4 High Availability, Backup and Restore Operations
Oracle Key Vault may be configured for high availability and automatic backups for continuous, reliable, and protected access to security objects with minimum downtime.
4.1 Why High Availability?
With data centers geographically dispersed around the globe there is an increased need for data to be reliably accessible, on-demand, at any time. Users carrying out business-critical operations need data to be accessible and recoverable with minimum downtime. These requirements are met in a high availability deployment.
You achieve high availability by adding redundancy in the form of a standby server, that can take over the functions of the primary server in case of failure. The standby server helps you eliminate single points of failure and reduce server downtime, two main reasons to deploy Oracle Key Vault in a high availability configuration.
Parent topic: High Availability, Backup and Restore Operations
4.2 About High Availability for Oracle Key Vault
A high availability Oracle Key Vault deployment consists of two Key Vault peer servers called primary and standby. The primary is the active server servicing endpoint requests. The standby takes over if the primary fails.
- How High Availability for Oracle Key Vault Works
- Configuring High Availability
- Switching Primary and Standby Servers
- Restoring High Availability After a Failover
- Disabling High Availability
- High Availability Read-Only Restricted Mode
Parent topic: High Availability, Backup and Restore Operations
4.2.1 How High Availability for Oracle Key Vault Works
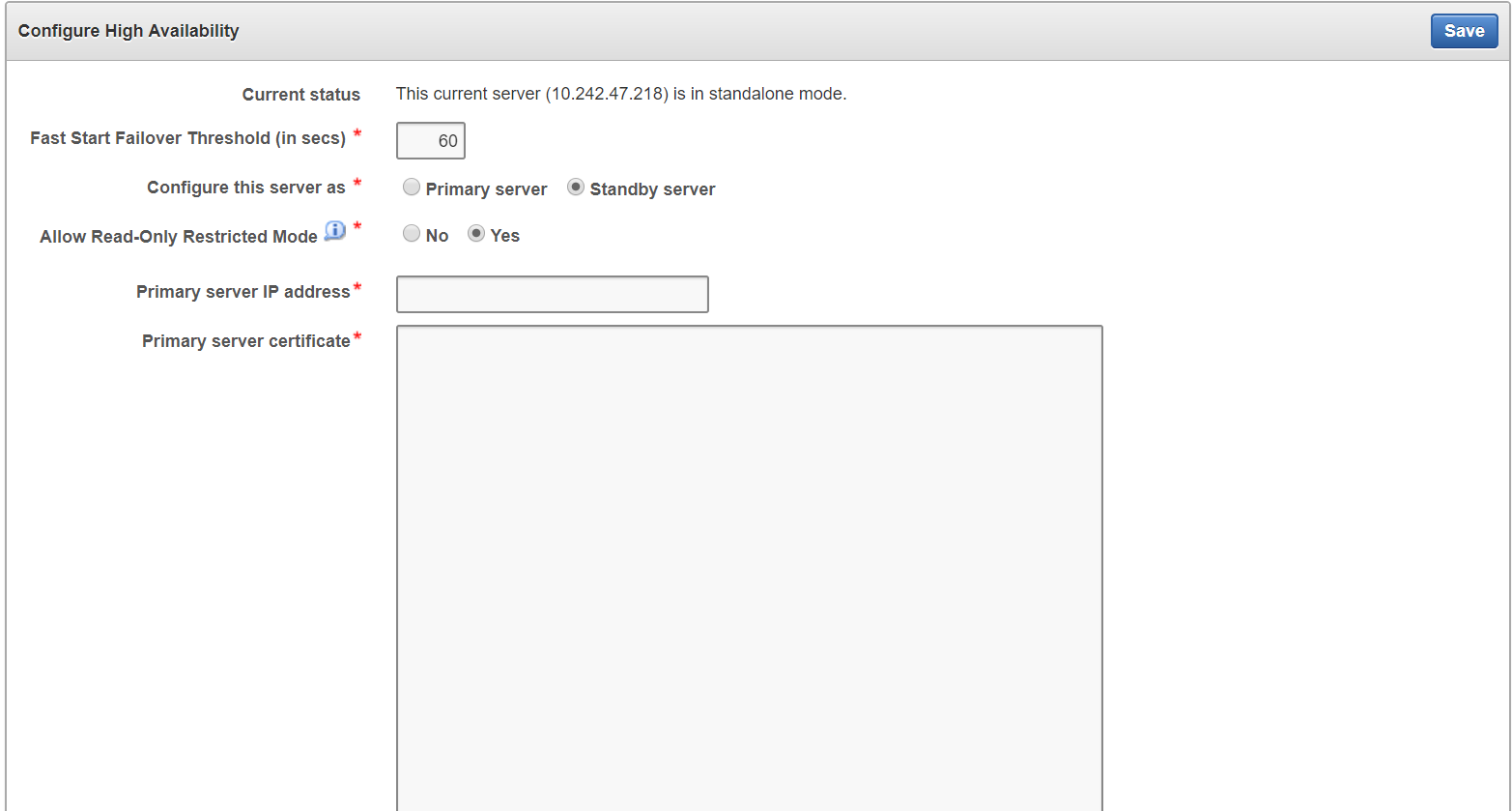
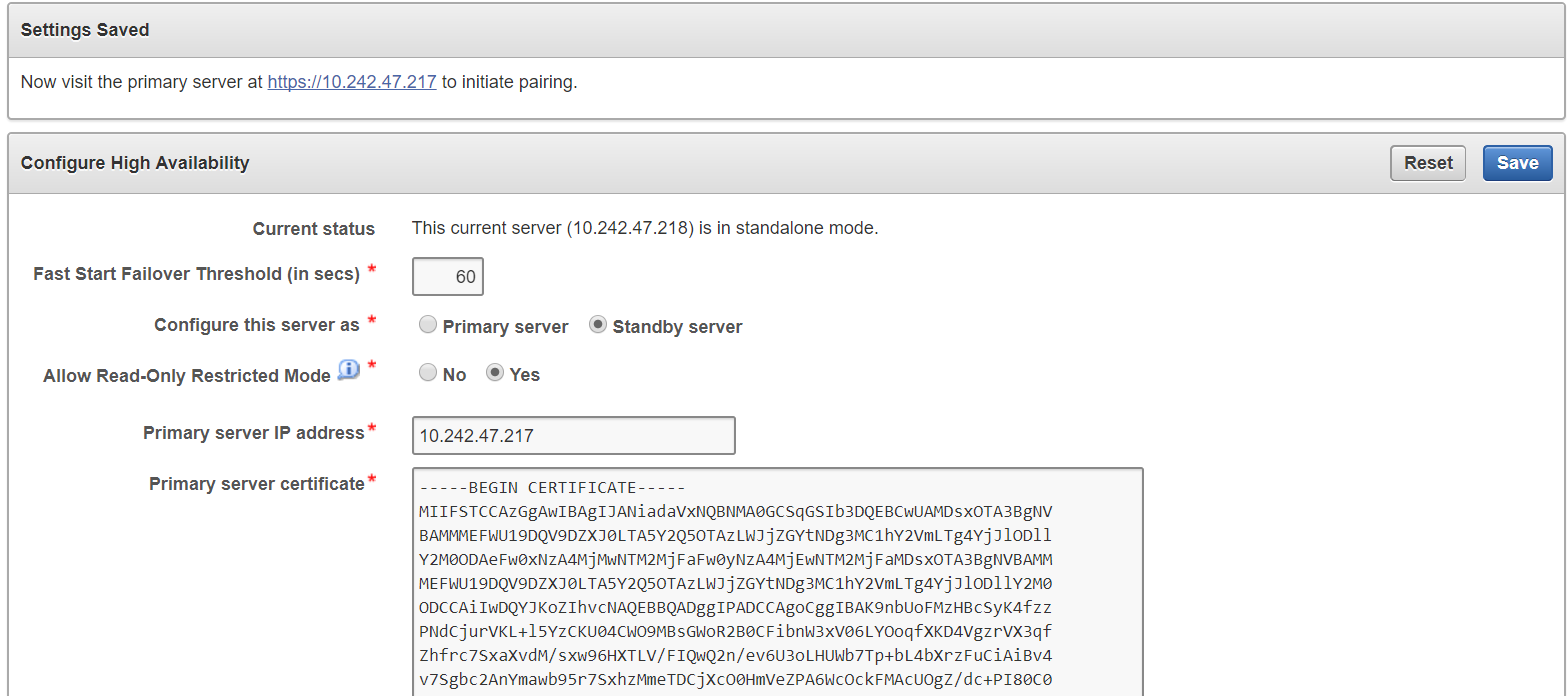
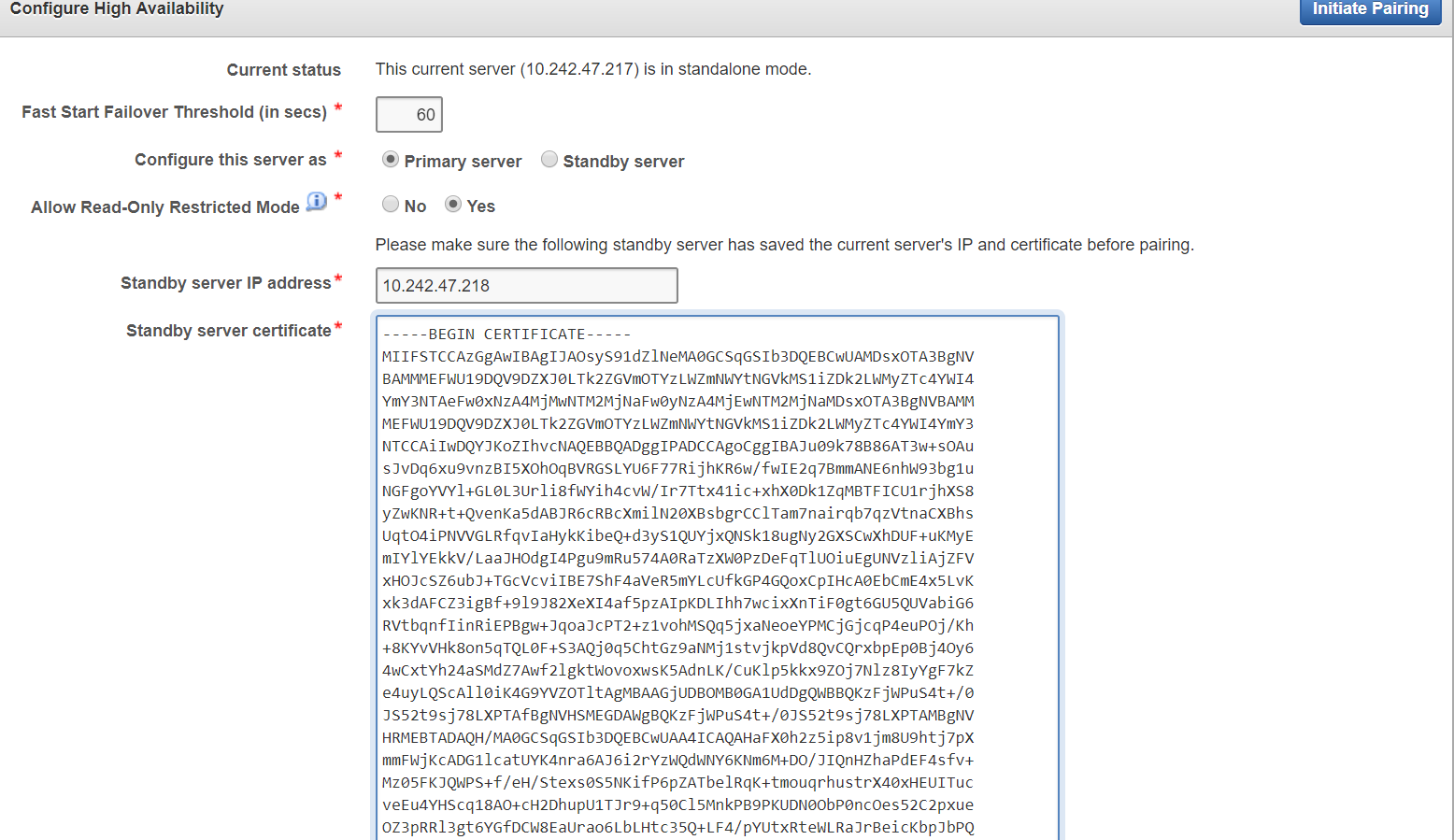
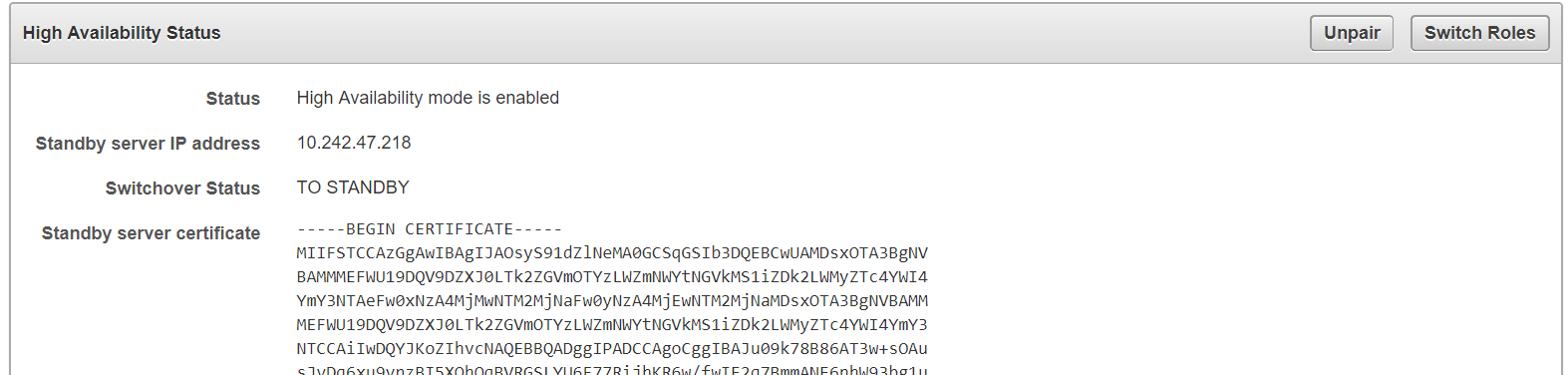
You configure high availability by providing the primary and standby servers with each other's IP address and certificate, then pairing them. While pairing the primary and standby servers, you can select one as the primary server, and the other as the standby. A failover timeout that you set, determines when the standby starts to take over as primary.
Prerequisites:
It is highly recommended to keep the primary and standby systems as identical as possible, as their roles can be reversed in maintenance periods and failure situations. These include the following:
-
Key Vault software versions
-
Disk size
-
RAM size
-
System clocks on both systems must be synchronized
If your deployment requires high availability, we recommend configuring it before adding endpoints to Key Vault so that endpoints know about both primary and standby servers. An endpoint added before the standby server will not know about the standby server unless you re-enroll the endpoint. If you configure high availability after adding endpoints, you must re-enroll the endpoints that were previously enrolled with the primary and standby servers in standalone mode.
