Set Up the Service
Like other Oracle Cloud services, you must create an instance of DevCS before you can start using it. You can create only one instance in an identity domain. After creating the instance, set up connections to Compute and Object Storage services on Oracle Cloud Infrastructure (OCI) or Oracle Cloud Infrastructure Classic (OCI Classic).
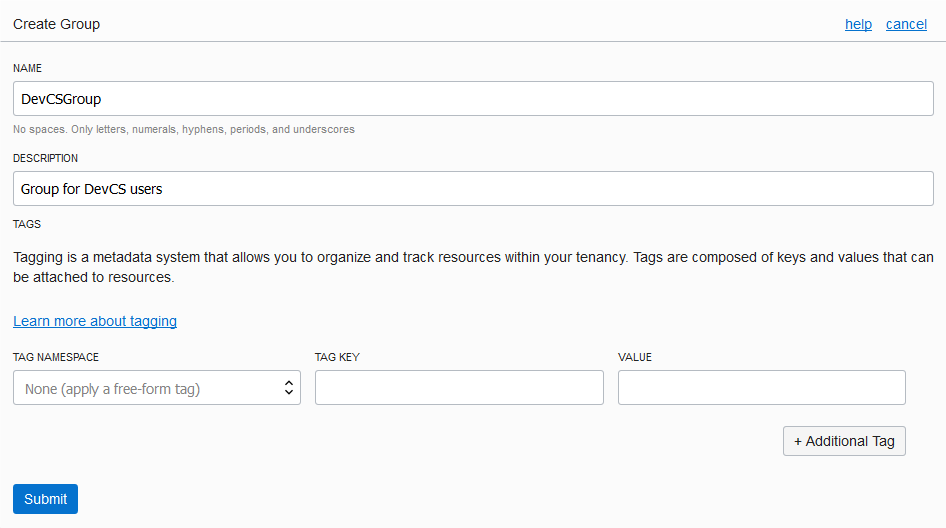
Create the DevCS Instance
You can create only one DevCS instance in an Oracle Cloud account. Before you attempt to create an instance make sure there's no existing DevCS instance in your account.
The DevCS Organization page opens. Click the OCI Credentials link or the OCI Account tab to configure OCI connections before you create a project.
Connect to OCI or OCI Classic
You need to connect to the Oracle Cloud Infrastructure Compute (OCI Compute) or Oracle Cloud Infrastructure Compute Classic (OCI Compute Classic) because they provide the virtual machines (VMs) on which DevCS runs its builds.
You need to connect to Oracle Cloud Infrastructure Object Storage (OCI Object Storage) or Oracle Cloud Infrastructure Object Storage Classic (OCI Object Storage Classic) because they are used to store build and Maven artifacts for DevCS projects. Note that this feature is not available to DevCS users in the Traditional identity domain, who run builds using shared build executors, not virtual machines (VMs).
If you're an OCI user, set up connections to OCI Compute and OCI Object Storage. DevCS runs its builds on OCI Compute VMs, and stores build and Maven artifacts on the OCI Object Storage buckets.
If you're an OCI Classic user, set up connections to OCI Compute Classic and OCI Object Storage Classic. DevCS runs its builds on OCI Compute Classic VMs, and stores build and Maven artifacts on the OCI Object Storage Classic containers.
Set Up the OCI Connection
Before you set up the connections, set up your OCI account to host DevCS resources. They allow DevCS to manage necessary resources, such as VMs for your builds and storage buckets for your project data.
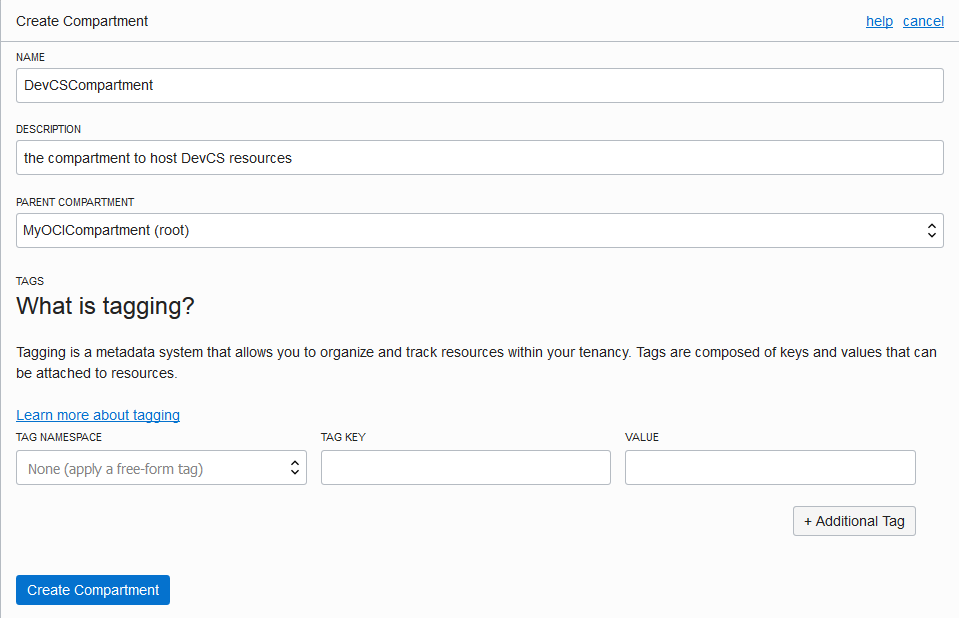
You can use the root compartment and the tenancy user that was created when the OCI account was created, but it's recommended to create a dedicated compartment to host DevCS resources. This allows you to organize DevCS resources better as they aren't mixed with the other resources of your tenancy. You can also restrict users and control read-write access to the compartment without affecting other resources. To learn more about compartments, see Understanding Compartments.
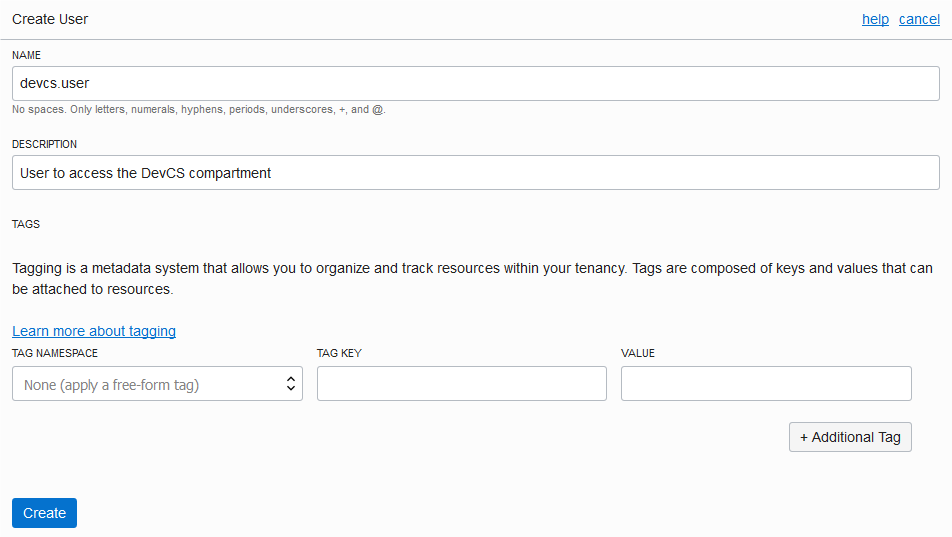
After setting up your OCI account, share the compartment's and the created user's details with the DevCS Organization Administrator to set up the OCI connection in DevCS.
