1.2 Understanding Oracle Access Management Access Manager
Oracle Access Management Access Manager (Access Manager) is the former (standalone) product named Oracle Access Manager. Access Manager provides the Oracle Fusion Middleware 11g single sign-on (SSO) solution.
It operates independently (as described in this book) but can also operate with the Access Manager Authentication Provider as described in the Securing Applications with Oracle Platform Security Services.
For information on the differences between Access Manager 11g, 10g and other software, see:
Access Manager SSO allows users and groups to access multiple applications after authentication, eliminating the need for multiple sign-on requests. To enable SSO, a Web server, Application Server, or any third-party application must be protected by a WebGate (or mod_osso instance) that is registered as an agent with Access Manager. Administrators then define authentication and authorization policies to protect the resource. To enforce these authentication policies, the agent acts as a filter for HTTP requests.
Note:
WebGates are agents provided for various Web servers by Oracle as part of the product. Custom access clients, created using the Access Manager SDK, can be used with non-Web applications. Unless explicitly stated, information in this book applies equally to both.
You can also integrate any Web applications currently using Oracle ADF Security and the OPSS SSO Framework with Access Manager. (See Integrating Oracle ADF Applications with Access Manager SSO.) The following sections contain more details on Access Manager.
1.2.1 About Components in Access Manager
Access Manager 11g sits on an instance of Oracle WebLogic Server and is part of the Oracle Fusion Middleware Access Management architecture.
While providing backward compatibility and co-existence with existing solutions, Access Manager 11g replaces and converges the earlier technologies Access Manager 10g and Oracle Application Server SSO (OSSO) 10g. Figure 1-2 illustrates the primary Access Manager 11g components and services. The Protocol Compatibility Framework interfaces with OAM WebGates, mod_osso agents, and custom Access Clients created using the Access Manager Software Developer Kit (SDK).
Note:
This section does not illustrate or discuss all Access Manager components.
Figure 1-2 Access Manager 11g Components and Services
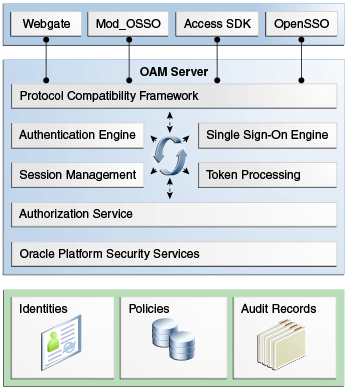
Description of "Figure 1-2 Access Manager 11g Components and Services"
Figure 1-3 illustrates the distribution of Access Manager components.
Figure 1-3 Access Manager 11g Component Distribution
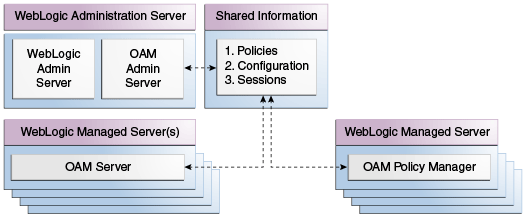
Description of "Figure 1-3 Access Manager 11g Component Distribution"
The Oracle Access Management Console resides on the Oracle WebLogic Administration Server (referred to as AdminServer). WebLogic Managed Servers hosting OAM runtime instances are known as OAM Servers. Information shared between the two includes:
-
Agent and server configuration data
-
Access Manager policies
-
Session data (shared among all OAM Servers)
Starting in the 11g Release 2 (11.1.2.3), a Policy Manager Console can optionally be deployed on the WebLogic Managed Servers. See Oracle Access Management Console and the Policy Manager Console for details.
1.2.2 Understanding Access Manager Deployments
Your enterprise may have more than one Oracle Access Manager deployments. Irrespective of the deployment size, the configuration wizard installs various components in a newly created WebLogic Server domain.
Table 1-1 describes the types of deployments in which Access Manager might be installed by your enterprise.
Table 1-1 Access Manager Deployment Types
| Deployment Type | Description |
|---|---|
|
Development Deployment |
Ideally a sandbox-type setting where the dependency on the overall deployment is minimal |
|
QA Deployment |
Typically a smaller shared deployment used for testing |
|
Pre-production Deployment |
Typically a shared deployment used for testing with a wider audience |
|
Production Deployment |
Fully shared and available within the enterprise on a daily basis |
During initial installation and configuration of Access Manager in your deployment, you create a new WebLogic Server domain (or extend an existing domain). Regardless of the deployment size or type, in a new WebLogic Server domain, the following components are installed using the Oracle Fusion Middleware Configuration Wizard.
-
WebLogic Administration Server
Note:
In an existing WebLogic Server domain, the WebLogic Administration Server is already installed and operational.
-
Oracle Access Management Console deployed on the WebLogic Administration Server
-
A WebLogic Managed Server for Oracle Access Management services
-
Application deployed on the Managed Server
See Also:
Understanding Oracle WebLogic Server Domains in Understanding Domain Configuration for Oracle WebLogic Server
Once the domain is configured, additional details are defined for OAM Servers, Database Schemas, (optional) WebLogic Managed Servers and clusters, and the following store types:
-
Policy Store: The default policy store is file-based for development and demonstration purposes, and is not supported in production environments. All policy operations and configurations are performed directly on the database configured as the policy store in production environments.
See Also:
-
Identity Store: The default Embedded LDAP data store is set as the primary user identity store for Access Manager.
See Also:
-
Keystore: A Java keystore is configured for certificates for Simple or Certificate-based communication between OAM Servers and WebGates during authorization. The keystore bootstrap also occurs on the initial AdminServer startup after running the Configuration Wizard.
See Also: