45.3 Managing Token Issuance Templates
An issuance template contains rules on how a token will be created and is specific to a token type.
Each issuance template indicates Signing and Encryption and also contains Attribute Name, Value Mapping, and Filtering settings to be sent as part of the token. This section provides the following information:
45.3.1 About Managing Token Issuance Templates
Each Token Issuance Template indicates how to construct a token.
In other words, which signing or encryption to use when constructing a token. Each Token Issuance Template also defines the attributes mapping and filtering rules to be applied to the attributes that will be included in the outgoing token. However, Issuance Templates do not list the attributes that will be sent in the outgoing token: these are defined in the Relying Party Partner Profile.
Token Issuance Template details which will differ depending on your chosen token type. Table 45-2 describes where to find more information.
Table 45-2 Issuance Template Requirements
| Topic | Figures and Tables |
|---|---|
|
General Details |
|
|
Issuance Properties: Username Tokens |
|
|
Issuance Properties: SAML Tokens |
|
|
Security: SAML Tokens |
|
|
Attribute Mapping: SAML Tokens |
General Details
Figure 45-3 shows the New Issuance Template page with defaults showing. Unless explicitly stated, General information is the same regardless of the Token Type you choose. For more information, see Table 45-3. After you fill in General information and click Save, you cannot return and edit the template name or token type.
Figure 45-3 Issuance Template: General Details and Defaults
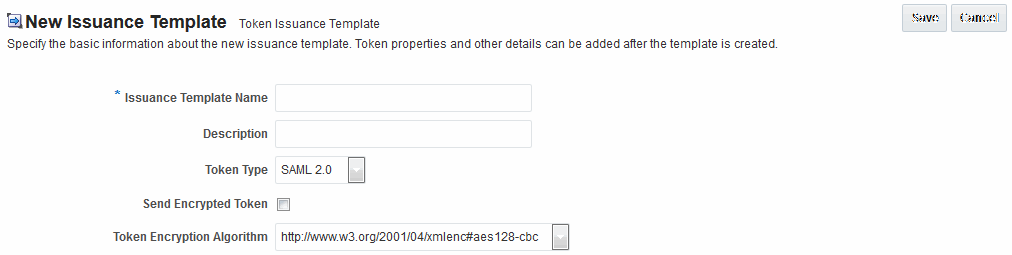
Description of "Figure 45-3 Issuance Template: General Details and Defaults"
Table 45-3 Issuance Template: General Details
| Elements | Description |
|---|---|
|
Issuance Template Name |
Enter a unique name for this template. |
|
Description |
Optional. |
|
Token Type |
Choose a standard (or custom, if any) token type from those listed. |
|
SAML, Username, and Custom Token Types |
|
|
Send Encrypted Token |
Click to enable token encryption. |
|
Token Encryption Algorithm |
When token encryption is enabled, choose a Token Encryption Algorithm from those listed. |
Issuance Properties: Username Token Type
If the token type is Username, the Issuance Properties shown in Figure 45-4 are needed for a Username token type template.
Figure 45-4 Issuance Properties: Username Token Type
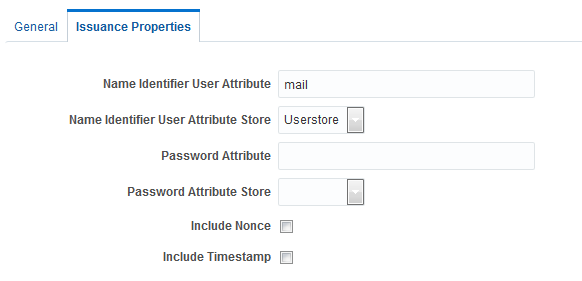
Description of "Figure 45-4 Issuance Properties: Username Token Type"
Table 45-4 describes the Issuance Properties for the Username token type.
Table 45-4 Issuance Properties: Username Token Type
| Element | Description |
|---|---|
|
Name Identifier User Attribute |
Attribute to be used to populate the Username element in the Username Token. |
|
Name Identifier User Attribute Store |
Choose the user attribute store type:
Note: If the Attribute Store is the Userstore, LDAP is used to retrieve the attribute from the user record. If the Attribute Store is context, data from the incoming token is used as the attribute source. |
|
Password Attribute |
Attribute to be used to populate the Password element in the Username Token. |
|
Password Attribute Store |
Choose the password attribute store type:
Note: If the Attribute Store is the Userstore, LDAP is used to retrieve the attribute from the user record. If the Attribute Store is context, data from the incoming token is used as the attribute source. |
|
Include Nonce |
Indicates whether or not a Nonce made of random data should be included in the Username token. Default: Disabled |
|
Include Timestamp |
Indicates whether or not a the Created element should be included in the Username token. Default: Disabled |
Issuance Properties: SAML Token Types
SAML 1.1 and 2.0 token types require the issuance properties illustrated in Figure 45-5.
Note:
These issuance properties differ from those for Username token type.
Figure 45-5 Issuance Properties: SAML Token Types
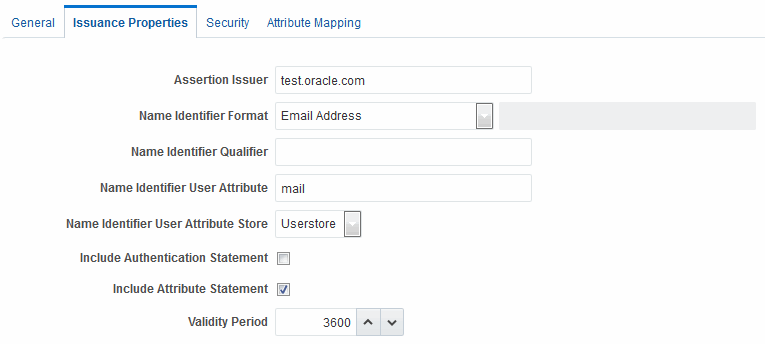
Description of "Figure 45-5 Issuance Properties: SAML Token Types"
Table 45-5 describes all Issuance Properties by token type. Only SAML token types require issuance properties.
Table 45-5 Issuance Properties: SAML Token Types
| Element | Description |
|---|---|
|
Assertion Issuer |
Specifies the identifier representing the issuer of the assertion. This string is used to represent this Security Token Service as the issuer of the assertion. |
|
Name Identifier Format |
Choose a format from the list and then enter the details in the text field. Options may include Custom, Kerberos Principal Name, Unspecified, X509 Subject Name and others. |
|
Name Identifier Qualifier |
Contains the string that will be set as the Name Identifier Qualifier. |
|
Name Identifier User Attribute |
References the attribute that will be used to populate the value of the Name Identifier. |
|
Name Identifier User Attribute Store |
Note: If the Attribute Store is the Userstore, LDAP is used to retrieve the attribute from the user record. If the Attribute Store is context, data from the incoming token is used as the attribute source. |
|
Include Authentication Statement |
Indicates whether or not a SAML Authentication Statement should be included in the Assertion. Default: Disabled Note: An authentication operation is required for a statement of this type to be included. An authentication statement will be included if the incoming token contained some authentication data and that those were validated (for example, the incoming SAML Assertion contains an authentication statement, or a Username Token contains credentials that were validated). |
|
Include Attribute Statement |
Indicates whether or not a SAML Attribute Statement will be included in the outgoing Assertion. A statement of this type will be included only if this flag is set to true and if at least one attribute is included in the outgoing Assertion. Default: Enabled Note: the RP PP will determine which attributes need to be included in an outgoing token. |
|
Validity Period |
Specify the length of time (in seconds) that the token will be valid. Default: 3600 (seconds) |
Security Details: SAML Tokens
Only SAML token types require Security Details.
See Figure 45-6.
See Table 45-6.
Figure 45-6 Security Details: SAML Tokens
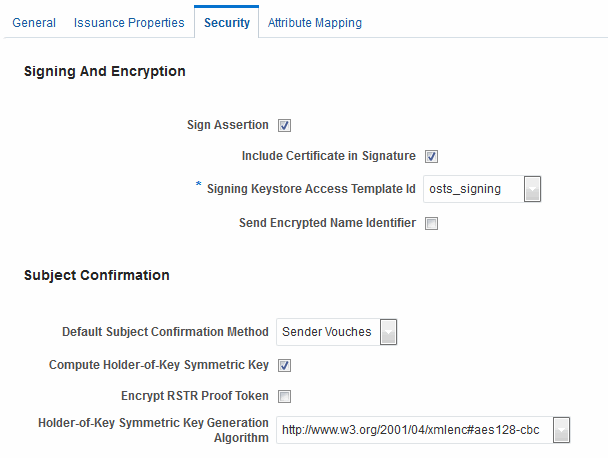
Description of "Figure 45-6 Security Details: SAML Tokens"
Table 45-6 Security Details: SAML Tokens
| Elements | Description |
|---|---|
|
Signing And Encryption |
Indicates whether or not the Assertion will be signed using the Key referenced by the Signing Keystore Access Template ID field. |
|
Sign Assertion |
Indicates whether or not the assertion will be digitally signed with a certificate. Default: Enabled |
|
Include Certificate in Signature |
Indicates whether or not the signing certificate will be included in the Assertion. Default: Enabled |
|
Signing Keystore Access Template Id |
References the key to be used to sign assertions created with this issuance template. The key templates are defined in the Security Token Service Settings section. |
|
Send Encrypted Name Identifier |
Indicates whether the encrypted token name identifier will be sent as part of the digital assertion signature. |
|
Subject Confirmation |
|
|
Default Subject Confirmation Method |
Indicates which Subject Confirmation Method will be used by default, if the requester did not specify a method in the WS-Trust request. Possible values are:
|
|
Compute Holder-of-Key Symmetric Key |
Default: Enabled Indicates whether or not Security Token Service will generate random data when creating the Secret Key for the Holder of Key Symmetric Key data.
|
|
Encrypt RSTR Proof Token |
Indicates whether or not the Proof Token must be encrypted when returning the server entropy or secret key to the requester in the WS-Trust response, when the Subject Confirmation method is Holder of Key with Symmetric Key Default: Disabled |
|
Holder-of-Key Symmetric Key Generation Algorithm |
Select the symmetric key generation algorithm that will be used to create the secret key when the Subject Confirmation method is Holder of Key with Symmetric Key: |
Attribute Mapping: SAML Tokens
When the token type is SAML 1.1 or 2.0, it is possible to define attribute mapping and filter rules that will be applied to the attributes included in the Assertion.
