3.4 Certificate Validation and Revocation
The Certificate Validation module is used by the Security Token Service to validate X.509 tokens and to verify whether or not the certificates have been revoked.
It supports the following options:
-
A Certificate Revocation List (CRL) is a list of certificates (identified by serial numbers) that have been revoked. Revoked certificates are listed with a reason, an issue date, and the issuing entity. (In addition, each list contains a proposed date for the next release.) Entities presenting these (revoked) certificates should no longer be trusted. When a potential user attempts to access a server, the server allows or denies access based on the CRL entry for the particular user. For more information, see Enabling the Certificate Revocation List Functionality
-
The Online Certificate Status Protocol (OCSP) was developed as an alternative to CRLs. OCSP specifies how the client application that requests information on a certificate's status will obtain it from the server that responds to the request. An OCSP responder can return a signed response signifying that the certificate specified in the request is either good, revoked or unknown. If the OCSP cannot process the request, it returns an error code. For more information, see "Enabling OCSP Certificate Validation" and Additional OCSP Configurations
-
A CRL Distribution Point extension (CDP extensions) contains information regarding the location of Certificate Revocation Lists (CRLs) and OCSP servers. You o use the Administration Console to define these points. For more information, see Enabling CRL Distribution Point Extensions
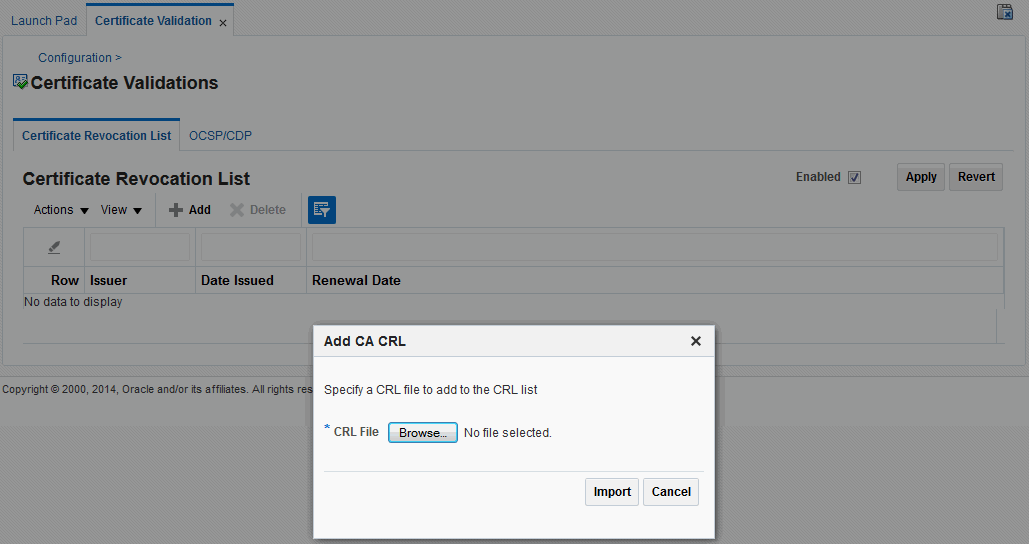
3.4.1 Enabling the Certificate Revocation List Functionality
Users with Oracle Access Management Administrator credentials can use the following procedure to enable the CRL functionality and import a current Certificate Authority Certificate Revocation List (CA CRL). Before beginning, you should have your CA CRL ready to import.
To enable:
Note:
To search for CRLs in the table, enable Query by Example from the View drop-down. Enter filter strings in the header fields displayed and hit Enter.
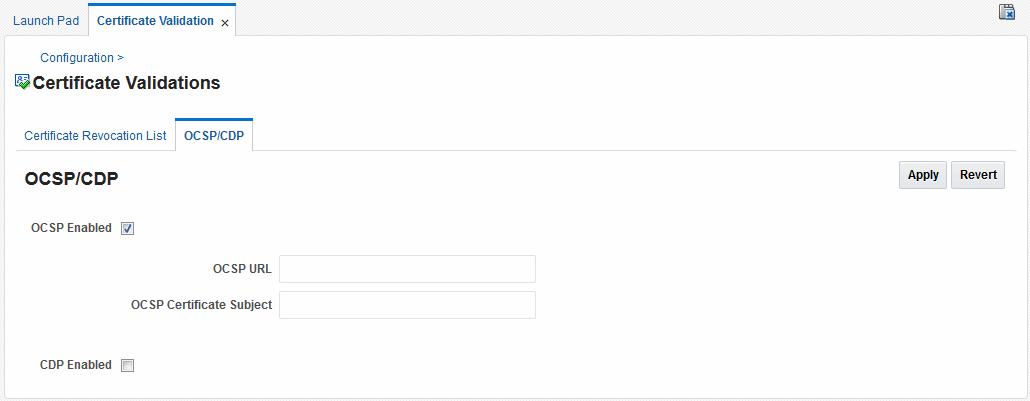
3.4.2 Enabling OCSP Certificate Validation
Users with Oracle Access Management Administrator credentials can use the following procedure to enable the OCSP. Before you begin, you should have the URL of the OCSP service ready to import.
To enable:
-
Under the Configuration section of the Oracle Access Management Console, click Certificate Validation.
The Certificate Revocation List page is displayed. Confirm that the Enabled box is checked.
-
Click the OCSP/CDP tab.
-
Enable OCSP.
