25.11 Defining Authorization Policy Rules
When Allow access rules, Deny access rules, or both are specified and do not apply to a user, the user is not qualified by the rule, and is denied access to the requested resource by default.
To specify who is allowed or denied access to the resource, the rule can do the following:
-
Identify the users by user name, role, or an LDAP filter whose criteria the user must satisfy.
-
Stipulate the computers where users can access resources.
-
Set a time period when the rule applies.
This section provides the following topics:
25.11.1 Authorization Policy Rules
Rules are new constructs in the Access Manager 11g policy model. A Rule specifies of how to combine condition evaluation outcomes. Each Rule also contains a rule effect (ALLOW or DENY), which determines the overall policy outcome.
Authorization rules define the actions to take during evaluation of the policy, conditions, and rules as well as what to do based on the outcome. There are three possible outcomes:
-
True (Allow access): If the user meets the Allow access condition, the user qualifies for the Allow access part of the rule.
-
False (Deny access): If the user meets the Deny access condition, the user qualifies for the Deny access part of the rule.
-
Inconclusive: If the user satisfies neither the Allow access nor the Deny access conditions, the rule is said to be unqualified for that user. You can also think of this as the user not qualifying for the rule. If evaluation of a rule results in an unqualified user, the user is denied access to the resource based on that rule.
In some cases, a single authorization rule is all that is required to protect the resources of an Application Domain or a policy. You can configure a rule to identify who is allowed access to the resources it protects, who is denied access to them, and under what conditions these controls apply (for example, when they apply and from which computer). An authorization rule does not need to cover all users in its Allow access and Deny access conditions. Users who request access to a resource that is protected by the rule but do not qualify for any of the conditions are, by default, denied access to the resource.
For other cases, it may be necessary to configure multiple authorization conditions into rules to protect resources. You can impose complex conditions on different users. For example, you can define a rule that includes several authorization conditions, one or more of which a user must meet to qualify for access to a protected resource (or to qualify for denial of access to it). For example, you might require the user to meet two conditions—such as belonging to one group and using a computer assigned a specific IP address—to be granted access to the resource.
Oracle Access Management Console makes it easy for you to form expressions for an authorization rule. Conditions are declared outside of rules and are referenced within rules. Evaluation outcomes are combined in either Simple mode or Expression mode. Figure 25-27 shows the Rules tab in an authorization policy.
Figure 25-27 Authorization Policy Rules Tab: Simple Mode
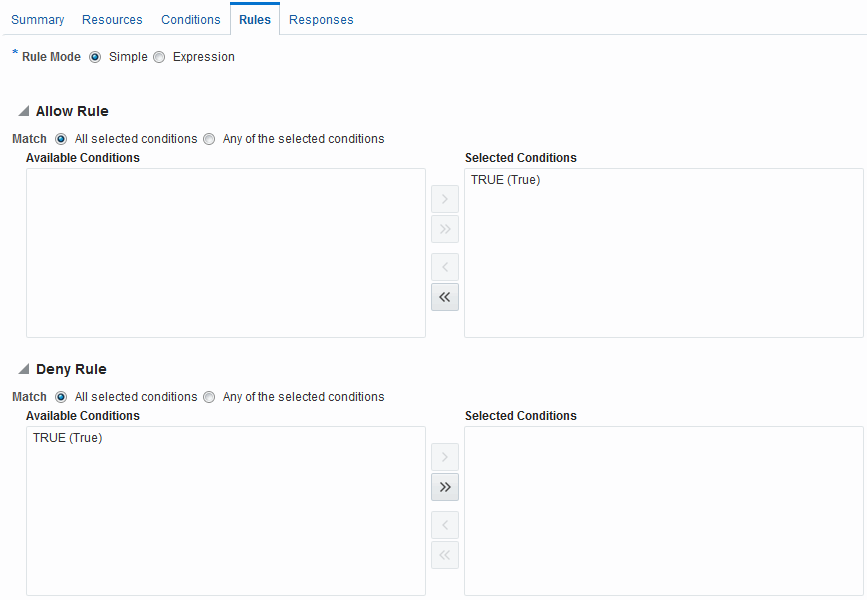
Description of "Figure 25-27 Authorization Policy Rules Tab: Simple Mode"
Table 25-22 describes the elements and controls on the Rules tab for Simple Mode evaluations.
