2About Security for Siebel CRM
About Security for Siebel CRM
This chapter provides an overview of security resources available for Oracle’s Siebel Business Applications and an overview of configuring security. It contains the following topics:
About This Guide
This guide provides recommendations for safeguarding your Siebel CRM deployment from internal (intranet) and external (Internet) security threats. The most important reason for securing an application is to protect the confidentiality, integrity, and availability of an organization's critical information. However, to protect Siebel CRM data, you must secure both your Siebel Business Applications and the computing environment in which they run.
This guide provides the information you need to protect your Siebel CRM deployment:
It describes the Siebel security architecture and security concepts.
It outlines the security controls provided by Siebel CRM.
It provides detailed procedural information on how to implement the security controls to secure your application.
Siebel Security Hardening provides general recommendations for securing Siebel CRM and the deployment environment (network, operating system, database).
Siebel Security Hardening provides detailed procedural information on implementing Siebel security controls only where such information is not provided elsewhere in the Siebel Bookshelf.
General Security Concepts
When assessing the security needs of an organization and evaluating security products and policies, the manager responsible for security must systematically define the requirements for security and characterize the approaches to satisfying those requirements.
To create an effective security plan, a manager must consider the following:
What types of actions or security attacks can compromise the security of information owned by an organization?
What mechanisms are available to detect, prevent, or recover from a security breach?
What services are available to enhance the security of data processing systems and information transfers within an organization?
Classifications of security services include:
Confidentiality. Confidentiality makes sure that stored and transmitted information is accessible only for reading by the appropriate parties.
Authentication. Authentication makes sure that the origin of a message or electronic document is correctly identified, with an assurance that the identity is correct.
Integrity. Integrity makes sure that only authorized parties are able to modify computer system assets and transmitted information.
Nonrepudiation. Nonrepudiation requires that neither the sender or receiver of a message be able to deny the transmission.
Access control. Access control requires that access to information resources can be controlled by the target system.
This guide describes security services available with Siebel CRM. These services are intended to counter security attacks; they use one or more security mechanisms to provide the service.
Industry Standards for Security
Siebel CRM adheres to common security standards to facilitate the integration of its applications into the customer environment. Siebel CRM is designed so that customers can choose a security infrastructure that best suits their specific business needs.
Supported standards include:
Lightweight Directory Access Protocol (LDAP). Siebel CRM provides preconfigured integration with LDAP for user authentication purposes. For more information, see Security Adapters for LDAP Authentication and Security Adapter Authentication.
Communications encryption. Siebel CRM supports the use of the following technologies for communications encryption:
-
Transport Layer Security (TLS) encryption and authentication. TLS can be used to protect communications between the following:
Siebel CRM components, that is, Siebel Servers and Web servers.
Siebel Web servers and Siebel Web Clients, if support for the protocol is provided by the Web server. The use of TLS for Web server and Siebel Web Client communications is transparent to Siebel CRM.
Siebel Servers and Microsoft Exchange Server email servers.
The following table lists topics that provide information on configuring TLS.
Information Type
Topic
Configuring TLS for communication between Siebel Web clients and Siebel Application Interface.
Configuring TLS for communication between Siebel components.
Using TLS to secure user login credentials
Using TLS to secure communications between Siebel Servers and directory servers.
-
RSA SHA-1 password hashing. Siebel user passwords can be hashed using the SHA-1 algorithm. For more information, see About Password Hashing.
Note: The SHA-1 hashing algorithm is the only algorithm supported for password hashing in Siebel Enterprise. SHA-2 must not be used for any participating node, since the enterprise supports only SHA-1. In addition, the Siebel Gateway security profile does not support SiebelHash (the Siebel proprietary algorithm) and so must not be used anywhere in the enterprise.AES. Siebel data can be encrypted using Advanced Encryption Standard (AES). Multiple key lengths are supported for AES. For more information, see About Data Encryption.