Get the Required OCI Input Values
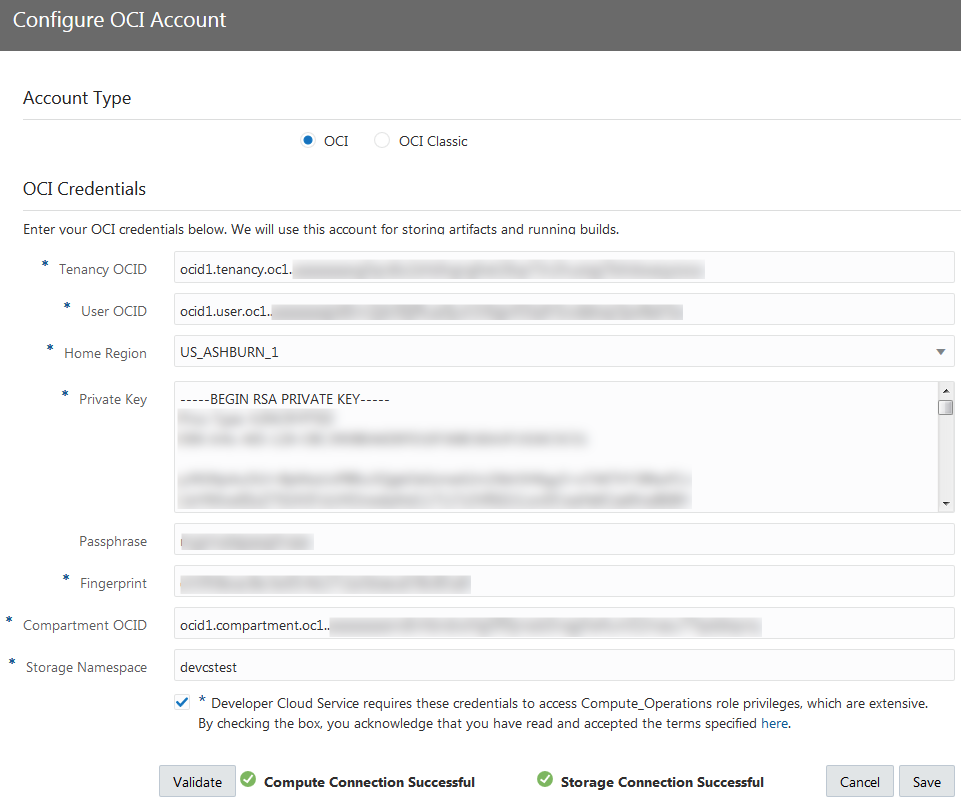
Every Oracle Cloud Infrastructure resource has an Oracle-assigned unique ID called an Oracle Cloud Identifier (OCID). To connect to OCI, you need the account's tenancy OCID, home region, the compartment's OCID that hosts DevCS resources, and the OCID and fingerprint of the user who can access the DevCS compartment. To connect to OCI Object Storage, you need the Storage namespace. You can get these values from the OCI Console pages.
This table describes how to get the OCI input values required for the connection.
| To get these values ... | Do this: |
|---|---|
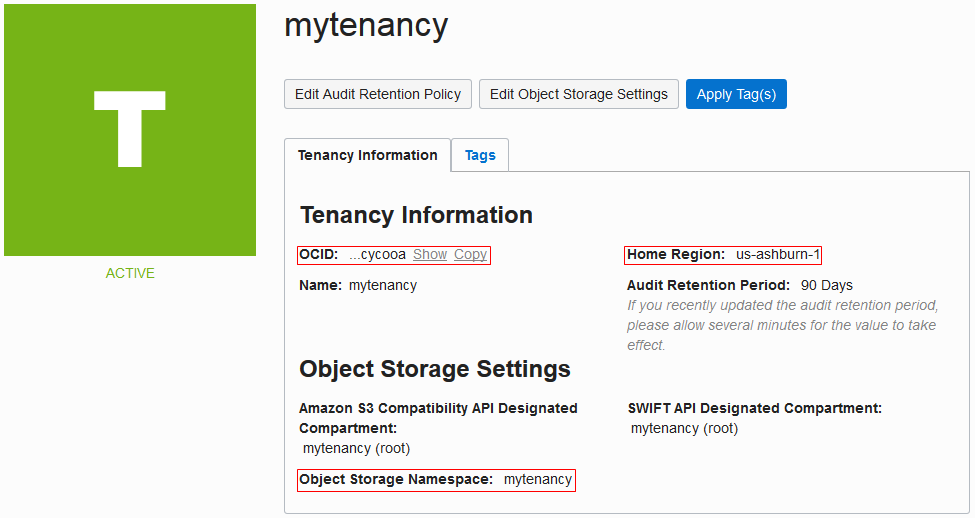
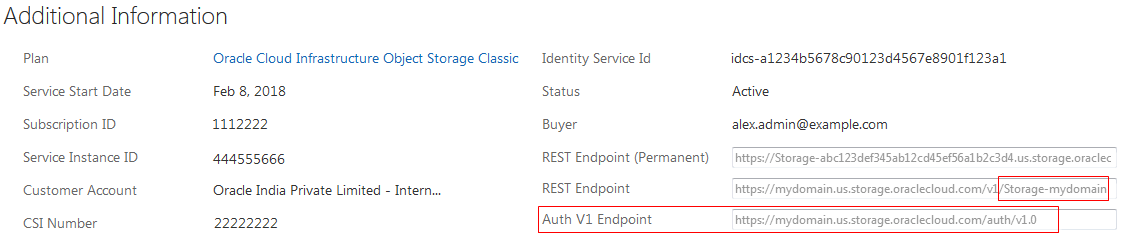
| Tenancy OCID, Home Region, and Storage Namespace | On the OCI console, from the left navigation bar, select Administration > Tenancy Details.