If you want to add SNMP support in a high availability environment, you must configure SNMP on both primary and standby servers before pairing them. This is because the standby server is no longer accessible from the management console as all requests are forwarded to the primary server.
If you want to use a third-party certificate in a high availability configuration, you must install it on the primary and standby servers first, and then pair them.
With persistent cache enabled, both the primary and the standby will cache the master keys from Oracle Key Vault independently. Ensure that a TDE operation is executed on primary and standby after they are started. The persistent cache feature also enables endpoints to be operational during high availability configuration, and switchover and failover operations.
If enabled, the Read-Only Restricted mode of Oracle Key Vault 12.2.0.5.0 and higher ensures endpoint operational continuity if either primary or standby server is not available. Read-Only Restricted mode also ensures uniform behavior of the surviving Oracle Key Vault server in the event that either the primary or standby servers go down.
A High Availability configuration is characterized by continuous synchronization between the primary and standby server. When synchronization is lost between the primary and standby servers, it is possible to encounter a split-brain scenario where two primary servers might be active simultaneously. In such a scenario, both servers record new data that diverges from the last synchronized state. When connectivity is restored between the primary and standby servers, it may not be possible to reconcile the changes on the two servers, and data loss may occur.
You can enable or disable restricted mode when configuring High Availability by setting the Allow Read-Only Restricted Mode radio button to Yes or No on the Configure High Availability page.
When Read-Only Restricted mode is enabled, the primary server enters Read-Only Restricted mode if the standby server is unavailable. In Read-Only Restricted mode, the primary server will allow keys to be retrieved, but will not allow keys to be modified or new keys to be added. This ensures that endpoints still have access to their keys, and key data or metadata is not lost due to a split-brain scenario. However, the primary server still writes audit records, which may be lost if a split-brain scenario occurs with the standby server.
When Read-Only Restricted mode is disabled, the primary server becomes unavailable, and stops accepting new requests if the standby server is unavailable. Endpoints connected to Oracle Key Vault will be unable to retrieve keys from the server until connectivity is restored between primary and standby servers. The Persistent Master Key Cache feature can be used to avoid endpoint downtime. Data integrity is ensured by allowing endpoints to communicate with one primary server at any given time. Split-brain situations, and the risk of data loss associated with such situations, are avoided.
Parent topic: About High Availability for Oracle Key Vault
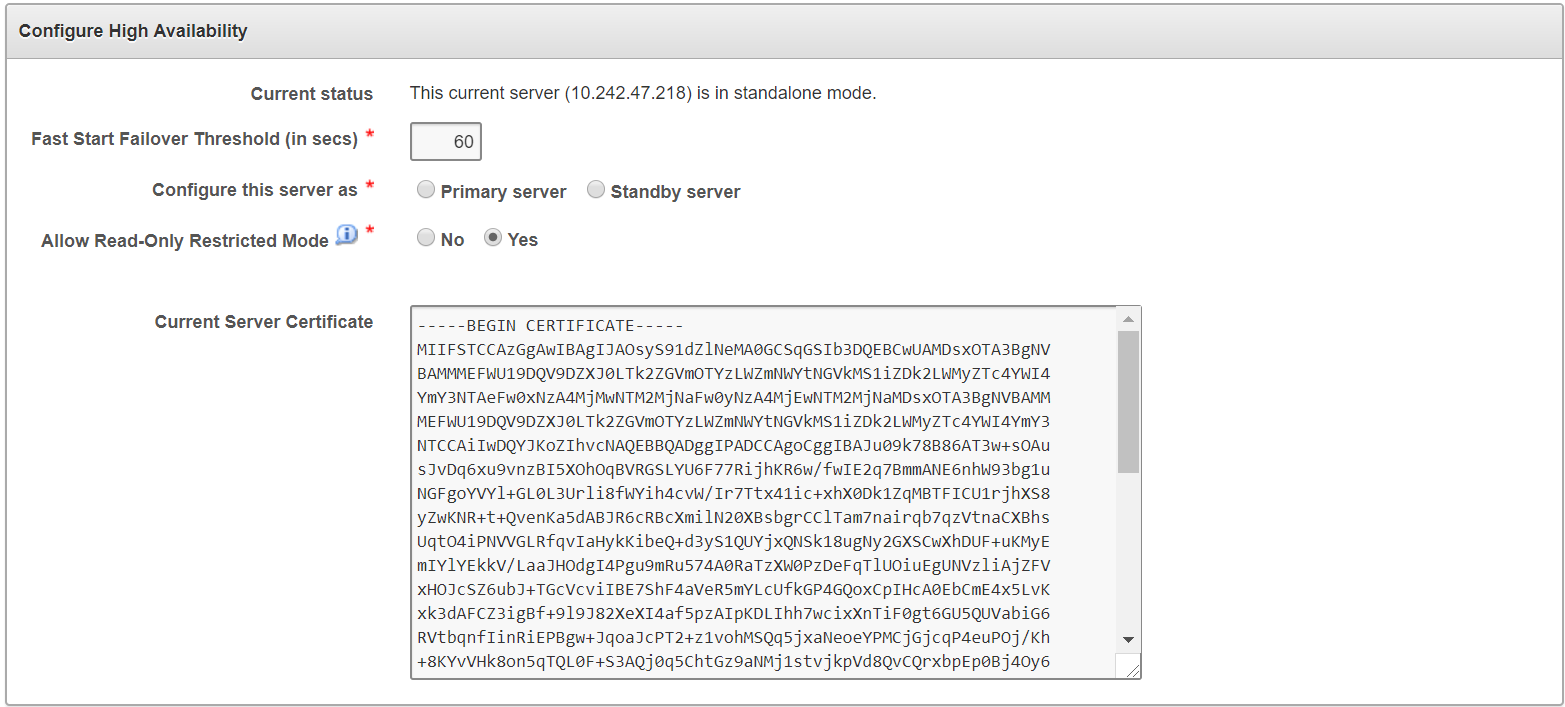
4.2.2 Configuring High Availability
To configure High Availability:
Note:
When High Availability is configured, you cannot log in to the standby server using a web browser.
To manage High Availability, log in to the primary server using a web browser.
Caution:
Ensure that you leave Read-Only Restricted Mode enabled while configuring High Availability. Enabling it later requires a reinstall of the Oracle Key Vault appliance software on the standby server.
After configuring High Availability, do not change the system time on the primary server. The changed system time causes the standby server to go down, thus disrupting the functioning of the High Availability configuration.
Parent topic: About High Availability for Oracle Key Vault
4.2.3 Switching Primary and Standby Servers
The high availability configuration allows you to switch roles of the primary and standby server. This is useful during maintenance periods, when you might want to bring a server down to upgrade software or install patches.
If you have persistent cache enabled and the persistent cache timeout is sufficiently tuned, then the endpoints will continue to be operational during the switchover, minimizing endpoint downtime.
You can switch roles as follows:
Parent topic: About High Availability for Oracle Key Vault
4.2.4 Restoring High Availability After a Failover
A failover takes place if the primary server fails. If the primary is not available, the standby server takes over the primary role. If the standby does not hear from the primary for a time exceeding the Fast Start Failover Threshold value, it will assume that the primary is down and start the failover process. You can configure the value in the Fast Start Failover Threshold field from the Key Vault user interface from the default of 60 seconds. Should the failed server (old primary) come back up, it will automatically become the new standby server, in most cases.
If the primary server fails permanently, the standby server will take over as primary. In this case high availability will have to be restored with manual intervention as follows:
Note:
When Read-Only Restricted mode is disabled, the primary server's failover status goes into suspended state causing the standby server to wait indefinitely for the primary server to come back up. This is expected behavior to avoid a split-brain scenario where two primary servers are simultaneously active.
When Read-Only Restricted mode is enabled, a primary or standby server failure causes the operational peer to enter Read-Only Restricted mode, thus ensuring endpoint operational continuity.
See Also:
For more information about recovering from High Availability failover situations, see Failover Situations in High Availability Mode.
Parent topic: About High Availability for Oracle Key Vault
4.2.5 Disabling High Availability
You can disable high availability by un-pairing the primary and standby servers. After un-pairing, the primary and standby will operate in standalone mode. To prevent endpoints from connecting to the old standby (new standalone Oracle Key Vault server) you need to take the old standby off the network.
To disable high availability follow the steps below:
Parent topic: About High Availability for Oracle Key Vault
4.2.6 High Availability Read-Only Restricted Mode
You can configure Oracle Key Vault for high availability restricted mode.
- About High Availability Read-Only Restricted Mode
- States of Read-Only Restricted Mode
- Recovering from Read-Only Restricted Mode
- Read-Only Restricted State Functionality
- Enabling Read-Only Restricted Mode
- Disabling Read-Only Restricted Mode
- Best Practices
Parent topic: About High Availability for Oracle Key Vault
4.2.6.1 About High Availability Read-Only Restricted Mode
High Availability Read-Only Restricted mode ensures endpoint operational continuity when primary or standby Oracle Key Vault servers are affected by server, hardware, or network failures.
- How High Availability Read-Only Restricted Mode Works
- High Availability without Read-Only Restricted Mode
- High Availability with Read-Only Restricted Mode
Parent topic: High Availability Read-Only Restricted Mode
4.2.6.1.1 How High Availability Read-Only Restricted Mode Works
High Availability Read-Only Restricted mode is supported in Oracle Key Vault 12.2.0.5.0 and later.
In Oracle Key Vault 12.2.0.4.0, when an unplanned shutdown caused the standby server to go offline, the primary server was also unavailable to the endpoints. However, when a planned shutdown caused the standby server to go offline, the primary server was still available to the endpoints.
Oracle Key Vault 12.2.0.5.0 and later support High Availability Read-Only Restricted mode. High Availability Read-Only Restricted mode ensures endpoint operational continuity when the primary or standby Oracle Key Vault servers are affected by server, hardware, or network failures.
When an unplanned shutdown causes the primary or standby server to go offline, the endpoints can still connect to the surviving peer server in order to perform critical operations. High Availability Read-Only Restricted mode ensures that operations that replicate data are blocked. Operations that replicate data are allowed when both primary and standby servers are back online, thus ensuring that no critical data is lost.
In High Availability Oracle Key Vault deployments, the single point of failure is eliminated by replicating the primary server’s data to the standby server. In Read-Only Restricted mode, generation of non-critical data such as audit records is enabled. However, generation of critical data such as keys is disabled. When the primary server is down, operations that generate new critical data on the standby are disabled. The reverse is also true. When the standby server is down, operations that attempt to modify or create any data on the primary server are disabled.
In a High Availability deployment without Read-Only Restricted mode, most endpoint operations are blocked because endpoint operations generate audit records, which is data that needs replication, thus disrupting operational continuity.
The following are the benefits of using Read-Only Restricted mode:
-
Allows endpoint operational continuity when the primary or standby server is offline
-
Ensures symmetrical behavior when the primary or standby server is offline
Parent topic: About High Availability Read-Only Restricted Mode
4.2.6.1.2 High Availability without Read-Only Restricted Mode
When High Availability is configured without Read-Only Restricted mode, the impact on endpoint operations differs, depending on the type of failure encountered: primary failure, standby failure, or a network failure that prevents communication between the primary and standby servers. The following are the possible scenarios:
-
Primary server failure: The standby server will failover and take over from the affected primary server. This allows the Oracle Key Vault service to remain operational. Data modifications are stored on the primary server until they can be replicated to the standby server. This ensures endpoint operational continuity when the primary server goes offline due to an unplanned shutdown.
-
Standby server failure: The primary server is unavailable to the endpoints, as it is not possible to distinguish a standby server failure from a network failure that prevents communication between the primary and standby servers.
-
Power loss or network connectivity failure: The primary and standby servers are unable to communicate. The standby server will failover and take over from the primary server. To avoid a split-brain scenario, only one of the servers is allowed to service the endpoints.
Note:
A split-brain scenario in Oracle Key Vault occurs when the primary server fails, causing the standby server to failover and take over from the primary server. This causes a situation where the primary and standby servers are available to service the endpoints, and create new data. A split-brain scenario causes data on the primary and standby servers to go out of sync. This can lead to data loss and corruption, as well as loss of operational continuity. To avoid a split-brain scenario, only one of the servers is allowed to service the endpoints after a failover occurs.In High Availability without Read-Only Restricted mode, one of the following situations is triggered when a failure occurs:
-
Endpoints suffer a temporary operational disruption to avoid a split-brain scenario.
-
The standby server accepts new requests and generates new data without attempting to synchronize the data with the failed primary server. Replication of data is temporarily disabled until the primary server is online, thus ensuring operational continuity.
Parent topic: About High Availability Read-Only Restricted Mode
4.2.6.1.3 High Availability with Read-Only Restricted Mode
Note:
It is recommended that you configure High Availability with Read-Only Restricted mode enabled, which is the default mode. While configuring High Availability, ensure that Yes is selected in the Allow Read-Only Restricted Mode field on the Configure High Availability page.Read-Only Restricted mode ensures endpoint operational continuity as well as symmetrical behavior when the primary or standby server is offline. Symmetrical behavior ensures that the online server seamlessly takes over from its failed peer, and continues to service the endpoints without any disruption. For more information about High Availability failover situations with Read-Only Restricted mode, see Failover Situations with Read-Only Restricted Mode.
In Read-Only Restricted mode, the surviving Oracle Key Vault server operates with limited functionality. Endpoint operations that add or modify critical data on the Oracle Key Vault server are blocked. However, endpoint operations that involve fetching of data are allowed. This ensures endpoint operational continuity and data integrity. For more information about blocked and allowed operations, see Read-Only Restricted State Functionality.
For more information about Read-Only Restricted state, see States of Read-Only Restricted Mode.
Note:
Read-Only Restricted Mode has no impact on a standalone server.Parent topic: About High Availability Read-Only Restricted Mode
4.2.6.2 States of Read-Only Restricted Mode
A server using read-only restricted mode is affected by the failure in a primary server, a standby server, and the network.
Parent topic: High Availability Read-Only Restricted Mode
4.2.6.3 Recovering from Read-Only Restricted Mode
To recover an instance from Read-Only Restricted mode after a network failure or standby server failure, manual intervention may be required. You will need to unpair and reset the surviving instance, reinstate a new Oracle Key Vault server, and pair it as the new standby to the surviving server. The following are the possible scenarios:
-
Primary server failure: Depending on the operational state of the primary server at the time of failure, it could be restarted and some functionality may be available. However, due to possible corruption of the embedded key vault database, recovery may not be possible and the Oracle Key Vault instance would need to be reinstated because of the partial failure. If the failed server is unable to re-pair with the peer server within 20 minutes, the server needs to be re-instantiated.
Even though the endpoint processes communicating with the Oracle Key Vault servers retain the IP address of the last known reachable server, they do have to determine the IP address of the new Key Vault server when spawned. The endpoint processes attempt to communicate with the Oracle Key Vault server configured as the primary server in the configuration scripts, and then waits for a response before trying to reach the server configured as the standby server in the configuration scripts. The wait for the response is an unnecessary delay that every new process incurs when communicating with the standby Oracle Key Vault server. To minimize downtime, it is recommended that you initiate a switchover after reinstating the failed primary server.
-
Standby server failure: The primary server will run in the Read-Only Restricted mode if there is a standby server failure. Re-instate the standby server if it does not automatically re-pair with the primary server.
-
Power loss or network connectivity failure: When a network failure occurs, the primary and standby servers are unable to communicate, and both servers enter Read-Only Restricted mode. The standby also attempts to failover to the primary server. Once communication is re-established between the primary and standby servers, the old primary server is automatically converted to the new standby. The data from the new primary server overwrites the old primary server’s data, resulting in the loss of audit records from the old primary server. It is recommended that you enable SYSLOG auditing to preserve the audit records that were overwritten on the old primary. Similar to recovering from primary server failure, it is recommended to do a switchover after recovery. It is also recommended that you do not enroll any new endpoints before the switchover.
For more information about restoring High Availability after a failover, see Restoring High Availability After a Failover.
Parent topic: High Availability Read-Only Restricted Mode
4.2.6.4 Read-Only Restricted State Functionality
Read-Only Restricted mode puts the Oracle Key Vault instance into the Read-Only Restricted mode state, but does not put the embedded Oracle Key Vault database into the Read-Only Restricted mode state. Read-Only Restricted mode introduces the following deviations from normal functionality:
-
All operations that generate new data are blocked. Operations that fetch existing data are allowed. Audit records for endpoint operations are generated as in normal operation. Internal system operations of the Oracle Key Vault database are not impacted. Functionality such as alerts continue to work normally.
-
Endpoints are allowed to fetch keys from the Oracle Key Vault server. Endpoints cannot create new keys or modify existing keys.
-
Administrators can log in to the Oracle Key Vault Management Console. Creation of an endpoint or a wallet, deletion of keys, and operations that modify or delete data are blocked.
-
Unpairing of primary and standby Oracle Key Vault servers running in Read-Only Restricted mode are allowed.
-
Backup operations are blocked to avoid data mismatches between backups.
Table 4-1 Allowed and Blocked Operations in Read-Only Restricted Mode
| Operation | Allowed or Blocked |
| Log in to Oracle Key Vault | Allowed |
| Endpoint operations such as fetching keys from the cache | Allowed |
| Endpoint operations that add, modify, or delete data such as rotation of keys on the database | Blocked |
| System operations such as enabling SSH access | Allowed |
| System operations that write data such as setting up a REST server and creating virtual wallets | Blocked |
| Oracle Key Vault Management Console access | Allowed |
| All Administrator and endpoint operations that add new data or modify existing data | Blocked |
| Backup operations | Blocked |
In Read-Only Restricted mode, if you attempt to execute operations that generate new data or modify existing data on the Oracle Key Vault server, the Key Vault Server in Read-Only Restricted Mode error is displayed.
If you attempt to upload a wallet to the Java keystore, you are prompted for the source Java keystore password. After entering the password, the Key Vault Server in Read-Only Restricted Mode error is displayed.
Parent topic: High Availability Read-Only Restricted Mode
4.2.6.5 Enabling Read-Only Restricted Mode
Read-Only Restricted mode is enabled by default when High Availability is configured.
Caution:
It is recommended that you configure High Availability with Read-Only Restricted mode enabled.Note:
Read-Only Restricted mode has no effect on a standalone server.Parent topic: High Availability Read-Only Restricted Mode
4.2.6.6 Disabling Read-Only Restricted Mode
Read-Only Restricted mode is enabled by default when High Availability is configured.
Caution:
It is recommended that you configure High Availability with Read-Only Restricted mode enabled. Do not disable Read-Only Restricted mode while configuring High Availability, unless it is necessary.Note:
Read-Only Restricted mode has no effect on a standalone server.Parent topic: High Availability Read-Only Restricted Mode
4.2.6.7 Best Practices
The following are best practices to ensure operational continuity and minimal downtime of Oracle Key Vault:
-
Configure auto-login for Hardware Security Module (HSM) on TDE-enabled endpoint databases. For more information about configuring auto-login for Hardware Security Module (HSM), see “Configuring Auto-Login Hardware Security Modules” in the Oracle Database Advanced Security Guide.
-
Apply the database patch for Bug 22734547 to tune the Oracle Key Vault heartbeat.
-
Ensure the Read-Only Restricted mode is enabled in High Availability Oracle Key Vault deployments.
-
Set the duration in the Fast Start Failover Threshold field on the Configure High Availability page to a value that avoids unnecessary failover due to transient network interruptions.
-
Configure Syslog auditing to capture audit records in Read-Only Restricted mode.
-
Switch over to the original primary server in case the primary server is reinstated.
Parent topic: High Availability Read-Only Restricted Mode
4.3 Backup and Restore Oracle Key Vault Data
Oracle Key Vault provides the facility to backup and restore Key Vault data for disaster recovery purposes.
It is highly recommended to back up data periodically to reduce down time and recover from unexpected data losses and system failures. You can restore a new or existing Oracle Key Vault appliance from a backup.
- About Backing Up and Restoring Data in Key Vault
- Backing Up Key Vault Data
- About Backup Schedule Types and States
- Scheduling and Managing Key Vault Backups
- Restoring Oracle Key Vault Data
- Backup and Restore Best Practices
Parent topic: High Availability, Backup and Restore Operations
4.3.1 About Backing Up and Restoring Data in Key Vault
Key Vault provides the facility to backup and restore security objects stored and managed in Key Vault for disaster recovery purposes.
Backup and restore operations may be performed from the Key Vault management console. You must be a user with system administrative privileges to back up and restore Key Vault data. Backups may be scheduled at periodic intervals to run automatically at designated times. They may also be run on-demand to save a current snapshot of the system.
It is highly recommended that you back up Key Vault data regularly on a schedule. This practice ensures that backups are current and hold the most recent data. The backup can be used to restore a new or existing Key Vault server and be fully operational with minimum downtime and data loss.
Key Vault encrypts all backed up data, which is copied to the backup destination using the secure copy protocol (SCP). You must therefore ensure that SCP is supported at the backup destination.
Parent topic: Backup and Restore Oracle Key Vault Data
4.3.2 Backing Up Key Vault Data
The first step to backing up data is to create a backup destination, which is the location where Key Vault data will be copied to and stored.
The primary reason for adding a backup destination is to have the backup data available in a location other than the Key Vault server itself. This ensures that you have all the relevant data to recover in case of a catastrophic failure with the Key Vault server or hardware.
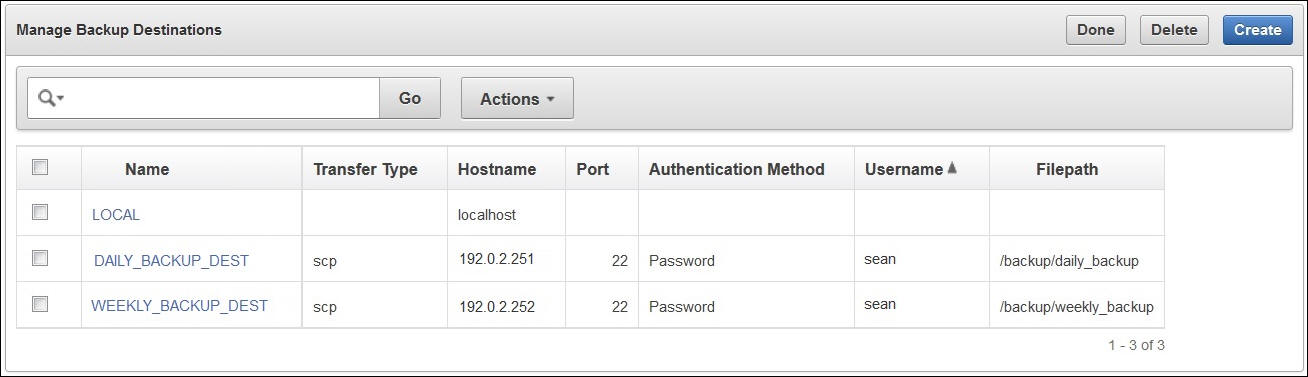
The backup destination is usually another server or computer system that you have access to. You can add, delete, and modify a backup destination.
- About Key Vault Backup Destinations
- Create a Remote Backup Destination
- Change Settings on a Remote Backup Destination
- Delete a Remote Backup Destination
Parent topic: Backup and Restore Oracle Key Vault Data
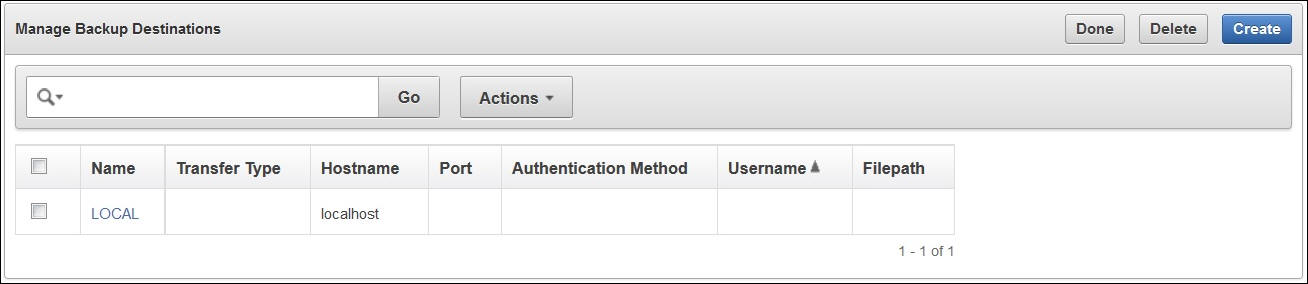
4.3.2.1 About Key Vault Backup Destinations
The backup operation copies Oracle Key Vault data to a backup destination of your choice. The backup destination stores the data until it is needed.
Key Vault provides two types of backup destinations: local and remote. The local backup destination resides on the Key Vault server itself, the remote one resides externally in a different server or computer system. You can create more than one backup destination for greater availability.
Backup destinations may be:
-
Local
The local backup destination,
LOCAL, is present out of the box and cannot be removed.Backups to
LOCALare useful to save a current state of Key Vault. Since these backups are stored in Key Vault, they will be lost in case of a failover or switchover in a high availability deployment. It is therefore highly recommended that you back up the data to a remote destination before you perform operations like failover and switchover.A
LOCALdestination can store only the last full backup and the cumulative incremental backups after that full backup. After a new full backup of the periodic backup toLOCALcompletes, the previous periodic full or cumulative incremental backups are deleted. For more information about backups, see Two Types of Key Vault Backups. -
Remote
Remote backup destinations reside on external servers and can be dispersed geographically for disaster recovery purposes.
Each backup destination on the external server is associated with a backup catalog file called
okvbackup.mgrthat Key Vault maintains at the backup destination. The fileokvbackup.mgrcatalogs the backups performed and is used to restore data.Note:
You cannot use another Key Vault appliance as a remote backup destination.Caution:
-
Oracle Key Vault may not be able to find the backups if you delete or modify the backup catalog file. Therefore do not delete or modify this file.
-
Do not configure the same remote backup destination directory for different Key Vault servers as backup destinations, because backups that happen concurrently from different Key Vault servers will overwrite each other's catalog file, with the result that Key Vault may not be able to locate the backups correctly.
-
Parent topic: Backing Up Key Vault Data
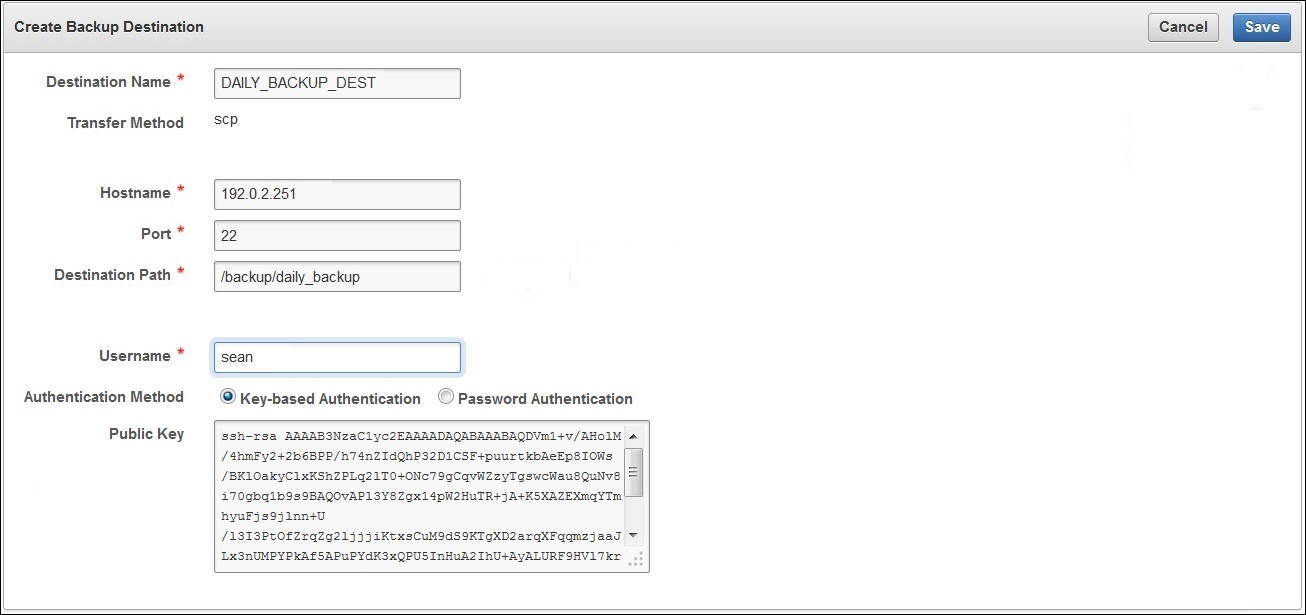
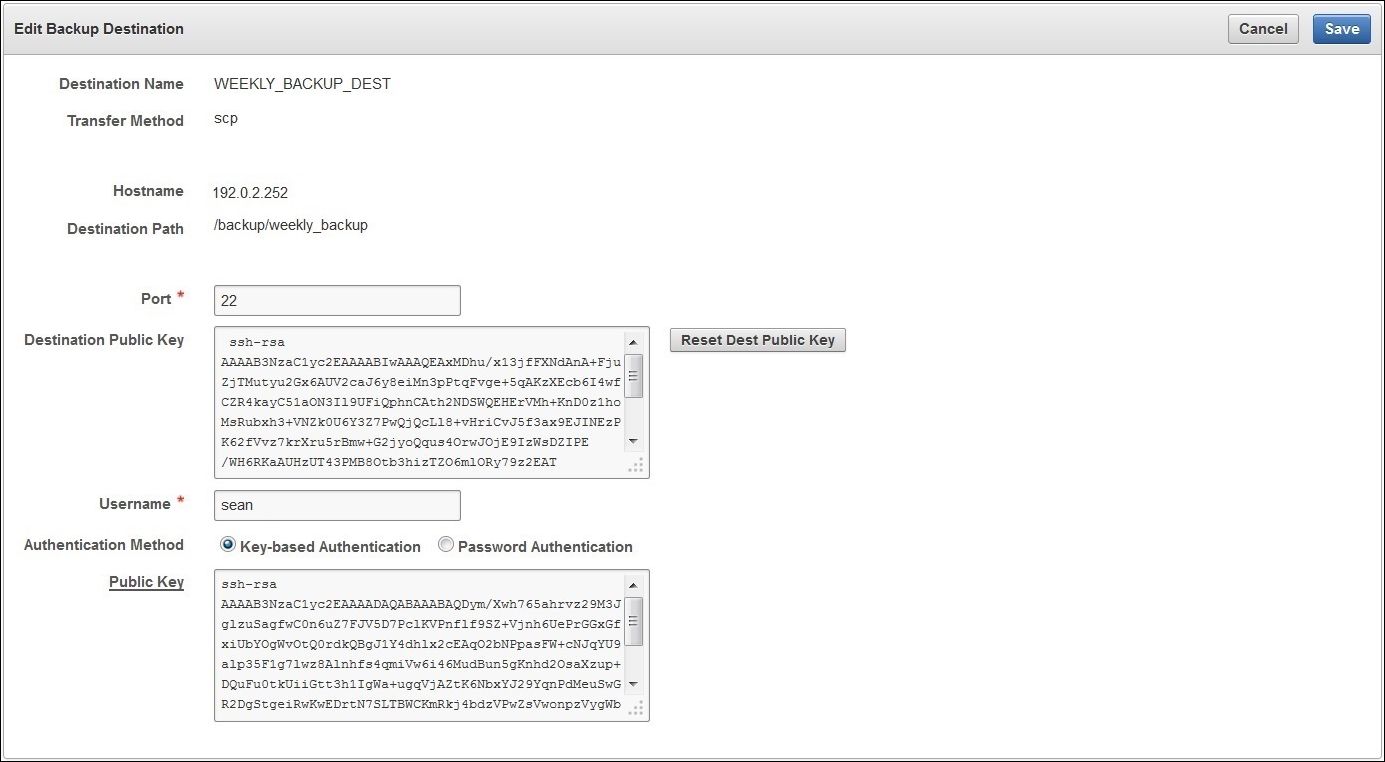
4.3.2.2 Create a Remote Backup Destination
To create a remote backup destination, you must provide a user account, a unique existing directory location on an external server, and an authentication method (password or key-based). Oracle Key Vault needs this information to make a secure connection with the remote server.
Parent topic: Backing Up Key Vault Data
4.3.2.3 Change Settings on a Remote Backup Destination
Once the backup destination is created, you can only change the SCP port number and details of the user account. You may not change any other setting.
To change allowable settings of a backup destination:
Parent topic: Backing Up Key Vault Data
4.3.2.4 Delete a Remote Backup Destination
You can delete a remote backup destination to stop future backups to that destination server. Backups already on the destination server will remain there.
To delete a remote backup destination:
Parent topic: Backing Up Key Vault Data
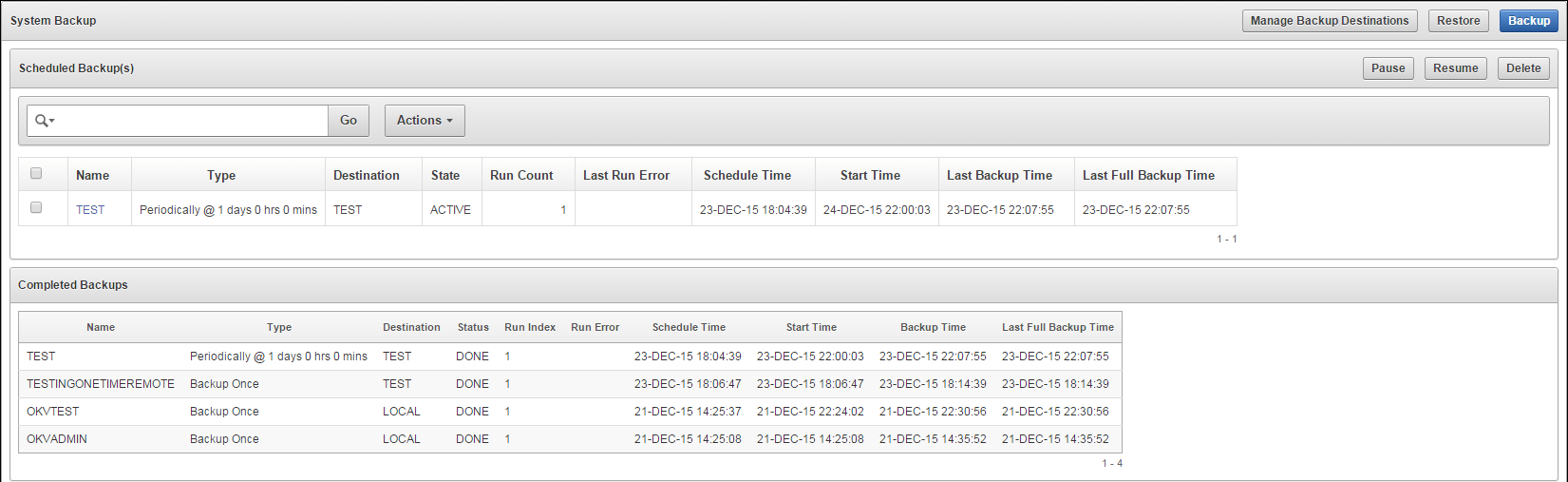
4.3.3 About Backup Schedule Types and States
You can schedule backups in Key Vault for specific times and backup destinations. The backup process starts at the scheduled time and generates a system backup, which is a file that is stored on the backup destination. There is one backup file for each completed backup.
No backup can start if another backup is in progress. You can change the schedule of backups as needs change. You can continue working with Key Vault while the backup is in progress.
A system reboot will terminate any ongoing backup. If you must reboot the system, you can cancel a backup that is scheduled to happen at the same time, and backup the system after the reboot.
Parent topic: Backup and Restore Oracle Key Vault Data
4.3.3.1 Two Types of Key Vault Backups
Oracle Key Vault provides two types of backups that can be scheduled:
-
One-time backup
A one-time backup makes a full backup of the Key Vault system. More than one such one-time backup can be scheduled together.
One-time local backups should be taken before making significant configuration changes to Key Vault, in case you need to recover from configuration failures.
LOCALdestinations can only store the last one-time backup. When a one-time backup toLOCALcompletes, the previous backup is deleted. -
Periodic backup
A periodic backup makes a backup at regular intervals at a specified frequency. The process first makes a full backup of the Key Vault system and puts it in active state. For more information about backup states, see Scheduled Backup States in Key Vault. At the end of the subsequent periodic interval, a cumulative incremental backup starts. This cumulative incremental backup holds changes from the last full backup. Another full backup is made after 7 days have passed since the last full backup.
For example, if the backup period is once a day, then every seventh one is a full backup. If the backup period is every 8 days, then all backups are full backups. If the backup period is 12 hours, then there are 13 cumulative backups before a full backup.
Periodic backups should be scheduled with a period of at least one day to minimize data loss.
A
LOCALdestination can store only the last full backup and the cumulative incremental backups after that full backup. After a new full backup of the periodic backup toLOCALcompletes, previous periodic full or cumulative incremental backups are deleted.Cumulative incremental backups are faster than full backups. Only one periodic backup can be scheduled at any time.
Parent topic: About Backup Schedule Types and States
4.3.3.2 Scheduled Backup States in Key Vault
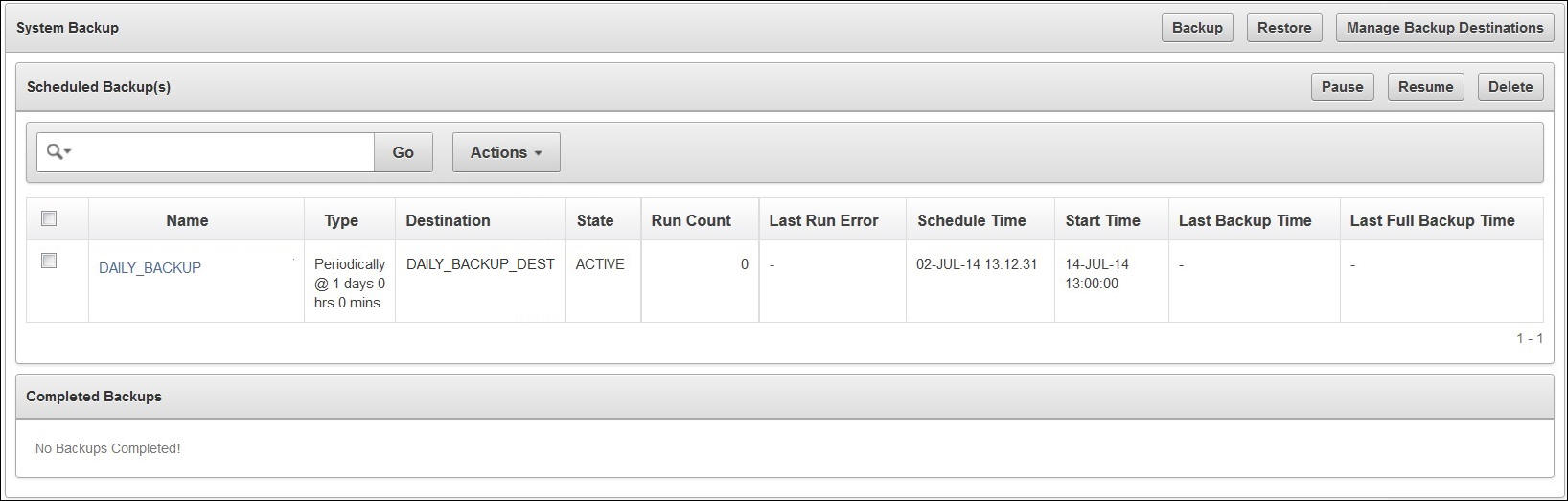
Scheduled backups have four states, which indicate whether the backup is scheduled, in progress, completed, or paused:
-
ACTIVE
The backup is scheduled and will be processed at the specified start time or period.
-
ONGOING
The backup is in progress.
-
DONE
The backup is complete.
-
PAUSED
All future backups are on hold and will not start even if the start time has passed. They will start when they are explicitly resumed.
You can change the state from active to paused and back. Put a scheduled backup in the paused state for these situations:
-
When communication between Key Vault and the remote destination is broken
-
If the remote destination is down
-
If you want to defer the backup
You can delete the scheduled backups that have not completed.
-
Parent topic: About Backup Schedule Types and States
4.3.4 Scheduling and Managing Key Vault Backups
You can schedule Key Vault backup(s) to specific backup destination(s) and time(s). Note, that you must create the backup destinations that you will use prior to this step. Backup schedules may be modified or deleted to accommodate changes.
- Schedule a Backup on Key Vault
- Change Backup Schedule on Oracle Key Vault
- Delete a Backup Schedule from Key Vault
- How High Availability Affects Key Vault Backups
- Protecting the Backup Using the Recovery Passphrase
Parent topic: Backup and Restore Oracle Key Vault Data
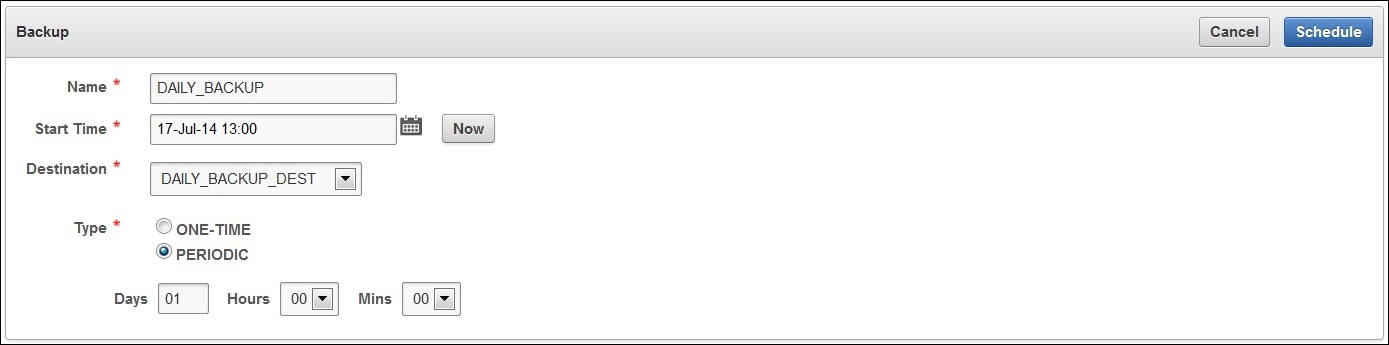
4.3.4.1 Schedule a Backup on Key Vault
You can also schedule a one-time or periodic backup to a local or remote backup destination. You can start a one-time backup to start immediately without setting a time.
To schedule a backup:
-
Log in to the Oracle Key Vault management console as a user who has the System Administrator role.
-
Select the System tab, and then System Backup from the left sidebar.
The System Backup page appears.
-
Click Backup.
The Backup page appears.
-
In the Name field, enter a name for the backup.
-
Click the Calendar icon and select the Start Time.
-
Select the Destination for the backup from the list.
-
Select the Type: ONE-TIME or PERIODIC.
The Backup page is the same for one-time or periodic backups. In case of a periodic backup additional fields for Days, Hours and Mins appear. You must enter values for these fields.
-
Click Schedule.
The System Backup page appears listing the scheduled backup in Scheduled Backup(s).
To start an immediate one-time backup:
Parent topic: Scheduling and Managing Key Vault Backups
4.3.4.2 Change Backup Schedule on Oracle Key Vault
You can not change the schedule of a backup in progress. To change the backup schedule the state must be active or paused.
Parent topic: Scheduling and Managing Key Vault Backups
4.3.4.3 Delete a Backup Schedule from Key Vault
- Log in to the Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then System Backup from the left sidebar.
- Check the box(es) of scheduled backup(s) listed in Scheduled Backup(s).
- Click Delete to delete the scheduled backups.
Parent topic: Scheduling and Managing Key Vault Backups
4.3.4.4 How High Availability Affects Key Vault Backups
It is important to note that backups are performed on the primary server in a high availability deployment. Since the standby synchronizes its state with the primary, it is not necessary to backup the standby.
Points to consider during failover or switchover in a high availability deployment would be:
-
Any backups in progress will terminate if there is a failover or a high availability switchover. Backups to
LOCALare private to the Oracle Key Vault appliance and therefore the local backup on the primary appliance is not available after a failover or switchover. -
Backups scheduled with password authentication start as usual after the failover or switchover.
-
Remote backups using key-based authentication will need to update the public key on the destination to match the one shown on the new primary system.
Parent topic: Scheduling and Managing Key Vault Backups
4.3.4.5 Protecting the Backup Using the Recovery Passphrase
Oracle Key Vault uses the recovery passphrase to control who can restore user and system data.
To restore a backup, use the Oracle Key Vault recovery passphrase from the time when the backup was initiated. This is necessary even if the recovery passphrase was changed after the backup completed. Oracle recommends that you make a new backup every time the recovery passphrase is changed to ensure that there is always a copy of the backup that is protected by the most recent recovery passphrase.
See Also:
"Emergency System Recovery Process" for information on the recovery passphrase and how it is used
Parent topic: Scheduling and Managing Key Vault Backups
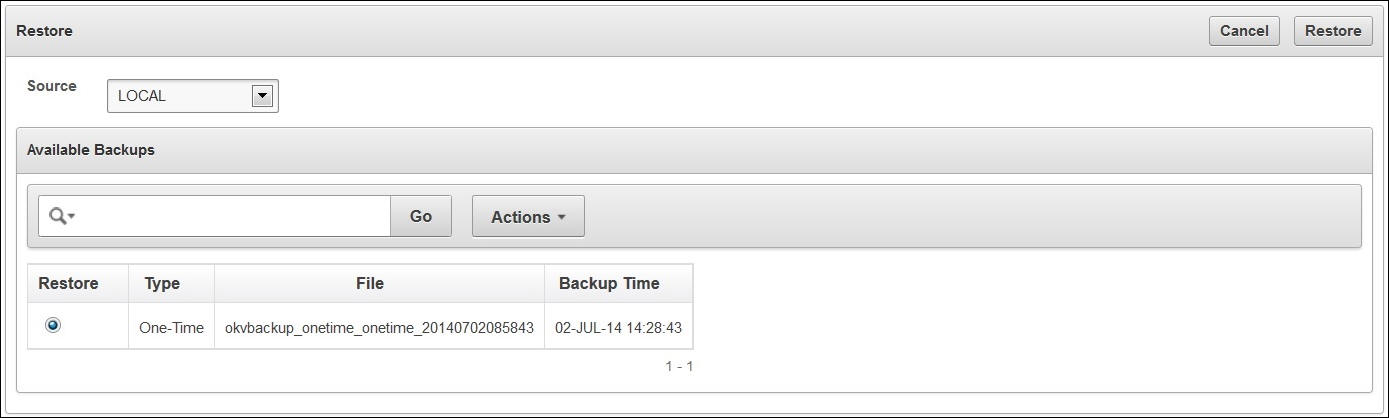
4.3.5 Restoring Oracle Key Vault Data
You can restore Key Vault data from a remote backup destination onto a new or existing Key Vault server to minimize downtime and data loss. The restore process replaces all the data on the new server except the root and support user passwords. You will not be able to restore data to a server if there is a scheduled backup in process on the server.
Note:
You must restore Key Vault data to a server only after ensuring that all scheduled backups on the server are completed.
- About the Key Vault Restore Process
- Restore Key Vault Data
- High Availability and the Restore Operation
- Third-Party Certificates and the Restore Operation
- Changes Resulting from a System State Restore
Parent topic: Backup and Restore Oracle Key Vault Data
4.3.5.1 About the Key Vault Restore Process
Restoring data to a Key Vault server replaces the data in the server with that of the backup. Any changes made since the last backup will be lost.
The maximum life of a backup is 1 year. Any backup older than a year cannot be restored.
You must have the recovery passphrase that was in effect at the time of the backup in order to restore data from a backup. If you have not changed the recovery passphrase since installing Key Vault, then you must use the recovery passphrase that you created during the post-installation process.
There are two steps to restoring data in Key Vault: Setup and Restore.
-
Setup consists of:
-
Installing the Oracle Key Vault appliance.
-
Setting up the backup destinations.
-
-
Restore the Oracle Key Vault appliance by:
-
Determining the backup to use from a remote or local backup destination.
-
Providing the recovery passphrase to begin the restore process.
-
Note:
The recovery passphrase was created in Performing Post-Installation Tasks
Parent topic: Restoring Oracle Key Vault Data
4.3.5.2 Restore Key Vault Data
Before you restore ensure that you have the correct recovery passphrase. You will need to enter it during the restore process.
To restore data from a backup:
Parent topic: Restoring Oracle Key Vault Data
4.3.5.3 High Availability and the Restore Operation
In a high availability deployment you must consider the following points while restoring data to Key Vault:
-
Restore only if both primary and standby are lost.
-
You must restore the backup on a standalone Key Vault appliance only, even if the backup was taken from the primary.
-
The restore operation replaces the Key Vault appliance with the backup. This means that some data can be lost. You might need to restore the endpoint database.
-
If you restore a backup taken from the primary node, then you must discard (or reinstall) the standby server and configure a new standby.
-
If the standby server has taken over as primary, then there is no need to restore data from a backup to the new standby server. Just configure a new standby server and it automatically synchronizes with the functioning primary.
Parent topic: Restoring Oracle Key Vault Data
4.3.5.4 Third-Party Certificates and the Restore Operation
A third-party certificate installed at the time of a backup will not be copied when you restore another appliance from this backup. You will have to re-install the third-party certificate on the new appliance in order to use it.
See Also:
Parent topic: Restoring Oracle Key Vault Data
4.3.5.5 Changes Resulting from a System State Restore
Restoring an Oracle Key Vault appliance brings the system state back to the time when the backup was created.
Therefore, any changes made after the backup was made do not exist on the restored system. For example, if a user's password was changed after the backup operation, the new password will not be available in the restored system. The restored system will have the password that was in effect when the backup was made.
Note:
Restoring also changes the recovery passphrase to the one that was in effect during the backup.
You should change the user passwords, enroll the endpoints created after backup, and make other similar changes, if required. You should confirm that everything is configured correctly after restoring.
If you are not certain that you restored the correct backup, then you can restore a different one. To restore another backup, first configure the remote destination of this backup on the restored Oracle Key Vault itself, and then start the restore process. You do not need to reinstall the Oracle Key Vault appliance.
When the appliance has been restored and functional, you can continue to backup Key Vault data to new or previous remote destinations.
Depending on the age of your backup, the restored server may be missing endpoints, security objects, and other changes made after the restored backup was taken. You may need to enroll missing endpoints and upload missing security objects, or choose a more recent backup to restore. It is also recommended that you change user passwords after a restore operation.
Parent topic: Restoring Oracle Key Vault Data
4.3.6 Backup and Restore Best Practices
The following best practices will help you to keep backups current so that you can recover from catastrophic failures with minimum down time and data loss:
-
Ensure that the recovery passphrase at the time of backup is accessible because you will need it to restore data from a backup.
-
Backup data any time you change the recovery passphrase.
-
Ensure that you create at least one remote backup destination in a high availability deployment. Since the local backup resides on the Key Vault server itself, it will be lost in a failover or switchover situation.
-
Do not delete the backup catalog file associated with a remote backup destination, even if you stop using the backup destination. If you ever need to restore from a backup on this server, you will need the backup catalog file.
-
If you use the same remote server for multiple backup destinations, ensure that the directories are unique so that you have distinct backup catalog files associated with each backup destination. If you fail to do this, the backup catalog file will get overwritten during subsequent backups and become unusable.
-
Before you restore data ensure that all scheduled backups are complete.
-
To create remote backup destinations successfully:
-
Ensure that the servers used as remote backup destinations are up.
-
Ensure connectivity between Key Vault and remote server you plan to use as a backup destination.
-
Ensure that the remote server designated as a backup destination supports the secure copy protocol (SCP).
-
Validate user account credentials on remote server before you create the backup destination on Key Vault.
-
Ensure that the destination directory has write permissions.
-
Create more than one remote backup destination on multiple servers for redundancy.
-
Ensure that destination directories are unique if you are using the same remote server for multiple backup destinations. You must do this to prevent later backups from overwriting previous ones.
-
-
Schedule a periodic backup with a period of one day. This ensures that you have a full backup once in seven days.
-
Perform a one-time backup once every seven days.
-
Perform a local one-time backup before system changes. You can use this backup as a restore point.
-
Backup before and after upgrading Key Vault server software.
-
Change the backup destination after each upgrade. If at all possible do not reuse the backup destination.
Parent topic: Backup and Restore Oracle Key Vault Data