6.3 Managing Individual OAM Server Registrations
OAM Server instances can be registered and managed using the Oracle Access Management Console.
Topics here include:
6.3.1 OAM Server Registration Page
Users with valid Administrator credentials can register a freshly installed Managed Server (OAM Server instance) or modify an existing OAM Server registration using the Oracle Access Management Console.
Alternatively: You can use custom WLST commands to register and manage OAM Server instances. Changes are reflected in the Oracle Access Management Console and are automatically propagated to every OAM Server in the cluster.
Figure 6-1 illustrates a typical OAM Server registration page when viewed within the Oracle Access Management Console. To access the OAM Server registration page using the Oracle Access Management Console, click Configuration in the top right of the console and then click the Server Instances link on the Configuration page. From the resulting Server Instances search page, click Create in the Search Results table to display the Create: OAM Server page. See Registering a Fresh OAM Server Instance for details on how to configure this page.
Figure 6-1 OAM Server Registration Page with Proxy Tab Displayed
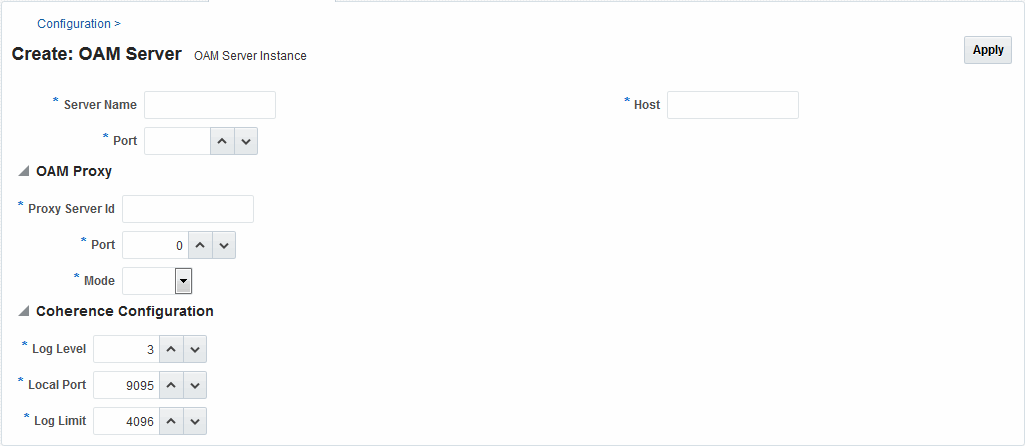
Description of "Figure 6-1 OAM Server Registration Page with Proxy Tab Displayed "
Individual server registration settings are described in Table 6-2.
Table 6-2 OAM Server Instance Settings
| Element | Definition |
|---|---|
|
Server name |
The identifying name for this server instance, which was defined during initial deployment in the WebLogic Server domain. |
|
Host |
The full DNS name (or IP address) of the computer hosting the server instance. For example: host2.domain.com. |
|
Port |
The port on which this server communicates (listens and responds). Default: 5575 Note: If both the SSL and Open ports of the Managed Server are enabled, then the Managed Server is set to the SSL port by default. If you must use the non-SSL port, the credential collector URL of the authentication scheme must be set to the absolute URL which points to See Also: Securing Communication |
|
Proxy |
See "OAM Proxy Settings" |
|
Coherence |
See Also:
6.3.1.1 OAM Proxy Settings
An integrated proxy server (OAM Proxy) is installed with each Managed Server for OAM Server. The OAM Proxy is used as a legacy Access Server to provide backward compatibility for 10g Agents that are registered with Access Manager 11g. The Agent can be freshly installed or currently operating within an Oracle Access Manager 10g SSO deployment.
Each OAM Proxy instance requires a different port. The proxy starts listening when the application starts. Registered access clients can immediately communicate with the proxy.
The OAM Proxy handles both configuration and run-time events. Each OAM Proxy can accept requests from multiple access clients concurrently. Each OAM Proxy enables access clients to interact with Access Manager 11g. This includes:
-
10g (10.1.4.3) WebGates
-
10g (10.1.4.2.0) WebGates
-
10g (10.1.4.0.1) WebGates
-
11g WebGates (needs no proxy)
Note:
For Access Clients, Access Manager 11g provides authentication and authorization functionality only. Policy modification through Access Clients is not supported.
OAM Proxy settings are documented in Table 6-3.
Table 6-3 OAM Proxy Settings for an Individual OAM Server
| OAM Proxy Setting | Value |
|---|---|
|
Port |
The unique port on which this OAM Proxy instance is listening. On a default installation, the port is 5575. |
|
Proxy Server ID |
The identifier of the computer on which the OAM Proxy (and this OAM Server instance) resides. DNS hostname is preferred; however, you can use any valid and relevant string. On a default installation, the Proxy Server ID is AccessServerConfigProxy. |
|
Mode |
OAM channel transport security for the OAM Proxy can be one of the following (the agent mode must match during registration and can be higher after registration):
On a default installation, the Mode is Open. Note: Simple and Cert transport security modes are governed by information defined on the OAM Server Common Properties OAM Proxy tab, as described in "Managing the Access Protocol for OAM Proxy Simple and Cert Mode Security". See Also: Securing Communication if you are configuring Simple or Cert transport security modes. |
OAM Proxy Logging: Oracle Access Management services use the same logging infrastructure as any other Oracle Fusion Middleware 11g component, as described in Auditing Administrative and Run-time Events. However, OAM Proxy uses Apache log4j for logging.
6.3.1.2 Coherence Settings for Individual Servers
Coherence provides replicated and distributed (partitioned) data management and caching services on top of a reliable, highly scalable peer-to-peer clustering protocol. Coherence has no single points of failure; it automatically and transparently fails over and redistributes its clustered data management services when a server becomes inoperative or is disconnected from the network.
When a new server is added, or when a failed server is restarted, it automatically joins the cluster and Coherence fails back services to it, transparently redistributing the cluster load. Coherence includes network-level fault tolerance features and transparent soft re-start capability to enable servers to self-heal.
Coherence modules consist of the values, and types for the individual server instance, as shown in Figure 6-1.
WARNING:
Oracle recommends that you do not modify Oracle Coherence settings for an individual server unless you are requested to do so by an Oracle Support Representative.
Table 6-4 Default Coherence Settings for Individual OAM Servers
| Coherence Module | Type of Entry | Description and Default Values |
|---|---|---|
|
LogLevel |
String |
The Coherence log level (from 0 to 9) for OAM Server events. |
|
LogPort |
int (integer) |
The listening port for Coherence logging on the WebLogic Server. |
|
LogLimit |
String |
The Coherence log limit |
Coherence Logging: Appears only in the WebLogic Server log. There is no bridge from Oracle Coherence logging to Oracle Access Management logging. For Oracle Fusion Middleware 11g logging infrastructure details, see Logging Component Event Messages.
6.3.2 Registering a Fresh OAM Server Instance
Users with valid Administrator credentials can register a new Managed Server (OAM Server) instance using the Oracle Access Management Console. Each OAM Server must be registered to communicate with agents.
Before you begin, the new Managed Server instance must be configured in the Oracle WebLogic Server domain, but not yet started.
6.3.3 Viewing or Editing Individual OAM Server Registrations and Proxy Settings
Changes made are immediately visible in the Oracle Access Management Console and propagated to all OAM Servers in the cluster.