There are three different rules:
-
Attribute name mapping where the local name of an attribute can be changed to another value. For example, givenname can be changed to firstname.
-
Attribute value mapping where the local value of an attribute can be translated to another value. For example, President to CEO.
-
Attribute value filtering where the local value of an attribute can be filtered so it is not included in the outgoing assertion. For example, some sensitive attribute values could be removed while others would be issued.
See Also:
Token Mapping attributes in Figure 45-9 and Table 45-11.
Table 45-7 Issuance Template: Attribute Mapping, SAML Token
| Element | Description |
|---|---|
|
Attribute Name Mapping |
Defines an optional mapping between the local name of an attribute, and the name used to reference this attribute in the assertion. The mapping is optional. If an attribute does not have a mapping defined, then its local name will be used, and the namespace will be set to
|
|
Attribute Value Mapping |
Defines an optional value mapping for an attribute that will be included in the Assertion. Note: this attribute value mapping applies to an Attribute Name mapping. In order to define an attribute mapping for an attribute, it is required to first define an attribute name mapping for that attribute.
|
|
Attribute Value Filters |
Defines an optional value filtering for an attribute that will be included in the Assertion. Note: This attribute value filtering applies to an Attribute Name mapping. In order to define an attribute filtering for an attribute, it is required to first define an attribute name mapping for that attribute.
|
Attribute Value Condition Filters
This optional value filtering applies to an Attribute Name mapping and will be included in the Assertion. To define an attribute filtering for an attribute, you must first define an attribute name mapping for that attribute. The Condition is associated with the expression to determine whether or not the attribute value should be filtered. The possible Condition values are:
-
regexp: the expression will contain a regular expression, and if it evaluates to true, the attribute value will be filtered.
-
equals: if the attribute value matches the data contained in the expression field, then it will be filtered.
-
not-equals: if the attribute value does not match the data contained in the expression field, then it will be filtered.
-
not-equals: if the attribute value does not match the data contained in the expression field, then it will be filtered.
-
endswith: if the attribute value ends with the data contained in the expression field, then it will be filtered.
-
contains: if the attribute value contains an occurrence of the data contained in the expression field, then it will be filtered.
-
not-contains: if the attribute value does not contains any occurrence of the data contained in the expression field, then it will be filtered.
-
equals-null: if the attribute value is null, then it will be filtered.
-
not-equals-null: if the attribute value is not null, then it will be filtered.
45.3.2 Managing a Token Issuance Template
Users with valid Oracle Access Management Administrator credentials can develop a new Token Issuance Template or edit an existing template.
Skip any steps that do not apply to you. The following procedure describes how to create a new Token Issuance Template for a Security Assertion Markup Language (SAML) token.
Prerequisites for Managing a Token Issuance Template
Confirm that the desired LDAP Identity Store is registered with and configured as the Default Store.
To create a new token issuance template:
-
In the Oracle Access Management Console, click Federation at the top of the window.
-
In the Federation console, select Token Issuance Templates the View menu in the Security Token Service section.
-
New Token Issuance Template:
-
Click the New Issuance Template button in the upper-right corner (or click the Add (+) button above the Search Results table).
-
General: Define general information for this template.
See Table 45-3.
-
Click Save and dismiss the confirmation window (or click Cancel without saving).
-
Username Token Type: Define issuance parameters for this template.
See Table 45-4
-
SAML Token Type: Define parameters for this template.
See Table 45-5
See Table 45-6
See Table 45-7
-
Click Apply (or click Revert without saving it).
-
Close the definition.
-
-
Find an Existing Template: From the Token Issuance Templates page:
-
Find All: review the results table. All templates are returned by default when you access the Issuance Templates page.
-
Narrow the Search: Specify your search criteria and click the Search Button, and review the results table.
See Table 45-1.
-
Reset the Search Form: Click the Reset button.
-
-
Edit a Template: Start with the saved page you just created.
Alternatively: Use Step 3 to find the desired template and click the name in the Search Results table to display the definition.
-
Edit details as needed.
-
Click the Apply button at the top of the page to submit changes (or Revert to undo your changes).
-
-
Remove a Template:
-
Click the desired name in the Search Results table to select the item to remove.
-
From the Actions menu, click Delete (or click the Delete (X) command button above the table.
-
Click the Delete button in the Confirmation window (or click No to cancel the operation).
-