17 Performing Advanced Configuration Tasks for Oracle Privileged Account Manager
This chapter provides information about performing some advanced configuration for Oracle Privileged Account Manager.
This chapter includes the following sections:
-
Section 17.3, "Adding New Connectors to an Existing Oracle Privileged Account Manager Installation"
-
Section 17.6, "Moving from a Test Environment to a Production Environment"
-
Section 17.7, "Rebranding Oracle Privileged Account Manager"
Note:
If you are using Oracle Privileged Account Manager on IBM WebSphere, refer to "Differences in Performing Advanced Configuration Tasks for Oracle Privileged Account Manager on IBM WebSphere" in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for information about this topic.17.1 Configuring Oracle Privileged Account Manager to Communicate With Target Systems Over SSL
Oracle Privileged Account Manager can connect to target systems through Secure Socket Layer (SSL) or non-SSL options. The SSL option is more secure, but requires some additional configuration.
To communicate securely over SSL with a target system, the WebLogic instance running Oracle Privileged Account Manager must trust the SSL certificate used by the target system because Oracle Privileged Account Manager inherits its SSL configuration from the WebLogic container in which it runs. To have the WebLogic instance running Oracle Privileged Account Manager (and therefore Oracle Privileged Account Manager) trust the target system's SSL certificate, you must import the certificate into the truststore used by that WebLogic instance.
Note:
The steps for configuring SSL communication are different if you are using an IBM WebSphere instance.Refer to "Differences When Configuring Oracle Privileged Account Manager to Communicate with Target Systems Over SSL" in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for instructions.
Use the following steps to enable SSL communication between the target system and Oracle Privileged Account Manager:
-
Export the SSL certificate from the target system host computer.
Note:
The steps for exporting an SSL certificate are different for each target system type. Refer to the product documentation provided for your target system for detailed instructions. -
Copy the certificate to the machine where you have the WebLogic instance running Oracle Privileged Account Manager.
If you have the Oracle Privileged Account Manager Console and the Oracle Privileged Account Manager server running on different machines, you must copy the SSL certificate to the Oracle Privileged Account Manager server machine.
-
Run the following command to import the certificate into the JVM truststore of the WebLogic Server on which Oracle Privileged Account Manager is running:
JAVA_HOME\bin\keytool -import -file FILE_LOCATION -keystore TRUSTSTORE_LOCATION -storepass TRUSTSTORE_PASSWORD -trustcacerts -alias ALIAS
Where
-
JAVA_HOME is the location used by your WebLogic server. For example.
-
MW_HOME/jrockit.. -
MW_HOME/jdk.. -
The location where you installed the Java software
-
-
FILE_LOCATION is the full path and name of the certificate file.
-
TRUSTSTORE_LOCATION is one of the following truststore paths:
Table 17-1 Truststore Locations
If you are using: Import the Certificate into the Keystore in This Directory: Oracle jrockit_R27.3.1-jdk
JROCKIT_HOME/jre/lib/securityThe default Oracle WebLogic Server JDK
WEBLOGIC_HOME/java/jre/lib/security/cacertsA JDK other than Oracle
jrockit_R27.3.1-jdk or
Oracle WebLogic Server JDKJAVA_HOME/jre/lib/security/cacerts -
TRUSTSTORE_PASSWORD is the password for the truststore.
-
ALIAS is an alias for the certificate.
Note:
The default password for thecacertskeystore is changeit. -
-
Restart all WebLogic servers.
Note:
For more information about WebLogic security concepts and how to create custom keystores, refer to "Configuring Identity and Trust" in the Oracle Fusion Middleware Securing Oracle WebLogic Server.17.2 Securing Data On Disk
Oracle Privileged Account Manager can operate with or without Oracle Database Transparent Data Encryption (TDE) mode. This feature enables you to protect sensitive data stored in operating system files by encrypting it. Then, to prevent unauthorized decryption, it stores encryption keys in an external security module. Transparent Data Encryption provides the assurance that the data is encrypted, yet handling encrypted data becomes transparent to applications.
Note:
Oracle strongly recommends that you enable TDE mode for enhanced security.For more information about Transparent Data Encryption, refer to the "Securing Stored Data Using Transparent Data Encryption" topic in Oracle Database Advanced Security Administrator's Guide.
You can enable or disable TDE mode at any point after installing and configuring Oracle Privileged Account Manager.
This section describes how to change the TDE mode for Oracle Privileged Account Manager. The topics include:
Note:
The instructions for enabling or disabling TDE mode are essentially the same whether you are using a WebLogic server or an IBM WebSphere server.Refer to "Differences When Securing Data On Disk" in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for information about the minor differences if you are using Oracle Privileged Account Manager on IBM WebSphere.
17.2.1 Enabling TDE Mode
You can enable TDE mode by performing the following steps:
-
Section 17.2.1.2, "Enable Encryption in the Oracle Privileged Account Manager Schema"
-
Section 17.2.1.3, "Enable TDE Mode in the Oracle Privileged Account Manager Server Configuration"
17.2.1.1 Enable TDE in the Database
Enable TDE in the database by referring to one of the following procedures, depending on the Oracle Database version you are using:
-
To enable TDE in Oracle Database Release 11.2, refer to the "Enabling Transparent Data Encryption" section in the Oracle Database Advanced Security Administrator's Guide.
-
To enable TDE in Oracle Database Release 12.1, refer to the "Configuring Transparent Data Encryption" section in the Oracle Database Advanced Security Administrator's Guide.
Note:
-
For additional information about storing data, refer to "Securing Stored Data Using Transparent Data Encryption" in the Oracle Database Advanced Security Administrator's Guide.
-
Enabling TDE involves the creation of an encryption wallet. The wallet is a critical component of TDE, and should always be backed up. If the wallet is lost, encrypted data cannot be recovered. Refer to Oracle's best practices for "Transparent Data Encryption" at the following location:
http://www.oracle.com/technetwork/database/security/twp-transparent-data-encryption-bes-130696.pdf
17.2.1.2 Enable Encryption in the Oracle Privileged Account Manager Schema
You can enable encryption in the Oracle Privileged Account Manager schema by using sqlplus (or any other client) to run the following opamxencrypt.sql script with the Oracle Privileged Account Manager schema user:
IAM_HOME/opam/sql/opamxencrypt.sql
For example,
sqlplus DEV_OPAM/password1 @IAM_HOME/opam/sql/opamxencrypt.sql
17.2.1.3 Enable TDE Mode in the Oracle Privileged Account Manager Server Configuration
You can enable TDE mode in the Oracle Privileged Account Manager server configuration by using one of the following methods:
From the Oracle Privileged Account Manager Console
To enable TDE mode by using the Console, refer to step 3 in Section 5.2.3.1, "From the Console."
From the Oracle Privileged Account Manager Command Line Tool
To enable TDE mode (if the tdemode flag is set to false) by using the command line tool, complete the following steps:
Note:
Before you begin, ensure that the Oracle Privileged Account Manager server is running.-
Set the environment variables,
ORACLE_HOMEandJAVA_HOME. -
Run the following script:
On UNIX, type:
ORACLE_HOME/bin/opam.sh -url OPAM_Server_Url -x modifyconfig -configtype global -propertyname tdemode -propertyvalue true -u OPAM_APPLICATION_CONFIGURATOR_USER -p Password
On Windows, type:
ORACLE_HOME\bin\opam.bat -url OPAM_Server_Url -x modifyconfig -configtype global -propertyname tdemode -propertyvalue true -u OPAM_APPLICATION_CONFIGURATOR_USER -p Password
-
Perform the steps described in the "Optional: Enabling TDE in Oracle Privileged Account Manager Data Store" section of the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
17.2.2 Disabling TDE Mode
You can switch to non-TDE mode by performing the following steps:
-
Section 17.2.2.1, "Disable TDE Mode in the Oracle Privileged Account Manager Server Configuration"
-
Section 17.2.2.2, "Disable Encryption in the Oracle Privileged Account Manager Schema"
17.2.2.1 Disable TDE Mode in the Oracle Privileged Account Manager Server Configuration
You can disable TDE mode in the Oracle Privileged Account Manager server by using one of the following methods:
From the Oracle Privileged Account Manager Console
To disable TDE mode by using the Console, refer to step 3 in Section 5.2.3.1, "From the Console."
From the Oracle Privileged Account Manager Command Line Tool
To disable TDE mode by using the command line tool, complete the following steps:
Note:
Before you begin, ensure that the Oracle Privileged Account Manager server is running.-
Set the environment variables,
ORACLE_HOMEandJAVA_HOME. -
Run the following script:
On UNIX:
ORACLE_HOME/opam/bin/opam.sh -url OPAM_Server_Url -x modifyconfig -configtype global -propertyname tdemode -propertyvalue false -u OPAM_APPLICATION_CONFIGURATOR_USER -p Password
Where
OPAM_Server_Urlis of the form:https://OPAM_Managed_Server_Hostname:OPAM_Managed_Server_SSL_port/opam
On Windows:
ORACLE_HOME\opam\bin\opam.bat -url OPAM_Server_Url -x modifyconfig -configtype global -propertyname tdemode -propertyvalue false -u OPAM_APPLICATION_CONFIGURATOR_USER -p Password
Where
OPAM_Server_Urlis of the form:https://OPAM_Managed_Server_Hostname:OPAM_Managed_Server_SSL_port/opam
17.2.2.2 Disable Encryption in the Oracle Privileged Account Manager Schema
You can disable encryption in the Oracle Privileged Account Manager schema by using sqlplus (or any other client) to run the following opamxunencrypt.sql script with the Oracle Privileged Account Manager schema user:
IAM_HOME/opam/sql/opamxunencrypt.sql
For example,
sqlplus DEV_OPAM/password1 @MW_HOME/Oracle_IDM1/opam/sql/opamxunencrypt.sql
17.3 Adding New Connectors to an Existing Oracle Privileged Account Manager Installation
This section describes the processes for adding new connectors to your existing Oracle Privileged Account Manager installation. The topics include:
17.3.1 Adding Connectors Supplied by Oracle
If you are adding new ICF connectors that are supplied by Oracle, then they will be accompanied by installation instructions. These instructions describe where to store the connector bundle and how to modify the installation specific opam-config.xml file.
17.3.2 Adding Custom Connectors
Oracle Privileged Account Manager can use custom connectors that you created or that were created by a third party. However, these connectors must strictly adhere to the ICF standard. After verifying that the connector is ICF-compliant, perform the following steps to deploy the connector for Oracle Privileged Account Manager consumption:
-
Put the connector bundle in a location on the file system where the bundle can be read by the Oracle Privileged Account Manager at run time.
-
Perform the following steps to create a configuration block for the connector and include that block in the installation specific
opam-config.xmlfile:-
Design and create a relevant configuration block.
Both the
opam-config.xmlandopam-config.xsdfiles contain documentation and an example at the beginning of the file describing how to create a configuration block. -
Ensure that this connector configuration block includes the file system location you specified for the connector bundle in step 1.
-
Add the new connector configuration block to the
opam-config.xmlfile by containing it in a<connectorConfig>block. -
Validate the modified
opam-config.xmlfile against theopam-config.xsdfile to ensure that the Oracle Privileged Account Manager server can read the modified file. You can use your favorite XML schema validation tool for this purpose.
-
-
Restart the Oracle Privileged Account Manager server.
-
Connect to Oracle Privileged Account Manager, and then add and configure a new target system using the newly added connector type.
17.4 Copying Passwords to the Clipboard
See Also:
Section 20.4, "Frequently Asked Questions" for more information about ZeroClipboard and this featureOracle Privileged Account Manager enables an end user to copy any checked out password directly to the clipboard without revealing the password in plain text. This ability provides greater security and eliminates the need to manually type the password to checkout privileged accounts.
This section discusses the following topics:
17.4.1 Downloading and Deploying the ZeroClipboard Library Files on the Server
Before you can copy the checked out passwords to the clipboard, you must deploy the ZeroClipboard library on the server.
Note:
For more information about ZeroClipboard, refer to:You must download and deploy the ZeroClipboard v1.x. library from the following URL:
https://github.com/zeroclipboard/zeroclipboard/tree/1.x-master
To do so:
-
Click the Download ZIP button on the lower-right side of the page and save the ZIP file to a desired location.
-
Extract the contents of the Zip file and locate the zeroclipboard-master directory.
-
Deploy the ZeroClipboard library files on the web application server such as WebLogic, WebSphere, and so on.
The following example explains the procedure to deploy ZeroClipboard library files on the WebLogic server:
-
Create a directory named ZeroClipboard in Oracle Privileged Account Manager, for clipboard operations.
For example:
$ORACLE_HOME/ZeroClipboardNote:
The name of the directory created in this step must be "ZeroClipboard" to allow Oracle Privileged Account Manager to successfully load files from this directory. -
Copy the ZeroClipboard.js and ZeroClipboard.swf files from the zeroclipboard-master directory to the $ORACLE_HOME/ZeroClipboard directory that you created in Step 3a of this procedure. Within the ZeroClipboard directory, create another directory named WEB-INF, such as,
$ORACLE_HOME/ZeroClipboard/WEB-INF -
In the WEB-INF directory, create a file named web.xml with the following content:
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web application 2.3//EN" http://java.sun.com/j2ee/dtds/web-app_2_3.dtd> <web-app> </web-app>
The location of this .xml file must be similar to the following sample location:
$ORACLE_HOME/ZeroClipboard/WEB-INF/web.xml -
Save the web.xml file.
-
Log in to the WebLogic Server Administration console.
-
Click Deployments (in the left pane) and Install, and specify the path to the ZeroClipboard directory you created in Step a.
-
From the listed options, select ZeroClipboard and click Next.
-
Retain the default options in "Install this deployment as an application" and click Next.
-
Select the managed servers that are running Oracle Privileged Account Manager, and click Finish.
-
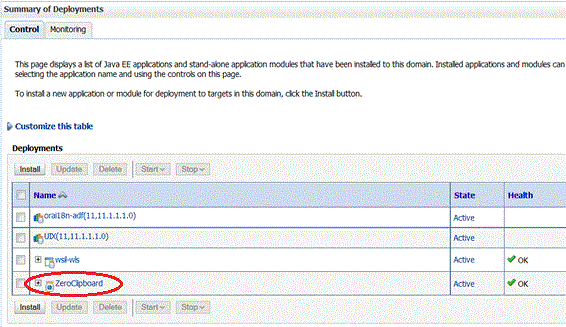
The Deployment Success message will pop-up and you should be able to see ZeroClipboard in the Deployments screen as shown in the screenshot below:
-
17.4.2 Installing the Adobe Flash Plug-in
The Adobe Flash Player plug-in is used to copy passwords to clipboard in Oracle Privileged Account Manager. You must enable the Flash plug-in, download it, and install the latest version of this plug-in on your browser.
Note:
The Flash plug-in installation is required only on the web browser client is used to view the Oracle Privileged Account Manager Console. It is not required on the managed server that is running the application.To download the Flash plug-in and ensure that you have correctly configured the plug-in, refer to:
17.5 Advanced Management of Session Manager Data
This section describes how to manage your Oracle Privileged Session Manager (Session Manager) data. The topics include:
17.5.1 Overview
The Session Manager stores all of its session recording data in the Oracle Privileged Account Manager database schema. Over time, as more information is recorded, the disk footprint for this database schema will grow. Therefore, having a strategy to effectively manage this data is important.
Compliance regulations may require that you store audit data (such as session recordings) for long periods. You need a good backup and recovery plan to protect the data.
A good backup plan accounts for these basic guidelines:
-
Growth rate of session recordings: The growth rate depends on the number of sessions and the type of activity (which results in recordable data) that occurs on those sessions. The growth of the session recording data generated daily determines, in turn, how often you want to perform backups.
-
Compliance regulations: Consult your organization's compliance regulations to determine how frequently backups are required and for how many years session recording storage is mandatory.
-
Online or offline data management: Consult your organization's compliance regulations to determine how frequently backups are required and what portion of session recording data must be easily accessible.
Oracle Database uses Oracle Recovery Manager (RMAN) for backup and recovery.
For details, refer to:
-
http://www.oracle.com/technology/deploy/availability/htdocs/BR_Overview.htm -
http://www.oracle.com/technology/deploy/availability/htdocs/rman_overview.htm
Note:
The Oracle Privileged Account Manager schema is created using the Oracle Repository Creation Utility (RCU) and the session recording data in the Oracle Privileged Account Manager schema is stored in theOPSM_SESSIONS table.17.5.2 Partitioning
The Oracle Privileged Account Manager schema is unpartitioned by default. However, session recording data is cumulative and older data is never removed. If you store a high volume of session recording data, then you should consider partitioning the OPSM_SESSIONS table, which allows for easier archiving.
Benefits of partitioning include:
-
Improved Performance: If a table is range-partitioned by Timestamps, for example, queries by Timestamps can be processed on the partitions within that time-frame only.
-
Better Manageability: You can create partitions on separate tablespaces (thus different disks), which enables you to move older data to slower and larger disks, while keeping newer data in faster and smaller disks.
In addition, partitioning makes archiving much easier. For example, you can compress a single partition rather than having to partition the entire table.
-
Increased Availability: If a single partition is unavailable, for example, and you know that your query can eliminate this partition from consideration, then the query can be successfully processed without needing to wait for the unavailable partition.
17.5.3 Partition OPSM_SESSIONS Table
In this example, the OPSM_SESSIONS table is partitioned on a quarterly basis. Depending on your needs, you can choose to implement a different partitioning scheme.
To minimize application down time, Oracle recommends that partitioning is done before using this schema for an Oracle Privileged Account Manager deployment. If you are partitioning on an active Oracle Privileged Account Manager deployment, then you must first shut down all Oracle Privileged Account Manager processes before proceeding with the following steps.
The partitioning steps are as follows:
-
Login to the database using SQLPlus as the Oracle Privileged Account Manager schema user.
-
Rename the existing unpartitioned table. For example:
RENAME OPSM_SESSIONS TO OPSM_SESSIONS_NONPART;
-
Create a new partitioned table that follows the table structure of the unpartitioned table. This example uses the range-partitioning (by Timestamp) scheme:
CREATE TABLE OPSM_SESSIONS PARTITION BY RANGE (STARTTIME) ( PARTITION OPSM_SESSIONS_DEFAULT VALUES LESS THAN (MAXVALUE) ) AS SELECT * FROM OPSM_SESSIONS_NONPART; -
Enable row movement to allow data to automatically move from partition to partition when new partitions are created. For example:
ALTER TABLE OPSM_SESSIONS ENABLE ROW MOVEMENT;
-
You can now create partitions. In this example, partitions are created by calendar quarter:
ALTER TABLE OPSM_SESSIONS SPLIT PARTITION OPSM_SESSIONS_DEFAULT AT (TO_DATE('01/04/2013', 'DD/MM/YYYY')) INTO (PARTITION OPSM_SESSIONS_Q1_2013, PARTITION OPSM_SESSIONS_DEFAULT) UPDATE INDEXES; ALTER TABLE OPSM_SESSIONS SPLIT PARTITION OPSM_SESSIONS_DEFAULT AT (TO_DATE('01/07/2013', 'DD/MM/YYYY')) INTO (PARTITION OPSM_SESSIONS_Q2_2013, PARTITION OPSM_SESSIONS_DEFAULT) UPDATE INDEXES; ALTER TABLE OPSM_SESSIONS SPLIT PARTITION OPSM_SESSIONS_DEFAULT AT (TO_DATE('01/10/2013', 'DD/MM/YYYY')) INTO (PARTITION OPSM_SESSIONS_Q3_2013, PARTITION OPSM_SESSIONS_DEFAULT) UPDATE INDEXES; ALTER TABLE OPSM_SESSIONS SPLIT PARTITION OPSM_SESSIONS_DEFAULT AT (TO_DATE('01/01/2014', 'DD/MM/YYYY')) INTO (PARTITION OPSM_SESSIONS_Q4_2013, PARTITION OPSM_SESSIONS_DEFAULT) UPDATE INDEXES;
Note:
You should periodically create new partitions for new quarters.17.5.4 Purging
Purging removes the Oracle Privileged Account Manager session recording data from the Oracle Privileged Account Manager schema. Therefore, if you foresee needing to revisit this data at a later point, then use Oracle Recovery Manager (RMAN) for backup and recovery.
Keep in mind that with a range-partitioned table it is much more efficient to drop a partition when you want to remove old data, rather than deleting individual rows.
ALTER TABLE OPSM_SESSIONS DROP PARTITION OPSM_SESSIONS_Q1_2013;
Once partitions are created, you can purge and back up a particular partition. Refer to the Oracle Database documentation for details.
17.5.5 Managing Oracle Text Index for Session Recordings
Oracle Privileged Account Manager uses Oracle Text CONTEXT Index to index session recordings. These indexes (OPSM_SESSIONS_METADATA and OPSM_SESSION_RMETADTA) are used when performing a pattern search for Checkout History.
To maintain these indexes perform the following:
-
Connect to the database using OPAM schema.
-
Find OPAM_BINSTORE_TS_NAME name using the following query:
SELECT UNIQUE TABLESPACE_NAME FROM USER_SEGMENTS where tablespace_name LIKE'%_BINSTORE';
-
Create a storage preference using the commands below. Oracle recommends you to be familiar with BASIC_STORAGE clause of Oracle Text and add more storage clauses if required.
BEGIN ctx_ddl.create_preference('opam_text_storage', 'BASIC_STORAGE'); ctx_ddl.set_attribute('opam_text_storage','I_TABLE_CLAUSE', 'tablespace <OPAM_BINSTORE_TS_NAME> storage (initial 10M next 10M)'); ctx_ddl.set_attribute('opam_text_storage', 'I_INDEX_CLAUSE', 'tablespace <OPAM_BINSTORE_TS_NAME> storage (initial 1M) compress 2'); ctx_ddl.set_attribute('opam_text_storage', 'K_TABLE_CLAUSE', 'tablespace <OPAM_BINSTORE_TS_NAME> storage (initial 10M next 10M)'); ctx_ddl.set_attribute('opam_text_storage', 'R_TABLE_CLAUSE', 'tablespace <OPAM_BINSTORE_TS_NAME> storage (initial 1M) lob (data) store as (cache)'); ctx_ddl.set_attribute('opam_text_storage', 'N_TABLE_CLAUSE', 'tablespace <OPAM_BINSTORE_TS_NAME> storage (initial 1M)'); ctx_ddl.set_attribute('opam_text_storage', 'P_TABLE_CLAUSE', 'tablespace <OPAM_BINSTORE_TS_NAME> storage (initial 1M)'); END; / -
Apply the new storage preference using the following commands:
ALTER INDEX opam_text_storage REBUILD PARAMETERS;
ALTER INDEX opam_text_storage' REBUILD PARAMETERS;
-
Verify that the above tables are moved to the new tablespace by querying USER_SEGMENTS table.
-
Make sure the Text index status is valid after this step.
17.5.5.1 Text Index Optimization
The Text index could become fragmented due to on-going operations on the Text index. Optimizing the text index on regular basis removes the old data and minimizes the fragmentations, which can improve the search performance.To perform this, Oracle Privileged Account Manager has introduced the following Oracle Database scheduler jobs:
-
FAST_OPTIMIZE_METADATA
-
REBUILD_OPTIMIZE_RMETADATA
-
FAST_OPTIMIZE_RMETADATA
-
REBUILD_OPTIMIZE_METADATA
These jobs reside in OPAM database schema and they are disabled by default. Oracle strongly recommends you to view these jobs, make schedule changes if needed and enable them. When changing the schedule, make sure the new schedule is set on the same line as the default schedule.
FAST_OPTIMIZE_METADATA and FAST_OPTIMIZE_RMETADATA meant to be running on frequent basis. By default, it is scheduled to run once a day at 1 AM and 2 AM respectively.
REBUILD_OPTIMIZE_METADATA and REBUILD_OPTIMIZE_RMETADATA does a full optimization and rebuilds the Text index. They are not meant to be running frequent basis. By default, REBUILD_OPTIMIZE_METADATA and REBUILD_OPTIMIZE_RMETADATA is scheduled to run every Sunday at 2 AM and 4 AM respectively. Note that optimization may take a long time if your Text index is big.
Perform the following steps to change the schedule and/or enable these jobs.
Make sure the default schedule (daily 1 AM and 2 AM for FAST and every Sunday 2 AM and 4 AM for REBUILD) is acceptable to your environment. If not, change the schedule. If you are not sure, you can keep the default schedule and change later when needed.
Enable the jobs using the following commands:
.
BEGIN
DBMS_SCHEDULER.ENABLE ('FAST_OPTIMIZE_METADATA');
END;
/
BEGIN
DBMS_SCHEDULER.run_job ('REBUILD_OPTIMIZE_METADATA');
END;
/
.
Note:
The Text index optimization can be done when the server is up and search is taking place.17.5.5.2 Updating the Synchronization Frequency
By default, the index is synchronized every hour. You can update the synchronization frequency by using sqlplus (or any other client) to run the following opamupdateotextind.sql script with the Oracle Privileged Account Manager schema user:
IAM_HOME/opam/sql/opamupdateotextind.sql
For example,
sqlplus DEV_OPAM/pwd1 @IAM_HOME/opam/sql/opamupdateotextind.sql
You must enter the new frequency (in minutes) when prompted.
For more information about Oracle Text CONTEXT Index, refer to "Indexing with Oracle Text" in Oracle Text Application Developer's Guide.
17.6 Moving from a Test Environment to a Production Environment
For information about moving Oracle Fusion Middleware components from one environment to another, refer to "Moving from a Test to a Production Environment" in Oracle Fusion Middleware Administrator's Guide.
For information about moving Identity Management components, including Oracle Privileged Account Manager, from a test environment to a production environment, refer to "Moving Identity Management Components to a Target Environment" in Oracle Fusion Middleware Administrator's Guide.
17.7 Rebranding Oracle Privileged Account Manager
If necessary, you can rebrand the Login and Oracle Privileged Account Manager pages. The following topics contain instructions for changing the page title, branding text, and logo image on these pages:
Tip:
Create a back-up copy before you modify any files.17.7.1 Customizing the Login Page
You configure branding changes for the Login page in the oinav.ear/oiNavApp-war.war/SignIn.jspx file.
To change the Login page title, modify the title in af:document "#{signinBean.signInTitle}".
Refer to the following code sample:
<af:document id="d1" title="#{signinBean.signInTitle}" theme="dark"
initialFocusId="pt1:_pt_it1">
To change the branding text on the Login page, modify the value of af:outputText "#{signinBean.title}", which is defined in the branding facet.
Refer to the following code sample:
<f:facet name="branding">
<af:outputText value="#{signinBean.title}" id="ot1"/>
</f:facet>
To change the logo image on the Login page, perform these steps:
-
Copy the new image, for example
newlogo.png, into the following directory:oinav.ear/oiNavApp-war.war/images
-
To skip the default logo, add the following line to the
oinav.ear/oiNavApp-war.war/SignIn.jspxfile:<f:attribute name="brandingLogoCls" value=""/>
-
If the new logo's image size is larger than the default size 30, add the following line to adjust the header size:
<f:attribute name="globalBrandingSize" value="60"/>
-
Modify the branding facet by replacing
newlogo.png,newlogo mouse over text, andnew branding text.Refer to the following code sample:
<f:facet name="branding"> <af:panelGroupLayout layout="horizontal"> <af:image source="/images/newlogo.png" shortDesc="newlogo mouse over text" id="im1"/> <af:spacer width="5"/> <af:outputText value="new branding text" id="ot1"/> </af:panelGroupLayout> </f:facet>
17.7.2 Customizing the Oracle Privileged Account Manager Page
You configure branding changes for the Oracle Privileged Account Manager page in the oinav.ear/oiNavApp-war.war/opam.jspx file.
Oracle Privileged Account Manager Page Title
To change the page title on the Oracle Privileged Account Manager page, modify the title in af:document "#{resBundle.PRODUCT_OPAM}"
Refer to the following code sample:
<af:document title="#{resBundle.PRODUCT_OPAM}" id="d1" theme="contentBody">
Oracle Privileged Account Manager Branding Text
To change the branding text on the Oracle Privileged Account Manager page, modify the value of af:outputText "#{resBundle.OPAM_PRODUCT_TITLE}", which is defined in the branding facet.
Refer to the following code sample:
<f:facet name="branding">
<af:outputText value="#{resBundle.OPAM_PRODUCT_TITLE}" id="ot1"/>
</f:facet>
Oracle Privileged Account Manager Page Logo Image
To change the logo image on the Oracle Privileged Account Manager page, perform these steps:
-
Copy the new image, for example
newlogo.png, into the following directory:oinav.ear/oiNavApp-war.war/images
-
To skip the default logo, add the following line to the
oinav.ear/oiNavApp-war.war/opam.jspxfile:<f:attribute name="brandingLogoCls" value=""/>
-
If the new logo's image size is larger than the default size 30, add the following line to adjust the header size:
<f:attribute name="globalHeaderSize" value="30"/>
-
Modify the branding facet by replacing
newlogo.png,newlogo mouse over text, andnew branding text.Refer to the following code sample:
<f:facet name="branding"> <af:panelGroupLayout layout="horizontal"> <af:image source="/images/newlogo.png" shortDesc="newlogo mouse over text" id="im1"/> <af:spacer width="5"/> <af:outputText value="new branding text" id="ot1"/> </af:panelGroupLayout> </f:facet>
17.7.3 Customizing the About Oracle Information
This section describes how to hide or replace the About Oracle information.
To Hide the About Oracle Link:
Add the following line in the oinav.ear/oiNavApp-war.war/SignIn.jspx file:
<f:attribute name="manageGlobalNav" value="true"/>
To Replace the About Oracle Link and Text:
-
Extract the contents of the archive from the following location to a temporary folder.
ORACLE_HOME/modules/oracle.idm.uishell_11.1.1/oracle.idm.uishell.war -
Extract the contents of the
/WEB-INF/lib/oracle-idm-uishell.jarfile to a temporary location. -
Search for
ABOUT_ORACLEin thetemplates/IdmSignIn.jspxfiles, and replace the text and destination attribute:<af:commandNavigationItem text="#{resBundle.ABOUT_ORACLE destination="http://www.oracle.com/us/corporate/index.htm" id="_pt_cni1"/> -
Repackage the JAR file and put it in the
/WEB-INF/lib/directory of the extracted Web Archive (WAR) file. -
Repackage the
oracle.idm.uishell.warfile and put it back in its original location.