Access and Secure Business Objects
Enable role-based security to control access to your business objects through REST endpoints, both for apps in your visual application and external clients. You can configure each business object's security settings to control the user roles that can access the endpoints and the types of operations they can perform.
Secure Business Objects
User roles can be used to secure the data stored in business objects.
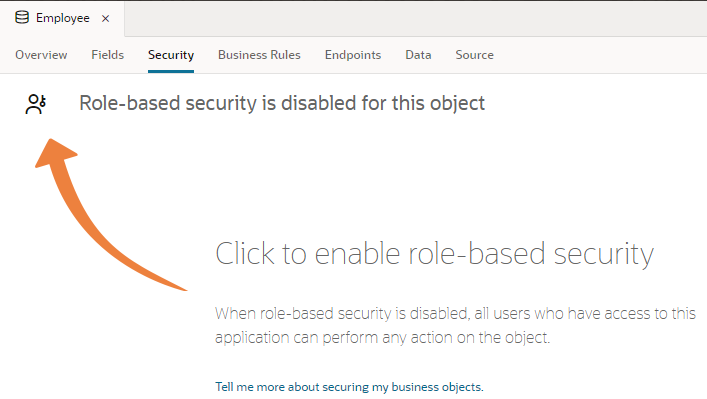
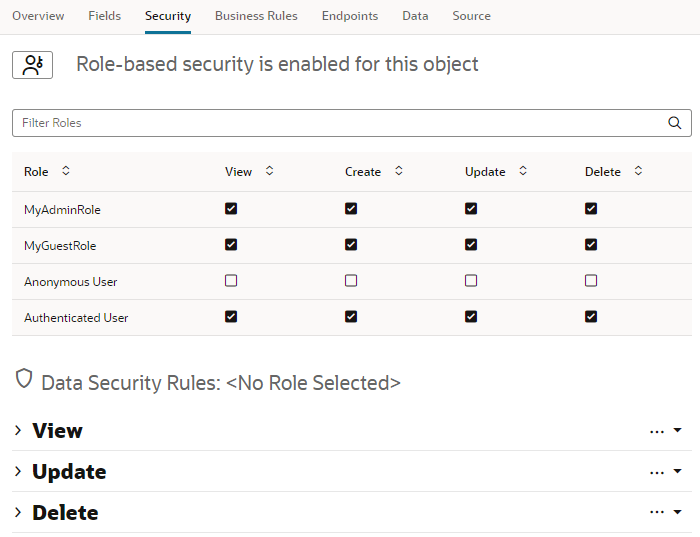
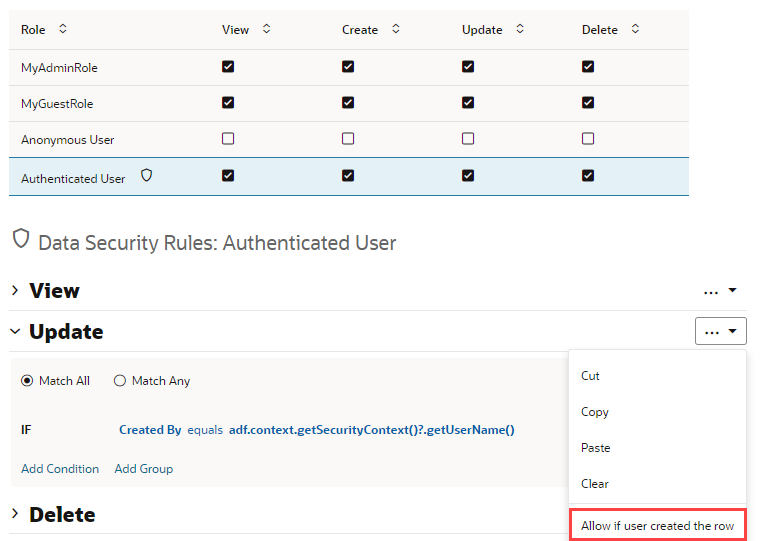
By default, the business objects in your application are accessible to all users that can access the application. To secure the data stored in objects, you can use user roles to restrict a user’s access to view, create, update, and delete operations by configuring role-based access for each operation. Users can only perform the operations and interact with the business objects associated with the role that the user has been assigned.
To allow anonymous access to the data in a business object, for each operation you must explicitly set the permissions granted to the Anonymous User authentication role.
