Understanding Data Encryption for Payroll for North America
This topic provides additional information about the implementation of the bank account number encryption that is specific to Payroll for North America.
The content is grouped into these sections:
Video: Image Highlights, PeopleSoft HCM Update Image 39: HCM Encryption Configuration
Video: Image Highlights, PeopleSoft HCM Update Image 40: HCM Encryption Product Uptakes
To comply with Nacha’s data security requirements, Payroll for North America uses the HCM Encryption Framework to encrypt and mask bank account numbers stored in the database.
This table lists the source records delivered for bank account number encryption, the products or functional areas in which they are used, and the pages on which bank account numbers are masked when encryption is run on them.
Use this table as a tool to decide which source records need to be encrypted for your products. For example, if you want to encrypt bank account numbers in your Federal Payroll system, set the action to encrypt all the source records that are listed for Federal Payroll in this table when you run the encryption process (HCCRYPTAE).
|
Source Record |
Used In |
Pages |
|---|---|---|
|
DIR_DEP_DISTRIB |
|
|
|
GARN_SPEC |
Payroll for North America |
Deduction Distribution Information Page from the Garnishment Spec Data 6 page (U.S. version). |
|
GENL_DEDUCTION |
Federal Payroll |
|
|
GP_RCP_PYE_DTL |
Global Payroll for United States |
Add Deduction Recipients Page. See Also Understanding Data Encryption for Global Payroll for United States. |
|
GVT_DED_DIST |
Federal Payroll |
Deduction Distribution Information page from the General Deduction Distribution Page. |
|
GVT_GARN_PAYEE |
Federal Payroll |
(USF) GVT Employee Distribution Page from the Garnishment Payee Table page. |
|
GVT_GARN_SPEC |
Federal Payroll |
Deduction Distribution Information Page from the Garnishment Spec2 page. |
|
GVT_PAM_SAL_DTL |
Federal Payroll |
Not applicable (Source record is used in PAM/SPS reporting) |
|
GVT_PAM_VEN_SUM |
Federal Payroll |
Not applicable (Source record is used in PAM/SPS reporting) |
|
GVT_TAX_ROUTING |
Federal Payroll |
|
|
PYE_BANKACCT |
Global Payroll for United States |
See Also Understanding Data Encryption for Global Payroll for United States. |
|
PY_BNKACCT_XREF |
|
Not applicable (Source record used in the check reconciliation process) |
|
RECIPIENT |
Global Payroll for United States |
Define Deduction Recipients Page. See Also Understanding Data Encryption for Global Payroll for United States. |
|
SRC_BANK |
|
|
|
VNDR_BANK_ACCT |
|
Bank Accounts Page from the Vendor Information - Locations page. |
After the encryption process is run for the selected source records, the account numbers are encrypted and masked in the database. The account numbers displayed on the corresponding pages are also masked, unless the users are granted the roles that allow them to view the unmasked data. See the Delivered Roles For Viewing Unmasked Data topic for system-delivered roles that grant access to unmasked data. For the Request Direct Deposit page (for administrator) and the Direct Deposit page (for employee), the masking of the account numbers is controlled by the installation options rather than the encryption process. See the Direct Deposit Installation Options and Data Masking topic for more information.
The encryption (or decryption) process for the bank account numbers should only be run when users are not allowed to access or update the bank account numbers in the database.
In most cases, the encryption process needs to be run only once unless there is compelling reason to do so again later (for example, changing to a new encryption profile). While it is not practical to prevent users from accessing the system during the encryption run, there are certain pages, processes, and programs from which users must be locked out in order to prevent inconsistent or unpredictable outcomes. They are:
Pages:
Employee Self-Service Direct Deposit page.
Administer Request Direct Deposit page.
Deduction Distribution Information page from the Garnishment Spec Data 6 page (U.S.).
Source Banks Account page.
(USF) Employee Deduction Distribution page from the Create General Deductions page.
(USF) Distribution Information page from the Voluntary Deductions page (employee self-service page).
(USF) Deduction Distribution information page from the General Deduction Distribution page.
(USF) GVT Employee Distribution page from the Garnishment Payee Table page.
(USF) Deduction Distribution Information page from the Garnishment Spec2 page.