-
Enter the URL of the OCSP Service.
-
Enter the Subject DN of the OCSP Service.
-
Save this configuration.
Figure 3-6 illustrates how to add an OCSP URL using the Administration Console. See "WLST configureOAMOSCSPCertValidation" for details on how to do this using the WLST command.
-
-
Proceed to "Enabling CRL Distribution Point Extensions".
3.4.3 Enabling CRL Distribution Point Extensions
Users with Oracle Access Management Administrator credentials can use the following procedure to add CRL distribution points in issued certificates.
To enable:
-
Under the Configuration section of the Oracle Access Management Console, click Certificate Validation.
The Certificate Revocation List page is displayed. Confirm that the Enabled box is checked.
-
Open the OCSP/CDP tab.
-
Enable CDP.
-
Save this configuration.
Figure 3-6 illustrates this.
-
3.4.4 Additional OCSP Configurations
Support for HTTP Proxy and multiple OCSP Responder configurations have been added for this 11g Release 2 (11.1.2.3) version of Oracle Access Manager.
The following example illustrates the current Certificate Validation Module configuration.
Certificate Validation Module Configuration
<Setting Name="CertValidationModule" Type="htf:map">
<Setting Name="certpathvalidationocspcertsubject"
Type="xsd:string"></Setting>
<Setting Name="certpathvalidationocspurl" Type="xsd:string"></Setting>
<Setting Name="certvalidationcrlstorelocation"
Type="xsd:string">/scratch/maymaria/installed/wlsHome/user_projects/
domains/base_domain/config/fmwconfig/amcrl.jar</Setting>
<Setting Name="defaulttrustcastorelocation"
Type="xsd:string">/scratch/maymaria/installed/wlsHome/user_projects/
domains/base_domain/config/fmwconfig/amtruststore</Setting>
<Setting Name="defaulttrustcastoretype" Type="xsd:string">jks</Setting>
<Setting Name="certpathvalidationcdpenabled"
Type="xsd:boolean">false</Setting>
<Setting Name="certpathvalidationcrlenabled"
Type="xsd:boolean">false</Setting>
<Setting Name="certpathvalidationocspenabled"
Type="xsd:boolean">false</Setting>
</Setting>
The following sections contain configuration information for these new features.
3.4.4.1 Configuring Multiple OCSP Responders
To support multiple OCSP Responders, the three lines of configuration from the following example of Multiple OCSP Responder Configuration must be added to the top of the Certificate Validation Module configuration section (illustrated in the following example).
Multiple OCSP Reponder Configuration
<Setting Name="CertValidationModule" Type="htf:map">
<Setting Name="certpathvalidationocspurltocamap" Type="htf:map">
<Setting Name="<url_value>" Type="xsd:string">
<ocsp_responder_subject></Setting>
</Setting>
<Setting Name="useJDKOCSP" Type="xsd:string">false</Setting>
...
</Setting>
Configure the first and second lines to enable multiple OCSP responders.
-
Set
certpathvalidationocspenabledto true. -
Update the
certpathvalidationocspurltocamapconfiguration. It is of type Map, the key is the OCSP Responder URL (URL Encoded) and the value is the OCSP Responder's Certificate subject.<Setting Name="certpathvalidationocspurltocamap" Type="htf:map"> <Setting Name=" http%3A%2F%2Flocalhost%3A9797" Type="xsd:string"> emailAddress=sagar@pspl.com,CN=ps2436,OU=OBLIX-QA,O=PSPL, L=PUNE,ST=MAHA,C=MY</Setting> </Setting> -
(Optionally) set values for
certpathvalidationocspcertsubjectandcertpathvalidationocspurl.
The Responder URLs will be fetched first from the AuthorityInformationAccess extension of the user's X.509 certificate and second from Modules/Plugin (CertValidation). The Responder Subjects will be fetched first from the defined configuration map and second from the Module/Plugin (CertValidation) configuration. In cases where these configurations are not found, the OCSP validation will fail.
Configure the third line to provide backward compatibility for those who want to use JDK OCSP validation rather than the new OAM OCSP Checker. By default, the JDK OCSP Checker is enabled. When configuring the OAM OCSP Checker using the WLST command, the flag is set to false. For more information on the WLST command, see WLST configureOAMOSCSPCertValidation.
Depending on the Certificate Validation Module configuration there are three different options as documented in Table 3-5.
Table 3-5 OCSP Responder Configuration Options
| Configuration | OCSP Configuration (certpathvalidationocspenabled) | CRL Configuration (certpathvalidationcrlenabled) | JDK/OAM OCSP Configuration (useJDKOCSP) |
|---|---|---|---|
|
No OCSP Checking Simple certificate validation is performed during OAM X-509 authentication |
False |
False |
False |
|
OAM OCSP X-509 authentication performs certificate validation with OCSP checking using the new OAM OCSP Checker. |
True |
True/False (does not matter) |
False |
|
JDK OCSP X-509 authentication performs certificate validation with OCSP checking using the JDK OCSP Checker. |
True |
True |
True |
To enable OCSP validation to be done using one configured responder URL, set the certpathvalidationcrlenabled and certpathvalidationocspenabled properties to true and set values for the certpathvalidationocspcertsubject and certpathvalidationocspurl properties. If these properties are not set, OCSP validation will be done using the responder URL defined within the user certificate's AIA Extension. If no URL is defined, OCSP validation will fail.