About Supported Security Products
To augment the security of your Siebel CRM deployment, Oracle has alliances with leading security providers. For information, visit the Oracle Partner Network Web site at
http://www.oracle.com/us/partnerships/index.html
Oracle also provides a suite of security products, some of which have been certified for use with Siebel CRM. For information on the Oracle Identity Management products, go to
http://www.oracle.com/us/products/middleware/identity-management/overview/index.html
For information about third-party products supported or validated for use with Siebel CRM, see the Certifications tab on My Oracle Support.
Siebel Security Architecture
The components of Siebel security architecture include:
User authentication for secure system access
End-to-end encryption for data confidentiality
Authorization for appropriate data visibility
Audit trail for data continuity
Secure physical deployment to prevent intrusion
Security for mobile devices
Web browser security settings
User Authentication for Secure System Access
Siebel CRM provides an open authentication architecture that integrates with a customer’s selected authentication infrastructure. For more information, see Security Adapter Authentication and Single Sign-On Authentication. Siebel CRM supports three types of user authentication. A logical view of each type of authentication is illustrated in the following figure, where each arrow represents a Siebel CRM authentication mechanism:
Database authentication. A database security adapter is provided to support database credential collection and verification of users.
LDAP authentication. LDAP security adapters are provided to support credential collection and verification of users in an LDAP-compliant directory.
Web Single Sign-On (Web SSO). A configurable mechanism for communicating with Web SSO infrastructures is provided, allowing for Siebel user authentication by a third party at the Web-site level.
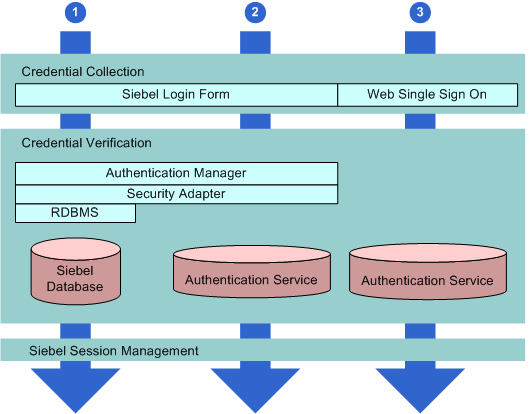
Customers can also develop custom security adapters using a security adapter SDK.
The authentication mechanisms illustrated in this figure apply whether users access Siebel CRM from within a LAN or WAN, or remotely. Additional information on each method of authentication is provided in the following topics.
Security Adapter for Database Authentication
Siebel CRM provides a database security adapter mechanism for credential collection and verification. The default login form collects Siebel user name and password credentials. The security adapter works with the underlying security systems of the database to verify users’ credentials.
With database authentication, each user must have a valid database account in order to access a Siebel application. The database administrator (DBA) must add all user database accounts. Database authentication deployment supports password hashing for protection against hacker attacks.
Any Siebel application can use database authentication, which is configured as the default. However, some functionality provided by Siebel CRM, such as workflow processes to support user self-registration or forgotten password scenarios (capabilities commonly used in customer applications), require authentication using LDAP security adapters. For this reason, database authentication is rarely used with customer applications.
Security Adapters for LDAP Authentication
For employee or customer applications, Siebel CRM includes a preconfigured security adapter interface to allow organizations to externalize credential verification in an LDAP-compliant directory. The interface connects to a security adapter, which contains the logic to validate credentials to a specific authentication service.
Siebel customers can therefore verify user credentials with security standards such as LDAP.
Siebel CRM provides security adapters for leading authentication services.
LDAP security adapter integration is supported for directory servers that are compliant with the LDAP 3.0 standard.
For information about third-party LDAP directory servers supported or validated for use with Siebel CRM, see Directory Servers Supported by Siebel CRM. You can also build security adapters to support a variety of authentication technologies. For information on custom security adapters, see Security Adapter SDK.
Web Single Sign-On
Siebel CRM offers customers the capability of enabling a single login across multiple Web applications; this is known as Web Single Sign-On (SSO). Siebel CRM provides a configurable mechanism for communicating with Web SSO infrastructures, identifying users, and logging users into the Siebel application.
With Web SSO, users are authenticated independently of Siebel CRM, such as through a third-party authentication service, or through the Web server.
Security Adapter SDK
Oracle offers the Siebel Security Adapter Software Developers Kit (SDK) to allow companies to build additional security adapters. Such additional adapters can support other authentication technologies such as biometrics or smart cards.
For example, a security adapter might be created for a portable device that provides users with a key that changes at frequent intervals. When a security adapter for this device is deployed, only by supplying both the currently displayed key and the user’s password or other credentials can the user gain access to the Siebel application.
The security adapter interface is critical to the Siebel architecture because, for most Siebel customers, authentication has become an enterprise decision, rather than an application-specific decision. The authentication service can be a shared resource within the Enterprise, thereby centralizing user administration. The Siebel Security Adapter SDK is described in 476962.1 (Article ID) on My Oracle Support.
End-to-End Encryption for Data Confidentiality
Stored data can be selectively encrypted at the field level, and access to this data can be secured. In addition, data can be converted into an encrypted form for transmission over a network. Encrypting communications safeguards such data from unauthorized access. Transmitted data must be protected from intrusive techniques (such as sniffer programs) that can capture data and monitor network activity.
End-to-end encryption protects confidentiality along the entire data path: from the client browser, to the Web server, to the Siebel Server, to the database, and back. The following figure shows the types of encryption available for communications within the Siebel environment.
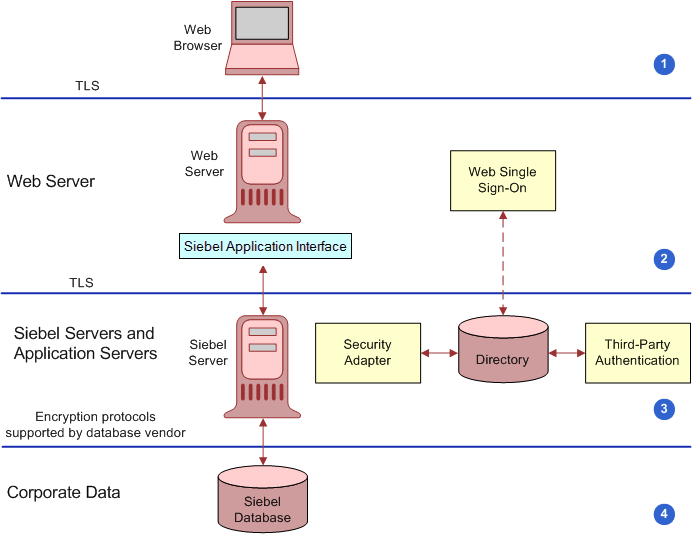
This figure shows that communications encryption is available between the following:
Client Browser to Web Server. Siebel CRM runs using the Siebel Web Client in a standard Web browser. When a user accesses a Siebel application, a Web session is established between the browser and the Siebel Server, with the Web server in between. To protect against session hijacking when sensitive data is transmitted, it is recommended that you use the TLS protocol for communications between the browser and Web server, if support for this protocol is provided by your Web server.
The Siebel Application Interface can be configured to allow only URLs that use TLS over HTTP (HTTPS protocol) to access views in a Siebel application in the following scenarios:
Use HTTPS on the login view to protect password transmission. See Implementing Secure Login.
Use HTTPS for the entire application. See About the Siebel Web Client and Using HTTPS.
Web Server to Siebel Server. Siebel CRM components communicate over the network using Siebel TCP/IP using TLS. These technologies allow data to be transmitted securely between the Web server and the Siebel Server. For more information, see Process of Configuring Secure Communications.
Siebel Server to Database. For secure transmission between the database and the Siebel Server, data can be encrypted using the proprietary security protocols specific to the database that a customer is using.
Database Storage. Siebel CRM allows customers to encrypt sensitive information stored in the database so that it cannot be viewed without access to the Siebel application. Customers can configure Siebel Business Applications to encrypt data before it is written to the database and decrypt the same data when it is retrieved. This prevents attempts to view sensitive data directly from the database. Siebel CRM supports data encryption using AES algorithms. For more information, see About Data Encryption.
About Controlling Access to Data
Authorization refers to the privileges or resources that a user is entitled to within Siebel CRM. Even among authenticated users, organizations generally want to restrict visibility to operating system data. Siebel CRM uses two primary access-control mechanisms:
View-level access control to manage which application functions a user can access.
Record-level access control to manage which data items are visible to each user.
Access control provides Siebel customers with a unified method of administering access to many content items for many users. For more information, see Configuring Access Control.
View-Level Access Control
Organizations are generally arranged around functions, with employees being assigned one or more functions. View-level access control determines what parts of the Siebel application a user can access, based on the functions assigned to that user. In Siebel CRM, these functions are called responsibilities.
Responsibilities define the collection of views to which a user has access. An employee assigned to one responsibility might not have access to parts of Siebel CRM associated with another set of responsibilities. For example, typically a system administrator has the ability to view and manage user profiles, while other employees do not have this ability. Each user’s primary responsibility also controls the user’s default screen tab layout and tasks.
Record-Level Access Control
Record-level access control assigns permissions to individual data items within an application. This allows Siebel customers to authorize only those authenticated users who need to view particular data records to access that information.
Siebel CRM uses three types of record-level access: position, organization, and access group. When a particular position, organization, or access group is assigned to a data record, only employees who have been assigned that position, organization, or access group can view that record.
A position represents a place in the organizational structure, much like a job title. Typically, a single employee occupies a position; however, it is possible for multiple employees to share a position. Position access allows you to classify users so that the hierarchy between them can be used for access to data.
For example, a supervisor would have access to much of the data that a subordinate has access to; the same applies to others who report to the same manager.
Similarly, an organization, such as a branch of an agency or a division of a company, is a grouping of positions that map to the physical hierarchy of a company. Those employees assigned to a position within a certain organization are granted access to the data that has been assigned to that organization. Visibility to data can be set up to restrict employees from accessing data outside their own organization.
An access group is a less-structured collection of users or group of users, such as a task force. Groups can be based on some common attribute of users, or created for a specific purpose, pulling together users from across different organizations and granting them access to the same data.
Support for Auditing in a Siebel Environment
Siebel CRM supports various degrees of auditing:
At the simplest level, each data record has created and last updated fields (when and by whom). With additional configuration, you can generate an activity for additional levels of auditing. This is best used when there are limited needs for auditing, for example, just a few areas to track.
Siebel CRM maintains an audit trail of information that tells when business component fields have been changed, who made the change, and what has been changed. It is also possible to maintain an audit trail of when the business component fields have been viewed or exported and who viewed or exported fields. Siebel Audit Trail is a configurable feature that allows users to choose business components and fields to audit, and to determine the scope of the audit.
Siebel customers can choose to audit all activity, or to limit the scope of auditing to those operations performed by certain responsibilities, positions, or employees. Siebel CRM allows customers to audit specific data fields or objects.
Using Siebel Workflow, you can configure workflow processes to save information on changes to specific business components.
You can attach scripts to the business component Write_Record event and save information about the transaction.
Siebel customers can use database auditing that is included with all supported databases. All vendors support high levels of audits: B3 or C2 Orange book levels. (Database auditing requires a security person to review the audit information.)
If you implement a shared database account with LDAP or Web Single Sign-On authentication mechanisms, then database auditing cannot provide detailed information about an individual user’s database access. For additional information, see Configuring the Shared Database Account.
Secure Physical Deployment to Prevent Intrusion
Access to the physical devices that host Siebel CRM must be protected. If these devices are compromised, then the security of all applications on the computer is at risk. Utilities that provide computer-level security, by either enforcing computer passwords or encrypting the computer hard drive, can be used and are transparent to the Siebel application.
In Siebel application deployments, the Web server resides in the demilitarized zone (DMZ). Clients outside the firewall access the Web server and the Siebel Server through a secure connection.
In employee application deployment, clients as well as servers often reside behind a firewall.
In customer or partner application deployment, or in employee application deployment where employees accessing the application are outside of the firewall, the Siebel Server is deployed behind an additional firewall.
Siebel CRM also supports reverse proxy configuration to further enhance the DMZ security. Increasingly, firewall vendors offer virtual private network (VPN) capabilities. VPNs provide a protected means of connecting to the Siebel application for users (such as employees) who require remote access.
Siebel CRM works with leading third-party vendors to provide additional physical security measures, such as attack prevention, data back-up, and disaster recovery. For example, HTTP load balancing protects against denial-of-service attacks by handling TCP connections and catching incoming attacks before they reach the Siebel Server. Furthermore, only one IP address and one port have to be opened on the firewall between the Web server and the Siebel Server.
The architecture of Siebel CRM takes advantage of high availability technologies, such as Microsoft Cluster Services, which allow multiple computers to function as one by spreading the load across multiple systems. High availability technologies address the need for failover and catastrophic recovery management. For more information, see Siebel Deployment Planning Guide. For information about security issues related to the physical deployment of Siebel components, see Siebel Security Hardening.
Security for Mobile Solutions
Oracle provides a suite of mobile solutions that allow remote access to data within Siebel CRM. These solutions support a variety of mobile devices, including tablets, smart phones, and laptop computers (running Siebel Mobile Web Client).
Oracle provides security for customers using these devices to access Siebel CRM, and works with alliance partners for other types of mobile devices.
For information about security issues when accessing Siebel CRM from a browser on a mobile device, see Siebel Mobile Guide: Connected and Siebel Mobile Guide: Disconnected.
For information about security issues for Siebel Mobile Web Client, which can be installed on mobile devices such as laptop computers, see Configuring Encryption for Mobile Web Client Synchronization and About Authentication for Mobile Web Client Synchronization. Siebel Remote and Replication Manager Administration Guide provides additional information on Mobile Web Client security measures.
Mobile Device User Authentication
Mobile devices themselves must be secure. If a mobile device falls into the wrong hands, then organizations need assurance that sensitive data will not be compromised. Siebel CRM is fully compatible with the embedded security within these devices, as authentication is generally a device-level decision, rather than an application-specific one.
Security Settings for the Web Browser
Certain features and functions in Siebel CRM work in conjunction with security or other settings on the Web browser.
For information about the browser standards required for Siebel Open UI, see the Certifications tab on My Oracle Support and About Siebel Open UI. For more information about settings in your Web browser, see the documentation for your browser.
Web Sites with Security Information
The following Web sites provide information about managing security on your network and about industry trends in security:
Oracle Security Solutions page at
RSA Laboratories home page at
RSA Laboratories Crypto FAQ at
CERT Coordination Center, Carnegie Mellon University at
Microsoft Safety and Security home page at
Using Transport Layer Security with Siebel CRM
It is strongly recommended that you implement Transport Layer Security (TLS) encryption for all of the following services and communication paths in a Siebel CRM implementation:
For communications between Siebel Web server and Siebel Web Client.
For communications between Siebel Server and the Web server.
For encryption of communications between Siebel Enterprise components, for example, communications between the Siebel Server to Siebel Web server (Siebel Application Interface), or between Siebel Servers.
For communications between an LDAP security adapter and a directory server.
For communications using Siebel CRM external interfaces (EAI), which use Web services to send and receive messages over HTTP.
For communications between Siebel Server and an email server, including encryption for SMTP, IMAP, and POP3 sessions between Siebel Server and an email server.
For more information about the support for TLS encryption provided by Siebel CRM, see Supported TLS, SHA-2 and SHA-3 and 1944467.1 (Article ID) on My Oracle Support. For more information about configuring security in Siebel CRM, see Roadmap for Configuring Security.
Supported TLS, SHA-2 and SHA-3
This topic lists the level of support for TLS and RSA SHA (including SHA-192, SHA-224, SHA-256, SHA-384, and SHA-512). Siebel implements TLS security for the services and communication paths listed in Using Transport Layer Security with Siebel CRM.