Table 25-22 Authorization Policy Rules Elements
| Element | Description |
|---|---|
|
Rule Mode |
The method used for evaluation of conditions and rules:
|
|
Allow Rule |
The rule that allows access based on evaluation of your rules and the Selected Conditions list. |
|
Deny Rule |
The rule that denies access based on the evaluation of your rules and the Selected Conditions list. |
|
Match |
Criteria you choose to either match All conditions in the Selected Conditions list or Any conditions the Selected Conditions list. |
|
Available Conditions |
A list of all defined conditions for this authorization policy. |
|
Selected Conditions |
A list of the specific conditions that you build by moving items from the Available Conditions list to this list for use during the policy evaluation process. |
|
Arrow Controls |
Controls in the form of arrows enable you to add a condition to the Selected Conditions list (or vice versa to remove a condition from those selected). |
25.11.2 Expressions and Expression-Based Policy
When a user requests access to a resource that is protected by an authorization condition and rule, information about the user is checked against the rule. If the condition stipulates other information, such as time period or time of day the condition applies, that, too, is checked. This process is referred to as evaluation of the rule.
An authorization expression consists of a single rule or a group of rules combined to express more complex conditions. For example, you can create an expression that requires a user to meet the Allow access conditions of two rules to be granted access to the resource. You use the Oracle Access Management Console to create these expressions, which include the following elements:
-
Authorization conditions that you select from those that are defined and available in the authorization policy
-
Operators that you use to combine rules to provide the kind of authorization protection that you want (Table 25-24)
For expressions that contain multiple conditions, a user may qualify for none of the expression's conditions, one of the conditions, or for the conditions of multiple rules. In any case, it is the result of evaluation of the expression—all of its conditions and how they are combined—not any one condition, that determines whether a user is allowed or denied access to a resource.
About the Definitive Result of an Authorization Expression: Access Manager evaluates the rules of an expression until it can produce a definitive result. Evaluation of an authorization expression may produce a definitive Allow access result, a Deny access result, or an Inconclusive result.
Figure 25-28 shows the Rules tab when you use Expression as a Rule Mode.
Figure 25-28 Rules Tab: Expression Rule Mode
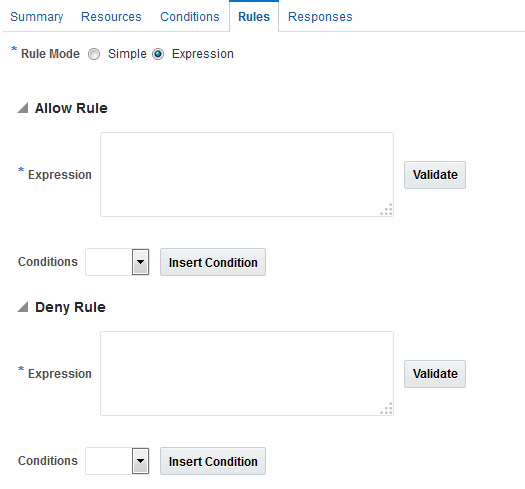
Description of "Figure 25-28 Rules Tab: Expression Rule Mode"
Table 25-23 describes the elements on the Rule tab in Expression mode.
Table 25-23 Rule Tab in Expression Mode
| Element | Description |
|---|---|
|
Rule Mode |
The method used for evaluation of conditions and rules:
See Also: Table 25-24 |
|
Allow Rule |
The rule that allows access based on evaluation of your rules and the Selected Conditions list. |
|
Deny Rule |
The rule that denies access based on the evaluation of your rules and the Selected Conditions list. |
|
Conditions |
Provides a list of all conditions defined for this authorization policy. |
|
Insert Condition |
Adds the selected Condition to the expression window. |
|
Validate |
Automatically tests the validity of the expression and reports results. |
Table 25-24 identifies the operators you can use when building an authorization expression.
Table 25-24 Operators for Expressions in Authorization Rules
| Operator | Description |
|---|---|
|
( ) |
By default, two rules on either side of an AND operator compose the compound AND condition. Rules on either side of an OR operator are alternatives. When no parenthesis are used to enforce grouping of rules, the AND operator takes precedence over the OR operator. You can use parenthesis to override the default way in which the rules of an expression are grouped. Evaluation still occurs from left to right, but the rules are organized within the couplings and groups you create through use of parenthesis. |
|
& |
The AND operator, which you use to form a compound condition which combines authorization rules. Any number of rules can be combined using the AND operator to implement the full scope of conditions a user must meet to satisfy the authorization requirement. However, a user must satisfy the same kind of condition—either Allow Access or Deny Access—of all of the rules of the AND compound condition for the AND clause to produce a definitive result. An authorization expression can contain more than one coupling or grouping of rules combined using AND. For example, it may contain several AND clauses, one connected to another by an OR operator. |
|
| |
The AND operator. An authorization expression can include a complex rule containing two or more alternative authorization conditions. Authorization rules forming a complex condition are combined using the OR operator. Each of the authorization rules specified by a complex OR condition stands on its own. Unlike compound conditions using the AND operator, the user need qualify for the condition of only one of the authorization rules connected by OR operators. An authorization expression can contain as many authorization rules connected using the OR operator as are required to express the authorization policy for the resources it protects. You can use the OR operator to connect authorization rules all of which have Deny Access conditions, all of which have Allow Access conditions, or which specify a mix of Deny Access and Allow Access conditions. You can connect single rules to single rules using OR, and you can connect a single rule to a clause containing rules combined using AND. |
25.11.2.1 Expression Evaluation in Authorization Rules
The result of evaluation of an authorization rule, in conjunction with other authorization rules, if more than one is included in the expression, determines if a user is granted access to the requested resource.
Evaluation of the rule occurs as follows:
-
Each authorization rule specified in the expression is evaluated from left to right. The outcome is combined progressively with the previously evaluated rules.
-
When the evaluation outcome is good enough to decide the overall policy outcome without having to evaluate any more rules, evaluation stops and the overall outcome is returned.
-
Each evaluation outcome can be either True, False, or Inconclusive.
Authorization Success: In this case, the user succeeds in gaining access to the requested resource. This result is associated with the Allow Access condition of the expression.
Authorization Failure: In this case, the user fails to gain access to the requested resource. This result is associated with the Deny Access condition of the expression.
Authorization Inconclusive: In this case, the rules of the expression produce conflicting results, and the user is denied access to the resource. If the match for Identity, IP4 address, or timing condition fails then expression evaluation stops and the result of the overall evaluation is deemed Inconclusive. However, based on the other rules present in the expression, this result might not affect the overall policy evaluation.
For example, the following expression:
(Rule1 AND Rule 2) OR (Rule 3 AND Rule 4)
Yields the following outcomes:
-
Rule1 - INCONCLUSIVE
-
Rule2 - FALSE
-
Rule3 - TRUE
-
Rule4 - TRUE
-
Overall: TRUE (Allow)
The following sample expression uses (in order of type) Identity, Temporal, IP4Range, and Attribute conditions:
(IsEMEAemployee & IsEMEAWorkingHours & !(ConnectedOverVPN |NotReadDisclaimer))
Condition names that include spaces, tabs, or special characters (if properly escaped when defining the expression) are properly handled
25.11.3 Defining Rules in an Authorization Policy
Users with valid Administrator credentials can add rules to an authorization policy.
Prerequisites
Defining Authorization Policy Conditions.
See Also:
To define authorization policy rules
-
Locate the desired domain as described in "Searching for an Authorization Policy".
-
Click the Rules tab.
-
Expression:
-
Click Expression as the Rule Mode.
-
In the Allow Rule Expression field, build your expression by entering operators (Table 25-24) and choosing and inserting conditions (Table 25-23).
-
Click the Validate button to confirm your expression.
-
Repeat Steps b and c for the Deny Rule.
-
Click Apply.
-
-
Simple Rule Mode:
-
Click Simple as the Rule Mode.
-
Allow Rule:
Click to Match either:
- All selected conditions
- Any of the selected conditions
Using arrows for Allow (or Deny) Rule, move desired conditions from the Available Conditions column into the Selected Conditions column.
Click Apply.
-
Repeat step b for the Deny Rule.
-
-
Click Apply and then close the Confirmation window.
-
Verify the rules by accessing the resource and evaluating the results.