5 Securing Mobile Security Access Server Resources
Mobile Security Access Server (MSAS) provides a central access point for securing traffic from mobile devices to intranet resources such as web sites or web services exposed as URLs. These resources, defined as URLs inside MSAS proxy and virtual applications, can be secured using predefined access policies and assertions installed with MSAS.
This chapter includes the following topics:
5.1 Overview of Mobile Security Access Server Resource Security
To secure the communication between the mobile device and the back-end URLs, you can attach access policies and assertions at policy enforcement points on each URL in an MSAS application. These policies and assertions enforce security during the request phase from the client, the invocation of the back-end URL, and the response phase back to the client.
You can configure both authentication and authorization using the access policies. Typically, the authorization policies work in conjunction with the authentication policies. The authentication policies are used to verify the identity of the user accessing the URL, then the authorization policy confirms the roles to which the user belongs and performs the authorization check.
The predefined policies provided with Mobile Security Access Server are based on common best practice policy patterns used in customer deployments. The policies are constructed using assertions based on predefined assertion templates. If a predefined policy satisfies the requirements of your use case, you can attach the policy to the appropriate endpoints. If, however, you need to edit and customize the policy for each URL, you may prefer to directly attach an assertion, provided in a predefined assertion template, because you can edit the attached assertion directly.
5.2 Attaching Policies and Assertions to Virtual Applications
Virtual applications defined in the MSAS environment specify virtual URLs for back-end URLs. In this case, the Mobile Security Access Server acts as reverse-proxy and hides the actual back-end URL from the clients.
In a virtual application, you attach policies and assertions at the HTTP method level of virtualized URLs. The policy enforcement endpoints to which you can attach policies are:
-
On-Request—Secures the request phase from the client to Mobile Security Access Server using the policies and assertions referenced. Note that the same policies and assertions that are attached to the on-request endpoint are automatically attached to the on-response endpoint to secure the response sent back to the client.
-
Invoke—Secures the connection between Mobile Security Access Server and the back-end service using the policies and assertions referenced.
-
On-Response—Secures the response phase from Mobile Security Access Server to the client. If the attached policy or assertion does not have any response behavior, the policy is not enforced.
For a list of the policies and assertions that are supported for MSAS, see "Summary of Supported Policies and Assertions".
To attach policies and assertions to the policy enforcement endpoints of a virtual URL:
-
Navigate to the URLs Summary page for the virtual application to be secured:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed in the MSAS Applications page by using the Search field. See "Searching for MSAS Applications".
-
Click the virtual application icon,
 , or the name of the virtual application that you want to secure.
, or the name of the virtual application that you want to secure. -
In the MSAS Application Details page, click the URLs search icon to display the URLs Summary page for the virtual application.
-
-
Click the URL icon,
 or the name of the URL to be secured to display the URL Policy Configuration page.
or the name of the URL to be secured to display the URL Policy Configuration page. -
Click the options menu
 for the policy enforcement endpoint to which you want to attach policies or assertions.
for the policy enforcement endpoint to which you want to attach policies or assertions. -
To attach a policy to a policy enforcement endpoint:
-
Click Add Policy to attach a policy. The list of policies is filtered to reflect only the policies that are available for the type of endpoint. For example, only policies that can be attached to invoke the back-end service are listed for the Invoke policy enforcement endpoint.
You can use the search field to refine the list of policies displayed. Enter all or part of a policy name in the Search field, select the desired operator, and press the search icon.The results that match the search criteria are displayed in the Search Results table.
Optionally, use the View menu to change the columns displayed, or to change the order of the columns.
-
Select the policy to be attached and click Add Selected.
-
Review the selections in the Selected Policies table. To remove an entry from the table, select the policy to be removed, then click Remove Selected. To remove all policies from the table, click Remove All.
When you have confirmed the list of policies to be attached, click Attach Policies. The attached policies are listed in a table under the associated policy enforcement endpoint.
-
-
To attach an assertion to a policy enforcement endpoint:
-
Click Add Assertion to attach an assertion to the endpoint. The list of assertions is filtered to reflect only the assertions that are available for the type of endpoint, organized by template name. For example, only assertions that can be attached to invoke the back-end service are listed for the Invoke policy enforcement endpoint.
You can use the search field to refine the list of assertions displayed. Enter all or part of an assertion name in the Search field, select the desired operator, and press the search icon.The results that match the search criteria are displayed in the Search Results table.
Optionally, use the View menu to change the columns displayed, or to change the order of the columns.
-
Select the assertion to be attached and click Add Selected.
-
Review the selections in the Selected Assertion Templates table. To remove an assertion from the table, select the assertion to be removed, then click Remove Selected. To remove all assertions from the table, click Remove All.
If desired, you can also specify an alternate name for the assertion in the Assertion Name field.
-
When you have confirmed the assertions to be attached, click Add Assertion. The attached assertions are listed in a table under the associated policy enforcement endpoint.
-
-
To change the order of the policies and assertions attached to a policy enforcement endpoint, click the options menu
 for the endpoint, then click Reorder. In the Reorder window, select the policy or assertion, then click the up or down arrow to adjust the order as desired. Click OK.
for the endpoint, then click Reorder. In the Reorder window, select the policy or assertion, then click the up or down arrow to adjust the order as desired. Click OK.Policies and assertions are enforced in the order in which they are attached to the endpoint.
-
Click Validate to ensure that the combination of policies and assertions attached to the endpoint is valid.
If there is a validation error, a dialog box displays describing the error. To remove an attached policy/assertion template, click the options menu for the policy or template, then click Delete.
-
Click Apply to attach the policies or assertions to the endpoint.
Note that the same policies and assertions that are attached to the on-request endpoint are automatically attached to the on-response endpoint to secure the response sent back to the client. If the attached policy/assertion does not support response behavior, then the attachment is ignored.
5.3 Attaching Policies and Assertions to Proxy Applications
Proxy applications defined in the MSAS environment specify back-end URLs that will be proxied directly through the Mobile Security Access Server. In this case, the Mobile Security Access Server acts as a forward proxy. The back-end URLs are visible to the client but the requests are proxied through the Mobile Security Access Server.
For proxy applications, you attach policies at the URL level corresponding to the back-end URL. The policy enforcement endpoints to which you can attach policies are:
-
On-Request—Secures the request phase from the client to Mobile Security Access Server using the policies and assertions referenced. Note that the same policies and assertions that are attached to the on-request endpoint are automatically attached to the on-response endpoint to secure the response sent back to the client.
-
Invoke-Proxy—Secures the connection between Mobile Security Access Server and the back-end service using the policies and assertions referenced.
-
On-Response—Secures the response phase from Mobile Security Access Server to the client. If the attached policy or assertion does not have any response behavior, the policy is not enforced.
For a list of the policies and assertions that are supported for MSAS, see "Summary of Supported Policies and Assertions".
To attach policies and assertions to the policy enforcement endpoints of a proxy URL:
-
Navigate to the URLs Summary page for the proxy application to be secured:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed in the MSAS Applications page by using the Search field. See "Searching for MSAS Applications".
-
Click the proxy application icon,
 , or the name of the proxy application that you want to secure.
, or the name of the proxy application that you want to secure. -
In the MSAS Application Details page, click the URLs search icon to display the Proxy URLs Summary page for the proxy application.
-
-
Click the Proxy URL icon,
 , or the name of the URL to be secured to display the URL Policy Configuration page.
, or the name of the URL to be secured to display the URL Policy Configuration page. -
Click the options menu
 for the policy enforcement endpoint to which you want to attach policies or assertions.
for the policy enforcement endpoint to which you want to attach policies or assertions. -
To attach a policy to a policy enforcement endpoint:
-
Click Add Policy to attach a policy. The list of policies is filtered to reflect only the policies that are available for the type of endpoint. For example, only policies that can be attached to invoke the back-end service are listed for the Invoke-Proxy policy enforcement endpoint.
You can use the search field to refine the list of policies displayed. Enter all or part of a policy name in the Search field, select the desired operator, and press the search icon.The results that match the search criteria are displayed in the Search Results table.
Optionally, use the View menu to change the columns displayed, or to change the order of the columns.
-
Select the policy to be attached and click Add Selected.