TLS Support
It is strongly recommended that you move the following services in Siebel to a more secure TLS configuration as follows:
Siebel Application Interface to Client HTTPS traffic encrypted via TLS 1.2
Siebel Cloud Gateway to Siebel Server internal traffic encrypted via TLS 1.2
Siebel EAI/Web Services over HTTPS encrypted over TLS 1.2
Siebel IMAP/POP encrypted over TLS 1.2
Siebel Server to SWSE SISNAPI Traffic encrypted over TLS 1.2
Siebel Enterprise SISNAPI Traffic encrypted over TLS 1.2
Siebel ADSI client encrypted over TLS 1.2
Siebel LDAPS client encrypted over TLS 1.2
Siebel Management Server/Agent Traffic encrypted over TLS 1.2
Siebel (SSSE) to Exchange encrypted over TLS 1.2
Siebel SISNAPI traffic encrypted over TLS 1.2
Siebel WebLogic Integrations (Such as BIP) over TLS 1.2
Application Interface HTTPS Traffic Using TLS 1.2
Application Interface fully supports TLS 1.2 encryption for client-side connections, including reverse proxy configuration. TLS configuration, including application interface and Web client encryption, for this part of the product is detailed in Communications and Data Encryption.
Application Interface always uses TLS to communicate with Siebel Gateway, Siebel Management Console and Siebel database. Encryption for these connections cannot be disabled but you can force the use of TLS 1.2 (https://tomcat.apache.org/tomcat-8.0-doc/ssl-howto.html). For Siebel, the Tomcat JSSE (Java Secure Socket Extension) implementation and Java configuration is used (https://www.java.com/en/configure_crypto.html provides information on the granular configuration for TLS; as an example, you can limit Java to use only TLS 1.2).
To force the use of TLS 1.2, set the following in the server.xml file: clientAuth="false" sslProtocol="TLS1.2". All servers (Siebel Management Console, Application Interface, Siebel Gateway) require this setting. For example:
<Connector port="443" protocol="org.apache.coyote.http00.Http00NioProtocol" maxThreads="150" SSLEnabled="true" scheme="https" secure="true" SSLVerifyClient="require" SSLEngine="on" SSLVerifyDepth="2" keystoreFile="E:\Siebel\AI\applicationcontainer\siebelcerts\keystore.jks" keystorePass="siebel" keystoreType="JKS" truststoreFile="E:\Siebel\AI\applicationcontainer\siebelcerts\keystore.jks” truststorePass="siebel" truststoreType="JKS" clientAuth="false" sslProtocol="TLS" sslEnabledProtocols="TLSv1.2"/>
LDAPS (Encrypted) Over TLS 1.2
The LDAP service is usually hosted behind a secure firewall. Customers using Oracle LDAP client can encrypt traffic using TLS 1.2. This may require the latest patches of the Oracle Database Client certified for the product. Make sure that the latest security patches are installed for proper functionality.
Inbound EAI/Web Services Over HTTPS Encrypted Over TLS 1.2
Siebel supports EAI inbound on all platforms using the native support for TLS 1.2 and the support of the Web Server.
Outbound EAI/Web Services Over HTTPS Encrypted Over TLS 1.2
TLS 1.2 is supported on all platforms. It is recommended that you host this service behind a secure firewall. Communications and Data Encryption describes how to configure TLS and components for secure communications. EAI object managers remain compatible with SSL 3.0 but it is recommended that you only use TLS 1.2. You can use only one transport per object manager.
Siebel Message Queueing Support and JMS Over TLS 1.2
You can encrypt this service using TLS 1.2. It is recommended that you host this service behind a secure firewall. Communications and Data Encryption describes how to configure TLS and components for secure communications. For encryption information, see Configuring TLS Encryption for Siebel Enterprise or Siebel Server.
Siebel Management Server/Agent Traffic Encrypted Over TLS 1.2
Communications and Data Encryption describes how to configure TLS and components for secure communications. Customers using SSL may expose data to severe vulnerability risk.
Email Response/IMAP/POP/SMTP Over TLS 1.2
You can encrypt this service to varying degrees depending on technology. IMAP/POP3/SMTP can support TLS 1.2. For information about TLS configuration for this part of the product and about email response and encryption, see Siebel Email Administration Guide. OpenSSL is an option for TLS 1.2 connections with POP3. You can enable this by using the EnableOpenSSL parameter on the Mail component. OpenSSL v1.0 does support the "DHE-RSA-AES256-SHA" cipher. Use of IMAP with TLS 1.2 requires the use of JavaMail 1.6.3 or higher.
Siebel Enterprise SISNAPI TCP-IP Traffic Encrypted Over SSL
You can encrypt this service using TLS 1.2.
Siebel WebLogic Integration (such as BIP)
Log in to the WebLogic console.
Click <Domain>, Environment, Servers, <Server>.
Under Configuration and General, make sure the SSL Listen Port Enabled check box is selected.
Go to the SSL tab, click Advanced, and make sure that the Use JSSE SSL check box is selected..
Restart WebLogic for the changes to take effect.
Java Secure Socket Extension (JSSE) enablement sets WebLogic to use the TLS features of Java instead of its own SSL implementation. (WebLogic’s internal SSL implementation is not compatible with the current TLS implementations in modern browsers.) WebLogic 12.2.1.0.0 uses JSSE by default and does not have check boxes anymore to switch back to its own version of SSL. To force TLS 1.2, set weblogic.security.SSL.protocolVersion=TLSv1.2 in the WebLogic startup parameter in setDomainEnv.sh. This will reject any client that does not support TLS 1.2.
SHA-2 and SHA-3 Support
Siebel implements SHA functions in a variety of use cases. The secure hashing algorithm supported is based on the certificate type implemented and the support level provided by Siebel. The level of support for SHA-2 and SHA-3 (including SHA-192, SHA-224, SHA-256, SHA-384, and SHA-512) is as follows:
SHA-2 and SHA-3 (limited by third party used)
Web server to Web Client
MQ and JMS
SHA-2
EAI SOAP Web services
EAI HTTP Transport business service
Email response IMAP/POP (OpenSSL can be used)
SISNAPI
Oracle LDAP Client (may required the latest database clients)
About Siebel Open UI
Siebel Open UI is the most secure Siebel CRM client available and is therefore recommended if your Siebel implementation has high-security requirements. In particular, note the following about Siebel Open UI:
Siebel Open UI uses an open architecture that allows you to run Siebel CRM on any Web browser that is compliant with the World Wide Web Consortium (W3C) standards. Siebel Open UI also supports a number of operating systems, including Windows, Mac OS, or LINUX.
The Siebel Open UI client is compatible with many security features supported by the Web browser on which it runs.
Siebel Open UI uses only three technologies to render the client code: HTML, CSS, and JavaScript. Because of the small set of underlying technologies that are used to render the client and the absence of third-party plug-ins, Siebel Open UI provides the smallest possible attack surface.
Siebel Open UI clients enforce session security by requiring that session IDs can only be passed in session cookies. For information, see Session Cookie.
For additional information about Siebel Open UI, see Deploying Siebel Open UI and Configuring Siebel Open UI.
Roadmap for Configuring Security
This topic provides a general overview of tasks you can perform to take advantage of security resources for Siebel CRM. Use this topic as a checklist for setting up security for your Siebel environment.
Each task includes a pointer for more information on how to perform the task. Pointers include references to later topics in this guide as well as to other documents on the Siebel Bookshelf.
To configure security, perform the following tasks:
During Siebel CRM installation, plan your Siebel Server and port usage for firewall access.
For guidelines on implementing firewalls and port usage, see Siebel Security Hardening.
After you install Siebel CRM, change the passwords for Siebel accounts regularly:
Change the password for the Siebel administrator account regularly.
Add a password for updating Web server images.
For more information, see Changing and Managing Passwords.
Make sure communications and important data is encrypted. See Communications and Data Encryption.
Implement security adapter authentication or Web Single Sign-On to validate users. For more information, see Security Adapter Authentication and Single Sign-On Authentication.
Set up an access control system to control user visibility of data records and Siebel application views. For more information, see Configuring Access Control.
Enable audit trail functionality to monitor database updates and changes.
For information on Siebel audit trail functionality, see Siebel Security Hardening and Siebel Applications Administration Guide.
Make sure communications between Mobile Web Clients and your Siebel site are secure.
Enable encryption for Mobile Web Clients. See Configuring Encryption for Mobile Web Client Synchronization.
For other Mobile Web Client security issues, such as changing passwords on the local database, and encrypting the local database, see Siebel Remote and Replication Manager Administration Guide.