Understanding PeopleSoft CRM Security
This topic discusses:
Security building blocks.
Security terminology.
PeopleTools security.
Application security.
Distributed security.
This diagram provides an illustration of the different layers of security that are delivered in the PeopleTools and Customer Relationship Management security infrastructure. This topic will cover each of these security building blocks to assist you in implementing the security needed for your enterprise.
Image: Security building blocks
This diagram provides an illustration of the different layers of security that are delivered in the PeopleTools and Customer Relationship Management security infrastructure.
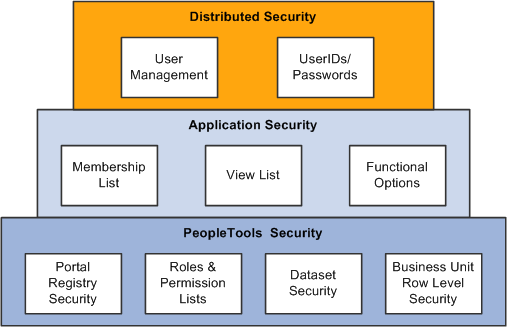
PeopleTools security controls row-level access to transactions. For example, you would use dataset security to enable a sales representative to see leads as the lead owner, or to enable a sales manager to view leads as manager, and so on.
Application security provides three key elements of CRM security: memberships lists, view lists, and functional options. Membership lists can define the characteristics of one or a group of users whose system and data access must be secured. View lists can define the characteristics of one or a group of objects (for example, customers) that a member group has view privileges to. Functional options restrict the user to a set of allowable actions within a secured transaction.
Distributed Security or Delegated administration enables you to set up administrators that are external to your enterprise so they can give other users system access, within the confines of the permissions that you allow the administrator to grant.
Before you can fully enable security, you must understand the security terms and functions at each level of the system:
|
Security Type |
Where Implemented |
Function |
|---|---|---|
|
Network |
Network software |
Controls entry into the network and authorizes rights to use shared resources. |
|
Relational database management system |
Operating system |
Controls access to the database. |
|
User |
PeopleTools |
Controls access to application pages, functions, and business components. |
|
Object |
PeopleTools |
Controls access to objects or object groups that are used in application development. |
|
Query |
PeopleTools |
Defines the set of table rows that a user can access while making system queries. |
|
Row-level |
PeopleTools and PeopleSoft applications |
Restricts access to a subset of data rows within tables to which the user has authority. |
|
Permission list level |
PeopleSoft applications |
Enables PeopleSoft application security. |
Use PeopleTools security to define roles and permissions. PeopleSoft delivers a set of roles out of the box that you can use to set up role-based access to PeopleSoft transactions. PeopleSoft provides a recommended set of roles and permissions with each of the products delivered. You can add or modify new or existing roles and permissions to fit your business requirements.
This topic discusses
Portal registry.
Roles and permission lists.
Dataset security.
Business unit row level security options.
Preferred markets and security.
Portal Registry
The portal registry is a set of dedicated PeopleSoft database tables that store every content reference, typically a URL, available through the portal. A portal registry has a tree-like structure in which content references are organized, classified, and registered. A portal registry contains folders and content references. Folders group and organize content references into a multilevel hierarchy. Except for the root folder, each folder has a parent folder, and each folder can contain content references as well as other folders. Content references are objects that have been registered in the portal registry.
There are several ways to access and maintain the portal registry:
Use the registration wizard to register content references, assign security, and update.
Use the Menu Import feature to upgrade custom menu group definitions.
Use portal administration pages to add, change, or delete folders and content references from a portal registry.
Use the portal registry application programming interface (API) for programmatic access to the registry.
Use the security synchronization process to update the portal registry security based on the menu and script security.
See PeopleTools: Portal Technology product documentation.
Roles and Permission Lists
Permission lists are the building blocks of user security authorizations. You typically create permission lists before you create user profiles and roles. When defining permission lists, however, consider the roles and user profiles that you will use them with. Recall that roles are intermediary objects between permission lists and users. You use roles to assign permissions to users dynamically. Permission lists may contain any number of permissions, such as sign-in times, page permissions, and component interface permissions. Permission lists are more flexible and scalable when they contain fewer permissions.
Dataset Security
Dataset security controls row-level access to transactions. Dataset security is achieved by associating the definition of a dataset to the search definition for transactions that have multiple dataset rules. PeopleSoft dataset security framework may be used to build dataset rules and assign the dataset rules to PeopleTools roles.
PeopleSoft delivers a set of dataset security rules that may be used to secure transaction rows. PeopleSoft CRM uses dataset security for data searches to restrict transaction rows.
It is also used in these applications and functions:
PeopleSoft Sales (leads and opportunities).
PeopleSoft Order Capture (quotes and orders).
Calendar and Task Management.
PeopleSoft Marketing (audience and marketing programs).
Business Unit Row-Level Security Options
You can implement security to prevent individual users or roles from accessing specific rows of data that are controlled by key fields. Likewise, you can restrict users so that they can access only a specific subset of rows. For example, you might set the user ID security for a call center agent in Paris so that the agent can access only the data that is for a particular European business unit. If you have a team of call center agents in Paris, you could add them all to a role and then use role security to give them all the same access to the system.
A user can belong to multiple roles and use the menu items that are assigned to all of those roles.
Note: You cannot define row-level security attributes by combining roles. In PeopleTools, you designate row-level security for a user by selecting a row-level security role. The row-level security attributes for the role that you select become the security attributes for the user.
This table describes the consequences of row-level security when you use different combinations of system security options and roles:
|
System Security |
Role of User ID |
Row-Level Security |
|---|---|---|
|
No security |
The user ID is not linked to a role. |
Not applicable. All users can access every object because you have not implemented security. |
|
User-level security |
The user ID is not linked to a role. |
Defined in the application by key field security. |
|
Role-level security |
A user ID is normally assigned to a row-level security role. You can link a user ID to multiple roles, but not when you specify row-level security. |
Defined by a row-level security role. If a user ID is not assigned to a row-level security role, then the user has access to menu items but not to any application pages with key fields that are enabled for row-level security. |
|
Permission list-level security |
All users in a permission list have the same level of security. |
Users are limited to the key fields that are specified by the permission list that is assigned to their user IDs. |
You must define the users or roles that have access to specific business units and setIDs. For example, you might give a particular role access to only one business unit. When a user in the role enters prompts for business units (for example, when entering data that has business unit as the primary key), the available selections include only the business units for which the user has been granted authority. The user's available data has been filtered through one or more levels of security.
The number of users that are assigned the same level of security is a key factor in determining whether you base security on user IDs or roles. If a large number of users have identical access requirements, consider using roles. By assigning the users to a single role, you can make subsequent changes to access requirements once rather than many times.
Preferred Markets and Security
The preferred market that is associated with a user ID controls the data and functions that a user can access. Preferred markets are of two types: industry and geographic.
If a user's preferred market is geographic, the user can only access functionality and data that are valid for business units in the geographic region or country. For example, a country might require certain information about imports that users in another country would not need to enter.
If the user's preferred market is by industry, the user is granted access to only the functionality and data that are implemented for those industries.
See:
“Understanding Portal Technology” in Peopletools Portal technology product documentation.
PeopleTools: Security Administration
This topic discusses:
Enterprise administration.
CRM application security terminology.
Application security framework.
Security objects.
Dynamic and static membership lists.
Dynamic and static view lists.
Implicit view lists.
Functional options.
Functional option groups.
Functional options conflict resolution.
Enabling functional options.
Business object search system processing.
Catalog security.
How security is processed at runtime.
Enterprise Administration
Application Security consists of three main pieces: membership lists, view lists and functional options. Using PeopleSoft CRM application security, enterprise administrators have the ability to:
Define the community of participants for which security is restricted (membership list)
Define a set of business processes or actions that a participant in the membership group can perform.