-
Review the selections in the Selected Policies table. To remove an entry from the table, select the policy to be removed, then click Remove Selected. To remove all policies from the table, click Remove All. Note that if you are adding an assertion, you can also specify an alternate name for the assertion in the Assertion Name field.
When you have confirmed the list of policies to be attached, click Attach Policies.
-
-
To attach an assertion to a policy enforcement endpoint:
-
Click Add Assertion to attach an assertion to the endpoint. The list of assertions is filtered to reflect only the assertions that are available for the type of endpoint, organized by template name. For example, only assertions that can be attached to invoke the back-end service are listed for the Invoke policy enforcement endpoint.
You can use the search field to refine the list of assertions displayed. Enter all or part of an assertion name in the Search field, select the desired operator, and press the search icon.The results that match the search criteria are displayed in the Search Results table.
Optionally, use the View menu to change the columns displayed, or to change the order of the columns.
-
Select the assertion to be attached and click Add Selected.
-
Review the selections in the Selected Assertion Templates table. To remove an assertion from the table, select the assertion to be removed, then click Remove Selected. To remove all assertions from the table, click Remove All.
If desired, you can also specify an alternate name for the assertion in the Assertion Name field.
-
When you have confirmed the assertions to be attached, click Add Assertion.
-
-
To change the order of the policies and assertions attached to a policy enforcement endpoint, click the options menu
 for the endpoint, then click Reorder. In the Reorder window, select the policy or assertion, then click the up or down arrow to adjust the order as desired. Click OK.
for the endpoint, then click Reorder. In the Reorder window, select the policy or assertion, then click the up or down arrow to adjust the order as desired. Click OK.Policies and assertions are enforced in the order in which they are attached to the endpoint.
-
Click Validate to ensure that the combination of policies and assertions attached to the endpoint is valid.
If there is a validation error, a dialog box displays describing the error. To remove an attached policy/assertion template, click the options menu for the policy or template, then click Delete.
-
Click Apply to save the attachments to the URL.
Note that the same policies and assertions that are attached to the on-request endpoint are automatically attached to the on-response endpoint to secure the response sent back to the client. If the attached policy/assertion does not support response behavior, then the attachment is ignored.
5.4 Viewing Policies Attached to an Application
You can view the policies attached to each URL in an application on the URL Policy Configuration page for the URL.
To view the policies attached to a URL in an application:
-
Navigate to the MSAS Applications page:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed by using the Search field. See "Searching for MSAS Applications".
-
-
Click the icon, or the name of the application for which you want to view the attached policies.
-
Click the URLs search icon to navigate to the URLs page for virtual applications or Proxy URLs page for proxy applications.
-
Click the URL or Proxy URL icon, or the URL name, to open the URL Policy Configuration page. The attached policies and assertions are listed in a table under the associated policy enforcement endpoint.
-
To view the details of an attached policy, select the policy in the endpoint table. Policies are indicated with the
 icon.
icon.The policy details are displayed in the right pane. Details are provided in the following tabs.
Tab Description General For attached policies, this tab displays general information about the policy in read-only format, including the name, display name, category, description, whether the policy is enabled, and the type of endpoints to which the policy can be attached, and version information for the policy. Click Versioning History to open the Policy Version History page that you use to view a list of all versions of the policy, view the details of any policy version in read-only format, activate any version of a policy, and delete or export any version of a policy.You cannot edit a policy from the Policy Version History page. You must edit and save the policy in the Policy Details page. For more information, see "Creating and Editing a Policy".
Assertions Click this tab to view the assertions in the policy. Click an assertion to view details about the assertion including the name, the category to which the assertion belongs (for example security/authentication or security/authorization), the type of assertion (for example http-jwt-token), and whether the assertion is enforced. The Details section provides the ability to view the settings for the selected assertion. Assertion template details vary based on the type of assertion. For example, assertions that include message protection will include settings that are specific to message security.
Overrides Click this tab to view the configuration properties for the policy. Configuration properties vary based on the assertion in the policy. Use these fields to override a property on a per-attachment basis. For details about overriding configuration properties in a policy, see "Configuring Policy Overrides". Authorization Note: This tab is available only with the Fine-grained authorization using Oracle Entitlements Server policy and is used to configure fine-grained authorization. For configuration information, see "Configuring Authorization". -
To view the details of an attached assertion, select the assertion in the endpoint table. Assertions are indicated with the
 icon.
icon.The assertion details are displayed in the right pane. Details are provided in the following tabs.
Tab Description General This tab displays details about the assertion including the name, the category to which the assertion belongs (for example security/authentication or security/authorization), the type of assertion (for example http-jwt-token), and whether the assertion is enforced. The Details or Settings section provides the ability to view the settings for the selected assertion. Assertion template details vary based on the type of assertion. For example, assertions that include message protection will include settings that are specific to message security.
Details about each predefined policy and assertion template are provided in Policy and Assertion Template Reference for Oracle Mobile Security Access Server.
Overrides Click this tab to view the configuration properties for the assertion. Configuration properties vary based on the assertion. Use these fields to override a property on a per-attachment basis. For details about overriding configuration properties in a policy, see "Configuring Policy Overrides".
5.5 Configuring Policy Overrides
The configuration properties included with the predefined policies allow you to override certain configuration settings, such as the CSF key used for storing the signature-key password. The scope for the configuration property override value is limited to the specific policy attachment.
You can override the value when you attach the policy to the endpoint as described in this section. Alternatively, you can change the default value of a configuration override property in a policy. If you do so, any endpoint to which you attach the policy can use these values. To edit the configuration property in a policy, see "Creating and Editing a Policy".
Note:
Oracle recommends that you do not edit the predefined policies so that you will always have a known set of valid policies.If you wish to edit a configuration property in a predefined policy, Oracle recommends that you clone the policy and then edit it.
The configuration properties that you can override in a predefined policy are inherited from the assertion templates that are included in the policy. For additional information, see the following topics:
-
"Predefined Policies" and "Predefined Assertion Templates" in Policy and Assertion Template Reference for Oracle Mobile Security Access Server to determine the configuration properties associated with each policy and assertion template.
-
"Assertion Template Configuration Properties" in Policy and Assertion Template Reference for Oracle Mobile Security Access Server for an alphabetized list of the overrideable properties.
-
"Predefined Policies" in Oracle Fusion Middleware Security and Administrator's Guide for Web Services for additional policies and associated configuration properties.
To override configuration properties in an attached policy or assertion:
-
Attach the policy or assertion template to the endpoint as described in "Attaching Policies and Assertions to Virtual Applications" and "Attaching Policies and Assertions to Proxy Applications".
-
Select the policy or template from the list under the policy enforcement endpoint. The details for the policy or template are displayed in the right pane.
-
Click the Overrides tab.
-
Enter the override value in the Value field for the property and click Apply.
The property is overridden on a per-attachment basis.
Note:
You cannot override a property of type "constant".
5.6 Validating Policy Attachments
The type and number of assertions within a policy may be valid and, therefore, a policy may be internally consistent and valid. However, when more than one policy is attached to a policy enforcement endpoint, the combination of policies must also be valid. Specifically, the following must be true:
-
If the On-Request policy enforcement endpoint contains an authentication policy and an authorization policy, the authentication policy must precede the authorization policy. Instructions for reordering policy attachments are provided in "Attaching Policies and Assertions to Virtual Applications" and "Attaching Policies and Assertions to Proxy Applications".
-
Only one security policy or assertion with subtype authentication can be attached to a policy enforcement endpoint.
5.7 Detaching Policies from an Application
To detach a policy from a virtual or proxy application:
-
Navigate to the MSAS Applications page:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed by using the Search field. See "Searching for MSAS Applications".
-
-
Click the icon, or the name of the application for which you want to detach a policy or assertion.
-
Click the URLs search icon to navigate to the URLs page for virtual applications or Proxy URLs page for proxy applications.
-
Click the URL or Proxy URL icon, or the URL name, to open the URL Policy Configuration page. The attached policies and assertions are listed in a table under the associated policy enforcement endpoint.
-
To detach a policy or assertion, click the options icon for the policy or assertion, then click Delete.
-
Click OK in the Delete window.
-
Click Apply to save your changes.
5.8 Configuring Authorization in MSAS Applications
Authorization (also known as access control) is granting access to specific resources based on an authenticated user's entitlements. Entitlements are defined by one or several attributes. An attribute is the property or characteristic of a user, for example, if "Marc" is the user, "conference speaker" is the attribute.
Most often, authentication is the first step of determining whether a user should be given access to a resource. After the user is authenticated, the second step is to verify that the user is authorized to access the resource.
Authorization enables you to determine what operations authenticated clients can access. Mobile Security Access Server uses role-based authorization, which is based on the notion that a set of identities, known as principals, can be grouped into roles, and then a policy can be applied to each of the roles.
The following sections describe how to configure authorization in Mobile Security Access Server:
5.8.1 Managing Roles in an MSAS Application
In Mobile Security Access Server, the scope of an application role is the MSAS application. That is, the roles in one MSAS application apply only to that application and are not visible to other MSAS applications. Application roles are supported in both virtual and proxy applications.
Mobile Security Access Server provides the following functions for application role management:
-
Create, update, delete, and view application roles.
-
Manage application role hierarchy where roles can be combined in a hierarchy where higher-level roles subsume permissions owned by sub-roles.
-
Map external roles to application roles.
-
Map users to application roles.
You manage roles in a MSAS application using the MSAS Application Roles Summary page. From this page you can:
-
View a list of the application roles configured in the application.
-
Search for application roles in the application.
-
Navigate to the Application Roles page where you can create and add roles to an application, edit existing roles, manage application role hierarchy, and map users to application roles.
-
Delete application roles from an application.
5.8.1.1 Creating an Application Role
You create MSAS application roles from the Application Roles Summary page.
To create an MSAS application role:
-
Navigate to the Applications Roles Summary page:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed in the MSAS Applications page by using the Search field. See "Searching for MSAS Applications".
-
Click the application icon, or the name of the application for which you want to create roles.
-
In the MSAS Application Details page, click the Application Roles search icon.
-
-
In the Application Roles Summary page, click +Add Role.
-
In the Application Roles page, enter a name, display name, and description for the application role.
Field Description Name Enter a name for the application role. The name must be unique within the MSAS application. Display Name Optionally, enter a meaningful name that can be used to identify the application role in the console. If you do not provide a display name, the role name is used. Description Optionally, enter a brief description of the role. -
Optionally, position the role being created into the application role hierarchy.
-
Click the App Role Hierarchy tab if it is not already selected.
-
Click Inherits From to specify the application roles from which the role being created should inherit permissions.
-
Enter all or part of a role name in the Search field and click Search. An empty strings fetches all roles in the application. The first five roles are shown.
-
Click Load More Items to display additional roles.
-
Click Add to Hierarchy for each role from which the current role should inherit permissions. The selected roles are added to the App Roles table.
-
Click Inherited By to view the application roles that inherit the permissions of this role.
-
-
Optionally, map external roles to the application role being created.
-
Click the External Role Mapping tab.
-
Enter all or part of an external role name in the Search field and click Search. An empty strings fetches all roles in the application. If necessary, click Load More Items to display additional roles.
-
Select the external role and click Map to Role for each external role that you want to map to the role being created.
-
-
Optionally, map users to the application role being created.
-
Click the User Mapping tab.
-
Enter all or part of a user name in the Search field and click Search. An empty strings fetches all users in the application. If necessary, click Load More Items to display additional users.
-
Select the user and click Map to Role for each user that you want to map to the role being created.
-
-
Click Apply to create the role with specified role hierarchy and mapping.
5.8.1.2 Viewing Roles in an MSAS Application
You can view the roles configured in an MSAS application from the Application Roles Summary page. From there you can click on a specific role to view the configuration details of that role.
To view the configured application roles:
-
Navigate to the MSAS Applications page:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed by using the Search field. See "Searching for MSAS Applications".
-
-
Click the application icon, or the name of the application for which you want to view the details.
-
In the MSAS Application Details page, click the Application Roles search icon to navigate to the Application Roles Summary page where the roles configured in the application are displayed in a table. Only the first 5 roles configured are displayed. To view additional roles, click Load More Items.
