare the local store of user credentials with a remote backup file and write the newer set over the older set. This selective backup/restore, or synchronization, can be triggered from the command line (and thus from an "at," or timed, job) or by configuring certain Agent events (for example, the Startup task, the Refresh task, and so on).
Note:
Individual sets of credentials are not compared; for this more-granular level of synchronization, see Synchronization.2.5.13 Command-Line Synchronization
To trigger a command-line synchronization, run the Agent from the command line (even when the Agent is currently running) using the following syntax:
ssoshell.exe /mobility /sync [path] /silent
Where
[path]
is the actual path to the directory where the backup file may exist. (Default: the last directory to which a command line backup file was stored, or where Shell:AutoBackupPath points.)
/silent
means do not show the Backup/Restore Wizard when performing the backup/restore.
To perform a completely-silent synchronize with a network share at \\FS\Backup\Private:
ssoshell.exe /mobility /sync \\FS1\Backup\Private /silent
To synchronize to the last-used location, or to where Shell:AutoBackupPath points:
ssoshell.exe /mobility /sync /silent
2.6 Setting Password Policies
Logon Manager allows administrators to set policies that control automatic password generation. Password policies simplify user logons while ensuring the organization's security.
Most applications have constraints for passwords: how long they can or must be, whether they must or must not include numbers or symbols, and so on. Logon Manager's password generation feature improves application logon security by automatically creating passwords made up of random characters according to predefined sets of constraints, stored as password policies. Each policy can apply to multiple applications or subscribers.
Using predefined password policies, you can completely automate password changes and implement sophisticated security schemes, including complex passwords, frequent password changes, and application-specific passwords unknown to users.
Note:
If the policy you create makes a password difficult or impossible, Logon Manager will try to create a password for up to five seconds and then notify the user that it was unable to generate a password. You can preview the passwords a particular policy generates by clicking Test Policy.2.6.1 Creating Password Generation Policies
Click Password Generation Policy in the left pane. This option displays the currently available password generation policies and provides access to policy settings.
See Setting Password Policies for more information.
To add a new password policy:
-
Do one of the following:
-
Click Add in the right pane.
or
-
In the left pane, right-click Password Generation Policy then click New Policy on the shortcut menu.
-
-
Enter a Policy Name and click OK. The Policy Subscribers tab appears in the right pane, where you can add applications that will use the new policy.
To modify a listed password policy's configuration:
-
Click a policy, then click Edit. The Policy Subscribers tab appears in the right pane.
To delete one or more password policies:
-
Select a policy (use Ctrl+click or Shift+click to select multiple entries), then click Remove.
2.6.2 Adding a Password Policy
Use this dialog to add and name a new password generation policy.
-
Enter a Policy Name and click OK.
To display this dialog:
-
Right-click Password Generation Policy and choose New Policy from the shortcut menu.
or
-
Choose Password Generation Policy from the Insert menu.
2.6.3 Working with a Selected Password Policy
The list under Password Generation Policies represents configured password generation policies. You can use the tabs in the right pane to view or modify a policy's properties, add or remove applications that use the policy, or change security settings.
See Setting Password Policies for more information.
To view or edit a password policy:
-
Click Password Generation Policies in the left pane
-
Select a policy from the list in the right pane, then click Edit. The Policy Subscribers tab appears in the right pane.
or
-
In the left pane, click the plus sign (+) next to the Password Generation Policies icon (or double-click Password Generation Policies) to display the configured policies.
-
Click a policy icon to select it. The Policy Subscribers tab appears in the right pane.
| Control | Function |
|---|---|
| Add | Create another policy. |
| Delete | Delete the selected policy. |
| Add Note | Attach notes about this policy for future reference. |
2.6.4 Managing Policy Subscribers
Use the Policy Subscribers tab to add or manage the applications that use the selected password generation policy.
See Setting Password Policies for more information.
To add applications to a policy:
-
Click Add. The Select Application dialog appears.
-
Select the applications that will use this policy. (Use Ctrl+click or Shift+click to select multiple entries.)
-
Click OK.
To remove applications from a policy, select a policy (use Ctrl+click or Shift+click to select multiple entries) and click Remove.
Click Add Notes to enter notes.
To display this tab:
-
Click Password Generation Policies in the left pane.
-
Select a policy from the list in the right pane, then click Edit.
-
The Policy Subscribers tab appears in the right pane.
2.6.5 The Password Constraints Tab
Use the Password Constraints tab to set or modify the allowed type, number, position, and repetition of characters in passwords. These constraints apply to new passwords that Logon Manager automatically generates for applications that subscribe to the selected policy.
To view a set of test passwords based on the passwords constraints for this policy, click the Test Policy button.
See Setting Password Policies for more information.
To set password constraints:
-
Do one of the following:
-
Select a password policy.
or
-
Create a new password policy.
-
-
Click the Password Constraints tab in the right pane.
-
Select constraint options from the displayed controls.
2.6.5.1 Password Constraint Options
The following tables list the various password constraint options and their possible values.
| Password Length | Options |
|---|---|
| Minimum Length | Minimum number of characters a password most contain: 1-128, default: 8 |
| Maximum Length | Maximum number of characters a password can contain: 1-128, default: 8 |
| Repeating Characters | Options |
|---|---|
| Maximum repeated non-consecutive characters | Maximum number of times a given character can be repeated in a password (in any position): 0-127, default: 7 |
| Maximum repeated consecutive characters | Number of times a given character can be repeated consecutively (adjacent to itself): 0-127, default: 7 |
| Alphabetic Characters | Options |
|---|---|
| Allow Uppercase Characters | Check to allow uppercase characters to be included in a password, and enter or select the minimum quantity to permit. |
| Allow Lowercase Characters | Check to allow lowercase characters to be included in a password, and enter or select the minimum quantity to permit. |
| Numeric Characters | Options |
|---|---|
| Allow Numeric Characters | Check to allow numeric characters to be included in a password, and enter or select the minimum and maximum quantity to permit. |
| Can Start Password | Check to allow password to begin with numeric characters. Default: numeric characters are allowed to begin a password. |
| Can End Password | Check to allow password to end with numeric characters. Default: numeric characters are allowed to end a password. |
| Special Characters | Options |
|---|---|
| Allow Special Characters | Check Allow Special Characters to allow non-alphabetical and/or non-numeric characters, and enter or select the minimum and maximum quantity to permit. Default: special characters are not allowed. |
| Can Start Password | Select to allow password to begin with a special character. Default: special characters are not allowed to begin a password. |
| Can End Password | Select to allow password to end with special a character. Default: special characters are not allowed to end a password. |
| Other Characters | |
|---|---|
| Check to allow other characters to be included in a password. |
| Excluded Characters | |
|---|---|
| Enter the specific characters to exclude from a password. |
| Previous Password Constraints | Options |
|---|---|
| Password must not be the same as previous password | Select to prevent reusing the previous password. |
| Limit the amount of characters that are the same as the previous password | Select to limit repetition of characters from the previous password. |
| Number of characters that can be the same from the previous password | If some number of characters from the previous password is permissible, select the maximum number of characters to allow.
Note: Logon Manager recognizes multiple occurrences of a character as the same character and will therefore permit more than one occurrence of that character in the new password. So, if the previous password contained three "A"s, and you specify that one character from the previous password can repeat, Logon Manager will allow more than one instance of "A" in the new password. |
| Test Policy |
|---|
| Displays the Test Password Policy dialog, which lets you generate and view a set of test passwords based on the current policy settings. |
2.6.6 Testing a Password Policy
Use the Test Password Policy dialog to generate a set of test passwords based on the currently-selected password policy. This lets you preview how the Agent will respond to a password change request from an application that subscribes to this policy. You can choose the number of test passwords to generate.
If the password constraints you have set are contradictory or too restrictive to generate any passwords, a message appears explaining how many passwords failed the test and why.
2.6.6.1 Generating a Test Password
Use this screen to generate a list of passwords that conform to your policy and determine if the policy adequately addresses your needs.
-
Select or enter the Number of test passwords to generate.
-
Click Generate Passwords. The sample passwords display in the output window.
-
When you are finished, click Cancel or the X in the upper right corner to close the dialog.
To display this dialog:
-
Do one of the following:
-
Select a password policy
or
-
Create a new password policy.
-
-
Click the Password Constraints tab in the right pane.
-
Set or modify the constraint settings, then click Test Policy.
2.7 Using Passphrase Sets
To enhance security, you can create groups of questions to present to the user upon a password reset request. Create, configure, modify, and delete, these groups, called Passphrase Sets, using the Passphrase Questions screens.
Note:
This feature is used only with Windows Authenticator v2, LDAP Authenticator v2, and in Authentication Manager with the Smart Card authenticator (SCAuth).For increased security, the current authenticator checks the SecondaryAuth.dll signature to verify its authenticity before loading it. If you choose to use a secondary authentication extension other than the one that ships with the product, you must submit it to Oracle for signing before you can implement it.
2.7.1 Adding a Passphrase Set
To add a passphrase set:
-
Do one of the following:
-
In the left pane, right-click Passphrase Questions and select New Passphrase from the shortcut menu.
or
-
Right-click in the right pane and select New Passphrase from the shortcut menu.
or
-
Click the Add button at the bottom of the right pane.
or
-
From the Insert menu, select Passphrase.
-
-
In the Add Passphrase Set dialog, type a passphrase set name and click OK.
-
Use the Questions tab in the right pane to add questions to the current passphrase set.
2.7.2 Deleting a Passphrase Set
To delete a passphrase set, do one of the following:
-
In the left pane, select Passphrase Questions.
-
From the list of passphrase sets in the right pane, select a set and click the Delete button.
or
Select a set, right-click, and select Delete from the shortcut menu.
or
-
Double-click Passphrase Questions in the left pane, or click the "+" sign to expand the menu.
-
From the expanded Passphrase Questions menu, right-click an existing passphrase set, and select Delete from the shortcut menu.
2.7.3 Modifying a Passphrase Set
To modify a passphrase set:
-
Double-click a passphrase set under the Passphrase Questions menu. The questions in that set display in the Questions tab in the right pane.
-
To add a question to the set, click the Add button and type your question into the Add a Question dialog. Then click OK.
-
To edit a question in the set, select it and click the Edit button. Make changes to the question in the Add a Question dialog. Then click OK.
-
To delete a question in the set, select it and click the Remove button. Logon Manager asks you to confirm the deletion. Click OK.
-
2.7.4 Setting the Default Passphrase Set
Use this option to designate a Passphrase set as the default. The default set contains passphrase questions that users answer during First-Time Use (FTU). The FTU wizard is invoked when:
-
A user starts the Agent for the first time after installation.
or
-
The administrator deploys an
ftulistobject (for example, theftulist.inifile).
On first-time use, Logon Manager users select a passphrase question and supply an answer. This stored passphrase answer can be used to reset Logon Manager authentication if the user later changes the primary logon password. The next time single sign-on re-authentication is required, the user enters the new password, and Logon Manager displays the passphrase question to confirm the user's identity.
The Agent uses only one passphrase set. You must decide which set of questions you want the user to answer and designate that set as the default passphrase set. The set you designate as the default is the only one written to the ftulist.
If you import an ftulist to the Administrative Console and change the passphrase set before you re-export the ftulist to the repository, the passhprase set is not included in the export unless you reset it as the default.
To assign a default passphrase set, do one of the following:
-
In the right pane, right-click on the set name, then select Set As Default from the shortcut menu.
or
-
In the left pane, right-click on the set name, then select Set As Default on the shortcut menu.The passphrase set name will appear in bold type in both the right and left panes, indicating that it is the default set.
2.7.5 Working with the Questions Tab
Use the Questions tab to manage questions and settings in the selected passphrase set. To display this tab, from the left pane, select Passphrase Questions and select the Default Set displayed in bold.
To add questions to a passphrase set:
-
Select a language from the drop-down menu.
-
Click Add or select Passphrase from the Insert menu.
-
In the Add Question dialog, enter a question.
-
Select or enter a minimum length for the reply.
-
Click OK.
The following table lists the ways you can configure a set of passphrase questions.
| Control | Function |
|---|---|
| Language | Select language for passphrase questions. |
| Default Question | Lists current default passphrase question, which is checked by default. When a new passphrase question is added the default passphrase is unchecked. When checked, the default passphrase is disabled for the current passphrase set. When unchecked the default passphrase is enabled for the current passphrase set. |
| Enabled Question | Lists current passphrase questions. Checked items are the enabled passphrases for the current set. To disable a passphrase click the checkbox to clear it. To modify a passphrase question, double-click it, or select it and click Edit. |
| Add | Add a new passphrase question. Displays the Add Question dialog |
| Remove | Delete the selected passphrase question. Displays a confirmation prompt. |
| Edit | Modify the selected passphrase question. Displays the Edit Question dialog. |
| Set This Passphrase Set as Default | Sets the current set as the default. The default passphrase set name in the left pane displays in bold. |
| Remove or Disable? | After a passphrase question has been created, deployed, and put into use by end-users, it should not be deleted. Users who have selected a passphrase question that has been deleted will not be able to change their passwords without losing access to their Logon Manager credentials. Instead, to remove an in-use passphrase question (and keep it from being displayed during first-time use), disable the question by clearing its checkbox in the list in the Questions tab. |
2.8 Working with Credential Sharing Groups
Credential sharing groups are sets of applications that share the information of one or more fields to facilitate account management, allowing users to apply a credential change made in one application to other specified applications automatically. For each group that you create, you can include any number of applications and designate which credentials they have in common.
When Logon Manager handles a credential change for any application that is a member of the sharing group, it automatically applies the credential change to all other group members. Any number or combination of Windows, mainframe/host, and Web applications can share a single credential. When using the Windows (Domain) or Directory Server (LDAP) authenticator, selected applications can share a single credential with the authenticator as well.
Applications will share credentials for only their initial deployment to the Agent unless you enable credential sharing groups. Set this parameter in the Required Password Change settings. You can permit or prohibit users' control over which of their applications share credentials in the Global Agent Password Change Settings.
For example, an enterprise might have a new Web interface to an old mainframe application. One way to share the credential between these two is to use a credential sharing group. Some applications share a common credential (for example, an Intranet application and an e-mail application). These applications should be in the same credential sharing group.
Note:
The Windows authenticator password is in a predefined group named Domain.The LDAP Directory Server authenticator is in a predefined group named LDAP.
2.8.1 Adding Predefined Applications to a Credential Sharing Group
The Administrative Console does not currently support adding predefined applications (those included in the default configuration file applist.ini) to credential sharing groups. You must do this manually by creating identically-named sections in entlist.ini (the custom-application configuration file) that identifies the sharing group. The following example adds an Internet Explorer pop-up application to the credential sharing group OurServer:
Example
[~Internet Explorer Pop-up XP]
Group=OurServer
2.8.2 Creating Credential Sharing Groups
Click Credential Sharing Groups in the left pane. This option displays the currently available credential sharing groups and provides access to group settings. Credential sharing is enabled by default.
See Settings for a Selected Credential Sharing Group for the procedure to configure a group.
To create a credential sharing group:
-
Select Credential Sharing Groups in the left pane to display current password groups in the right pane.
-
Do one of the following:
-
Click Add in the right pane.
or
-
In the left pane, right-click Credential Sharing Groups, then select New Group on the shortcut menu.
-
-
In the Add Sharing Group dialog, enter a Group Name and click OK.
-
With a group selected, click Add in the right pane to add applications to the group. See Adding Applications to a Credential Sharing Group for more information.
2.8.3 Viewing or Editing a Sharing Group
To view or edit a credential sharing group:
-
Select Credential Sharing Groups in the left pane.
-
Select a group from the list in the right pane, then click Edit.
or
-
In the left pane, click the plus sign (+) next to the Credential Sharing Groups icon (or double-click Credential Sharing Groups) to display the configured groups.
-
-
Do one of the following:
-
Select a group icon. The list of applications for this group appears in the right pane.
or
-
Right-click a group icon to display a shortcut menu with these options:
-
Delete. Delete the selected group.
-
Rename. Rename the selected group.
-
-
2.8.4 Deleting a Credential Sharing Group
To delete a credential sharing group, select the group (use Ctrl+click or Shift+click to select multiple entries), then click Remove.
Note:
You cannot delete the default groups, Domain or LDAP.2.8.5 The Domain Sharing Group
The domain sharing group is the predefined credential sharing group for the Windows authenticator.
See Adding Applications to a Credential Sharing Group for more information about using this panel.
To select the domain credential sharing group:
-
Select Credential Sharing Groups in the left pane.
-
Select Domain from the list in the right pane, then click Edit.
or
-
In the left pane, click the plus sign (+) next to the Credential Sharing Groups icon (or double-click Credential Sharing Groups) to display the configured groups.
-
Click Domain.
2.8.6 The LDAP Sharing Group
The LDAP sharing group is the predefined credential sharing group for the Directory Service authenticator.
To select the LDAP credential sharing group:
-
Select Credential Sharing Groups in the left pane.
-
Select LDAP from the list in the right pane, then click Edit.
or
-
In the left pane, click the plus sign (+) next to the Credential Sharing Groups icon (or double-click Credential Sharing Groups) to display the configured groups.
-
Click LDAP.
2.8.7 Settings for a Selected Credential Sharing Group
Logon Manager provides flexibility and granularity for you to control how credential sharing groups work. You can configure the following options:
-
Sharing any or all fields for a group of applications:
-
Username
-
Password
-
Third Field
-
Fourth Field
Note:
Administrators should take care to avoid resetting the Password field value when Microsoft Windows 7 users are logged on.
-
-
Pre-filling all shared fields when a user first encounters an application in a sharing group, thus requiring the user to enter information only for fields that are not shared by the group.
-
Automatically creating an account when a user encounters an application for which all credentials are pre-determined.
-
Designating a key field; that is, a field that the Administrative Console uses when updating shared credentials, changing credentials only for accounts with the same key value.
See Creating Credential Sharing Groups for more information.
The following table lists the controls to configure a credential sharing group.
| Group account management | |
|---|---|
| Shared credentials | List of fields that can be included in a credential sharing group. Check the appropriate boxes.
|
| Key credential within group | Designates a field that indicates to the Administrative Console to update shared credentials only for accounts that share this field value.
If the user wants to create an account that is not constrained by the key field, that account must have a new key field to avoid updating all existing accounts. |
| Pre-fill shared credentials | Specifies that shared fields be pre-populated with the shared credentials when the user creates a new account for an application.
Note: This setting is enabled by default. |
| Automatically create accounts when all credentials are known | Specifies that Logon Manager should create an account automatically when the user encounters an application that has all fields pre-determined.
In order for Logon Manager to complete account creation, you must also enable the "Auto-Submit" setting. Otherwise, the "New Logon" dialog appears as usual. Note: This field is available only if Key credential within group is set to None. |
2.8.8 Adding Applications to a Credential Sharing Group
To add an application to a credential sharing group:
-
Click Add. The Select Application dialog appears.
-
Select the applications to include in the selected group. (Use Ctrl+click or Shift+click to select multiple entries.)
-
Click OK.
2.8.9 Editing Applications in a Credential Sharing Group
To edit a applications in a credential sharing group:
-
Select a group from the left pane, and click Add.
-
Select the applications that you want to add to this group. (Use Ctrl+click or Shift+click to select multiple entries.) Click OK after you finish making your selections.
-
In the Shared credentials section, under Group account management, check the boxes next to Username, Password, Third Field, and Fourth Field as required.
-
To specify a field as the key credential field, select from the Key credentials within group dropdown list.
-
Optionally, if you did not specify a key credential (by selecting None in the previous step):
-
Check Pre-fill shared credentials if you want Logon Manager to fill shared credentials automatically.
-
Check Automatically create accounts when all credentials are known if you want Logon Manager to create an account without prompting the user with the New Logon dialog.
Note:
Pre-fill shared credentials and Automatically create accounts when all credentials are known are unavailable if you select a key credential.In order to create accounts automatically when all credentials are known, you must also enable Auto-Submit for the application.
-
2.9 Working with User Exclusions
Using the Exclusions settings, you can prevent specific users from saving credentials for specific applications. The process for creating and publishing an exclusion list follows the same workflow as that for other objects in the Administrative Console.
Note:
Use exclusions only for applications for which you want some, but not all, users excluded.If you want to exclude an application from the entire enterprise, turn on the Global Agent Setting, Limit user to predefined applications for… under User Experience > Application Response > Initial Credential Capture. Any application for which you do not create a template will be excluded globally.
Ordinarily, when Logon Manager first detects an application, it prompts the user to enter the credentials to be stored and automatically injected for future use. Using exclusions, if the user enters a username that you have added to the exclusion list for a specific application, Logon Manager does not permit the user to save credentials.
After you publish an exclusion list to Logon Manager:
-
Users can log on to applications manually, using excluded credentials, but the Agent does not respond to the application with credentials on the exclusion list, and users cannot save credentials that appear on the exclusion list.
-
Excluded credentials that the user already has saved, prior to the policy being put in place, will no longer be presented to the application, and those excluded credentials are deleted from the user's credential list.
-
Silent credential capture will not capture excluded credentials.
2.9.1 Creating an Exclusion List
To create a new Exclusion list, in the Administrative Console:
-
Do one of the following:
-
From the Insert menu, select Exclusion List.
-
Select the Exclusions node in the left pane, and click Add at the bottom of the right pane.
-
Right-click on the Exclusions node, and select New List from the contextual menu.
-
Select the Exclusions node and right-click in the empty space in the right pane.
-
-
Enter a name for the list in the Add Exclusion List dialog.
The exclusion list name appears under the Exclusions node of the tree in the left pane. The right pane contains three tabs associated with each exclusions list:
-
Exclusion subscribers
-
Excluded usernames
-
Security
Use these tabs to configure each exclusion list.
2.9.2 Publishing an Exclusion List
The procedure for publishing exclusions is identical to that for publishing any other configuration object. For the procedure to publish an exclusion list, see Publish to Repository.
2.9.2.1 Special Considerations for Active Directory Users
Active Directory users who publish exclusion lists must be members of the "SSOExclusionAdmins" Global Security Group, if the group exists. Logon Manager handles the SSOExclusionAdmins group as follows:
-
If you are using Active Directory and the SSOExclusionAdmins group exists, a user must be a member of this group to publish exclusions.
-
If you are using Active Directory and the SSOExclusionAdmins group does not exist, or if you are using another directory service, anyone with publishing rights can publish an exclusion list.
-
If you are using Active Directory, the SSOExclusionAdmins group exists, and a non-group member attempts to publish several objects that include an exclusion object, the other objects will be published without the Exclusion object.
2.9.2.2 Publishing Exclusion Lists with Configuration Files
You cannot publish exclusion lists as standalone configuration (entlist.ini) files. When you publish configuration files (that is, you have checked the box in the File mode section of the Publish to Repository screen), exclusion lists are published as a subset of an application for which you've configured exclusions.
2.9.3 Add Exclusion List Dialog
Use this dialog to add and name a new exclusion list.
Enter an Exclusion List name and click OK.
To display this dialog:
-
Right-click Exclusions and choose New List from the shortcut menu.
or
-
Choose Exclusion List from the Insert menu.
2.9.4 Working with a Selected Exclusion List
From the left pane, select the list you want to work with. Use the tabs in the right pane to view this list's properties, add or remove applications and users to which the list applies, or change security settings.
See Working with User Exclusions for more information.
2.9.4.1 Selecting an Exclusion List for Viewing or Editing
To view or edit an exclusion list:
-
Click Exclusions in the left pane.
-
Select an Exclusion list from the list in the right pane, then click Edit; or double-click the Exclusion list name in the right pane. The Exclusion Subscribers tab appears in the right pane.
or
-
In the left pane, click the plus sign (+) next to the Exclusions icon (or double-click Exclusions) to display the created Exclusion lists.
-
Click an Exclusion list to select it. The Exclusion Subscribers tab appears in the right pane.
| Option | Function |
|---|---|
| Add | Create another Exclusion list. |
| Remove | Delete the selected list. |
| Add Notes | Attach notes about this list for future reference. |
2.9.4.2 Exclusion Subscribers
Use this tab to add applications to an exclusion list.
-
Select an Exclusion list from the Exclusions node in the left pane.
-
Click Add on the bottom of the tab.
-
In the Select Application screen, select the application that you want to add to the list. Use Shift+Click or Ctrl+Click to add multiple selections.
-
Click OK. The applications you selected appear in the tab window.
2.9.4.3 Excluded Usernames
Use this tab to add users to an exclusion list.
-
Select an Exclusion list from the Exclusions node in the left pane.
-
Click Add on the bottom of the tab.
-
In the Excluded Usernames screen, select the users that you want to add to the list. Use Shift+Click or Ctrl+Click to add multiple selections.
-
Click OK. The users you selected appear in the tab window.
2.10 Using Shared Accounts
Use this node to manage shared account rights for users. It contains two tabs:
-
Default Rights
-
Admin Rights
These tabs provide the same settings, but differ in which users you assign these rights.
Use this tab to define the shared account rights for each new application. This feature sets standard rights for each application. After each application is created, change the rights as needed.
| Element | Description |
|---|---|
| Directory | Select the target directory server. |
| Element | Description |
|---|---|
| Name | Lists the groups or users who currently have access to this item. |
| ID | Lists the user's account name. |
| Access | Indicates the permissions that have been granted to the user or group (Add Logon, Modify Logon, or Delete Logon). To change a user's or group's access rights, right-click the user or group and select Add Logon, Modify Logon, or Delete Logon from the shortcut menu. |
| Element | Description |
|---|---|
| Copy Permissions to | Use this button to easily apply the shared account rights for the current application to multiple applications. Clicking this button displays a dialog listing all the applications. Select the applications that you want these shared account rights to be copied to. Use Ctrl+click to select multiple entries. Click OK. |
| Add | Displays the Add User or Group dialog (for Active Directory or AD LDS (ADAM)) to select the users or groups who should have access to the currently selected item. |
| Remove | Removes selected users or groups from the list. Select a user or group to remove; use Ctrl+click to select multiple entries. |
| Add User or Group dialog | The Select User or Group dialog varies based on the directory server being used:
For AD/AD LDS (ADAM), use this control to select the individual users or user groups that are to be added to the access list for the current configuration item (Add Logon, Modify Logon, Delete Logon). |
| Element | Description |
|---|---|
| Search Base | The base (highest-level) directory to begin searching for user or group accounts. All subdirectories of the base directory are searched. Enter a location or click Change to browse the directory tree. |
| Change | Displays the Select Search Base dialog to browse for a base directory for the search.
Use this dialog to browse to and select the base (highest-level) directory for user or group names. Click OK when finished. |
| Search | Begin searching the base directory for users and groups. |
| Users or Groups | Lists the search results. Select the names to be added to the access list for the current configuration item. Use Ctrl+click or Shift+click to select multiple entries. Click OK when finished to copy your selections to the access list. |
| Active Directory or ADAM | Use this dialog to select the individual users or user groups that are to be added to the access list for the current configuration item (Add Logon, Modify Logon, Delete Logon). |
| Element | Description |
|---|---|
| List Names From | Select an Active Directory domain or server. |
| Names | Lists the names of users and groups for the selected domain or server. Select one or more names to add to the access list. |
| Add | Copies users and groups selected in the Names list to the Add Names list. Use Ctrl+click of Shift+click to select multiple entries. |
| Members | When a group is selected, the Names list displays the Global Group Membership dialog, which list the members of the selected group. |
| Search | Displays the Find Account dialog for searching one or more domains for a specific user or group. |
| Add Names | Display the names of the users or groups for whom you have added so far. Click OK to add these names to the access list for the current configuration item.
Note: You can type or edit user names in this list. However, entries are checked for invalid account names and duplicate account selections are automatically removed when you click OK. |
2.11 Storing User Data
Logon Manager stores user credentials locally in the …\Application Data\Passlogix folder. Global Agent Settings are stored in the Local Machine registry key (HKLM); settings modified the user are stored in the Current User registry key (HKCU).
Logon Manager can also perform a complete backup of credentials and settings to a file (.bkv). The backup can be performed manually by the user, or automatically by administrative configuration). For details on this feature, see File-Based Backup/Restore.
Logon Manager can also synchronize individual user credentials with these remote sources, including file-systems, databases, and directory servers. These remote sources can provide the Agent with application logons. First-time-use (setup) information and administrative overrides (Global Agent Settings). For details on this feature, see Synchronization.
2.11.1 Storing Credentials in the User Object
Note:
This section applies to Active Directory only.With Active Directory installations, you can configure Logon Manager to store user data under the user object, rather than in the standard vgoconfig container. To do this, take the following steps:
-
Use the Enable Storing Credentials under User Object command (on the Repository menu) to update the directory schema to allow user-credential containers as children of user objects. This command also modifies the directory-root security settings to grant users the rights to create the credential containers.
-
Do one of the following:
-
Select the Store data under the user objects option (see Adding a Locator Object) to create a
vgolocatorobject ("default" for all users that use this locator, or for specific user by distinguished name) that points to the user objects. -
Use the Location for storing user credentials Agent setting (in the Active Directory Synchronization Settings) to configure the Agent to disregard the vgolocator object and always store credentials under the user object.
-
2.11.2 File-Based Backup/Restore
If the Backup/Restore module is installed, the Administrative Console can perform a complete backup/restore of user credentials and settings to or from another location. The backup/restore can be performed manually (by the user) or automatically (by administrative configuration). Also, a selective backup/restore (writing the newer information over the older information) can be performed automatically (by administrative configuration).
Note:
If the Backup/Restore module is installed, the user can perform a manual backup, store to any location (even a floppy drive), and select any password (even a one-character password).2.11.2.1 Automatic Backup
You can configure the Agent to perform a full backup of user credentials and settings. This backup can be triggered from the command line (and thus from an "at," or timed, job) or by configuring certain Agent events (for example, the Startup task, the Refresh task, and so on).
2.11.2.2 Command-Line Backup
To trigger a command-line automatic backup, run the Agent from the command line (even when the Agent is currently running) using the following syntax:
ssoshell.exe/mobility /backup [path] /silent
where:
[path] is the actual path to the directory where the backup file is placed. The default is the last directory where a command line backup file was stored.
and:
/silent indicates to hide the operation when performing the backup.
To perform a completely silent backup to a network share at \\FS\Backup\Private:
ssoshell.exe /mobility /backup "\FS1\Backup\Private" /silent
To back up to the last-used location:
ssoshell.exe /mobility /backup /silent
2.11.2.3 Event-Driven Automatic Backup
To configure the Agent to perform an automatic backup upon certain Agent events, determine the command line string needed to perform the desired backup. Then, set the appropriate task. For example, to perform a backup with every change in credentials, set a task to run When logons change (add, delete, copy, modify) (under User Experience > Custom Actions) to the command line string.
2.11.2.4 Forced Restore
The Agent can be configured to perform a full restore of user credentials and settings, replacing any existing data. This restore can be triggered from the command line (and thus via a remote "run" command) or by configuring certain Agent events (for example, the startup task).
2.11.2.5 Command-Line Forced Restore
To trigger a command-line forced restore, run the Agent from the command line (even when the Agent is running) using the following syntax:
ssoshell.exe /mobility /restore [path] /silent
where:
[path] is the path to the directory where the backup file exists. The default is the last directory where a command line backup file was stored.
and:
/silent indicates to hide the operation when performing the restore.
To perform a completely silent restore from a network share at \\FS\Backup\Private:
ssoshell.exe /mobility /restore "\FS1\Backup\Private" /silent
To restore from the last-used location:
ssoshell.exe /mobility /restore /silent
2.11.2.6 Event-Driven Forced Restore
To perform a forced restore upon certain Agent events, determine the command line string needed to perform the desired restore. Then, set the appropriate task. For example, to perform a restore at startup, set a task to run After Agent starts (in the Global Agent Custom Actions Settings) to the command line string.
2.12 Creating and Using Templates
Note:
For a complete discussion of configuring and diagnosing templates, see the guide, Configuring and Diagnosing Logon Manager Application Templates.Logon Manager recognizes and responds to a wide array of logon scenarios. Users can configure each logon in advance or as they encounter them. When a user configures a logon, the Agent displays a list of predefined applications. Users select an application from this list or create a logon for an unlisted application.
Predefined applications simplify configuration for the user and increase the reliability of both recognizing and responding to logon and password-change requests.
Preconfigured application logons for many popular Windows applications are included with the Administrative Console in the form of templates that contain all or part of the logon's configuration. You can also convert the application logons that you create into templates through the Administrative Console. The applist.ini file (located in the installation directory in the Plugin\LogonMgr directory) includes predefined logons for network and web pop-up logon dialogs boxes and for many online service providers.
Templates provide two practical benefits for creating and managing pre-configured logons:
-
You can store, share, and reuse a group of specific logon settings as a starter set for creating new logons based on the template. Your templates appear as options in the Add Application dialog.
-
If you make changes to a template's source logon, you can easily apply your changes to any logon based on that template, by using the Update Applications command on the Tools menu.
You use a template to create a logon by selecting it from the Applications drop-down list in the Add Application dialog. You are prompted if additional information is needed to complete the configuration.
You can update application logons with any changes made in their originating templates. Open the Administrative Console XML file containing the applications and select the Update Applications command from the Tools menu.
To create a template:
-
Select an existing application logon in the Manage Templates dialog from the Tools menu.
-
Choose the logon settings (for the application and for individual forms) that you want to be able to override later; use the Tab in the Edit Template dialog (click Edit in the Manage Templates dialog). For Web and Windows applications, you can also choose a setting that the template user must provide in order to complete the logon configuration (on the Supply Info tab).
-
Save the current file to the Templates folder under the Administrative Console program directory (typically, this is
C:\Program Files\Passlogix\SSO Administrative Console\Templates).
Note:
When creating templates, take precautions to ensure that no complete template name exactly matches the first part of another template name. If the Agent finds two templates, one of whose names is a subset of the other, the Agent recognizes the template with the shorter name.For example, if two templates are named ABC and ABD, this issue does not occur. But if one template is named ABC, and one is named ABC_D, the Agent recognizes only the ABC template, and ignores the ABC_D template, regardless of which application is opened.
To add templates to Logon Manager:
-
Create the application logons using the Administrative Console configuration features.
-
Create and deploy an entlist as an
INIfile or equivalent synchronization object. -
Use Export to INI file to create an
entlist.inifile. -
Use Publish to Repository to create an entlist synchronization object.
-
Do one of the following:
-
If you are using synchronization to deploy application logons, do not use the Location of
entlist.inifile setting. The synchronizer automatically locatesentlist.iniandftulist.iniin the user's%AppData%\Passlogixdirectory. -
If you are not using synchronization to deploy application logons, use the Location of entlist.ini file setting in the Global Agent Synchronization settings.
-
Note:
The administrator must createentlist.ini; the Agent does not create it automatically.2.12.1 Managing Templates
Use this dialog to create, modify, and remove templates for application logons. To display this dialog, on the Tools menu, click Manage Templates.
2.12.1.1 Creating a Template for a Running Application
You can create a new template, or edit an existing one, on-the-fly for a Windows or Web application while the application is running.
Note:
This procedure applies only to Windows and Web applications. If you attempt this procedure for a host or mainframe application, the Host/Mainframe Form Wizard launches.In order to perform this procedure, both the Administrative Console and the Logon Manager Agent must be running, and you must configure the Agent settings to display the Title Bar Button menu.
2.12.1.1.1 Creating a Template for a Running Windows Application
To create a template for a running Windows application:
-
Launch the application for which you want to create a template.
-
Select Create Template from the application's Title Bar Button menu.
Description of the illustration lm_create_template.png
Two things happen:
-
In the application's window, Logon Manager detects the credential fields and highlights them.
-
A condensed version of the Form Wizard appears. Enter information for the following fields:
-
Form Name. This field is pre-filled with the name of the selected application. You can leave this as it is or change it if you want to.
-
Form Type. Select the form type from the drop-down menu:
Logon
Logon Success
Logon failure
Password change
Password change success
Password change failure
-
Add to Template.
This field defaults to the New Template selection. Alternatively, the drop-down menu contains the list of all configured Windows application templates to which you might want to add this form.
-
Edit Fields/Hide Details.
Toggle this button to expand the window to display the entire Form Wizard, or collapse the window to the simpler Form Wizard.
-
-
2.12.1.1.2 Creating a Template for a Running Web Application
To create a template for a running Web application:
-
Launch the application for which you want to create a template.
-
Select Create Template from the application's Title Bar Button menu.
-
The Web Form Wizard launches.
-
In the Web page, Logon Manager detects the credential fields and highlights them.
-
A condensed version of the Form Wizard appears. Enter information for the following fields:
-
Form Name. This field is pre-filled with the name of the selected application. You can leave this as it is or change it if you want to.
-
Form Type. Select the form type from the drop-down menu:
Logon
Logon Success
Logon failure
Password change
Password change success
Password change failure
-
Add to Template.
This field defaults to the New Template selection. Alternatively, the drop-down menu contains the list of all configured Windows application templates to which you might want to add this form.
-
Edit Fields/Hide Details.
Toggle this button to expand the window to display the entire Form Wizard, or collapse the window to the simpler Form Wizard.
-
2.12.1.2 Creating a New Template for Applications That Are Not Running on Your Workstation
You can create a template for an application, even if it is not running or installed on your workstation. To create a new template in this scenario:
-
Click Add to create a new template from an application logon.
-
From the Select Applications dialog, select the application on which to base the template.
-
Click OK. In the Edit Template dialog, specify the settings that must be supplied by an administrator, and the template's overriding settings.
2.12.1.3 Modifying an Existing Template
To modify an existing template, select an application from the list and click Edit. In the Edit Template dialog, modify the settings that must be supplied by an administrator, and the template's overriding settings.
2.12.1.4 Deleting a Template
To delete a template, select an application from the list and click Remove.
2.12.1.5 Adding Application Templates to Logon Manager
To add templates to Logon Manager:
-
Create the application logons using the Administrative Console's configuration features.
-
Create and deploy an entlist as an
INIfile or equivalent synchronization object.-
Export to an
INIfile to create anentlist.inifile. -
Publish to the repository to create an entlist synchronization object.
-
-
Do one of the following:
-
If you are using synchronization to deploy application logons, do not use the Location of
entlist.inifile setting. The synchronizer automatically locatesentlist.iniandftulist.iniin the user's%AppData%\Passlogixdirectory. -
If you are not using synchronization to deploy application logons, use the Location of
entlist.inifile setting in the Synchronization Global Agent Settings.
-
Note:
The administrator must createentlist.ini; the Agent does not create it automatically.2.12.2 General Guidelines for Setting Up Applications
Setting up and configuring applications is easiest when you do the following:
-
Have the target applications on the same workstation as the Administrative Console.
-
Minimize the number of other applications running during configuration.
-
To facilitate creating application configurations and testing:
-
Configure your workstation not to use a synchronizer extension.
-
When the application logon request causes the Agent to respond, tell the Agent to ignore it.
-
In the Administrative Console, create the application configuration and then use Export Apps to Agent (on the Tools menu) to overwrite the local
entlist.inifile. -
Keep Logon Manager visible, and select Refresh whenever you finish exporting from the Administrative Console.
-
Bring up the application logon dialog to see if your new configuration works properly within the Agent.
-
2.12.3 Adding Windows Applications
The easiest and most precise way to configure Windows applications is by using The Windows Form Wizard.
Before you begin Windows logon configuration, review the General Guidelines for Setting Up Applications.
2.12.3.1 Special Issues and Settings
Some Windows applications interact in unusual ways or have special requirements. For these scenarios, the Administrative Console offers these additional configuration options.
2.12.3.1.1 Special Configuration Settings
The following table lists configuration settings to consider when creating Windows templates.
| Tab | Setting | Consideration |
|---|---|---|
| Fields | SendKeys | Use the SendKeys option for Windows applications that:
|
| Miscellaneous Tab (for a new or selected logon form) | Allowable Class | Use the Allowable Class option to identify logon or password-change window classes that must be present in order to execute this logon. This is useful for applications that present logon or password-change windows with non-standard class names. |
| Ignore this Window Class | Use the Ignore Window Class option for applications that:
|
|
| Attach to window's Message Queue | Use the Attach to… option to keep the focus on the target logon window while sending credentials. | |
| Preset Focus | Use the Preset Focus options to have the Agent set the focus on a field before entering data in it. | |
| Miscellaneous Tab (for a selected application) | Service Logon | Select the Service Logon option to let the Agent detect an application that runs as a Windows service (that is, in the System space, rather than the User space). |
| Third/Fourth Field Label | Use these options to specify the text labels the Agent should use to display these additional fields. | |
| File extension for Icon | Use this option to provide a Windows file extension to associate with a logon; this lets the Agent map an icon to it. |
2.12.4 Adding Web Applications
Logon Manager detects and responds to logon and password-change requests for predefined Web applications. Much like Windows and host/mainframe applications, administrators define Web applications by including a section in entlist.ini.
The Agent recognizes specific strings of data at specified locations within the HTML code of a Web page. This data tells the Agent how to detect the Web site's logon and password-change screens, where to enter the user credentials, and how to submit those credentials.
The easiest and most precise way to configure Web applications is by using the Web Form Wizard. Before you begin this procedure, refer to the General Guidelines for Setting Up Applications.
Note:
Web applications can have the logon and password change forms on the same page, on different pages within the same URL, or at different URLs. Furthermore, logons can be in the same form at different URLs, or on different forms at different URLs.If you add a configuration for a site where the user's local store already includes a logon, your new configuration will override the user's. The user will need to re-enter credentials for this application.
The user can still view the old logon in Logon Manager.
2.12.5 Adding Host/Mainframe Applications
Logon Manager provides single sign-on functionality to host/mainframe applications through host emulators that:
-
Implement HLLAPI (high-level language application programming interface).
or
-
Have a built-in scripting language that can display a dialog.
The host emulator enables an end user to connect the Windows workstation to a mainframe, AS/400, OS/390, Unix, or other host-based session. Logon Manager recognizes a terminal screen by looking for specific strings of data at specific screen locations.
In order for Logon Manager to recognize host emulators, enable mainframe support by selecting MFEnable in the Global Agent Settings for Host/Mainframe Application Response.
All host/mainframe applications must be predefined. The Logon Manager end user has no means to define host/mainframe applications. The administrator must also configure the host emulators themselves in order for Logon Manager to recognize them. Any host emulator can use application logons created by any other host emulator. See Section 7.2.4, "Configuring Host Emulators," for procedures to configure specific emulators.
Note:
Logon creation is easiest using a host emulator that allows you to select text and that displays the row and column coordinates of your selection.For information on configuring an emulator that does not support HLLAPI but does have a scripting language, contact Oracle.
For emulators that do not implement HLLAPI or have a scripting language, you can, in some cases, configure the host/mainframe application as a Windows application (to detect the form by its window title) and using SendKeys to supply user credentials. See Windows applications Special Configuration Settings for more information.
The easiest, and most precise way to configure host/mainframe applications is by using the Host/Mainframe Form Wizard. Before you begin this procedure, refer to the General Guidelines for Setting Up Applications.
2.12.5.1 Configuring a Host/Mainframe Application Manually
The following procedure describes the steps for manually configuring or modifying a host/mainframe logon. Refer to the specific dialogs and controls for more information. Before you begin this procedure, see the General Guidelines for Setting Up Applications and Creating a Template Using an Open Application for the procedure to select an application from a list of open applications.
-
Start the application and configure the host emulator. See Section 7.2.4, "Configuring Host Emulators," for more information.
-
In the Administrative Console, do one of the following:
-
Create a new host/mainframe application logon.
or
-
In the left pane, click Applications and select a host/mainframe application. Click the General tab in the right pane.
-
-
In the Identification tab of the Host/Mainframe form-configuration dialog:
-
Select a logon form from the list and click Edit.
-
Specify one or more Text Matching captions, so that this page can be identified uniquely from other pages. Specify the identifying Text string of the caption and its starting Row and Column numbers.
-
Specify the Fields for credentials. Click Edit (under Fields) to display the SendKeys (Host/Mainframe) dialog. Specify the starting Row and Column for each field and the keystrokes to send.
-
-
If the terminal response time requires a pause between credential field entries, select the Options tab and enter the number of milliseconds to pause in Delay Field.
-
Repeat the steps above for each additional logon screen.
-
To add password change information, repeat the process with the Password Change tab and the password change dialog in the target application.
2.12.5.2 Adding Java Applications and Applets
You can configure Java application logons and Java applet logons (in Web pages) by using the The Windows Form Wizard. The procedures for creating and deploying are generally identical for Java and Windows applications.
Note:
In order for the Agent to detect and use Java application logons, the Java Runtime Environment (JRE) must be installed on the workstation prior to installing Logon Manager. If JRE is not already present when Logon Manager is installed, the Agent's Java Helper component is not available for installation.Before you begin Java logon configuration, refer to the General Guidelines for Setting Up Applications for configuring applications.
2.12.5.3 Adding Telnet Applications
Logon Manager supports Telnet sessions using HLLAPI (high-level language application programming interface) implemented by a mainframe/host emulator. For the most current list of supported emulators, see the Oracle certification matrix:
http://www.oracle.com/technetwork/middleware/ias/downloads/fusion-certification-100350.html.
Configuring a logon for a Telnet application is essentially identical to adding host/mainframe applications in general, but with these exceptions:
-
Host applications generally display text captions and data fields in fixed positions, which lets Logon Manager detect a screen as a logon form using Text Matching and absolute row/column coordinates. By contrast, a Telnet application, including its logon screen, appears in a scrolling text window. The screen position of the text caption for Logon Manager to match (and begin the logon) should be set as a row number relative to the cursor (negative for above, positive for below) and an absolute column number. See the example in the next section.
-
If one or both of the caption's coordinates are unpredictable, you can use an asterisk (*) for the row setting to match text in any row (and a fixed column), for the column setting to match text in any column (and a row relative to the cursor), or for both settings to match text anywhere on screen.
-
When supplying credentials for a Telnet logon, Logon Manager ignores the row and column coordinate settings for field-matching. However, the settings must be present in the logon configuration. Use one (1) as the value for both row and column coordinates for all credential fields in a Telnet logon.
-
In order to ensure that the Telnet logon credentials are filled in properly, Logon Manager is enabled with timing logic. The Delay Field setting (on the Options tab for configuring a host/mainframe logon form) indicates the time in milliseconds that the Agent should pause between each action.
Note:
See Section 7.2.4, "Configuring Host Emulators," for additional information on HLLAPI configuration.2.12.5.4 Adding a Telnet Application Logon
The easiest, and most precise way to configure Telnet applications is by using the Host/Mainframe Form Wizard. Before you begin this procedure, refer to the General Guidelines for Setting Up Applications.
2.12.5.5 Configuring a Telnet Application Logon Manually
The following procedure describes the steps for manually configuring or modifying a Telnet logon. Refer to the specific dialogs and controls for more information. Before you begin this procedure, refer to the General Guidelines for Setting Up Applications.
-
Start the application and configure the host emulator.
-
In the Administrative Console, do one of the following:
-
Create a new Host/Mainframe application logon.
or
-
In the left pane, click Applications and select a host/mainframe application.
-
-
Click the General tab in the right pane.
-
Select a logon form from the list and click Edit.
-
In the General tab of the Host/Mainframe form-configuration dialog:
-
Specify one or more Text Matching captions, so that this page can be identified uniquely from other pages. Specify the identifying Text string of the caption and its starting Row and Column numbers.
The row numbers should be relative to the current cursor position and can be negative integers. See the example below.
The column number is an absolute position.
You can also use an asterisk (*) for the row or column as a wildcard.
-
Specify the Fields for credentials. Under Fields, click Edit. In the Edit SendKeys Fields and Actions dialog, select each field, and set the Row and Column for each field to one (1). If needed, specify any additional keystrokes that should follow each field entry.
-
-
If the terminal response-time requires a pause between credential field entries, select the Options tab and type the number of milliseconds to pause in Delay Field.
-
Repeat the steps above for each additional logon form.
-
To add Password Change information, repeat the process with the Password Change tab and the password change dialogs in the target application.
Because the text in a Telnet application scrolls, the row positioning must be set relative to the cursor's row, which is always row one (1). Therefore, the row coordinate for a caption ("Welcome to VAX/VMS_V6.1") that is two rows above the cursor is negative two (-2). The column setting of the start of the caption text is an absolute coordinate; in the example here, nine (9).
| Screen text column | |
|---|---|
| 123456789022345678903234567890123 | |
| Row# | 123456789012345678901234567890123 |
| -4 | |
| -3 | |
| -2 | Welcome_to_VAX/VMS_V6.1_ |
| -1 | |
| 1 | Username: _ |
| 2 | |
| 3 | |
| 4 |
For Logon Manager to identify this sample screen, you would set these text matching criteria (using the Text Matching dialog):
| Match 1 | |
|---|---|
| Text | Welcome to VAX/VMS V6.1 |
| Row | -2 |
| Column | 9 |
| Match 2 | |
|---|---|
| Text | Welcome to VAX/VMS V6.1 |
| Row | -2 |
| Column | 9 |
2.12.6 Bulk-Adding Applications for First-Time Use
After the initial product installation, the First-Time Use Wizard requests various items of information to complete the setup process. If multiple authenticators are installed, the user is prompted to choose a Primary Logon Method. In addition, Logon Manager can also prompt the user for application usernames/IDs and passwords to quickly populate the user's store.
Note:
In order to use Bulk-Add, you must enable First-Time Use.The configuration settings for the First-Time Use Wizard are specified in the ftulist.ini file. You can have Logon Manager prompt users to provide credentials (username/ID, password, third field) for their existing logons. Combining first-time use configuration with predefined logons ensures that users reap the benefits of single sign-on immediately after installation. Alternatively, users can configure their individual logons as they encounter each application.
Note:
All Logon Manager configuration files (includingentlist.ini and ftulist.ini can be created and edited only through the Administrative Console.2.12.6.1 Specifying Applications to Bulk-Add
Note:
Applications must be individually configured to be used in a bulk-add. See Bulk-Adding Applications for First-Time Use.-
Select Applications in the left pane, then select the Bulk-Add tab in the right pane.
-
Click Add.
-
From the Select Application dialog, select the applications to add to this group. (Use Ctrl+click or Shift+click to select multiple entries.)
-
Click OK.
-
Enter or edit the Date Stamp in
yyyymmddformat (for example20130615for June 15, 2013). If this date is later than the last date that a given Agent completed setup, then the Agent activates the Setup Wizard to add the new logons.
To enable a logon for Bulk-Add:
-
Select Applications in the left pane, then select an application.
-
Click the Bulk-Add tab in the right pane.
-
Select Enable Bulk-Add capability for this application.
-
If the user must re-enter one or more fields for confirmation, then select the appropriate Confirm settings.
2.13 Creating New Applications
The Applications tab displays application configuration information and provides access to logon settings.
Click Applications in the left pane to display these tabs in the right pane:
-
The Applications List displaying currently configured logons.
-
The Bulk Add (multiple logon deployment) controls.
Right-click Applications in the left pane to display a shortcut menu with these options:
| Menu Option | Function |
|---|---|
| New Windows App | Configure a new Windows application. Displays the Add Application dialog. |
| New Web App | Configure a new Website application. Displays the Add Application dialog. |
| New Host App | Configure a new mainframe application. Displays the Add Application dialog. |
| Import | Open stored application configurations in a .REG or .INI file. |
| Export | Save one or more application configurations in an .INI file. |
2.13.1 The Applications List
This menu option displays a list of applications with logons configured for use with Logon Manager.
To use this tab:
-
Click Applications in the left pane, then click the Applications List tab in the right pane.
-
To add new applications click Add.
-
To modify a listed application's logon configuration, click an application, then click Edit.
-
To delete one or more logon configurations, click an application (use Ctrl+click or Shift+click to select multiple entries), then click Delete.
2.13.2 Adding an Application
Use the Add Application dialog to begin configuring a new application logon. You can define an application logon from scratch or you can use a stored template that provides pre-configured values for some or all logon settings.
To add an application:
-
Enter a Name for the new logon.
-
Select an Application Type:
-
Windows
-
Web
-
Host/Mainframe
-
-
Do one of the following:
-
Select a template from the Application drop down list and click Next to provide any additional information needed to complete the logon.
-
Leave the Application selection as New [type] Application and click Finish to create an entirely new logon.
-
-
If this application requires authentication by RSA (SecurID/SoftID) token, select the RSA securID check box.
-
Click Finish.
The Form Wizard for the selected Application Type launches. See The Windows Form Wizard, Web Form Wizard, or Host/Mainframe Form Wizard for more information.
To display the Add Application dialog, do one of the following:
-
Right-click Applications in the left pane, then choose the application type (Windows, Web or Host/Mainframe) from the shortcut menu.
or
-
Click Add in the Applications list.
2.13.2.1 Adding an Application from a Template
Use this wizard page to supply application logon configuration settings that are not provided by the application logon template. Settings that must be supplied to complete the logon are marked in the left pane with a red X. 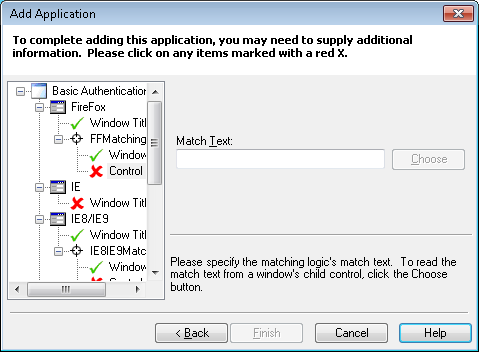
-
In the left pane of the dialog, click a logon setting item that is marked by a red X. The corresponding dialog for supplying the setting appears in the right pane.
-
Enter or choose the requested setting. A green check mark replaces the red X when the setting is completed.
-
Click Finish to close the wizard and add the new application.
To display this page:
-
Do one of the following:
-
Right-click Applications in the left pane, then choose the application type (Windows, Web or Host/Mainframe) from the shortcut menu.
or
-
Click Add in the Applications list.
-
-
In the New Application dialog, select a template from the Application drop down list and click Next.
2.13.3 Creating a New Windows or Java Application Template
You can create a new Windows application template using the Applications menu or the Add Application icon in the Administrative Console, or directly from the window of an open application.
2.13.3.1 Creating a Template Using the Administrative Console
To create a Windows or Java application template using the Administrative Console:
-
In the left pane, right-click Applications then select New Windows App from the shortcut menu. The Add Application dialog appears with the Windows option selected.
-
Enter a Name for the new logon and click OK. The Windows Form Wizard (for configuring new logon forms) appears.
or
-
Click the Add Application icon on the Administrative Console toolbar.
-
Select an application from the Select Window screen. The Windows Form Wizard (for configuring new logon forms) appears.
Continue to The Windows Form Wizard for more information.
2.13.3.2 Configuring a Template Manually
To create a Windows or Java application template manually:
-
Enter the Name of the application.
-
In the AppPathKey group, click Add.
-
In the Add AppPathKey dialog, enter a valid application key (usually the application executable's name, such as
Eudora.exe). Click OK. -
In the Window Titles group click Add, then enter the Window title or click Choose to open the Select Window dialog, where you can select a title from a currently-running application window.
-
Click OK.
2.13.3.3 Creating a Template Using an Open Application
You can create a new template on-the-fly for a Windows application while the application is running.
In order to perform this procedure, both the Administrative Console and the Logon Manager Agent must be running, and you must configure the Agent settings to display the Title Bar Button menu.
-
Launch the application for which you want to create a template.
-
Select Create Template from the application's Title Bar Button menu.

Two things happen:
-
In the application's window, Logon Manager detects the credential fields and highlights them.
-
A condensed version of the Form Wizard appears. Enter information for the following fields:
-
Form Name. This field is pre-filled with the name of the selected application. You can leave this as it is or change it if you want to.
-
Form Type. Select the form type from the drop-down menu:
Logon
Logon Success
Logon failure
Password change
Password change success
Password change failure
-
Add to Template. This field defaults to the New Template selection. Alternatively, the drop-down menu contains the list of all configured Windows application templates to which you might want to add this form.
-
Edit Fields/Hide Details. Toggle this button to expand the window to display the entire Form Wizard, or collapse the window to the simpler Form Wizard.
-
-
Continue to The Windows Form Wizard for more information.
2.13.4 The Windows Form Wizard
Use the Windows Form Wizard to perform any of these tasks:
-
Configure new logons for Windows applications or for Java applets and applications
-
Add new forms to existing logons
-
Create forms for automatic password changes
-
Create forms for supporting a password confirmation field displayed in a separate window
-
Create forms for automatic detection of password change success and failure
The Windows Form Wizard lets you use the application itself to identify its forms, the individual fields, and the submit OK button.
Before you begin this procedure, refer to the General Guidelines for Setting Up Applications for configuring applications. Also see Adding Windows Applications for specific information about configuring Windows application logons.
To display the Windows Form Wizard, do one of the following:
-
Create a new Windows or Java application logon.
or
-
In the Identification tab (Windows), click Wizard.
To configure a form:
-
Start the target application and navigate to the target form. Arrange the Administrative Console and target application windows so that you can see both at the same time.
-
In the Form Wizard, select the type of form you want to configure. The available options are:
-
Logon. Configures a logon form.
-
Logon success. Configures a form that detects a match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's entries and displays the Logon Success dialog. If this form is not present, the Agent captures credentials immediately after the user enters them and clicks OK.
-
Logon failure. Configures a form that detects a non-match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's incorrect entries and displays the Logon Failure dialog. If this form is not present, the Agent immediately informs the user that the credentials are incorrect, displaying either the New Logon dialog or the Retry Logon dialog to allow the user to re-enter credentials.
-
Password change. Configures a password change form.
-
Password confirmation. Configures a new password confirmation form for applications that display their "Confirm password" field in a separate window.
-
Password change success. Configures a form that serves as a match for the target application's password change success message. Since this form does not inject credentials, the Credentials page of the Windows Form Wizard is skipped. When the password change success message is detected, Logon Manager will automatically save the new credentials.
-
Password change failure. Configures a form that serves as a match for the target application's password change failure message and reinjects credentials when the password change failure message is detected. If you select this option, you will be presented with the Credentials page of the Windows Form Wizard in which you will configure the necessary fields.
Refer to Configuring and Diagnosing Logon Manager Application Templates for a full discussion on using the forms above.
-
-
Specify whether the application that you are configuring is running on the Local Computer or a Remote Computer. If you select Remote Computer, enter the path to the application.
Note:
Logon Manager must be running on the computer you select. -
In the Application Window list, select the window to configure. Note that a blinking outline indicates the application window you select.
Use the Application type: dropdown menu to filter the list. An application is classified as either:
-
A standard Windows application.
-
A Java, SAP, or Modern UI application.
-
-
Confirm that you have selected the correct window, then click Next.
-
In the Credential Fields page list, click the Detect Fields button. The Wizard attempts to detect and configure the credential fields and marks them accordingly:
-
Username/ID
-
Password (Logon forms only)
-
Old Password (password change forms only)
-
New password (password change forms only)
-
Confirm new password (password change and password confirmation forms only)
-
Submit button
-
-
Confirm that the Wizard has selected the correct fields. You can modify a selection, if necessary:
-
Select a field to configure; for example, the logon window's user ID field. In the application's window, a blinking outline indicates the field corresponding to your current selection.
-
Confirm that you have selected the correct field, then right-click the selected item and choose the field type (for example, UserID) from the shortcut menu. The corresponding icon appears to the left of the item. To deselect an item, right-click the item and choose None from the shortcut menu.
Note:
Password change success forms do not inject credentials and thus do not require you to configure any fields. In such cases, proceed to step 8, as the Credential Fields page will not be displayed.The Class and Text columns provide cues to the fields. For example, text boxes appear as "Edit" Class; password fields usually have the Text value *** HIDDEN ***.
-
-
Repeat this process for each field required to complete the logon form. You can configure up to four fields in all.
-
Confirm that you have configured the necessary fields and button, then click Next A summary page appears, listing your configuration.
-
Do one of the following:
-
Click Back to return to a previous page and make corrections.
-
Click Finish to complete the logon configuration and close the Form Wizard.
-
2.13.4.1 Selecting the Window Title
Use the Select Window dialog to choose the title of an application's logon or password change window.
Select the logon or password change window and click OK.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
2.13.4.2 The Windows Form Wizard Application Tab
Use this Form Wizard page to select the application's logon or password/PIN change window.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently available applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.3 The Windows Form Wizard Credential Field Tab
Use this Form Wizard page to select the fields of the application's logon or password change window.
| Control | Function |
|---|---|
| Credential Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID or Text, to sort the list. Right-click a field in the list to display a shortcut menu of field types and the submit control:
|
| Refresh | Updates the field list. |
| Use "Send Keys" for this form, do not use Control IDs | Indicates that the Agent should transmit logon data to this form as a series of keystrokes, rather than by addressing individual fields by Control ID. See SendKeys for more information. |
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Detect Fields | Scans the field list and attempts to match them with field types. Note that although Detect Fields is usually accurate with typical applications, the fields should be verified for proper field types. |
| Refresh | Updates the field list. |
| Back | Go back to the previous Wizard page |
| Next | Go forward to the next Wizard page. |
The Summary screen displays the results of the Wizard. Do one of the following:
-
Click Finish to save your settings and close the Wizard.
or
-
Click Back to return to a previous page and modify your settings.
2.13.4.4 Windows Form Wizard for RSA SecurID Applications
Use the Windows Form Wizard to perform any of these tasks:
-
Configure new logons for RSA SecurID Windows applications
-
Add new forms to existing RSA SecurID logons
-
Create forms for automatic PIN changes
-
Create forms for supporting a PIN confirmation field displayed in a separate window
-
Create forms for automatic detection of PIN change success and failure
The Windows Form Wizard lets you use the application itself to identify its forms, the individual fields, and the submit OK button.
Before you begin this procedure, refer to the General Guidelines for Setting Up Applications for configuring applications. Also see Adding Windows Applications for specific information about configuring Windows application logons.
To display the Windows Form Wizard, do one of the following:
-
Create a new Windows or Java application logon. Be sure to select the RSA SecurID check box in the Add Application dialog.
or
-
In the Identification tab (for a Windows form), click Wizard.
To configure a form:
-
Start the target application and navigate to the target form. Arrange the Administrative Console and target application windows so that you can see both at once.
-
In the Form Wizard, select the type of form you want to configure. The available options are:
-
SecurID Logon. Configures a SecurID logon form.
-
PIN Change. Configures a PIN change form.
-
Confirm PIN. Configures a new PIN confirmation form for applications that display their "Confirm PIN" field in a separate window.
-
Logon Success. Configures a form that serves as a match for the target application's Logon Success message. Since this form does not inject credentials, the Credentials page of the Windows Form Wizard is skipped. When the logon success message is detected, Logon Manager will automatically save the new credentials.
-
Logon Failure. Configures a form that serves as a match for the target application's logon failure message and reinjects credentials when the logon failure message is detected. If you select this option, you will be presented with the Credentials page of the Windows Form Wizard in which you will configure the necessary fields.
-
PIN Change Success. Configures a form that serves as a match for the target application's PIN change success message. Since this form does not inject credentials, the Credentials page of the Windows Form Wizard is skipped. When the PIN change success message is detected, Logon Manager will automatically save the new credentials.
-
PIN Change Failure. Configures a form that serves as a match for the target application's PIN change failure message and reinjects credentials when the PIN change failure message is detected. If you select this option, you will be presented with the Credentials page of the Windows Form Wizard in which you will configure the necessary fields.
-
-
In the Application Window list, select the window to configure. Note that a blinking outline indicates the application window you select.
-
Specify whether the application is running on the Local Computer or a Remote Computer. If you select Remote Computer, enter the path to the application.
Note:
Logon Manager must be running on the computer you select. -
In the Application Window list, select the window to configure. Note that a blinking outline indicates the application window you select.
Use the Application type: dropdown menu to filter the list. An application is classified as either:
-
A standard Windows application.
-
A Java, SAP, or Modern UI application.
-
-
Confirm that you have selected the correct window, then click Next.
-
In the Credential Fields page, for each credential field:
-
Select a field to configure; for example, the logon window's user ID field. In the application's window, a blinking outline indicates the field corresponding to your current selection.
-
Confirm that you have selected the correct field, then right-click the selected item and choose the logon field type (for example, UserID) from the shortcut menu. The corresponding icon appears to the left of the item. To deselect an item, right-click the item and choose None from the shortcut menu.
Note:
New PIN Acceptance forms do not inject credentials and thus do not require you to configure any fields. In such cases, proceed to step 7, as the Credential Fields page will not be displayed.The Class and Text columns provide cues to the fields. For example, text boxes appear as "Edit" Class; PIN fields usually have the Text value *** HIDDEN ***
-
-
Repeat this process for each field required to complete the logon form. You can configure up to four fields in all.
-
Confirm that you have configured the necessary fields and button, then click Next. A summary page appears, listing your configuration.
-
Do one of the following:
-
Click Back to return to a previous page and make corrections.
-
Click Finish to complete the logon configuration and close the Form Wizard.
-
2.13.4.4.1 Credential Field (Windows Form Wizard for RSA-securID Applications)
Use this Form Wizard page to select the fields of the application's logon or password change window.
| Element | Function |
|---|---|
| Credential Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, or Text, to sort the list. Right-click a field in the list to display a shortcut menu of field types and the submit control:
|
| Refresh | Updates the field list. |
| Use "Send Keys" for this form, do not use Control IDs | Indicates that the Agent should transmit logon data to this form as a series of keystrokes, rather than by addressing individual fields by Control ID. See SendKeys for more information. |
| Element | Function |
|---|---|
| Refresh | Updates the field list. |
| Back | Go back to the previous Wizard page |
| Next | Go forward to the next Wizard page. |
2.13.4.5 The Windows Form Wizard Identification Tab
Use the Identification (Windows) tab to modify program and window information about a Windows application logon configuration.
-
Configure a logon manually by adding, editing, or deleting entries in the AppPathKeys and Window Titles lists.
or
-
Use The Windows Form Wizard to define windows, titles and fields by pointing and clicking.
To display this tab, do one of the following:
-
Create a new Windows application logon.
or
-
In the left pane, click Applications and select a Windows application.
-
Click the General tab in the right pane.
-
Select a logon form from the list and click Edit.
The Windows form-configuration dialog appears, displaying the General tab.
| Control | Function |
|---|---|
| Form name | Name of the application logon form. |
| AppPathKeys | The Windows registry key identifying an application associated with this logon to match against running processes. (Usually the application executable's name.) |
| Window Titles | Text matched against logon window titles to identify logon requests. Click Choose to select a title from a currently-running application window. |
| Disabled | Select to disable this Windows template. This can be used with the Sort Order feature to disable certain Web pop-ups.
This feature is useful in a situation where an application has hundreds of windows titles defined using regular expressions (see Regular Expression Syntax for more information) or wild cards, but a few of those window titles should not be responded to. Rather than creating hundreds of templates to respond to, an administrator can define the window title to match (with regular expressions or wild cards), and exclude those that should not be matched by creating a disabled template for them. |
| Wizard | Start the Windows Form Wizard for configuring an application visually. |
2.13.4.6 The Windows Form Wizard Fields Tab
Use the Fields (Windows) tab to define how the Agent interacts with the fields of the logon form. You can identify one of the following for the currently-selected application form:
-
Up to four logon fields (user ID, password, etc.), using Control IDs
-
A series of keystrokes (with optional timings) that fill-in and submit the logon form, using SendKeys.
To display this tab, do one of the following:
-
Create a new Windows application logon.
or
-
In the left pane, click Applications and select a Windows application.
-
Select the General tab in the right pane.
-
Select a logon form from the list and click Edit.
-
In the Windows form-configuration dialog General tab, click the Fields tab.
| Control | Function |
|---|---|
| Transfer Method (choose one) |
|
| Fields | Fields with transfer methods configured for this logon form. You can:
|
2.13.4.6.1 The ControlID Dialog
Use the Control ID dialog to identify the fields and the submit button of a logon form in order to configure the Manager's response.
| Control | Function |
|---|---|
| Field | Select the credential data that the control represents, or identify the control as the Submit (OK) button.
|
| Control ID | Enter the Control ID of the selected field or button. |
| Skip field if control is disabled | Select this option to prevent the Agent from entering data if the selected field is set not to accept user entry. |
To display this dialog, do one of the following:
-
Create a new Windows application logon.
or
-
In the left pane, select Applications and select a Windows application.
-
Select the General tab in the right pane.
-
Do one of the following:
-
Select a logon form from the list and click Edit.
or
-
Click Add to configure a new form.
-
-
From the Windows form configuration dialog General tab, do one of the following:
-
Click the Fields tab, select Control IDs as the Transfer Method, then click Edit.
or
-
Click the Matching tab, click Add, then click Control ID.
-
2.13.4.7 SendKeys for a Windows Application Logon
Use the SendKeys dialog to specify a series of keystrokes that Logon Manager should transfer to the logon form.
Use the SendKeys option for Windows applications that:
-
Cannot receive credentials from the Windows message queue or by other techniques the Agent normally uses to send credentials.
-
Do not use standard Windows controls that have Control IDs.
-
Dynamically generate controls or do not use Windows controls at all (for example, Flash applications).
The New Actions list box in the right pane of the SendKeys dialog provides the keystroke options for each action. Highlight the action for which you want to configure SendKeys, and select or type the options you need on for each action. Click the Insert button to add the key or action to the series.
Note:
For East-Asian Language Applications: When adding information using SendKeys in an East Asian-language (Chinese, Japanese, Korean) application template, you must insert an Enter key press preceding the Tab key that advances to the next field. The Enter key signals the Input Method Editor that you have completed the field and allows the IME to differentiate the credentials fields.Journal Hook SendKeys for East-Asian languages is not compatible with Logon Manager.
Your selections appear in the Current Actions list in the left pane:
-
To change the order of the series, select an item and click the Up or Down arrows to move it.
-
To delete an item, select it, and click Delete.
-
To edit an item, select it, and click Edit. The Edit Action dialog opens. Edit the fields as necessary and click OK.
| New Action | Control | Function |
|---|---|---|
| Fields | Field Type | Select a credential item from the list to add to the series.
|
| Character to insert after field | Select a keystroke to insert automatically after the field is filled:
Also see Special Keys, below. |
|
| Inject directly into control | Injects the credential directly into the control. Click the ellipsis ("…") button to open the Choose Control ID dialog.
Note: When using SendKeys, the application is treated as a Windows application. The controls that appear in the Choose Control ID dialog indicate whatever Windows controls Logon Manager can find. |
|
| Insert | Add the current selection to the series. | |
| Click | Click at a coordinate | Simulates a mouse click at the X, Y coordinate specified.
X: Choose the X coordinate for the mouse click. Y: Choose the Y coordinate for the mouse click. Relative to the: Select where the mouse click will be relative to:
Mouse button: Select which mouse button will be clicked:
|
| Click on a control | This option is similar to clicking at a specified coordinate, except that Logon Manager determines where the control is and simulates a click in the center of the control. Click the ellipsis ("…") button to open the Choose Control ID dialog.
Note: When using SendKeys, the application is treated as a Windows application. The controls that appear in the Choose Control ID dialog indicate whatever Windows controls Logon Manager can find. |
|
| Insert | Add the click selection to the series. | |
| Run Task | Command line to run | Enter a Command line to be executed. This feature allows you to run a program in the middle of entering keystrokes.
Click the ellipsis ("…") button to open the Choose Control ID dialog. Note: Virtual key codes cannot be used within the command line (the initial backquote character will terminate the command line). |
| Expected return code | Enter the expected return code. The rest of the SendKeys script is discarded if this value is not returned. | |
| Time out (sec.) | Enter the number of milliseconds to wait for the task to complete. The rest of the Sendkeys script is discarded if this timeout is reached. The maximum timeout period is five (5) seconds. | |
| Insert | Add the task to the series. | |
| Delay | Length of delay (in seconds) | Type or select a delay between keystrokes. |
| Insert | Add the delay to the series. | |
| Set Focus | Set focus to control | Sets the focus to the control. Click the ellipsis ("…") button to open the Choose Control ID dialog.
Note: When using SendKeys, the application is treated as a Windows application. The controls that appear in the Choose Control ID dialog indicate whatever Windows controls Logon Manager can find. |
| Insert | Add the focus to the series. | |
| Text | Enter text to insert | Type any literal text to add to the series. |
| Insert | Add the text to the series. | |
| Special Keys | Category/Keys | Choose a keystroke category (for example, Movement keys) from the left list, then a specific key (for example, Page Down) from the right list. |
| Key Press | Insert the key as a single keystroke (default). | |
| Key Down/Up | Insert the key as a pair of actions: key-press and key-release. This option lets you insert other keystrokes between these actions to indicate one or more keys held down as another is typed, as for a "hot key" combination that moves the focus to a specific text box.
For example, to insert the keystroke Alt+P, select the Key Down/Up option, then select Modifier for the Category and Alt for the Key. and click Insert. This inserts two actions: [Down:Alt] and [Up:Alt]. Select the Text tab and enter P in the text box. In the left pane, select [Up:Alt] and click Insert. The P is inserted between the two Alt-key actions, producing Alt-P. |
|
| Insert | Add the keystroke to the series. |
To display this dialog, do one of the following:
-
Create a new Windows application logon.
or
-
In the left pane, click Applications and select a Windows application.
-
Click the General tab in the right pane.
-
Do one of the following:
-
Select a logon form from the list and click Edit.
or
-
Click Add to configure a new form.
The Windows form-configuration dialog opens, displaying the General tab.
-
-
Click the Fields tab, select SendKeys as the Transfer Method, then click Edit.
2.13.4.8 Kiosk Manager SendKeys (for a Windows Application)
Use the SendKeys dialog to specify a series of keystrokes that Kiosk Manager should transfer to the logon form.
Note:
See Adding Telnet Applications for information about configuring logons for Telnet applications.The tabs in the right pane of the SendKeys dialog provide the keystroke options. Select or type the options you need on each tab. Click the Insert button to add the key or action to the series.
Your selections appear in the list in the left pane. To change the order of the series, select an item and click the up or down arrows to move it. To delete an item, select it and click Remove.
| Tab | Function | Input |
|---|---|---|
| Text tab | Enter text to insert | Type any literal text to add to the series. |
| Insert | Add the text to the series. | |
| Delay tab | Length of delay (in seconds) | Type or select a delay between keystrokes. |
| Insert | Add the delay to the series. | |
| Special Keys tab | Category/Keys | Choose a keystroke category (for example, Movement keys) from the left list, then a specific key (for example, Page Down) from the right list. |
| Key Press | Insert the key as a single keystroke (default) | |
| Key Down/Up | Insert the key as a pair of actions: key-press and key-release. This option lets you insert other keystrokes between these actions to indicate one or more keys held down as another is typed, as for a "hot key" combination that moves the focus to a specific text box.
For example, to insert the keystroke "Alt+P", choose the Key Down/Up option, then select Modifier for the Category and Alt for the Key. and click Insert. This inserts two actions: [Down:Alt] and [Up:Alt]. Select the Text tab and type P in the text box. In the left pane, select [Up:Alt] then click Insert. The P is inserted between the two Alt-key actions, producing "Alt-P." |
|
| Insert | Add the keystroke to the series. |
2.13.4.9 Matching Tab for Configuring a Windows Application
Use the Matching (Windows) tab to distinguish among similar forms within the same Windows application. The supported form types, referred to here as target forms, are:
-
Logon
-
Password Change
-
Password Confirmation
-
Logon Success
-
Logon Failure
-
Password Change Success
-
Password Change Failure
Note:
Unlike the "Logon," "Change Password," "Confirm," and "Ignore" match types, these matches cannot be explicitly selected by the user. They are determined by form type.
| Element | Function |
|---|---|
| Allowable Class | Click Choose to identify the logon or password-change window class that must be present in order to execute this logon. This is useful for applications that present logon or password-change windows with non-standard class names. Displays the Select Window dialog. |
| Regular Expression | Select whether the Allowable Class uses a regular expression. |
| Ignore this Window Class | Click Choose to select the logon or password-change window to ignore when executing a logon. This is useful for applications that use hidden logon or password-change dialogs or that present duplicate dialogs. Displays the Select Window dialog. |
| Regular Expression | Select if the ignored Window Class uses a regular expression. |
| Attach to window's Message Queue | Select to hold on to the target window while sending credentials. |
| Preset Focus | Select to set the focus on a logon field before the Agent places data in the field. |
| System Logon | (Reserved) |
| Use WM_CHAR messages to fill controls | Some applications require that you enter passwords via a keyboard and not set text commands. Enabling this setting simulates keyboard entry in an alternate way by setting text within controls. |
| Allow fallback from ControlIDs to SendKeys | Indicates whether to use SendKeys to enter credentials if direct injection using ControlIDs fails. Default is Yes. |
| Sort Order | Specify the order in which Logon Manager searches templates for window class titles containing regular expressions. By setting sort order, you increase the efficiency of your search without eliminating less precise matches. If you do not assign a sort order to a template, Logon Manager checks templates in ascending order (lower values are checked first). Default is 1000. |
The Agent uses the match criteria you supply to distinguish among similar forms. This lets the Agent apply a single set of user credentials appropriately to these multiple forms. You can use also use matching to identify forms that the Agent should ignore.
Do one of the following:
-
Click Add to create a new matching criterion.
or
-
Select a Match and click Edit.
The Matching dialog appears.
Note:
The easiest and most efficient way to create match criteria is by using the Control Match Wizard. The Wizard lets you specify match criteria by selecting elements from the target form itself. You can also create and modify match criteria manually.
To display this tab, do one of the following:
-
Create a new Windows application logon.
or
-
In the left pane, click Applications and select a Windows application.
-
Click the General tab in the right pane.
-
Select a form from the list and click Edit.
-
Select the Matching tab.
2.13.4.10 The Windows Form Wizard Matching Dialog
Use this dialog to create match criteria that the Agent uses to distinguish among similar target forms that use the same credential data. This lets the Agent apply a single set of user credentials appropriately to these multiple forms. To display this dialog, from the Matching tab (for configuring a Windows logon form) click Add.
The easiest and most efficient way to create match criteria is through the Control Match Wizard. The Wizard lets you specify match criteria by selecting elements from the target form itself. You can also create and modify match criteria manually.
2.13.4.11 Creating Match Criteria Using the Wizard
Click Wizard and follow the onscreen instructions.
2.13.4.12 Creating or Modifying Match Criteria Manually
To create or modify matching criteria manually:
-
Enter a Match name and select the Type of target form.
-
Add or edit the Window Titles that the target form displays, or select Use Titles from Main.
-
Add or edit the Control Matching items; these are criteria based on the properties of form objects (such as a text caption or a control class). Together these items uniquely identify the target form.
-
Add or edit the Control IDs of the target form's credential fields.
-
Click OK.
| Control | Function |
|---|---|
| Match Name | Enter or edit the name for the Match |
| Type | Select the type of form to match:
Note: Unlike the Logon, Change Password, Confirm, and Ignore match types, these matches cannot be explicitly selected by the user. They are determined by form type. |
| Windows Titles | Click Use Titles from Main to copy the Windows Titles in the General tab for this logon or click Add to enter titles manually. |
| Control Matching | Click Add (or select a matching item and click Edit) to display the Control Matching dialog. |
| Control ID | Click Add (or select a Control ID item and click Edit) to display the Control ID dialog. |
| Wizard | Start the Control Match Wizard. |
2.13.4.13 Add or Edit a Title on the Windows Matching Tab
Use this dialog to add or modify the text string that the Agent uses to detect specific application windows (for example, for logon entry or password change) by their window title.
2.13.4.13.1 Specifying a Window Title for Matching
To specify a window title for matching:
-
Select one of the following (see Matching Expressions).
-
Exact match
-
Use wildcards (does not apply to Kiosk Manager)
-
Use regular expression (does not apply to Kiosk Manager)
-
-
Type (or edit) the Window Title or a matching expression.
-
Click OK.
2.13.4.13.2 Matching Expressions
For applications that have varying text in their URLs, you can use substrings or regular expressions to specify how to match the variable text.
| Element | Usage |
|---|---|
| Wildcards |
Note: This does not apply to Kiosk Manager. |
| Regular Expressions | You can also use the set of regular expressions to specify a string pattern that the Agent should recognize as a match.
Note: This does not apply to Kiosk Manager. |
2.13.4.13.3 Matching Environment Variables
For applications that include the user's name in the URL (as derived from the DOMAINUSER environment variable in the workstation operating system), select Exact as the matching criterion, and use one of the following substitution tokens in the match string:
| Variable | Usage |
|---|---|
%DOMAINUSER% |
User name exactly as derived from the environment variable |
%UC%%DOMAINUSER% |
User name converted to all upper case |
%LC%%DOMAINUSER% |
User name converted to all lower case |
Example
The following Window Title entry matches a password-change window title that includes the username:
Password Expired - %UC%%DOMAINUSER%
2.13.4.14 Control Matching
Use the Control Matching dialog to specify a match criterion based on the properties of a target-form control (such as a text caption or a control style).
| Control | Function | |
|---|---|---|
| Control ID | Type the numeric identifier of the control. | |
| Match Condition | Select one property of the control, select a relation (Equals or Not Equal, Equals regular expression, Not equals regular expression), and type or select the condition that should (or should not) be met. The valid conditions for each property are: | |
| Class | Edit or Static control. | |
| Style | A decimal numeric identifier for the aggregate of styles applied to the control. | |
| Text | A literal string. | |
Click OK to save and exit the dialog or Cancel to exit without changes.
2.13.4.15 Control ID Dialog (Windows Fields Tab)
Use the Control ID dialog to identify the fields and the Submit button of a logon form in order to configure the Agent's response.
| Control | Function |
|---|---|
| Field | Select the credential data that the control represents, or identify the control as the Submit (OK) button.
|
| Control ID | Enter the Control ID of the field or button. |
| Control Type | Select the control type:
|
Note:
In most cases, you can use the Windows Form Wizard to identify fields and Control IDs.2.13.4.16 Control Match Wizard
Use the Control Match Wizard to define match criteria by choosing from the windows and controls of the target application. The Agent uses match criteria to identify a target form, such as a password-change dialog, that is similar to the currently selected logon. The Agent then supplies data to the matched target form using the same credentials as the original logon. You can also use match criteria to specify target forms similar to the current logon that the Agent should ignore.
To create match criteria using the Wizard:
-
Start the target application and navigate to the target form. Arrange the Administrative Console and target application windows so that you can see both at the same time.
-
Select a form Match Type, then follow the onscreen instructions or help topics.
-
Ignore
-
Logon
-
Password Change
-
Password Confirm
-
See the Matching Tab for Configuring a Windows Application for more information.
To display the Control Match Wizard:
-
From the Matching tab, select Add (for configuring a Windows logon form). The Matching dialog appears.
-
Click Wizard.
2.13.4.17 Ignore App Window
Use this Wizard page to choose the application window that the Agent should recognize.
-
Select the application window that the Agent should ignore from the Window List.
-
Click Next to display the Match Fields page.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.18 Ignore Match Fields
Use this Wizard page to choose a set of match fields: one or more window objects that uniquely identify the application window that the Agent should recognize. You can identify a match field by its Class (the type of control, such as Edit or Static), its Style (the aggregate of its properties identified by a number), or its Text.
-
In the field list, right-click a field and select the match criteria.
-
Click Next to display the Summary page.
| Control | Function |
|---|---|
| Match Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, Text or Style) to sort the list. Right-click a field in the list to display a shortcut menu of match criteria:
|
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Refresh | Updates the list. |
| Back | Goes back to the previous Wizard page. |
| Next | Goes forward to the next Wizard page. |
2.13.4.19 Logon App Window
Use this Wizard page to choose the application window that the Agent should recognize.
-
Select the application window that the Agent should recognize as a logon form from the Window List.
-
Click Next to display the Match Fields page.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.20 Logon Match Fields
Use this Wizard page to choose a set of match fields: one or more window objects that uniquely identify the application window that the Agent should recognize. You can identify a match field by its Class (the type of control, such as Edit or Static), its Style (the aggregate of its properties identified by a number), or its Text.
-
In the field list, right-click a field and select the match criteria
-
Click Next to display the Credentials page.
| Control | Function |
|---|---|
| Match Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, Text, or Style) to sort the list. Right-click a field in the list to display a shortcut menu of field types:
|
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.21 Logon Credential
Use this Wizard page to identify the field in which the Agent should supply credential data.
-
In the field list, right-click a field and select the credentials.
-
Click Next to display the Summary page.
| Control | Function |
|---|---|
| Credential Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, Text, or Style) to sort the list. Right-click a field in the list to display a shortcut menu of field types:
|
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.22 Password Change App Window
Use this Wizard page to choose the application window that the Agent should recognize.
-
Select the application window that the Agent should recognize as a password-change form from the Window list.
-
Click Next to display the Match Fields page.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.23 Password Change Match Fields
Use this Wizard page to choose a set of match fields: one or more window objects that uniquely identify the application window that the Agent should recognize. You can identify a match field by its Class (the type of control, such as Edit or Static), its Style (the aggregate of its properties identified by a number), or its Text.
-
In the field list, right-click a field and select the match criteria
-
Click Next to display the Credentials page.
| Control | Function |
|---|---|
| Match Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, Text, or Style) to sort the list. Right-click a field in the list to display a shortcut menu of field types:
|
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.24 Password Change Credential
Use this Wizard page to identify the field in which the Agent should supply credential data.
-
In the field list, right-click a field and select the credentials.
-
Click Next to display the Summary page.
| Control | Function |
|---|---|
| Credential Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, Text, or Style) to sort the list. Right-click a field in the list to display a shortcut menu of field types:
|
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.25 Password Confirm App Window
Use this Wizard page to choose the application window that the Agent should recognize.
-
Select the application window that the Agent should recognize as a password-confirmation form from the Window list.
-
Click Next to display the Match Fields page.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.26 Password Confirm Match Fields
Use this Wizard page to choose a set of match fields—one or more window objects that uniquely identify the application window that the Agent should recognize. You can identify a match field by its Class (the type of control, such as Edit or Static), its Style (the aggregate of its properties identified by a number), or its Text.
-
In the field list, right-click a field and select the match criteria
-
Click Next to display the Credentials page.
2.13.4.27 Password Confirm Credential
Use this Wizard page to identify the field in which the Agent should supply credential data.
-
In the field list, right-click a field and select the credentials.
-
Click Next to display the Summary page.
| Control | Function |
|---|---|
| Credential Fields | Displays the fields of the currently selected application window. Click on the headers (Class, ID, Text, or Style) to sort the list. Right-click a field in the list to display a shortcut menu of field types:
|
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individuals fields generated by native Control IDs. |
| Refresh | Updates the list. |
| Back | Go back to the previous Wizard page. |
| Next | Go forward to the next Wizard page. |
2.13.4.28 Options Tab for Configuring a Windows Application
Use the Options (Windows) tab to refine properties of the currently-selected application logon form for special configurations.
To display this tab, do one of the following:
-
Create a new Windows application logon.
or
-
In the left pane, click Applications and select a Windows application.
-
Click the General tab in the right pane.
-
Select a logon form from the list and click Edit.
-
Select the Options tab.
2.13.4.28.1 Select Window [Class]
The Select Window dialog lets you select the class name for an onscreen window. Use this dialog to specify a window class that the Agent should allow or that it should ignore.
The Select Window dialog displays when you select one of the following options in the Options tab for a Windows logon.
-
Allowable Class. Select a logon or password-change window class that must be present in order for the Agent to execute a logon.
-
Ignore this Window Class. Select a logon or password-change window class that should be ignored when detecting credential fields.
| Control | Function |
|---|---|
| Window List | Displays the windows of currently applications. Click on the column heads to sort the list. |
| Show hidden window | Select to include hidden windows in the Window list. |
2.13.5 Creating a New Web Application Template
The Web Form Wizard simplifies the process of creating a new Web application template. You can launch the Web Form Wizard using the Applications menu or the Add Application icon in the Administrative Console, or directly from the window of an open application.
2.13.5.1 Creating a Template Using the Administrative Console
To create a template using the Administrative Console:
-
In the left pane, right-click Applications then select New Web App from the shortcut menu. The Add Application dialog appears with the Web option selected.
-
Enter a Name for the new logon and click OK. The Web Form Wizard (for configuring new logon forms) launches.
or
-
Click the Add Application icon (below) on the Administrative Console toolbar.

-
Select a Web application from the Select Window screen. The Web Form Wizard (for configuring new logon forms) launches.
2.13.5.2 Creating a Template Using an Open Application
You can create a new template on-the-fly for a Web application while the application is running.
In order to perform this procedure, both the Administrative Console and the Logon Manager Agent must be running, and you must configure the Agent settings to display the Title Bar Button menu.
-
Open a browser and navigate to the URL for which you want to create a template.
-
Select Create Template from the browser's Title Bar Button menu.

The Web Form Wizard (for configuring new logon forms) launches.
2.13.5.3 Web Form Wizard
The Web Form Wizard lets you browse the Web application itself to capture the identifiers for its logon or password-change windows, the individual fields, and the Submit (OK) button. To display the Web Form Wizard:
-
Create a New Web application.
-
In the New Web Application configuration dialog, click Wizard. The Web Form Wizard appears.
Note:
When using a workstation running at 800x600 resolution, buttons are missing from the bottom of the Web Form Wizard. The wizard is also extremely slow to start at this resolution. Oracle recommends that you set the resolution on your workstation to a higher resolution.2.13.5.4 Configuring a Web Application Using the Wizard
To configure a Web Application with the Web Form Wizard:
-
In the first Wizard dialog that appears, select the type of application form you want to configure. The available options are:
-
Logon. Configures a logon form.
-
Logon success. Configures a form that detects a match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's entries and displays the Logon Success dialog. If this form is not present, the Agent captures credentials immediately after the user enters them and clicks OK.
-
Logon failure. Configures a form that detects a non-match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's incorrect entries and displays the Logon Failure dialog. If this form is not present, the Agent immediately informs the user that the credentials are incorrect, displaying either the New Logon dialog or the Retry Logon dialog to allow the user to re-enter credentials.
-
Password change. Configures a password change form.
-
Password confirmation. Configures a form that verifies that the user's second password entry in a password change form is identical to the first password entry.
-
Password change success. Configures a form that serves as a match for the target application's password change success message. Since this form does not inject credentials, the Credentials page of the Web Form Wizard is skipped. When the password change success message is detected, Logon Manager will automatically save the new credentials.
-
Password change failure. Configures a form that serves as a match for the target application's password change failure message and reinjects credentials when the password change failure message is detected. If you select this option, you will be presented with the Credentials page of the Web Form Wizard in which you will configure the necessary fields.
Refer to Configuring and Diagnosing Logon Manager Application Templates for a full discussion on using the forms above.
Note:
If you are editing an existing form, this dialog will not appear.
-
-
In the Web Form Wizard, enter the Web Address (URL) of the Web site and click Go. The top pane of the Wizard acts as a web browser window. You can resize the Wizard's window as needed.
-
In the top pane, navigate to the Web site's logon form. When the Wizard detects one or more forms in a web page, it lists the forms and their elements (fields and buttons) in the bottom pane.
-
Click the Detect Fields button. The Wizard attempts to detect and configure the credential fields and marks them accordingly:
-
Username/ID
-
Password
-
Old Password (password change forms only)
-
New Password (password change forms only)
-
Submit button.
-
-
(Optional) Select Use ordinals instead of names. The Credential Fields Screen displays the fields, assigning Control IDs by location order instead of using native (dynamic) Control IDs.
-
(Optional) Select Show non-input fields. The Administrative Console detects fields that have input functionality but into which you cannot enter information, such as IMG tags that function as Submit buttons, and includes these fields in the Web Form Wizard fields list.
-
(Optional) Select Allow multiple field designation. The Administrative Console recognizes multiple fields that require the same credential, such as enter and confirm password fields, or a page with the same field on two forms.
-
Confirm that the Wizard has selected the correct fields. You can modify a selection, if necessary:
-
If you are editing an existing template, you may change the form type using the Form Type drop-down at the lower right. Keep in mind that if you do so, you will need to reconfigure the template (reassign fields, and so on). Only fields relevant to a given form type are displayed when that form type is selected.
-
Identify and select a field from the list in the bottom pane. (The Element and Type descriptions provide cues.) In the top pane, a blinking outline indicates the corresponding field or button you have selected.
-
Confirm that you have selected the correct field, then right-click the selected item and choose from the shortcut menu (for example, UserID). An icon appears to the left of the item. To deselect an item, right-click the item and select None from the shortcut menu.
-
-
Confirm that the Wizard has selected the correct fields. You can modify a selection, if necessary:
-
If you are editing an existing template, you may change the form type using the Form Type drop-down at the lower right. Keep in mind that if you do so, you will need to reconfigure the template (reassign fields, and so on). Only fields relevant to a given form type are displayed when that form type is selected.
-
Identify and select a field from the list in the bottom pane. (The Element and Type descriptions provide cues.) In the top pane, a blinking outline indicates the corresponding field or button you have selected.
-
Confirm that you have selected the correct field, then right-click the selected item and choose from the shortcut menu (for example, UserID). An icon appears to the left of the item. To deselect an item, right-click the item and select None from the shortcut menu.
-
-
Confirm that the Wizard has selected the correct fields. You can modify a selection, if necessary:
-
If you are editing an existing template, you may change the form type using the Form Type drop-down at the lower right. Keep in mind that if you do so, you will need to reconfigure the template (reassign fields, and so on). Only fields relevant to a given form type are displayed when that form type is selected.
-
Identify and select a field from the list in the bottom pane. (The Element and Type descriptions provide cues.) In the top pane, a blinking outline indicates the corresponding field or button you have selected.
-
Confirm that you have selected the correct field, then right-click the selected item and choose from the shortcut menu (for example, UserID). An icon appears to the left of the item. To deselect an item, right-click the item and select None from the shortcut menu.
-
-
Repeat this process for each field required to complete the logon form. You can configure up to four fields in all.
-
Repeat the two previous steps for each field required to logon. You can configure up to four fields in all.
-
When you have completed your configuration click OK to save it and close the Web Form Wizard.
2.13.5.5 Web Form Wizard (for RSA SecurID Applications)
Use the Web Form Wizard to perform any of these tasks:
-
Configure new logons for RSA SecurID Windows applications
-
Add new forms to existing RSA SecurID logons
-
Create forms for automatic PIN changes
-
Create forms for automatic detection of PIN change success and failure
The Web Form Wizard lets you browse the Web application itself to capture the identifiers for its forms and windows, the individual fields, and the submit (OK) button. To display the Web Form Wizard:
-
Create a new Web application. Be sure to select the RSA SecurID check box in the Add Application dialog.
-
In the New Web Application configuration dialog, click Wizard. The Web Form Wizard appears.
Note:
When using a workstation running at 800x600 resolution, buttons are missing from the bottom of the Web Form Wizard. The wizard is also extremely slow to start at this resolution. Oracle recommends that you set the resolution on your workstation to a higher resolution.
To configure a Web Application Using the RSA SecurID Wizard
-
In the dialog that appears, select the type of application form you want to configure. The available options are:
-
SecurID Logon. Configures a SecurID logon form.
-
SecurID Logon success. Configures a form that detects a match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's entries and displays the Logon Success dialog. If this form is not present, the Agent captures credentials immediately after the user enters them and clicks OK.
-
SecurID Logon failure. Configures a form that detects a non-match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's incorrect entries and displays the Logon Failure dialog. If this form is not present, the Agent immediately informs the user that the credentials are incorrect, displaying either the New Logon dialog or the Retry Logon dialog to allow the user to re-enter credentials.
-
PIN change. Configures a PIN change form.
-
PIN confirmation. Configures a form that verifies that the user's second password entry in a password change form is identical to the first password entry.
-
PIN change success. Configures a form that serves as a match for the target application's PIN change success message. Since this form does not inject credentials, the Credentials page of the Web Form Wizard is skipped. When the PIN change success message is detected, Logon Manager will automatically save the new credentials.
-
PIN change failure. Configures a form that serves as a match for the target application's PIN change failure message and reinjects credentials when the PIN change failure message is detected. If you select this option, you will be presented with the Credentials page of the Web Form Wizard in which you will configure the necessary fields.
Refer to Configuring and Diagnosing Logon Manager Application Templates for a full discussion on using the forms above.
Note:
If you are editing an existing form, this dialog will not appear.
-
-
In the Web Form Wizard, enter the Web Address (URL) of the Web site and click Go. The top pane of the Wizard acts as a Web browser window. You can resize the Wizard's window as needed.
-
In the top pane, navigate to the Web site's logon form. When the Wizard detects one or more forms in a Web page, it lists the forms and their elements (fields and buttons) in the bottom pane.
-
Click the Detect Fields button. The Wizard attempts to detect and configure the credential fields and marks them accordingly:
-
SecurID Username
-
Passcode
-
Tokencode
-
Old PIN (PIN change and PIN change failure forms only)
-
New PIN (PIN change and PIN change failure forms only)
-
Submit button
-
-
(Optional) Select Use ordinals instead of names. The Credential Fields Screen displays the fields, assigning Control IDs by location order instead of using native (dynamic) Control IDs.
-
(Optional) Select Show non-input fields. The Administrative Console detects fields that have input functionality but into which you cannot enter information, such as IMG tags that function as Submit buttons, and includes these fields in the Web Form Wizard fields list.
-
(Optional) Select Allow multiple field designation. The Administrative Console recognizes multiple fields that require the same credential, such as enter and confirm password fields, or a page with the same field on two forms.
-
Confirm that the Wizard has selected the correct fields. You can modify a selection, if necessary:
-
If you are editing an existing template, you may change the form type using the Form Type drop-down at the lower right. Keep in mind that if you do so, you will need to reconfigure the template (reassign fields, and so on). Only fields relevant to a given form type are displayed when that form type is selected.
-
Identify and select a field from the list in the bottom pane. (The Element and Type descriptions provide cues.) In the top pane, a blinking outline indicates the corresponding field or button you have selected.
-
Confirm that you have selected the correct field, then right-click the selected item and choose from the shortcut menu (for example, SecurID Username). An icon appears to the left of the item. To deselect an item, right-click the item and select None from the shortcut menu.
-
-
Repeat this process for each field required to complete the logon form. You can configure up to four fields in all.
-
Repeat the two previous steps for each field required to logon. You can configure up to four fields in all.
-
When you have completed your configuration click OK to save it and close the Web Form Wizard.
2.13.5.6 Identification Tab for Configuring a Web Application
Use the Identification (Web) tab to modify program and window information for a Web application logon configuration.
-
You can configure a logon manually by adding, editing, or deleting entries in the Form name and URL fields.
or
-
You can use the Web Form Wizard to define URLs, forms, and fields by pointing and clicking.
To display this tab, do one of the following:
-
Create a new Web application logon.
or
-
In the left pane, click Applications and select a Web application.
-
Click the General tab in the right pane.
-
Select a form from the list and click Edit.
The Web form-configuration window appears, displaying the General tab.
Control Function Form name Enter an application name. URL One or more URLs of the logon or password-change form to configure. Click Add (or select a matching item and click Edit) to display the URL dialog. Click Delete to remove a URL.
2.13.5.7 Fields Tab for Configuring a Web Application
Use the Fields (Web) tab to define how the Agent interacts with the fields of the logon form. Select one of the following transfer methods for the currently-selected application form:
-
Up to four logon fields (user ID, password, etc.), using Control IDs
-
A series of keystrokes (with optional timings) that fill in and submit the logon form, using SendKeys or SendKeys using Journal Hook.
If you want to switch from one transfer method to the other after creating a Web form, select the desired transfer method on this screen. The Administrative Console converts the fields for the transfer method you selected.
Note:
When you switch from Control IDs to SendKeys, all fields convert with a direct injection setting. You can change the injection method during the editing process. When you switch from SendKeys to Control IDs, any field that is not set to inject directly does not convert.
To display this tab, do one of the following:
-
Create a new Web application logon.
or
-
In the left pane, click Applications and select a Windows application.
-
Select the General tab in the right pane.
-
Select a logon form from the list and click Edit.
-
Select the Fields tab.
| Control | Function |
|---|---|
| Transfer method (choose one) |
Options:
|
| Fields | One or more credential fields (including the Submit button) with transfer methods and their identifying information. You can:
|
2.13.5.8 Dynamic and Ordinal Control IDs
Certain applications change the Control ID for each field with every application launch. Logon Manager provides you with the option to assign ordinal ID numbers to replace these dynamic Control IDs, thereby eliminating variations in Control IDs with each application launch.
Note:
Logon Manager assigns mandatory ordinal field IDs by default to .NET applications, which have no native support for Control IDs.To configure Logon Manager to assign ordinal Control IDs:
-
Launch the Administrative Console.
-
Pause the Logon Manager Agent.
-
Launch an application to create a template.
-
Launch the template wizard.
-
Select Logon.
The Control ID for each field appears in the Credential Fields screen. For applications with dynamic Control IDs, these ID numbers will vary with each launch. (This does not apply to .NET applications, which have no native Control IDs.)
-
Select Use ordinals instead of Control IDs.
-
The Credential Fields Screen displays the fields, assigning Control IDs by location order instead of using native (dynamic) Control IDs.
-
For applications with native Control ID Support, if Use ordinals instead of Control IDs is checked, the Control ID detection is done by enumerating controls on the application window. The ID column will be filled with field ordinals and the display refreshes.
-
If you opt not to use ordinal IDs, dynamic Control IDs will display as the default (except for .NET applications, for which the ordinals are already displayed).
-
If you select Use 'Send Keys' for this form. Do not use Control ID, the Use ordinals instead of Control IDs option is unavailable.
-
-
Select a numeric field value to determine which field is assigned to the ID. The field will be surrounded by a flashing border. Right-click the dropdown menu to select the field name (for instance, Username or Password).
2.13.5.9 Choose Control ID
Use the ConfigName wizard to select a logon window's text control to use as the initial name of the application logon. Use this feature to name a logon (when it is added to the Agent) with a variable text item (such as an account name) that appears in the logon window.
-
Select the window that contains the text control you want to use, then click Next.
-
Select the control that contains the text item to use as the logon's initial configuration name. Click Finish.
| Control | Function |
|---|---|
| Window List | Displays the windows of the current applications. Click on the column heads to sort the list. |
| Show hidden window | Specifies to include hidden windows in the Window list. |
| Next | Advances to the next Wizard page. |
| Control | Function |
|---|---|
| Control List | Displays the controls of the currently-selected application window. Click on the headers (Class, ID, or Text) to sort the list. |
| Use ordinals instead of Control IDs | Indicates that the Agent should transmit data to this form as a series of numbered Control IDs assigned by Logon Manager, rather than addressing individual fields generated by native Control IDs. |
| Refresh | Updates the field list. |
| Back | Returns to the previous Wizard page. |
2.13.5.10 SendKeys Settings for a Web Application
Use the controls on this screen to define SendKeys actions. If you convert the transfer method from Control IDs to SendKeys or SendKeys using Journal Hook, the Administrative Console automatically converts the ControlID settings to SendKeys actions, and specifies the Direct injection option. If you convert from either SendKeys transfer method to Control IDs, you must configure the settings to use direct injection or they will be lost.
To use the SendKeys editor:
-
On the Fields tab, select SendKeys as the transfer method. The Fields window changes to reflect conversion of the existing fields, whose names now include -> direct injection.
-
Click the Edit button to open the SendKeys editor. The Current Actions list contains the items that the editor has detected.
The New Actions dialog contains a list of additional controls to add to the form. Depending on what you select in this list, the options vary.
For example, if you select Fields from the New Actions list, the Field Type dialog appears, offering choices of a third and fourth field. If you select Delay, a menu in which you can specify a delay interval appears.
-
Select an item in the Current Actions list and click the Edit button below the list to change the settings for that field or action. Click the Up or Down arrows to reorder the list.
-
Use the New Actions section of the SendKeys editor to add fields and actions to the list. Refer to the following tables for information on configuring the various action choices.
After you configure a New Action and insert it, it appears as part of the Current Actions list.
| Current Actions | Function |
|---|---|
| Keys/Actions | Lists the keys and actions that the editor detected. If you converted this list from Control IDs to SendKeys, every action is configured for direct injection by default.
Use the Up and Down arrows to reorder the items in this list. |
| New Action | Controls | Description |
|---|---|---|
| Fields | Field Type | Select a credential item from the list to add to the series.
|
| Character to insert after field | Select a keystroke to insert automatically after the field is filled:
Also see Special Keys, below. |
|
| Inject directly into control | Injects the credential directly into the control. Click the ellipsis ("…") button to open the Web Field dialog. | |
| Web Field | Function | This box is pre-filled with the name of the field that you are editing and cannot be changed.
|
| Frame | Identifies the frame number in the Web page that contains the function you are configuring. | |
| Form | Identifies the type of form you are creating based on the function. | |
| Field identification | Identifies the field as specified in the Web page. | |
| Field type | Identifies the type of field:
|
|
| Insert | Add the current selection to the series. |
| New Action | Controls | Description |
|---|---|---|
| Click | Click on a control | Click the ellipsis ("…") button to open the Web Element dialog, and click Wizard to launch the Web Form Wizard. This time, the wizard identifies only clickable fields.
Select the field that you want to associate with a click, and select OK. The wizard closes and returns you to the Web Element dialog. Its fields are populated with the information that the wizard identified. |
| Frame | Identifies the frame number in the Web page that contains the function you are configuring. | |
| Form | Identifies the type of form you are creating based on the function. | |
| Field identification | Identifies the field as specified in the Web page. | |
| Field type | Identifies the type of field:
The Agent detects where the control is and simulates a click in the center of the control. |
|
| Insert | Add the click selection to the series. |
| New Action | Controls | Description |
|---|---|---|
| Run Task | Command line to run | Enter a Command line to be executed. This feature allows you to run a program in the middle of entering keystrokes.
Click the ellipsis ("…") button to open the Choose File dialog. Note: VirtualKeyCodes cannot be used within the command line (the initial backquote character will terminate the command line). |
| Expected return code | Enter the expected return code. The rest of the SendKeys script is discarded if this value is not returned. | |
| Time out (sec.) | Enter the number of milliseconds to wait for the task to complete. The rest of the SendKeys script is discarded if this timeout is reached. The maximum timeout period is five (5) seconds. | |
| Insert | Add the task to the series. |
| New Action | Controls | Description |
|---|---|---|
| Delay | Length of delay (in seconds) | Type or select a delay between keystrokes. |
| Insert | Add the delay to the series. |
| New Action | Controls | Description |
|---|---|---|
| Set Focus | Set focus to control | Sets the focus to control. Click the ellipsis ("…") button to open the Web Element dialog and launch the Web Form Wizard. Select which of the available fields will receive focus. Click OK. |
| Insert | Add the focus to the series. |
| New Action | Controls | Description |
|---|---|---|
| Text | Enter text to insert | Enter any literal text to add to the series. |
| Insert | Add the text to the series. |
2.13.5.11 Matching Tab for Configuring a Web Application
Use the Web Matching tab to distinguish among logon, password-change, or password-confirmation forms (referred to here as target forms) within the same Web application, typically a multi-form portal page. The Agent uses the matching criteria you supply here to distinguish among similar forms.
This tab is typically used to refine the detection match criteria, that is, the set of HTML tags and values you use to identify a specific page. You can then create an offset match that uses a subset of the detection match to identify the desired logon or password-change form on the page.
To display this tab:
-
Create a new Web application logon.
or
-
In the left pane, select Applications and select a Web application.
-
Click the General tab in the right pane.
-
Select a form from the list and click Edit.
-
Select the Matching tab.
2.13.5.12 Creating or Modifying Detection-Matching Criteria
To create or modify detection-matching criteria:
-
In the Detection Match list, do one of the following:
-
Click Add to create a new matching criterion.
-
Select a match and click Edit to modify an existing match.
-
-
From the Edit Match dialog, enter or select the required information, then click OK to return to this dialog.
-
If necessary, adjust the match criteria order.
-
Select a match to move.
-
Click the Up or Down arrow.
-
-
Click OK.
2.13.5.13 Offset Matching
Note:
Offset matching should only be used with portal Web pages.This type of matching is used with portal pages that have multiple windows that the user can rearrange, add, and remove. If the site you are matching on is not a portal, leave the offset matching section on this panel blank.
With regular match detection, the forms must always appear in the same order. With offset matching, you can rearrange the forms (which look like a window) and isolate a specific window from all the others. This only applies to portal pages because these pages are dynamic, and ordinal values are used to match instead of field names.
Use the Offset Start field to tell Logon Manager which match result's forms to use for the form offsets. The offset start value should be the number of the offset matches. For example, if there are three offset matches, the offset start value should be 3.
To create or modify Offset Matching criteria:
-
In the Offset Match list, do one of the following as needed:
-
Click Copy from Detection to copy defined Detection Match criteria.
-
Click Add to create a new matching criterion.
-
Select a match and click Edit to modify an existing match.
-
-
In the Edit Match dialog, enter or select the required information, then click OK to return to this dialog.
-
If necessary, adjust the match criteria order.
-
Select a match to move.
-
Click the Up or Down arrow.
-
Select an Offset Start.
-
-
Click OK.
2.13.5.14 Edit Match Criteria for a Web Application
Use this dialog to create or modify matching criteria for the selected Web form.
| Control | Function |
|---|---|
| Tag | Enter an HTML tag type; for example, <TD> for a table cell. |
| Match Tag Instance | Select to match a specific instance of the Tag and select the instance number; for example, 3 for the third table cell on the page. |
| Criteria | Select one criteria type:
|
| Value | Enter the actual text to match.
|
| Operation | Select the relationship of this match to any others:
Note: The AND, OR, and NOT operators specify the conditions under which the Agent should respond to Web match combinations. If you assign a match value of AND to a match criterion, that criterion must be present for the Agent to respond to a page. So, when several fields are assigned an AND operator, all those criteria must be present. If you assign a match value of OR to several match criteria, the Agent responds if any one of the criteria is present. The NOT operator is used as an excluder when performing a match. The Agent responds to any criteria that are assigned the AND and OR operators, unless the conditions of the NOT criteria are present. The Agent excludes the instances specified by the NOT operator. |
2.13.5.14.1 Offset Matching Example
Following is a sample portal page that contains three windows. The goal is to log on to the Sales Database window. In order to do that, isolate that window from all the others windows on the page.
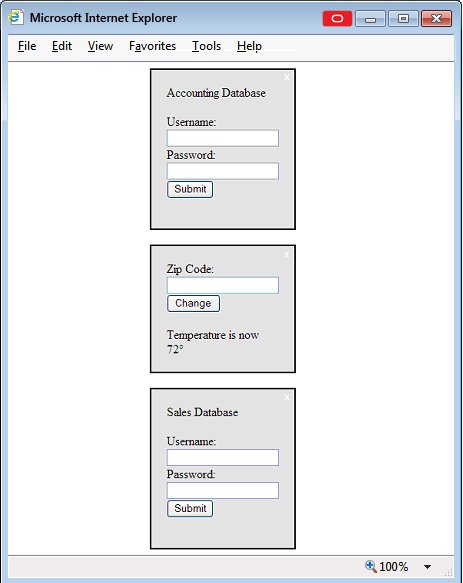
Description of the illustration lm_match_off_example.png
Note:
Like most portal sites, the windows can be rearranged and windows can be added or removed by the user so the order and the existence of windows can change. This can be done using both Detection Matching and Offset Matching (collectively referred to as Web Matching). This example describes Offset Matching.Below is an HTML fragment that is shown when you click View > Source from the browser's toolbar (the HTML has been greatly simplified to illustrate the important elements):
<div name="portalLogon1">
p
Accounting Database
</p>
<form>
Username: <input type="text" name="username">
Password: <input type="password" name="password">
<input type="submit" >
</form>
</div>
<div name="weatherStation">
<form>
Zip Code: <input type="text" name="zipCode">
<input type="submit" >
</form>
<p>Temperature is now 72°</p>
</div>
<div name="portalLogon2">
<p>
Sales Database
</p>
<form>
Username: <input type="text" name="username">
Password: <input type="password" name="password">
<input type="submit" >
</form>
</div>
Each window is represented by a <div> tag and each <div> tag has a name attribute, which you use to filter out windows that are not pertinent to your task.
To do this, add an Offset Match to look for all <div> tags with the name attribute that contains the word portalLogon. Click Add to match this criterion.
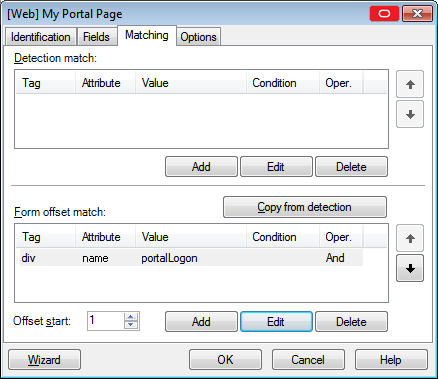
Description of the illustration lm_match_off_exmple.png
For this example, all the windows are now filtered out except the two portalLogon windows. The Agent now focuses only on the following windows:
<div name="portalLogon1">
…
</div>
<div name="portalLogon2">
…
</div>
To isolate the Sales Database window, you must add another offset match form. The HTML source indicates that the window to isolate contains a <p> tag that contains the text Sales Database. Click Add to match this criterion.
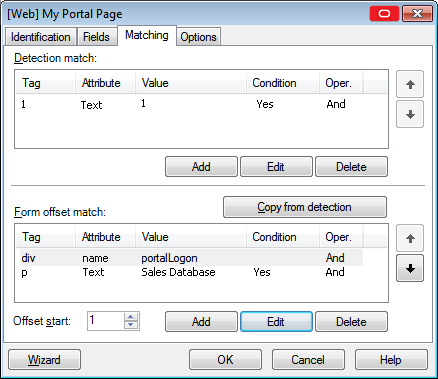
Description of the illustration lm_match_off_exm_1_entry.png
The Agent now sees only one window:
<div name="portalLogon2">
…
</div>
Because the targeted window is isolated, this is all the matching that you need to add.
The remaining task is to set the Offset Start values. To set this, determine at which match the form you want is visible. In this example, there are two matches.
The first matches the <div> tag, and the second match matches the <p> tag. In this match, the <form> tag is visible since it is contained in the <div> tag:
<div name="portalLogon2">
…
<form>
…
</form>
</div>
In the second match, the <form> tag cannot be seen since it is not contained in the <p> tag.
<p>
Sales Database
</p>
The Offset Match cannot be set to 2. It must be set to 1. This tells the Agent that the form offset for the fields is relative to the first match (the <div> match), as follows:
<div name="portalLogon2">
<p>
Sales Database
</p>
<form>
Username: <input type="text" name="username">
Password: <input type="password" name="password">
<input type="submit" >
</form>
</div>
All the form offsets and field offsets in the Fields list (found in the General tab) are relative to the above HTML.
2.13.5.15 Add/Edit URL
Use this prompt to specify the URL of the logon or password-change form to configure.
To specify a URL for matching
-
Select one of the following (see Matching Expressions).
-
Exact
-
Wildcard (does not apply to Kiosk Manager)
-
Regular Expression (does not apply to Kiosk Manager)
-
-
Enter (or edit) the URL or a matching expression.
-
Click OK.
2.13.5.16 Matching Expressions
For applications that have varying text in their URLs, you can use substrings or regular expressions to specify how to match the variable text.
| Option | Function |
|---|---|
| Wildcards |
Note: This does not apply to Kiosk Manager. |
| Regular Expressions | You can also use the set of regular expressions to specify a string pattern that the Agent should recognize as a match.
Note: This does not apply to Kiosk Manager. |
2.13.5.17 Matching Environment Variables
For applications that include the user's name in the URL (as derived from the DOMAINUSER environment variable in the workstation operating system), select Exact as the matching criterion, and use one of the following substitution tokens in the match string:
| Variable | Function |
|---|---|
%DOMAINUSER% |
User name exactly as derived from the environment variable |
%UC%%DOMAINUSER% |
User name converted to all upper case |
%LC%%DOMAINUSER% |
User name converted to all lower case |
Example
This URL entry matches a password-change window title that includes the username:
Password Expired - %UC%%DOMAINUSER%
2.13.5.18 Adding and Editing Web Fields
Use this dialog to specify a credential field or Submit button on a Web form.
| Option | Function | |
|---|---|---|
| Function | Select a credential type:
|
|
| Frame | Type the target name of the browser frame in which the field appears (specified by the NAME attribute in a <frame> element in the target page's parent frameset). |
|
| Form | Type the name of the form in which the field appears (specified by the NAME attribute in the <form> element in the target page). |
|
| Field identification | Select the ellipsis ("…") button to launch the Field Identification dialog, where you can select which type of field you want to match. | |
| Field type | Select the field type (corresponding to the type attribute of the field's <input> element) or a hyperlink anchor or IMG tag (<A HREF=...>) used as a Submit button. |
|
| Credential Type | <INPUT TYPE=...> Options |
|
| UserID | Text | |
| Password | Password | |
| Third Field | Select one | |
| Fourth Field | Select multiple | |
| New Password | ||
| Confirm New Password | ||
| Submit | Submit | |
| Image | ||
| Button | ||
Anchor (<A HREF...> tag) |
||
IMG (<A HREF...> tag) |
||
2.13.5.19 Field Identification Dialog
Use this screen to specify the type of field you want the Agent to recognize. Check the appropriate radio button from among the following:
-
Use field name. Select for a Web site whose fields have consistent, named labels, such as "User" or "e-mail."
-
User ordinal number. Select if you want to replace varying field numbers with ordinals for dynamic Web pages. See Dynamic and Ordinal Control IDs for more information.
-
Use matching. Select for a Web site where the field index varies depending on the user. Choose from among the matching choices as explained in the following table.
| Field | Function | |
|---|---|---|
| Tag | Enter an HTML tag type; for example, <TD> for a table cell. |
|
| Match Tag Instance | Select to match a specific instance of the Tag and select the instance number; for example, 3 for the third table cell on the page. | |
| Criteria | Select one criteria type:
Note: Certain browsers' innerHTML properties tags can differ from the normal HTML. For instance, the tags might appear in a different letter case, or they might add or remove spacing between the tag and the enclosed text. In order to avoid matching problems, use alternate tags and wildcard characters to account for these differences. Example: Although you would expect the tag for a bold "OK" button to be: |
|
| Value | Enter the text of the Criteria to match. | |
| Match Whole Value | Select to enforce strict matching of the Value you entered in the previous field (that is, any additional text in the tag element will cause the match to fail). | |
| Use regular expression | Select any legal expression to match the Value you entered in the previous field (you can use wildcards to create a broader matching range).
Note: Do not use the colon ( |
|
2.13.5.20 Options Tab for Configuring for a Web Application
Web pages occasionally include forms that require a short time to become enabled as the page loads. In such a case, Logon Manager might submit credentials too soon. To avoid this occurrence, use the Submit Delay setting on the Options tab to allow time for all forms to become enabled.
| Setting | Function |
|---|---|
| Dynamic Page | Check to indicate that the Web page for the template includes dynamic content. |
| Adheres to Logon Loop Grace Period | Select to have the Agent ignore this application's logon form when the logon loop grace period (set on the application's Miscellaneous tab) is in effect. |
| Auto-Recognize | Select to have the Agent recognize the application automatically. Specifying a status for this setting on the Options tab overrides the Global Agent Setting. If this setting is checked, the user can configure this setting from the Logon Manager. If this setting is unchecked, the user will not have access to this setting from the Logon Manager. |
| Auto Submit | Select to have the Agent automatically select OK for this application logon after providing credentials. |
| Preset Focus | Select to set the focus on a logon field before the Agent places data in the field. |
| Submit via Keyboard | Select to instruct the Agent to enter a programmatic Submit command for Web pages that have no Submit button. |
| Submit Delay (milliseconds) | Enter a time in milliseconds for the Agent to wait to submit credentials. |
To display this tab:
-
In the General tab in the right pane for a Web application, double-click or right-click on the Web application, and select the Options tab.
2.13.5.21 Proxy Tab for Configuring a Web Application
Use the Proxy tab to:
-
Provide mock values for the single sign-on fields when the fields are first rendered to the Web page.
-
Configure form masking to prevent the user from seeing or altering the injected credentials.
| Setting | Function |
|---|---|
| Mock Fields | Contains the field values for the proxy connection. |
| Clear All | Deletes the entries in the Mock Value column. |
| Edit | Select a field from the list, and click to launch the Update Mock Field dialog. |
| Mask form | Enable/disable masking for the form |
| RED/GRN/BLUE | Set the numerical value for the red, green, and blue components of the desired mask color. |
| HEX | Enter the hexadecimal value for the desired mask color. |
| Select color | Opens the color picker, allowing you to pick the desired mask color visually. |
| Image | Relative path and filename of the desired mask image to be used instead of a solid color mask. |
| "Timeout | Number of seconds before the form mask is dismissed. |
| Close button | Enable/disable the Close button on the form mask (allows user to remove the mask). |
| Opacity | Percentage opacity of the form mask. |
| Default | Reset all form mask options to default values. |
| Wizard | Click to launch the Web Form Wizard. |
| OK | Click to confirm your settings. |
| Cancel | Click to dismiss the dialog without saving changes. |
2.13.5.21.1 Update Mock Field Dialog
Use this dialog to edit the fields in the Web Proxy list.
The uneditable You are updating field displays the field you selected in the previous dialog. Enter the desired information in the Mock value field and click Update to save your changes. Click Close to dismiss the dialog without saving changes.
2.13.6 Creating a New Host/Mainframe Application
Use this dialog to configure a new logon for a host/mainframe application.
-
Start the target application.
-
In the left pane, right-click Applications then select New Host App from the shortcut menu.
-
The Add Application dialog appears with the Host/Mainframe option selected.
-
In the Add Application dialog, enter a Name for the new logon and click OK. The Host/Mainframe Form Wizard (for configuring new logon forms) appears.
See Adding Host/Mainframe Applications for more information.
2.13.6.1 Host/Mainframe Form Wizard
Use the Host/Mainframe Form Wizard to perform any of these tasks:
-
Configure new logons for a host/mainframe emulator or Telnet (scrolling-screen) applications.
-
Add new forms to existing logons.
-
Create forms for automatic password changes.
-
Create forms for detecting password change success and failure.
The Host/Mainframe Form Wizard lets you use the application itself to identify its logon/password-change windows and the individual username/ID, password, and other fields. The general steps for creating a logon are as follows:
-
Start the target emulator or Telnet application.
-
Select the Form Type and Screen Type.
-
Copy the text of the application's logon/password-change screen and paste it to the Administrative Console.
-
Indicate the text and position of onscreen captions that identifies the screen as a logon/password-change form.
-
Indicate the position (or, for Telnet applications, the sequence) of the individual username/ID, password, and other fields.
-
Review the configuration and make changes as needed, using the Back and Next buttons.
-
To modify a host/mainframe logon's settings manually, use the Identification Tab for Configuring a Host or Mainframe Application.
-
Before you begin this procedure, refer to the General Guidelines for Setting Up Applications for configuring applications. Also see Adding Host/Mainframe Applications for specific information about creating and configuring host/mainframe logons.
2.13.6.2 Configuring a Host/Mainframe Application
Start the target application in the host/mainframe emulator or Telnet.
-
In the Administrative Console, do one of the following:
-
Create a new host/mainframe application logon.
-
Select an existing host mainframe application, then in the General tab, click Add.
-
-
In the Host/Mainframe Wizard, select the form type. The available options are:
-
Logon. Configures a logon form.
-
Logon success. Configures a form that detects a match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's entries and displays the Logon Success dialog. If this form is not present, the Agent captures credentials immediately after the user enters them and clicks OK.
-
Logon failure. Configures a form that detects a non-match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's incorrect entries and displays the Logon Failure dialog. If this form is not present, the Agent immediately informs the user that the credentials are incorrect, displaying either the New Logon dialog or the Retry Logon dialog to allow the user to re-enter credentials.
-
Password change. Configures a password change form.
-
Password confirmation. Configures a form that verifies that the user's second password entry in a password change form is identical to the first password entry.
-
Password change success. Configures a form that serves as a match for the target application's password change success message. Since this form does not inject credentials, the Credentials page of the Host/Mainframe Wizard is skipped. When the password change success message is detected, Logon Manager will automatically save the new credentials.
-
Password change failure. Configures a form that serves as a match for the target application's password change failure message and reinjects credentials when the password change failure message is detected. If you select this option, you will be presented with the Credentials page of the Host/Mainframe in which you will configure the necessary fields.
Refer to Configuring and Diagnosing Logon Manager Application Templates for a full discussion on using the forms above.
-
-
In the Screen Type wizard page, do one of the following:
-
Choose Fixed Screen for applications running on a host/mainframe emulator that presents logon forms as static text pages.
-
Choose Scrolling Screen for applications running on Telnet or other scrolling-screen consoles that request logon information as a series of prompts.
-
-
In the Paste Screen Text page that opens, in the target application, copy all of the onscreen text to the Windows Clipboard.
Note:
Some emulators provide a Copy command or button; others let you select Ctrl+C to copy. In Windows Telnet, select the text and press Enter. -
In the Administrative Console's Paste Screen Text page, click Paste Text to paste the text into the wizard page, and click Next.
Note:
If the emulator screen does not use return or line-feed characters, adjust the Characters per Line to set proper text wrapping. -
In the Cursor Position page, click or use the arrow keys to place the text cursor in the exact position that it appears in the Telnet application's window.
-
Click Next to display the next wizard page.
-
In the Text to Match wizard page, select a block of text that identifies the screen as a logon or password-change form. Right-click the selection, and click Add as Text Match. Repeat this step for additional text blocks.
-
When your selections are complete, click Next to display the next wizard page.
-
In the Fields wizard page, do one of the following:
-
For a fixed-screen logon, place the text cursor at the starting position of a field. Right-click and select the field type (Username/ID, Password, Third Field, Fourth Field) from the shortcut menu. Repeat this step for each required field.
-
For a scrolling screen, place the text cursor at the prompt-entry position. Click Add, then select the first field type requested. Repeat this step for each required prompt.
-
-
When your selections are complete, click Next to display the summary page.
-
Review the configuration. To make changes, use the Back and Next buttons to display a page.
-
When your configuration is complete, click Finish.
2.13.6.3 Host/Mainframe Form Wizard for RSA SecurID
Use the Host/Mainframe Form Wizard to perform any of these tasks:
-
Configure new logons for a host/mainframe emulator or Telnet (scrolling-screen) applications
-
Add new forms to existing logons
-
Create forms for automatic PIN changes
-
Create forms for detecting PIN change success and failure
The Host/Mainframe Form Wizard lets you use the application itself to identify its windows and fields. The general steps for creating a logon are as follows:
-
Start the target emulator or Telnet application.
-
Select the Form Type and Screen Type.
-
Copy the text from the form displayed by the application and paste it to the Administrative Console.
-
Indicate the text and position of onscreen captions that identifies the screen as a form of the selected type.
-
Indicate the position (or, for Telnet applications, the sequence) of the individual username/ID, PIN, and other fields.
-
Review the configuration and make changes as needed, using the Back and Next buttons.
To modify a host/mainframe logon's settings manually, use the Identification Tab for Configuring a Host or Mainframe Application.
Before you begin this procedure, refer to the General Guidelines for Setting Up Applications for configuring applications. Also see Adding Host/Mainframe Applications for specific information about creating and configuring host/mainframe logons.
2.13.6.4 Configuring a Host/Mainframe Application for RSA SecurID
Start the target application in the host/mainframe emulator or Telnet.
-
In the Administrative Console, do one of the following:
-
Create a new host/mainframe application logon. Be sure to select the RSA SecurID check box in the Add Application dialog.
-
Select an existing host mainframe application, then in the General tab, click Add.
-
-
In the Host/Mainframe Wizard, select the form type. The available options are:
-
SecurID Logon. Configures a logon form.
-
SecurID Logon success. Configures a form that detects a match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's entries and displays the Logon Success dialog. If this form is not present, the Agent captures credentials immediately after the user enters them and clicks OK.
-
SecurID Logon failure. Configures a form that detects a non-match during silent credential capture. In the presence of this form, the Agent delays credential capture until it verifies the user's incorrect entries and displays the Logon Failure dialog. If this form is not present, the Agent immediately informs the user that the credentials are incorrect, displaying either the New Logon dialog or the Retry Logon dialog to allow the user to re-enter credentials.
-
PIN change. Configures a PIN change form.
-
PIN confirmation. Configures a form that verifies that the user's second password entry in a password change form is identical to the first password entry.
-
PIN change success. Configures a form that serves as a match for the target application's PIN change success message. Since this form does not inject credentials, the Credentials page of the Host/Mainframe Wizard is skipped. When the PIN change success message is detected, Logon Manager will automatically save the new credentials.
-
PIN change failure. Configures a form that serves as a match for the target application's PIN change failure message and reinjects credentials when the PIN change failure message is detected. If you select this option, you will be presented with the Credentials page of the Host/Mainframe Wizard in which you will configure the necessary fields.
Refer to Configuring and Diagnosing Logon Manager Application Templates for a full discussion on using the forms above.
-
-
In the Screen Type wizard page, do one of the following:
-
Choose Fixed Screen for applications running on a host/mainframe emulator that presents logon forms as static text pages.
-
Choose Scrolling Screen for applications running on Telnet or other scrolling-screen consoles that request logon information as a series of prompts.
-
-
In the Paste Screen Text page that opens, in the target application, copy all of the onscreen text to the Windows clipboard.
Note:
Some emulators provide a Copy command or button; others let you select Ctrl+C to copy. In Windows Telnet, select the text and select Enter. -
In the Administrative Console's Paste Screen Text page, click Paste Text to paste the text into the wizard page, and click Next.
Note:
If the emulator screen does not use return or line-feed characters, adjust the Characters per Line to set proper text wrapping. -
In the Cursor Position page, click or use the arrow keys to place the text cursor in the exact position that it appears in the Telnet application's window.
-
Click Next to display the next wizard page.
-
In the Text to Match wizard page, select a block of text that identifies the screen as a logon or password-change form. Right-click the selection, and click Add as Text Match. Repeat this step for additional text blocks.
-
When your selections are complete, click Next to display the next wizard page.
-
In the Fields wizard page, do one of the following:
-
For a fixed-screen logon, place the text cursor at the starting position of a field. Right-click and select the field type (Username/ID, Password, Third Field, Fourth Field) from the shortcut menu. Repeat this step for each required field.
-
For a scrolling screen, place the text cursor at the prompt-entry position. Click Add, then select the first field type requested. Repeat this step for each required prompt.
-
-
When your selections are complete, click Next to display the summary page.
-
Review the configuration. To make changes, use the Back and Next buttons to display a page.
-
When your configuration is complete, click Finish.
2.13.6.5 Identification Tab for Configuring a Host or Mainframe Application
Use the Identification tab to modify information about a Host/Mainframe application logon form.
Note:
See Adding Telnet Applications for information about configuring logons for Telnet applications.To display this tab, do one of the following:
-
Create a new host/mainframe application logon.
or
-
In the left pane, select Applications and select a host/mainframe application.
-
Click the General tab in the right pane.
-
Select a logon form from the list and click Edit.
The Host/Mainframe form-configuration dialog appears, displaying the General tab.
| Control | Function |
|---|---|
| Form Name | The name of the application logon form. You can edit the name. |
| Window Titles | Because some emulators do not have unique characteristics within their screens to differentiate one from another, you have the option of selecting the window title from a list of open emulator applications.
|
| Text Matching | Displays the literal text string that the Agent uses to identify this form: the screen coordinates (Row and Column numbers) of the first character of the string. Click Add to specify a new text identifier or Edit to modify an existing one. |
| Fields | Displays the series of keystrokes that Logon Manager transfers to the host application's logon form. To add or modify a keystroke series, click Edit to display the Edit SendKeys Fields and Actions dialog. |
| Wizard | Start the Host/Mainframe Form Wizard for configuring an application visually. |
2.13.6.6 Text Matching (on a Host/Mainframe Logon Form)
Use the Text Matching dialog to specify the text and position of an onscreen caption that identifies the screen as a logon or password-change form.
You must also specify the location (row and column number) of the first character of the text. Use the cursor-position indicator in the status bar at the bottom of the session window to find the row and column numbers of the text.
Note:
For Telnet applications, use row coordinates relative to the cursor position. See Adding Telnet Applications for an example. You can also use an asterisk (*) for wildcard matching of a row, column or both.When you have completed your entries for a match, click OK.
| Control | Function |
|---|---|
| Row | Enter the row number (vertical screen coordinate) of the first character of the Text.
For Telnet applications (with supported host emulators), this value is relative to the cursor position and can be negative (to indicate a row above the cursor) or an asterisk (*) to indicate any row onscreen). |
| Column | Enter the column number (horizontal screen coordinate) of the first character of the Text. For Telnet applications (with supported host emulators), this setting can be an asterisk (*) to indicate any row onscreen. |
| Text | Enter the string of text to match. |
To display this dialog, click the Add button under Text Matching on the Identification Tab for Configuring a Host or Mainframe Application.
2.13.6.7 Edit SendKeys Fields and Actions for a Host/Mainframe Application
Use the Edit Fields/Actions dialog to specify a series of keystrokes for Logon Manager to transfer to the host application's logon form.
The tabs in the right pane of the Edit Fields/Actions dialog provide the keystroke options. Select or enter the options you need on each tab. Click the Insert button to add the key or action to the series.
Your selections appear in the list in the left pane. To change the order of the series, select an item and click the Up or Down arrows to move it. To modify an item, select it, and click Edit to display the Fields dialog. To delete an item, select it, and click Delete.
| Tab | Command | Action |
|---|---|---|
| Fields tab | Select fields to insert | Select a credential item from the list to add to the series:
Use the Up and Down arrows for correct navigation through the form. |
| Insert this character after field | Select a keystroke to insert automatically after the field is filled:
Also see Special Keys, below. |
|
| Position | Enter the row and column coordinates of the first character of the text-entry field.
If the column number is variable, (for example, most Unix systems include the affected username as part of the New Password and Confirm Password field labels when changing passwords), you can use a regular expression to wildcard the variable portion of the field label so that Logon Manager always injects credentials in the correct spot. |
|
| Insert | Add the current selection to the series. | |
| Delay tab | Length of delay (in seconds) | Enter or select a delay between keystrokes. |
| Text tab | Enter text to insert | Enter any literal text to add to the series. |
| Insert | Add the text to the series. | |
| Special Keys tab | Category/Key | Select a keystroke category (for example, Movement keys) from the left list, then a specific key (for example, Page Down) from the right list. |
| Insert | Add the keystroke to the series. |
To display this dialog:
-
Do one of the following:
-
Create a new Host/Mainframe application logon.
or
-
In the left pane, select Applications and select a host application.
-
Click the General tab in the right pane.
-
Do one of the following:
Select a logon form from the list and click Edit.
or
Click Add to configure a new form.
The Host/Mainframe form-configuration dialog appears, displaying the General tab.
-
-
Under the Fields list box, click Edit.
2.13.6.8 Fields Tab for Configuring a Host or Mainframe Application
Use the Fields tab to define how the Agent interacts with the fields of a form.
You must also specify the location (row and column number) of the first character of the field. Use the cursor-position indicator in the status bar at the bottom of the session window to find the starting row and column numbers of the text. When you have completed your entries, click OK.
See Adding Host/Mainframe Applications for more information.
| Field/Actions | Function |
|---|---|
| Fields/Actions | Select the field type:
Use the Up and Down arrows to reorder the fields for correct navigation through the form. Click Edit to specify the way the Agent navigates the form. |
2.13.6.9 Matching Tab for Configuring a Host or Mainframe Application
Use the Matching tab to specify the text that identifies the screen as a logon or password-change form.
| Field | Function |
|---|---|
| Row | Enter the row number (vertical screen coordinate) of the first character of the text.
For Telnet applications (with supported host emulators), this value is relative to the cursor position and can be negative (to indicate a row above the cursor) or an asterisk (*) to indicate any row onscreen). |
| Column | Enter the column number (horizontal screen coordinate) of the first character of the text.
For Telnet applications (with supported host emulators), this setting can be an asterisk ( |
| Text to Match | Displays the literal Text string that the Agent uses to identify this form: the screen coordinates (Row and Column numbers) of the first character of the string. Click Add to specify a new text identifier or Edit to modify an existing one. |
2.13.6.10 Options Tab for Configuring a Host or Mainframe Application
Use the Options tab to configure behaviors for a host or mainframe application.
To display this tab, do one of the following:
-
Create a new host/mainframe application logon.
or
-
In the left pane, click Applications and select a host/mainframe application.
-
Click the General tab in the right pane.
-
Select a logon form from the list and click Edit.
-
In the Host/Mainframe form-configuration dialog, select the Options tab.
| Control | Function |
|---|---|
| Field Delay | Enter a time in milliseconds for the Agent to wait to submit credentials. |
| Screen type | Specify whether the application has a fixed or scrolling screen. |
| Column position of cursor | Specify the column where the cursor should be placed before starting to enter credentials.
Enter the starting column number of the text cursor when logon or password change begins. If this position varies (for example, most Unix systems include the affected username as part of the New Password and Confirm Password field labels when changing passwords), you can use a wildcard for the variable portion of the field label so that Logon Manager always injects credentials in the correct spot. |
| Adhere to logon loop grace period | Select to have the Agent ignore this application's logon form when the logon loop grace period (set on the application's Miscellaneous tab) is in effect. |
| Auto-Recognize | Select to have the Agent recognize the application automatically. If this setting is checked or unchecked, it overrides the Global Agent Setting. If this setting is checked, the user can configure this setting from Logon Manager. If this setting is unchecked, the user will not have access to this setting from Logon Manager. |
| Auto-Submit | Select to have the Agent automatically select OK for this application logon after providing credentials. |
2.14 Configuring a Specific Application
The application list represents all configured application in Logon Manager. Use the tabs in the right pane to view or modify an application's properties.
To select an application for viewing or editing:
-
Click Applications in the left pane, then click the Applications List tab in the right pane.
-
Select an application from the list, then click Edit.
or
-
In the left pane, click the plus sign (+) next to the Applications icon (or double-click Applications) to display the configured logons.
-
Do one of the following:
-
Click a logon icon to select it. The General tab appears in the right pane.
or
-
Right-click a logon icon to display a shortcut menu with the following options:
-
| Option | Function |
|---|---|
| New Form | Add a new form for the selected application logon. Displays the corresponding configuration dialog for the selected application type. |
| Delete | Delete the selected logon. |
| Make copy | Duplicate the selected logon. |
| Rename | Rename the selected logon. |
| Publish… | Select to launch the Publish to Repository dialog, from which you can select among all publishable items and the repository to which you want to publish them. |
| Publish To | Select to specify a repository to which you want to publish a specific item. |
2.14.1 General Tab (for a Selected Application
Use the General tab to add or modify form or field configurations for the selected application.
| Option | Function |
|---|---|
| Description | A meaningful description of the application for the user. |
| Reference | An internal reference describing the version/variant of the application template.
Note: This field is read-only on the client side. |
| Category | Enter the category under which the application will appear; for example, "Finance," "Development," and so on. |
| Icon Image URL | The URL to the icon image that will appear next to the application entry. |
| Logo Image URL | The URL to the full-size application logo image. |
| Vendor | The vendor of the application. |
| Administrator | Contact information for the application's administrator within your organization. |
| Forms | A list of all forms associated with this application. |
| Add | Add a new form for the selected application. The corresponding configuration dialog for the selected application type appears. |
| Edit | Modify an existing logon form. Select a form from the Forms window, then click Edit. The corresponding configuration dialog for the selected application type appears. |
| Delete | Remove a form. Select a form from the Forms window, then click Delete. If only one form is listed, deleting it will remove the application entirely. |
| Add Notes | Type or modify optional comments or documentation. |
| Deny response | Check this button to prevent the Agent from responding to this form.
Note: Disabling any form in a template disables the entire template. |
To display this tab:
-
Do one of the following:
-
Select an application.
or
-
Configure a new application.
-
-
Click the General tab in the right pane.
2.14.2 Bulk Add Tab (for a Selected Application)
Use the Bulk-Add tab for special configurations of the currently-selected application. Also see Bulk-Adding Applications for First-Time Use for more information.
| Control | Function |
|---|---|
| Enable Bulk-Add capability for this application | Select to enable this application to be included in a bulk-add. |
| Confirm UserID during Bulk-Add | Select to require the user to confirm username in order to perform a bulk-add. |
| Confirm Password during Bulk-Add | Select to require the user to confirm password in order to perform a bulk-add. |
| Confirm Third Field during Bulk-Add | Select to require the user to confirm a third field's information in order to perform a bulk-add. |
| Confirm Fourth Field during Bulk-Add | Select to require the user to confirm a fourth field's information in order to perform a bulk-add. |
To display this tab:
-
Do one of the following:
-
Select an application.
or
-
Configure a new application.
-
-
Click the Bulk-Add tab in the right pane.
2.14.3 Authentication Tab (for a Selected Application)
Use the Authentication tab to set the minimum authentication grade for the selected application.
The Primary Logon Method used must have an Authentication Grade equal to or higher than this value in order for Logon Manager to log on to the selected application.
If the end-user's Primary Logon Method has an authentication grade lower than the minimum set for this application, when the user requests access to the application, Logon Manager prompts the user to authenticate at a higher grade. The user will only gain access after successfully logging on at the required grade.
To set the authenticator grade for primary logon methods using the Authentication Grade setting.
| Control | Function |
|---|---|
| Minimum Authentication Grade | Select or type the numeric value of the lowest Authentication Grade the end user's Primary Logon Method must have. The default is 1. |
To display this tab:
-
Do one of the following:
-
Select an application.
or
-
Configure a new application.
-
-
Click the Authentication tab in the right pane.
2.14.4 Error Loop Tab (for a Selected Application)
Use the Error Loop tab (under a selected application) to control the appearance and behavior of the Logon Error dialog for individual applications.
| Control | Function |
|---|---|
| Logon timeout (sec.)
[ |
Maximum time in seconds between successive logon attempts before Logon Error dialog appears. Default is 30.
Note: If the logon timeout is set to zero (0), a logon error (for example, entering the wrong credentials) does not cause the Logon Error dialog to display. |
| Max. retries
[ |
Maximum number of retries (after first try) allowed before the Logon Error dialog appears. Default is 0. |
| Hide "Confirm Password"
[ |
Whether to suppress the Confirm Password dialog after the user enters a password. Default is No. |
| *(Global registry equivalents shown in brackets.) | |
To display this tab:
-
Do one of the following:
-
Select an application.
or
-
Configure a new application.
-
-
Click the Error Loop tab in the right pane.
2.14.5 Password Change Tab (for a Selected Application)
Use the Password Change tab to set or modify options that control how the Agent manages password changes.
The Agent distinguishes between logon and password change fields that appear on the same screen or on different tabs of a dialog. In the instance of this type of screen, the Agent prompts the user, through the Action Chooser dialog, to select a password change or logon. You can configure a period of time for which the user will not need to change passwords, and hence will not receive the Action Chooser.
| Setting Group | Control | Function |
|---|---|---|
| Password Change | Password Change Dialog Behavior | Controls how the Agent responds when an application prompts the end user to change passwords. The options are:
|
| Prevent Ability to Cancel | When enabled, disables the Cancel button in the password change dialog, prohibiting the user from canceling the password change process. | |
| Enable Password verify pop-up dialog | Check this box if you want to display the password change verification pop-up dialog, which provides an additional confirmation that the password has been changed. | |
| Lock focus to password change dialog | When enabled, locks desktop focus to the password change dialog, preventing interaction with the target application until the user completes or dismisses the dialog. | |
| Allow to finish with unsaved changes after successful submit | Check this box to allow the user to finish the password change process after a successful submission, even if he has unfinished updates. Logon Manager displays a warning message, alerting the user that he has unsaved changes. | |
| Password Generation Policy | Select a password generation policy. To subscribe multiple applications to a policy, see Policy Subscribers. Also see Creating Password Generation Policies. | |
| Credential Sharing Group | Select a credential sharing group. To assign multiple applications to a password group, see Working with Credential Sharing Groups. |
| Setting Group | Control | Function |
|---|---|---|
| Password Expiration | Enable Password Expiration | Select this check box to require users to change passwords after a specified period. |
| Number of days until password expires | Enter or select the number of days for which a user's password is valid. | |
| Run this command when the password expires | Type the full path and command (or click Browse to locate the executable file) that should be invoked when the user attempts to log on after the Number of days setting has elapsed.(Example: C:\Program Files\PassChange\passchange.exe.) |
| Setting Group | Control | Function |
|---|---|---|
| Logon Chooser | Bypass Logon Chooser | Controls whether the Logon Chooser appears when a password change is initiated. When enabled, the password change dialog will be displayed immediately if the selected condition is met. The available conditions are listed below.
Options:
|
| Bypass Logon Chooser for
This setting is new as of 11.1.1.5.0. |
If you select to bypass the Logon Chooser by either means above, specify the forms that you want the Agent to bypass.
Options:
|
| Setting Group | Control | Function |
|---|---|---|
| Action Chooser Grace Period | Days | Enter the length of the grace period (in days) for which the Agent will not display the Action Chooser dialog. |
| Automatically proceed with password change | When enabled, the Action Chooser is bypassed when the grace period expires and password change initiates automatically.
Note: This option is only available after the grace period has been specified. |
To display this tab:
-
Do one of the following:
-
Select an application.
or
-
Configure a new application.
-
-
Click the Password Change tab in the right pane.
2.14.6 Events Tab (for a Selected Application)
Use this tab to add a logon event and configure the environment surrounding it.
| Setting Group | Control | Function |
|---|---|---|
| Add Logon Event | Run this command when a logon for this application is added | This setting allows you to define a process (such as exe, web, script, etc.) to be run immediately after the Add Logon Wizard is completed for an application.
For example, this setting could be used to launch a password change application right after credentials are entered into the Agent, thus allowing the Agent to change the application password immediately. Click the Browse button to locate a command to be entered. |
| Setting Group | Control | Function |
|---|---|---|
| Pre Logon Event | Run this command before a logon for this application is used | This setting allows you to define a pre-logon task that occurs prior to each logon instance, transmitting information from this process about the current logon attempt. The information in the resulting exit code cues Logon Manager whether to continue credential submission or abort the logon process.
For example, you might want to run a script to call an API, perform a task to ensure that an application is in the state required for logon, or check usernames against a list of permitted or prohibited applications. Click the Browse button to locate a command to be entered. |
| Failure Return Code | The Agent will ignore a logon returning a number of errors equal to or higher than the number set in this field. A higher setting allows the application to return multiple error codes. The default for this setting is 1. | |
| Time out | Specifies the time, in milliseconds, for the Agent to wait for the task to complete. This setting is incremental from 1.000 to 5.000 milliseconds (default). If the task has not completed within the specified time, the task terminates and logon does not occur. |
Note:
It is recommended that you specify a full path to the application to run, and surround it with double quotes. For example,"C:\Program Files\My Tools\checktool.exe"2.14.7 Miscellaneous Tab (for a Selected Application)
Use this tab for special configurations of the currently-selected application.
| Setting Group | Control | Function |
|---|---|---|
| Miscellaneous | Allow Masked Fields to Be Revealed | Select to enable the Reveal button for masked fields in Wizards and property pages. |
| Force Reauthentication | Select to require the user to reauthenticate before providing credentials to this application. | |
| Auto Submit | Select to have the Agent automatically select OK for this application logon after providing credentials. | |
| Service Logon | Select to let the Agent detect an application that runs as a Windows service (that is, in the System space, rather than the User space). | |
| Auto-Recognize | Select to have the Agent recognize applications and Web sites and log users on automatically. If this setting is checked or unchecked, it overrides the Global Agent Setting.
If this setting is checked, the user can configure this setting from the Logon Manager. If this setting is unchecked, the user will not have access to this setting from the Logon Manager. If this setting has a green box instead of a check, this means that the user can configure this setting from Logon Manager. |
|
| Mask Third Field | Select to mask the third field of an application logon. This affects the third field appearance on the following pages: New Logon property, Error Loop dialog, Logon Properties, and FTU Entry. By default, this box is checked (third field is masked). | |
| Mask Fourth Field | Select to mask the fourth field of an application logon. This affects the fourth field appearance on the following pages: New Logon property, Error Loop dialog, Logon Properties, and FTU Entry. By default, this box is checked (fourth field is masked). | |
| Prohibit disabling the addition of new logons | Specifies whether the Disable button in the New Logon dialog is active for this application. When enabled, the Disable button is deactivated and the user is prohibited from adding new logons for this application when auto-prompted by the Agent. When disabled, clicking the Disable button adds this application is to the Exclusions list in the Agent settings dialog.
Options:
|
|
| Prohibit canceling the addition of new logons | Specifies whether the Cancel button in the New Logon dialog is active for this application. When enabled, the Cancel button is deactivated and the user is prohibited from canceling a logon addition in progress for this application after being auto-prompted by the Agent. When disabled, clicking the Cancel button defers the logon addition until the next time this application is detected.
Options:
|
|
| Allow creation of multiple accounts during credential capture | Specifies whether to enable the checkbox that allows the user to add another set of credentials in the New Logon dialog.
For any template, this setting overrides the Global Agent Setting of the same name. |
|
| File extension (for Icon) | Enter a Windows file extension associated with a logon. Instructs the Agent to map an icon to the configuration. | |
| ConfigName | Click Choose to select the windows and control that contains the text to use to create the new logon's initial configuration name (Windows applications only). | |
| UserID Field Label | Type a text label to be used by the Agent for the username/ID field. | |
| Password Field Label | Type a text label to be used by the Agent for the password field. | |
| 3rd Field Label | Type a text label for the Agent to use when displaying a third logon field. | |
| 4th Field Label | Type a text label for the Agent to use when displaying a fourth logon field. |
| Setting Group | Control | Function |
|---|---|---|
| Logon Chooser | Logon chooser columns | Select Choose to open the Logon Chooser Columns window, which contains a list of possible columns to display in the Logon Chooser dialog.
Note: Third and Fourth field selection is available only if you do not choose to mask them in the setting above. |
| Setting Group | Control | Function |
|---|---|---|
| SendKeys Settings | Delay Char | Use this setting to add a delay, in milliseconds, between every press in SendKeys, slowing credential submission. This setting is useful for applications that require additional time to recognize credential input. |
| Setting Group | Control | Function |
|---|---|---|
| Logon Loop Grace Period | None | The user is logged on automatically after initial logon. There is no grace period between logon prompts. (Default) |
| Prompt | If the logon grace period has not expired, the user receives a prompt asking if he wants to log back on to an application. | |
| Silent | The Agent ignores the application for the duration of the grace period and does not inject credentials until the grace period expires. | |
| Minutes | Set the length of the grace period in minutes. | |
| Reset for each process | When enabled, the grace period is reset for each new process that is launched. This will cause Logon Manager to log the user on to an application when the application is closed and restarted, even if the grace period has not expired.
When disabled, the grace period is not reset for each new process. Logon Manager does not attempt to log the user on to an application that has been restarted until the grace period has expired. (When this is disabled and the grace period has not expired, the user will be prompted to log on again if the Prompt/Silent option is set to Prompt.) |
| Setting Group | Control | Function |
|---|---|---|
| Credential Capture Mode | Configures credential capture behavior by using one of the modes below.
Note: Silent credential capture mode is not compatible with applications that require SendKeys. For this reason, you cannot use this mode for host/mainframe applications, nor for any Web or Windows application for which you use SendKeys. You should not use silent credential capture for applications where the username and password are obfuscated. |
|
| Default to global agent setting | Specifies that this application should use the same value as that in the global agent setting.
Selecting any of the following settings overrides the global agent setting. |
|
| Do not capture silently | Presents the New Logon dialog in which the user enters credentials manually. | |
| Capture, but do not inform user | The Agent captures the credentials as the user enters them, and does not inform the user of the process. | |
| Capture, and inform user with balloon tip | The Agent captures the credentials as the user enters them, and displays a balloon tip near the system tray to inform the user during the process. | |
| Capture, and present New Logon dialog | The Agent captures the credentials as the user enters them, and displays a balloon tip near the system tray to inform the user during the process. After capturing the credentials, the Agent displays the New Logon dialog with the user's entries pre-filled. The user can accept, change, cancel, or disable. | |
| Silent capture timeout | The time (in milliseconds) that the Agent should wait to create an account after the user submits credentials.
If this timeout expires before the Agent can determine if the logon succeeded or failed, it dismisses the credentials it captured. |
|
To display this tab:
-
Do one of the following:
-
Select an application.
or
-
Configure a new application.
-
-
Click the Miscellaneous tab in the right pane.
2.14.8 Security Tab-Role/Group Support (for a Selected Application)
Use this tab to set the access rights for the currently selected configuration item. You can assign access rights to these items:
-
Application logons (including associated credential sharing groups)
-
Password generation policies
-
Global Agent settings
-
Passphrase question sets
-
Exclusion lists
Note:
For increased security on Active Directory domains, right-click the domain administrator's name and select DENY. This action will ensure that application templates are not automatically sent to domain administrators.| Control | Function |
|---|---|
| Directory | Select the target directory server. |
| Access information: | |
| Name | Lists the groups or users who currently have access to this item. |
| ID | The user account name. |
| Access | Indicates whether the user or group has read/write or read-only access rights to the currently selected item. To change a user or group's access rights, right-click the user or group and select Read or Read/Write from the shortcut menu. |
| Actions: | |
| Copy Permissions To… | Displays the Select Application screen. Select an application to add; use Ctrl+Click or Shift+Click to select multiple entries. Click OK to confirm your selection. |
| Add | Displays the Add User or Group dialog (for LDAP or Active Directory) to select the users or groups who should have access to the currently selected item. Click OK to confirm your selection. |
| Remove | Removes selected user(s) or group(s) from the list. Select a user or group to remove; use Ctrl+Click or Shift+Click to select multiple entries. Click OK to confirm your selection. |
2.14.9 Provisioning Tab-Role/Group Support (for a Selected Application)
To access this tab, expand Applications and double click any application. Click the Provisioning tab.
From this tab, you can add and remove permissions. You can also select the level of access rights (for example, add/modify/delete applications) for those permissions.
| Control | Function |
|---|---|
| Directory | Select the target directory server. |
| Access information: | |
| Name | Lists the groups or users who currently have access to this item. |
| ID | Lists the user account name. |
| Access | Indicates the permissions that have been granted to the user or group (Add, Modify or Delete Logon). To change a user or group's access rights, right-click the user or group and select Add Logon, Modify Logon or Delete Logon from the shortcut menu. |
| Actions: | |
| Copy Permissions To… | Use this button to easily apply the provisioning rights for the current application to multiple applications. Clicking this button displays a dialog listing all the applications. Selects the applications that you want these provisioning rights to be copied to. Use Ctrl+Click or Shift+Click to select multiple entries. Click OK to confirm your selection. |
| Add | Displays the Add User or Group dialog (for LDAP or Active Directory) to select the users or groups who should have access to the currently selected item. |
| Remove | Removes selected user(s) or group(s) from the list. Select a user or group to remove; use Ctrl+Click or Shift+Click to select multiple entries. |
2.14.9.1 Add User or Group Dialog
The Select User or Group dialog varies based on the directory server being used:
-
LDAP
-
Active Directory
-
AD LDS (ADAM)
2.14.9.1.1 LDAP
Use this dialog to select the individual users or user groups that you want to add to the access list for the current configuration item (Add Logon, Modify Logon, or Delete Logon).
| Control | Function |
|---|---|
| Search Base | The base (highest-level) directory to begin searching for user/group accounts. All subdirectories of the base directory are searched. Enter a location or click Change to browse the directory tree. |
| Change | Displays the Select Search Base dialog to browse for a base directory for the search. Use this dialog to browse to and select the base (highest-level) directory to search for user/group names. Click OK when finished. |
| Search | Begin searching the base directory for users and groups. |
| Users or Groups | Lists the search results. Select the names to be added to the access list for the current configuration item. Use Ctrl+Click or Shift+Click to select multiple entries. Click OK when finished to copy your selections to the access list. |
2.14.9.1.2 Active Directory and AD LDS (ADAM)
Use this dialog to select the individual users or user groups that you want to add to the access list for the current configuration item (Add Logon, Modify Logon, or Delete Logon).
| Control | Function |
|---|---|
| List Names From | Select an Active Directory domain or server. |
| Names | Lists the names of users and groups for the selected domain or server. Select one or more names to add to the access list. |
| Add | Copies user(s) and group(s) selected in the Names list to the Add Names list. Use Ctrl+Click or Shift+Click to select multiple entries. |
| Members | When a group is selected in the Names list, displays the Global Group Membership dialog, which lists the members of the selected group. |
| Search | Displays the Find Account dialog for searching one or more domains for a specific user or group. |
| Add Names | Display the names of the user(s) or group(s) that have been added. Click OK to add these names to the access list for the current configuration item.
Note: You can type or edit user names in this list. However, entries are checked for invalid account names, and duplicate account selections are automatically removed when you click OK. |
2.14.10 Privileged Accounts Tab (for a Selected Application)
Use this tab to specify whether the account for this template is privileged. Check the box to identify this template as belonging to a privileged account.
See Privileged Accounts Settings for more information about configuring a privileged account.
2.14.11 Delegated Credentials Tab (for a Selected Application)
Use this tab to specify whether a user can delegate credentials for this application to another user, and the terms of the delegation. This feature is useful in scenarios where one user (the delegator) temporarily assigns some responsibilities to another user (the delegatee), but where the delegatee will not be performing the delegator's duties permanently.
The delegator is required to authenticate when revoking a delegated credential. To complete the revocation, the delegatee must also authenticate. This causes a repository synchronization that reverts the credentials back to their undelegated state.
Only the delegator can revoke delegated credentials. If for any reason you need to revoke credentials from the delegatee in the delegator's absence, you can lock the delegatee's account and force a password reset.
Delegated credentials are installed during installation of the Logon Manager Client as one of the selections in the Advanced installation setup mode.
| Control | Function |
|---|---|
| Allow users to delegate credentials for this application | Check the box if you want to allow a user to delegate credentials to another user. After the box is checked, the following configuration options become available.
Default is Disabled. |
| Allow reveal password | Specify whether to allow the delegatee to see the delegator's password.
Default is Disabled. |
| Maximum number of delegation days | Specify the maximum number of days that the delegatees has the delegator's credentials for this application.
Default is 15. |
| Permitted usage | Specify the day(s), and time interval for each day, that the delegatee can access the application. |
Note:
You must also specify the path to the provisioning service and the encryption algorithm in the Global Agent Provisioning Settings.2.14.11.1 Setting Up Delegated Credentials with Oracle Repositories
You have the option of using Oracle Internet Directory (OID), Oracle Unified Directory (OUD), or Oracle Virtual Directory (OVD) for your repository. Perform the following configuration steps to use delegated credentials with any of these Oracle repositories.
-
Navigate to the Provisioning Gateway Service folder (typically,
%PG_SERVER%\Service). -
Open the web.config file in a text editor. Near the end of the file there are two lines:
-
<add key="LDAP_Username" value="" /> -
<add key="LDAP_Password" value="" />
-
-
Set the value attribute of these lines to the username and password of a directory account with permissions to do the following (this account does not have to be an administrator account):
-
Read the objects in the Locator container
-
Read the objects in the CO container
-
Read and write objects in the People container and its sub-containers
-
-
Encrypt the
web.configfile where you are storing these credentials:-
From the command prompt, go to the directory:
%Windows%\Microsoft.NET\Framework\v2.0.50727. -
Enter the following command:
aspnet_regiis -pef "appSettings" "C:\Program Files\Passlogix\v-GO PM\Service"(assuming you installed the Provisioning Gateway server in the folder:C:\Program Files). -
Open the
web.configfile to make sure theappSettingssection has been encrypted.
-
2.14.11.2 Export to INI File
An entlist.ini file is a store of selected application, all password policies, and groups. To export selected items to an INI file:
-
Do one of the following:
-
Select applications to export (use Ctrl+Click or Shift+Click to select multiple entries), then click OK.
or
-
Click Export All to export all listed applications.
-
-
If any of the applications you have selected is enabled for Bulk-Add, you can select Create First-Time-Use file to generate a bulk-add (
ftulist.ini) file. -
Click OK. The Export EntList file dialog appears.
-
Locate and open the folder for the file, name the file, and click Save.
-
If you chose to create a First-Time Use file, the Export First-Time Use dialog appears. Locate and open the folder for the file (rename the file if desired), and click Save.
To display the Export EntList file dialog:
-
Right-click Applications and select Export from the shortcut menu.
or
-
Choose Export from the File menu.
2.14.11.3 Export EntList File
Save an exported application configuration file (enlist.ini) to disk. The Export EntList file dialog displays when you export application logon information using the Export to INI dialog.
-
Locate and open the folder for the file, name the file, and click Save.
-
If you chose to create a First-Time Use file, the Export First-Time Use dialog opens. Locate and open the folder for the file (rename the file if desired), and click Save.
2.14.11.4 Export First-Time Use
Save a first-time-use file (ftulist.ini) to disk. The Export First-Time Use dialog opens when you create a First-Time Use file while exporting application logon information to an enlist.ini file.
-
Locate and open the folder for the file (rename the file if desired).
-
Click Save.
2.14.11.5 Import Merge Conflict
The Import/Merge Conflict dialog appears if the merged file contains items with the same names as those in the current configuration.
-
Select the items to import and click OK.
The items you select overwrite the current like-named items.
2.14.11.6 Override Settings Tab (Edit Template Dialog)
Use this tab to select the settings that the template updates in all logons that are based on it. You can choose global overrides that apply to all of the forms in the application logon configuration, and you can also select specific overrides for individual forms.
The left pane displays the hierarchy of the application and its component forms:
-
The global override settings for applications correspond to the general configuration settings for each application-type.
-
The form-specific settings correspond to the configuration controls for individual logons.
Both Setting types are listed in the right pane with a category that corresponds to the application-configuration dialog in which you make the setting. Refer to the dialog or tab for information on each setting.
| Control | Function |
|---|---|
| Applications |
|
| Windows forms |
|
| Web forms |
|
| Mainframe/Host forms |
|
To display this tab:
2.14.11.7 Supply Info Tab (Edit Template Dialog)
Use this tab to specify what information an administrator must provide in order to complete an application logon based on this template. You can choose all items or choose individual items by selecting checkboxes.
2.14.11.8 Update Applications (from Template)
Use this dialog to update application logons based on a template that has been modified since the logons were created. Only logons whose templates have been modified appear in the list. Select the applications to update (use Ctrl+Click or Shift+Click for multiple applications), then click Update.
2.14.11.9 Launch Tab (for a Selected Application)
Use this tab to specify the location of the target application.
| Control | Function |
|---|---|
| Launch URIs | The list of URI(s) that will be accessed when the user launches the application. Click Add or Edit to open the Manage Launch URI dialog, where you configure these URIs. |
| Login Failure URI | The URI that should be accessed if the user's logon fails. |
| Add | Allows you to add a URI to the list by opening the Manage Launch URI dialog. |
| Edit | Allows you to change settings for a selected Launch URI by opening the Manage Launch URI dialog. |
| Delete | Deletes the selected Launch URI. |
2.14.12 Launch Tab (for a Selected Application)
Use this tab to specify the application launch URI, as follows:
-
In the Launch tab, click Add.
-
In the Manage Launch URI dialog's Type dropdown:
-
Select Web for a client application that supports launching a Web application directly.
-
Select WebProxy, for a client application that does not support launching a Web application directly.
-
-
Enter the URI or (its proxy version, depending on your selection in the previous step) of the target Web application. This URI will be accessed when the user launches the application. Obtain this URI from your application administrator.
-
Click Update to save your changes.
| Control | Function |
|---|---|
| Launch URIs | The list of URI(s) that will be accessed when the user launches the application. Click Add or Edit to open the Manage Launch URI dialog, where you configure these URIs. |
| Login Failure URI | The URI that should be accessed if the user's logon fails. |
| Add | Allows you to add a URI to the list by opening the Manage Launch URI dialog. |
| Edit | Allows you to change settings for a selected Launch URI by opening the Manage Launch URI dialog. |
| Delete | Deletes the selected Launch URI. |
2.14.12.1 Manage Launch URI
Use this tab to specify the location (the target) that will be accessed when the user launches the application.
| Control | Function |
|---|---|
| Type | Select the type of URI that this will be:
|
| URI | Enter the URI or its proxy version of the target Web application. |
| Update | Click to save the new configuration and close the Manage Launch URI dialog. |
| Close | Click to close the Manage Launch URI dialog without saving changes. |
2.14.13 Testing Templates
The Administrative Console Template Test Manager provides a simple way to validate templates that you have created, before publishing them. It engages the Agent directly, bypassing the repository and synchronization. The manager guides you through the test, prompting you to take action at various points, and asking questions about the results. Your answers to these questions are the cue to the manager's next steps.
Using the Template Test Manager requires the following:
-
The Administrative Console
-
The Logon Manager Agent
-
Application templates that you want to test added to the Administrative Console
-
Applications whose templates you have added to the Administrative Console
Note:
The Template Test Manager supports Windows applications only.To use the Template Test Manager:
-
Launch the Administrative Console.
-
Right-click on a template under the Applications menu, and select Test to launch the Template Test Manager. During testing, the Administrative Console application window minimizes and the Template Test Manager receives focus.
-
Observe the three sections of the manager window:
-
The Forms to be validated section contains the name of the template (and all its forms) that you have selected to test. A status icon appears next to each name to indicate its status:

Processing 
Success 
Failure -
The Status Messages section apprises you of the test status.
-
The Interactions section prompts you to take the actions required to proceed with the test. Watch the status messages and follow the interactions prompts and proceed accordingly.
-
-
The manager asks if the Agent detected the template. If the test was successful, click Yes, and then click Finish. If the test is not successful, click the button that best describes why detection was unsuccessful:
-
Yes, but also responds to other windows that should be ignored.
-
No (any other reason).
-
-
Click Next to receive suggestions to correct the errors in the template.
-
Continue the process until the Agent responds correctly to the template.
-
Select Close to shut down the Template Test Manager and return to the Administrative Console.
Example
-
In the Administrative Console, you have selected an application template, right-clicked it, and selected Test. The Template Test Manager launches, and the template's forms appear in the "Forms to be validated" section, but the Agent is not running. The Status Messages section reads, "Waiting for the Logon Manager Agent…" This indicates that the Agent is not active and that you must launch it to begin the test. So, the Interactions section displays the action request, "Launch the Logon Manager Agent."
-
You launch the Agent, and the status message indicates that the Template Test Manager is publishing the template to the Agent. The "Actions" message prompts you to launch the application for the template you are testing.
-
After you launch the application, the Agent should detect it and respond (in accordance with your configuration for initial credential capture).
-
The Interactions section informs you that you are at the "Detection" stage and presents the question, "Does the Agent detect the window?" Select the appropriate response:
-
Yes
-
Yes, but also responds to other windows that should be ignored
-
No
-
-
Click Next.
-
If you responded Yes, the Interactions section in the next screen informs you that the test was completed successfully. A check icon appears next to the template name.
-
If you responded with either of the other answers, click Next and the manager prompts you through a series of troubleshooting tests, offering suggestions based on your input.
-
Continue the process until you have modified the template to achieve successful results.
-
Click Close when done.
2.15 SSO Applications Node
The SSO Applications node allows you to add Federated and SSO-Protected applications to Logon Manager.
To add an application:
-
Do one of the following:
-
Right-click on the SSO Applications node and select the application type from the context menu.
-
Right-click in the empty area under Applications List and select the application type from the context menu.
-
Select the SSO Applications node and click the Add button at the bottom right.
-
-
In the Add SSO Application dialog, select an application type if it is not already selected, enter a name for this application, and click OK.
The application appears under the SSO Applications node. When you select it, two tabs display to the right:
-
General
Use this tab to define field configurations for the selected application.
Option Function Description A meaningful description of the application for the user. Reference An internal reference describing the version/variant of the application template. Note: This field is read-only on the client side.
Category Enter the category under which the application will appear; for example, "Finance," "Development," and so on. Icon Image URL The URL to the icon image that will appear next to the application entry. Logo Image URL The URL to the full-size application logo image. Vendor The vendor of the application. Administrator Contact information for the application's administrator within your organization. -
Launch
Use this tab to specify the location of the target application.
Control Function Launch URIs The list of URI(s) that will be accessed when the user launches the application. Click Add or Edit to open the Manage Launch URI dialog, where you configure these URIs. Login Failure URI The URI that should be accessed if the user's logon fails. Add Allows you to add a URI to the list by opening the Manage Launch URI dialog. Edit Allows you to change settings for a selected Launch URI by opening the Manage Launch URI dialog. Delete Deletes the selected Launch URI.
Use this tab to specify the location (the target) that will be accessed when the user launches the application.
| Control | Function |
|---|---|
| Type | Select the type of URI that this will be:
|
| URI | Enter the URI or its proxy version of the target Web application. |
| Update | Click to save the new configuration and close the Manage Launch URI dialog. |
| Close | Click to close the Manage Launch URI dialog without saving changes. |
2.16 Configuring Logon Manager for Specific Environments
These topics describe how to configure Logon Manager to support specific environments.
2.16.1 Configuring the Agent for Windows Authentication
Logon Manager supports Windows Authentication v2 as the Primary Logon Method (Authenticator), creating a true single sign-on user experience. The Agent can use the Windows logon credentials as its authentication. In order for Logon Manager to support this, the administrator needs to be aware of two issues:
-
The OS must have 128-bit encryption installed.
-
The administrator must enable user-level profiles.
2.16.1.1 Confirming 128-bit Encryption
To check the encryption strength of the OS, launch Microsoft Internet Explorer, and select Help>About. Confirm that Cipher Strength is 128-bit.
If the OS is not 128-bit, download the update from Microsoft:
http://www.microsoft.com/windows/ie/ie6/downloads/recommended/128bit/default.mspx.
2.16.2 Configuring the Agent for Directory Server Synchronization
This topic describes the settings needed to configure Logon Manager to use a directory server as a repository. The configuration is similar for all supported directory servers, with explanations of any differences.
-
See Using Role/Group Support with Directory-Server Synchronization for more information about how Logon Manager makes use of directory server resources.
-
See Configuring the Agent with Global Agent Settings for detailed descriptions of the associated registry entries.
Note:
Where the LDAP AUI and LDAP Directory Server extension are both installed, values must exist in bothAUI\LDAP and Extensions\SyncManager\Syncs\%LDAP%.-
Point Logon Manager to the server or servers.
-
Do one of the following:
-
From Global Agent Settings in the left pane, select an existing set of registry entries.
-
Import a saved set of settings (File>Registry>Import).
-
Create a new set of registry settings (Insert>Global Agent Settings).
-
-
In the left pane of the Administrative Console, select and open the set of settings, select and open Synchronization (add the appropriate extension if needed), select and open the appropriate extension, then select and open Servers.
-
In the right pane, select Servers, select the ellipsis ("…") button, enter the server names, or IP addresses, and click OK.
For Microsoft Active Directory Server (other than AD LDS (ADAM)):
-
If no Servers are entered for the Active Directory extension, and the user account is in an Active Directory domain, then Logon Manager uses Active Directory domain resources to discover the server. If one or more servers are specified in the Global Agent Settings, then Logon Manager uses the Servers list to locate the server.
-
Unless otherwise configured, Logon Manager queries the domain name server (DNS) for the name of the preferred domain controller assigned to the local subnet.
-
In Active Directory networks with multiple servers, be sure to enable replication in order to include the Logon Manager schema extension and related objects. This assures that Logon Manager will always find SSO information on every server it connects with.
-
If one or more servers are provided for Microsoft Active Directory Server, use server names, rather than IP addresses.
For Microsoft AD LDS (ADAM):
-
At least one server must be specified for AD LDS (ADAM) services.
-
Use the port parameter (for example myserver.com:9890) to specify particular instances of AD LDS (ADAM) running on a single server.
-
Applications templates must reside in a specific OU and not at the root of the AD LDS (ADAM) instance.
-
-
Point Logon Manager to the User path.
-
In the left pane, select the appropriate extension. Then do one of the following:
-
For an LDAP extension, select Required.
-
For an Active Directory extension, select Advanced.
-
-
In the right pane, select User Paths, then select the ellipsis ("…") button, enter the user path(s), and click OK.
-
Enable or disable SSL.
-
In the left pane, select the appropriate extension.
-
In the right pane, select SSL options as follows:
-
If using SSL, select SSL (for LDAP or Active Directory) and select Connect via SSL (defaults to port #636).
Note:
SSL is not enabled by default; the non-secure default port is #389.To set non-standard ports, use the Servers setting (for LDAP or Active Directory).
-
If using SSL, select When SSL Fails (for LDAP or Active Directory) appropriately.
For Novell eDirectory: There are two major caveats for Novell eDirectory and some other environments. If the domain name for a user is in the form of:
cn=%UserName%,ou=people,dc=Oracle,dc=cominstead of the form:
namingattribute=%UserName%,ou=people,dc=Oracle,dc=comwhere
namingattributecan be any string, do the following:-
In the left pane, select the appropriate extension, then select Advanced.
-
Select Naming Attribute string and set it to CN.
-
Select Alternate User ID location and set it to:
uid=%user%,pathwhere
pathis the rest of the path to the object; for example:uid=johnd,ou=people,dc=Company,dc=com
-
2.16.2.1 Using Role/Group Support with Directory-Server Synchronization
In directory-server synchronization installations, Logon Manager provides support for role/group access control for individual configurations, including application logons, password-change policies, Global Agent Settings, and passphrase question sets. When this feature is enabled, you can assign access-control lists, similar to those used in Windows security to the individual logons, policies, settings, and question sets.
Role/group support-enabled configurations are exported to a synchronizer container object just like the standard Logon Manager configuration objects (EntList, FTUlist, and AdminOverride). When role/group support is enabled and these access-controlled objects are present in the container, they override the standard objects. Follow these steps to configure role/group support:
-
Configure these Global Agent Settings to enable role/group security support and update the Agent:
Setting Location Setting Name Function Synchronization Enable role/group security support Enables role/group support for application logons, password policies, Global Agent Settings, and passphrase question sets. Options:
-
Do not use role/group security (default).
-
Use role group security.
Synchronization > selected sync > Advanced Configuration Objects Base Locations (LDAP, Active Directory, AD LDS (ADAM))
Specifies where to begin the search for role/group-enabled configuration objects. The search is from the specified locations or locations downward, (away from the root). If there are no entries for this setting, the search is from the root. -
-
Specify the access rights for each configuration:
Use the Security tab for each configuration (application logons, password policies, Global Agent Settings, and passphrase question sets) to specify the users and groups that should have access to it.
-
Export the configurations to a synchronizer container.
-
Connect to the synchronizer directory.
-
In the right pane, right-click a container object and choose Publish to Repository from the shortcut menu to display this window.
-
Choose Administrative Console as the Data Source.
-
Choose and complete the Wizard procedure to export the configuration objects as individual, access-controlled objects.
Note:
For best performance and highest security, Oracle recommends the following practices:-
Unless your organization explicitly requires role/group support, make certain that Enable role/group security support is set to Do not use….
-
For best security, make certain that there are no user-writable areas anywhere down the directory tree from the location specified by Configuration Objects Base Locations (LDAP, Active Directory, AD LDS (ADAM)).
-
For best performance, always specify at least one location for Configuration Objects Base Locations. This ensures that the entire server is not searched.
-
To minimize the search load and length, be sure to store as little unnecessary data as possible down the directory tree from the location specified by Configuration Objects Base Locations.
2.16.3 Configuring the Agent for Database Synchronization
You can distribute the configuration settings described below to the client workstations either as part of the general deployment of the Agent software (by modifying the MSI installer file) or, after Agent deployment, by distributing a registry entries (.REG) file to merge with the client workstation's registry.
-
See Considerations Before Deploying Logon Manager for topics about Logon Manager Agent rollout.
-
See Database Synchronization Support for more information about how Logon Manager makes use of database server resources.
-
See Configuring the Agent with Global Agent Settings for detailed descriptions of the associated registry entries.
-
Point Logon Manager to the database server.
-
Do one of the following:
-
Import a saved set of settings (from the File menu, choose Registry, then Import).
Note:
The Console produces a.REGfile compatible only with 32-bit systems. If you are merging the.REGfile on a 64-bit system, you must run the following command to move the merged registry data to the correct location within the registry (otherwise, Universal Authentication Manager will not function):reg.exe COPY HKLM\Software\PasslogixHKLM\Software\Wow6432Node\Passlogix /s -
Create a new set of registry settings (from the Insert menu, choose Global Agent Settings).
-
-
In the left pane, select and open the set of registry settings, select and open Synchronization, add the appropriate extension (if needed), select and open the appropriate extension, then select and open Servers.
-
In the right pane, select Servers, click the ellipsis ("…") button, enter the database server name(s) and click OK.
-
Export the settings to the Agent by selecting a method for initial distribution to client workstations:
-
Customize the
MSIpackage that installs the Logon Manager Agent to include these settings. -
Distribute a
.REGfile that you export from the Administrative Console. The.REGfile can be merged with the client workstation's registry locally by double-clicking the file icon.
Note:
The Console produces a.REGfile compatible only with 32-bit systems. If you are merging the.REGfile on a 64-bit system, you must run the following command to move the merged registry data to the correct location within the registry (otherwise, Universal Authentication Manager will not function):reg.exe COPY HKLM\Software\PasslogixHKLM\Software\Wow6432Node\Passlogix /s -
2.16.4 Configuring the Agent for File System Synchronization
This topic describes the settings needed to initially configure the Logon Manager Agent to synchronize application logons, global agent settings, and user credentials with a network file share.
The configuration settings described below can be distributed to the client workstations either as part of the general deployment of the Agent software (by modifying the MSI installer file), or after Agent deployment, by distributing a registry-entries (.REG) file that can be merged with the client workstation's registry.
-
See Considerations Before Deploying Logon Manager for topics about Logon Manager Agent rollout.
-
See File System Synchronization Support for more information about how Logon Manager makes use of file system resources.
-
See Overriding Settings for detailed descriptions of the associated registry entries.
-
Point the Logon Manager Agent to the server.
-
Do one of the following:
-
Import a saved set of settings (choose Registry, then Import from the File menu).
-
Create a new set of registry settings (from the Insert menu, choose Global Agent Settings).
-
Select an existing set of registry entries (by selecting it in the left pane under Global Agent Settings).
-
-
In the left pane, select and open the set of registry settings, select and open Synchronization, add the appropriate extension (if needed), select and open the appropriate extension, then select Required.
-
In the right pane, select Server, enter the server names or IP address, and click OK.
-
Export the settings to the Agent.
-
Select a method for initially distributing the global agent settings to client workstations:
-
Customize the MSI package that installs the Logon Manager Agent to include these settings.
-
Distribute a
.REGfile that you export from the Administrative Console. The.REGfile can be merged with the client workstation's registry locally by double-clicking the file icon.Note:
The Console produces a.REGfile compatible only with 32-bit systems. If you are merging the.REGfile on a 64-bit system, you must run the following command to move the merged registry data to the correct location within the registry (otherwise, Universal Authentication Manager will not function):reg.exe COPY HKLM\Software\PasslogixHKLM\Software\Wow6432Node\Passlogix /s
-
2.16.5 Configuring the Agent in a Citrix Environment
The Logon Manager default installation process automatically detects and installs the components necessary for Logon Manager in a Citrix environment. The installation process enables Logon Manager support for every application published on that Citrix server.
2.16.5.1 Installing Logon Manager on Citrix Server
To install Logon Manager on Citrix Server:
-
Log on to the Terminal server as an administrator and close all applications.
-
Click Start and then click Run.
-
In the Run Dialog window, enter
cmdand press Enter. -
In the Command Prompt window, enter
change user/installand press Enter. -
Install Logon Manager with the appropriate installation options for your environment.
-
At the command prompt, enter
change user/executewhen installation is complete.
2.16.5.2 Controlling Logon Manager for Specific Applications in Citrix
The following section explains how to change the default installation of Logon Manager and enable it for only specific applications in a Citrix environment. There are two steps in this process:
-
Remove global Logon Manager support.
-
Specify applications to be SSO-enabled through their published application configurations.
2.16.5.2.1 Removing Global Logon Manager Support
To remove global Logon Manager support:
-
Click Start and then click Run.
-
In the Run Dialog window, enter
Regeditand press Enter. -
Go to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon. -
From the right pane, right-click the string value AppSetup and select Modify.
-
Delete the value data in this entry that refers to
SSOLauncher. (C:\Program Files\Passlogix\v-GO SSO\wts\ssolauncher.exe /nossoshutdown) -
If you are using Windows Authentication v1, add the
CheckForParentProcesskey to the Passlogix registry hive. This ensures authentication event handoff to Logon Manager.HKEY_LOCAL_MACHINE\SOFTWARE\Passlogix\AUI\WinAuth\DWORD:CheckForParentProcessValue=0
Removing ssolauncher.exe from AppSetup configures Logon Manager not to function with any applications on this Citrix server unless specified in your published applications configuration.
2.16.5.2.2 Specifying Which Applications Are SSO-Enabled Through the Published Application Configuration (SSOLauncher)
Since Logon Manager support is now globally disabled, you must specify which applications you wish to be published with Logon Manager support by including the SSOLauncher.exe command in the published application properties.
-
Open Citrix Management Console.
-
Publish/Locate the application you would like to enable for Logon Manager.
-
Right-click on the published application and select Properties.
-
On the Application Location tab, add to the front of the Command Line the following syntax:
C:\Program Files\Passlogix\v-GO SSO\wts\SSOLauncher.exe/application
The command for SSOLauncher.exe is added to your published application's command line; it does not replace it.
Following is an example of the Command Line syntax for the application ACT:
C:\Program Files\Passlogix\v-GO SSO\wts\SSOLauncher.exe" /application C:\Program Files\ACT\act.exe
Note:
This example is based on the assumption that Logon Manager and ACT are both installed on the C:\ drive of the Citrix Server.See SSOLauncher for Citrix Servers for more information.
2.16.5.2.3 Enabling Citrix Server Monitoring
To enable Logon Manager to be monitored by Citrix Server, so that Logon Manager will not keep otherwise-ended sessions alive, go to the following registry tree:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\ Wfshell\TWI
If an entry named LogoffCheckSysModules exists, append to it the following items:
-
ssosehell.exe -
ssocredcap64.exe -
ssocredcap.exe -
ssobho.exe -
ssox64ho.exe -
ssowebho.exe -
ssomho.exe -
ssosapho.exe -
idcontext.exe -
ssoauth.exe
For example, change:
app1.exe,app2.exe
to:
app1.exe,app2.exe,ssoshell.exe,ssocredcap64.exe
and so forth.
If the current LogoffCheckSysModules includes ssomozho.exe, remove this executable.
If the entry does not exist, create LogoffCheckSysModules as type STRING and set to include the executables above.
Also see the reference topic, Best Practices for Deploying the Agent in a Citrix Environment.
2.16.5.3 SSOLauncher for Citrix Servers
This utility lets you control the delivery Logon Manager with published applications in a Citrix Server environment.
To use the ssolauncher utility:
-
Copy the
ssolauncherutility in theWINNT\system32folder. Otherwise you must include the full path to where ssolauncher resides. -
You can now manage the applications you that you want Logon Manager to run by utilizing the ssolauncher utility. By accessing the Citrix Published Application Management console and applying the ssolauncher command through the Application Definition command line, you can make Logon Manager run on an application-by-application basis.
Note:
Thessolauncher command is applied in front of the command line. For example:
ssolauncher.exe /application "C:Program Files\Internet Explorer\IEXPLORE.EXE"
The following are the commands for ssolauncher:
| Command | Function |
|---|---|
| /application | The full path of the application to execute. This is required. |
| /command | Used to supply command parameters to an application. This is optional. |
| /directory | Used to supply working to an application. This is optional. |
| /wait | The number of milliseconds to wait for an application to shut down. This is optional. If not specified ssolauncher will wait forever for the application to terminate. |
| /verbose | This supplies dialogs for error message if ssolauncher has any failures. |
| /nossoshutdown | Prevents shutting down SSO when application completes. |
| /SSOCOMMAND LOGON | Used to initiate a command to the "Log On Using Logon Manager" trigger, located in the Logon Manager system tray icon. |
For example, the following command line launches AIM:
ssolauncher.exe /verbose /application "C:\Program Files\AIM95\aim.exe" /directory "C:\Program Files\AIM95"
Note:
The command should begin and end with quotation marks if it contains backslash (\) characters.2.17 Configuring the Agent with Global Agent Settings
This section discusses the ways in which an administrator can configure the Agent's behavior. It begins with a discussion of the differences between using Global Agent Settings and administrative overrides: the best practices for the use of each, and which is preferable to use for different functions.
Following the best practice discussion is a complete list of Global Agent Settings, including all setting options, registry paths, and default values.
2.17.1 Global Agent Settings vs. Administrative Overrides
Logon Manager's behavior, including its interaction with the directory, is governed by settings configured and deployed to the end-user machine by the Logon Manager administrator using the Administrative Console. The settings fall into one of the following categories:
-
Global Agent settings are the "local policy" for the Agent; they are stored in the Windows registry on the end-user machine and are included in the Logon Manager
MSIpackage to provide the Agent with an initial configuration during deployment.Global Agent settings are stored in
HKEY_LOCAL_MACHINE\Software\Passlogix(32-bit systems) orHKEY_LOCAL_MACHINE\Wow6432Node\Software\Passlogix(64-bit systems).Note:
Users able to modify theHKLMhive can alter their Global Agent Settings and thus change the behavior of the Agent from the one originally intended. To ensure that a setting will not be changed by the end-user, deploy it through an administrative override. -
Administrative overrides take precedence over the Global Agent Settings stored in the Windows registry and constitute the "domain" policy for the Agent. Overrides are downloaded from the central repository by the Agent during synchronization and stored in the Agent's encrypted and tamper-proof local cache, which makes them immune to end-user alterations. When role/group security is enabled, administrative overrides can be applied on a per-user or per-group basis; they can also be applied enterprise-wide to enforce configuration consistency for all users.
Note:
Be conservative when planning your administrative overrides. Fewer overrides mean less data to store and transfer, and thus more efficient synchronization with the central repository. Reducing the number of overrides also simplifies troubleshooting by eliminating unknowns, as administrative overrides cannot be viewed on the end-user machine.
Global Agent settings together with administrative overrides constitute the complete configuration policy for the Agent. The rest of this section describes the recommended optimal configuration.
Following is a typical view of the Administrative Console:
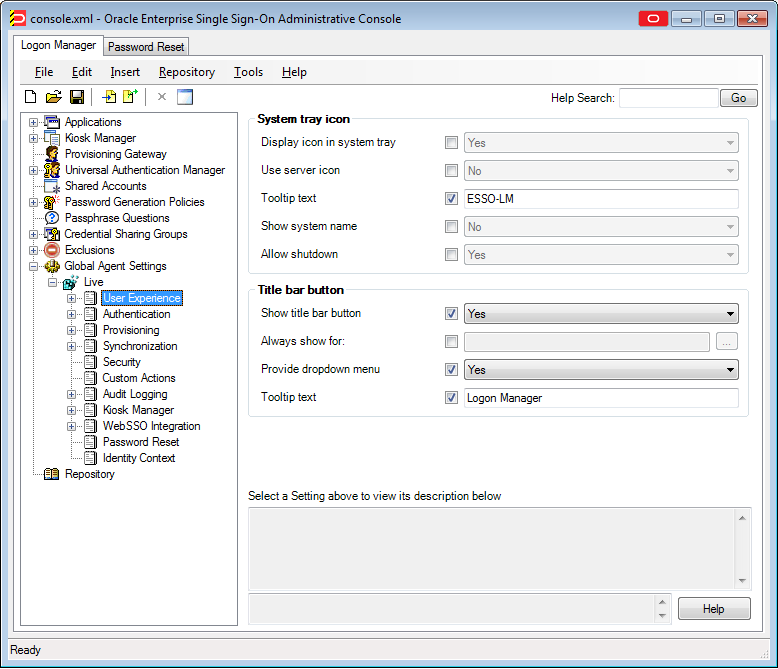
Note:
In a development or staging environment, disable the option Check for publisher's certificate revocation in Internet Explorer to eliminate a delay when the Administrative Console launches and your machine is not connected to the Internet. (The delay is caused by Internet Explorer's attempting to look up the server's certificate and timing out when a certificate authority cannot be reached.) Do not disable this option on production machines.The best practice for settings not described in this and other Logon Manager guides is to leave them at their default values, unless your environment dictates otherwise. The default value is automatically in effect whenever the check box for the setting in the Administrative Console is left blank. The value is visible in the inactive field next to the check box.
2.17.1.1 Recommended Global Agent Settings
This section lists Oracle-recommended best-practice Global Agent Settings. Configure the settings as described below and include them in the customized Logon Manager MSI package.
2.17.1.1.1 Allow User to Exclude Accounts from Credential Sharing Groups
Credential sharing groups allow you to share a single credential among a group of applications; the credential is managed at the group level, and the changes propagate instantly to all applications in the group. When an application is part of a credential sharing group and the user has more than one set of credentials for the application, all but the shared credentials must be excluded from the group. This feature gives users the ability to exclude logons from assigned credential sharing groups.
Located in: Global Agent Settings > Live > User Experience > Password Change
To enable: Select the check box, then select Allow from the drop-down list.
When this option is enabled, users can exclude a logon as follows:
-
In the "Logon Manager" window, select the logon you want to exclude from the assigned group.
-
Click Properties.
-
In the dialog that appears, select the Exclude from password sharing group check box.
-
Click OK.
-
Click Refresh to synchronize the changes with the central repository.
2.17.1.1.2 Restrict Disconnected Operation
As a best practice, the Agent should run even if it cannot reach the central repository so that users can receive the benefits of single sign-on when not on the corporate network. Before working offline, the user must have done the following:
-
Completed the First Time Use (FTU) wizard while connected to the repository to generate encryption keys that protect the user's credentials. The keys are stored in the repository and in the Agent's local cache.
-
Synchronized with the repository at least once to obtain templates, policies, and any pre-provisioned credentials. These items are stored in the Agent's local cache for offline use.
If the user has successfully synchronized on one machine and completes the FTU on a secondary machine (such as a laptop) that has never been used with Logon Manager and is not connected to the repository, the keys generated on the secondary machine will not match the keys already stored in the repository. The secondary machine will not be able to synchronize with the repository due to this mismatch.
In order to avoid this problem and still allow users to work offline, do the following:
-
In your custom
MSIpackage, configure the Agent not to run when disconnected from the repository, as shown below:Located in: Global Agent Settings > Live > Synchronization

To set: Select the check box, then select No from the drop-down list.
-
After deployment, push an administrative override that lifts this restriction, as described in Allow the Agent to Run when Disconnected from the Repository. (The override will be in effect after first successful synchronization.)
2.17.1.1.3 Select the Primary Authenticator for End-Users
Oracle highly recommends that you select and configure the primary authenticator in the following scenarios:
-
If you want to disable the First-Time Use (FTU) wizard, as described in Do Not Show the First-Time Use Wizard.
-
If you want users to authenticate only via the selected primary authenticator.
For information on configuring specific authenticators, see the Authentication section of the Global Agent Settings.
Note:
If this setting is left blank and the FTU wizard is disabled, the first installed logon method (in descending alphabetical order) is automatically selected by default. To view the list of installed authenticators, temporarily enable the setting and examine its drop-down list.Located in: Global Agent Settings > Live > User Experience > Setup Wizard
To set: Select the check box, then select the desired logon method from the drop-down list.
2.17.1.1.4 Do Not Show the First-Time Use Wizard
When Logon Manager starts for the first time, the FTU wizard appears and prompts the user to:
-
Restore credentials and settings from a backup file (if a backup exists).
-
Select the primary logon method.
-
Authenticate to Logon Manager using the selected primary logon method.
-
Provide credentials for default applications.
As a best practice, avoid burdening end-users with setting up Logon Manager manually. Instead, disable the FTU wizard, select the primary authenticator as described in the previous section, and provision the required applications beforehand; at that point, the only thing users will need to provide on the first launch of Logon Manager is their Windows password.
Located in: Global Agent Settings > Live > User Experience > Setup Wizard
To disable: Select the check box, then select No from the drop-down list.
2.17.1.1.5 Disable the Reauthentication Timer
Disable the reauthentication timer so that users are not interrupted by unexpected reauthentication prompts. (The user is prompted at the next secure operation that occurs after the timer expires.)
Note:
This is not an inactivity timer; this function is best served by the secure screensaver included in the operating system.Located in: Global Agent Settings > Live > Security
To disable: Select the check box, then enter 4,294,967,295 in the field; this value disables the timer.
2.17.1.1.6 Use the Default Encryption Algorithm
Do not change the default encryption algorithm (AES MS CAPI) that Logon Manager uses to encrypt application credentials to retain compatibility with all supported operating systems. Not all algorithms supported by Logon Manager function with all operating systems. (The operating systems supported by a given algorithm are listed next to the algorithm's name in the drop-down list.)
Note:
Oracle strongly advises you to use MS CAPI algorithms to retain FIPS compliance across your enterprise.Located in: Global Agent Settings > Live > Security
To set: Select the check box, then select the desired encryption method from the drop-down list.
Oracle recommends that you leave this setting at the default value shown above.
2.17.1.2 Recommended Administrative Overrides
This section lists recommended best-practice administrative overrides. Configure the overrides as described below and push them to the central repository. The overrides will be applied to end-user machines during the next synchronization event.
2.17.1.2.1 Configure Silent Credential Capture
Logon Manager provides the ability to automatically (silently) capture credentials when a user logs into a supported application for the first time instead of displaying the interactive wizard. To simplify the user experience, Oracle recommends that you take advantage of this feature, but configure it so that users are aware that Logon Manager is capturing their credentials; fully silent capture (without user notification) may lead to trust issues (most users prefer to have a choice whether their credentials are captured or not) and increase incoming helpdesk calls as a direct result.
-
For most applications, set the Credential capture mode option to Capture and inform the user with balloon tip.
-
For applications that do not support silent credential capture (such as applications that require Logon Manager to use the SendKeys response method), set the Credential capture mode option to Do not capture silently.
Located in: Global Agent Settings > Live > Use Experience > Application Response > Initial Credential Capture
To set: Select the check box, then select the desired value from the drop-down list.
2.17.1.2.2 Make the Logon Manager Agent Wait for Synchronization on Startup
To ensure that users always have the most recent credentials, application templates, password policies, and administrative overrides, configure the Agent to wait for synchronization on startup. When this option is enabled, the Agent checks whether the directory is online when initializing and does one of the following:
-
If the directory is online, the Agent does not respond to application logon requests until it successfully synchronizes with the directory.
-
If the directory is offline, the Agent does not attempt to synchronize and starts immediately.
Located in: Global Agent Settings > Live > Synchronization
Use the default value shown above unless your environment requires otherwise.
2.17.1.2.3 Use Optimized Synchronization
Optimized synchronization instructs the Logon Manager Agent to synchronize only credentials that have changed since the last synchronization. Do one of the following, depending on your environment:
-
Enable this option to improve synchronization performance on deployments with more than five credentials per user.
-
Disable this option to improve synchronization performance on deployments with fewer than five credentials per user and large number of downloaded templates per user.
Located in: Global Agent Settings >Live > Synchronization
Use the default value shown above unless your environment requires otherwise.
2.17.1.2.4 Allow the Agent to Run when Disconnected from the Repository
This override is required to lift the restriction placed on the Agent in its initial configuration as described in Restrict Disconnected Operation. When this override is applied, users will benefit from single sign-on capability while not on the corporate network.
Located in: Global Agent Settings > Live > Synchronization
To allow: Select the check box, then select Yes from the drop-down list.
Note:
This override must be applied in tandem with the restriction described in Restrict Disconnected Operation.2.17.1.2.5 Set the Optimal URL Matching Precision for Web Applications
URL matching precision determines how many levels within a URL are considered when matching the URL of an application to that defined in the template. If the URL matching precision is set too low, Logon Manager might mistake one intranet application for another and respond with incorrect credentials. If URL matching precision is set too high, an application served through a distributed infrastructure with unique host names may be erroneously recognized as separate applications due to the varying host name.
Follow these guidelines when determining the optimal URL matching precision for your environment:
-
Typically, set URL matching precision to 5 (the maximum value). This will ensure that Logon Manager only responds when the URL of the application requesting logon exactly matches the URL stored in the template. The auto-recognize feature will have limited functionality.
-
If you want to get the maximum benefit from the Logon Manager auto-recognize feature for Web applications, leave URL matching precision at its default value of 2. However, response to intranet applications might be impaired.
Located in: Global Agent Settings > Live > User Experience >Application Response > Web Applications
To set: Select the check box, then enter the desired value in the field.
2.17.1.2.6 Limit Users to Predefined Applications
Logon Manager allows you to prevent users from storing credentials for applications for which templates do not exist in the repository. To simplify the user experience while maintaining a degree of flexibility, Oracle recommends that you do the following, based on the type of application:
-
Windows applications. Determine and provision the required applications before users begin working with Logon Manager. Instruct Logon Manager to store credentials only for applications for which templates already exist in the repository. Since users will not be prompted to store credentials for unprovisioned Windows applications, you retain full control of the single sign-on process for your enterprise applications.
Located in: Global Agent Settings > Live > User Experience > Application Response >Initial Credential Capture
To set: Select the check box, then select Predefined applications only from the drop-down list.
-
Web applications. To provide the maximum value of single sign-on, you should allow users to store credentials for Web applications of their choice (by using this option's default value of Unlimited). Note, however, that users will be prompted to store credentials for each unprovisioned Web application every time they access it, until credentials are successfully stored. For this reason, Oracle recommends that you set this option to Predefined applications only rather than Unlimited. In the end, your decision will depend on the needs of your organization.
Located in: Global Agent Settings > Live > User Experience > Application Response > Initial Credential Capture
To set: Select the check box, then select Unlimited from the drop-down list.
Note:
The individual options shown above take precedence over the All applications option.
2.17.1.2.7 Create and Set the Company Password Change Policy
By default, Logon Manager ships with an inadequate default password change policy that must be replaced with a new policy which meets the security requirements of your organization. Include the name of your organization in the policy name to indicate that it is not a built-in policy. You must create this policy before setting this option; for instructions on creating a password change policy, see Adding a Password Policy.
Located in: Global Agent Settings > Live > User Experience > Password Change
To set: Select the check box, then select the desired policy from the drop-down list.
Note:
The policy set as the default password change policy is in effect enterprise-wide.2.17.1.2.8 Force Reauthentication when Revealing Masked Fields
To prevent unauthorized access to stored application passwords, configure Logon Manager to prompt the user to authenticate when the "reveal masked fields" feature is invoked within the Agent. Configuring this policy as an administrative override will also prevent a rogue administrator from manually adding the setting to the local machine's registry and gaining unauthorized access to the local user's passwords if the setting is left unconfigured during initial deployment.
Located in: Global Agent Settings > Security
To set: Select the check box, then select Yes from the drop-down list.
2.17.1.2.9 Select an Audit Logging Method
Configure and use audit logging to make troubleshooting your installation efficient. The audit method you choose will depend on the needs of your organization; a quick summary of the available methods is provided below.
-
Syslog and Windows Event Logging Server are the methods of choice for most organizations.
-
Databases are also supported (a valid ODBC connection string to the database is required).
-
If you want to implement a custom event logging system, Logon Manager offers the "XML File" option which exposes raw log data that can be directly parsed by an external application. (Be aware that the raw log data are not self-cleaning and will grow indefinitely unless cleaned up externally.)
For more information on the available audit methods, see Audit Logging Settings.
2.17.1.2.10 Select Event Types to Log
If you are using an audit logging method other than the Reporting Server, you must select the types of events that should be logged. Oracle highly recommends logging all event types for maximum benefit during troubleshooting.
Note:
You must select the Event Types: Info item in addition to the desired event types. This item is the parent to all event types and is required for data capture.Located in: Global Agent Settings > Audit Logging > Selected Audit Logging Method>
To set: Select the check box, then select the desired event types in the dialog that appears. When you are finished, click OK to dismiss the dialog.
2.17.2 Working with a Set of Global Agent Settings
Global Agent Settings contain defaults, switches, and other configuration information that modify the behavior of Logon Manager on the desktop. Double-click items in the list in the right pane to view or modify the individual settings. Click Add Notes to enter notes about this set of settings.
To view a set of Global Agent Settings:
-
Do one of the following:
-
Click Global Agent Settings in the left pane, then double-click a set of settings from the right pane.
or
-
In the left pane, click the plus sign (+) next to the Global Agent Settings icon (or double-click Global Agent Settings) to display the sets of settings.
-
-
Do one of the following:
-
Select a Global Agent Settings icon. The list of individual settings appears in the right pane.
or
-
Right-click a Global Agent Settings icon to display a shortcut menu with these options:
Control Function Export Save the selected set of settings to a registry file or administrative override object. Write to Live HKLM Export the current Agent configuration to the local-machine registry (HKLM). Test Launch the Logon Manager Configuration Test Manager, which tests your connections and adjusts settings, if necessary. Manage Synchronizers Add, delete, and reprioritize synchronizers. Delete Delete the selected set of settings. Make copy Duplicate the selected set of settings. Rename Rename the selected set of settings. Publish Opens the Publish to Repository dialog, from which you can select the Global Agent Settings and other objects you want to publish. Publish To Allows you to select a location to which to publish the selected set of Global Agent Settings. -
2.17.2.1 Creating and Importing Global Agent Settings
The Global Agent Settings contain Agent configuration information and provide access to stored sets of Global Agent Settings. To create or import a set of Global Agent Settings:
-
Click Global Agent Settings in the left pane to display a list of sets of Global Agent Settings in the right pane.
-
Right-click Global Agent Settings in the left pane to display a shortcut menu with these options:
Control Function New Settings Create a new set of Global Agent Settings. Displays the Settings dialog. Import Import a set of Global Agent Settings from an external source: From File Import a set of settings from an administrative override object ( INI) file or a registration-entries (REG) file. Navigate to the file and click Open.From Live HKLM Import the current Agent configuration from the local-machine registry ( HKLM) as a set of settings named Live.Publish Opens the Publish to Repository dialog, from which you can select the Global Agent Settings and other objects you want to publish. Note:
If the imported settings have the same name as an existing set in the current configuration, the imported set is named "Copy of" existing settings.If this version of the Administrative Console is installed on a foreign operating system (any operating system other than English), do not use the New Settings option. Rather, use the Import option. If you use the New Settings option, the path for the synchronization extension points to an invalid location, which results in a synchronization failure.
2.17.2.2 Adding a Set of Global Agent Settings
Use this dialog to add and name a new set of Global Agent Settings.
-
Enter the Set of Settings Name and click OK.
To display this dialog:
-
Right-click Global Agent Settings and choose New Settings from the shortcut menu.
or
-
Choose Global Agent Settings from the Insert menu.
2.17.2.3 Exporting a Set of Global Agent Settings
To export a set of Global Agent Settings:
-
(Optional) Select Unicode format for the
.REGfile, if desired. See Export Format for options for this menu. -
Click an option.
-
In the File Save dialog, locate and open the folder for each file, name the file, and click Save.
To display this dialog:
-
Right-click the Global Agent Settings icon in the left pane and select Export from the shortcut menu.
2.17.2.4 Export Format
Use this dialog to select an output format for the selected set of settings.
| Control | Function |
|---|---|
| Administrative Override Object | Export the settings as an administrative override object (INI) file. |
| HKLM Registry | Export the settings as a registration-entries (REG) file. |
| Both | Export both file types. |
Unicode encoding (.REG format only) |
Export the .REG file in Unicode format. |
Note:
The Console produces a.REG file compatible only with 32-bit systems. If you are merging the .REG file on a 64-bit system, you must run the following command to move the merged registry data to the correct location within the registry (otherwise, Universal Authentication Manager will not function):
reg.exe COPY HKLM\Software\Passlogix HKLM\Software\Wow6432Node\Passlogix /s
2.17.3 Global Agent Settings in Depth
This section provides detailed information about each Global Agent Setting. The settings are listed in the order in which they appear in the Administrative Console. Each listing includes the setting's registry path, description, setting options (if applicable), default (if applicable), whether the setting is overrideable, and the registry and data types.
2.17.3.1 User Experience
The User Experience settings control the Agent as a Windows application, including its interactions with the end user and with other programs.
2.17.3.1.1 System tray icon
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Display icon in system tray
|
Specifies whether to show the Logon Manager icon in the system tray. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Use server icon
|
Specifies whether to use the alternative server icon, as opposed to the standard system tray icon. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Tooltip text
|
Specifies the text to display when the mouse hovers over the system tray icon. (Recommended use: Label each Citrix Server/Terminal Services/Remote server) | 63 characters maximum
(Default: Oracle Enterprise Single Sign-On Logon Manager) |
Yes | string/Ø |
| Show system name
|
Specifies whether to append the computer name to the tooltip text, separated by a space-dash-space. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Allow shutdown
|
Specifies whether the "Shut Down" option is enabled on the system tray icon menu for the end user. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Pause behavior
|
Specifies the behavior of the Pause option in the context menu of the Logon Manager tray icon. | 0: Pause indefinitely (Default)
1: Do not allow pause 2: Self un-pause after pause timeout |
Yes | dword/Ø |
| Pause timeout
|
Specifies the length of time the pause will last, in milliseconds when Pause behavior is set to Self un-pause after a pause timeout; has no effect otherwise. | Minimum: 0ms
Maximum: 1800000ms Default: 60000ms |
Yes | dword/int |
2.17.3.1.2 Title bar button
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Show title bar button
|
Specifies whether to show the Logon Manager button on all window title bars. This button can be configured for single-click application recognition and response, or it can provide a menu similar to the system tray menu, by changing the "Provide Dropdown Menu" setting. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Always show for
|
Identifies a list of applications (by executable filename, such as "notepad.exe") for which the title bar button should always be displayed. This setting overrides the "Show title bar button" setting.
Click the ellipsis button ("…") button to enter the application names. Separate application names with a carriage return. |
Yes | string/Ø | |
| Provide dropdown menu
|
Specifies whether to show the menu from the title bar button. If turned off, the title bar button acts as a single-click button for application recognition and response. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Tooltip text
|
Specifies the text to display when the mouse hovers over the title bar button. | Default: Oracle Enterprise Single Sign-On Logon Manager | Yes | string/Ø |
2.17.3.2 Application Response
The Application Response settings control the behavior of the Agent when the end user provides credentials for new logons and when detecting applications requiring logons.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Log on to waiting applications upon Agent startup
|
Enables the Agent, at startup, to submit credentials to a Windows or Java application that has already presented its logon form before the Agent was initialized and ready.
Note: Web and host/mainframe application logons are not affected by this setting. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| SendKeys event interval
|
Specifies the minimum time to allow between SendKeys key events. This is especially useful for eastern languages where keystrokes are sometimes lost.
Note: Logon Manager does not support credential submission using Journal Hook SendKeys. |
0: Best speed (Default)
60: Typical for eastern languages 80: Use for slow system 120: Use for very slow system |
Yes | dword/Ø |
| Respond to hidden and minimized windows
|
Specifies whether the Agent will respond to hidden and minimized windows.
Note: This setting must be disabled when using Kiosk Manager. |
0: Yes (Default)
1: No |
Yes | dword/Ø |
| Applications that hooks should ignore
|
Specifies applications that are incompatible with hooks, and which Logon Manager should therefore ignore. Click the ellipsis "…" button and enter the list of paths to exclude, separating items with semi-colons. This list can include full paths or sub-strings of paths.
Example: To exclude all applications from all folders whose paths contain "C:\Program Files\Java," and all folders whose paths contain "Administrative Console," enter the following:
Note: This setting is specifically for applications that might cause loss of functionality for compatibility reasons. Such applications might be discovered only in a production environment. Do not use this setting for applications that are compatible with Logon Manager functionality; for these applications, use the exclude/ignore settings on the appropriate application-type settings pages. You cannot use this setting as an administrative override. |
Yes | string/ string |
2.17.3.3 Initial Credential Capture
The Initial Credential Capture settings control the behavior of the Agent when it first encounters an application.
2.17.3.3.1 User interface
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Credential capture mode
|
Specifies how the Agent should respond when it encounters a new application requiring credentials, and the level of involvement on the user's part.
Silent credential capture mode is not compatible with applications that require SendKeys. For this reason, you cannot use this mode for host/mainframe applications, nor for any Web or Windows application for which you use SendKeys. You should not use silent credential capture for applications where the username and password are obfuscated. Silent Credential Capture for on-the-fly Web applications requires a "Submit" element with one of the following tags:
You must create a template for a Web application if the "Submit" element has an underlying tag of <img> or <a>. |
0: Do not capture silently. Presents the New Logon dialog in which the user enters credentials manually.
1: Capture, but do not inform user. The Agent captures the credentials as the user enters them, and does not inform the user of the process. 2: Capture, and inform user with balloon tip (Default) The Agent captures the credentials as the user enters them, and displays a balloon tip near the system tray to inform the user during the process. 3: Capture, and present New Logon dialog. The Agent captures the credentials as the user enters them, and displays a balloon tip near the system tray to inform the user during the process. After capturing the credentials, the Agent displays the New Logon dialog with the user's entries pre-filled. The user can accept, change, cancel, or disable. |
Yes | dword/Ø |
| Enable Auto-Prompt
|
Specifies whether to automatically prompt the user to add a logon when a new application is detected. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Enable Auto-Enter
|
Specifies whether to log on to an application after configuring it (adding its credentials).
Note: The end-user can override this setting by deselecting it in the Logon Manager "Response" tab. |
0: No
1: Yes (Default) |
Yes | dword/Ø |
| Enable Auto-Recognize
|
Specifies whether to automatically provide credentials to applications.
Note: The application configuration-specific setting overrides the global setting. |
0: No
1: Yes (Default) |
Yes | dword/Ø |
| Allow creating multiple accounts during credential capture
|
Specifies whether to enable the checkbox in the New Logon dialog that allows the user to add another set of credentials. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Prohibit canceling the addition of new accounts
|
Specifies whether the user has the option to click the Cancel button or close the "New Logon" dialog to defer entering credentials. This permits current access to an application and re-prompts the user to enter credentials at the next appropriate instance. | 0: Yes
1: No (Default) |
Yes | dword/Ø |
| Prohibit disabling the addition of new accounts
|
Specifies whether the Disable button is available in the New Logon dialog, allowing the user to reject adding credentials for applications permanently.
Note: Disabling an application adds it to the Exclusions list in Agent settings. |
0: Yes
1: No (Default) |
Yes | dword/Ø |
| Prohibit excluding accounts from credential sharing groups
|
Specifies whether to disable the checkbox in the New Logon dialog that allows an account to be excluded from credential sharing groups. This checkbox will be available for the "Account Properties" dialog. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.3.3.2 Limit response to predefined applications for…
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| All application types
|
Sets the following options:
The "Predefined applications only" setting prohibits both options. The 'Unlimited' setting permits both options. |
0: Predefined applications only
1: Unlimited (Default) |
Yes | dword/Ø |
| Windows applications
|
Specifies whether the users is allowed to add credentials for Windows applications that are not predefined by the administrator. | 0: Predefined applications only
1: Unlimited (Default) |
Yes | dword/Ø |
| Web applications
|
Sets the following options:
The "Predefined applications only" setting prohibits both options. The "Unlimited" setting permits both options. The "Manually add undefined" setting prohibits the first option and permits the second option. |
0: Predefined applications only
1: Unlimited (Default) 2: Manually add undefined |
Yes | dword/Ø |
| Allowed Web pages
|
Use this setting to list the Web pages that the Agent should allow. Click the ellipsis "…" button to add the allowed Web pages and enter the regular expressions that match the URLs. (There is no default for this setting.)
Note: Use this setting only when you select "All application types" or "Web applications" for "Predefined applications only." |
Yes | string/Ø |
2.17.3.4 Web Application Response
The Web Applications Response settings control the behavior of the Agent with Web applications.
Because some Web applications contain content that changes with each visit, you can configure a Web template to re-scan dynamic Web pages, detect changes, and respond appropriately.
2.17.3.4.1 Credential field identification
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Show border
|
Specifies whether to display a highlighted border around the credential fields of a Web form during logon. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Border appearance
|
Default border color/size/style for highlighting detected web page fields.
See Border Values for Web Logon Credential Fields for more information. |
Default: red 6px solid | Yes | string/ string |
2.17.3.4.2 Behavior
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| URL matching precision
|
Number of levels of the host portion of the URL used for application detection and response.
For example, for the URL http://mail.company.co.uk: 2=match to 3=match to 4=match to Note: Values less than 2 are treated as 2. |
Minimum: 2 (Default)
Maximum: 5 |
Yes | dword/int |
| Scroll into view
|
Enables or disables scrolling the browser window to bring the logon fields into view.
This setting disables scrolling when the user has not yet stored credentials for a Web application. The Agent always scrolls when injecting credentials into the logon fields for an account that already exists. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Activate tab
|
Enables or disables activating the tab that identifies the logon fields. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Respond to IE modal dialogs
|
Enables Agent response to a Web page that displays as a modal dialog or HTML application. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.3.4.3 Response control
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Applications to ignore
|
Enter a comma-delimited list of applications (without path or extension) that the Browser Helper Object (BHO) should not attach to when searching for logons. Used when the BHO causes conflicts with certain applications.
Example: |
Yes | string/Ø | |
| Web pages to ignore
|
Use this setting to list the Web pages that the Agent should ignore. Used when the BHO causes conflicts with specific web applications or sites. Click the ellipsis ("…") button to enter the regular expressions that match the URLs to be ignored (one per line).
Examples:
|
Yes | string/Ø | |
| Allowed dynamic Web pages
|
Use this setting to list the dynamic (DHTML) Web pages allowed by the Agent. By default, the BHO does not detect changes made to a dynamic page after the initial presentation of the page.
Click the ellipsis ("…") button to enter the regular expressions that match the URLs. Examples:
|
Yes | string/Ø |
2.17.3.5 Windows Application Response
The Windows Applications Response setting controls the behavior of the Agent with Windows applications.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Allow fallback from Control IDs to SendKeys
|
Allows fallback to SendKeys when direct injection of credentials using Control IDs fails. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Supported Window Classes for Applications
|
Specifies the list of window class names that the Agent recognizes as applications. This setting is provided to improve performance by restricting the Agent to this list. To enable support for dynamic window classes, delete the default settings to set this value to null. | #32770;Dialog;ThunderRT5 FormDC; ThunderRT6FormDC (Default) |
Yes | string/ string |
| Ignored Window Classes for Applications
|
Specifies the list of window class names that the Agent does not recognize as applications. This setting allows you to direct the Agent to ignore a specific window class globally. | No default | Yes | string/ string |
2.17.3.6 Java Application Response
The Java Application Response settings control the behavior of the Agent with Java applications.
2.17.3.6.1 Exclusions
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Excluded Java versions
|
Specifies Java versions to exclude, listed as regular expressions. Enter one expression per line. | No | string/Ø | |
| Excluded Java vendors
|
Specifies Java vendors to exclude, listed as regular expressions. Enter one expression per line.
This setting is new as of Logon Manager version 11.1.1.5.0. |
No | string/Ø |
2.17.3.6.2 Response delays
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Time allowed for Java applets to load
|
Specifies the maximum time (in seconds) that the Agent waits for a Java applet to be fully loaded in the browser. | (Default: 6) | Yes | dword/int |
| Delay after Java runtime startup
|
Specifies the length of time (in milliseconds) the JHO should wait before listening to window events at Java startup. Adding a delay can resolve timing conflicts during Java runtime initialization. | (Default: 0) | Yes | dword/int |
| Delay between retries
|
Specifies the length of time (in milliseconds) the JHO should wait between retries of credential injection into a form control. | (Default: 500) | Yes | dword/int |
2.17.3.6.3 Retry behavior
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Maximum times to retry credential injection
|
Specifies the number of times to retry credential injection. | (Default: 0) | Yes | dword/ int |
2.17.3.6.4 Java events to respond to
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Hierarchy events
|
Specifies which Java hierarchy events are recognized. Set the flag using the following syntax:
This instructs the JHO to recognize all hierarchy events. |
(Default: 0) | Yes | dword/int |
| Window events
|
Specifies which Java window events are recognized. | A combination of the following values:
(Default: 255-All window events are recognized.) The recommended setting for new installations of Logon Manager is 3. |
Yes | dword/int |
| Component events
|
Specifies which Java component events are recognized. | A combination of the following values:
(Default: 15-All component events are recognized.) The recommended setting for new installations of Logon Manager is 0xB (11). |
Yes | dword/int |
| Injection type
|
Specifies the injection type that the JHO uses to submit data to the controls. | One of the following values:
Note: For combo and list boxes, the JHO always uses |
Yes | dword/int |
2.17.3.7 Host/Mainframe Application Response
The Host/Mainframe Response settings control the behavior of the Agent with host/mainframe applications.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| 16-bit screen capture attempts
|
Specifies the number of times to attempt the 16-bit screen capture. If an attempt is unsuccessful after the allotted number of tries, the Agent reverts to the 32-bit method. | (Default: 5) | Yes | dword/ int |
| Credential request delay interval
|
Specifies the interval (in milliseconds) between prompts to create a logon for a mainframe session.
When a user logs on to a mainframe session that matches a configured application for which there is no stored password, the Agent prompts the user: "Would you like Logon Manager to remember your logon information for this application?" If the user selects Not Now, the next time the user presses any key on the mainframe screen, the Agent prompts the user again. This delay setting is the amount of time the Agent should wait before displaying the question again. |
(Default: 60000) | Yes | dword/int |
| Polling interval
|
Specifies the interval (in milliseconds) between instances when the Agent checks the host emulator for changes. Lower values can use more CPU time; higher values can increase the time between when a screen appears and when the Agent provides credentials. | (Default: 700) | Yes | dword/int |
2.17.3.8 Password Change
The Password Change settings control the Agent behavior and policies for password generation and credential maintenance.
2.17.3.8.1 Password change behavior
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Default password policy
|
Name of the Password Generation Policy that application templates will use when no policy is defined in the application template. To define this setting, ensure that you currently have a defined/named policy loaded in the console, so the dropdown allows you to select the policy.
Note: If no policy is defined here or in the template, a default policy of exactly eight alpha-only characters applies. For this reason, it is important to define a more appropriate policy. |
Yes | string/Ø | |
| Allow user to exclude accounts from credential sharing groups
|
Allows end user to exclude application logons from an assigned credential sharing group.
Enabling this option causes a check box to appear on the New Logon and Properties dialogs, giving the user the choice to omit accounts from credential sharing groups. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Change passwords automatically
|
Specifies the level of control given to the user in the password change process. |
|
Yes | dword/Ø |
| Manual password change behavior
|
Specifies the behavior of the Password Change Wizard when a user encounters a password-change request. |
|
Yes | dword/Ø |
| Pop-up dialog text after submission
|
To change the default text, select the checkbox and highlight the current text, then type in new text. To restore default text, unselect the checkbox. | Default: After closing this message, verify that the application accepted the password. Select OK if it was accepted. If it was rejected, please try again. | Yes | string/Ø |
2.17.3.8.2 Allowed character sets
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Lowercase characters
|
Specifies the list of lowercase alphabet characters to allow in passwords. | Any lowercase characters
(Default: All lowercase characters) |
Yes | string/Ø |
| Uppercase characters
|
Specifies the list of uppercase alphabet characters to allow in passwords. | Any uppercase characters
(Default: All uppercase characters) |
Yes | string/Ø |
| Numeric characters
|
Specifies the list of numeric characters to allow in passwords. | Any numeric characters
(Default: All numeric characters) |
Yes | string/Ø |
| Special characters
|
Specifies the list of non-alphanumeric (special) characters to allow in passwords | !@#$^&*()_-+=[]\|,? (Default) | Yes | string/Ø |
2.17.3.9 User Interface
The User Interface settings control the appearance of the Agent when performing a logon and of the information presented in the Logon Manager and "Logon Chooser" dialog.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Language
|
Specifies the language in which to present the user interface.
Note: Other values may be acceptable based on localized versions. The display font should support the desired characters in the specified language. |
English (Default)
Chinese (Simplified) Chinese (Traditional) Czech Danish Dutch Finnish French German Greek Hungarian Italian Japanese Korean Norwegian Polish Portuguese (Brazil) Portuguese (Portugal) Romanian Russian Slovak Spanish Swedish Thai Turkish |
Yes | string/Ø |
| Allow refresh in My Accounts
|
Enables/disables the SSO Manager Refresh button. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Columns in "Details" view of My Accounts
|
Click the ellipsis "…" button to display the Edit Columns dialog. Choose the appearance and order of columns in the Logon Manager. | 1: Application Name
2: URL/Module 3: Username/ID 4: Password 5: Modified 6: Last Used 7: Description 8: Reference 9: Group 10: Third Field 11: Fourth Field (Default: 1,2,3,4,5,6,7,8,9) |
Yes | string/Ø |
| Columns in Logon Chooser
|
Click the ellipsis "…" button to display the Edit Columns dialog. Choose the appearance and order of columns in the Agent's "Logon Chooser" dialog. | 1: Username/ID
2: Application Name 3: Description (Default: 1,2,3) |
Yes | string/Ø |
| Logon animation's duration
|
Specifies the duration (in milliseconds) that the animated spinner appears (pausing response). A value of 0 (the default) disables the spinner. | (Default: 0) | Yes | dword/int |
2.17.3.9.1 Edit Columns
Use the Edit Columns dialog to select and order the logon details that appear as columns in the Agent's Logon Manager and Logon Chooser dialogs.
-
To add detail columns, select the columns in the Available list, then click >> to move your selections to the Selected list.
-
To remove detail columns, select the columns in the Selected list, then click << to move your selections to the Available list.
-
To change the order of the columns, select a column in the Available list and click Up or Down.
2.17.3.10 Setup Wizard
The Setup Wizard settings control the behavior of the First-Time-Use Wizard, which launches when you start Logon Manager for the first time. See First-Time-Use Scenarios for more information.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Show first-time-use (FTU) wizard
|
Controls whether the Setup Wizard displays when first-time-use is invoked.
Note: If more than one authenticator (primary logon method) is installed, then the first authenticator in the list is automatically selected as the end user's primary logon method. You must have the FTU Wizard enabled in order to use the Bulk-Add feature. |
0: Yes (Default)
1: No |
Yes | dword/Ø |
| Selected authenticator
|
Enables the selected logon method as the primary logon method and hides all other installed logon methods.
Note: To hide the primary logon method selection menu, use the "Show first-time-use (FTU) wizard" setting. If the primary logon method selection page is hidden, and this setting is blank, then the first installed logon method in the list is automatically selected. |
None (Default: End-users select their own primary logon method)
MSauth: Windows v2 WinAuth: Windows LDAPauth: LDAP v2 LDAP: LDAP SCauth: Smart Card ROSCAuth: Read-Only Smart Card ProxcardAuth: Proximity Card SecureIDAuth: RSA SecurID Entrust: Entrust MultiAuth: Authentication Manager UAMAuth: Universal Authentication Manager |
Yes | string/Ø |
| Skip selection page if only one authenticator is installed
|
Hides the Select Primary Logon Method step in the Setup Wizard if only one authenticator (primary logon method) is installed. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.3.11 Authentication
Use the Global Agent Authentication Settings to configure the overall authentication environment and individual authenticator settings. Select a topic below to learn more about authentication options.
-
Authentication Manager. This pane and its sub-panes contain settings that apply to your overall authentication configuration.
-
Enrollment
-
Grade
-
Order
-
-
Authenticator Panes. Each pane contains settings applicable to a specific authenticator.
-
Windows v2
-
Windows v2 Passphrase
-
Windows (deprecated)
-
LDAP v2
-
LDAP v2 Special Purpose
-
LDAP
-
LDAP Special Purpose
-
Smart Card
-
Read-Only Smart Card
-
Proximity Card
-
-
Secure Data Storage. Refer to this section for information about configuring storage for use with strong authenticators.
-
Strong Authentication. Refer to this section for information about advanced configuration of strong authenticators, such as cards and tokens.
2.17.3.12 Authentication Manager
The Authentication Manager setting controls the number of authenticators and their priority.
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Allowed number of authenticators
|
Specifies the maximum number of logon methods that the Agent offers the user to select. If the user receives and skips this number of logon methods, a "Choose Logon" dialog appears.
Note: This setting is only used for the Multi-Authenticator primary logons. |
(Default: 1) | Yes | dword/int |
2.17.3.12.1 Enrollment Settings
The Authentication Manager Enrollment settings specify the primary logon methods (authenticators) that can be used by the Multi-Authenticator primary logon.
The settings on this page will determine whether a user will be required to set up a specific logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. Use these settings for Multi-Authenticators only.
For each primary logon method, select one of the following:
-
Disabled. The logon method will not be presented to the user during the FTU Wizard.
-
Optional. Logon Manager will have the option to configure this logon or to skip it. If the user defers the logon request, Logon Manager will not ask again. (Default)
-
Required. The user will be required to configure this logon. If this logon is not configured, the user will not be able to complete enrollment.
-
Incremental. Logon Manager will have the option to configure this logon or to skip it. If the user defers the logon request, Logon Manager will ask for credentials each time the application starts.
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Windows v2
|
Specifies whether a user will be required to set up Windows v2 as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| Windows
|
Specifies whether a user will be required to set up Windows as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
Note: Windows Authenticator is deprecated as of version 11.1.2 and is listed for upgrade scenarios only. Do not use this authenticator for new configurations. |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| LDAP v2
|
Specifies whether a user will be required to set up LDAP v2 as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| LDAP
|
Specifies whether a user will be required to set up LDAP as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| Smart card
|
Specifies whether a user will be required to set up smart card as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| Read-only smart card
|
This setting determines whether a user will be required to set up read-only smart card as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| Proximity card
|
Specifies whether a user will be required to set up proximity card as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| RSA SecurID
|
Specifies whether a user will be required to set up RSA SecurID as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| Entrust
|
Specifies whether a user will be required to set up Entrust as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method. | 0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| Universal Authentication Manager
|
Determines whether a user will be required to set up Universal Authentication Manager as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
This setting is only used for Multi-Authenticator primary logons. |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| ESSO-UAM: Windows Password
|
Determines whether a user will be required to set up Universal Authentication Manager: Windows Password as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
This setting is only used for Multi-Authenticator primary logons. |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| ESSO-UAM: Fingerprint
|
Determines whether a user will be required to set up Universal Authentication Manager: Fingerprint as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
This setting is only used for Multi-Authenticator primary logons |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| ESSO-UAM: Smart Card
|
Determines whether a user will be required to set up Universal Authentication Manager: Smart Card as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
This setting is only used for Multi-Authenticator primary logons. |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| ESSO-UAM: Proximity Card
|
Determines whether a user will be required to set up Universal Authentication Manager: Proximity Card as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
This setting is only used for Multi-Authenticator primary logons. |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
| ESSO-UAM: Challenge Questions
|
Determines whether a user will be required to set up Universal Authentication Manager: Challenge Questions as a primary logon method during the First Time Use Wizard, if Authentication Manager is chosen as the primary logon method.
This setting is only used for Multi-Authenticator primary logons. |
0: Disabled
1: Optional (Default) 2: Required 3: Incremental |
Yes | dword/Ø |
2.17.3.12.2 Grade Settings
The Authentication Manager Grade settings specify an authentication grade for each primary logon method.
Authentication Grades are numeric values:
-
An authentication grade automatically defaults to grade level 1 if authentication grading is turned on and no grade level is specified.
-
The higher the grade level specified, the stronger the authentication level that is being requested.
-
The grading scale can be arbitrarily configured. For example, an expected normal scenario would be a scale of 1-3, but you have the flexibility to make this 1-5 or 1-n, as required. Any grade less than 1 will be converted to 1.
The Multi-Authenticator logon supports the authentication grades by mapping the grades to the authentication methods used, if you choose Authentication Manager as the primary logon method.
If a user tries to access credentials with a grade level that is too low, he will be asked to authenticate at a higher grade and only gain access if successful.
Lockouts occur as per normal Logon Manager authentication lockout policy. Since graded authentication uses the core SSO authentication process, this will happen naturally.
Set a number grade value (≥1) for each logon method. Use these settings for Multi-Authenticators only.
| Display Name/ Registry Path | Description Text | Options/Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Windows v2
|
Assigns an authentication grade to Windows v2. Set a number grade value (≥1). The higher the grade level specified, the stronger the authentication level that is being requested. | (Default: 1) | Yes | dword/Ø |
| Windows
|
Assigns an authentication grade to Windows. Set a number grade value (≥1).
Note: Windows Authenticator is deprecated as of version 11.1.2 and is listed for upgrade scenarios only. Do not use this authenticator for new configurations. |
(Default: 1) | Yes | dword/Ø |
| LDAP v2
|
Assigns an authentication grade to LDAP v2. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| LDAP
|
Assigns an authentication grade to LDAP. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| Smart card
|
Assigns an authentication grade to Smart card. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| Read-only smart card
|
Assigns an authentication grade to read-only smart card. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| Proximity card
|
Assigns an authentication grade to Proximity card. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| RSA SecurID
|
Assigns an authentication grade to RSA SecurID. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| Entrust
|
Assigns an authentication grade to Entrust. Set a number grade value (≥1). | (Default: 1) | Yes | dword/Ø |
| Universal Authentication Manager
|
Assigns an authentication grade to Universal Authentication Manager. Set a number grade value (>=1).
This setting is only used for Multi-Authenticator primary logons. |
(Default: 1) | Yes | dword/Ø |
| ESSO-UAM: Windows Password
|
Assigns an authentication grade to Universal Authentication Manager: Windows Password. Set a number grade value (>=1).
This setting is only used for Multi-Authenticator primary logons. |
(Default: 1) | Yes | dword/Ø |
| ESSO-UAM: Fingerprint
|
Assigns an authentication grade to Universal Authentication Manager: Fingerprint. Set a number grade value (>=1).
This setting is only used for Multi-Authenticator primary logons |
(Default: 1) | Yes | dword/Ø |
| ESSO-UAM: Smart Card
|
Assigns an authentication grade to Universal Authentication Manager: Smart Card. Set a number grade value (>=1).
This setting is only used for Multi-Authenticator primary logons. |
(Default: 1) | Yes | dword/Ø |
| ESSO-UAM: Proximity Card
|
Assigns an authentication grade to Universal Authentication Manager: Proximity Card. Set a number grade value (>=1).
This setting is only used for Multi-Authenticator primary logons. |
(Default: 1) | Yes | dword/Ø |
| ESSO-UAM: Challenge Questions
|
Assigns an authentication grade to Universal Authentication Manager: Challenge Questions.
This setting is only used for Multi-Authenticator primary logons. |
(Default: 1) | Yes | dword/Ø |
2.17.3.12.3 Order Settings
The Authentication Manager Order settings specify the sequence in which the installed logon methods will be presented to the end user during reauthentication scenarios, if Authentication Manager is chosen as the primary logon method.
For each primary logon method, select or enter a number to indicate the logon method's position in the FTU/logon order. Use these settings for Multi-Authenticators only.
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Windows v2
|
Sets the ordered position for Windows v2. This will be the order that Windows v2 will be presented to the end user during reauthentication scenarios. | (Default: 2) | Yes | dword/int |
| Windows
|
Sets the ordered position for Windows. This will be the order that Windows will be presented to the end user during reauthentication scenarios.
Note: Windows Authenticator is deprecated as of version 11.1.2 and is listed for upgrade scenarios only. Do not use this authenticator for new configurations. |
(Default: 2) | Yes | dword/int |
| LDAP v2
|
Sets the ordered position for LDAP v2. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 3) | Yes | dword/int |
| LDAP
|
Sets the ordered position for LDAP. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 3) | Yes | dword/int |
| Smart card
|
Sets the ordered position for smart card. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 1) | Yes | dword/int |
| Read-only smart card
|
Sets the ordered position for read-only smart card. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 1) | Yes | dword/int |
| Proximity card
|
Sets the ordered position for proximity card. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 6) | Yes | dword/int |
| RSA SecurID
|
Sets the ordered position for RSA SecurID. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 6) | Yes | dword/int |
| Entrust
|
Sets the ordered position for Entrust. This will be the order that Windows will be presented to the end user during reauthentication scenarios. | (Default: 4) | Yes | dword/int |
| Universal Authentication Manager
|
Sets the ordered position for Universal Authentication Manager. This will be the order that Universal Authentication Manager will be presented to the end user during reauthentication scenarios.
This setting is only used for Multi-Authenticator logons. |
(Default: 10) | Yes | dword/int |
| ESSO-UAM: Windows Password
|
Sets the ordered position for Universal Authentication Manager: Windows Password. This will be the order that the method will be presented to the end user during reauthentication scenarios.
This setting is only used for Multi-Authenticator logons. |
(Default: 11) | Yes | dword/int |
| ESSO-UAM: Fingerprint
|
Sets the ordered position for Universal Authentication Manager: Fingerprint. This will be the order that the method will be presented to the end user during reauthentication scenarios
This setting is only used for Multi-Authenticator logons |
(Default: 12) | Yes | dword/int |
| ESSO-UAM: Smart Card
|
Sets the ordered position for Universal Authentication Manager: Smart Card. This will be the order that the method will be presented to the end user during reauthentication scenarios.
This setting is only used for Multi-Authenticator logons. |
(Default: 13) | Yes | dword/int |
| ESSO-UAM: Proximity Card
|
Sets the ordered position for Universal Authentication Manager: Proximity Card. This will be the order that the method will be presented to the end user during reauthentication scenarios.
This setting is only used for Multi-Authenticator logons. |
(Default: 14) | Yes | dword/int |
| ESSO-UAM: Challenge Questions
|
Sets the ordered position for Universal Authentication Manager: Challenge Questions. This will be the order that the method will be presented to the end user during reauthentication scenarios.
This setting is only used for Multi-Authenticator logons. |
(Default: 15) | Yes | dword/int |
2.17.3.13 Windows v2 Authenticator Settings
The Windows v2 authenticator settings are the primary controls for the Windows Authenticator version 2.
Note:
Windows Authenticator version 2 is the preferred authenticator for Logon Manager and is installed by default. For more information about this authenticator, see Section 7.2.7, "Configuring Windows Authenticator Version 2".2.17.3.13.1 Recovery
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Recovery method
|
Specifies the reset method to use when the user's password changes. | 4ED42DB8-B8F1-4AE6-B13A-272F74B48FE7: User passphrase (Default)
B623C4E7-A383-4194-A719-7B17D074A70F: Passphrase suppression using user's SID 7B4235FF-5098-435c-9A05-052426D96AA8: Passphrase suppression using secure key |
Yes | string/Ø |
| Use Windows Data Protection (DPAPI)
|
Set to Yes to use a DPAPI key to protect the Kiosk Manager encryption key, instead of the traditional two-key system of User Password and Recovery Key.
Note: Consult Microsoft and Oracle DPAPI best practices to ensure your Active Directory and desktop infrastructure is capable and configured to use DPAPI. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.3.13.2 User interface
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Window title
|
Use this setting to customize the window title name for this authenticator. Check the box and enter the desired name.
Note: This entry is not required. |
Yes | string/ string |
|
| Window subtitle
|
Use this setting to customize the window subtitle name for this authenticator. Check the box and enter the desired name.
Note: This entry is not required. |
Yes | string/ string |
|
| Custom image for authentication prompt
|
Enter the fully-qualified path, including the file name, to the image, or click the ellipsis ("…") button and browse to the image file.
Note: The image file must be in bitmap (.bmp) format. The dimensions set for this image are 300 pixels wide by 100 pixels tall. You cannot change these dimensions. If the image is smaller it will be centered in this area; if it is larger, it will be cropped equally on all sides. |
No | string/ filename |
|
| Reauthentication dialog
|
Select which method to use when Logon Manager requires the end-user to re-authenticate.
Note: While the setting is called "Use GINA," it also applies to the Credential Provider mechanism in Windows Vista and newer operating systems. |
0: Use SSO dialog. (Default) The user is presented with an authentication dialog whenever reauthentication is needed, and at initial enrollment.
1: Use GINA. The Windows desktop is locked, and the user must reauthenticate to the operating system (using whatever GINA or Credential Provider is installed) before Logon Manager is unlocked. |
Yes | dword/Ø |
| Domains
|
Specifies the domain(s) whose member users are permitted to authenticate. Enter one or more desired NetBIOS domain names separated by commas. | No | string/Ø | |
| Prefill username/ID on FTU
|
Select whether to have Logon Manager populate the Windows Authenticator V2 authentication dialog with the current user's username/ID.
Note: This setting is applicable only at FTU. |
0: No-User must fill these fields manually.
1: Yes -Logon Manager populates these fields automatically (Default) |
Yes | dword/Ø |
2.17.3.13.3 Connection information
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Use SSL
|
Specifies whether to connect via SSL.
Note: This setting applies only to Domain Change Password scenarios. |
0: No (insecure) (default to port #389)
1: Yes (default to port #636) (Default) |
Yes | dword/Ø |
2.17.3.13.4 Credential sharing
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Include in Domain credential sharing group
|
Enables credential sharing from the authenticator to credentials in a special credential sharing group called "Domain." Whenever the authenticator detects a new password, the password is automatically shared with the Domain credential sharing group. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Share credentials with other authenticators
|
Eliminates double authentication by linking authenticator credentials. If multiple authenticators use the same credentials, the duplicate credentials are used without requiring the user to reenter them.
Enter a comma-separated list of authenticators to share the credentials with, for example " Note: To locate other authenticator names, refer to the list located under |
Yes | string/ string |
|
| Share credentials with synchronizers
|
This setting eliminates double authentication when an authenticator shares credentials with one or more synchronizers.
Enter a comma-separated list of synchronizers to share the credentials with, for example " Note: To locate other synchronizer names, see the name listed in the registry for that synchronizer (located under |
Yes | string/ string |
2.17.3.14 Windows v2 Authenticator Passphrase Settings
The Windows v2 Authenticator Passphrase settings configure options for users' Windows Authenticator version 2 passphrases.
2.17.3.14.1 User interface
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Message
|
Use this setting to display a user agreement-style dialog where the user must check a checkbox to continue. This is typically used to suggest the importance of the passphrase that users enter. Check the box and enter the desired message.
Note: This message can contain multiple lines, 180 character maximum. The character sequence " |
Yes | string/ string |
|
| Message dialog title
|
Use this setting to customize the user agreement-style dialog title. Check the box and enter the desired title. | Yes | string/ string |
|
| Checkbox label
|
Use this setting to customize the user agreement style dialog checkbox. Check the box and enter the desired label.
Note: The user must check this checkbox before the dialog can be dismissed. The OK button is disabled until this checkbox is checked. |
Yes | string/ string |
2.17.3.14.2 Options
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Minimum length
|
Default required length of a passphrase. You can override this setting by specifying the required length for a specific question. | 8: Default | Yes | dword/int |
| User can change passphrase
|
Toggles availability of the user's option to change the answer to the verification question. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Reset with old password
|
Allows the previous password to be used in the passphrase process. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Force password re-enrollment when using old password to reset
|
Specifies whether the user can skip the Logon Manager passphrase prompt. Enabling this feature ensures that after a user enters his previous Windows password, Logon Manager will prompt him to enter a new passphrase.
Warning: Disabling this feature entails the risk of a complete lockout to Logon Manager. This can happen if a user no longer remembers his passphrase, and subsequently forgets his Windows password. In this scenario, a user would be completely locked out of Logon Manager. |
0: Yes (Default)
1: No |
Yes | dword/Ø |
2.17.3.15 Windows Authenticator Settings
The Windows authenticator settings are the primary controls for the Windows Authenticator.
Note:
Windows Authenticator is deprecated as of version 11.1.2 and is listed for upgrade scenarios only. Do not use this authenticator for new configurations.2.17.3.15.1 User interface
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Window title
|
Use this setting to customize the window title name for this authenticator. Check the box and enter the desired name.
Note: This entry is not required. |
Yes | string/ string |
|
| Window subtitle
|
Use this setting to customize the window subtitle name for this authenticator. Check the box and enter the desired name.
Note: This entry is not required. |
Yes | string/ string |
|
| Custom image for authentication prompt
|
Enter the fully-qualified path, including the file name, to the image, or click the ellipsis "…" button and browse to the image file.
Note: The image file must be in bitmap (.bmp) format. The dimensions set for this image are 300 pixels wide by 100 pixels tall. You cannot change these dimensions. If the image is smaller it will be centered in this area; if it is larger, it will be cropped equally on all sides. |
No | string/ filename |
|
| Require old password when Windows password changes
|
Provides enhanced security by requiring the user to enter the previous password when changing to a new one. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.3.15.2 Credential sharing
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with other authenticators
|
This setting eliminates double authentication by linking authenticator credentials. If multiple authenticators use the same credentials, the duplicate credentials are used without requiring the user to reenter them.
Enter a comma-separated list of authenticators to share the credentials with, for example " Note: To locate other authenticator names, refer to the list located under |
Yes | string/ string |
|
| Share credentials with synchronizers
|
This setting eliminates double authentication when an authenticator shares credentials with one or more synchronizers.
Enter a comma-separated list of synchronizers to share the credentials with, for example " Note: To locate other synchronizer names, see the name listed in the registry for that synchronizer (located under |
Yes | string/ string |
2.17.3.16 LDAP v2 Authenticator Settings
The LDAP v2 authenticator settings are the primary controls for enabling LDAP version 2 authentication.
2.17.3.16.1 Recovery
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Recovery method
|
Specifies the method for recovering a user's lost password.
Note: For an in-depth discussion of LDAP v2 configuration, see Chapter 7, "Understanding the Logon Manager Secondary Authentication API." |
User passphrase (Default)
Passphrase suppression using user's SID Passphrase suppression using secure key Passphrase suppression using entryUUID |
Yes | string/Ø |
2.17.3.16.2 Connection information
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Directory type
|
Specifies the type of the target directory server software. If your server software is not listed, select LDAP-compliant Directory Server. | Unspecified LDAP Directory
Microsoft Active Directory Novell eDirectory LDAP-compliant Directory Server Oracle Directory Server Enterprise Edition IBM Tivoli Directory Server Oracle Internet Directory Siemens DirX Directory Server |
Yes | dword/Ø |
| Servers
|
Enter the servers to try, in the format "computer[:port]" (one server per line), where computer is the server name or IP, and port is assumed to be default (636 for SSL, 389 for no SSL) if not specified.
Examples:
Note: You musty specify at least one server for this extension to work. |
No | string/Ø | |
| User paths
|
Enter the fully-qualified path to where the user account is located. There can be unlimited paths to search. The extension searches these in order, looking for the user account. If not found, the extension will search the directory tree.
Note: You must either specify a value for UserPrepend or at least one value for |
Yes | string/Ø | |
| Use SSL
|
Specifies whether to connect via SSL. | 0: No (insecure) (default to port #389)
1: Yes (default to port #636) (Default) |
Yes | dword/Ø |
2.17.3.16.3 User interface
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Window title
|
Use this setting to customize the Window title name for this authenticator.
Note: This entry is not required. |
Yes | string/ string |
|
| Show user path
|
Enable this setting to display the User path combo box control in the LDAP v2 authentication dialog. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Custom image for authentication prompt
|
Enter the fully-qualified path, including the file name, to the image, or click the ellipsis "…" button and browse to the image file.
Note: The image file must be in bitmap (.bmp) format. The dimensions set for this image are 300 pixels wide by 100 pixels tall. You cannot change these dimensions. If the image is smaller it will be centered in this area; if it is larger, it will be cropped equally on all sides. |
Yes | string/ filename |
2.17.3.16.4 Credential sharing
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with other authenticators
|
Enter a comma-separated list of authenticators with which to share the credentials, for example "WinAuth, MSAuth."
Note: For other authenticator names, refer to the list located under HKLM\Software\Oracle\AUI. |
Yes | string/ string |
|
| Share credentials with synchronizers
|
Enter a comma-separated list of synchronizers to share the credentials with, for example "ADEXT,LDAPEXT."
Note: For other synchronizer names, refer to the list located under |
Yes | string/ string |
|
| Include in LDAP credential sharing group
|
Enables credential sharing from the authenticator to credentials in the Group Domain. (Also requires AccessManager:PWSEnable to be enabled.) |
0: No
1: Yes (Default) |
Yes | dword/Ø |
2.17.3.17 LDAP v2 Authenticator Special Purpose Settings
The LDAP v2 Authenticator Special Purpose settings control special-case options for enabling standard LDAP v2 authentication.
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Naming attribute string
|
String to prepend to UserPaths when the DN for a user is in the form of:
instead of the form:
(where Note: Usually, you must set this value to |
Yes | string/ string |
|
| BIND timeout
|
Enter the length of the timeout (in milliseconds) of LDAP BIND call. | (Default depends on the operating system) | Yes | dword/ int |
| Alternate user ID location
|
Specifies where to locate a user object when the user validates against an attribute other than the username.
Example If users authenticate with an employee ID # for logon (validation against the empid attribute) and the user object is in:
set UserLocation to
instead of to
Note: For Novell eDirectory, UserLocation should be: If using |
Yes | string/ string |
2.17.3.18 LDAP Authenticator Settings
The LDAP authenticator settings are the primary controls for enabling standard LDAP authentication. These settings must be used in order for the Agent to use LDAP as a primary logon method.
2.17.3.18.1 Connection information
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Directory type
|
Specifies the type of directory server. If the directory server is not listed, select "Generic LDAP Directory." | 0: Unspecified LDAP Directory
3: Novell eDirectory 5: Generic LDAP Directory (Default) 8: Oracle Directory Server Enterprise Edition 9: IBM Tivoli Directory Server 10: Oracle Internet Directory 11: Siemens DirX Directory Server |
Yes | dword/Ø |
| Servers
|
Specifies the servers to try, in the format computer[:port] (one server per line), where computer is the server name or IP, and port is assumed to be default (636 for SSL, 389 for no SSL) if not specified.
Examples
Note: You must specify at least one server in order for this extension to work. |
No | string/Ø | |
| User paths
|
Specifies the fully-qualified path to where the user account is located.
There can be unlimited paths to search. The extension searches these in order, looking for the user account. If the account is not found, the extension will search the directory tree. Note: You must specify a value for either UserPrepend or at least one value for UserPaths for this extension to work. If using UserPaths, do not use UserLocation. |
Yes | string/Ø | |
| Use SSL
|
Specifies whether to connect via SSL. | No. (insecure) (default to port #389)
Yes. (default to port #636) (Default) |
Yes | dword/Ø |
2.17.3.18.2 Active Directory
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Enable Domain name support
|
Enables Active Directory Domain name support. End users can specify the Domain name (for example, domainname\username) at primary logon.
Alternatively, the administrator can specify a default Domain name (see the "Active Directory: Default Domain name" setting, below) to let end users log on by username alone. If you don't specify a Domain, Logon Manager uses the local workstation's Domain. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Default Domain name
|
The Active Directory Domain name to use for primary logon if you don't specify a Domain for the username/ID credential (for example, domainname\username).
Use this setting only if you set the "Active Directory: Domain name support enabled" setting to "Use AD Domain names." If you enable Domain name support and this setting is blank (and the end user does not specify a Domain), Logon Manager uses the local workstation's Domain. |
Yes | string/ string |
2.17.3.18.3 User interface
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Window title
|
Use this setting to customize the Window title name for this authenticator.
Note: This entry is not required. |
Yes | string/ string |
|
| Password change window title
|
Use this setting to customize the Active Directory Change Password Window title name for this synchronizer.
Note: This entry is not required. |
Yes | string/ string |
|
| Password change window subtitle
|
Use this setting to customize the Active Directory Change Password Window subtitle name for this synchronizer.
Note: This entry is not required. |
Yes | string/ string |
|
| Custom image for authentication prompt
|
Enter the fully-qualified path, including the file name, to the image, or click the ellipsis "…" button and browse to the image file.
Note: The image file must be in bitmap (.bmp) format. The dimensions set for this image are 300 pixels wide by 100 pixels tall. You cannot change these dimensions. If the image is smaller it will be centered in this area; if it is larger, it will be cropped equally on all sides. |
No | string/ filename |
|
| Show user path
|
Use this setting to show/hide the User Path combo box control in the LDAP authentication dialog. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
2.17.3.18.4 Credential sharing
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with other authenticators
|
Enter a comma-separated list of authenticators with which to share the credentials. For example "WinAuth, MSAuth."
Note: To locate other authenticator names, refer to the name listed in the registry for that authenticator (located under: |
Yes | string/ string |
|
| Share credentials with synchronizers
|
Enter a comma-separated list of synchronizers with which to share the credentials. For example "ADEXT,LDAPEXT."
Note: To locate other synchronizer names, refer to the name listed in the registry for that synchronizer (located under: |
Yes | string/ string |
2.17.3.19 LDAP Authenticator Special Purpose Settings
The LDAP Authenticator Special Purpose settings control special-case options for enabling standard LDAP authentication.
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Naming attribute string
|
Specifies the string to prepend to UserPaths when the DN for a user is in the form of:
instead of the form:
(where Note: Usually, you must set this value to If using |
Yes | string/ string |
|
| BIND timeout
|
Specifies the timeout (in milliseconds) of the LDAP BIND call. | Default depends on the operating system. | Yes | dword/ int |
| Alternate user ID location
|
Specifies where to locate a user object when the user validates against an attribute other than the username.
Example If users authenticate with an employee ID # for logon (validation against the empid attribute) and the user object is in:
set UserLocation to
instead of to
Note: For Novell eDirectory, UserLocation should be: If using UserLocation, do not use UserPrepend or UserPaths. |
Yes | string/ string |
|
| Enable directory search for users
|
Enables or disables directory search for the user account.
When the user account is not found in the given path, the authenticator will search for it from that location down the directory tree. The search is performed whether using "User Paths" or the "Alternate User ID location." |
0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.4 Using Strong Authenticators
Logon Manager includes both standard logon methods such as LDAP and Windows Logon, and strong authenticators such as smart cards, proximity devices, and RSA SecurID tokens. Logon Manager enables organizations to seamlessly bridge strong authentication to all of their applications. Users can employ different authenticators at different times and application access can be controlled based upon the authenticator used.
Note:
See the Oraclecertification matrix for the most up-to-date list of supported authentication devices.Logon Manager provides authentication support from a variety of strong authenticators for all authentication events: initial authentication, re-authentication, and forced authentication.
This section describes any specific settings that can be enabled within a strong authenticator in order for the authenticator to work with Logon Manager. It also describes all the Administrative Console settings and any steps that must be taken to integrate with Kiosk Manager, as well as any known issue or technical notes that apply to a specific strong authenticator.
2.17.5 Strong Authenticator Configuration Settings
If the strong authenticator you are using is not listed in this section, there are no specific settings that must be adjusted or relevant technical notes.
Select your strong authenticator, or see the Kiosk Manager integration notes, which apply to all authenticators:
2.17.5.1 Smart Cards
Smart Card settings are available in the Authentication section of Global Agent Settings in the Administrative Console. This section also includes steps that you must take to integrate Smart Cards with Kiosk Manager, and other technical notes about using this authenticator.
2.17.5.1.1 Administrative Console Settings
The smart card settings control special-case options for smart-card authentication. These settings are not required.
To access the smart card settings, click Global Agent Settings > Live > Authentication > Smart Card. See the Smart Card Authentication section for a full discussion of these settings.
2.17.5.1.2 Smart Card Initialization
Prior to use with Authentication Manager, smart cards must be initialized and contain a valid PIN. If Authentication Manager is configured to use smart card certificates, smart cards must contain a valid PKI certificate. If the smart cards are also to be used with Kiosk Manager, they must have a serial number.
Authentication Manager does not provide any smart card initialization, configuration, or administration services, so this step must be performed using a third-party Card Management System (CMS) or middleware administration utility compatible with your smart card.
2.17.5.2 Integrating with Kiosk Manager
This section applies when using the Smart Card authenticator with Kiosk Manager.
2.17.5.2.1 Support for storing and passing through the synchronization credentials with Kiosk Manager and Smart Card integration.
When using Smart Card authenticator with Kiosk Manager, the user's synchronization credentials can optionally be stored on the smart card by the authenticator. If stored in this manner, the credentials are then silently passed through to Logon Manager after a user initiates a Kiosk Manager session by inserting their smart card into the reader and entering the correct PIN. This feature prevents a double authentication when starting a Kiosk Manager session whereby the user authenticates with their smart card and PIN and then is subsequently prompted by Logon Manager to provide their synchronization username and password.
2.17.5.2.2 .NET Smart Cards.
Due to technical limitations with the .NET cards, when using .NET smart cards with Kiosk Manager, inserting the smart card when Kiosk Manager is locked always causes a new session to start. To unlock an existing session, click the Unlock Existing Session link.
2.17.5.2.3 Separate Authentication Prompts Appear for the Kiosk Manager Session and Logon Manager when Smart Card is the Primary Logon Method.
In a Kiosk Manager environment that uses smart cards as the primary logon method, users are prompted to authenticate separately to Kiosk Manager and Logon Manager.
This occurs because a smart card authentication is only valid for the process that initiated it and cannot be shared between processes. This is a design characteristic of the smart card middleware and not Oracle software.
When the Kiosk Manager session starts, Kiosk Manager queries the smart card middleware for authentication and the user is prompted to authenticate via smart card and PIN. This authentication is valid for the Kiosk Manager process only; therefore, when the Kiosk Manager session is successfully created and Logon Manager starts, the user is authenticated again, this time to Logon Manager.
This double-prompt can be eliminated by configuring an Active Directory/AD LDS (ADAM) synchronizer to use the card's certificate and the smart card authenticator to share credentials with synchronizers. Configure the following settings:
-
On the Global Agent Settings' Smart Card Authenticator Settings, add ADEXT or ADAMSyncExt to the list for the setting, "Share credentials with synchronizers."
-
On the Global Agent Settings' Active Directory/AD LDS (ADAM) synchronizer pages Credential sharing group, add SCAuth to the list for the setting, "Share credentials with authenticators."
-
On the Global Agent Settings' Active Directory/AD LDS (ADAM) synchronizer pages' Connection information group, select Use card's certificate for Credentials to use.
-
On the Global Agent Settings' Kiosk Manager page, disable the setting, Pre-populate on startup under the Strong authenticator options group.
2.17.5.2.4 HID Crescendo C200 and C700 smart cards.
When using HID Crescendo C200 or C700 as smart cards with Kiosk Manager, a smart card-only reader should be used. Using a dual function smart card and proximity card reader is unsupported. The HID Crescendo C200 mini-driver should be installed from Microsoft's update catalog: http://test.catalog.update.microsoft.com/v7/site/search.aspx?q=umdf.
2.17.5.2.5 Using SSO-Generated Keys Technical Note.
When the Use default certificate for authentication (located in the Logon Manager Administrative Console Global Agent Settings > Authentication > Smart Card) is set to No, users may be prompted to enter their PIN twice during the First Time Use (FTU) enrollment process.
This is normal and necessary in order to create the SSO keyset. Subsequent authentications after FTU only prompt users to enter their PIN once.
2.17.5.3 Smart Card Middleware
These technical notes are in reference to known issues and considerations with Smart Card middleware.
2.17.5.3.1 Gemplus Libraries 4.20 with Authentication Manager
Re-authentication events do not display the PIN dialog. When authenticating to Logon Manager, the first authentication properly displays a PIN dialog and allows a successful authentication. Subsequent re-authentication events within a short period of time do not display the PIN dialog, preventing authentication from succeeding.
To work around this, restart the Logon Manager process requesting authentication.
2.17.5.3.2 Netmaker Net iD 4.6 with Kiosk Manager
When starting a new Kiosk Manager session, the user's synchronization credentials are not read off the card. After entering their PIN, users must then manually enter their synchronization credentials to start the session.
2.17.5.3.3 RSA RAC 2.0 / Smartcard Middleware 2.0 with Kiosk Manager
RSA Middleware reports that no smart cards are present when Kiosk Manager is locked and a smart card is inserted into a reader. Sessions must be manually started. After Kiosk Manager is unlocked, authentication to Logon Manager with smart cards will work as expected.
2.17.5.3.4 Smart Card and Read-Only Smart Card Middleware Default Library Path Locations
The following table provides the default installation paths for all supported smart card middleware. These are sample paths to enter in the PKCS #11 Library Path field located on the Read-Only Smart Card > Advanced and Smart Card > Advanced panels:
| Smart Card Type | Library Path |
|---|---|
| Axalto Access Client Software 5.2 | C:\Program Files\Axalto\Access Client\v5\xltCk.dll |
| GemSafe Libraries 4.2.0 | C:\Program Files\Gemplus\GemSafe Libraries\BIN\GCLIB.DLL |
| HID C700 middleware | aetpkss1.dll |
| NetMaker Net iD 4.6 | iidp11.dll |
| RSA Authentication Client 2.0 / Smartcard Middleware 2.0 | C:\Program Files\RSA Security\RSA Authentication Client\Pkcs11.dll |
| SafeSign/RaakSign Standard 2.3 | aetpkss1.dll |
| Schlumberger Cyberflex Access 4.5 | C:\Program Files\Schlumberger\Smart Cards and Terminals\Cyberflex Access Kits\v4\slbCk.dll |
| Siemens 3.2.41 (CardOS API v3.2) | siecap11.dll |
| Read-Only Smart Card Type | Library Path |
|---|---|
| Fujitsu mPollux DigiSign Client 1.3.2-34(1671) | C:\Program Files\Fujitsu Services\Fujitsu mPollux DigiSign Client\Cryptoki.dll |
| SafeSign Identity Client 2.2.0 | aetpkss1.dll |
Note:
Any file without a fully-qualified path listed in the tables above resides in the system directory and therefore does not require a full path when being specified.2.17.5.4 Smart Card Authenticator Settings
The Smart Card authenticator settings control special-case options for smart card authentication. Also see Smart Cards in the Strong Authenticators section for configuration with Kiosk Manager and technical notes.
2.17.5.4.1 Options
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Smart card library
|
Specifies whether to use the Cryptographic Service Provider (CSP) or the PKCS #11 library to perform cryptographic operations on the smart card.
Note: Set this to PKCS # 11 only if using SafeSign/RaakSign middleware. |
0: CSP (Default)
1: PKCS#11 |
Yes | dword/Ø |
| Use default certificate for authentication
|
Specifies whether to use the default logon certificate (provided by the administrator) on the card for authentication. With this setting disabled (the default), the public/private keys in the SSO container on the card will be used (and created if necessary). | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Store synchronization credentials
|
Specifies whether to store the user's synchronization repository credentials on the smart card.
Store credentials when using smart card authorization in conjunction with Kiosk Manager and/or if using the read-only smart card authenticator. Note: Performance improves when credentials are not stored on the smart card because the read/write operation adds time to the authentication process. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Store the PIN
|
Specifies whether to store the smart card PIN (creating the possibility that the Agent might prompt for the PIN), or to let the smart card drivers handle the PIN request. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| PKCS#11 Library Path
|
Specifies the path to the smart card middleware file, which implements the PKCS#11 standard. | Yes | string/ string |
|
| Custom certificate check extension path
|
Specifies the path to the custom certificate check extension.
Note: This entry is not required. |
Yes | string/ string |
|
| Allow secure PIN entry
|
Specifies whether to allow users to enter a PIN on a smart card reader keypad that supports secure PIN entry.
Note: You cannot use secure PIN entry in conjunction with a PIN recovery group. |
0: Only allow non-SPE login (Default)
1: Only allow SPE login |
Yes | dword/Ø |
| Lock desktop on smart card removal
|
Specifies whether to lock the desktop when the smart card owner removes the smart card from the reader. By default, this value is set to No. If the value is set to Yes, the user's workstation locks when the smart card is removed.
If the user locks the desktop using Ctrl+Alt-Delete, the authentication status remains unchanged. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Allow forced verification
|
Specifies whether Logon Manager should automatically authenticate users after they authenticate to Windows with a smart card.
Setting this to No (the default) requires a user to enter a PIN for both Windows logon and to authenticate to Logon Manager. Setting this to Yes eliminates the double PIN prompt and the user needs to enter a PIN only to authenticate to Windows, while Logon Manager automatically authenticates the user. Note: To use this feature, you MUST install Network Provider with Logon Manager. This is available during the installation on the Advanced Setup panel under Authenticators. Refer to Oracle Enterprise Single Sign-On Suite Installation Guide for more information. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.5.4.2 User interface
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Window title
|
Use this setting to customize the window title name for this authenticator. Check the box and enter the desired name.
Note: This entry is not required. |
Yes | string/ string |
|
| Window subtitle
|
Use this setting to customize the window subtitle name for this authenticator. Check the box and enter the desired name.
Note: This entry is not required. |
Yes | string/ string |
2.17.5.4.3 Recovery
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Recovery method
|
Specifies which supplier of the reset passphrase to use:
|
1: Passphrase (Default)
2: Encryption certificate 3: Smart card PIN |
Yes | dword/Ø |
| Recovery certificate object identifier
|
Specifies the object identifier of the certificate to use for the certificate-based passphrase feature. The authenticator searches the "Enhanced Key Attributes" of each certificate on the smart card for this Object Identifier.
Note: You must set the "Recovery method" option to Encryption certificate. This entry is not required. |
Yes | string/ string |
|
| PIN recovery group
|
Enter the domain security group name (in format domain\group) for the PIN Recovery Group. Members of this group have permission to authenticate to Logon Manager without a smart card, using only a PIN.
This setting is useful in a scenario where users lose their cards and are waiting for replacements. In the interim, users can be added to this PIN recovery group so that they can authenticate to Logon Manager without their cards. To use this feature, you MUST set the "Recovery method" setting above to Smart card PIN. Note: You cannot use a PIN recovery group in conjunction with secure PIN entry. |
Yes | string/ string |
2.17.5.4.4 Credential sharing
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with synchronizers
|
This setting eliminates double authentication when an authenticator shares credentials with one or more synchronizers.
Enter a comma-separated list of synchronizers to share the credentials with, for example " Note: To locate other synchronizer names, see the name listed in the registry for that synchronizer (located under |
Yes | string/ string |
2.17.5.5 Read-Only Smart Cards
Read-Only Smart Card settings are available in the Authentication section of Global Agent Settings in the Administrative Console. This section also includes steps that you must take to integrate Smart Cards with Kiosk Manager, and other technical notes about using this authenticator.
2.17.5.5.1 Administrative Console Settings
The read-only smart card settings control special-case options for read-only smart card authentication. These settings are not required.
To access the smart card settings, click Global Agent Settings > Live > Authentication > Read Only Smart Card. See the Read-Only Smart Cards section for a full discussion of these settings.
2.17.5.5.2 Read-Only Smart Card Initialization
Prior to use with Authentication Manager, read-only smart cards must be initialized and contain a valid PIN and PKI certificate. If the smart cards are also to be used with Kiosk Manager, they must have a serial number.
Authentication Manager does not provide any smart card initialization, configuration, or administration services, so this step must be performed using a third-party Card Management System (CMS) or middleware administration utility compatible with your smart card.
2.17.5.6 Integrating with Kiosk Manager
The following notes explain special considerations when integrating a Read-Only Smart Card authenticator with Kiosk Manager.
2.17.5.6.1 Support for storing and passing through the synchronization credentials with Kiosk Manager and Read-Only Smart Card integration
When using Read-Only Smart Card authenticator with Kiosk Manager, the user's synchronization credentials can optionally be stored by setting Store Synchronization Credentials to Yes and configuring the Secure Data Storage feature. If stored in this manner, the credentials are then silently passed through to Logon Manager after a user initiates a Kiosk Manager session by inserting their read-only smart card into the reader and entering the correct PIN. This feature prevents a double authentication when starting a Kiosk Manager session whereby the user authenticates with their read-only smart card and PIN and then is subsequently prompted by Logon Manager to provide their synchronization username and password.
2.17.5.6.2 Separate Authentication Prompts Appear for the Kiosk Manager Session and Logon Manager when Read-Only Smart Card is the Primary Logon Method
In a Kiosk Manager environment that uses read-only smart cards as the primary logon method, users are prompted to authenticate separately to Kiosk Manager and Logon Manager.
This occurs because a smart card authentication is only valid for the process that initiated it and cannot be shared between processes. This is a design characteristic of the smart card middleware and not Oracle software.
When the Kiosk Manager session starts, Kiosk Manager queries the smart card middleware for authentication and the user is prompted to authenticate via smart card and PIN. This authentication is valid for the Kiosk Manager process only; therefore, when the Kiosk Manager session is successfully created and Logon Manager starts, the user is authenticated again, this time to Logon Manager.
There is currently no workaround for this behavior.
2.17.5.7 Read-Only Smart Card Authenticator Settings
The Read-Only Smart Card authenticator settings control special-case options for read-only smart card authentication.
2.17.5.7.1 Options
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Store synchronization credentials
|
Specifies whether to store the user's synchronization repository credentials using Secure Data Storage.
Note: Using this setting requires that you enable and configure Secure Data Storage. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| PKCS#11 Library Path
|
Specifies the path to the smart card middleware file, which implements the PKCS#11 standard.
Note: This entry is not required unless you set "Store synchronization credentials" to Yes or are using read-only smart cards with Kiosk Manager. |
Yes | string/ string |
|
| Custom certificate check extension path
|
Specifies the path to the custom certificate check extension.
Note: This entry is not required. |
Yes | string/ string |
|
| Allow secure PIN entry
|
Use this setting to allow users to enter a PIN on a smart card reader keypad that supports secure PIN entry. | 0: Only allow non-SPE login (Default)
1: Only allow SPE login |
Yes | dword/Ø |
2.17.5.7.2 Recovery
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Recovery method
|
Enables the use of the reset passphrase. The passphrase can be supplied either by the user (entering the passphrase in a dialog) or by the newest non-default encryption certificate on the card itself. | 1: Passphrase (Default)
2: Encryption certificate |
Yes | dword/Ø |
| Recovery certificate object identifier
|
Specifies the object identifier of the certificate used for the certificate-based passphrase feature. The authenticator searches the "Enhanced Key Attributes" of each certificate on the smart card for this object identifier.
Note: You must set the "Recovery method" option to Encryption certificate. This entry is not required. |
Yes | string/ string |
2.17.5.8 Proximity Cards
Proximity Card settings are available in the Authentication section of Global Agent Settings in the Administrative Console. This section also includes steps that you must take when using Active Directory or AD LDS (ADAM), and other technical notes about configuring and using this authenticator.
2.17.5.9 Integrating with Kiosk Manager
The following notes explain special considerations when integrating a Proximity Card authenticator with Kiosk Manager.
2.17.5.9.1 Support for storing and passing through the synchronization credentials with Kiosk Manager and Proximity Card integration
Support for storing and passing through the synchronization credentials with Kiosk Manager and Proximity Card integration
When the Proximity Card authenticator's second factor is set to User Defined PIN, the user's synchronization credentials can optionally be stored by the authenticator by configuring the Secure Data Storage feature. If stored in this manner, the credentials are then silently passed through to Logon Manager after a user initiates a Kiosk Manager session by tapping a proximity card and entering the correct PIN. This feature prevents a double authentication when starting a Kiosk Manager session whereby the user authenticates with their proximity card and PIN and then is subsequently prompted by Logon Manager to provide a synchronization username and password.
2.17.5.10 Active Directory Technical Notes
An Active Directory administrator must perform the following steps on the CN=Users container on the Active Directory controller to grant read/write access to the Creator Owner user.
Without these steps, users will not have sufficient rights to change their proximity card number. As a result, when a user enters the passphrase scenario to update his card information (lost card scenario), the error, "Proximity card assigning failed" displays.
-
Open Active Directory Users and Computers console on AD controller.
-
Right-click on the Users AD object (
CN=Users). -
Click Properties in pop-up menu.
-
Click the Security tab.
-
Click the Add button.
-
Under Enter the object names to select, type
CREATOR OWNER. -
Click the Check Names button to resolve the entry.
-
Click OK.
-
Under Group or user names: highlight CREATOR OWNER.
-
Click the Advanced button.
-
The Advanced Security Settings for Users window displays. Verify that Allow inheritable permissions from the parent to propagate to this object and… checkbox is checked (set to TRUE).
-
Double-click the CREATOR OWNER user.
-
Set Apply Onto dropdown to Child Objects only.
-
Set the Read All Properties and Write All Properties checkboxes under Allow to checked (set to TRUE).
-
Apply all changes.
To use the proximity card authenticator with Active Directory, you must enable the storing of credentials under user objects:
-
Open the Administrative Console.
-
Connect to the repository.
-
From the Repository menu, select Enable Storing Credentials under User Objects (Active Directory only).
2.17.5.11 AD LDS (ADAM) Technical Notes
An AD LDS (ADAM) administrator must perform the following steps on the "OU=People" container on the AD LDS (ADAM) server to grant read/write access to the users.
-
Open an AD LDS (ADAM) Tools Command Prompt on the AD LDS (ADAM) server.
-
Execute the following command to give users Read permission to the
Peoplecontainer and its sub-objects:dsacls.exe \\<hostname>:<port>\<adam container dn> /I:T /G <user/group/role DN>:GR -
Execute the following command to give users Create Child and Write Self permissions to the
Peoplecontainer and its sub-objects:dsacls.exe \\<hostname>:<port>\<adam container dn> /I:T /G <user/group/role DN>:CCWS
2.17.5.12 OmniKey Proximity Card Reader Technical Note
When using the OmniKey family proximity card readers, it is recommended that the driver be installed through Windows updates.
2.17.5.13 Proximity Card Authenticator Settings
The proximity card authenticator settings are used for configuring proximity card authentication. Also see Proximity Cards in the Strong Authenticators section for configuration with Kiosk Manager and technical notes.
2.17.5.13.1 Options
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Card family
|
Specifies the proximity card family type. | 0: HID ISO / DUO PROX (Default)
1: iClass 2: Indala / EM |
Yes | dword/Ø |
| Reader type
|
Specifies the name of the proximity card reader to use. | OMNIKEY CardMan 5x25-CL 0-Omnikey CardMan 5125 (Default)
OMNIKEY CardMan 5x21-CL 0-Omnikey CardMan 5121 OMNIKEY CardMan 5x21-CL 0-Omnikey CardMan 5321 No entry-RFIdeas (all readers) |
Yes | string/Ø |
| Second factor authentication
|
Specifies whether to use the Active Directory password or a user-defined PIN for the second factor in authentication. | 0: AD password (Default)
1: User-defined PIN |
Yes | dword/Ø |
2.17.5.13.2 PIN Settings
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Minimum length
|
Specifies the minimum length of the user-defined PIN. | Default is 4 | Yes | dword/ int |
| Maximum length
|
Specifies the maximum length of the user-defined PIN. | Default is 8 | Yes | dword/ int |
| Maximum retries
|
Specifies the number of PIN attempts before the authentication fails. | Default is 3 | Yes | dword/ int |
| Alphanumeric constraints
|
Specifies the alphanumeric requirements of the user defined PIN. | 1: Numbers only
2: Letters only 3: Numbers and letters (Default) |
Yes | dword/Ø |
2.17.5.14 RSA SecurID
This section lists steps that you must take to integrate RSA SecurID with Kiosk Manager, and other technical notes about installing and using this authenticator.
2.17.5.14.1 Installing the RSA SecurID Method
Before installing the RSA SecurID authentication method, the RSA middleware must be installed and configured. There are two middleware options for the RSA SecurID authenticator:
-
RSA Local Authentication Client (LAC). If using RSA LAC, you must install the RSA SecurID Logon Method in the Authentication Manager installer.
-
RSA Local Authentication Toolkit (LAT). If using RSA LAT, you must install the RSA SecurID Logon Method as well as the Local Authentication Toolkit, if not previously installed, in the Authentication Manager installer. Installing RSA LAT will prompt you to reboot your machine so that it can start the service.
After RSA LAT is installed, according to the RSA documentation on LAT, you must perform the following two steps:
-
Get the server.cerfile from your RSA Authentication Manager administrator and place it in the subdirectory of the main installation directory. For example:
C:\Program Files\RSA Security\RSA Authentication Agent\Agenthost Autoreg Utilitydirectory. -
Get the
sdconf.recfilefrom your Authentication Manager administrator and place it in thesystem32directory.
Note:
These notes are stated in the RSA SecurID Local Authentication Toolkit document and also mentioned in RSA Authentication Agent 6.1 for Microsoft Windows Installation and Administration Guide.After RSA SecurID is installed, there are no specific settings that must be set in the Administrative Console.
2.17.5.15 Configuring the SoftID Helper
The SoftID Helper is an extension helper that adds SSO support for SecurID applications. This section describes how to install and configure the SoftID helper and enable RSA SecurID application templates.
2.17.5.15.1 Prerequisites
Logon Manager supports the following combinations of software and hardware tokens for SoftID applications:
-
RSA SecurID Software Tokens
-
RSA Authentication Client and RSA SecurID SID800 Hardware Authenticator
-
Both software and hardware tokens. If both are installed on the machine, Authentication Manager looks for the hardware token first, and if it cannot find the hardware token, it defaults to the software token.
One of the above combinations must be installed before installing and using the SoftID Helper.
2.17.5.15.2 Install Logon Manager
Install Logon Manager with Authentication Manager and Authentication Manager with the SoftID helper. See the Oracle Enterprise Single Sign-On Suite Installation Guide for more information.
2.17.5.15.3 Configuring RSA SecurID Application Templates
This example walks through setting up a new RSA SecurID application for an application called Login Tester.
-
Open the Administrative Console.
-
Launch the application for which you are defining a template.
-
Right-click Applications and select New Windows Application. The Add Application dialog appears.
-
Enter the application Name and check the RSA SecurID check box. Click Finish. The Form Wizard appears.
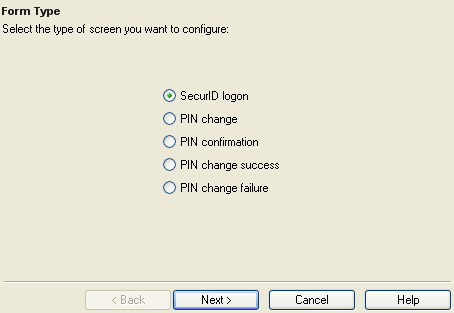
-
Select the SecurID Login button. Click Next. If the application for which you are defining a template is running, the window title will appear in the next wizard panel.
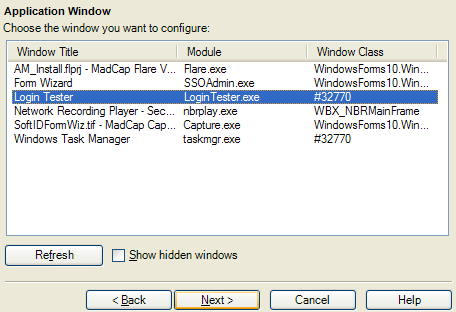
-
Select the Window Title for your application. Click Next.
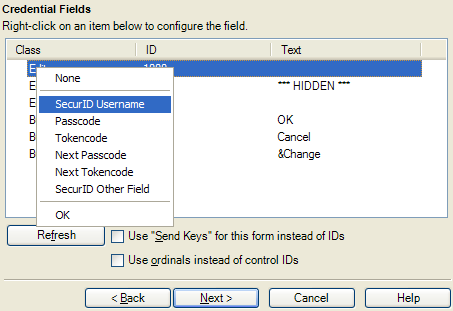
-
On this dialog, you configure the SecurID Username, Passcode, and OK button fields as well as any other applicable fields for your application. Right-click on the class and select the fields. Click the Help button for more information on configuring the credential fields. Click Next when you are done. A Summary panel appears.
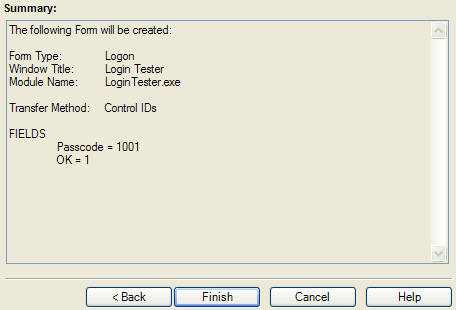
-
Review the summary. Click Finish when done.
-
The Windows Logon Form appears. Change any other applicable settings and click OK.
-
Export the template to the Agent. See Publish to Repository for more information on exporting applications.
-
When the Agent launches, the user will go through the FTU Wizard. They must select Authentication Manager as the primary logon method.
-
When the application for which you defined a template launches, the Agent will first ask the user if they want to add credentials for the application. If the user selects Yes, the Agent will prompt the user to enter their credentials into the New Logon for this application.
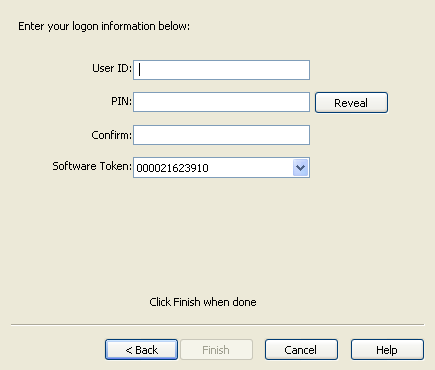
-
The user must enter the User ID, PIN and select the Software Token. The user's PIN is set up through the RSA middleware prior to use with Authentication Manager. Authentication Manager automatically populates the Software Token field as it detects the serial number of the available token.
-
Click Finish when done. The Agent will log the user onto the RSA SecurID application every time the application is started.
2.17.5.16 First-Time-Use Scenarios
In the setup phase, the user will go through the normal Logon Manager First-Time-Use (FTU) wizard until the Select Primary Logon Method dialog is displayed.
The behavior of this setup wizard is configured through the Administrative Console.
Setup Flow Example
-
The first dialog in the Setup Wizard lists the setup tasks necessary for the local installation of Logon Manager. Click Next to begin setup.
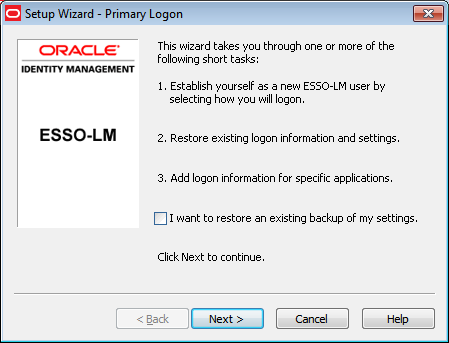
-
The dialog lists the setup tasks necessary for your local installation of Logon Manager, choosing your primary logon method and supplying the credentials for that method. Click Next.
-
The Primary Logon dialog prompts you to select a logon method. Select your desired primary logon method. Only methods that are currently installed will appear in the drop-down box. Click Next.
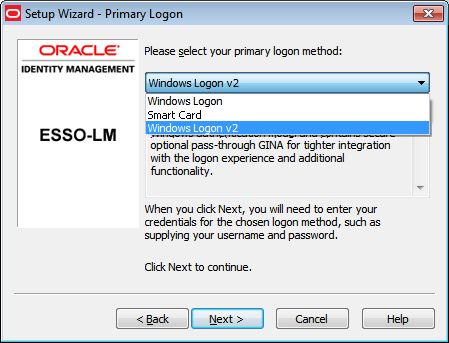
-
Enroll in your selected primary logon method. For example, if a smart card authenticator is installed, you will see the dialog below. Clicking Cancel for a required authenticator cancels the Setup Wizard.
-
Insert your smart card. You are prompted to enter your PIN. Enter it and click OK. A message indicating enrollment success appears. Click OK.
-
If the passphrase option is enabled, you might be prompted to enter a passphrase with a minimum answer length of eight characters. Enter an answer, confirm (re-enter) it, and click OK.
-
The Setup Wizard indicates that the process is complete and Logon Manager is ready for use. Click Finish to complete.
2.17.5.17 Integrating with Kiosk Manager
When using the RSA SecurID authenticator with Kiosk Manager, you have to enable and configure Secure Data Storage in the Administrative Console.
RSA SecurID authenticator uses the user's PIN rather than the repository password for the pre-population of the synchronization dialog. Secure Data Storage is used to securely save the PIN which then is associated with the repository credentials on the server. See the Secure Data Storage section to set it up.
2.17.5.17.1 Support for storing and passing through the synchronization credentials with Kiosk Manager and RSA SecurID integration:
When using the RSA SecurID authenticator with Kiosk Manager, the user's synchronization credentials can optionally be stored by the authenticator by configuring the Secure Data Storage feature. If stored in this manner, the credentials are then silently passed through to Logon Manager after a user initiates a Kiosk Manager session with an RSA SecurID token. This feature prevents a double authentication when starting a Kiosk Manager session whereby the user authenticates with a PIN and Tokencode and then is subsequently prompted by Logon Manager to provide a synchronization username and password.
2.17.5.18 Microsoft Visual C++ Technical Note
Microsoft Visual C++ 2005 Redistributable Package (x86) is required for the RSA SecurID authenticator. This can be downloaded from Microsoft's web site: http://www.microsoft.com/Downloads/details.aspx?FamilyID=32bc1bee-a3f9-4c13-9c99-220b62a191ee&displaylang=en.
2.17.5.19 PIN Mode Support Technical Note
Due to an incompatibility between RSA Local Authentication Toolkit and Visual Studio 2005, the RSA SecurID authenticator does not support New PIN Mode for SID700 and SID800. A support case has been opened with RSA (# C0842539).
2.17.5.20 Secure Data Storage
Secure data storage settings control the location for data storage. Secure data storage can be used for:
-
The RSA SecurID authenticator in a Kiosk Manager environment.
-
The Proximity Card authenticator in a Kiosk Manager environment when using "User Defined PIN" as second factor authentication.
-
The Read-Only Smart Card authenticator in a Kiosk Manager environment.
Note:
Secure Data Storage is supported for Active Directory, AD LDS (ADAM), and Oracle Internet Directory.When using Secure Data Storage, you must log on to Windows using a domain user account.
To access the secure data storage settings, click Global Agent Settings > Live > Authentication > Secure Data Storage. See the Secure Data Storage section for a full discussion of these settings.
2.17.5.21 Enabling Secure Data Storage
Regardless of your repository, start the procedure for enabling secure data storage as follows:
-
On the Secure Data Storage pane, set Enable Data Storage to Yes.
-
Create a new Organizational Unit that will serve as the data storage location.
-
Specify the fully-qualified distinguished name for this object as the value of the Data storage location setting.
-
Continue to the next steps below for the appropriate repository.
-
Grant control:
-
For Active Directory
-
Grant FULL CONTROL permission to this Organizational Unit to Everyone.
-
Apply this to This object and all child objects.
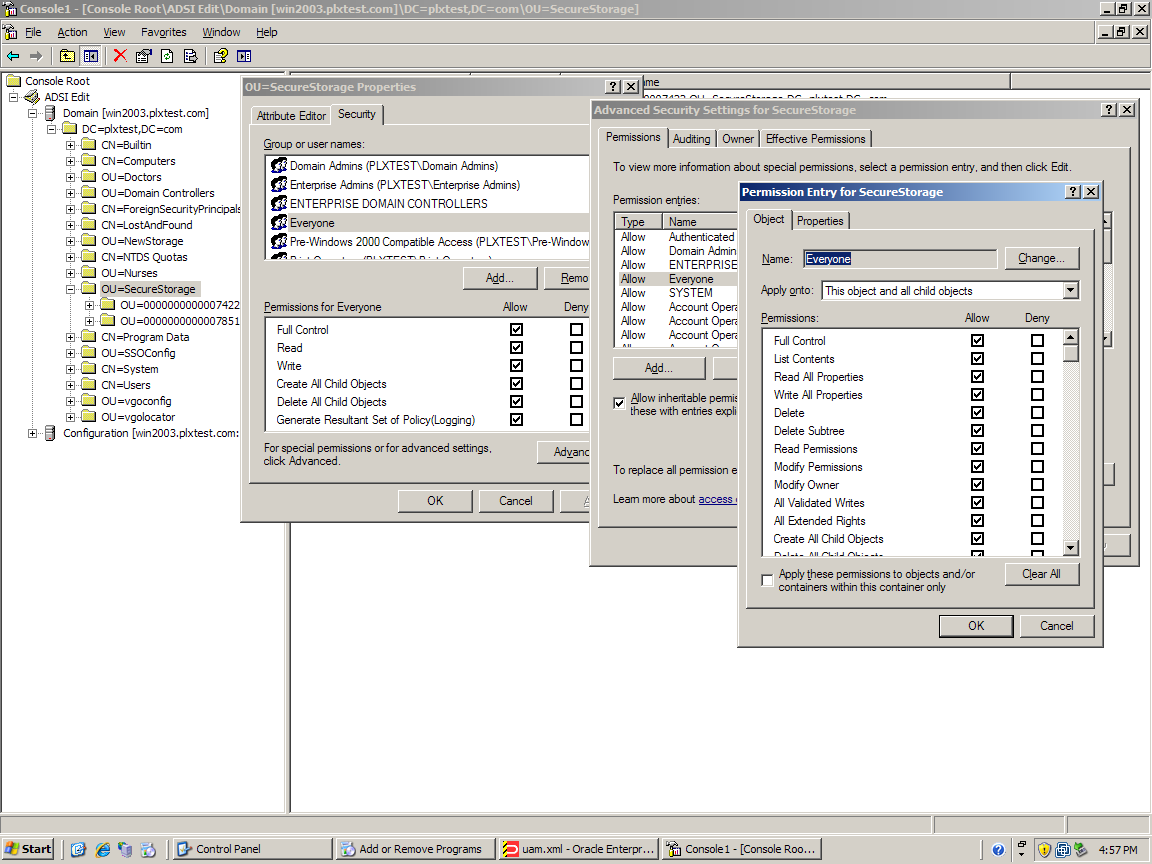
-
-
For AD LDS (ADAM)
Grant General Access (GA) permission to this Organizational Unit and its sub-objects for Everyone:
:dsacls.exe \\<hostname>:<port>\<adam container dn> /I:T /G "Everyone":GA -
For Oracle Internet Directory
-
Grant anonymous users access to the Secure Data Storage container.
-
Log on to the Directory Services Manager as an administrator.
-
Select the Data Browser tab.
-
In the tree, navigate to and select the Secure Data Storage container that you created.
-
Select the Subtree Access tab.
-
Create a new access entry under Structural Access Control and Content Access Control. Accept the default permissions and click OK.
-
Apply the changes. The default permissions grant Everyone with bind mode None the appropriate access:
-
-
2.17.5.22 Secure Data Storage Authenticator Settings
These settings are used for configuring secure data storage.
| Display Name/ Registry Path | Description Text | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Enable data storage
|
Specifies whether to store users' synchronization credentials securely within the repository. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Data storage location
|
Enter the fully-qualified path to the location in the repository where the data will be stored. | Yes | string/ string |
2.17.5.23 Kiosk Manager Integration Notes
The following notes explain special considerations when integrating Secure Data Storage with Kiosk Manager.
2.17.5.23.1 Domain Password Change
This issue occurs when using proximity devices, smart cards, and read only smart cards.
If a user's domain password is changed, the next time the user tries to start a session on a kiosk with the device within the lifetime period of the old password, depending on their sync repository, the following occurs:
-
Active Directory: This error message displays: "Unable to connect to network…".
-
AD LDS (ADAM): Kiosk Manager stops responding and requires a restart.
There are two workarounds to this issue:
-
Users can manually start a Kiosk Manager session by authenticating with a username and new password within the password lifetime period.
-
Administrators can change the lifetime period of an old password to decrease the probability that this issue will occur. Refer to Microsoft Help and Support for more details:
http://support.microsoft.com/kb/906305.
2.17.5.23.2 Hardware Reassignment
If a hardware device, such as a smart card, is ever reassigned to another user, it is possible that Kiosk Manager will log on as the original user. This occurs because Kiosk Manager keeps a device-to-username mapping.
There is no workaround for this issue. It is strongly recommended that these devices not be reassigned to avoid this issue.
2.17.6 Provisioning Gateway Server Locations
Use this tab to specify the location(s) of Provisioning Gateway Servers.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| PG Server locations
|
Click the ellipsis ("…") button and enter the URL(s) for the Provisioning Gateway Server(s). For example:
There is no default for this setting. |
Yes | string/Ø | |
| Request timeout
|
Specifies how long (in milliseconds) to wait for a response from the Provisioning Gateway Server
This setting is not required. |
60000 (Default) | Yes | dword/int |
2.17.6.1 Delegated Credentials Settings
Use these settings to specify the server(s) and encryption for delegated credentials.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| PM Locations
|
Click the ellipsis ("…") button and enter the path, or list of paths, to the provisioning service. Enter one path per line. For example:
|
Yes | string | |
| Encryption algorithm
|
Select the default encryption algorithm from the dropdown menu.
Note: All algorithms except AES 256 have been deprecated as of version 11.1.2 and are listed for upgrade scenarios only. Do not select other algorithms for new configurations. This setting is not required. |
AES 256 (Default)
Triple DES (deprecated) |
Yes | dword |
2.17.6.2 Privileged Accounts Settings
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Allow password reveal
|
Specifies whether the user is permitted to reveal the masked fields of checked out accounts. | 0-Do not allow reveal (default)
1-Use application template setting. |
Yes | dword/Ø |
| Validate account status before each use
|
Specifies when the account status check should occur.
When set to "Before every use," a check is made when the user attempts to use a checked-out account (logon or reveal password). The OPAM Client will check to make sure that the Provisioning Gateway Server is reachable and that the account has not been checked in. |
0-During synchronization only (default)
1-Before every use |
Yes | dword/Ø |
2.17.7 Synchronization Settings
The Synchronization settings are the general options for credential synchronization for all synchronizer extensions. Use these settings to control the following functions and features:
-
Performance
-
User Mobility
-
Security and Management
2.17.7.1 Manage Synchronizers Dialog
The Synchronizers dialog displays the current set of available synchronizers and the order by which the Agent searches them.
To change the search order:
-
Select a synchronizer and click the up or down buttons to reposition it.
To add a synchronizer:
-
Click Add. The Add Synchronizer dialog appears.
To display this dialog:
-
Select a set of Global Agent Settings.
-
Do one of the following:
-
Right-click Synchronization and choose Manage Synchronizers from the shortcut menu.
or
-
Choose Sync Extension from the Insert menu.
2.17.7.2 Add Synchronizer Dialog
Use the Add Synchronizer dialog to include a synchronizer in the Agent's search list.
-
Enter a Name for the new synchronizer.
-
Select a Sync Type from the list.
-
Click OK to add the synchronizer and return to the Manage Synchronizers dialog.
To display this dialog:
-
Select a set of Global Agent Settings.
-
Do one of the following:
-
Right-click Synchronization and select Manage Synchronizers from the shortcut menu.
or
-
Choose Synchronizer from the Insert menu.
-
Click Add. The Add Synchronizer dialog displays.
2.17.7.3 Using the Edit List Dialog for Synchronizer Settings
The Edit List dialog displays when you click the ellipsis ("…") button for various synchronizer settings, as listed in the following table. Use this dialog to enter items described in the window title bar (for example, Servers).
-
Type one item for each line. Press Enter at the end of each line. Do not use any other delimiter characters.
-
Click OK when finished.
Use this dialog with the following Global Agent Settings:
| Synchronizer | Setting |
|---|---|
| LDAP Synchronizer | UserPaths |
| LDAP Synchronizer Servers | Servers |
| LDAP Authenticator Servers | Servers |
| Active Directory Synchronizer | UserPaths |
| Active Directory Synchronizer Servers | Servers |
| Database Synchronizer Servers | Servers |
| Oracle Access Manager Endpoints Entry | URLs |
| Shell Tasks | Deletion Tasks
|
2.17.7.4 General Synchronization Options
Use this screen to configure non-synchronizer-specific settings.
2.17.7.4.1 Options
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Synchronizer order
|
Specifies the order of synchronization extensions to use. If no value is specified, all extensions are used (in an unpredictable order).
For reads, the first operational synchronizer is authoritative, and no other synchronizer is queried. For writes, all synchronizers are updated, in the order specified in this setting. Examples: LDAPExt, ADExt, FileSync Remote, AD, FileSync Local, SmartCard, MySmartCard, ADExt, ADExtRemote |
Yes | string/ synchronizer |
|
| Use configuration objects
|
When this setting is disabled, all templates and policies are consolidated into one of two objects: CN=vgoentlist and CN=vgoadminoverride.
When this setting is enabled, all template and policies are independent objects for directory-based synchronizers. In this mode, additional features are available, including role/group security and directory hierarchy support. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Allow disconnected operation
|
Specifies whether the offline cache is usable or the First-Time-Use Wizard executes when the Agent is unable to connect to any synchronizer repository. If this setting is disabled, and the repository is not available, the Agent shuts down. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Delete local cache
|
Specifies whether to delete the user's data files and registry keys upon shutdown of the Agent. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
| Deleted credential cleanup
|
Length of time (in days) for which a credential's "deleted" flag is retained after a credential is deleted. Used to ensure that the credential is deleted from all of a user's local caches on multiple systems. | (Default: 30) | Yes | dword/ int |
| Location of entlist.ini file
|
Enter the fully-qualified path and filename to the entlist.ini file. Only applicable in standalone (no synchronizer) mode.
This setting should be used only to deploy Administrative Console templates locally to the workstation when synchronization is not installed. The setting should NOT be used when synchronization is installed and application templates are deployed via a repository such as Active Directory. See Creating and Using Templates for more information. |
Yes | string/ filename |
2.17.7.4.2 Behavior
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Wait for synchronization at startup
|
Specifies whether to wait for synchronization at startup, which ensures that the user's data is current, and new templates and policies are put into effect before Logon Manager logs on to applications.
Note: With this setting enabled, Logon Manager does not respond until the synchronization is complete. Synchronization times vary based on your synchronization infrastructure and the number of templates and policies in the repository. |
0: No
1: Yes (Default) |
Yes | dword/Ø |
| Interval for automatic resynchronization
|
Interval (in minutes) between automatic resynchronizations. This synchronization interval is not reset if a manual, user-generated sync event (such as an Logon Manager refresh) takes place.
A value of zero (0) disables this setting, which means that synchronization occurs only during normal sync events such as Logon Manager startup or user credential update. Generally set when Provisioning Gateway is in use, to ensure that updates are delivered in a timely manner. |
(Default: 0) | Yes | dword/ int |
| Optimize synchronization
|
With this setting enabled, the synchronization function uses a checksum object called SyncState to determine changed credentials, rather than retrieving all credentials. Changed credentials are then independently synchronized without synchronizing all credentials. Note that templates and policies are always synchronized in full during each sync event. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Use aggressive synchronization
|
With this setting enabled, each time Logon Manager detects a logon event, a synchronization occurs before the target application credential is decrypted and passed to the application.
This feature ensures that the most current credentials or settings are used at all times. The feature is normally only used in special cases where a user uses multiple systems to simultaneously access the same application (such as through a Citrix farm). Note: This feature can have a significant performance impact on both client and server computers. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Resynchronize when network or connection status changes
|
Enables or disables monitoring for changes in the network connection status. Enabling this setting causes the Agent to perform resynchronization when a status change occurs (for example, reconnecting to the network). | 0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.7.5 Active Directory Synchronization Settings
Use these settings to configure a Microsoft Active Directory (AD) synchronization.
Note:
If users will be synchronizing with an Active Directory or AD LDS (ADAM) repository from outside of the corporate network, you must allow RPC protocol-based connections through the corporate firewall; otherwise, users will be unable to synchronize with the repository.2.17.7.5.1 Synchronizer location
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| AD Sync DLL location
|
Enter the path\filename of the Active Directory synchronizer extension. | Default: %INSTALLDIR% Plugin\SyncMgr\ ADEXT\adsync.dll |
No | string/ filename |
2.17.7.5.2 Data storage configuration
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Base location(s) for configuration objects
|
Specifies where to begin the search for Configuration Objects (templates and policies). This is a fully-qualified, distinguished path, such as:
The search starts from the specified location(s) and searches all subordinate |
No | string/ Ø |
|
| Location for storing user credentials
|
Credentials can be stored either as objects subordinate to the Active Directory user object, or as specified by an Oracle locator object. | 0: As specified by locator object (Default)
1: Under respective directory user objects |
Yes | dword/Ø |
| Prepend Domain when naming objects
|
Enables prepending the user's Domain to the username in naming the user's container.
Example: For the Domain "company" and user "jamesk" the container is named "jamesk" with this flag disabled and "company.jamesk" with this flag enabled. Note: If you enable this setting, do not select to enable storing credentials under User Object (in the Directory menu). If you enable credential storage in User Objects, you must disable this option (the default setting). If you enable both options, synchronization does not occur. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| Base location(s) for UAM storage index
|
Fully qualified DN of the Universal Authentication Manager index container. | No | string/Ø | |
| Use secure location for storing user settings
|
Set to Yes if you want the synchronizer to use a secure location for storing user registry settings in Active Directory.
Set to No only for the duration of the Logon Manager client's upgrade period for backward compatibility with Logon Manager versions prior to 11.1.2. Note: You should not select Yes for this setting until you have upgraded all Logon Manager clients to version 11.1.2. You must select Yes for this setting under the following conditions:
|
0: No (Default)
1: Yes (recommended) |
Yes | dword/Ø |
2.17.7.5.3 Connection information
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Credentials to use
|
Specifies which credentials to use when authenticating to the Active Directory Server. | 0: Use local computer credentials only
1: Use Active Directory server account only (recommended that UserPathN be set) 2: Try local computer credentials; if it fails, use Active Directory server account (Default) 3: Use card's certificate. Use this setting to allow users to authenticate to the repository using a smart card's certificate and their PIN instead of a username and password. 4: Try card's certificate; if logon is canceled, use Active Directory server account. |
Yes | dword/Ø |
| Prompt when disconnected
|
Allows the user to work offline without prompting/notification if a synchronization event fails. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Servers
|
Servers to try, in the format computer[:port] (one server per line), where computer is the server name, and port is assumed to be the default (636 for SSL, 389 for no SSL) if not specified.
Example:
Note: This setting is not normally used when storing Oracle data in Active Directory. Active Directory requires use of computer names (not IP addresses). |
No | string/Ø | |
| User Paths
|
Enter the fully-qualified path to where the user account is located. There can be unlimited paths to search. The extension searches these in order, looking for the user account. If not found, the extension will search the directory tree.
Note: This entry is not required for this extension. |
Yes | string/Ø | |
| Use SSL
|
Specifies to connect via SSL. | 0: No (insecure) (default to port #389)
1: Yes (default to port #636) (Default) |
Yes | dword/Ø |
| Logon attempts
|
Specifies the number of times to present the Synchronization dialog to the user. For example, if you set this value to 3, the Synchronization dialog displays a maximum of three times if the user submits incorrect credentials. | Default: 3 | Yes | dword/ int |
2.17.7.5.4 User interface
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Descriptive name
|
Enter a logon dialog title to differentiate between multiple synchronizer extensions having the same name.
Note: This entry is not required. |
Yes | string/ string |
|
| Password change window title
|
Use this setting to customize the Active Directory Change Password window title name for this synchronizer.
Note: This entry is not required. |
Yes | string/ string |
|
| Password change window subtitle
|
Use this setting to customize the Active Directory Change Password window subtitle name for this synchronizer.
Note: This entry is not required. |
Yes | string/ string |
2.17.7.5.5 Credential sharing
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with authenticators
|
This setting eliminates double authentication by linking authenticator and synchronizer credentials. If authenticators and synchronizers use the same credentials, the duplicate credentials are used without requiring the user to reenter them.
Enter a comma-separated list of authenticators with which to share the credentials, for example WinAuth, MSAuth. Note: To locate other authenticator names, see the name listed in the registry for that authenticator (located under |
Yes | string/ string |
2.17.7.6 AD LDS (ADAM) Synchronization Settings
Use these settings to configure an AD LDS (ADAM) synchronization.
Note:
If users will be synchronizing with an Active Directory or AD LDS (ADAM) repository from outside of the corporate network, you must allow RPC protocol-based connections through the corporate firewall; otherwise, users will be unable to synchronize with the repository.2.17.7.6.1 Synchronization location
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| ADAM Sync DLL location
|
Enter the path\filename of the AD LDS (ADAM) synchronizer extension. | Default: %INSTALLDIR%Plugin\ SyncMgr\ ADAMext\ ADAMsyncExt.dll |
No | string/ filename |
2.17.7.6.2 Data storage configuration
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Base location(s) for configuration objects
|
Specifies where to begin the search for Configuration Objects (templates and policies). This is a fully-qualified, distinguished path, such as:
The search starts from the specified location(s) and searches all subordinate |
No | string/Ø | |
| Prepend Domain when naming objects
|
Enables prepending of the user's Domain to the username in naming the user's container.
Example: For the Domain " |
0: No (Default)
1: Yes |
Yes | dword/Ø |
| User Domain name to use
|
Specifies the domain name to use in the container name (for example, DomainName.UserName) when you enable the Prepend Domain setting. The user can specify another domain the in the logon dialog.
If User Domain is " |
Yes | string/ string |
2.17.7.6.3 Connection information
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Credentials to use
|
Specifies which credentials to use when authenticating to the AD LDS (ADAM) server. | 0: Local computer credentials
1: ADAM server account 2: Try local computer credentials before using ADAM server account (Default) 3: Use card's certificate. Use this setting to allow users to authenticate to the repository using a smart card's certificate and their PIN instead of a username and password. 4: Try card's certificate; if logon is canceled, use ADAM server account. |
Yes | dword/Ø |
| Prompt when disconnected
|
Allows the user to work offline without prompting/notification if a synchronization event fails. | 0: Yes
1: No (Default) |
Yes | dword/Ø |
| Servers
|
Specifies the servers to try, in the format computer[:port] (one server per line), where computer is the server name, and port is assumed to be the default (636 for SSL, 389 for no SSL) if not specified.
Examples:
|
No | string/ string |
|
| Use SSL
|
Specifies to connect via SSL. | 0: No (insecure) (default to port #389)
1: Yes (default to port #636) (Default) |
Yes | dword/Ø |
2.17.7.6.4 User interface
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Descriptive name
|
Specify a logon dialog title to differentiate among multiple synchronizer extensions having the same name.
Note: This entry is not required. |
Yes | string/ string |
|
| Password change window title
|
Use this setting to customize the AD LDS (ADAM) Change Password window title name for this synchronizer.
Note: This entry is not required. |
Yes | string/ string |
|
| Password change window subtitle
|
Use this setting to customize the AD LDS (ADAM) Change Password window subtitle name for this synchronizer.
Note: This entry is not required. |
Yes | string/ string |
2.17.7.6.5 Credential sharing
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with authenticators
|
This setting eliminates double authentication by linking authenticator and synchronizer credentials. If authenticators and synchronizers use the same credentials, the duplicate credentials are used without requiring the user to reenter them.
Enter a comma-separated list of authenticators with which to share the credentials, for example WinAuth, MSAuth. Note: To locate other authenticator names, see the name listed in the registry for that authenticator (located under |
Yes | string/ string |
2.17.7.7 Database Synchronization Settings
Use these settings to configure database synchronization.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| DB Sync DLL location
|
Enter the path\filename of the Database synchronizer extension. | Default: %INSTALLDIR% Plugin\ SyncMgr\ DBEXT\ DBExt.dll |
No | string/ string |
| Servers
|
Specifies the database servers and the order to attempt connection for synchronization. Select the checkbox and click the ellipsis "…" button to open the "Edit List" dialog. Enter the full connection address (computerName.dbServerName) for one database server on each line; end each line by pressing Enter. Do not use any other delimiter characters.
You must specify at least one server for the extension to work. For Oracle To connect to an Oracle database, use the following connection string:
where the To connect to the Oracle database, the Oracle client must be installed on the same machine as the Administrative Console. For SQL Server To connect to a SQL Server that is hosting multiple instances, use the following connection string (with no manual line break):
|
No | string/ string |
|
| Append Domain when naming objects
|
Enables appending the user's Domain to the username in naming the user's container.
Example: For the Domain " |
0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.7.8 File System Synchronization Settings
Use these settings to configure a File System synchronization.
2.17.7.8.1 Synchronizer location
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| File Sync DLL location
|
Enter the path\filename of the File System synchronizer extension. |
Default: %INSTALLDIR% Plugin\ SyncMgr\ FileSyncExt\ filesync.dll |
No | string/ filename |
2.17.7.8.2 Data storage configuration
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Prepend Domain when naming user folders
|
Enables prepending the user's Domain to the username in naming the user's container.
Example: For the Domain " |
0: No
1: Yes (Default) |
Yes | dword/Ø |
2.17.7.8.3 Connection information
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Prompt when disconnected
|
Allows the user to work offline without prompting/notification if a synchronization event fails. | 0: Yes
1: No (Default) |
Yes | dword/Ø |
| Server
|
Enter the list of UNC paths to try for synchronization. You must specify Server1 for this extension to work.
Examples:
The File System extension requires use of proper UNC paths. Only one path is supported. Failover is not supported. |
Yes | string/ string |
|
| Logon attempts
|
Specifies the number of times to present the Synchronization dialog to the user. For example, if you set this value to 3, the Synchronization dialog displays a maximum of three times if the user submits incorrect credentials. | Minimum value of 1
Default: 3 |
Yes | dword/ int |
2.17.7.8.4 User interface
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Descriptive name
|
Specifies a logon dialog title to differentiate among multiple synchronizer extensions having the same name.
Note: This entry is not required. |
Yes | string/ string |
2.17.7.9 LDAP Synchronization Settings
The LDAP/IBM Synchronization settings must be set for all LDAP synchronizer extensions.
You can bind to a directory before or after searching for a specific user account. If you choose to search for a user account before binding, Logon Manager begins searching at the user path you specify and continues down the tree until it locates the user account and binds to that directory, or it exhausts all paths. If Logon Manager does not find the user account you specify, the user receives a message that the system has been configured incorrectly and to contact the administrator.
Typically, Logon Manager uses anonymous binding for LDAP directories, but it also allows you to create a browse-only account to search for a user in scenarios where anonymous binding is disabled. In such cases, the account name is not the user's name and therefore is not readily identifiable (for instance, an employee ID or social security number). The browse-only account facilitates user searches when the alternate user ID option is enabled, identifying the user who belongs to the alternate user ID. Use the Alternate User ID location, BIND User Name, and BIND User Password settings to configure the browse-only account.
2.17.7.9.1 Synchronizer location
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| LDAP Sync DLL location
|
Enter the path\filename of the LDAP Directory Server synchronizer extension. |
Default: %INSTALLDIR%Plugin\ SyncMgr\ LDAP\ ldapsync.dll |
No | string/ filename |
2.17.7.9.2 Data storage location
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Base location(s) for configuration objects
|
Specifies where to begin the search for Configuration Objects (templates and policies). This is a fully-qualified, distinguished path, such as:
The search starts from the specified location(s) and searches all subordinate |
No | string/Ø |
2.17.7.9.3 Connection information
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Prompt when disconnected
|
Allows the user to work offline without prompting/notification if a synchronization event fails. | 0: Yes
1: No (Default) |
Yes | dword/Ø |
| Directory type
|
The specific type of directory server. If the directory server is not listed, select Unspecified LDAP Directory (the default) for backwards compatibility in upgrade scenarios; otherwise select Generic LDAP Directory. | 0: Unspecified LDAP Directory (Default)
3: Novell eDirectory 5: Generic LDAP Directory 8: Oracle Directory Server Enterprise Edition 9: IBM Tivoli Directory Server 10: Oracle Internet Directory 11: Siemens DirX Directory Server |
Yes | dword/Ø |
| Servers
|
Servers to try, in the format computer[:port] (one server per line), where computer is the server name, and port is assumed to be the default (636 for SSL, 389 for no SSL) if not specified.
Example:
|
No | string/Ø | |
| User paths
|
Enter the fully-qualified (distinguished) path to the location of the user account when LDAP Directory Search is not enabled. There can be unlimited paths to search. The extension searches these in order, looking for the user account. When using LDAP Directory Search, if the user account is not found in the given userpath, the extension searches down the directory tree from that path.
Example:
Note: You must specify at least one value for UserPath for this extension to work. |
Yes | string/Ø | |
| Use SSL
|
Specifies to connect via SSL. | 0: No (insecure) (default to port #389)
1: Yes (default to port #636) (Default) |
Yes | dword/Ø |
2.17.7.9.4 Administrative security
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Administrative group DN
|
Enter the Distinguished Name for the administrative group. This value is placed in the ACI.
Example:
|
Yes | string/ string |
|
| Security version
|
Updates the ACI with a new :AdminGroup value when this value is higher than :SecurityUpgrade.
Use this setting in conjunction with the Administrative Group DN setting to update of the security rights on the people container used by Logon Manager to store LDAP user credentials for deployed environments. To do this:
The next time Logon Manager performs a synchronization, it updates the security to the new Administrative Group DN and sets its current internal Security Version to the one configured. This forces the security update to run only once. Note: This setting is not meant to be used as a typical upgrade path for the security change. It is recommended that you use in-place mechanisms that exist for the various servers. |
Yes | dword/ string |
2.17.7.9.5 User interface
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Descriptive name
|
Specifies a logon dialog title to differentiate among multiple synchronizer extensions having the same name.
Note: This entry is not required. |
Yes | string/ string |
|
| Show user path
|
Use this setting to show/hide the User Path combo box control in the LDAP synchronizer authentication dialog. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Logon attempts
|
Specifies the number of times to present the Synchronization dialog to the user. For example, if you set this value to 3, the Synchronization dialog displays a maximum of three times if the user submits incorrect credentials. | Minimum value of 1
Default: 3 |
Yes | dword/int |
2.17.7.9.6 Credential sharing
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Share credentials with authenticators
|
This setting eliminates double authentication by linking authenticator and synchronizer credentials. If authenticators and synchronizers use the same credentials, the duplicate credentials are used without requiring the user to reenter them.
Enter a comma-separated list of authenticators with which to share the credentials, for example WinAuth, MSAuth. Note: To locate other authenticator names, see the name listed in the registry for that authenticator (located under |
Yes | string/Ø |
2.17.7.10 LDAP Special Purpose Synchronization Settings
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Naming attribute string
|
String to prepend to User Paths. This is required when the domain name for a user is in the form:
instead of the form:
(where Note: Typically, you must set this value to cn for Novell eDirectory. If you use UserPrepend, you must use User PathN and not use UserLocation. |
Yes | string/ string |
|
| BIND timeout
|
Enter the length of the timeout (in milliseconds) of the LDAP BIND call. | Default depends on the operating system | Yes | dword/ int |
| BIND user DN
|
Specifies LDAP "browse only" account user DN. This must be in the format:
(for example, You must enable anonymous binding on the directory for LDAP Directory Search functionality. If you do not enable anonymous binding, you must use this account to perform the directory search. The search is performed whether using "User Paths" or the "Alternate User ID location." |
Yes | string/ string |
|
| BIND user password
|
Specifies LDAP "browse only" account user password.
You must enable anonymous binding on the directory for LDAP Directory Search functionality. If you do not enable anonymous binding, you must use this account to perform the directory search. The search is performed whether using "User Paths" or the "Alternate User ID location." |
Yes | string/ Masked String |
|
| Alternate user ID location
|
Specifies where to locate a user object when the user validates against an attribute other than the username.
Example: If users authenticate with an employee ID # for logon (validation against the empid attribute) and the user object is in:
set UserLocation to
instead of to
Note: For Novell eDirectory, UserLocation should be: If using |
Yes | string/ string |
|
| Enable directory search for users
|
Enables or disables directory search for the user account. When the user account is not found in the given path, the extension will search for it from that location down the directory tree. The search is performed whether using "User Paths" or the "Alternate User ID location."
If you enable this setting and have moved a user to a different OU in the LDAP directory since the last synchronization, the user will receive a prompt for credentials at the next logon. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.7.11 Roaming Profile Synchronization Extension Settings
Note:
Roaming Profile is deprecated as of version 11.1.2 and is listed for upgrade scenarios only. Do not use this synchronizer for new configurations.The Administrative Console uses the Roaming Profile synchronizer to support file system synchronization with roaming profiles. You can use the Roaming Profile synchronizer in deployments that meet the following conditions:
-
Users are set up to use roaming profiles on the server.
-
The Delete Local Cache setting has not been enabled for synchronization.
-
You are using v1 Authentication.
If the above conditions exist, set up the roaming profile environment as follows:
-
Set Logon Manager to operate in a multi-sync environment, where one of the sync extensions installed is the roaming sync extension. A multi-sync environment is one in which at least two sync extensions are installed. For example, if you are using AD sync extension, you must install AD sync extension and Roaming profile extension.
-
The Roaming Profile Synchronizer extension must be first in the synchronizer configuration order. To set this order, expand Global Agent Settings > Live and click on Synchronization. In the Synchronizer order field, click the ellipsis "…" button. On the Synchronizers panel, make sure that the Roam setting is in the top position, and the other synchronizer type (for example, Active Directory) being used is second.
-
You do not need to change any other synchronizer settings when using Roaming Profiles.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Roaming Sync DLL location
|
Enter the path\filename of the roaming synchronizer extension. | Default: %INSTALLDIR% Plugin\ SyncMgr\ RoamExt\ RoamSyncExt.dll |
No | string/ filename |
2.17.8 Security Settings
The Security settings control the frequency with which end-users must re-enter their primary logon passwords, their ability to view their application logon passwords, and the preferred encryption provider and strength.
2.17.8.1 Security Options
| Display Name/ Registry Path |
Description | Options/Default | Overridable | RegType/DataType |
|---|---|---|---|---|
| Store user data on disk in encrypted file
|
Specifies to store a copy of user data (for example, credentials) locally in an encrypted database file in each user's ApplicationData folder. |
0: No
1: Yes (Default) |
Yes | dword/Ø |
| Default encryption algorithm
|
Select the default encryption algorithm from the dropdown menu.
Note: Non-MS CAPI algorithms have been deprecated and are listed for upgrade scenarios only. Do not select these algorithms. |
0: Cobra 128-bit (deprecated)
512: Cobra 128-bit (also) (deprecated) 513: Blowfish 448-bit (deprecated) 1028: Triple-DES 168-bit (deprecated) 1285: AES 256-bit (deprecated) 25700: Triple-DES (MS CAPI) (All OSs) (deprecated) 25723: Triple-DES (MS CAPI) (XP/2003 only) (deprecated) 25956: RC-4 (MS CAPI) (All OSs) (deprecated) 25979: RC-4 (MS CAPI) (XP/2003 only) (deprecated) 26491: AES (MS CAPI) (All OSs) (Default) |
Yes | dword/Ø |
| Reauthentication timer
|
Time (in milliseconds) between reauthentication requests. If set to 4,294,967,295 (0xFFFFFFFF), the time never expires and the user will never need to reauthenticate, except in forced authentication scenarios. | Default for client-side installations: 900000
Default for Terminal Services environments: 4,294,967,295 (disabled) |
Yes | dword/int |
| Require reauthentication before updating account credentials
|
Specifies whether the user must enter Logon Manager credentials before changing application credentials, even though the authentication timer has not expired. | 0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.8.2 Masked fields
| Display Name/ Registry Path | Description | Options/Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Obfuscate length
|
Specifies whether to display encrypted fields with a string of blank characters different from the length of the obfuscated data. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Allow revealing
|
Specifies whether the user is permitted to reveal masked fields. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
| Require reauthentication to reveal
|
Specifies whether the user must enter Logon Manager credentials in order to reveal masked fields, assuming that you have set "Allowed revealing" to Yes. | 0: No
1: Yes (Default) |
Yes | dword/Ø |
2.17.9 Custom Actions Settings
The Custom Actions settings control the tasks (lists of commands) that should execute when specific Agent actions occur.
For each event, select the checkbox and click the ellipsis ("…") button to open the list dialog for that event. Enter one command on each line; end each line by pressing Enter. Do not use any other delimiter characters. They run one at a time, sequentially.
Logon Manager will not respond until all of the tasks complete.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| After Agent starts
|
Command(s) that will run every time the background task starts (the Tray Icon appears). | Yes | string/Ø | |
| Before each instance of the Agent executable starts
|
Command(s) that will be run before each agent executable is started.
Note: The intention of this option is to enable license checking before any part of the Agent is executed. The Agent will stop running if any of these tasks fails to set the registry value located at:
Each task should reset this to 0 when starting. Warning: Anything run in this way will impact performance of the Agent, as these tasks will run every time a new Agent process starts. |
Yes | string/Ø | |
| When logons are deleted
|
Command(s) that will run every time a user deletes an application configuration. | Yes | string/Ø | |
| When logons change (add, delete, copy, modify)
|
Command(s) that will run every time a user modifies credentials and configurations. | Yes | string/Ø |
2.17.10 Windows Event Log-Based Reporting
Large deployments of Logon Manager will often see the need for frequent auditing of user actions and information describing each action (such as date, time, and the name of the user). Logon Manager records this information through the Windows Event Log mechanism, enabling you to easily leverage your existing infrastructure to collect source data for system-wide audits.
Using the event log data recorded by Logon Manager, you can:
-
Track the actions of Logon Manager users, such as logons and password changes. This includes associated information such as the action type, AD account name, date, time, and the credentials used to perform the action, if applicable.
-
Track the credentials that were used to log on to an application over time by each user. This can help detect attempts of unauthorized access by users who share their credentials without permission.
-
Track the actions of Logon Manager administrators. For example, if someone pushes a misconfigured template to the repository, you can find out when the update was performed on that particular Logon Manager object and by whom.
-
Track application usage. You can use the event log data to analyze application usage by user, time, and date. Such information can aid you in gauging system loads, for example when setting up load balancing in large deployments.
2.17.10.1 Technical Prerequisites
The required event data is recorded on the machine hosting your Active Directory repository. In order to generate reports based on this data, you must:
-
Enable the required level of log verbosity for your Active Directory instance by setting the following registry value:
-
Path:
HKLM\SYSTEM\CurrentControlSet\Services\<AD_instance>\Diagnostics -
Key:
8Directory Access (DWORD) -
Value:
0x00000005(hex) -
Query the
Win32_NTLogEventhandler and filter your queries by event type SSOEventMgr. This is the event type used by Logon Manager when recording data in the Windows Event Log.
2.17.11 Audit Logging Settings
The Audit Logging settings let you specify the retry interval and size of the logging cache.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Cache limit
|
Maximum number of event log entries to be cached before old events are discarded. | Default: 200 | Yes | dword/ int |
| Retry interval
Extensions\EventManager:Retry |
Interval (in minutes) between retries for all Event Logging extensions.
Note: If you are using Reporting, you should set this value to zero (0). |
Default: 30 | Yes | dword/ int |
2.17.11.1 Configuring the Windows Event Logging Server
Note:
Domain users do not have permissions to write to a Microsoft Windows 2008 or 2012 Server application log by default. You must use the command-line toolwevtutil, which is a Microsoft utility for eventvwr. Contact Microsoft support if you need assistance using this command-line tool.To configure a server to receive Event Log messages:
-
Install the Agent on that server.
or
-
Copy
SSOeventmessage.dllfrom an Agent installation to the server, preferably in theSystem32directory. -
Create the following registry keys under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\ Services\Eventlog\Application\v-GO SSO:
| Field | Function |
|---|---|
| Name | EventMessageFile |
| Type | STRING |
| Value | Full path to the file SSOeventmessage.dll, including filename (recommended: %WinDir%\System32\SSOeventmessage.dll) |
| Field | Function |
|---|---|
| Name | TypesSupported |
| Type | DWORD |
| Value | 7 |
| Field | Function |
|---|---|
| Name | CategoryMessageFile |
| Type | STRING |
| Value | Full path to the file SSOeventmessage.dll, including filename (recommended: %WinDir%\System32\SSOeventmessage.dll) |
| Field | Function |
|---|---|
| Name | CategoryCount |
| Type | DWORD |
| Value | 4 |
2.17.11.2 Configuring the Reporting Server
The Reporting tool allows you to generate reports on user activities. Refer to Chapter 6, "Using the Administrative Console to Configure the Reporting Client" for complete information on using this tool.
2.17.11.2.1 Database
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Connection string
|
Database connection string in the OLE DB format:
|
No | string/ string |
|
| Stored procedure
|
The name of the stored procedure used to populate the database with events. When encoded events are sent to the database, the stored procedure is called to decode the XML file and store the events in the database. | Default: dbo.sp_WriteEvents |
No | string/ string |
2.17.11.2.2 Options
In order for Reporting to function properly, it is important that the following parameter values be set to zero (0):
-
HKEY_LOCAL_MACHINE\SOFTWARE\Passlogix\Extensions\EventManager\ CacheLimit:DWORD = 0and
-
HKEY_LOCAL_MACHINE\SOFTWARE\Passlogix\Extensions\EventManager\Retry:DWORD = 0
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Batch size
|
Defines the group size of events to be sent to the database Stored Procedure in one batch.
For example, if you have 1000 events in the Reporting Service cache and the Batch Size = 100, you will have 10 database Stored Procedure calls. |
Default: 100 | Yes | dword/ int |
| Cache limit
|
Maximum number of reporting events to cache before discarding old events. When this number is reached, the oldest events are discarded.
For example, if the batch size is 100 and an end-user's system cannot connect to the reporting service, it will keep logging events. When it reaches 1000, the oldest events will be discarded. (Default is |
Default: 4294967295, or 0xFFFFFFFF |
Yes | dword/ int |
| Retry interval
|
Specifies the timeout (in minutes) between sequential operations of the Reporting Service Cache offloading events to the database. An interval is necessary to reduce database connection load.
Note: You must restart the ESSO Reporting Service for your changes to take effect. |
Default: 30 | Yes | dword/ int |
2.17.11.3 Configuring Windows Event Viewer
The Windows Event Viewer settings enable event logging on a remote server. Specify which events should be logged. You can also change the default path to the Windows Event logging extension and Windows event message components, and you can modify the retry interval of the logging cache.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Windows event logging server
|
Specifies the server name for the Windows Event Logging extension (do not provide leading "\\" characters). If you do not specify a server, logging is performed on the local workstation.
The server should have a trusted relationship with the user's account and the user's workstation, depending on access rights and restrictions. |
Yes | string/ string |
|
| Retry interval
|
Specifies the interval (in minutes) between retries for the Windows Event Logging extension. | Default: 30 | Yes | dword/ int |
| Events to log
|
Event logging filter delineating which events (of those logged by the root Filter setting) to log to the Windows Event Logging extension.
Click the ellipsis "…" button to open the Events to log window, which presents a checklist of events for you to select. |
Default: 0
4: Credential Edit 8: Credential Delete 10: Credential Copy 20: Credential Add 100: Provisioning 200: Startup/Shutdown 400: Help 800: Settings Change 1000: Reauthentication 10000: Sync User Information 20000: Logon Field: System Username 40000: Logon Field: System Domain 80000: Logon Field: Third Field 100000: Logon Field: Username 200000: Logon Field: Fourth Field 800000: Application Password Change 1000000: Primary Logon Method Change 4000000: Backup/Restore 40000000: Event Types: Info |
Yes | dword/Ø |
2.17.11.3.1 Event Logging Filter Options
Select the events you want to log, then click OK. The table below groups the filters by function.
Note:
You must select Event Types Info to enable Event Logging.| Event Type | Name |
|---|---|
| Changes to user data (Credential) | Credential Add |
| Credential Copy | |
| Credential Delete | |
| Credential Edit | |
| Agent controls used (Feature) | Help |
| Reauthentication | |
| Settings Change | |
| Startup / Shutdown | |
| Credential data supplied (Logon) | Logon Field: Fourth Field |
| Logon Field: System Domain | |
| Logon Field: System Username | |
| Logon Field: Third Field | |
| Logon Field: Username | |
| Sync User Information | |
| Agent actions and changes (Application) | Primary Logon Method Change |
| Backup/Restore | |
| Application Password Change | |
| Event Types | Event Types Info (must be selected to enable Event Logging) |
To display this dialog, select the Filter option and click the ellipsis ("…") button on any of the following settings panels:
-
Event Logging (general)
-
XML File (for local storage)
-
Windows Event logging (advanced).
2.17.11.4 Configuring the Syslog Server
The Syslog settings control how the Agent records program events.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Destination host
|
Specifies the hostname to send messages to, using either a hostname or dotted IP v4 address.
Use 0.0.0.0 to disable sending to Syslog-Daemon, or use 255.255.255.255 to send to any daemon that is set up to receive broadcast messages. It must be on your local network as broadcast does not reach beyond a router. |
Default: localhost | No | string/ string |
| Destination port
|
Specifies the destination port for syslog messages using a number. | Default: 1468 | Yes | dword/ int |
| Protocol for sending messages
|
Specifies whether to send messages via TCP or UDP protocol.
Note that the UDP protocol is connectionless, so it is impossible to tell whether the Syslog Daemon is reachable at the specified hostname and port. If the UseTCP parameter is set to "Use UDP," the Syslog Extension returns |
0: Use UDP
1: Use TCP (Default) |
Yes | dword/Ø |
| Retry interval
|
Specifies the interval (in minutes) between retries for the Syslog extension. | Default: 30 | Yes | dword/ int |
| Events to log
|
Event Logging filter delineating which events (of those logged by the root Filter setting) to log to the Syslog extension. Click the ellipsis "…" button to see a list of events to log. | Default: 0
4: Credential Edit 8: Credential Delete 10: Credential Copy 20: Credential Add 100: Provisioning 200: Startup/Shutdown 400: Help 800: Settings Change 1000: Reauthentication 10000: Sync User Information 20000: Logon Field: System Username 40000: Logon Field: System Domain 80000: Logon Field: Third Field 100000: Logon Field: Username 200000: Logon Field: Fourth Field 800000: Application Password Change 1000000: Primary Logon Method Change 4000000: Backup/Restore 40000000: Event Types: Info |
Yes | dword/Ø |
2.17.11.5 XML File Event Logging
The XML File Event Logging settings let you specify which events should be logged locally. You can also change the default path to the local logging extension, and you can modify the retry interval of the logging cache.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Retry interval
|
Specifies the interval (in minutes) between retries for the Local (XML) File Logging extension. | Default: 30 | Yes | dword/ int |
| Events to log
|
Event Logging filter delineating which events (of those logged by the root Filter setting) to log to the Local (XML) File Logging extension.
Click the ellipsis "…" button to see a list of events to log. |
Default: 0
4: Credential Edit 8: Credential Delete 10: Credential Copy 20: Credential Add 100: Provisioning 200: Startup/Shutdown 400: Help 800: Settings Change 1000: Reauthentication 10000: Sync User Information 20000: Logon Field: System Username 40000: Logon Field: System Domain 80000: Logon Field: Third Field 100000: Logon Field: Username 200000: Logon Field: Fourth Field 800000: Application Password Change 1000000: Primary Logon Method Change 4000000: Backup/Restore 40000000: Event Types: Info |
Yes | dword/Ø |
2.17.11.6 Database Event Logging
Use the Database Event Logging menu to specify the server instance and table name where you want to send log data, as well as the fields to write to the database.
In addition to the fields, users must specify the server instance and table name. These are previously defined in the Database Setting and should not be required for Database Fields. If the database and table name are not specified for each field, events will not be written to the database.
The XML File Event Logging settings let you specify which events should be logged locally. You can also change the default path to the local logging extension, and you can modify the retry interval of the logging cache.
Note:
You must specify the database instance and table name in the Database Fields in order for events to be written to the database.| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Servers
|
Click the ellipsis "…" button to open a window in which to enter Database servers. Enter one server name per line, using the OLE DB format:
|
No | string/Ø | |
| Default server
|
If no other server is specified, the server to which the database log will be written. (OLE DB connection string) | Default: Server1 | No | string/ string |
| Default table
|
If no other table is specified, the table to which the database log will be written. | Yes | string/ string |
|
| Retry interval
|
Interval (in minutes) between retries for the Database extension. | Default: 30 | Yes | dword/ int |
| Events to log
|
Event Logging filter delineating which events (of those logged by the root Filter setting) to log to the Database extension. Click the ellipsis "…" button to see a list of events to log. | Default: 0
4: Credential Edit 8: Credential Delete 10: Credential Copy 20: Credential Add 100: Provisioning 200: Startup/Shutdown 400: Help 800: Settings Change 1000: Reauthentication 10000: Sync User Information 20000: Logon Field: System Username 40000: Logon Field: System Domain 80000: Logon Field: Third Field 100000: Logon Field: Username 200000: Logon Field: Fourth Field 800000: Application Password Change 1000000: Primary Logon Method Change 4000000: Backup/Restore 40000000: Event Types: Info |
Yes | dword/Ø |
2.17.11.6.1 Event Fields
The Event Fields screen lists the data assigned to each field in the event log. The fields are mapped to the log information as specified in the table below.
You can select which events to include in your log by checking the box next to the desired field(s). Fields 9 and 10 have no pre-assignment. Assign categories to these fields by checking their boxes and entering the name of the desired field next to the check box. Refer to the Events to log list on the Database screen for the available event names.
| Display Name/ Registry Path |
Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| AppName
|
The name of the application of the event log. | Default: AppName | Yes | string/ string |
| Category
|
The category of the event. | Default: Category | Yes | string/ string |
| Type
|
The specific type of event. | Default: Type | Yes | string/ string |
| TimeStamp
|
The time of the event. | Default: TimeStamp | Yes | string/ string |
| Field1
|
EventType | Default: Event type | Yes | string/ string |
| Field2
|
UserID | Default: User ID | Yes | string/ string |
| Field3
|
ThirdField | Default: Third field | Yes | string/ string |
| Field4
|
FourthField | Default: Fourth field | Yes | string/ string |
| Field5
|
WindowsUser | Default: Windows user | Yes | string/ string |
| Field6
|
Domain | Default: Domain | Yes | string/ string |
| Field7
|
ComputerName | Default: Computer name | Yes | string/ string |
| Field8
|
SSOSyncUser | Default: SSO synchronization user | Yes | string/ string |
| Field9
|
Customizable for your needs. | Open | Yes | string/ string |
| Field10
|
Customizable for your needs. | Open | Yes | string/ string |
2.17.11.7 Kiosk Manager Settings
Use the Kiosk Manager settings to configure sessions in a kiosk environment.
Note:
When using Kiosk Manager, you must disable response to hidden or minimized windows in User Experience settings.2.17.11.7.1 Session termination
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Allow administrator to closeKiosk Manager
|
Specifies whether an administrator has the ability to close Kiosk Manager. With this setting enabled, only a user with administrator credentials can close the Agent. | 0: No
1: Yes (Default) |
Yes | dword |
| Number of times to process termination
|
Enter the number of times that Kiosk Manager should process the termination of an application.
This setting instructs the termination process to loop a certain number of times or until it is done (whichever comes first). This allows Kiosk Manager to react to an application if it displays multiple screens during the termination process. |
Default: 1 | Yes | dword/ int |
| Timeout for locked session
|
Enter the length of time (in seconds) of inactivity after which Kiosk Manager should close a suspended/locked session. | Default: 600 (15 minutes) | Yes | dword/ int |
2.17.11.7.2 Multisession configuration
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Maximum number of sessions
|
Specifies the maximum number of sessions allowed at one time.
A setting of zero will be interpreted as one session. Note: There is no maximum number for this setting. |
Default: 1 | Yes | dword/ int |
| Track memory consumption
|
Specifies the level of memory usage at which Kiosk Manager should automatically close sessions. When system memory use has reached the percentage set by this value, Kiosk Manager automatically closes the oldest user sessions. | Minimum: 0 (disabled)
Maximum: 100 Default: 90 |
Yes | dword/ int |
2.17.11.7.3 Cached credentials
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Use cached credentials
|
Specifies whether to use cached credentials. If this setting is enabled, at logon the Agent displays a list of cached credentials for users to choose from. If this setting is disabled, the Agent does not display the list, and users must enter a user name at logon.
Enabling cached credentials improves performance. Note: When using Universal Authentication Manager as the primary logon method, you cannot use cached credentials (that is, select No for this setting). For a full discussion about configuring and deploying Universal Authentication Manager, see the Oracle Enterprise Single Sign-On Suite Installation Guide and Chapter 5, "Configuring Strong Authenticators with Universal Authentication Manager". |
0: No (Default)
1: Yes |
Yes | dword |
| Storage path
|
Specifies the default folder to store the cached credentials. The default is an empty string.
If this value is empty, the default folder is:
|
Default: An empty string | Yes | string |
| Expiration date
|
Specifies the number of days to retain cached credentials. Zero indicates that this feature is disabled. | Default: 30 | Yes | dword/ int |
2.17.11.7.4 Strong authentication options
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Lock session on smart card removal
|
Specifies whether to lock a session when the session owner removes the smart card from its reader. If set to not lock, the session remains open after smart card removal.
This setting is useful in a scenario where employees must display their smart cards at all times, and therefore cannot leave them in a reader. |
0: No
1: Yes (Default) |
Yes | dword |
| Lock session on read-only smart card removal
|
Specifies whether to lock a session when the session owner removes the read-only smart card from its reader. If set to not lock, the session remains open after read-only smart card removal.
This setting is useful in a scenario where employees must display their read-only smart cards at all times, and therefore cannot leave them in a reader. |
0: No
1: Yes (Default) |
Yes | dword |
| Lock session on ESSO-UAM token removal
|
Specifies whether to lock a session when the session owner removes a Universal Authentication Manager logon token from its reader (or taps out, in the case of passive proximity tokens). If set to not lock, the session remains open after token removal.
This setting is useful in a scenario where employees must display their tokens at all times, and therefore cannot leave them in a reader. Note: Any value other than zero (0) will result in token events being forwarded to Kiosk Manager. Whatever setting you select here will apply to all Universal Authentication Manager authenticators. |
0: No
1: Yes (Default) |
Yes | dword |
| Pre-populate on startup
|
Specifies whether to run a pre-populate step at startup. If an authenticator requires this step and Authentication Manager is not installed, this setting enables Kiosk Manager to perform the required pre-population, eliminating the need for the synchronization manager to reauthenticate.
Note: When using Universal Authentication Manager as the primary logon method, you must pre-populate on startup (that is, select Always for this setting). For a full discussion about configuring and deploying Universal Authentication Manager, see the Oracle Enterprise Single Sign-On Suite Plus Installation Guide and the Universal Authentication Manager Administrator's Guide. |
0: On device-in event (Default)
1: Always 2: Never |
Yes | dword |
| Monitor for device events
|
Specifies whether Kiosk Manager should actively monitor for device insertion and removal events.
Note: For integration with Universal Authentication Manager, you must select Always for this setting. |
0: Never
1: Only when Access Manager is installed (Default) 2: Always |
Yes | dword |
2.17.11.7.5 Audit Logging
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Event log name
|
Enter the name of the Windows event log for Kiosk Manager events. | Default: Application | Yes | string |
| Event log machine name
|
Enter the name of the local machine to log Kiosk Manager events. | No | string |
2.17.11.8 Kiosk Manager User Interface
The User Interface settings control the appearance and interaction of Kiosk Manager with end-users.
2.17.11.8.1 Options
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Allow computer restart
|
Specifies whether the restart computer option is enabled in the Kiosk Manager Desktop Manager. You can also choose to allow only an administrator to have privileges to restart the computer by selecting Administrator must supply password.
Note: If the Kiosk account does not have sufficient privileges, restarting might still be disabled. |
0: No (Default)
1: Yes 2: Administrator must supply password |
Yes | dword |
| Allow computer shutdown
|
Specifies whether the shutdown computer option is enabled in the Kiosk Manager Desktop Manager. You can also choose to allow only an administrator to have privileges to shut down the computer by selecting Administrator must supply password.
Note: If the Kiosk account does not have sufficient privileges, shutting down might still be disabled. |
0: No (Default)
1: Yes 2: Administrator must supply password |
Yes | dword |
| Show confirmation message when restarting kiosk
|
Specifies whether to prompt the user with a confirmation message after choosing to restart the kiosk. | 0: No (Default)
1: Yes |
Yes | dword |
| Show confirmation message when shutting down kiosk
|
Specifies whether to prompt the user with a confirmation message after choosing to shut down the kiosk. | 0: No (Default)
1: Yes |
Yes | dword |
| Lock session when screen saver times out
|
Specifies whether to lock a session after the screen saver timeout occurs. A blank value has the same effect as setting the value to "No."
Specifies whether Kiosk Manager should lock a session when the screen saver timeout occurs. If you set this value to No (default value) or do not specify a setting, Kiosk Manager does not lock the session after the screen saver timeout occurs if device detection is used to control the session. If you set this value to Yes, Kiosk Manager locks the session. |
0: No (Default)
1: Yes |
Yes | dword |
| Timeout for authentication prompt
|
Enter the length of time (in seconds) after which the synchronization/authentication dialog closes (due to inactivity). | Default: 600 [15 minutes] | Yes | dword/ int |
2.17.11.8.2 Status window
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Show desktop status window
|
Specifies whether to show the optional window that displays the current session owner. | 0: No (Default)
1: Yes |
Yes | dword |
| X coordinate
|
Enter the X coordinate (horizontal location) for the status window.
Note: Negative values are represented by large positive numbers in the registry. For example: -1 = 4294967295 and -2 = 4294967294. |
Default: 0 | Yes | dword/ int |
| Y coordinate
|
Enter the Y coordinate (vertical location) for the status window.
Note: Negative values are represented by large positive numbers in the registry. For example: -1 = 4294967295 and -2 = 4294967294. |
Default: 0 | Yes | dword/ int |
2.17.11.8.3 Transparent screen lock
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Use transparent lock
|
Specifies whether to enable the transparent screen lock.
Specifies whether to enable the transparent screen lock. The transparent screen lock provides the ability to lock the desktop inputs (keyboard and mouse) in view mode. For example, a monitoring application can be viewed without starting a session. When there are multiple sessions running, the last active session displays when transparent screen lock engages. |
0: No (Default)
1: Yes, but only for active session 2: Yes |
Yes | dword |
| Delay period
|
Specifies the number of seconds to wait for mouse and keyboard inactivity before showing the desktop.
Note: You must enable the Use transparent lock setting above in order to use this feature. |
5: Default | Yes | dword/ int |
| Ignore delay period if authentication is canceled
|
Specifies whether transparency should take effect immediately after canceling an authenticator or synchronizer dialog.
Note: You must enable the Use transparent lock setting above in order to use this feature. |
0: No (The desktop displays when the inactivity timer expires.) (Default)
1: Yes (The desktop displays instantly.) |
Yes | dword |
| Only recognize Ctrl-Alt-Del
|
Specifies whether the Agent should recognize only Ctrl-Alt-Del and authenticators that support "device-in" to display the Desktop Manager. | 0: No (Any keyboard or mouse activity results in displaying the Desktop Manager.) (Default)
1: Yes (The Agent ignores all keyboard or mouse activities. Only Ctrl-Alt-Del and authenticators that support "device-in" will be recognized to display the Desktop Manager.) |
Yes | dword |
2.17.11.8.4 Setting the Kiosk Manager Background Image
Use this panel to place a background image, such as your company logo, on the Kiosk Manager Desktop Manager.
To configure the administrative settings for the Desktop Manager background image:
See Customizing the Desktop Manager for examples of using all Kiosk Manager desktop customization settings.
-
Open the Administrative Console.
-
Navigate to Global Agent Settings > Live > Kiosk Manager > User Interface > Background Image.
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Location of image file
|
Fully-qualified path and filename of the image file.
Enter the fully-qualified path, including the filename, to the image file. Click the ellipsis "…" button to locate the file. |
Yes | string/ filename |
|
| X coordinate
|
Enter the X coordinate (horizontal location) for the image.
Note: Negative values are represented by large positive numbers in the registry. For example: -1 = 4294967295 and -2 = 4294967294. |
Default: 0 | Yes | dword/ int |
| Y coordinate
|
Enter the Y coordinate (vertical location) for the image.
Note: Negative values are represented by large positive numbers in the registry. For example: -1 = 4294967295 and -2 = 4294967294. |
Default: 0 | Yes | dword/ int |
| Width
|
Enter the width of the image (in pixels). | Default: 300 | Yes | dword/ int |
| Height
|
Enter the height of the image (in pixels). | Default: 300 | Yes | dword/ int |
| Placement behavior
|
Specifies how to handle the image with respect to its coordinates and dimensions. | 0: Normal (Place image in upper left corner of coordinates and clip if larger than specified height and width) (Default)
1: Auto (Place image in upper left corner of coordinates) 2: Center (Center image within coordinates and clip if larger than specified height and width) 3: Stretch (Stretch or shrink image to fit within specified coordinates) 4: Maximize (Stretch image to full screen size) |
Yes | dword |
2.17.11.8.5 Message
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Message text
|
Enter a message to display on Desktop Manager. This message appears when the user unlocks a new session. | Yes | string/ string |
2.17.11.8.6 Font
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Name
|
Specifies the Message Text font. Select a font from the drop-down list. | Yes | string/ string |
|
| Size
|
Specifies the Message Text font size. | Default: 0 | Yes | dword/ int |
| Style
|
Specifies the Message Text font style. | 0: Regular (Default)
1: Bold 2: Italic |
Yes | dword |
2.17.11.8.7 Color
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Background
|
Click the ellipsis "…" button to select the background color for the Message Text. | Yes | string/ color |
|
| Foreground
|
Click the ellipsis "…" button to select the foreground color for the Message Text. | Yes | string/ string |
2.17.11.8.8 Placement
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| X coordinate
|
Enter the X coordinate for the Message Text, positioned relative to the Status image on the Kiosk Manager Desktop screen. A negative value places the message to the left of the Status image.
Note: Negative values are represented by large positive numbers in the registry. For example: -1 = 4294967295 and -2 = 4294967294. |
Default: 0 | Yes | dword/ int |
| Y coordinate
|
Enter the Y coordinate for the Message Text, positioned relative to the Status image on the Kiosk Manager Desktop screen. A negative value places the message above the Status image.
Note: Negative values are represented by large positive numbers in the registry. For example: -1 = 4294967295 and -2 = 4294967294. |
Default: 0 | Yes | dword/ int |
| Width
|
Specifies the width of the Message Text (in pixels). | Default: 300 | Yes | dword/ int |
| Height
|
Specifies the height of the Message Text (in pixels). | Default: 300 | Yes | dword/ int |
| Size automatically
|
Specifies whether to auto-size the Message Text to fit the available area. | 0: No (Default)
1: Yes |
Yes | dword |
2.17.12 Oracle Access Manager Support
Logon Manager provides transparent single sign-on capability to Oracle Access Management Access Manager-protected Web applications by securely authenticating to Access Manager via one or more Access Manager endpoints using SSL, obtaining the Access Manager authentication cookie, and transparently injecting it into the current Web browser session. This 100% seamless integration completely eliminates the visibility of the logon process to Access Manager-protected Web applications, allowing for instant application availability without compromising security.
Note:
Logon Manager ships with a pre-configured template for Access Manager. You must publish this template to the repository and propagate it to Access Manager-enabled Logon Manager client machines to use this feature.Integration with Access Manager is only possible when using the Embedded Credential Collector; the Distributed Credential Collector is not supported.
To enable this capability, you must:
-
Install and configure at least one Access Manager endpoint within your Access Manager deployment.
-
Install the "OAM Support" component of Logon Manager on end-user machines as described in the Oracle Enterprise Single Sign-On Suite Installation Guide.
-
Publish the OAM Protected Resources template to the repository. This template is included in the Administrative Console installation.
-
Launch the Administrative Console.
-
Right-click on the Applications node and select New Web App.
-
Select OAM Protected Resources from the dropdown list of available applications.
-
Click Finish. The OAM Protected Resources application is now listed under the Applications node. There is no need to modify the URLs or logon fields; the template is configured for immediate use.
-
-
Configure Logon Manager to connect to the desired Access Manager endpoint(s) as described in Access Manager Settings. (If more than one endpoint is specified, Logon Manager will attempt connecting to each specified endpoint, in the order entered in the Administrative Console, until a connection is established.)
Note:
You must enter the endpoint URL(s) in the following format only:https://<server>:<port>/oam/services/rest/11.1.2.0.0/sso/token/where
<server>is the full network address of the target endpoint and<port>is the number of the port on which the endpoint is listening for connections. -
Provide Logon Manager with the end-user's Access Manager credentials using one of the following methods:
-
Remotely provisioning the credentials via Provisioning Gateway;
-
Configuring Logon Manager to use the user's repository credentials to authenticate to Access Manager;
-
Capturing the Access Manager credentials from the end-user during Logon Manager's first attempt to authenticate to Access Manager. (The captured credentials are stored in Logon Manager's secure cache once captured; the user will not be prompted to provide them again unless the secure cache is erased.)
-
The following session attributes are pushed by Logon Manager into the session:
| Attribute | Description |
|---|---|
| $session.attr.client.firewallenabled | Specifies whether a firewall is active on the client machine. |
| $session.attr.client.antivirusenabled | Specifies whether an anti-virus application is active on the client machine. |
| $session.attr.client.fingerprint | Specifies a unique identifier for the client machine. |
After being positively authenticated to Access Manager, the session cookie remains in the Web browser's cache as long as Logon Manager is running and is periodically updated according to an update interval configured by the administrator, or upon expiration. When Logon Manager shuts down, the cookie is removed from the Web browser's cache.
Note:
Logon Manager does not support password change for Access Manager credentials. If the user's Access Manager password expires, it must be reset via other means. If Logon Manager cannot authenticate with the currently supplied credentials to Access Manager, it will prompt the user to enter valid credentials.You can change the message that prompts the user to enter Access Manager credentials using the Authentication dialog message setting in the User interface settings group, or leave the default message. If you choose to change it, select a message that will be meaningful to the user in your particular environment.]
2.17.12.1 Access Manager Settings
The following settings configure Access Manager integration with Logon Manager.
2.17.12.1.1 Connection Information
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Endpoints
|
A list of URLs that the Agent should use as Access Manager token endpoints.
Check the box and click the ellipsis (…) button, then enter the URLs in the Endpoints window, one per line. Click OK when you have entered all the URLs you want the Agent to try. The Agent attempts to use the URLs in the order that you enter them; if the first URL fails, the Agent proceeds to the second one, and so on. |
Yes | string/Ø | |
| Use sync credentials to authenticate to OAM
|
Allows Logon Manager to use the synchronizer's credentials to automatically create an account for an Access Manager template.
Note: This feature supports only Active Directory, AD LDS (ADAM), and LDAP synchronizers. You cannot enable this setting with the Active Directory synchronizer unless you select Use Active Directory server account only for the Credentials to use setting. You cannot enable this setting with the AD LDS (ADAM) synchronizer unless you select ADAM server account for the Credentials to use setting. |
0: No (Default)
1: Yes |
Yes | dword/Ø |
2.17.12.1.2 Behavior
| Display Name/ Registry Path |
Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Perform OAM server certificate validation
|
Specifies whether the Agent should check the Access Manager server certificate when connecting to the endpoint. If the certificate is invalid, no connection is established. | 0: No. The Agent ignores the server certificate (less secure) (Default)
1: Yes. The Agent checks the server certificate. |
Yes | dword/Ø |
| OAM credentials request retry interval
|
Specifies the interval (in seconds) after which the Agent will ask for Access Manager credentials again if the user cancels an Access Manager credentials request.
Values can range from zero (the Agent request credentials immediately) to 300 (the Agent requests credentials after five minutes). |
Any integer between 0 and 300.
Default is 30. |
Yes | dword/ int |
| OAM session renewal interval
|
Specifies the interval (in minutes) that the Agent uses for polling an Access Manager endpoint in order to detect whether the Access Manager session token is valid.
The minimum value is one minute, which means that the Agent checks the Access Manager session token validity at one minute intervals. Note: Greater interval values create less network traffic but lower sensitivity to Access Manager session token expiry. |
Any positive integer.
Default is 1. |
Yes | dword/ int |
2.17.12.1.3 User interface
| Display Name/ Registry Path |
Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Authentication dialog message
|
The message that Logon Manager displays to prompt the user for Access Manager credentials. This message should be meaningful to the user in your environment and approximately the same length as the default message. | Default: Logon Manager needs your credentials for Access Manager. If you do not know these credentials, contact your administrator. | Yes | string/ string |
2.17.13 Integrating with Password Reset
The Universal Authentication Manager Challenge Questions logon method enables the use of Password Reset to store questions and answers enrolled by the user through Universal Authentication Manager (existing Password Reset enrollments cannot be used by Universal Authentication Manager) providing portability for the enrollment data. Synchronization with Password Reset also enables control over the questions that are available to different users and groups, as well as individual customization of the weight of each question, as allowed by Password Reset.
In order to configure Universal Authentication Manager to integrate with Password Reset, you must do the following:
-
Install the Challenge Questions logon method if it has not already been installed. For instructions, see the Oracle Enterprise Single Sign-On Suite Installation Guide.
-
Install and configure Password Reset as described in the Oracle Enterprise Single Sign-On Suite Installation Guide.
-
Obtain the Password Reset synchronization URL.The URL will have the following format:
https://<hostname>:<port>/vGOSelfServiceReset/WebServices/Synchronization.asmx -
Configure Universal Authentication Manager to synchronize with Password Reset as described in Chapter 5, "Integrating with Password Reset".
-
Configure the challenge questions as desired within Password Reset. For more information, see Chapter 4, "Using the Administrative Console to Configure Password Reset".
-
Instruct users to select their questions and provide answers by enrolling the Challenge Questions logon method via Universal Authentication Manager; existing Password Reset enrollments cannot be used by Universal Authentication Manager.
To configure Universal Authentication Manager to leverage Password Reset questions and answers for authentication, do the following:
-
Launch the Administrative Console.
-
Under the Global Agent Settings node navigate to the settings set you want to modify, or load it if necessary.
-
Navigate to the Password Reset node and select it.
-
In the right-hand pane, select the check-box next to the Password Reset Synchronization URL option and enter the appropriate URL in the following format:
https://<hostname>:<port>/vGOSelfServiceReset/WebServices/Synchronization.asmxNote:
If you have not configured your Password Reset deployment for SSL connectivity, replacehttps://withhttp://. -
Export your settings to a
.REGfile for distribution to end-user machines:-
From the File menu, select Export.
-
In the dialog that appears, click HKLM Registry Format (.REG).
-
In the Save dialog that appears, navigate to a desired target location, enter a descriptive file name and click Save.
-
-
Distribute the
.REGfile to end-user machines and merge it into each machine's Windows registry.Note:
The Console produces a.REGfile compatible only with 32-bit systems. If you are merging the.REGfile on a 64-bit system, you must run the following command to move the merged registry data to the correct location within the registry (otherwise, Universal Authentication Manager will not function):reg.exe COPY HKLM\Software\PasslogixHKLM\Software\Wow6432Node\Passlogix /s
2.17.13.1 Password Reset Settings
| Display Name/ Registry Path | Description | Options/ Default | Overridable | RegType/ DataType |
|---|---|---|---|---|
| Password Reset synchronization URL
|
Specifies the URL to the Password Reset synchronization server when configuring Universal Authentication Manager to leverage Password Reset's enrollment interview as challenge questions for authentication purposes.
Example
Note: If you have not configured your Password Reset deployment for SSL connectivity, replace |
Yes | string/ string |
2.17.14 Using the Configuration Test Manager
This tool enables you to test your Global Agent Settings to ensure that they are properly configured.
Note:
You can only run these tests on an Active Directory repository.To access this tool, either:
-
Select Test Global Agent Settings from the Tools menu. If you access the test manager from this location, you are required to pick a set of Global Agent Settings to test.
or
-
Right-click on a set of Global Agent Settings and click Test. If you access the test manager from this location, the tests will run on that set of Global Agent Settings only.
All changes made in the test manager are reflected in the Administrative Console. Upon launching the test manager, a dialog appears, informing you that any changes you make in the test manager will be reflected in the Administrative Console. You can dismiss this message by selecting Do not show this notice again.
Note:
Before using this tool, in addition to reading this help information, Oracle strongly recommends that you read Deploying Logon Manager with a Directory-Based Repository and the Configuring the Agent with Global Agent Settings.These describe best practices and recommended procedures for deploying Logon Manager on your repository and configuring the Logon Manager Agent with Global Agent Settings and administrative overrides.
There are three stages in the testing process:
-
Select Categories. Select the test categories to determine which tests to run.
-
Enter Parameters. Enter all data needed to run the tests.
-
Execution and Results. Run tests, view results, and make changes if necessary.
2.17.14.1 Categories
When you open this tool, the Categories stage is selected in the left pane. The Test Categories pane lists the categories and individual tests.
The Test Categories list is interactive—you can check or uncheck desired categories, and expand or collapse the categories to view the individual tests. You can click on any category or test and a description appears in the right pane.
By default, all categories are selected. Individual tests cannot be selected.
As long as at least one test category is selected, the Next button and the Parameters stage are enabled. The Execution and Results stage is unavailable until all of the data parameters are satisfied.
The Synchronization test category contains the following individual tests, which verify synchronization settings.
| Test Name | Test Description |
|---|---|
| Server Validation | Verifies that the specified server is a valid server name and is accessible. If an IP address is entered as the server name, or the server cannot be accessed, this test will fail. |
| SSL Configuration | Checks the server to determine if SSL is enabled. If SSL is not enabled on the server, and SSL is enabled in the Administrative Console, this test will fail. |
| Schema Extension | Verifies that the schema is extended. If the schema is not extended, this test will fail. |
| User Object Schema Extension | Verifies that the schema is extended under the Active Directory User Object. If the schema is not extended, this test will fail. This test applies to Active Directory synchronizers only. |
| Configuration Object Retrieval | Verifies that the Configuration Object Base Location path is valid and that the configuration objects can be retrieved with the test credentials. If the path is not valid or the test credentials supplied do not have permission to retrieve configuration objects, this test will fail. |
| Credential Location Access Rights | Verifies the proper access rights are assigned to the credential location on the server to upload, retrieve, and delete credentials. If the supplied test credentials do not have permission to perform any of these actions, this test will fail. |
Ensure the Synchronization test category is selected and click Next, or click the Parameters stage from the left pane.
2.17.14.2 Parameters
The Parameters stage collects all the data necessary to run the tests. The data requested during this stage is dependant upon the test categories selected in the Categories stage.
The Execution and Results stage is unavailable until all of the data parameters are satisfied.
2.17.14.2.1 Test Parameters
The parameters are listed in the Test Parameters pane and are dynamic based upon the tests selected. Each parameter has a status icon of Needed or Acquired to visually indicate which parameters need attention. For example, if the User Credentials have not been acquired, and the Global Agent Settings have been acquired, the Test Parameter list will look like this:
2.17.14.2.2 Data
The data needed for each parameter is entered in the Data pane on the right.
You must input all needed data before running any tests. After all parameters are successfully acquired, the Next button and Execution and Results stage become available.
The Next Parameter button, located on the bottom of the Data pane, is available when there are multiple parameters. It enables you to quickly click through all the parameters.
Note:
It is important that you ensure that the quality of the data parameters entered is good. Just because data exists and a status is set to acquired, does not mean the data is correct.As you enter, it is captured for the current session. You can either save or clear the data for future sessions:
-
Saving the data. If you want to save the data for future sessions, ensure the Save this value check box located below the Data pane is checked.
-
Clearing the data. If you want to clear the data for this and future sessions, click the Clear All Data button at the top of the Data pane. A message will appear asking if you are sure you want to do this. Confirming this action will clear all entered parameters, turning all of the parameter statuses to Needed. It will also disable the option to proceed to the Execution & Results stage.
After you have entered all data, click Next >, or select the Execution & Results stage in the left pane.
After all data has been acquired, move on to the next stage.
2.17.14.3 Execution and Results
The Execution & Results stage is where you run the tests, view the results, and make changes if necessary.
You cannot proceed to the Execution & Results stage until you have entered all of the data required during the Parameters stage.
The Test Execution and Results pane lists all the tests to be run, in the order that they will be run. After you click Execute Tests, the tests begin to run; while a test is in progress, an icon appears indicating the status of the testing. There are five possible statuses:
-
Passed. The test has completed and passed.
-
Need info. The test is paused to allow the user to enter prompted information.
-
Warning. The test has paused, prompting the user with a warning.
-
Failed. The test has failed. Information is provided explaining why the test failed. All testing stops when a single test fails.
-
In Progress. Test is in progress.
After the tests have run, you can click through them and read the results and messages about each test in the Description pane.
2.17.14.3.1 Description
The Description pane provides a description of the test. As tests run, the lower portion of the Description pane will provide messages such as warnings, passed and failed situations, and fields to change information and continue testing.
The Execute Tests button begins the testing. When tests are running, the Execute Tests button toggles to Stop Tests, allowing you to cancel the testing if desired.
In this pane, you can interact with either Failed or Need Info tests results. You are presented with information and actions or fields you can make changes to and re-run the tests.
2.17.14.3.2 Clear All Data
If you want to clear the data for this test and future sessions, click the Clear All Data button at the top of the Description pane. A message will appear asking if you are sure you want to do this and provide two paths:
-
Click OK to clear ALL parameters.
-
Click Cancel to close the dialog, and all data is retained.
If you click OK, and tests were previously run with results available in the right frame, the test results persist, but the Execute Test button is disabled.
After the configuration passes all the tests, you can exit by closing the Test Manager from the X in the top right title bar. You may also use the Clear All Data button, navigate to the Categories or Parameters page, and set things up to run different tests.
2.18 Deploying Logon Manager
The topics in this section describe the options for packaging, deploying, and managing Logon Manager in a networked environment:
2.18.1 Default MSI Deployment Options
This section describes using the default MSI package from the following perspectives:
2.18.1.1 Performing an Installation with the Shipped MSI Package
To perform an installation using the shipped MSI package, run the program setup from the network share and follow the prompts. Because each environment is different and each organization has different needs, Oracle recommends you perform a custom installation and select the desired components.
See the Oracle Enterprise Single Sign-On Suite Installation Guide for complete information.
2.18.1.2 Installing from the Command Line
The MSI package can be installed from the command line. To do this, run the setup program with the appropriate parameters. The components of the command line are the executable name, InstallShield parameters (for example, /qn for a quiet install), and the Logon Manager feature names.
| Command | Purpose |
|---|---|
/qn |
The MSI package should install quietly (optional) |
RUNVGO |
Whether the Agent should be launched after the install: YES or NO |
MDAC |
Whether to install MDAC: YES or NO |
ADDLOCAL "FeatureNames" |
FeatureNames is a comma-delimited list of the Logon Manager features to install. Refer to the Oracle Enterprise Single Sign-On Suite Installation Guide section on MSI Package Contents for a list of acceptable values. |
Note:
Quoting is critical. There must be quotes around each option's value (following the equal (=) sign, and the MSI features list.Example
Install (without seeing any visual signs) the core, the Windows authenticator, NO support for Microsoft Internet Explorer or hosts, and the Microsoft Active Directory synchronizer, and then start the Agent, as follows:
Msiexec /i ProductName.msi /qn RUNVGO="YES" ADDLOCAL="Core,Authenticators,SLA,LogonMgr,SetupMgr,SyncMgr,AD_Sync,English_Pack"
2.18.1.3 Installing the MSI Package Remotely
To install Logon Manager to a computer remotely, verify that your system meets the following conditions:
-
Windows Installer must be present on the remote computer.
-
The
MSIpackage must be accessible to the remote computer. -
The person performing the remote installation must have administrator access rights to the remote computer.
2.18.1.3.1 Editing the MSI Package
Some organizations want to distribute MSI packages without Oracle-supplied optional components or with additional components (for example, alternative authenticators). The Administrative Console includes an MSI Generator that you can use to create custom MSIs to suit the needs of your enterprise.
2.18.1.3.2 Adding Console-Created Application Logons and Global Agent Settings
You can also use the Custom MSI Generator to create a modified Logon Manager installation package. The modified MSI package you create with this feature can include:
-
Selected application logons from an
entlist.inifile or from the current Administrative Console configuration. -
Agent settings from an administrative overrides (
.ini) file or from the current Administrative Console configuration.
To do this use the Generate Customized MSI command on the Tools menu.
Note:
Use the Configuration Test Manager to verify that you have configured your Global Agent Settings correctly.2.18.1.4 Microsoft Windows Installer (MSI) Package
Logon Manager ships as an MSI package, a standard format used by installers from Microsoft and other vendors. Many other installers can read MSI files. For information on the contents of the Logon Manager Setup MSI, see the Oracle Enterprise Single Sign-On Suite Release Notes.
You might want to create an MSI package to meet special requirements, such as:
-
Providing custom applications and Logon Manager Agent configurations.
-
Deactivating some options or components (for example, different authenticators) before end users install the Agent.
-
Adding options or components to accommodate a complex environment, for example, one using biometric security devices or having an unusual network topology.
To meet these needs, there are these options:
-
Use a command-line installation.
-
Customize the installer package using the Administrative Console Custom MSI Generator.
-
Include logons and Global Agent Setting configurations that you created in the Administrative Console in the installer.
Note:
Use the Configuration Test Manager to verify that you have configured your Global Agent Settings correctly. -
Deploy using a third-party deployment tool.
2.18.2 Deploying the Agent with Anywhere
Anywhere provides a simple and flexible method for deploying configurations of Logon Manager, Authentication Manager, Provisioning Gateway, and Provisioning Gateway in any combination, all with little or no administrator involvement.
You can create as many configurations as necessary for members of your enterprise, and use Anywhere to take snapshots and compile complete deployment packages, which you then distribute to the appropriate users. Anywhere also simplifies the upgrade and rollback process, all with virtually no hands-on involvement on your part.
See Chapter 3, "Configuring an Agent Deployment with Anywhere" for complete instructions to configure and deploy Logon Manager using the Anywhere component.
2.18.3 Using the MSI Generator
The MSI Generator enables you to create a custom MSI package to use for mass deployment to Logon Manager end-users, based on an existing MSI package.
Generate MSI is typically used to modify the Logon Manager installation package (\Full\setup.msi on the Logon Manager distribution disk) to include logons or settings in the initial desktop installation of Logon Manager. The MSI file you create can include:
-
Selected application logons from an
entlist.inifile or from the current Administrative Console configuration. -
Agent settings from an administrative overrides (
.ini) file or from the current Administrative Console configuration.
To access this tool, select Generate Customized MSI from the Tools menu.
Note:
Before using this tool, in addition to reading this help information, Oracle strongly recommends that you refer to the Oracle Enterprise Single Sign-On Suite Installation Guide for a discussion of packaging Logon Manager for mass deployment.There are three stages in the .MSI generation process:
-
Base MSI Selection. Select a Base MSI file.
-
Selecting MSI Features. Select the features to include in your custom
MSIfile. -
Selecting a Set of Global Agent Settings and Generating a New MSI. Select the Global Agent Settings file to include, and an output file location.
2.18.3.1 Base MSI Selection
Upon opening this tool, the Base MSI Selection stage is selected in the left pane. All other stages are unavailable until the base MSI file is selected.
| Element | Function |
|---|---|
| Base (MSI)… | The base installer package to customize. Type the filename or click the ellipsis ("…") button to select the .msi file. |
| Output (MSI)… | The customized installer package that you will send to end users. Type a filename or click the ellipsis ("…") button to select an existing .msi file. |
-
In the Path field, click Browse…, navigate to the
MSIfile, and click Open. If an invalidMSIfile is selected, a message appears indicating that theMSIfile failed to open. -
Click Next >, or select the stage in the left pane.
2.18.3.2 Selecting MSI Features
The Feature Selection stage becomes available after you select a valid MSI file. The features display in a tree structure.
Make your selections and click Next >, or select the New MSI Generation stage in the left pane.
There are three possible states for the check boxes:
-
Unchecked. A state of no check in the parent node indicates that no child nodes are checked. The reverse is also true - if no child nodes are checked, the parent node is unchecked.
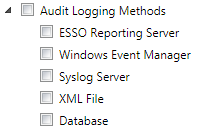
-
Partial Check. If any (but not all) of the child nodes are checked, the parent reflects this with a partial check state. A partial check in a parent node indicates that at least one of the non-default child nodes is checked.
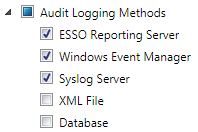
-
Checked. If a parent is checked, all of its children are checked as well. The reverse is also true—if all of the children are checked, the parent is checked as well.
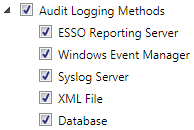
There might be some default items in the list that are required in the installer, and cannot be changed. An example of this is the English item in the Languages node in the Logon Manager
MSIfile. English is installed as the default language. Default items have no influence on the state of the checkboxes and are unavailable for selection.
2.18.3.3 Selecting a Set of Global Agent Settings and Generating a New MSI
The New MSI Generation stage becomes available after you select a valid MSI file. In this stage you choose the set of Global Agent Settings that you want to include, and Output location for the MSI file.
-
If you want to include a Global Agent Settings file in the
MSIfile, select it from the Global Agent Settings drop-down box. You can leave the default selection of <None> if you do not want to include a Global Agent Settings file. -
In the Output MSI field, click the Browse (…) button. Select a valid path and enter a File Name for the output
MSIfile. Click Save. If you enter an invalid path or name, a message appears indicating that the output MSI file name is invalid. -
Click Generate. A message appears indicating that the file has been saved. Click OK.
Note:
If an error occurs, ensure that you have entered a valid path and file name.2.18.4 Using Other Deployment Tools
Logon Manager works with numerous deployment methods and tools, including (but not limited to):
-
Manual installation (for example, from a CD-ROM or network share)
-
Microsoft Windows Installer (
MSI) service (local or remote installation) -
Network remote installation (for example, copy files and install registry entries remotely to a desktop)
-
Microsoft SMS
-
IBM Tivoli
-
Attachmate NetWizard
-
Intel LANDesk
-
Novadigm Radia/EDM
-
Novell ZENworks
-
HP OpenView
-
Seagate Desktop Management Suite
-
McAfee ZAC Suite
-
Veritas WinINSTALL
2.19 Using Kiosk Manager
Kiosk Manager delivers a secure, easy to use and easy to administer solution that addresses the needs of traditional single sign-on in a kiosk environment. Kiosk Manager has a client-side agent that provides user identification to the kiosk by prompting users to log on with a Windows password or any supported primary authenticator. The Agent suspends or closes sessions and seamlessly shuts down all applications after a specified period of inactivity.
The following topics are covered in this section:
The Administrative Console cannot run simultaneously with the Kiosk Manager Session Agent. If you launch the Session Agent while the Administrative Console is running, an error message displays saying, "Cannot run Kiosk Manager until Administrative Console is closed."
It is recommended that you do not use the Administrative Console on a workstation running Kiosk Manager.
2.19.1 Events and Actions
The following overview describes Kiosk Manager session functionality.
2.19.1.1 Types of Events
Kiosk Manager can be configured so that actions can be performed by any combination of the events below for all types of authenticators supported by Logon Manager:
-
After Session Unlocked
-
AM Device In
-
AM Device Out
-
AM Grace Period
-
Authenticator Logon
-
Authenticator Timeout
-
Before Session Unlocked
-
Cached Credential Session Start
-
Session End
-
Session Locked
-
Session Start
-
Timer Expired
-
Transparent Screen Displayed
-
Transparent Screen Hidden
-
User Change
2.19.1.2 Configuring Events and Action Lists
Based upon the above events, Kiosk Manager can run a specified terminate list, launch a custom task (.NET application or script) through a run list, or specify a special action:
-
Terminate list. A list of applications to be closed by Kiosk Manager on a specified event. (Previously known as black lists or applications to close on session end.)
-
Run list. Either a
.NET APIto call or a script of command lines to be executed by Kiosk Manager on a specified event. -
Special actions list. Special action lists specify how to handle application windows, such as the positioning of the application and the order that this application has actions performed on it.
These features are configured through the Logon Manager Administrative Console under Kiosk Manager > Actions and Session States:
-
An Action tells Kiosk Manager to do something, such as call a
.NETmethod or terminate a specific application. -
Session States are a list of events, authenticators, and security settings to associate with actions. For example, a defined Session State can instruct Kiosk Manager to perform a specified list of actions when a session ends.
See the following sections for instructions on:
2.19.1.3 Creating an Action List
An action tells Kiosk Manager to do something, such as call a .NET method or terminate a specific application.
There are two ways to create an action list:
-
Open the Administrative Console.
-
Expand the Kiosk Manager node.
-
Click Actions.
-
Click Add or right-click and select New Action.
-
Enter a Name, and then select the List Type. Click OK when complete. The three types of actions lists are:
-
Terminate List. A list of applications to be closed by Kiosk Manager on session end.
-
Run List. Either a
.NET APIto call or a script of command lines for Kiosk Manager to execute. -
Special Action List. Specifies how to handle application windows, such as the positioning of the application and the order of the actions performed on this application.
Note:
For more information, refer to the specific list section for complete instructions on creating all lists.
-
Another way to create an action list is:
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Select a Session State and click the Actions tab.
-
Click Add.
2.19.1.4 Creating and Using Terminate Lists
Use terminate lists to specify applications for Kiosk Manager to close on session end.
To display this tab:
-
Expand the Kiosk Manager node and select Actions.
-
Click on any Terminate List.
| Control | Function |
|---|---|
| AppPathKeys | The Windows registry key identifying an application associated with this logon to match against running processes. (Usually the application executable's name, such as Notepad.exe) |
| Window Titles | Text matched against logon window titles to identify logon requests. |
| Process Termination Type | Select the methods of termination for applications to be closed on session end:
Note: When using keystroke sequences to terminate an application, a visual flicker occurs on the end user's screen. This flicker is a function of using SendKeys to terminate an application. |
| Disabled | Select this checkbox to disable this list. Disabling a list allows you to retain the settings in a list without deleting the original list, allowing you to refer to the settings and use them with other lists. |
2.19.1.5 Configuring Kiosk Manager to Terminate an Application
To have Kiosk Manager terminate an application:
-
Under the AppPath Keys box, click Add. The Process Path Key dialog displays.
-
Enter a valid application key (usually the application executable's name, such as Notepad.exe). Click OK.
-
The application has been added to the list of applications to close on session end. Kiosk Manager will terminate these applications when a session ends.
-
Use the Edit and Delete buttons to modify or remove applications from this list.
-
In the Window Titles box, click Add. The Windows Title dialog appears.
-
Enter a valid windows title. Click OK.
2.19.1.6 Specifying a Window Title for Matching
To specify a window title for matching:
-
Enter (or edit) the exact Window Title.
-
Click OK.
2.19.1.7 Using SendKeys with Kiosk Manager
Note:
When using keystroke sequences to terminate an application, a visual flicker occurs on the end user's screen. This flicker is a function of using SendKeys to terminate an application.Each key is represented by one or more characters. To specify a single keyboard character, use the character itself. For example, to represent the letter A, pass in the string "A" to the method. To represent more than one character, append each additional character to the one preceding it. To represent the letters A, B, and C, specify the parameter as "ABC."
The plus sign (+), caret (^), percent sign (%), tilde (~), and parentheses () have special meanings to SendKeys. To specify one of these characters, enclose it within braces ({}). For example, to specify the plus sign, use "{+}". To specify brace characters, use "{{}" and "{}}". Brackets ([ ]) have no special meaning to SendKeys, but you must enclose them in braces. In other applications, brackets do have a special meaning that might be significant when dynamic data exchange (DDE) occurs.
To specify characters that aren't displayed when you press a key, such as ENTER or TAB, and keys that represent actions rather than characters, use the codes in the following table.
| Key | Code |
|---|---|
| BACKSPACE | {BACKSPACE}, {BS}, or {BKSP} |
| BREAK | {BREAK} |
| CAPS LOCK | {CAPSLOCK} |
| DEL or DELETE | {DELETE} or {DEL} |
| DOWN ARROW | {DOWN} |
| END | {END} |
| ENTER | {ENTER}or ~ |
| ESC | {ESC} |
| HELP | {HELP} |
| HOME | {HOME} |
| INS or INSERT | {INSERT} or {INS} |
| LEFT ARROW | {LEFT} |
| NUM LOCK | {NUMLOCK} |
| PAGE DOWN | {PGDN} |
| PAGE UP | {PGUP} |
| PRINT SCREEN | {PRTSC} (reserved for future use) |
| RIGHT ARROW | {RIGHT} |
| SCROLL LOCK | {SCROLLLOCK} |
| TAB | {TAB} |
| UP ARROW | {UP} |
| F1 | {F1} |
| F2 | {F2} |
| F3 | {F3} |
| F4 | {F4} |
| F5 | {F5} |
| F6 | {F6} |
| F7 | {F7} |
| F8 | {F8} |
| F9 | {F9} |
| F10 | {F10} |
| F11 | {F11} |
| F12 | {F12} |
| F13 | {F13} |
| F14 | {F14} |
| F15 | {F15} |
| F16 | {F16} |
| Keypad add | {ADD} |
| Keypad subtract | {SUBTRACT} |
| Keypad multiply | {MULTIPLY} |
| Keypad divide | {DIVIDE} |
To specify keys combined with any combination of the SHIFT, CTRL, and ALT keys, precede the key code with one or more of the following codes:
-
SHIFT +
-
CTRL ^
-
ALT %
To specify that any combination of SHIFT, CTRL, and ALT should be held down while several other keys are pressed, enclose the code for those keys in parentheses. For example, to specify to hold down SHIFT while E and C are pressed, use "+(EC)." To specify to hold down SHIFT while E is pressed, followed by C without SHIFT, use "+EC."
To specify repeating keys, use the form {key number}. You must put a space between key and number. For example, {LEFT 42} means press the LEFT ARROW key 42 times; {h 10} means press H 10 times.
Note:
In addition to the above SendKeys, there is also a wait command. The wait command is in the format {WAIT number} where "number" is the number of milliseconds delay. The wait can be anywhere in the string (that is, beginning, middle, end} and can be used as many times as needed.For example, if you want to send Ctrl+Shift+F7, then wait for 5 seconds, and then send Alt+F4, the format should be as follows:
^+{F7}{WAIT 5000}%{F4}
© 2001-2002 Microsoft Corporation. All rights reserved.
2.19.1.8 Creating and Using Run Lists
Use this panel to define either a .NET API to call or a script of command lines to be executed by Kiosk Manager.
-
Expand the Kiosk Manager node and select Actions.
-
Select a Run list.
| Setting | Control | Function |
|---|---|---|
| .NET API | Assembly | Click the ellipsis "…" button to locate the .NET assembly to use. The assembly loads. |
| Class | Select a .NET class using the drop-down box. The .NET classes listed will be those that are available in the selected assembly. |
|
| Method | Select a method to call using the drop-down box. The .NET methods listed will be those that are available in the selected class. The method will be limited to the following signature and will not take any parameters or return any values:
Unlike the script, processing will not continue until the method returns. |
|
| See The .NET API for an example of a command line script.
Note: |
||
| Script | Enter a command line script for Kiosk Manager to execute. If this list contains multiple commands, each line starts without waiting for the previous task to terminate or checking the previous task's return code.
Note: Command line calls are asynchronous (run in parallel to other tasks, including Kiosk Manager). |
|
| Disabled | Select this checkbox to disable this list. Disabling a list allows you to retain the settings in a list without deleting the original list, allowing you to refer to the settings and use them with other lists. | |
2.19.1.9 Creating and Using Special Actions Lists
Special action lists are used to specify how to handle application windows, such as the positioning of the application and the order that this application has these actions performed on it.
If an application window does not appear in a special actions list, it will be hidden.
To display this tab:
-
Expand the Kiosk Manager node and select Actions.
-
Click on any Special Actions list.
| Control | Function |
|---|---|
| AppPathKeys | The Windows registry key identifying an application associated with this logon to match against running processes. (Usually the application executable's name, such as Notepad.exe.) |
| Window Titles | Text matched against logon window titles to identify logon requests. |
| Reposition Application | This setting and those below it allow you to specify the position of the application.The state of this checkbox determines if the actions listed below it will be applied to the application window.
Options:
|
| Sort Order | This setting determines the order in which special actions are executed. This ensures that windows which are brought to the foreground can be in a specific order with a preferred window displayed on top when multiple windows are repositioned. |
| Bring to foreground | This setting ensures that the application window is always first in the application windows order. |
| Shared Application | Check this box to enable an application to be shared among user sessions. For example, if "Notepad.exe" is designated as a shared application, if user1 opens a document in notepad and then locks the session, notepad will be running when user2 starts a session. If user2 then closes notepad and locks the session, notepad will no longer be running when user1 logs back on. |
| Disabled | Select this checkbox to disable this list. Disabling a list allows you to retain the settings in a list without deleting the original list, allowing you to refer to the settings and use them with other lists. |
To configure an application:
-
Under the AppPath Keys box, click Add. The Process Path Key dialog displays.
-
Enter a valid application key (usually the application executable's name, such as Notepad.exe). Click OK.
-
The application has been added to the list of applications to close on session end. Kiosk Manager will terminate these applications when a session ends.
-
Use the Edit and Delete buttons to modify or remove applications from this list.
-
In the Window Titles box, click Add. The Windows Title dialog appears.
-
Enter a valid windows title. Click OK.
To specify a window title for matching
-
Enter (or edit) the exact Window Title.
-
Click OK.
2.19.1.10 Adding Applications with Process Path Keys
The Process Path Key is the name of the process executable; for example, IEXPLORE.EXE is the process path key for Internet Explorer. Use this dialog to add an application to the list of applications.
-
Enter a Process Path Key and click OK.
The Process Path Key is then created in the AppPath Keys dialog.
To display this tab:
-
In the left pane, click Kiosk Manager > Actions.
-
Click either:
-
Terminate list
-
Special Actions list
-
-
Click Add.
2.19.1.11 Selecting Default Applications to Leave Running
Use this dialog to add default applications to the list of applications to keep running on session end.
-
Select the desired applications to keep running on session end and click OK.
The selected applications are then listed in the AppPath Keys dialog.
To display this tab:
-
In the left pane, click Kiosk Manager.
-
Click Actions.
-
Select a Keep running list.
-
Click Defaults.
2.19.2 Session States
The Session States panel contains the list of existing Session States. Session States are a list of events to associate with an action. For example, a defined Session State might tell Kiosk Manager to perform a specific list of actions when a session ends.
2.19.2.1 Creating a Session State
To create a session state:
-
Open the Administrative Console.
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Click Add or right-click and select New Session State.
-
Type a Session State Name and click OK.
-
The new Session State is created. Each Session State has four tabs associated with it:
-
Events
-
Authenticators
-
Actions
-
Security
-
2.19.2.2 Copying a Session State
To copy a Session State:
-
Select a Session State.
-
Right-click Make Copy to quickly make a copy of this Session State. To change the name, right-click the Session State in the left pane and click Rename. You can also perform a copy by right-clicking the Session State in the left pane and clicking Copy.
2.19.2.3 Deleting a Session State
To delete a Session State:
-
Click Delete to delete a Session State. A confirmation message appears before the Session State is deleted.
-
Expand the Kiosk Manager node.
-
Right-click the Session State that you want to delete. Then either:
-
From the context menu, select Delete.
or
-
From the context menu, select Edit, then select Delete.
-
2.19.2.4 Selecting Session State Events
The Events tab contains a list of all the possible events that Kiosk Manager can respond to and the option to add custom events. Each listed event has a checkbox next to it that when checked indicates that the associated action lists should be executed when this event occurs. When a new Session State is created, Session End is checked by default.
To display this tab:
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Create an event in one of the following ways:
-
Select the predefined events for this Session State.
or
-
Create your own custom events by clicking the Add button. Use the Edit button to edit the custom event name and the Delete button to delete a custom event.
The following figure contains a list of the pre-defined events available to you.
-
2.19.2.5 Selecting a Predefined Event
From the Events tab, select from:
-
After Session Unlocked
This event runs when the user unlocks their session after authentication has taken place. If an authentication is canceled, this event will not be triggered.
-
AM Device In
This event is triggered when the SSO device monitor is enabled and detects a monitored authenticator (for example, a smart card is inserted or a biometrics device is in range).
-
AM Device Out
This event is triggered when the SSO device monitor is enabled and detects a monitored authenticator (for example, a smart card is removed or a biometric goes out of range). This event will only be triggered when:
-
A session is open or locked
-
A "Device-In" event started the session
-
-
AM Grace Period
This event is triggered if an authenticator which uses a grace period function is being used and a user returns to an open session within the grace period.
-
Authenticator Logon
This event is triggered when an authenticator has accepted a logon. For example, the correct password for WinAuth or the correct PIN for smart card is entered.
-
Authenticator Timeout
This event is triggered when Logon Manager's internal timer has expired.
-
Before Session Unlocked
This event is triggered when a user unlocks a session before authentication takes place.
-
Cached Credential Session Start
This event is triggered when a session is started and the user has cached credentials stored on the local computer.
-
Session End
This event is triggered when the session ends and the timer expires, or when another user starts a session.
-
Session Locked
This event is triggered when a user manually locks the session via the system tray.
-
Session Start
This event is triggered when a user starts a new session.
-
Time Expired
This event is triggered when the locked session timer has reached 00:00:00.
-
Transparent Screen Displayed
This event is triggered when the transparent lock initiates and the screen is visible to the user in locked mode.
-
Transparent Screen Hidden
This event is triggered when the transparent lock is ending.
-
User Change
This event is triggered when a user logs on to Kiosk Manager. This event sets two properties on the .NET object if they exist:
-
UserName. The sync user name.
-
DomainName. The sync domain name.
If the properties do not exist, nothing happens
-
Note:
Authentication Manager events run when the authenticator sends a message to Kiosk Manager indicating the event type.2.19.2.6 Adding a Custom Event
To add a custom event, click the Add button on the Events tab. The Custom Event dialog appears:
-
Enter an Event Name. This is the event name that displays.
-
Enter an Event Value. An external application generates the custom event, sending a message to the Kiosk Manager hidden window. The value is the custom value that the other application sends.
-
Click OK. The custom event is created.
2.19.2.7 Selecting a Session State Authenticator
The Authenticators tab contains a list of all the authenticators that Logon Manager supports as well as the option to add a custom authenticator. Each authenticator has a checkbox next to it that when checked indicates if the associated action lists should be executed when the selected events occur and the selected authenticator was used to authenticate the user.
When a new Session State is created, all authenticators are checked by default.
There are two ways to select authenticators:
-
Create your own custom authenticator by clicking the Add button. Use the Edit button to edit the custom event authenticator and the Delete button to delete a custom authenticator.
-
Select the pre-defined authenticator for this Session State. Available authenticators are:
-
Authentication Manager
-
Entrust
-
ESSO-UAM: Challenge Questions
-
ESSO-UAM: Fingerprint
-
ESSO-UAM: Proximity Card
-
ESSO-UAM: Smart Card
-
ESSO-UAM: Windows Password
-
LDAP
-
LDAP v2
-
Proximity Card
-
Read-Only Smart Card
-
SecurID
-
Smart Card
-
Universal Authentication Manager
-
Windows Logon (deprecated)
-
Windows Logon v2
Note:
To configure Kiosk Manager to use the Universal Authentication Manager authenticator, you must set Kiosk Manager to broadcast/monitor for token events. To do this, set the following registry key to a value of 2 (Always):HKEY_LOCAL_MACHINE\SOFTWARE\Passlogix\SM\Agent -
To display this tab:
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Select a Session State and click the Authenticators tab.
2.19.2.8 Adding a Custom Authenticator
Custom authenticators allow you to filter events based on that authenticator. To add a custom authenticator, click the Add button on the Authenticators tab. This opens the Custom Authenticator dialog:
-
Enter an Authenticator Name. This is the authenticator name that displays.
-
Enter an Authenticator Value. The authenticator value is the name that the authenticator is known by within the code. This name comes from the authenticator itself. For example, the value for Windows Authenticator v2 is MSAuth and for Smart Card is SCAuth.
-
Click OK.
To display this dialog:
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Select a Session State and click the Authenticators tab.
-
Click Add.
2.19.2.9 Using the Actions Tab to Add Session States
The Actions tab contains a list of all the actions associated with a specific Session State. This panel is empty for newly-created Session States. After you associate actions with the Session State, the actions appear in this panel.
Use this panel to create, associate, edit and delete actions.

To display this tab:
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Select a Session State and click the Actions tab.
To use the Actions tab:
-
To define a new action list, click Add. There are two types of action lists: Terminate lists and Run lists. A new action that you create from this panel is automatically added to this session state.
-
To associate a defined action with this Session State, click Associate and select an action from the list.
-
To make changes to an action, highlight it and click Edit.
-
To delete an action from a Session State, click Delete. This deletes the action only from the current Session State, not the actions list.
2.19.2.10 Associating Actions to a Session State
Use the Select Actions dialog to select one or more actions to associate to this Session State.
Select the actions to add to this Session State (use Ctrl+Click or Shift+Click to select multiple entries). Click OK.
Note:
If actions are associated with this Session State and you are adding new actions, you must reselect ALL actions; otherwise the previous list of actions will be replaced with the newly-selected actions.To display this tab:
-
In the left pane, click Kiosk Manager.
-
Click Session States.
-
Select a session state and click the Actions tab.
-
Click Associate.
2.19.2.11 Configuring Session State Security
Use the Security tab to set the access rights for this Session State. You can assign access rights to these items:
-
Application logons (including associated credential sharing groups)
-
Password generation policies
-
Global Agent settings
-
Passphrase question sets
Note:
The security tab is available only if Role/Group security is enabled.
| Control | Function |
|---|---|
| Directory | Select the target directory server. |
| Access information | |
| Name | Lists the groups or users who currently have access to this Session State. |
| ID | The user account name. |
| Access | Indicates whether the user or group has read/write or read-only access rights to the currently selected Session State. To change a user or group's access rights, right-click the user or group and select Read or Read/Write from the shortcut menu. |
| Action | |
| Add | Displays the Add User or Group dialog (for LDAP or Active Directory) to select the users or groups who should have access to the currently selected Session State. |
| Remove | Removes selected user(s) or group(s) from the list. Select a user or group to remove; use Ctrl+Click or Shift+Click to select multiple entries. |
To display this tab:
-
Expand the Kiosk Manager node.
-
Click Session States.
-
Select a Session State and click the Security tab.
2.19.3 About Desktop Manager
The Desktop Manager is the logon dialog that manages the Kiosk Manager sessions on the kiosk. End users can start and unlock sessions from this dialog. Administrators can terminate sessions, shut down the computer, restart the computer, and exit Kiosk Manager.
Note:
The Desktop Manager is configured through the Administrative Console under Global Agent Settings > Kiosk Manager. The following sections contain all the necessary information to configure these settings.2.19.3.1 Administration Menu
The Administration menu is located on the top of the Desktop Manager.
The settings that are used to configure this menu are:
-
Restart Computer
Options are Yes, No, or Administrator must supply password. Default is No.
-
Shutdown Computer
Options are Yes, No, or Administrator must supply password. Default is No.
-
Allow administrator to close Kiosk Manager
Options are Yes or No. Default is Yes. This setting controls the Exit Kiosk Manager option and the X in the title bar.
Note:
If the Kiosk account does not have sufficient privileges, the Restart Computer and Shutdown Computer options may not work even if they are disabled.2.19.3.2 Session Termination
In addition to providing an administrator with rights to close sessions, there are other session termination settings you can configure. For information about configuring these settings, see Global Agent Kiosk Manager Settings.
2.19.3.3 Open Sessions (Multi-Sessions)
The Desktop Manager includes a list that displays all open sessions. Multiple sessions can be running at one time. There is no maximum amount of sessions. For information about configuring these settings, see Global Agent Kiosk Manager Settings.
2.19.3.4 Transparent Screen Lock
The transparent lock feature provides the ability to lock desktop inputs (keyboard and mouse) in view mode, so for example, a monitoring application can be viewed without starting a session. It is similar to the screen saver functionality. When Kiosk Manager invokes the transparent lock, the desktop and applications on the desktop continue to display on the monitor in real time. Transparent lock is disabled by default.
When there are multiple sessions running, the last active session is displayed when transparent lock engages.
Application priorities and positioning are configurable in the Special Actions lists.
Transparent lock events are set up in the Events panel of the Session States section.
-
Transparent Screen Displayed
This event is triggered when the transparent lock initiates and the screen is visible to the user in locked mode.
-
Transparent Screen Hidden
This event is triggered when the transparent lock is hidden.
Transparent lock can be invoked in the following ways:
-
Timeout
-
Canceling out of an authentication ONLY if Transparent Display After Cancel is set to Enable.
To initiate a session while transparent lock is running, move the mouse or click any keyboard button. If Transparent Only Recognize Ctrl-Alt-Delete is set to Enable, users will have to click Ctrl+Alt+Delete to disengage Transparent Lock.
Note:
Transparent screen lock is configured through the Administrative Console on the Global Agent Settings > Kiosk Manager > User Interface panel.2.19.3.5 Terminating Sessions
Administrators can terminate Kiosk Manager user sessions from the Desktop Manager by clicking Terminate Sessions from the Administration menu. This menu option is not configurable.
When you click Terminate Sessions, the Authenticate as Administrator dialog appears, prompting you to enter administrative credentials before performing this action.
After you submit your credentials, the Terminate Sessions dialog appears.
You can select only one session at a time. Select Cancel and use the X to close this dialog.
2.19.3.6 Customizing the Desktop Manager
The Desktop Manager can be customized in several ways. Refer to the following sections for more information about each option.
-
General Custom User Interface Options. See Global Agent Settings Kiosk Manager User Interface.
-
Upload a background image around the logon dialog. See Setting the Kiosk Manager Background Image.
-
Add a custom text message around the logon dialog. See Global Agent Kiosk Manager Message Settings.
-
Replace the Oracle and Kiosk Manager logo banner on the logon dialog. You may choose to display a company logo as the background image, or an important custom text message to inform your users of any important information. See Replacing the Logo Banner.
The information in the following section provides instructions to replace the logon dialog logo banner and an example of a customized desktop.
2.19.3.6.1 Replacing the Logo Banner
You can modify the Oracle Kiosk Manager logo banner on the Desktop Manager logon dialog through a manual step. To replace the logo:
-
Create a
brandingfolder within theSMAgent.exehome directory. -
Place the customized logo banner in the branding folder with the name
banner.gif. -
The customized banner appears the next time you start Kiosk Manager.
2.19.3.6.2 Examples of a Customized Background Image and Text Message
Customized Background Image on an 800x600 Display
The following screen shot illustrates the horizontal and vertical dimension of the Desktop Manager logon dialog and the coordinates and dimensions used to position it.
Customized Text Message on an 800x600 Display
The following screen shot illustrates an example of a text message. This text message displays the values used to customize the text message as seen in this screen shot.
The following screen shot displays the actual values used to produce the text message as seen above.
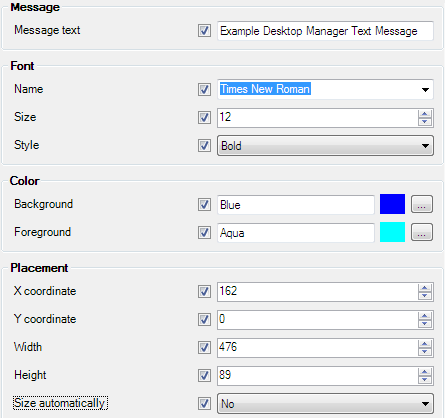
2.19.3.7 Desktop Status Window
The Desktop Status window is a small window that displays during a Kiosk Manager session. It allows you to conveniently view the current session owner and lock the session. If enabled, its default location is the upper right corner of the desktop during a session.
The Desktop Status window is hidden by default. The default values are calculated at runtime. The window is placed in the upper-right hand corner of the display with 10 pixels between the edge of the window and the physical edge of the screen. See Global Agent Settings Kiosk Manager User Interface for instructions to customize this window's appearance and location.
2.19.4 Event and Audit Logs
Kiosk Manager logs agent events to the local machine's Windows Event Viewer. This functionality is enabled by default. For a list of Kiosk Manager events that you can log, see Event Log Messages.
Kiosk Manager can also log events to a Syslog server application on the local kiosk machine or a remote machine.
To configure Syslog through the Agent installer:
Note:
This step must be performed before installing Kiosk Manager.-
Launch Add-Remove Programs from the Control Panel.
-
Click on Oracle Enterprise Single Sign-On Logon Manager and click Change.
-
Select Modify on the Program Maintenance panel.
-
On the Custom Setup panel, expand Extensions, and then expand Event Manager.
-
Select Syslog for installation.
-
Follow the prompts to complete installation of Syslog.
To configure Syslog through the Administrative Console:
-
Open the Administrative Console, expand Global Agent Settings > Audit Logging > Syslog Server.
-
Configure the settings for the target Syslog machine according to your environment. If logging to a remote machine, specify either a hostname or IP address of the remote machine in the Destination Host setting.
-
Navigate to Global Agent Settings > Kiosk Manager. Under the Audit Logging section, enter the Event log name and Event log machine name.
2.19.4.1 Event Log Messages
The following table lists the messages that currently are logged in the Event Viewer for applications:
| Message | Notes About Message (if Applicable) |
|---|---|
| User session started: domain/username | When a user session is started. |
| User session ended: domain/username | When a user session ends. |
| User session locked: domain/username | When a session is locked. |
| User session unlocked: domain/username | When a session is unlocked. |
| Process action: action type, action name | (IE, Terminate list, notepad_close)
This corresponds to the session actions in the repository. If the action does not have a corresponding state that triggers, you should not see the action logged in the event viewer. |
| Process state: state name, event GUID | (IE, Session_locked, {6D5B7645-25A5-42f3-B641-BFE4DC4F774C})
This corresponds to the Session States in the repository. A log entry is only generated if a state is triggered, such as a session lock. The GUID corresponds to the GUID for that state, if you viewed the state from the Administrative Console. For example, if you have a state in the repository for Transparent Lock but you do not have Transparent lock turned on, you should not see an event logged. |
| Transparent lock screen DISPLAYED | When transparent lock displays. |
| Transparent lock screen HIDDEN | When transparent lock is hidden. |
| Method Invocation: file path/file name, method name | Corresponds with Run List .Net API Assembly name and method. |
| Run list command: command name | Corresponds with Run List Script commands. |
| The following applications were not terminated: | This will only log applications that are specified in a terminate list and did not terminate. |
| Kiosk Manager STARTED | When Kiosk Manager is started. |
| Kiosk Manager SHUTDOWN | When Kiosk Manager is shut down. |
| Successfully closed: Application name | Applicable to all three closure methods in the terminate list—keystroke sequence, closure request, and process termination.
This event is logged when the application in a terminate list is closed. Logs are not generated for applications that are closed but not specified in a terminate list. |
2.19.4.2 Bypassing the Kiosk Manager Agent
If necessary, you can bypass the Kiosk Manager Agent when a kiosk starts up.
The Kiosk Manager Agent will not start if you hold the Shift key down when logging into the computer.
2.19.4.3 Closing the Kiosk Manager Agent
If necessary, the Kiosk Manager Agent can be closed on a kiosk by:
-
Pressing ALT + F4 on the keyboard.
-
Clicking Exit Kiosk Manager from the Administration menu on the Desktop Manager.
-
Clicking the X located on the top right of the window title bar.
The administrator is then prompted to enter his or her credentials. Only an administrator's credentials will succeed in closing the agent.
This feature is disabled by default. To enable this feature:
-
Open the Logon Manager Administrative Console, expand Global Agent Settings > Kiosk Manager.
-
Check Allow administrator to close Kiosk Manager.
-
Select Yes.
2.19.4.4 Setting Up a Trust
Kiosk Manager has the capability to allow other applications that trust Kiosk Manager authentication to retrieve the logged-on username. Kiosk Manager provides a public function in SSOUserInfo.dll with the following function signature:
extern "C" BOOL _stdcall GetUserId(BSTR* bstr);
Parameters:
bstr
Object into which to retrieve the username.
Return Value
Returns TRUE if the function succeeds and a user is currently logged in.
Returns FALSE if the function fails. Use GetLastError() for more information.
If the function succeeds, the username will be returned as: "DomainName\UserName"
Note:
Kiosk Manager can be set up to run a command line or call a.NET method after a user successfully starts a session. Utilize this mechanism to trigger the other application to request the logged-on username from Kiosk Manager.2.19.4.5 Using the MacListener Utility to Enable Caregiver Mobility and Oracle VDI Session Support
The MacListener utility enables Kiosk Manager to interface with Caregiver Mobility and Oracle VDI environments, allowing health-care professionals to log on to kiosk systems to access location-specific information, such as patient data or other local resources pertinent to the kiosk system's location. MacListener.exe ships with Oracle Enterprise Single Sign-On Suite and is located in the "Utility" sub-folder of the "Logon Manager" folder of the suite master archive.
MacListener.exe is a command-line utility that emulates the echo server by listening on a specific TCP/IP port for incoming client connections, receiving the client's MAC address in plain-text form, and running a specified command when a client disconnects with the client's MAC address appended to the end of the specified command in the following format:
/MACADDRESS=xx:xx:xx:xx:xx:xx
where xx:xx:xx:xx:xx:xx is the client's MAC address.
The syntax for using the MacListener.exe utility is as follows:
| Parameter | Description |
|---|---|
/PORT <port_number> |
Specifies the port number on which to listen for incoming client connections. |
/DEBUG |
Displays error messages. |
/E <command> |
Command to execute upon client disconnection. The MAC address received from the client will be appended to the end of the command in the format that follows. |
For example, if you launch the utility as follows:
MacListener /PORT=8080 /E=C:\Windows\Notepad.exe
and a client with a MAC address of 12:AB:34:CD:56:EF connects to the utility on port 8080, then the utility will execute the following command when the client disconnects:
C:\Windows\Notepad.exe /MACADDRESS=12:AB:34:CD:56:EF
2.19.5 Configuring Strong Authentication Options
The Administrative Console's Global Agent Settings > Kiosk Manager: Strong authenticator options allow you to configure how Kiosk Manager integrates with strong authenticators.
See Global Agent Kiosk Manager Settings for strong authentication options, and the Universal Authentication Manager section, Integrating with Kiosk Manager, for detailed information on integrating Kiosk Manager with Universal Authentication Manager.
2.19.6 Linking to Password Reset
You can add a link to Password Reset on the Kiosk Manager Desktop Manager. This allows users to reset their own kiosk passwords (for example, Microsoft Active Directory via LDAP authentication) using Password Reset.
Clicking this banner launches the Password Reset Web interface. Users can then follow the prompts to reset their password.
A link to the Password Reset client can be installed as a DOS command, using the following command syntax:
msiexec /i [/q] c:\ESSO Kiosk Manager 7.000.msi programURLs
/q Quiet mode: suppress all installer user-interface messages. Refer to the description of other Windows Installer command-line options for msiexec at http://msdn.microsoft.com.
programURLs (required):
REG_RESETURL=" http://host/vgoselfservicereset/resetclient/default.aspx"
REG_STATUSURL="http://host /vgoselfservicereset/resetclient/checkstatus.aspx"
where: host is the server name (or domain name or IP address) and path of the folder that holds the Password Reset service root folder.
2.19.7 Command Line Options
Command-line options are available to support non-kiosk environments and allow Kiosk Manager to run on a desktop machine without presenting a user interface.
/EVENT <EventName1> [EventName2…]
This option triggers the named event and Kiosk Manager performs the tasks associated with the event and terminates. The authenticator filters are ignored.
/RUN <ListName1> [ListName2…]
This option triggers Kiosk Manager to perform the tasks associated with the named list and terminate. The event and authenticator filters are ignored.
ListName can be either a Session State or an Action.
For example, "SMAgent/run StartVisualSourceSafe"
Some things to keep in mind when using the command line:
-
Any
SessionActionorSessionStatenames that have spaces in them must be enclosed in double quotes. -
Some command-line options prevent others from working. For example, multiple lists can be run with the
/RUNcommand. If/LOCKappears on the command line, the session is locked and the rest of the command line is ignored, including any options that appeared before/LOCK. -
/SHUTDOWN,/LOCK, and/TERMare the command-line options that cause Kiosk Manager to ignore the rest of the command line. -
The
/RUNand/EVENTcommands trigger Kiosk Manager to treat the rest of the command line as event and list names to be run. These will be run when all of the command line options have finished processing. The type of the parameter depends on the previous command. The command-line parameter type resets with the next/EVENTor/RUNparameter received. For example:SMAgent /Event "SM session start" "SM session end" /RUN termlist1 termlist2 runlistA "My SessionState"This command line will run the lists associated with events
"SM session start" "SM session end"and run the named lists:termlist1,termlist2,runlistAand"My SessionState".
2.19.8 The .NET API
Externally Callable Interfaces and Methods
A class named KioskAPI is available within the SMAgent.exe that is loaded by external programs.
The object is instantiated as follows:
Passlogix.SM.Manager.KioskAPI kiosk = newPasslogix.SM.Manager.KioskAPI();
The following methods are available:
void Lock();void Term();void Shutdown();void Event(string eventName);void Run(string runtaskName);
-
Lock. Locks the current Kiosk Manager session.
-
Term. Ends the user's session as if the Kiosk Manager timer expired for a user.
-
Shutdown. Terminates the
SMAgent.exe. -
Event. Simulates the named event to occur, causing Kiosk Manager to perform tasks associated with the named event without filtering by the authenticator. Event names are the
GUIDstrings fromEvents.xml. -
Run. Starts the named task without filtering by the event or authenticator. Task names are the SessionAction and SessionState names that are displayed by the Administrative Console.
Note:
Any SessionAction or SessionState names that have spaces in them must be enclosed in double quotes:kiosk.Run("\"My SessionAction\"");
Example to run tasks associated with the "SM Session End" event:
Passlogix.SM.Manager.KioskAPI kiosk = new
Passlogix.SM.Manager.KioskAPI();
if (kiosk != null)
kiosk.Event("{A644ED55-6A3F-4160-A355-C713C90733DF}");
Note:
Also see the .NET API Sample Code.2.19.8.1 .NET API Sample Code
Following is sample code for the .NET API using C# with properties for the "User Change" event.
using System;
using System.Collections.Generic;
using System.Text;
using System.Windows.Forms;
namespace ClassLibraryTest
{
public class TestClass
{
private string m_userName;
private string m_domainName;
public string UserName
{
set
{
m_userName = value;
}
get
{
return m_userName;
}
}
public string DomainName
{
set
{
m_domainName = value;
}
get
{
return m_domainName;
}
}
public void UserChange()
{
MessageBox.Show("UserChange called with user: " + DomainName + "\\" + UserName);
}
public void SessionStart()
{
MessageBox.Show("SessionStart called");
}
public void SessionEnd()
{
MessageBox.Show("SessionEnd called");
}
public void SessionLocked()
{
MessageBox.Show("SessionLocked called");
}
public void SessionUnlocked()
{
MessageBox.Show("SessionUnlocked called");
}
public void PreSessionUnlocked()
{
MessageBox.Show("PreSessionUnlocked called");
}
public void AuthLogon()
{
MessageBox.Show("AuthLogon called");
}
public void AuthTimeout()
{
MessageBox.Show("AuthTimeout called");
}
public void DeviceIn()
{
MessageBox.Show("DeviceIn called");
}
public void DeviceOut()
{
MessageBox.Show("DeviceOut called");
}
public void GracePeriod()
{
MessageBox.Show("GracePeriod called");
}
}
}
2.19.9 Kiosk Manager Best Practices
These best practices are recommendations that will help you implement an optimal Kiosk Manager configuration.
2.19.9.1 Deploying Kiosk Manager Settings
The most convenient way to mass deploy Kiosk Manager settings from the Administrative Console is to create a customized MSI package and distribute it to end user kiosk workstations using a deployment tool of your choice.
Note:
Administrative Overrides are not available for use with Kiosk Manager settings.2.19.9.2 SendKeys
SendKeys is not a reliable method and therefore not guaranteed to work as expected. It is recommended that you do not use SendKeys.
2.19.9.3 Disable Task Manager and Run
The Windows Task Manager and Run menu option are disabled programmatically as a function of the Kiosk Manager Registry Service. For added security, we recommend disabling these functions for any user account that you plan to use with a Kiosk Manager kiosk user account.
To remove the Run menu option from the Start menu:
-
Open the Group Policy editor by double clicking on
gpedit.msc(C:\WINNT\system32\gpedit.msc) -
Navigate to User Configuration > Administrative Templates > Start Menu and Toolbar.
-
In the right pane double-click Remove Run from the Start menu.
-
Select Enabled and click Apply and OK.
To disable Task Manager:
-
Open the Group Policy editor by double clicking on
gpedit.msc(C:\WINNT\system32\gpedit.msc) -
Navigate to User Configuration > Administrative Templates > System > Ctrl+Alt+Delete Options.
-
In the right pane double-click Remove Task Manager.
-
Select Enabled and click Apply and OK.
2.20 Provisioning Gateway Overview
Provisioning Gateway provides the ability to remotely add, modify, and delete application credentials directly within each user's Logon Manager credential store, eliminating the need for local credential capture and granting the user instant access to the target application. The Universal Authentication Manager Management Console is a standalone, browser-based application. See the separate guide, Administering Oracle Enterprise Single Sign-On Provisioning Gateway for instructions to configure and use this component.
You can configure provisioning in the following ways:
-
From the Provisioning node of the Administrative Console, define provisioning rights for each new application you create.
-
From the Provisioning tab of a selected application, add or remove rights, and copy rights to other applications.
To access the Provisioning Gateway Administrative Console, open a Web browser and enter this URL (replacing serverhost with the server where Provisioning Gateway was installed):
https://serverhost/Provisioning Gateway console/overview.aspx
2.20.1 Managing Provisioning
Use this node to manage provisioning rights for users. There are two tabs to set the rights:
-
Default Rights
-
Admin Rights
When you change the settings in this node, you must publish them to the repository in order for them to take effect. Right-click the node and select Publish.
2.20.1.1 Provisioning Default Rights Tab
Use this tab to define standard provisioning rights for each new application created. After you create an application, change the rights as needed.
| Control | Function |
|---|---|
| Directory | Select the target directory server. |
| Access information: | |
| Name | Lists the groups or users who currently have access to this item. |
| ID | Lists the user account name. |
| Access | Indicates the permissions that have been granted to the user or group (Add, Modify or Delete Logon). To change a user or group's access rights, right-click the user or group and select Add Logon, Modify Logon, or Delete Logon from the shortcut menu. |
| Actions: | |
| Copy permissions to… | Use this button to apply the provisioning rights for the current application to multiple applications. Click to display a list of all available applications, and select those to which you want to copy these provisioning rights. Use Ctrl+Click or Shift+Click to select multiple entries. Click OK. |
| Add | Displays the Add User or Group dialog (for LDAP or Active Directory) to select the users or groups to grant access to the currently selected item. |
| Remove | Removes selected user(s) or group(s) from the list. Select a user or group to remove; use Ctrl+Click or Shift+Click to select multiple entries. |
| Directory | Select the target directory server. |
2.20.1.2 Add User or Group Dialog
The Add User or Group dialog varies based on the directory server being used:
2.20.1.2.1 LDAP
Use this dialog to select the individual users or user groups that are to be added to the access list for the current configuration item (Add Logon, Modify Logon, or Delete Logon).
| Control | Function |
|---|---|
| Search Base | The base (highest-level) directory to begin searching for user/group accounts. All subdirectories of the base directory are searched. Type a location or click Change to browse the directory tree. |
| Change | Displays the Select Search Base dialog to browse for a base directory for the search. Use this dialog to browse to and select the base (highest-level) directory to search for user/group names. Click OK when finished. |
| Search | Begin searching the base directory for users and groups. |
| Users or Groups | Lists the search results. Select the names to be added to the access list for the current configuration item. Use Ctrl+Click or Shift+Click to select multiple entries. Click OK when finished to copy your selections to the access list. |
2.20.1.2.2 Active Directory/AD LDS (ADAM)
Use this dialog to select the individual users or user groups that are to be added to the access list for the current configuration item (Add Logon, Modify Logon, or Delete Logon).
| Control | Function |
|---|---|
| List Names From | Select an Active Directory domain or server. |
| Names | Lists the names of users and groups for the selected domain or server. Select one or more names to add to the access list. |
| Add | Copies user(s) and group(s) selected in the Names list to the Add Names list. Use Ctrl+Click or Shift+Click to select multiple entries. |
| Members | When a group is selected in the Names list, displays the Global Group Membership dialog, which lists the members of the selected group. |
| Search | Displays the Find Account dialog for searching one or more domains for a specific user or group. |
| Add Names | Displays the names of the user(s) or group(s) you have selected for addition to the access list for the current configuration item. Click OK to finalize the addition.
Note: You can type or edit user names in this list. However, entries are checked for invalid account names, and duplicate account selections are automatically removed when you click OK. |
2.20.1.3 Provisioning Admin Rights Tab
Use this tab to grant the user general administrative rights to the Provisioning Gateway Administrative Console.
| Control | Function |
|---|---|
| Directory | Select the target directory server. |
| Access information: | |
| Name | Lists the groups or users who currently have access to this item. |
| ID | Lists the user account name. |
| Access | Indicates the administrative rights that have been granted to the user or group (Delete SSO User or Map Templates). To change a user's or group's access rights, right-click the user or group and select Delete SSO User or Map Templates from the shortcut menu. |
| Actions: | |
| Copy permissions to… | Use this button to apply the provisioning rights for the current application to multiple applications. Click to display a list of all available applications, and select those to which you want to copy these provisioning rights. Use Ctrl+Click or Shift+Click to select multiple entries. Click OK. |
| Add | Displays the Add User or Group dialog (for LDAP or Active Directory) to select the users or groups to grant access to the currently selected item. |
| Remove | Removes selected user(s) or group(s) from the list. Select a user or group to remove; use Ctrl+Click or Shift+Click to select multiple entries. |
| Right-clicking on a server name in the list opens a context menu that allows you to perform any of the following: | |
| Remove | Removes the server from the Server list. |
| Publish… | Launches the Publish to Repository dialog, which allows you to choose from several objects and locations to publish. |
| Publish To | Allows you to select a single repository directly from the menu item; publishing occurs automatically after you select the repository. |
| Delete SSO User | Rescinds a user's access to an OPAM-enabled account. |
| Map Templates | Allows an administrator to map SSO templates to OPAM targets. Right-click on a user in the list, and select Map Templates from the context menu to grant the user mapping permissions. |
2.20.2 Oracle Privileged Accounts Manager (OPAM)
The OPAM tab contains a root node that allows you to connect to an OPAM server and a target repository. The server contains OPAM targets, and the repository contains Logon Manager templates and the mapping object.
Note:
If Logon Manager is synchronizing to an Active Directory repository and is using the "local computer credentials" option, you must enable sharing credentials from the authenticator to the Active Directory synchronization extension ("ShareCredsToSyncs") in the Global Agent Settings.To configure the Administrative Console support for OPAM:
-
Enter the URL of the server that contains OPAM targets. If you've previously entered URLs in this field, they will be available to select from the dropdown list.
-
Enter your Username and Password.
-
Select the target repository:
-
Click the Browse… button.
-
In the Connect to Repository dialog, enter the server name, select a repository type, enter the port number, your username, and password. Check the box if this is an SSL connection. Then click Apply.
-
In the Browse for Repository dialog, expand the desired DC node under the server, and select OU-SSO. This is where the ESSO configuration objects (COs) and mapping objects are stored. Click OK when done.
Note:
If the mapping object does not already exist, it will be created here.
-
-
Click Apply. The plug-in initiates an attempt to connect to the OPAM server and target repository.
-
When connection is successful, a Template Mapping node appears in the left navigation pane under OPAM.
When you select Template Mapping in the left navigation, the right pane displays a list of OPAM targets and their mapped templates. To change a target map:
-
Select the target from the list and click Edit.
-
In the Edit Mapping dialog, select a different template from the Available templates list.
-
Click OK to close the window. The selected target now appears in the list with the new template in the Mapped Template column. If for some reason, the change does not appear automatically, click the Refresh button to update the list.
| Control | Function |
|---|---|
| OPAM Server URL | Enter the URL of the OPAM server. The Administrative Console remembers previously entered URLs; they are available in the dropdown list. |
| Username | Enter your username. |
| Password | Enter your password. |
| Target repository | Click the Browse… button to launch the Connect to Repository dialog. Use this dialog to specify the server name and other repository information required. |
| Apply | Click Apply to save the OPAM configuration information you entered in the previous fields. |