CRM Application Security Terminology
This table lists terms related to security:
|
Term |
Definition |
|---|---|
|
Security Object |
An object or entity that is being secured. |
|
Membership List |
Characteristics of one or a group of users whose system and data access must be secured. The list ultimately contains a list of members. |
|
View List |
Characteristics of the viewing object (for example, customers) that are secured from the membership list. The list ultimately contains a list of objects. |
|
Functional Options |
A unique code that defines what someone can do within a transaction. |
|
Functional Option Group |
A grouping of functional options. |
|
Security Profile |
A template that defines the view lists and functional options. A security profile is given to one or multiple membership list domains. |
|
Transaction |
A primary business activity like creating orders, leads, opportunities, cases, service orders, and campaigns. |
|
Security List Record |
A table that stores the results of the security domain queries or the static list. |
PeopleSoft CRM Application Security Framework
PeopleSoft CRM application security framework is a characteristic-based security framework that enables PeopleSoft customers to secure data and functions within a transaction.
Use PeopleSoft application security to abstract customers as security objects. The characteristics that define the group of customers are called lists.
You can predefine the objects and lists as either membership or view to differentiate viewers from the target transactions or data objects.
Note: Application security is used only to secure objects (person, customer, product catalog, hold codes, performance metrics, and so on) and not transactions (orders, leads, opportunities, cases, and so on). Objects in this context mean setup data or data that is used to create a transaction.
PeopleSoft CRM does not deliver an application security feature for securing customers from user roles. To make this work, you would have to customize the security criteria in the Business Object Search adapter definition and then make some minor coding adjustments.
Application security involves setting up and defining:
Membership lists
Membership lists define the characteristics of one or a group of users to whom system and data access and functional permissions and privileges are granted. Users in a security membership list definition are associated with a security profile.
View lists
View lists define the characteristics of the viewing object (for example, customers or product catalogs) that are secured from the membership list.
Functional options
Functional options define the functions (for example, order submission) that can be carried out by members of a membership list.
Security profiles
Security profiles define the combination of view lists and functional options that make up a specific profile of view and function access. Security profiles are given to members belonging to a membership list.
This illustration represents a high-level view of a security profile using PeopleSoft CRM Application Security.
Image: Security profile definition
This illustration represents a high-level view of a security profile using PeopleSoft CRM Application Security.
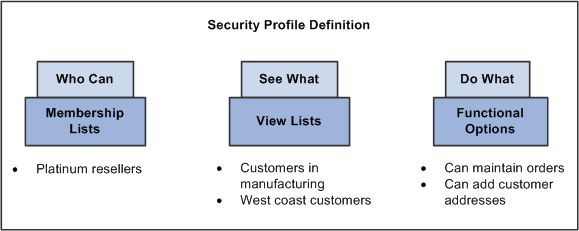
Security Objects
PeopleSoft delivers a number of security objects that you can use to implement security. You should not, however, change them in any way. Any changes that you make to the security objects delivered by PeopleSoft impact the security profiles and the security list tables. PeopleSoft recommends that you limit the number of security objects that you create and are careful how you use them.
PeopleSoft delivers these membership type security objects:
|
Security Membership Object |
Security Object Type |
Industry |
|---|---|---|
|
Customer |
Membership |
Order Capture |
|
Person |
Membership |
All |
|
Role |
Membership |
All |
Dynamic and Static Membership Lists
A dynamic membership list is a saved query of characteristics that result in a list of members for a membership list object. The queries are saved using the dynamic criteria definition that is linked to the membership list object.
If the domain type is dynamic, you can edit the membership criteria using the appropriate dynamic criteria definition. You can also view the results of the membership list.
You may associate the membership list to any security profile currently available in the system. Once you associated the membership list with a security profile, that security profile appears in the security profile list for the membership list. When needed, you can remove the association of the membership list to the security profile.
Static membership lists contain a specific list of members that you may associate with any security profile currently available in the system.
Dynamic and Static View Lists
A dynamic view list is a saved query of characteristics that results in a viewable list of objects. You set up a view list object similar to the way you set up a membership list object. After you establish a view list, you may grant one or more view list objects (dynamic or static) to a security profile.
Note: Not all objects can be used as view list objects.
PeopleSoft delivers these View List Security Objects as system data:
|
View List Security Object |
Security Object Type |
Application |
|---|---|---|
|
Catalog |
View List |
Order capture |
|
Customer |
View List |
All |
|
Hold Code |
View List |
Order capture |
|
Performance Metric |
View List |
Marketing |
Implicit View Lists
A dynamically defined view list can contain a bind variable or a criteria that is not resolved at the time of creation of the query but is resolved at runtime. This is called an implicit view list.
To set up an implicit view list, you must use the Configurable Search Setup - Search Fields page to select the bind variable for the security components and fields that you want to use on the Add View List or Add Membership List pages.
You can modify the Customer Search (RSEC_CUSTOMER_SRCH) component to use bind variables and create implicit view lists.
Functional Options
Functional options are defined independently of security objects and domains. Functional options let you determine what a user you can do within an application. For example, you can create functional options that enable users to submit orders or add new customers. To group view lists and functional options, you define a security profile. The security profile is then granted or associated to one or multiple membership lists.
Functional Option Groups
Functional option group is a grouping of functional options, which you can be associated with a security profile. Using functional option groups can make maintaining security profiles easier and more efficient. Enterprise administrators that must make wholesale changes to security profiles can simply change the functional option group associated with the security profiles that must be changed or updated.
Functional Option Codes
Functional options enable the enterprise administrator to define the functions that users can access within a transaction. Functional options codes are evaluated at run time by the transaction that is evaluating the functional option.
PeopleSoft delivers these functional options codes out of the box when you install and implement PeopleSoft CRM:
|
Functional Option Code |
Description |
Application/Function |
|---|---|---|
|
CORE_RSF_FCAST_ROLLUP |
Forecast will begin in rollup; otherwise it begins in summary. |
Sales |
|
CORE_RSF_FCAST_SIMPLE |
Forecast simple reduces options presented to the forecast user. |
Sales |
|
CORE_RSF_ADVANCED |
Controls basic versus advanced mode for lead and opportunity components. |
Sales |
|
CORE_RSF_AUTO_ASSIGN_OFF |
Controls the ability to automatically assign a lead or opportunity at save in add mode. |
Sales |
|
CORE_RSF_DEFAULT_OWNER |
When lead or opportunity is in add mode at save time, the current user is assigned as the primary sales rep by default. If revoked, then leave lead or opportunity unassigned. |
Sales |
|
CORE_RSF_SEARCH_PRODUCT_GROUP |
Enables the end user to search for product group on leads and opportunities. |
Sales |
|
CORE_RSF_SHOW_SITE |
Controls the ability to add a site to a lead or opportunity. |
Sales |
|
CORE_RSF_SUMMARY |
Control the display of the summary page in lead and opportunity. |
Sales |
|
OVERRIDE_IBU |
Override Inventory BU |
Order Capture |
|
RO_MAX_DISCOUNT_PERCENT |
Maximum discount percent. |
Order Capture |
|
RO_MAX_ORDER_TOTAL |
Maximum order total reached. |
Order Capture |
|
RO_MAX_SURCHARGE_PERCENT |
Maximum surcharge percent. |
Order Capture |
|
RO_MIN_MARGIN_PERCENT |
Maximum profit margin percent. |
Order Capture |
|
SEARCH_ALL_PRODUCTS |
When searching for products in Order Capture, this functional option give the user the ability to search for any products that are defined in the system instead of limiting them to the products that are defined in a catalog. |
Order Capture |
|
MKTHIDE |
Hides marketing fields. |
Marketing |
|
MKTDISP |
Makes marketing fields display-only. |
Marketing |
|
RC_CHOOSE_DIRECT_REPORT |
Choose Direct Report |
Call Center |
|
RC_ON_BEHALF_OF |
On Behalf of |
Call Center |
|
RC_SLA_DETACH |
Enables user to clear a service level agreement. |
Call Center |
|
RTM_EDIT_TASK |
Edit task functional option. |
Task Management |
|
QC |
Provides access to Quick Create. |
Business Object Search |
Functional Options Conflict Resolution
Conflicts can happen due to the granting of the same functional options within a single security profile or multiple security profiles. To resolve conflicts the system uses these rules:
If one functional option group grants an option and another revokes it, the revoke takes precedence. If the options are not in the same scenario, the option is granted. Revoke is for the functional option itself. (for example, do you have authorization for transfer money). If one functional option group says yes and another no, conflicts are resolved based on how the revoke options are set up.
For amounts there is a conflict resolution called max amount wins. This means that if one functional option group gives a user access to 2000 USD and another functional option group give a user access to 3000 USD, and the max amount win option is selected, the user gets access to 3000 USD.
Enabling Functional Options
The display template framework enables you to configure functional option security for your pages. By referencing the functional option on a button or field within the display template, the functional option security is enabled.
Business Object Search System Processing
The transaction adapter determines, based on the transaction, what fields appear on the customer information subpage and the criteria definition that defines the advanced search page. The criteria definition determines what criteria fields appear on the advanced search page, how they appear, and the search definitions to invoke.
The search definition determines the roles to search for the criteria fields, the fields that appear in the search results, how the search results appear, and the quick create definition that the user accesses to create a new business object.
For each role that is searched, the search role determines the security that is applied, the relationships for the role, and whether fields appear in the search criteria or results set for the role. The field definitions determine how the search fields appear on the page, the database records that are searched for each field, and how the user can search for the field.
See Adding and Modifying BO Search and Quick Create Definitions.
Catalog Security
Catalogs are a single group of products or services that are marketed and displayed together because they share common criteria. PeopleSoft enables you to define the layout and content of online catalogs for internal and external use. You define the look and feel of catalogs by creating display templates, and then define the contents that you want to organize and present according to your template definitions. You can designate products for inclusion in a catalog either by direct association (using product IDs) or by creating business rules to dynamically build product content based on the selection criteria that you define. Similarly, you can control user access to catalogs by associating a Security Membership List with specific catalogs.
For Order Capture there is a functional option code called SEARCH_ALL_PRODUCTS. When searching for products in Order Capture, this functional option will give users the ability to search for any products that are defined in the system, instead of limiting the search to the products that are defined in a catalog. You must group this option into a functional option group. You would then associate it to a membership list in the security profile.
Security Memberships allow you to specify which users or groups of users can have access to certain catalogs. For example, a company can have a Membership List called All Persons that includes all of the people that have a person record in the system. This Membership List is then associated with a catalog.
This means that all of the people on this list can view this catalog. If a catalog called the Premier Catalog was for Premier Customers, a company can create a Membership List that contains all of their Premier Customers and the Premier Catalog would provide special pricing and recommendations for this group of users.
Note: PeopleSoft CRM does not support role-based catalogs, nor do we support role-based access to customers. The system can handle this type of functionality but you will need to customize your CRM application. The only area where you can use a role-based membership list, without customizing your application, is to control the Order Capture hold view list. The other area where you can use the role membership list, without customizing your application, is to control display logic in conjunction with a display template.
How Security Information is Processed at Runtime
PeopleSoft CRM application security uses several Application Engines and APIs (application programming interfaces) at runtime to help ensure that the customers to whom you have granted security have access to the correct information and customers.
Here are the elements of runtime security that are activated when a user, or customer attempts to access the PeopleSoft CRM applications that you have secured.