-
Optionally, use the Search field to find specific roles by entering all or part of a role name in the Application Roles search field and clicking the Search icon. Wildcards are not recognized and are treated as plain text. Searches are case-insensitive.
-
Click the role icon, the role name, or the options menu then Edit Role to open the Application Roles page
-
Click the App Role Hierarchy, External Role Mapping, and User Mapping tabs to view the role hierarchy and mapping.
5.8.1.3 Managing the Application Role Hierarchy
You can view and modify the role hierarchy of an application role, specifically the hierarchy of application roles below and above a given application role. Roles below a given role inherit the permissions of the selected role; a given role inherits the permissions of roles above it.
5.8.1.3.1 Roles that an Application Role Inherits
To view or modify the application role hierarchy below a given application role:
-
If it is already open, click the App Roles tab for the application to display the Application Roles Summary page.
Otherwise, navigate to the Applications Roles Summary page as described in "Viewing Roles in an MSAS Application".
-
Click the role icon, the role name, or the options menu then Edit Role to open the Application Roles page.
-
Click the App Role Hierarchy tab then Inherits From.
The App Roles table on the right displays the application roles from which the selected role inherits permissions.
-
To add a role to the hierarchy below the current role:
-
Enter all or part of a role name in the Search field and click Search. An empty strings fetches all roles in the application.
The first five roles are shown. If necessary, click Load More Items to display additional roles.
-
Click Add to Hierarchy for each role from which the current role should inherit permissions. The selected roles are added to the App Roles table.
-
-
To remove a role from the hierarchy, select the role in the App Roles list and click Remove.
-
Click Apply to update the role hierarchy.
5.8.1.3.2 Roles that Inherit an Application Role
To view or modify the application role hierarchy above a given application role:
-
If it is already open, click the App Roles tab for the application to display the Application Roles Summary page.
Otherwise, navigate to the Applications Roles Summary page as described in "Viewing Roles in an MSAS Application".
-
Click the role icon, the role name, or the options menu then Edit Role to open the Application Roles page.
-
Click the App Role Hierarchy tab then Inherited By.
The App Roles table displays the application roles that inherit the permissions of the current role.
5.8.1.4 Mapping External Roles to an Application Role
To map external roles to an application role:
-
If it is already open, click the App Roles tab for the application to display the Application Roles Summary page.
Otherwise, navigate to the Applications Roles Summary page as described in "Viewing Roles in an MSAS Application".
-
Click the role icon, the role name, or the options menu then Edit Role to open the Application Roles page.
-
Click the External Role Mapping tab.
-
To map an external role to the current role:
-
Enter all or part of a role name in the Search field and click Search. An empty strings fetches all roles in the application. If necessary, click Load More Items to display additional roles.
-
Click Map to Role for each external role that you want to map to the current role. The selected roles are added to the Mapped Roles table.
-
-
To remove the mapping from an external role, select the role in the Mapped Roles list and click Remove.
-
Click Apply to update the role mapping.
5.8.1.5 Mapping Users to an Application Role
To map users to an application role:
-
If it is already open, click the App Roles tab for the application to display the Application Roles Summary page.
Otherwise, navigate to the Applications Roles Summary page as described in "Viewing Roles in an MSAS Application".
-
Click the role icon, the role name, or the options menu then Edit Role to open the Application Roles page.
-
Click the User Mapping tab.
-
To map users to the current role:
-
Enter all or part of a user name in the Search field and click Search. An empty strings fetches all users in the application. If necessary, click Load More Items to display additional users.
-
Click Map to Role for each user that you want to map to the current role. The selected roles are added to the Mapped Users list.
-
-
To remove the mapping from a user, select the user in the Mapped Users list and click Remove.
-
Click Apply to update the role mapping.
5.8.1.6 Deleting Application Roles
You can delete MSAS application roles from the Application Roles Summary page.
To delete an application role:
-
If it is already open, click the App Roles tab for the application to display the Application Roles Summary page.
Otherwise, navigate to the Applications Roles Summary page as follows:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed in the MSAS Applications page by using the Search field. See "Searching for MSAS Applications".
-
Click the application icon, or the name of the application for which you want to create roles.
-
In the MSAS Application Details page, click the Application Roles search icon.
-
-
In the Application Roles Summary page, click the options menu icon in the row for the role to be deleted and click Delete Role.
-
In the Remove App Role window, click Remove to confirm the deletion.
The role is removed from the table in the Application Roles Summary page.
Note:
If the role that is deleted is inherited by another role, the inheritance is also deleted.
5.8.2 Configuring Authorization
You can configure authorization in Mobile Security Access Server by attaching the predefined authorization policy oracle/binding_oes_authorization_policy to the on-request policy enforcement point of a proxy or virtual URL, and then configuring the policy to specify users and roles that are authorized to access the proxy or virtual URL.
To configure authorization for an application:
-
Navigate to the URL Policy Configuration page for the URL for which you want to configure authorization:
-
From the Oracle Access Management home page, select the Mobile Security tab from the list of tabs at the top of the page.
-
In the Mobile Security Access Server section click Applications. Alternatively, you can click Environments, then click Applications in the MSAS tile.
-
If necessary, narrow the list of applications displayed in the MSAS Applications page by using the Search field. See "Searching for MSAS Applications".
-
Click the application icon, or the name of the application.
-
In the MSAS Application Details page, click the URLs search icon to display the URLs/Proxy URLs Summary page for the application.
-
Click the URL/Proxy URL icon, or the name of the URL to be configured to display the URL Policy Configuration page.
-
-
Click the options menu
 for the On-Request policy enforcement endpoint and select Add Policy.
for the On-Request policy enforcement endpoint and select Add Policy. -
Select the
oracle/binding_oes_authorization_policyfrom the table and click Add Selected, then Attach Policies.Note:
Do not attach this policy to URLs that contain a wildcard*. If you do so the policy will not be enforced at run time. -
Select the Fine-grained authorization using Oracle Entitlements Server policy in the table.
-
In the policy details in the right pane, select the Authorization tab.
-
In the Policy Effect field, select how the policy will govern the access to the protected URL:
-
Permit—Subjects will be permitted to access the protected URL.
-
Deny—Reserved for future use.
-
-
In the Subject field, specify the users for whom the operation selected in the Policy Effect field will be enforced. The subject can be configured as follows:
-
Application Role—The policy will be enforced for all members of the selected application roles.
-
External Role—The policy will be enforced for all members of the selected external roles.
-
User—The policy will be enforced for all selected users.
To select the subjects:
-
Click +Add to display the Add Roles page. By default, the Application Roles search operator is selected and the application roles configured in the application are listed in the Subject table. For details about configuring application roles, see "Managing Roles in an MSAS Application".
-
To add application roles to the subject list, select the roles in the table and click Add Selected.
-
To add external roles to the subject list, enter all or part of a role name in the search Name field, select External Role from the menu, and click Search. An empty strings fetches all external roles in the application. If necessary, click Load More Items to display additional roles. Select the external roles to be added from the table and click Add Selected.
-
To add users to the subject list, enter all or part of a user name in the search Name field, select User from the menu, and click Search. An empty strings fetches all users in the application. If necessary, click Load More Items to display additional users. Select the users to be added from the table and click Add Selected.]
-
Click Add to add the selected roles and users to the subject list.
-
-
If multiple subjects are specified, choose how the policy is enforced:
-
Any—The policy is enforced if at least one of the subject rules is satisfied.
-
All—The policy is enforced if all of the subject rules are satisfied.
Figure 5-1 shows a virtual URL with an attached authorization policy configured to allow access to all members of the Administrators role.