(USF) State Tax Routing 1 page.
(USF) Locality Tax Routing 1 page.
Batch processes: The Confirm process.
Programs that access account details: DDP001, DDP001CN, DDP002, DDP003, DDP003CN, DDP004, DDP005, DDP006, FGPY040, FGPY041, PAY003, PAY003CN, PAY040, PY_DIRDEP, and TAX870EU.
Payroll for North America delivers two roles that allow the administrator(s) to view unmasked account numbers for direct deposit, EFT child support garnishment payments, the Source Bank Accounts table, and vendors, even though the numbers are masked for everyone else. These roles are:
Bank Account Admin
This role allows users to see the unmasked account numbers on all administrator pages that store bank account numbers. Some examples include, but not limited to, the Request Direct Deposit Page, the Deduction Distribution Information Page from the Garnishment Spec Data 6 page, and the Bank Accounts Page for vendors.
This role also allows users to see the unmasked account numbers on the Source Bank Accounts Page and (CAN and USA) Canada Bank Additional Data or US Bank Additional Data Pages.
Source Bank Account Admin
This role allows users to see the unmasked account numbers on the Source Bank Accounts Page and (CAN and USA) Canada Bank Additional Data or US Bank Additional Data Pages.
See Also Grant Unmasked Access Page.
The installation options for direct deposit determine the masking of bank account numbers on direct deposit pages.
This example illustrates the Direct Deposit section of the Payroll for NA Installation page.
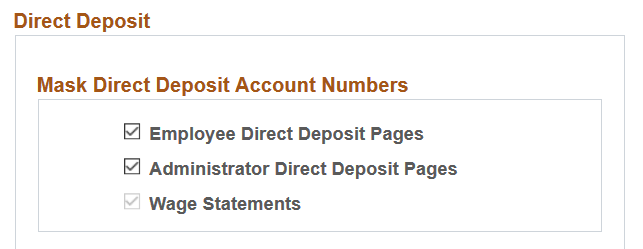
Wage Statements
When the Enable Encryption option is enabled on the HCM Options Page of the Installation Table, the Wage Statements option becomes selected and not editable by default. All account numbers on the wage statements, for both HTML (online pages) and PDFs will display as masked after the encryption is run.
Employee and Administrator Direct Deposit Pages
The masking of account numbers on the employee and administrator direct deposit pages is controlled by the Employee Direct Deposit Pages and Administrator Direct Deposit Pages options on the HCM Options page.
After encryption is run for the DIR_DEP_DISTRIB record, all account numbers will display as masked on the Direct Deposit Page and Request Direct Deposit Page if the options are selected. An exception to this is when the user is assigned the Bank Account Admin role, and this role is defined on the Grant Unmasked Access Page for the DIR_DEP_DISTRIB record. With this role, the user can view unmasked account numbers on the Request Direct Deposit page.
If these installation options are deselected, the account numbers on the same pages will not be masked.
Note: When DIR_DEP_DISTRIB is encrypted, the account numbers in the database are still masked even if the installation options for the direct deposit pages are deselected when DIR_DEP_DISTRIB is encrypted.
Each time an employee enters direct deposit data in Employee Self Service, audit records are added to the Direct Deposit Audit Record (PY_IC_DD_AUDIT).
(USF) In addition, audit records are added to the General Deduction Audit Record (PY_IC_DED_AUDIT) when federal employees enter general deduction data in Employee Self Service.
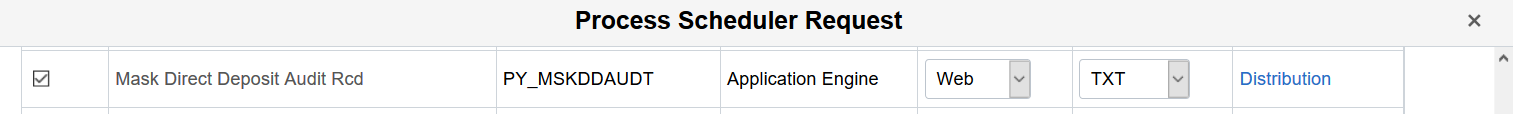
The account numbers in the audit records can be masked by running the Mask Direct Deposit Audit Rcd (PY_MSKDDAUDT) process after DIR_DEP_DISTRIB and GENL_DEDUCTION are encrypted. By running the process, all account numbers in both records will be masked.
To access the Process Request Dialog run control page, navigate to: . Click Run. Then, select the Mask Direct Deposit Audit Rcd row in the Process List section, and click OK.
This example displays the Mask Direct Deposit Audit Rcd process on the Process Schedule Request page, which is used to mask direct deposit account numbers in the audit record.
The Mask Direct Deposit Audit only needs to be run once. Subsequent updates for employee direct deposit transactions entered through Employee Self Service and general deduction transactions entered through Employee Self Service Voluntary Deduction will automatically be masked since the DIR_DEP_DISTRIB and GENL_DEDUCTION records have already been encrypted.
Important! Once the direct deposit account numbers have been masked in the PY_IC_DD_AUDIT and PY_IC_DED_AUDIT records, the direct deposit account numbers in the audit records cannot be unmasked.
Masked account numbers are displayed on advices and paychecks with partial direct deposit account number details when DIR_DEP_DISTRIB is encrypted.
Direct Deposit Register (DDP002)
Advice Print – US (DDP003)
Advice Print – Canada (DDP003CN)
Pay Check Print – US (PAY003)
Pay Check Print – Canada (PAY003CN)
Masked account numbers are displayed on these reports when DIR_DEP_DISTRIB is encrypted:
Payroll Advice Register (DDP004)
Direct Deposit Prenotification report (DDP005)
Direct Deposit Prenote Memo (DDP006)
Unmasked account numbers are displayed on the reports when DIR_DEP_DISTRIB is not encrypted.
Account numbers are always unmasked on these files, even when corresponding records are encrypted:
Direct Deposit files (DDP001 & DDP001CN)
Child Support – EFT file (PAY040)
Qtrly Wage - Eugene report (TAX870EU)
Treasury Interface Bulk File (FGPY041)
The bank account numbers that appear on the Vendor Listing report are masked when encryption is run on the VNDR_BANK_ACCT source record.
See Also Maintaining Vendor Information
When using VENDOR_SYNC, the bank account numbers will not be masked in the inbound or outbound messages, even if encryption is run on the VNDR_BANK_ACCT source record.
The bank account numbers that appear on these Check Reconciliation reports, Error Listing (PAY015A) and Checks Reconciled From Unprocessed Manual (PAY015B), are masked when encryption is run on the SRC_BANK and PY_BNKACCT_XREF source records.
The system includes a data conversion process (AE program DC33195853) that automatically sets the encryption status for the PY_BNKACCT_XREF source record to None or Encrypted, depending on whether data exists in the PAY_CHECK_DUE table or not.
Scenario 1: No Data in PAY_CHECK_DUE
If there isn’t any data in the PAY_CHECK_DUE table at the time the Data Conversion process is run, the process will always set the encryption status of the PY_BNKACCT_XREF source record to None on the Define Source Records Page.
Then during the first run of the Check Reconciliation process (PAY015A.SQR), it adds data in the PY_BNKACCT_XREF source record and updates the encryption status with the same value as the SRC_BANK source record.
If the encryption status of the PY_BNKACCT_XREF source record is not what you expected after the first run of the Check Reconciliation process, you can navigate to the Manage Encryption and Masking Page, select Encrypt (or Decrypt) in the Action field for the PY_BNKACCT_XREF source record to run the encryption process.
Scenario 2: Data Exists in PAY_CHECK_DUE
If data exists in the PAY_CHECK_DUE table at the time the Data Conversion process is run, the process creates a new PY_PAYCHECK_DUE table and generates data in the PY_BNKACCT_XREF source record. The process will automatically default the encryption status for PY_BNKACCT_XFER based on status of SRC_BANK. For example, if SRC_BANK displays Encrypted, PY_BNKACCT_XFER will also display Encrypted.
If the PY_BNKACCT_XFER source record is decrypted (or encrypted again) in the future, the status is set based on the action defined for its row on the Manage Encryption and Masking Page.