The Tenancy Information tab displays the tenancy OCID in OCID, home region in Home Region, and the storage namespace in Object Storage Namespace. Here's an example: |
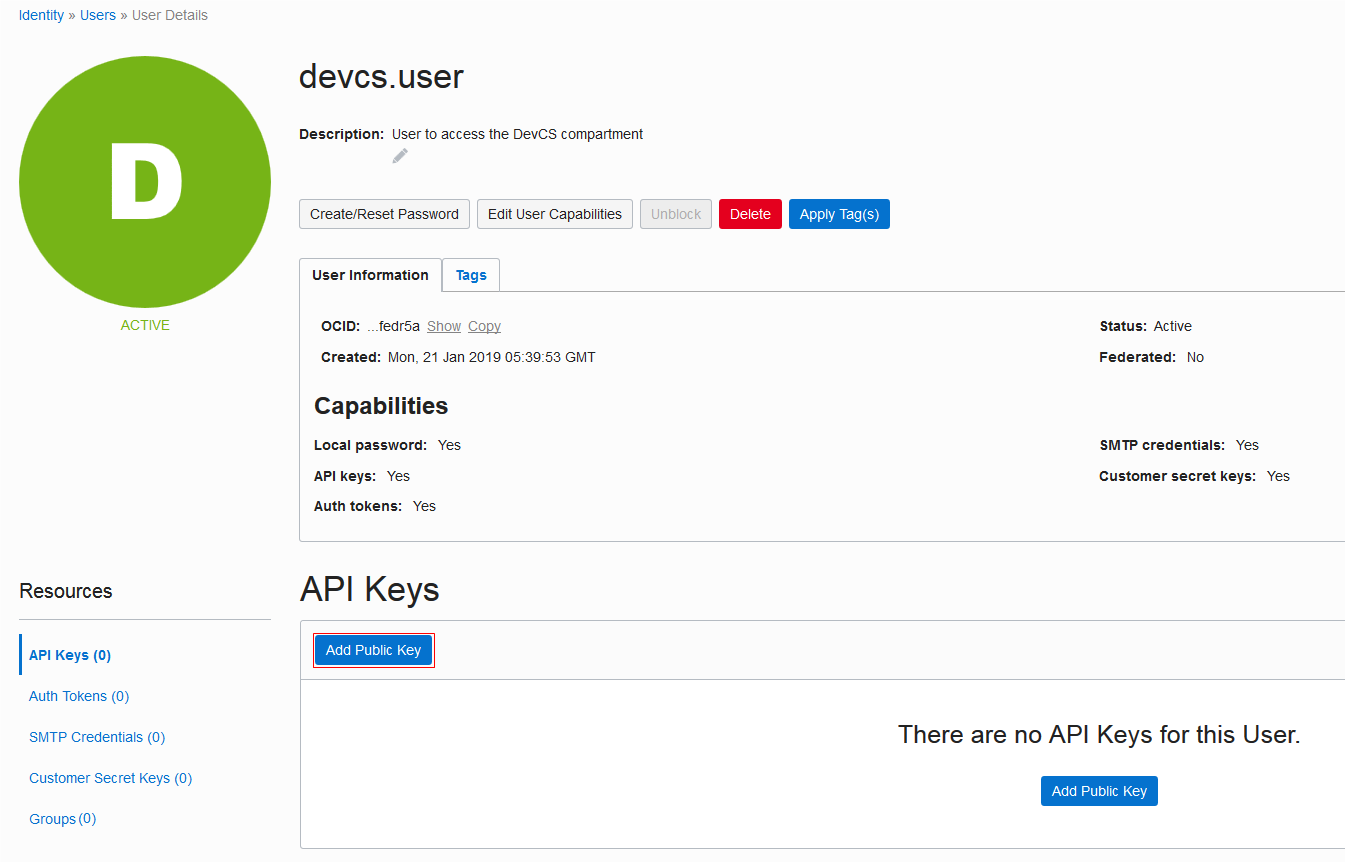
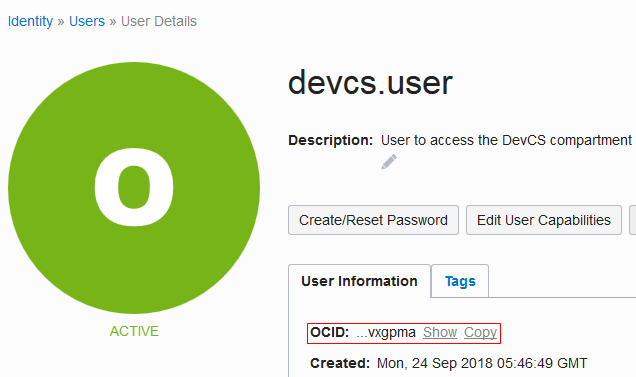
| User OCID and Fingerprint | On the OCI console, from the left navigation bar, under Governance and Administration, select Identity > Users.
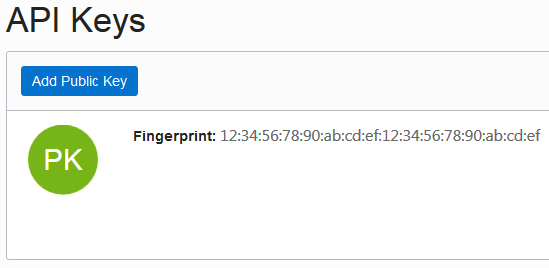
The User Information tab displays the user OCID in OCID. Click the Copy link to copy it to the clipboard. Here's an example of To get the fingerprint of the public key associated with your OCI account, scroll down to the API Keys section and copy the fingerprint value. |
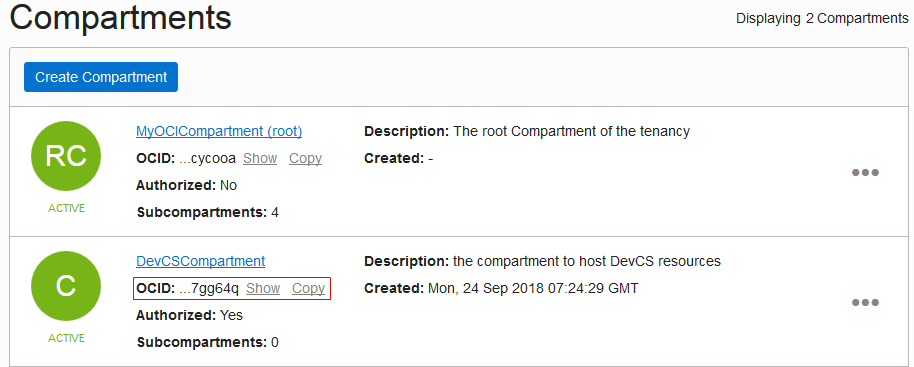
| Compartment OCID | On the OCI console, from the left navigation bar, select Identity > Compartments.