To enable role-based security for a business object:
Allow External Access to Your Business Objects
When configuring security, you can allow external clients to access the business objects in your application through their REST endpoints. For example, you might want an external service like Process Automation to update a business object after a process is complete, say change a status field from "requested" to "approved".
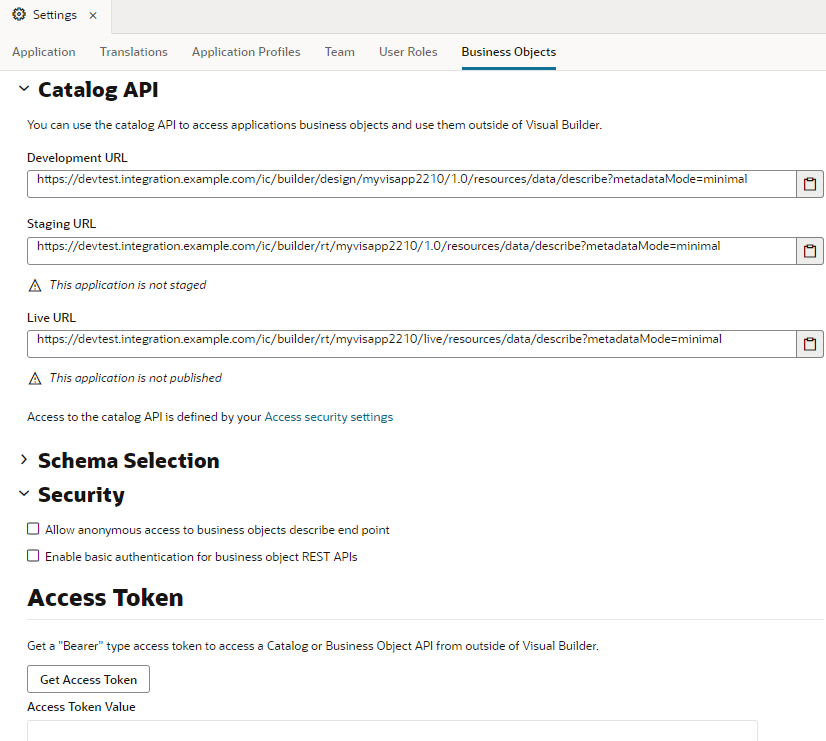
To do this, you need to retrieve the API for the catalog of endpoints exposed by your application's business objects, found in the Catalog API panel in the Business Objects tab of your application's Settings editor:
The Development, Staging, and Live versions of your visual application each have their own catalog APIs. Though the URLs for the Staged and Live applications are provided for development purposes, they will not provide any results until the applications are staged or published.
Tip:
For each URL, click the Clipboard icon to quickly copy the URL to your clipboard.- Open the Business Objects tab in the visual application’s Settings editor.
- Under Security, select an authentication option:
- Allow anonymous access to business objects describe end point
- Enable basic authentication for business object REST APIs
- Include
authin the Describe endpoint URL, for example:https://servicename-cloudaccount.test.oraclecloud.com/ic/builder/rt/myapp/1.0/resources/auth/data/describe?metadataMode=minimal - Add the “Authorization: Public” header to the request, for example, from the cURL command line:
curl -vhttps://servicename-cloudaccount.test.oraclecloud.com/ic/builder/rt/myapp/1.0/resources/data/describe?metadataMode=minimal -H 'Authorization: Public'
Access to the data in business objects is based on authentication and user roles. For each business object you need to explicitly enable role-based security and specify the operations that each defined authentication and user role can perform. You configure the security settings in the business object's Security tab. See Allow Anonymous Access.
Note:
Applications in other domains might need to be added to the CORS allowlist of origins permitted to access applications in your domain. An administrator can add domains in Administrator Settings.Additionally, for requests to access your APIs that are not made through a browser, the request might need to be explicitly modified to include an Origin header that matches the domain in the CORS allowlist. A more advanced alternative would be to add CSRF headers to POST requests that include the current CSRF token value and the session cookie so the server can match the token from the request with the one in the session cache.
Get an Access Token for Authentication
To access the APIs for the catalog or business objects from outside Visual Builder, you can get a bearer token to use with various authentication methods.
In the design-time, you can use the token to access any of your app's endpoints. At runtime, you can use the token to read the data in the app's business object.
- Oracle Cloud Account
- User Assertion OAuth 2.0
- Client Credentials OAuth 2.0
- Resource Owner OAuth 2.0
You cannot use the token with connections to Oracle Cloud Applications.
To generate a bearer token: