39.5 Defining Keystore Settings for Federation
The following topics describe how to define Keystore settings for Federation:
39.5.1 About Managing Keytore Settings for Identity Federation
You view and manage keystores configured for use with federation partners on the Federation Settings page of the console.
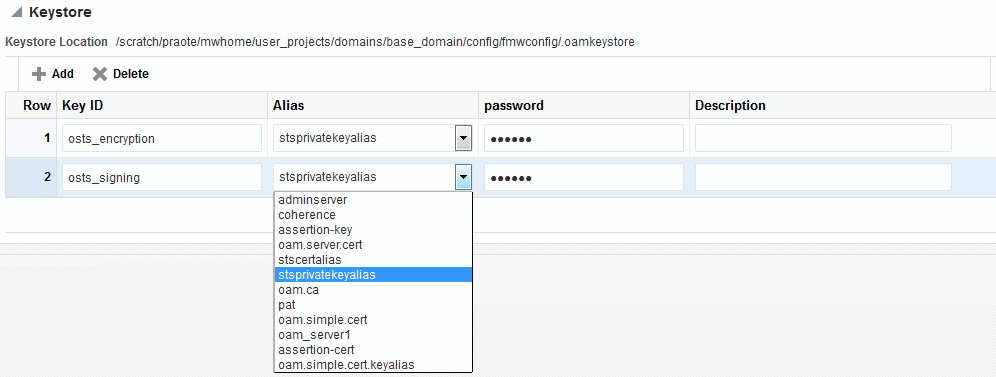
Figure 39-2 illustrates the expanded Federation Proxy Settings section of the Federation Settings page.
Table 39-4 describes each element on the Keystore Settings section of the Federation Settings page.
Table 39-4 Keystore Settings for Federation
| Element | Description |
|---|---|
|
Keystore Location |
This element specifies the keystore path. |
|
Key ID |
This is the unique key ID. |
|
Description |
This element provides a brief description of the key, such as its usage type. |
|
Alias |
This element specifies the key alias. Note: You can choose one of the aliases that is available in the keystore using the drop-down. |
|
Password |
This element specifies the key password. |
39.5.2 Managing Identity Federation Encryption/Signing Keys
As described in Managing Data Sources, Identity Federation uses keys in the following keystore to store encryption and signing certificates:
$DOMAIN_HOME/config/fmwconfig/.oamkeystore
39.5.2.1 Task Overview: Managing Identity Federation Encryption/Signing Keys
-
Resetting the System (.oamkeystore) and Trust (amtruststore) Keystore Password
-
Adding a New Key Entry to the System Keystore (.oamkeystore)
Note:
AM denotes Access Manager, STS denotes Security Token Service, and IF denotes Identity Federation in this discussion.
39.5.2.2 Resetting the System (.oamkeystore) and Trust (amtruststore) Keystore Password
You can reset the password that protects the keystores as well as the key entries which use the same password as the keystore.
The keystores have been created and configured by the IM/OAMAM/OSTS installer, and the password and the key entries password were randomly generated. The WLST resetKeystorePassword method allows you to set the .oamkeystore password and any key entries with a password identical to the .oamkeystore password to a new value. The command updates the:
-
.oamkeystore password
-
Key entries in the .oamkeystore which had the same password as the keystore
-
OAMAM/STS/IF configuration to reflect the change
-
amtruststore password if the keystore is protected by the same password as the .oamkeystore (default)
To set the system keystore (.oamkeystore) password:
39.5.2.3 Adding a New Key Entry to the System Keystore (.oamkeystore)
You can add a new key entry into the system keystore (.oamkeystore) using the keytool command to create and add the new key entry.
Once the entry has been added, it must be defined in the Identity Federation settings configuration screen so that it can be used to sign assertions and decrypt incoming messages.
39.5.2.3.1 Task Overview: Adding a New Key Entry to the System Keystore (.oamkeystore)
The following topics describe how to add a new entry to the system keystore to sign SAML assertions or decrypt XML-encrypted data not covered by WSS:
39.5.2.3.2 Adding a New Entry in the .oamkeystore
There are no prerequisites for this task. The system keystore (.oamkeystore) password has been reset.
To add a new entry in the .oamkeystore:
39.5.2.3.3 Adding a New Entry in the Identity Federation Settings
In the Identity Federation settings, you can add a new row to the Keystore table.
To add a new entry in the Identity Federation settings:
- In the Oracle Access Management Console, click Federation at the top of the window.
- In the Federation console, Select Federation from the drop-down list in the Settings section.
- On the Federation Settings page, navigate to the Keystore table.
- Add a row.
- Enter a key ID that will be used to reference this key when configuring Identity Federation.
- Select the alias of the key entry stored in .oamkeystore.
- Enter the key password.
- Click Apply.
39.5.2.3.4 Configuring the Signing and Encryption Key
Once the key has been added to the keystore table, you can configure Identity Federation to use the key.
To configure the signing and encryption key:
- In the Oracle Access Management Console, click Federation at the top of the window.
- In the Federation console, Select Federation from the drop-down list in the Settings section.
- Navigate to the General section.
- Select the Signing Key from the list of available key entries that were defined in the keystore table.
- Select the encryption key from the list of available key entries that were defined in the keystore table.
- Click Apply.
Identity Federation will now use those keys to sign and decrypt messages.
39.5.2.3.5 Using WLST for Key Transport Algorithm
Oracle Identity Federation supports RSA 1.5 as the key transport algorithm by default. The key transport algorithm can be changed from RSA 1.5 to RSA-OAEP based on the requirement, by adding a new property, defaultkeytransportmethod to oam-config.xml using the WLST commands.
You can configure the defaultkeytransportmethod parameter in oam-config.xml as follows:
<Setting Name=”defaultkeytransportmethod” Type=”xsd: xsd”> http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p </Setting>
-
To update the key transport algorithm for a specific partner only (in this example, OIFSP), use the following WLST command:
updatePartnerProperty(partnerName=”OIFSP”, partnerType=”SP”, propName=”defaultkeytransportmethod”, propValue=”http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p”,type=”string”)
-
To update the key transport algorithm for all partners that use a specific partner profile (in this example, saml20-sp-partner-profile), use the following WLST command:
putStringProperty("/fedpartnerprofiles/saml20-sp-partner-profile/defaultkeytransportmethod","http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p"); -
To update the key transport algorithm for all defined SP partners, use the following WLST command:
putStringProperty("/idpglobal/defaultkeytransportmethod", “http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p”)Note:
This is a global change.