The Compartments list displays the compartments with the compartment OCID in the OCID field. Click the Copy link to copy it to the clipboard. Here's an example: |
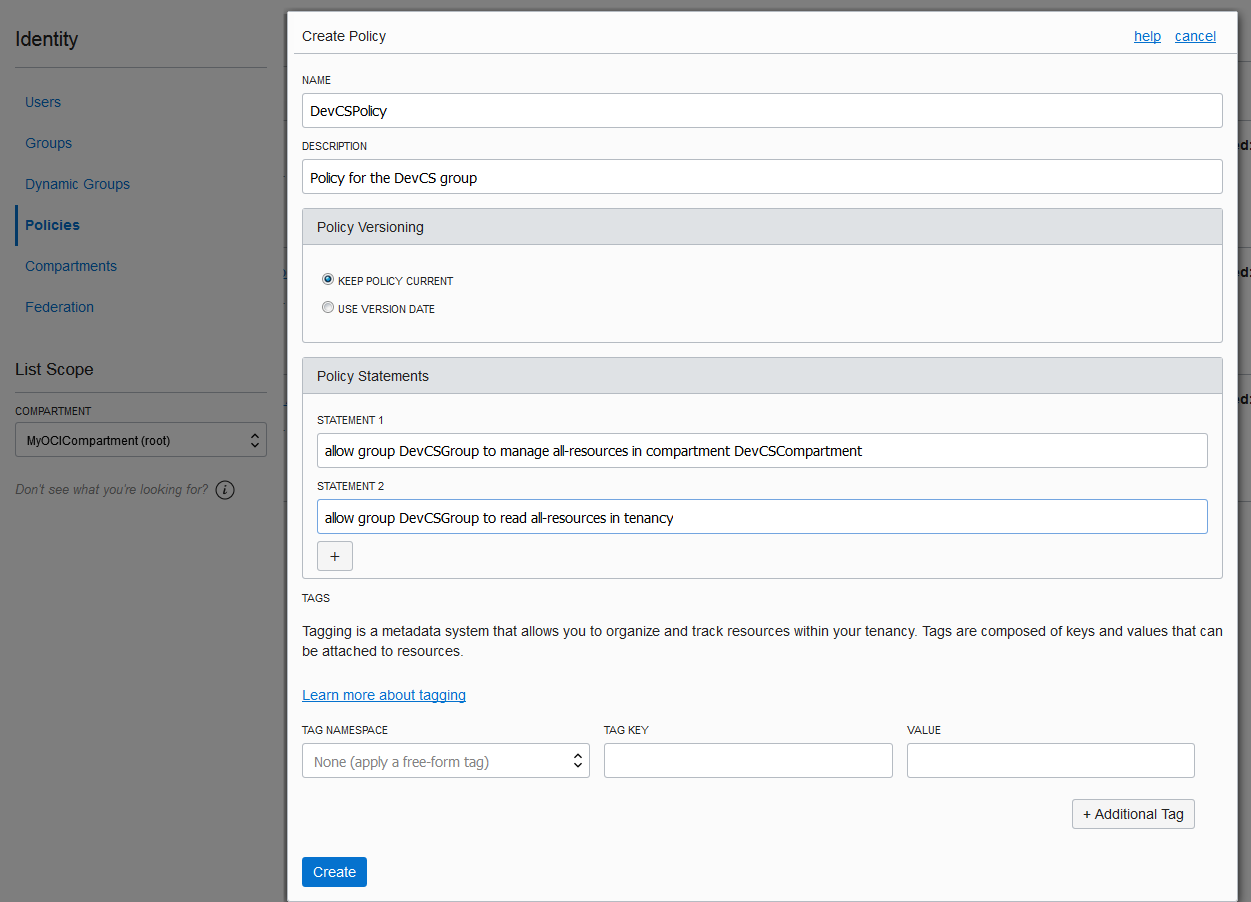
Set Up the OCI Connection in DevCS
To connect to OCI, get the DevCS compartment's details, user details, and the required OCID values. Then, create an OCI connection from DevCS. If you're not the OCI administrator, get the details from the OCI administrator.
Set Up the OCI Classic Connection
To connect to OCI Classic, you need the credentials of a user with the Compute.Compute_Operations and Storage.Storage_Administrator identity domain roles along with the service ID and Authorization URL of OCI Object Storage Classic.
The Compute.Compute_Operations role enables you to create, update, and delete VMs on OCI Compute Classic. The Storage.Storage_Administrator role enables you to store artifacts on OCI Object Storage Classic.
Before you create the OCI Compute Classic connection, you must check the Compute_Operations Role: Terms of Use and get the Service ID and the authorization URL of OCI Object Storage Classic:
Create an OCI Classic Connection from DevCS
After you have the required values, create an OCI Classic connection from DevCS.
