1 Getting Started with Oracle Security Monitoring and Analytics
About Oracle Security Monitoring and Analytics
Note:
As of September 2019, no enhancements have been made to this service and this functionality is no longer available to new customers.What is Oracle Security Monitoring and Analytics?
Oracle Security Monitoring and Analytics is a security solution provided as part of Oracle Management Cloud’s unified platform. Its core functionality is around cyber security, providing you with IT solutions in the form of anomaly detection and investigations, and remediation of the broadest range of security threats across on-premises and cloud IT assets. Oracle Security Monitoring and Analytics provides integrated security information and event management (SIEM) and user, and entity behavior analytics (UEBA) capabilities built on machine learning, user session awareness, and up-to-date threat intelligence context.
The following diagram shows the integration of Oracle Security Monitoring and Analytics with other cloud solutions also designed as platform components for Oracle Management Cloud.
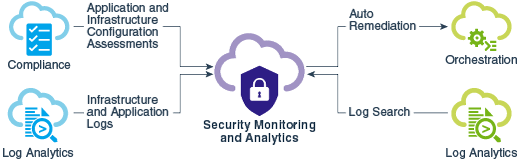
Product Key Features
Real-time threat detection based on rules and patterns:
Universal threat visibility— Collect and analyze any security relevant data.
SOC-ready content— Ready to use, vendor neutral SOC content library.
Threat intelligence leverage— Connect to any threat feed, leverage embedded reputation data.
Advanced threat analytics and visualization:
Data access anomaly detection— Detect SQL query anomalies for any user, database or application.
Identify anomalous activity of an entity based on instance-based and peer-based behavior baselines.
Multi-dimensional anomaly detection— Detect anomalies across multiple behavioral attributes.
Session awareness and attack chain visualization— Faster detection with user awareness kill chain visualization.
Enhanced Security Monitoring with Oracle Management Cloud Platform:
Topology awareness— Detect multi-tier application attacks and lateral movement indicators.
- Correlation Rule-tunning
- Customizable Watchlists
- Storage management
- Integration with IDCS and CASB services
Collecting Operating System Logs from Your Host Platforms
You can collect log data from your hosts and get immediate insight into potential security threats across your environments.
Collect Linux Default Logs
Enable default OS event logs in Linux.
Prerequisite Checklist
| 1. Host machine met OS requirements for local agent installations |
Requirement for Logs Collection on Unix in Installing and Managing Oracle Management Cloud Agents |
| 2. Oracle Management Cloud environment met the minimum standard setup requirements | To analyze security log data you must first enable Security Monitoring and Analytics (SMA) licensing. SMA licensing assumes that Log Analytics licensing is enabled as well. To enable these components and ensure you meet other prerequisites see Prerequisites and Requirements for Security Sources. |
Configuration Steps
| Linux Log Configuration | Task Requirements | For additional details, see... |
|---|---|---|
| STEP 1. - Enable host monitoring in OMC. | Enable the Linux host where you installed the agent. By default your host is already added as an entity, however, monitoring is disabled. | Enable Host Monitoring in Using Oracle Infrastructure Monitoring |
| STEP 2. - Associate your (Linux host) entity for log collection. | From Log Analytics > Log Admin > Entities, click New Association and select the new Linux host. | Configure New Entity Associations in Using Log Analytics |
| STEP 3. - Select log sources for your new (Linux host) entity. | Select the Linux logs that apply for your environment. | Host Sources Associating Entities to Existing Log Sources in Using Oracle Log Analytics |
| STEP 4. - Validate your log collection. | Ensure your setup is successfully completed: validate your collection. Navigate to Security Analytics > Security Data Explorer. | Validate Log Collections |
Collect Windows Default Logs
Enable default logs for Windows platforms.
Prerequisites
| Ensure that your OMC environment meets the typical requirements to enable platform logs. | To analyze security log data you must first enable Security Monitoring and
Analytics (SMA) licensing. SMA licensing assumes
that Log Analytics licensing is enabled as well. To
enable these components and ensure you meet other
prerequisites see Prerequisites and Requirements for Security Sources.
Environment Requirements in Installing and Managing Oracle Management Cloud Agents |
Table 1-1 Log Configuration Steps
| Windows Log Configuration | Task Requirements | For additional details, see... |
|---|---|---|
| STEP 1. - Enable host monitoring in OMC. | Enable the Windows host where you installed the agent. By default your host is already added as an entity, however, monitoring is disabled. | Enable Host Monitoring in Using Oracle Infrastructure Monitoring |
| STEP 2. - Associate your (Windows host) entity for log collection. | From Log Analytics > Log Admin > Entities, click New Association and select the new Windows host. | Configure New Entity Associations in Using Log Analytics |
| STEP 3. - Select log sources for your new (Windows host) entity. | Select the Windows Security Events log source to associate with your Windows host. | Host Sources Associating Entities to Existing Log Sources in Using Oracle Log Analytics |
| STEP 4. - Validate your log collection. | Ensure your setup is successfully completed: validate your collection. Navigate to Security Analytics > Security Data Explorer. | Validate Log Collections |