Application Engines
RSEC_DAEMON
Polls for application updates (for example, when a customer is added or updated) and triggers the RSEC_BUILDER
RSEC_BUILDER
Handles the writing of secure objects to list tables.
Runtime API
Determines security memberships and view lists.
Generate SQL filters for calling applications
Determines functional options, and functional option resolution.
Definitional API
Provides application programming interface to add and update security framework metadata.
PeopleCode Application Classes and SQL views provide the API to the security framework. This API is provided for impacted applications to access and update the application security framework. The API is used at runtime to evaluate membership and view privilege result sets, but there are some access methods that are provided to update the framework keys, membership, and view privilege tables directly. The API encapsulates all functionality and structure related to the security framework, so that calling applications do not need to understand the inner workings of the framework.
These access methods are an overview of how each of the impacted applications requirements are satisfied through the API.
API Based Direct Data Access
This access method is provided for instances where the membership tables contain all of the relevant data for the calling application. This method produces a result rowset based on the underlying security object definition. In this usage there are three known values and one unknown value. The three known values consist of a membership security object type, a view list object type, and either a membership object ID, and or a view list membership object ID. Based on the ID that is provided, the API determines the security profiles that are associated to the known entity, and from the profiles determines the data that is to be provided as a result set. The API returns this data in a rowset based on the security object’s list record.
API Based SQL Data Access
This access method is provided for instances when the results in the membership table need to be merged or joined in a larger SQL statement that is being constructed by the calling application. The known values and the method of data retrieval are the same as the direct data access method, the result of this call is a SQL select statement that returns the keys of the rows of the security object’s table. This SQL statement can be used in a SQL IN clause or correlated sub query to limit the results of the calling application’s constructed query.
SQL/Query Based Data Access
There may be instances in which the API cannot be used. An example of this is any time where the logic to determine a result set does not have the ability to run a PeopleCode based API, such as a standard PeopleTools prompt, a view, or a PeopleTools query. For these use cases the design provides example SQL that can be used to join the security data model.
Functional option Conflict Resolution
In instances where a key resolves the same functional option multiple times with different properties, the conflict needs to be resolved. Gathering the functional options and privilege overrides is possible using a SQL UNION, but the resolution of the rules is not possible within a single SQL select statement. This requires impacted applications to be in an environment where it is possible to run PeopleCode to determine the applicable functional options. Because of this functional options are not be determined or executed in a view or query type access method.
Executing Functional Options
An abstract class/interface is provided to model functional option classes. This class is used by the runtime application to run the functional option logic. The runtime class provides access to the logic that is relevant to the application and coded in the attached application class. The class also provides the ability to access the functional option amount value, operator, base currency, and perform currency conversion if required. The runtime API provide a method to pass multiple functional option codes, and execute them. A calling application’s framework could leverage this to provide data driven execution.
Update to Data Cache
Applications that are responsible for the security objects’ secured data require access to update the security cache when a change is made. Since it is possible that a configurable search definition references any data for a given object, all additions and updates to these objects trigger a cache refresh. The known values in this case are the security object type, and security object ID. The API triggers the data caching process providing the known values as parameters. These parameters trigger the caching process to deal only with data that is relevant (for example, the specific object ID).
Update to Security Framework
This access method is provided for instances where it is required to update the security framework data directly in a batch or EIP type mode. The API provides access to create membership, view privilege, functional option, and security key objects. The system provides methods to create the associations between the various security objects, and keys. Security Object types (for example, customers) cannot be created through the API. Since there is not a lot of business logic tied to the security setup components, the API uses SQL objects to update the framework tables directly rather than building component interfaces.
Note: To improve runtime performance, the result sets for static and dynamic membership and view privilege domains are cached into database list tables. Dynamic implicit domains are cached by spawning security keys for each member in the domain. An Application Engine process provides the mechanism for creating the cache tables that store the membership and view privilege lists.