![]() You must be the Organization Administrator to create the connection.
You must be the Organization Administrator to create the connection.
- Sign in to DevCS.
- In the navigation bar, click Organization
 .
. - Click the OCI Account tab.
- To create a connection, click Connect. To edit the connection details, click Edit.
- In Account Type, select OCI Classic.
- In the OCI Object Storage Classic section, fill in the required details.
- In the OCI Compute Classic section, fill in the required details.
- In Username and Password, enter the username and password of the user who’s assigned the Compute.Compute_Operations identity domain role.
- To agree to terms and conditions, select the terms and conditions check box.
- Click Validate.
- Click Save.
Compute_Operations Role: Terms of Use
Here are some special legal terms and guidance that apply to the usage of the Compute_Operations role for DevCS.
In addition to these DevCS terms, you should follow security best practices in maintaining the security of the username and password.
-
You must create a dedicated username and password for use by DevCS. When creating a username, avoid including personal names or personal information (like birthdays). Your password should always be complex and impossible to guess.
-
You understand that a user with the
Compute_Operationsrole can view, create, update and delete OCI Compute Classic resources such as VM instances, storage volumes, security rules, and security IP lists. Your failure to maintain security best practices to secure the username and password of the user with theCompute_Operationsrole may create a high risk for you and your organization. -
You should assign the
Compute_Operationsrole privileges only to the username created for DevCS. -
Notwithstanding DevCS terms, you acknowledge that Oracle isn’t responsible or liable for any action you take in accessing or creating access to the DevCS or OCI Compute Classic.
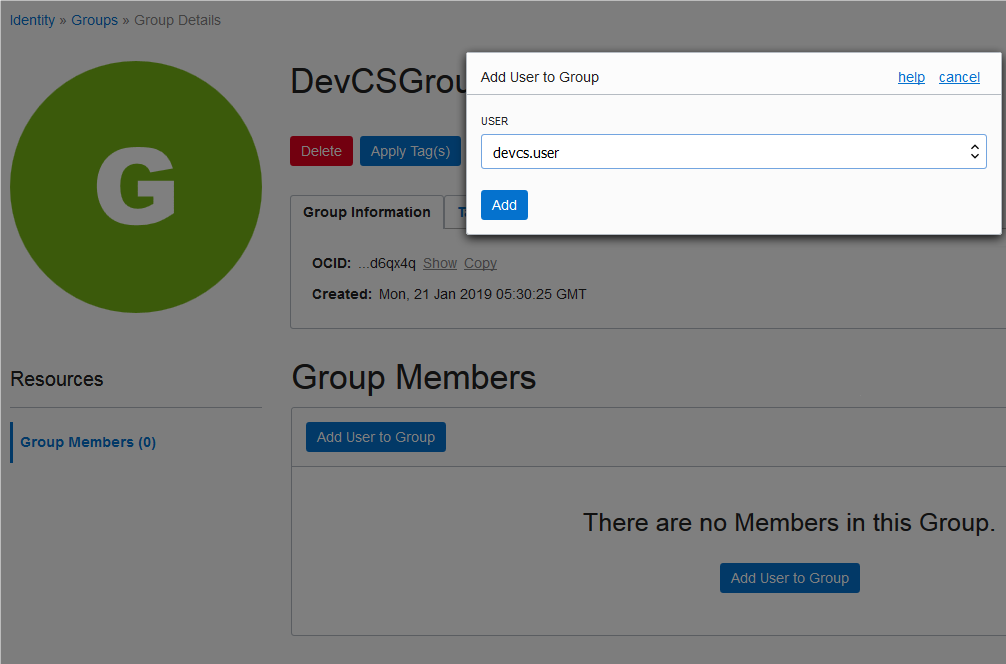
Add Users to the Identity Domain
To add users to your organization and projects, make sure they are added to your identity domain and assigned appropriate identity domain roles. An organization is the top-most entity in the project structure of DevCS. All users of the identity domain are available in your organization and then can be added to projects.
To add a user to the identity domain, invite the user to join Oracle Cloud. See Add Users and Assign Roles in Getting Started with Oracle Cloud. You must be assigned the Identity Domain Administrator (TenantAdminGroup) role to send an invite and assign the identity domain roles.