5 Configuring and Managing the Servers
This chapter provides information that administrators must know to configure and manage an Oracle Privileged Account Manager server and an Oracle Privileged Session Manager (Session Manager) server.
This chapter includes the following sections:
-
Section 5.2, "Managing an Oracle Privileged Account Manager Server"
-
Section 5.3, "Managing the Oracle Privileged Session Manager Server"
Note:
If you are using Oracle Privileged Account Manager on IBM WebSphere, refer to the "Differences in Configuring and Managing the Servers" section in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for information.5.1 Understanding the Servers
This section provides a high-level overview of the following servers:
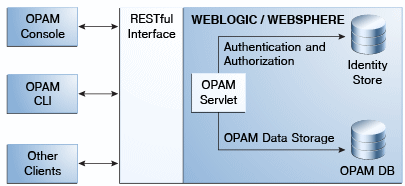
5.1.1 Oracle Privileged Account Manager Server
The Oracle Privileged Account Manager server implements the core functionality of Oracle Privileged Account Manager and makes authorization decisions that determine:
-
Which targets and privileged accounts are exposed to administrators and end-users
-
Which operations administrators and end-users can perform on targets, privileged accounts, and policies
In addition, the Oracle Privileged Account Manager server
-
Supports Usage and Password Policies for accounts
-
Enforces its authorization decisions
-
Supports authentication by using the SAML-based Oracle Security Token from OPSS Trust Services and HTTP-Basic Authentication
-
Supports different Admin Roles for the Oracle Privileged Account Manager server
Note:
For security purposes, the Oracle Privileged Account Manager server only responds to SSL traffic.When you add the Oracle Privileged Account Manager server target to the Oracle Privileged Account Manager user interface or to the Oracle Privileged Account Manager command line tool (CLI), you must provide the SSL endpoint as https://hostname:sslport/opam.
By default, WebLogic responds to SSL using port 7002 on the Admin Server and port 18102 on the Managed Server. You can use the WebLogic console to check the port for your particular instance.
The following figure illustrates the Oracle Privileged Account Manager server architecture.
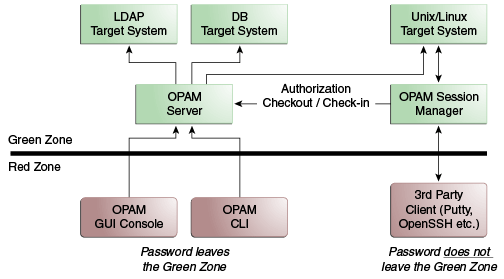
5.1.2 Oracle Privileged Session Manager Server
The Oracle Privileged Session Manager creates a single access point to target resources and enables you to manage privileged sessions to the target system through
-
Session Initiation by
-
Providing a single control point for privileged access
-
Never exposing privileged credentials
-
Supporting any compliant, third-party clients (such as Putty, OpenSSH, etc.)
-
-
Session Control by providing control through policy-based and administrator-initiated session termination and lockout.
-
Session Monitoring and Auditing by maintaining historical records (transcripts) to support forensic analysis and audit data
The following figure illustrates how the Oracle Privileged Session Manager relates to the Oracle Privileged Account Manager server.
5.1.3 Identity Connector Server
An identity connector server is required when an identity connector bundle is not directly executed within Oracle Privileged Account Manager. By using one or more identity connector servers, the ICF architecture permits Oracle Privileged Account Manager to communicate with externally deployed identity connector bundles. Identity connector servers are available for Java™ and Microsoft .NET Framework applications.
For more information refer to "Using an Identity Connector Server" of the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
Connector servers can be configured in Oracle Privileged Account Manager, then Oracle Privileged Account Manager will be able to use the supported connectors that are deployed on the connector server.
Oracle Privileged Account Manager can continue to use the locally available connector JAR to access the target system. Additionally, you can configure more than one connector server, and associate one server with the target system. Oracle Privileged Account Manager will use this server to access the target system.
Note:
For the Windows connector, you must use the .NET based identity connector server to access the target system.5.2 Managing an Oracle Privileged Account Manager Server
This section provides information administrators need to manage an Oracle Privileged Account Manager server, which includes the following topics:
-
Section 5.2.2, "Configuring a Connection to the Oracle Privileged Account Manager Server"
-
Section 5.2.3, "Managing Oracle Privileged Account Manager Server Properties"
5.2.1 Before You Begin
-
You must be an Oracle Privileged Account Manager administrator with the Application Configurator Admin Role to add and manage an Oracle Privileged Account Manager server.
Note:
For more information about this Admin Role, refer to Section 2.3.1, "Administration Role Types" and Section 3.3.4, "Assigning the Application Configurator Role to a User." -
The procedures described in this chapter reference information and instructions contained in the following Oracle publications. If necessary, review the referenced concepts, terminology, and procedures before you begin configuring the Oracle Privileged Account Manager server.
Table 5-1 Reference Information
| For Information About | Refer to |
|---|---|
|
Admin Roles |
Section 2.3.1, "Administration Role Types" and Section 3.3.4, "Assigning the Application Configurator Role to a User" |
|
Oracle WebLogic Server concepts and terminology |
Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help and Oracle Fusion Middleware Securing Oracle WebLogic Server |
|
Adding and managing an Oracle Privileged Account Manager server on IBM WebSphere |
"IBM WebSphere Identity Stores" in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management |
|
Directory structure |
"Oracle Fusion Middleware Directory Structure" in the Oracle Fusion Middleware Installation Planning Guide |
|
Starting WebLogic and Managed Servers |
"Starting or Stopping the Oracle Stack" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management |
5.2.2 Configuring a Connection to the Oracle Privileged Account Manager Server
When you log into Oracle Privileged Account Manager, the Oracle Privileged Account Manager Server URL is automatically detected by default.
Use the following steps to configure a new connection to the Oracle Privileged Account Manager server from the Oracle Privileged Account Manager Console:
-
Open Oracle Privileged Account Manager by logging in to:
http://<opam-managedserver-host>:<opam-managedserver-nonsslport>/oinav/opam
Note:
You must log in as a user with the Application Configurator Admin Role, or the Server Configuration page will not be accessible.For more information about this, and other, Admin Roles refer to Section 2.3.1, "Administration Role Types" and Section 3.3.4, "Assigning the Application Configurator Role to a User."
-
When the Oracle Privileged Account Manager Console is displayed, select Server Connection from the Configuration accordion.
-
When the Server Connection page is displayed, notice that the Oracle Privileged Account Manager Server URL is displayed as the Auto-Detect URL.
To add a different server, enter that server's Host name and SSL Port number.
Note:
You must provide a fully qualified host name for the Host value. Using localhost can cause problems, such as described in Section 20.3.13, "Cannot Open Session or Video Recordings." -
Click the Test button to test the connection settings.
If the server configuration tested successfully, a "
Test Succeeded" message is displayed. -
Click the Apply button to save this connection information.
5.2.3 Managing Oracle Privileged Account Manager Server Properties
You can use the Console or properties in the OPAM Global Config configuration entry to define server-level behavior for activities such as scheduler intervals, timeouts, etc. The available server properties are explained in detail in Section 5.2.3.1, "From the Console."
You can manage server properties defined in the OPAM Global Config configuration entry from two locations:
5.2.3.1 From the Console
Use the following steps to manage the Oracle Privileged Account Manager server properties from the Oracle Privileged Account Manager Console:
-
Open Oracle Privileged Account Manager by logging in to:
http://<opam-managedserver-host>:<opam-managedserver-nonsslport>/oinav/opam
Note:
You must log in as a user with the Application Configurator Admin Role, or the Server Configuration page will not be accessible.For more information about this, and other, Admin Roles refer to Section 2.3.1, "Administration Role Types" and Section 3.3.4, "Assigning the Application Configurator Role to a User."
-
When the Oracle Privileged Account Manager Console is displayed, select Server Configuration from the Configuration accordion.
-
When the Server Configuration page is displayed, you can modify any of the following server property options:
-
Usage policy enforcement interval in seconds. Specify an interval (in seconds) in which Oracle Privileged Account Manager checks accounts and then automatically checks-in the accounts that have exceeded the expiration time defined in the Usage Policy. (Default is
3600seconds) -
Password policy enforcement interval in seconds. Specify an interval (in seconds) in which Oracle Privileged Account Manager checks and then resets the password for any accounts that have exceeded the maximum password age defined in the Password Policy. (Default is
3600seconds) -
Target connection timeout in seconds. Specify an interval (in seconds) in which Oracle Privileged Account Manager allows an ICF connector to wait for a response from the target system to which it is connecting.
The default value for this setting is
20seconds, but in some deployments where network latency is high and target systems take longer to respond, you may need to increase this value. -
Require TDE enabled backend. Check this box to enable Oracle Privileged Account Manager to use Transparent Data Encryption (TDE) mode. The default is TDE mode enabled.
Enabling TDE ensures that all sensitive information stored by Oracle Privileged Account Manager (such as account passwords) is encrypted on disk.
Unchecking the box disables TDE mode.
Note:
Oracle strongly recommends that you enable TDE mode for enhanced security.Refer to Section 2.4.7, "Hardening the Back-End Oracle Privileged Account Manager Database" for more information about using TDE mode.
-
User's password retrieval option. Choose one of the following options from this menu to configure a password display option for users:
-
Enable show password. Provides only the Show Password button on the Checkout Account dialog. Users can click this button to view the account password, in clear text, directly on the dialog.
-
Enable copy password. Provides only the Copy Password button on the Checkout Account dialog. Users can click this button to copy the password to their clipboard for use.
-
Enable show password and copy password. Provides both a Show Password button and a Copy Password button on the Checkout Account dialog. Users can click the Show Password button to view the account password directly in the dialog box or click the Copy Password button to copy the password to their clipboard
-
-
Identity Store search filter. Enter one of the following values to configure how Oracle Privileged Account Manager searches the Identity Store:
-
beginswith(Default). Oracle Privileged Account Manager searches for the results that begin with the keyword. -
contains. Oracle Privileged Account Manager searches for results which contain the keyword.
-
-
Resource lock wait timeout in seconds: Specify an interval (in seconds) which defines the maximum time allowed for an operation to obtain a transaction lock on a resource. (Default is
120seconds.)
-
-
When you are finished, click the Apply button to save these configuration settings.
5.2.3.2 From the Command Line
To access the OPAM Global Config configuration entry and modify these server properties, use the getconfig and the modifyconfig commands from the command line.
Note:
Refer to Section A.2.1, "getconfig Command" and Section A.2.3, "modifyconfig Command" for detailed information about using these commands.
Refer to Section 17.2, "Securing Data On Disk" for more information about enabling or disabling TDE mode from the command line.
5.3 Managing the Oracle Privileged Session Manager Server
This section provides information administrators need to manage a Session Manager Server, which includes the following topics:
-
Section 5.3.2, "Configuring a Connection to the Oracle Privileged Session Manager Server"
-
Section 5.3.3, "Managing the Oracle Privileged Session Manager Properties"
5.3.1 Before You Begin
-
You must be an administrator with the Application Configurator Admin Role or the Security Administrator role to view the Session Manager Configuration page.
-
Only administrators with the Application Configurator Admin Role can modify any of the settings on the Session Manager Configuration page.
Note:
For more information about these Admin Roles refer to Section 2.3.1, "Administration Role Types" and Section 3.3.4, "Assigning the Application Configurator Role to a User."5.3.2 Configuring a Connection to the Oracle Privileged Session Manager Server
Use the following steps to configure the Oracle Privileged Session Manager server from the Oracle Privileged Account Manager Console:
-
Open Oracle Privileged Account Manager by logging in to:
https://<opam-managedserver-host>:<opam-managedserver-sslport>/opam
-
When the Oracle Privileged Account Manager Console is displayed, select Session Manager Configuration from the Configuration accordion.
Use the properties on the Session Manager Configuration page to configure the Session Manager. Refer to Section 5.3.3, "Managing the Oracle Privileged Session Manager Properties" for instructions.
Note:
You cannot run two instances of Oracle Privileged Session Manager on the same machine.5.3.3 Managing the Oracle Privileged Session Manager Properties
Use the following steps to manage the Session Manager properties from the Oracle Privileged Account Manager Console:
Note:
-
You can also configure Session Manager properties by using the Oracle Privileged Account Manager RESTful interface. Refer to Appendix B, "Working with Oracle Privileged Account Manager's RESTful Interface" for more information.
-
You cannot use the Oracle Privileged Account Manager Command Line Tool (CLI) to configure Session Manager properties.
-
Open Oracle Privileged Account Manager and navigate to the Session Manager Configuration page as described in Section 5.3.2, "Configuring a Connection to the Oracle Privileged Session Manager Server."
-
When the Session Manager Configuration page is displayed, configure the following options:
-
Session Monitoring Update Interval in seconds. Specify an interval (in seconds) in which Session Manager checks all checked-out sessions and updates their transcripts. Session Manager automatically terminates any sessions that have exceeded the expiration time defined in the Usage Policy. (Default is
60seconds). -
Max recording size per Session. Specify the maximum recording size that is allowed per session (in KB). This recording size limits how much data a user can use after checking out a session. When this quota is reached, the session is automatically terminated. The default is values is 10240.
-
Oracle Privileged Account Manager URLs. Use this table to manage an array of Oracle Privileged Account Manager servers to which Session Manager can connect:
Note:
Notice that the Oracle Privileged Account Manager Server URL is displayed by default in the first row of the table, as the Auto-Detect URL.Clicking the Add button removes the Auto-Detect URL. After adding one or more rows to the table, you must click Remove and remove all rows to use the Auto-Detect URL instead. The Auto-Detect URL is only displayed when the table is empty.
The Oracle Privileged Account Manager Server URL is multi-valued to allow for High Availability (HA).
Session Manager maintains the server list and, when required, uses it on a round-robin basis for connections to Oracle Privileged Account Manager. Connection attempts are made against all configured servers until one succeeds or all configured URLs are exhausted.
-
To add one or more Oracle Privileged Account Manager Server URLs, click Add.
When the new row is displayed in the table, enter the URL of an Oracle Privileged Account Manager server into the blank field. For example,
https://<opamserver_host>:<port>/opam
-
To delete one or more Oracle Privileged Account Manager Server URLs from the table, select the row and click Remove.
-
-
SSH Configuration. Use the following options to configure the connection details to be displayed for session checkouts:
-
Listener Port: Provide the reserved SSH port on which the Session Manager listener protocol is listening. The value must be greater than 1024 and it defaults to 1222.
-
Session Checkout Instructions: Enter an instruction message to be displayed when users check out a session. This message should describe the information a user must provide to connect to the Session Manager server by using a regular SSH client.
For example:
ssh -p <port> <opamuser>:<targetname>:<accountname>@<sessionmgrhost>Use opam password on password prompt
-
Note:
Windows Agent Count is the number of windows agents deployed. This is a read only field. -
-
When you are finished, click the Apply button to save these configuration settings.
-
Restart Oracle Privileged Account Manager.
Note:
Any time you change the Session Manager configuration, you must restart Oracle Privileged Account Manager for the changes to take effect.For the detailed instructions you need to check out and check in sessions, refer to Section 14.7, "Checking Out Privileged Account Sessions."
5.4 Managing a Connector Server
This section discusses the following topics:
-
Section 5.4.1, "Installing and Configuring a Connector Server"
-
Section 5.4.3, "Managing a Connector Server Configuration in Oracle Privileged Account Manager"
5.4.1 Installing and Configuring a Connector Server
The following is an overview of the procedure to configure the Connector Server:
-
Section 5.4.1.1, "Installing and Configuring The Connector Server"
-
Section 5.4.1.2, "Configuring SSL Between the Connector Server and the Windows Target"
5.4.1.1 Installing and Configuring The Connector Server
Identity connector servers are available for Java™ and Microsoft .NET Framework applications. See one of the following references depending on the requirements in your environment:
-
For Java based connector server, refer to the "Using the Java Connector Server" section of the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
-
For .NET based connector server refer to the "Using the Microsoft .NET Framework Connector Server" section of the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
The Windows Local connector is implemented in .NET. You must therefore deploy this connector to a .NET framework-based Connector Server.
Before you deploy the .NET Connector Server, check if you have installed Microsoft .NET Framework 4.5 on the same computer where you are installing the Connector Server.
If you are using .NET version 4.0 or above, perform the following steps in the .NET Connector Server configuration file(ConnectorServer.exe.config):
-
Search for startup.
-
Replace content between <startup> and </startup> with the following:
Note:
While configuring the Connector Server on a Windows platform, the version for the supportedRunTime parameter must be listed from the highest version to the lowest version.In other words, the supported runtime version must be listed in the descending order.
<startup> <supportedRuntime version="v4.0" sku=".NETFramework,Version=v4.5"/> <supportedRuntime version="v4.0" sku=".NETFramework,Version=v4.0"/> <supportedRuntime version="v2.0.50727"/> </startup> -
Specify a port for the connector server in the connector configuration file. The port is required for the Windows connector to connect to the Windows Connector server:
<add key="connectorserver.port" value="8759" /> -
In the command line, set a custom key for the .NET Connector Server. You must use the /setkey command-line argument, as described in the following procedure:
-
Navigate to the directory where the .NET Connector Server was installed. The default directory is
C:\Program Files\Identity Connectors\Connector Server. -
Run the following command:
ConnectorServer.exe /setkey NEW_KEYIn this command, NEW_KEY is the value for the new key. This key is required by Oracle Privileged Account Manager to connect to the .NET Connector Server.
-
-
Save the file.
-
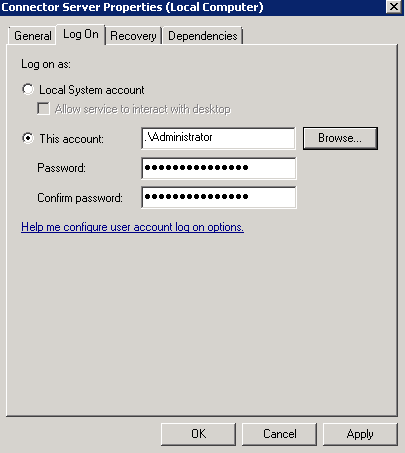
When managing the domain accounts with non-admin (delegated user) then you must start the Connector Server with Admin User Privileges.
Figure 5-3 shows how to start the Connector Server with Admin User Privileges.
Note:
To run the Connector Server service from the console or directly from command line, it must be run as an administrative user.You can start this by performing one of the following procedures:
-
From the Microsoft Services Console:
-
Right click the Connector Server, and click Properties.
-
Navigate to the Log on tab and select the This Account option for log on. Provide the credentials of a user who is a member of the Administrators group. Then, start the connector server.
-
-
From the Command Line: Login to the connector server machine with the credentials of a user who is a member of Administrators group. Open the console and navigate to the directory where the .NET Connector Server was installed. From this directory, run the following command:
ConnectorServer.exe /run
5.4.1.2 Configuring SSL Between the Connector Server and the Windows Target
The connection from the connector server to the target Windows machine is always secure. The Windows connector uses the "ADS_SECURE_AUTHENTICATION" option.
Refer to the "ADS_SECURE_AUTHENTICATION" section in the following link for more information:
http://msdn.microsoft.com/en-us/library/aa772247%28v=vs.85%29.aspx
Note:
Using "Secure Socket Layer (SSL)" is not supported as this option is not allowed by the WinNT API used by the connector. However, as mentioned in this section, the connection from the connector server to the Windows target is still secure.5.4.1.3 Configuring SSL Between Oracle Privileged Account Manager and the .NET Connector Server
To configure the SSL between Oracle Privileged Account Manager and the .NET connector server, you must perform the following procedure:
-
On the Windows machine hosting the connector server, export the certificate. To do so:
-
Click Start and then Run.
-
Enter the following command, and then click OK:
mmcThe Microsoft Management Console is displayed.
-
From the File menu, select Add/Remove Snap-in.
-
In the Add or Remove Snap-ins dialog box, select Certificates from the available snap-ins list, and then click Add.
-
In the Certificates snap-in dialog box, select Computer account, and then click Next.
-
In the Select Computer dialog box, select Local computer, and then click Finish.
-
In the Add or Remove Snap-ins dialog box, click OK.
-
In the left pane of the Console Root window, expand Certificates (Local Computer), Personal, and then select Certificates. All requested certificates will be displayed in the right pane.
-
Right-click the certificate, select All Tasks, and then click Export. The Certificate Export Wizard is displayed.
-
On the Welcome to the Certificate Export Wizard page, click Next.
-
On the Export Private Key page, select the No, do not export the private key option, and then click Next.
-
On the Export File Format page, select Base-64 encoded X.509(.CER) and click Next.
-
On the File to Export page, in the File name field, enter the name and location to which the certificate must be exported and then click Next. The following is a sample location:
C:\ WindowsLocalCer -
On the Completing the Certificate Export Wizard page, click Finish.
A dialog box with a message that the export was successful is displayed.
-
Click OK.
-
-
Configure the connector server for SSL. To do so:
-
Create a certificate store and add the certificate created in Step 1 of this procedure. To add a certificate store:
In a command window, enter the following:
C:\>certutil -f -addstore sslstore C:\WindowsLocalCer.cerThis command creates a new certificate store with the name 'sslstore' and adds the certificate WindowsLocalCer.cer to this store.
Note:
-
Ensure that the certificate store with the name mentioned in the preceding command does not already exist. In other words, the certificate store mentioned in the ConnectorServer.exe.Config file must have only one certificate. If there are more than one certificates, then the Connector Server will not start.
Run the following command to view the number of certificates present in the certificate store:
C:\>certutil -viewstore STORE_NAM -
If the certificate has been exported with a private key (for example, .pfx file), then you must import it into the certificate store named 'sslstore' using the MMC console.
-
-
Navigate to the location where Connector Server is installed and locate the ConnectorServer.exe.Config file.
-
In a text editor, open the ConnectorServer.exe.Config file for editing and change the values of the following lines:
From:
<add key="connectorserver.usessl" value="false" /> <add key="connectorserver.certificatestorename" value="ConnectorServerSSLCertificate" />
To:
<add key="connectorserver.usessl" value="true" /> <add key="connectorserver.certificatestorename" value="sslstore" />
-
Restart the Connector Server.
-
-
Configure Oracle Privileged Account Manager for SSL.
Import the target system certificate into the JDK used by Oracle Privileged Account Manager. To do so:
-
Copy the certificate generated in Step 1 of this procedure to the computer on which Oracle Privileged Account Manager is deployed.
-
Import the target system certificate into the JDK used by Oracle Privileged Account Manager (running on Oracle WebLogic Application Server) by running the following command:
keytool -import -keystoreMY_CACERTS-fileCERT_FILE_NAME-storepassPASSWORDIn the above command, MY_CACERTS is the full path and name of the certificate store. CERT_FILE_NAME is the full path and name of the certificate file, and PASSWORD is the password of the keystore.
The following is a sample command:
keytool -import -keystore /home/OPAM/jrockit_160_14_R27.6.5-32/jre/lib/security/cacerts -file /home/WindowsLocalCer.cer -storepass changeit
Note:
For more information on adding an SSL certificate to the Oracle Privileged Account Manager certificate store, refer to Section 17.1, "Configuring Oracle Privileged Account Manager to Communicate With Target Systems Over SSL." -
5.4.1.4 Enabling Logging
For information about enabling logging in the .NET connector server, refer to the "Configuring Trace Settings" section of Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
The Windows connector uses the built-in logging mechanism of the .NET framework. The log level is set in the .NET Connector Server configuration file (ConnectorServer.exe.config).
To enable logging for the Windows Local connector:
-
Go to the directory where the ConnectorServer.exe.config file is installed. The default directory is C:\Program Files\Identity Connectors\Connector Server. The ConnectorServer.exe.config file must be present in this directory.
-
In the ConnectorServer.exe.config file, add the lines shown in bold text:
<system.diagnostics> <trace autoflush="true" indentsize="4"> <listeners> <remove name="Default" /> <add name="myListener" type="System.Diagnostics.TextWriterTraceListener" initializeData="c:\connectorserver2.log" traceOutputOptions="DateTime"> <filter type="System.Diagnostics.EventTypeFilter" initializeData="Information" /> </add> </listeners> </trace> <switches> <add name="WindowsLocalSwitch" value="4" /> </switches> </system.diagnostics>The
value="4"sets the log level to Verbose. This value can be set as follows:Value Log Level value="4" or value="Verbose"
Verbose level. Most granular.
value="3" or value="Information"
Information level.
value="2" or value="Warning"
Warning level.
value="1" or value="Error"
Error level.
value="0"
No logging.
However, remember that the logging level has a direct effect on the performance of the .NET Connector Server.
-
You must stop and then restart the .NET Connector Server service.
5.4.2 Installing the Windows Connector
Oracle Privileged Account Manager can support the management of Windows local accounts using the Windows connector based on Identity Connector Framework (ICF).
The Windows connector is based on the Microsoft .NET Framework. It requires to be deployed on a .NET connector server.
5.4.2.1 Installing the Connector in the Connector Server
The following is the procedure to configure the Windows Connector. To install the connector in the connector server:
-
Stop the Connector Server.
-
Copy the "WindowsLocal.Connector-1.0.0.0.zip" file from the following location to the Windows target machine:
$ORACLE_HOME\opam-connectors\msft_windowslocal\bundle -
Unzip the .zip file and copy all the contents to
C:\Program Files\Identity Connectors\Connector Server. -
Restart the Connector Server.
5.4.3 Managing a Connector Server Configuration in Oracle Privileged Account Manager
The connector server is configured by specifying values for the properties mentioned in Table 5-3.
Table 5-3 Connector Server Configuration Properties
| Property | Description |
|---|---|
|
Name |
Name for the configuration |
|
Description |
Description of the configuration |
|
Host |
The connector server host |
|
Port |
The connector server port |
|
Server Key |
The key that is used to connect to the connector server |
|
SSL |
SSL enabled/disabled |
|
Timeout in Seconds |
Timeout in seconds for a connector server operation |
Refer to "Working with Oracle Privileged Account Manager's RESTful Interface" for more information about configuring connector servers through the RESTful Interface.
5.4.3.1 Managing a Connector Server Configuration
You can perform the following actions to manage the connector server configuration from the console:
-
Section 5.4.3.1.1, "Creating a Connector Server Configuration"
-
Section 5.4.3.1.2, "Opening a Connector Server Configuration"
-
Section 5.4.3.1.3, "Deleting a Connector Server Configuration"
5.4.3.1.1 Creating a Connector Server Configuration
You can create a connector server configuration from the console by specifying values in the Connector Server Configuration page, as described in the following procedure:
Note:
Only administrators with the Application Configurator Admin Role can create connector server configurations.-
Select Connector Server Configuration in the Configuration accordion.
-
When the Connector Server Configuration page is displayed, click Create in the Search Results toolbar.
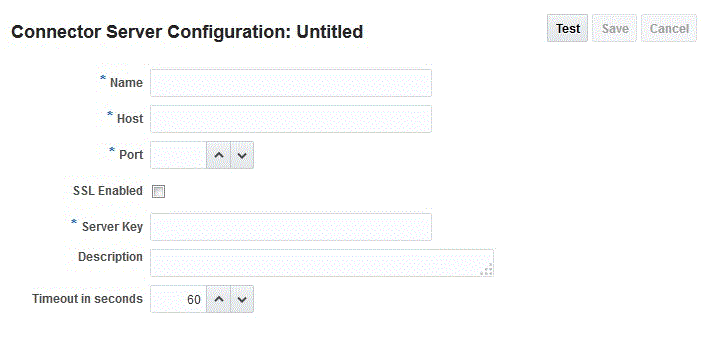
-
A new "Connector Server Configuration: Untitled" page is displayed. You can configure the Connector Server by specifying values for the properties displayed in this page.
Figure 5-4 shows the untitled connector server configuration page.
See Also:
Table 5-3, "Connector Server Configuration Properties" for detailed information about the configuration properties for a connector server -
After specifying the values, click Test to check if the configuration is successful. If a test fails, the "Test Failed" message is displayed it the dialog box. In this case, reconfigure the values and retry. If the test is successful, the "Test succeeded" message is displayed it the dialog box.
-
To save a successful connector server configuration, click Save.
5.4.3.1.2 Opening a Connector Server Configuration
You can search for and open a connector server configuration from the console as described in the following procedure:
-
Select Connector Server Configuration in the Configuration accordion.
-
When the Connector Server Configuration page is displayed, use the Search portlet parameters to configure your search.
For example:
-
To search for the "TestConnectorServer" configuration, you can type t, test, or testconnector into the Name field.
-
To search for all existing connector server configurations, do not specify any search parameters.
-
-
Click Search. The results will be populated in the Search Results table.
5.4.3.1.3 Deleting a Connector Server Configuration
You can delete a connector server configuration from the console as described in the following procedure:
Note:
Only administrators with the Application Configurator Admin Role can delete connector server configurations.-
Select Connector Server Configuration in the Configuration accordion.
-
When the Connector Server Configuration page is displayed, use the Search portlet to locate the configuration you want to delete.
-
Select the "Row number" of the connector server configuration number from the Search Results table and then click Delete.