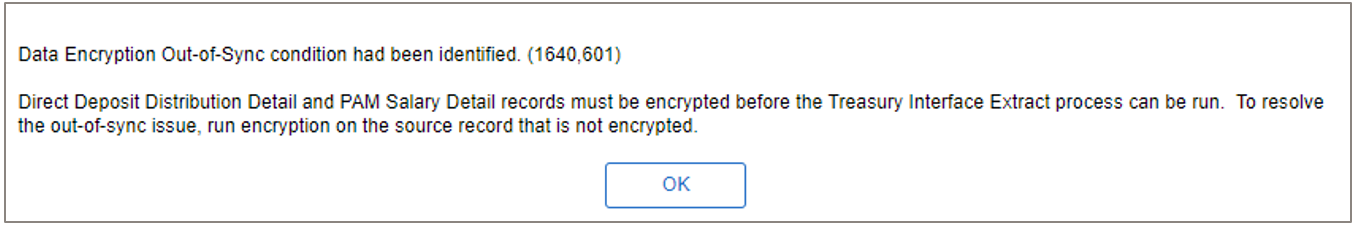
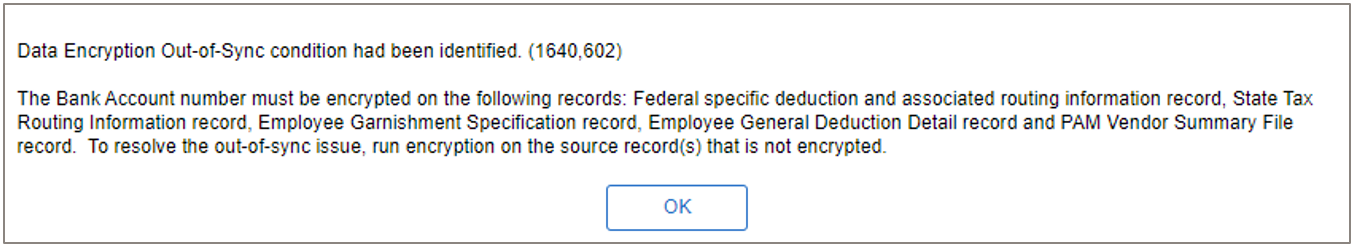
The system includes two error messages to ensure that the required source records are encrypted when running the Treasury Interface Extract process (FGPY040.SQR).
This example illustrates the error message that appears online when the Treasury Interface Extract Page is saved in any of these scenarios: 1) DIR_DEP_DISTRIB is encrypted and GVT_PAM_SAL_DTL is decrypted, or 2) GVT_PAM_SAL_DTL is encrypted and DIR_DEP_DISTRIB is decrypted.
This example illustrates the error message that appears online when the Treasury Interface Extract Page is saved and one or more of the bank account numbers is not encrypted on these records: GENL_DEDUCTION, GVT_DED_DIST, GVT_GARN_SPEC, GVT_GARN_SPEC, GVT_PAM_VEN_SUM, and GVT_TAX_ROUTING.
If the Treasury Interface Extract run control page was saved in the database before encryption was run, the Out-of-Sync messages will not appear online when the page is saved. Instead, the Out-of-Sync messages will be added to the FGPY040 log file.
To ensure that the Treasury Interface Extract process runs successfully, you must first encrypt these source records:
DIR_DEP_DISTRIB
GENL_DEDUCTION
GVT_DED_DIST
GVT_GARN_SPEC
GVT_PAM_SAL_DTL
GVT_PAM_VEN_SUM
GVT_TAX_ROUTING
If the need arises, account numbers can be decrypted on the Manage Encryption and Masking Page.
Specify Decrypt as the action for the source record you want to decrypt. The available values are controlled based on the Action value for the source record. Here are the examples for Payroll for North America:
DIR_DEP_DISTRIB options:
For the Decrypt action, the Process Record Mask value can be Do not Unmask or Unmask.
GARN_SPEC and SRC_BANK option:
For the Decrypt action, the Process Record Mask value is None (default and display only).
Suppose that the DIR_DEP_DISTRIB source record is decrypted, after the process completes, the run control status is Decrypted and the action is None (default).
Note: When you run the decryption process on a source record, the process decrypts the encrypted data for all entries in that source record, even though the data selection for the encryption of the source record was country-specific.