Figure 5-1 OES Authorization Policy Configuration
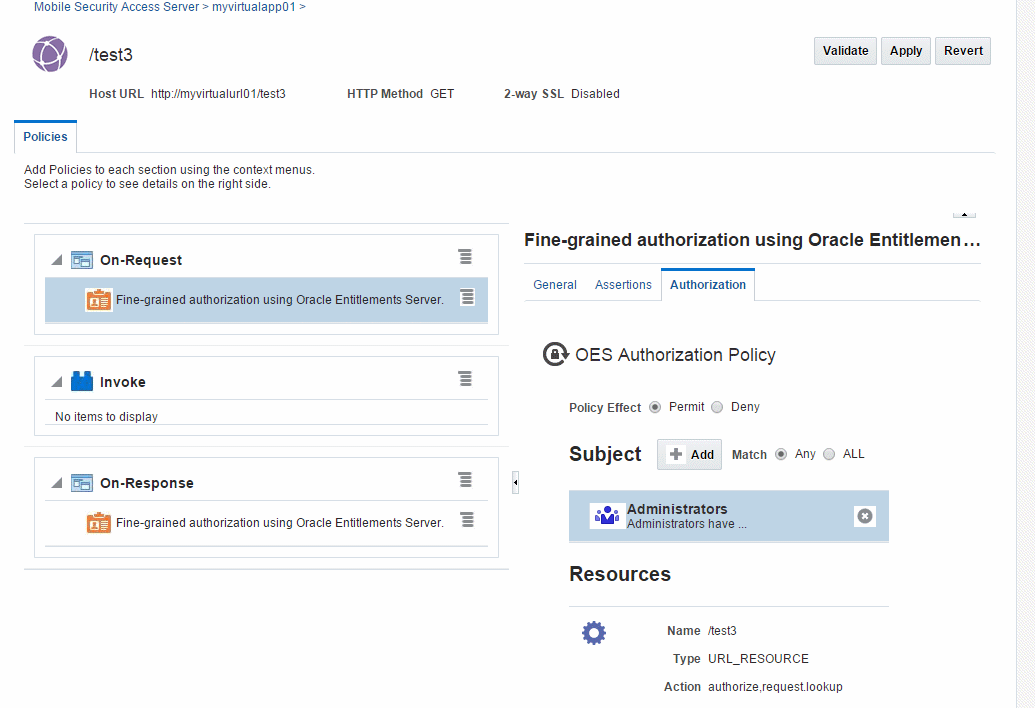
Description of "Figure 5-1 OES Authorization Policy Configuration"
-
-
Click Apply to save the authorization policy attachment and configuration. The authorization policy is automatically attached to the on-response endpoint. Because this policy does not support response behavior, the attachment is ignored.
Note:
You cannot edit a proxy URL that has theoracle/binding_oes_authorization_policyattached. Instead you should delete the URL and add a new proxy URL with the desired changes.
5.9 Summary of Supported Policies and Assertions
The following table summarizes the policies and assertions that are supported by Mobile Security Access Server based on policy enforcement endpoint type.
For more information about the policies and assertions, see:
-
"Predefined Policies" in Policy and Assertion Template Reference for Oracle Mobile Security Access Server
-
"Predefined Assertion Templates" in Policy and Assertion Template Reference for Oracle Mobile Security Access Server
Table 5-1 Supported Policies and Assertions
| Policy Enforcement Endpoint | Supported Policies | Supported Assertions |
|---|---|---|
|
On-request/On-response |
|
|
|
Invoke/Invoke-proxy |
|
|
|
Internal Use Only |
The following policies are used internally by MSAS to secure its instances. Warning: If you attach any of these policies to your policy enforcement endpoint, your endpoint will not be secure. Although the policy attachment will validate at design time, you will receive errors at run time.
|
The following assertions are used internally by MSAS to secure its instances. Warning: If you attach any of these assertions to your policy enforcement endpoint, your endpoint will not be secure. Although the policy attachment will validate at design time, you will receive errors at run time.
|
The following table summarizes the policies and assertions that are not supported by MSAS based on policy enforcement endpoint type.
WARNING:
If you attach any of the policies and assertions defined in Table 5-2 to your policy enforcement endpoint, your endpoint will not be secure. Although the policy attachment will validate at design time, you will receive errors at run time.
Table 5-2 Unsupported Policies and Assertions
| Policy Enforcement Endpoint | Unsupported Policies | Unsupported Assertions |
|---|---|---|
|
On-request/On-response |
The following policies are reserved for future use:
|
The following assertions are reserved for future use:
|
|
Invoke/Invoke-proxy |
The following policies are reserved for future use:
|
The following assertions are reserved for future use:
|