6 Registering Hosts and Deploying the Agent
If you're deploying the Audit Vault Agent, you register the host computers for the targets for which you want to collect audit data and deploy the Audit Vault Agent on each of them.
Note:
Starting in Oracle AVDF 20.9, you can use agentless collection instead of the Audit Vault Agent for up to 20 Oracle Database table audit trails. Starting in Oracle AVDF 20.10, you can also use agentless collection for Microsoft SQL Server directory audit trails for.sqlaudit and .xel (extended events). The
total number of audit trails for agentless collection should not exceed 20. See Adding Audit Trails with Agentless
Collection.
6.1 About Registering Hosts and Deploying the Agent
Learn how to register hosts and deploying the Audit Vault Agent.
Register a host computer from where audit data is collected. After registering the host, you can deploy the Audit Vault Agent on that host. The Audit Vault Agent is a component of Oracle Audit Vault and Database Firewall (Oracle AVDF) that you can download from the Audit Vault Server console. After being deployed, Audit Vault Agents are ready to collect data from targets. A target is a system that you want to monitor and protect.
| Step | Task | Reference Topic |
|---|---|---|
| 1 | Check the requirements. | Audit Vault Agent Requirements |
| 2 | Check the documentation about deploying the Audit Vault Agent. | Deploying the Audit Vault Agent on Host Computers |
| 3 | Register the host machine (agent machine). | Registering Hosts on the Audit Vault Server |
| 4 |
Download the Audit Vault Agent software from the Audit Vault Server console and deploy the agent. |
Deploying the Audit Vault Agent |
| 5 | Activate and start the Audit Vault Agent. | Activating and Starting the Audit Vault Agent |
| 6 | In case of any error or issue, refer to the troubleshooting documentation and known issues. |
After registering the hosts on the Audit Vault Server, perform the following steps to be able to collect audit records:
- Download the Audit Vault Agent software from the Audit Vault Server console.
- Deploy the Audit Vault Agent.
- Activate the Audit Vault Agent.
- Register one or more targets from which you want to collect audit data.
- Start collecting data from the targets' audit trails by using the Audit Vault Server console.
See Also:
- Registering Targets
- Configuring and Managing Audit Trail Collection
- Summary of Configuration Steps to understand the high-level workflow for configuring the Oracle Audit Vault and Database Firewall system
- Using the Audit Vault Command Line Interface
- Deploying the Audit Vault Agent on Host Computers
6.2 Registering Hosts on the Audit Vault Server
Learn about registering hosts on the Audit Vault Server.
Prerequisite: Check Product Compatibility Matrix for supported cluster/platforms for Agent deployment and before proceeding with the host registration.
To register a host computer in the Audit Vault Server:
Agent Deployment in a High Availability System
Audit Vault Agent may be associated with multiple IP addresses in the following cases:
-
Agent installed on a host with multiple network interface cards
-
Agent installed on a node of high availability cluster
-
Only one Audit Vault Agent installation is necessary for high availability cluster deployment. The Agent installation is needed only on active node of the cluster. Ensure the Audit Vault Agent installation directory is accessible from all nodes of the cluster.
-
Cluster management software must be configured to start, stop, and monitor the Agent by providing the necessary input. The Agent must be started automatically by the cluster management software on the active node and stopped automatically on passive nodes.
-
Use the following commands in the cluster manager software:
| Action | Command |
|
To stop the Agent |
|
|
To start the Agent |
|
|
To monitor the Agent |
|
See Also:
-
REGISTER HOST for the command line syntax to register a host.
-
Configuring or Changing the Audit Vault Server Services to configure DNS server.
6.3 Deploying the Audit Vault Agent on Host Computers
Learn about how to deploy the Audit Vault Agent on host computers.
Note:
When you register a host on the Audit Vault Server, an activation key is generated. When you deploy the Audit Vault Agent on the host computer, you need to provide the corresponding activation key, as discussed in the following procedures.
6.3.1 Audit Vault Agent Requirements
Learn about the Audit Vault Agent requirements.
Note:
Starting in Oracle AVDF 20.9, you can use agentless collection instead of the Audit Vault Agent for up to 20 Oracle Database table audit trails. Starting in Oracle AVDF 20.10, you can also use agentless collection for Microsoft SQL Server directory audit trails for.sqlaudit and .xel (extended events). The
total number of audit trails for agentless collection should not exceed 20. See Adding Audit Trails with Agentless
Collection.
Recommended Prerequisites for Installing Audit Vault Agent
- Ensure that you meet the system requirements. See Product Compatibility Matrix.
-
Ensure that you meet the following Java requirements:
- Install the supported Java version on the Audit Vault Agent. See Audit Vault Agent: Supported and Tested Java Runtime Environment.
- Apply the latest Java patches.
- Point the
JAVA_HOMEto the JRE/JDK directory and set the path before installing the Audit Vault Agent.
- Ensure that the host machine on which the Audit Vault Agent is deployed has at least 512 MB RAM.
- Apply the latest security patches for the OpenSSL libraries that are available from the OS vendor for the specific OS version on the host machine.
-
Ensure that the host machine on which the Audit Vault Agent is deployed has connectivity to the Audit Vault Server.
In a high availability environment, it must have connectivity to both primary and standby Audit Vault Servers.
- Ensure that two Audit Vault Server ports (1521 and 1522 by default) are configured for communication with the Audit Vault Agent.
- If you use Network Address Translation (NAT) in the network between the Audit Vault Server and the host machine where the agent is deployed, then ensure that the IP address of the host machine is resolvable from the Audit Vault Server.
-
Ensure that the user has the required OS permissions to install the agent.
For directory audit trails, the user must be able to access the audit trail location. See About Deploying the Audit Vault Agent for the OS permissions that are required for installing the agent.
-
Ensure that the Audit Vault Agent home directory is access protected.
Only the Agent user should have write or execute permissions on the agent home directory.
- Ensure that the Audit Vault Agent host machine system settings are access protected to prevent malicious users from making modification.
-
Ensure that the system time of the Audit Vault Agent and the target are synchronized.
They can be in different time zones. The time difference between these two systems (considering time zone conversion) should not exceed two seconds.
Additional Requirements for Starting the Audit Vault Agent as a Service on Windows
For Oracle AVDF 20.4 and earlier releases, comply with one of the following prerequisites:
-
Install the Visual C++ Redistributable for Visual Studio 2012 Update 4 package from Microsoft on the Windows host machine.
Ensure that the
msvcr110.dllfile is available in theC:\Windows\System32directory. - If the
msvcr110.dllfile is not present, then add it to the<Agent Home>/binand<Agent Home>/bin/mswin-x86-64directories.
For Oracle AVDF 20.6 and later releases, comply with one of the following prerequisites:
-
Install the Visual C++ Redistributable for Visual Studio 2017 package from Microsoft on the Windows host machine.
Ensure that the
vcruntime140.dllfile is available in theC:\Windows\System32directory. - If the
vcruntime140.dllfile is not present, then add it to the<Agent Home>/binand<Agent Home>/bin/mswin-x86-64directories.
Note:
There is a known issue in Oracle AVDF 20.5 for starting Audit Vault Agent as a service on Windows. See Error When Starting Audit Vault Agent as a Service on Windows in Oracle AVDF 20.5 for complete information. This issue is resolved in Oracle AVDF 20.6 and later.6.3.2 Audit Vault Agent Machine Java Best Practices
Learn some best practices regarding Java on the Audit Vault Agent machine.
- Ensure installation of Java and the Java home directory is managed by a trusted user.
- If Java is upgraded to a major version or if it is patched with security updates, then restart the Audit Vault Agent. This ensures the Audit Vault Agent runs with the updated Java.
6.3.3 Validation During Audit Vault Agent Deployment
Learn about validations performed by Oracle AVDF when deploying the Audit Vault Agent.
Starting Oracle AVDF release 20.6, some validations are performed when deploying Audit Vault Agent.
The following validations are performed when running the agentctl start
command. These requirements are mandatory and have to be complied, without which the
Audit Vault Agent installation cannot be completed.
- Minimum java version is installed on the host machine as per Audit Vault Agent: Supported and Tested Java Runtime Environment.
- Audit Vault Agent is being installed on the supported operating system version as per Product Compatibility Matrix.
- The Agent machine on which the Audit Vault Agent is being deployed can connect to the Audit Vault Server.
Ensure to comply with the requirements on the Agent machine:
- The Agent machine has a minimum of 512MB available space.
- The Agent machine must be able to connect to the Audit Vault Server.
- Sufficient permissions required to install the Audit Vault Agent are available.
6.3.4 About Deploying the Audit Vault Agent
Audit Vault Agent collects audit trail data from targets. The host computer where you deploy the Audit Vault Agent depends on the type of audit trail that you want to collect. The Audit Vault Agent includes plug-ins for each target type.
Use the following guidelines to choose the host computer where you need to deploy the Audit Vault Agent:
| Trail Type | Guideline for Host Computer |
|---|---|
TABLE |
Deploy the Audit Vault Agent on a remote host or on the host machine where the database is running. |
DIRECTORY |
Deploy the Audit Vault Agent on the host machine where
the DIRECTORY path exists or on a machine from which
the DIRECTORY path can be accessed.
|
TRANSACTION LOG |
Deploy the Audit Vault Agent on the host machine where the GoldenGate Integrated Extract path exists or on a machine from which it can be accessed. |
NETWORK |
Deploy the Audit Vault Agent on the host machine where the database is running. |
OS Permissions for Installing the Agent
| Operating System | User |
|---|---|
| Linux/Unix | Any user |
| Windows |
Any user for running the Audit Vault Agent from the command prompt The admin user for registering as a service |
Note:
- Host Monitor Agent on Linux/Unix/AIX/Solaris platforms must be installed as root user.
- If directory trails are used then Agent installation user should have read permission on the audit files.
- Host Monitor Agent on Windows platform, must be installed as admin user.
- Ensure that the host machine has OpenSSL
1.0.1 (or later) installed for Audit Vault Agent.
OpenSSL 1.1.1 and earlier on Windows platforms was deprecated in Oracle AVDF 20.11, and it will be desupported in one of the future releases. To prevent issues, you should move to OpenSSL 3.0.13 or later.
OpenSSL 1.0.2 on AIX platforms was deprecated in Oracle AVDF 20.15, and it will be desupported in one of the future releases. To prevent issues, you should move to OpenSSL 3.0.16 or later.
Deploying Audit Vault Agent Remotely or Locally
Table 6-1 Remote Agent or Local Agent
| Trail Type | Audit Vault Server Location | Agent Type | Detailed Information |
|---|---|---|---|
|
Directory |
On-premises |
Remote Agent Not installed on the target machine |
|
|
Directory |
On-premises |
Local Agent Installed on the target machine |
|
|
Directory |
OCI (Oracle Cloud Infrastructure) |
Remote Agent Not installed on the target machine |
|
|
Directory |
OCI (Oracle Cloud Infrastructure) |
Local Agent Installed on the target machine |
|
|
Table |
On-premises |
Remote Agent Not installed on the target machine |
|
|
Table |
On-premises |
Local Agent Installed on the target machine |
|
|
Table |
OCI (Oracle Cloud Infrastructure) |
Remote Agent Not installed on the target machine |
|
|
Table |
OCI (Oracle Cloud Infrastructure) |
Local Agent Installed on the target machine |
|
6.3.5 Steps Required to Deploy and Activate the Audit Vault Agent
Learn about the procedures to deploy and activate Oracle Audit Vault Agent.
Deploying and activating the Audit Vault Agent on a host machine consists of these steps:
6.3.6 Registering the Host
Learn about the procedure for registering the host.
To register the host on which you deployed the Audit Vault Agent, follow the procedure in Registering Hosts on the Audit Vault Server.
6.3.7 Deploying the Audit Vault Agent
Learn about deploying the Audit Vault Agent.
You must use an OS user account to deploy the Audit Vault Agent. In this step, you copy the agent.jar file from the Audit Vault Server and deploy this file on the host machine.
Note:
Ensure that all security patches from the OS vendor is applied on the host machine.
See Also:
The Audit Vault Agent is supported on Unix and Microsoft Windows platforms. It requires Java version 1.8 to be installed on the host machine. See Product Compatibility Matrix for Agent platform support details for the current release and for the supported Java versions.
To copy and deploy the Audit Vault Agent to the host computer:
Caution:
After deploying the Audit Vault Agent, do not delete theAgent_Home directory unless directed
to do so by Oracle Support. If you are updating an existing Audit Vault Agent, then
do not delete the existing Agent_Home directory.
Note:
If you run into any issues, see the following topics for more information:
6.3.8 Activating and Starting the Audit Vault Agent
Learn how to activate and start Audit Vault Agent.
In this step, you activate the Audit Vault Agent with the Agent activation key and start the Agent.
Prerequisites
-
Follow and complete the procedure in Registering Hosts on the Audit Vault Server.
-
Log in to the Audit Vault Server console as an administrator. See Using Audit Vault Server Console for more information.
To activate and start the agent:
See Also:
-
Registering and Unregistering the Audit Vault Agent as a Windows Service to start or stop the agent Windows service through the Windows Services applet in the Windows Control Panel, in case the Agent is deployed on a Microsoft Windows host computer.
-
ACTIVATE HOST for the command line syntax to activate the Agent.
6.3.10 Configuring Agent Auto Restart Functionality
Learn how to configure the Audit Vault Agent auto restart functionality.
Audit Vault Agent collects audit data from the target and sends it to the Audit Vault Server. The Agent must continuously run to carry out this task seamlessly. In some cases where the host machine (Agent machine) is restarted or the Agent goes down, then the Agent may stop running. It needs to be manually restarted so that it can continue to collect audit data.
Starting with Oracle AVDF release 20.7, the Audit Vault Agent can be configured to restart automatically. This functionality can be configured by the agent user. It periodically monitors the status of the Agent and restarts whenever required.
Note:
In Oracle AVDF releases 20.3 to 20.6, there is an existing functionality which involves configuring a service to restart the Agent. In case you have configured this functionality as mentioned in Audit Vault Agent Auto Start Configuration, then disable this previously configured functionality before proceeding with the below commands.
Run the following commands in the Agent_Home/bin directory to enable
or disable the Agent auto restart functionality:
| Task | Command |
|---|---|
|
To enable Agent auto restart functionality and to start the Agent |
|
|
To enable Agent auto restart functionality, if the Agent is not activated |
|
|
To disable Agent auto restart functionality and to stop the Agent |
|
|
To enable Agent auto restart functionality when the Agent is already
in |
|
|
To disable Agent auto restart functionality without stopping the Agent |
|
Note:
- Use the commands wisely as it involves two tasks (enabling or disabling the Agent auto restart functionality and starting or stopping the Agent). In case the Agent is manually stopped and the auto start service is still in effect, then the Agent is automatically started again. If the Audit Vault Agent service is started, do not stop the Agent alone without stopping the service.
- The Agent auto restart functionality must be enabled again, after updating the Java version on the Audit Vault Agent.
- The Agent auto restart functionality may not work, if the Audit Vault Agent is not properly installed or if it is not registered in the Audit Vault Server console.
- In case the Audit Vault Agent is being managed by another application such as cluster manager, then do not use the Agent auto restart functionality.
6.3.11 Configuring Agent Auto Restart Functionality Remotely
Learn how to configure Agent auto restart functionality remotely.
Agent auto restart functionality can be configured remotely starting with Oracle AVDF release 20.8. The administrator can enable this functionality through Audit Vault Server for multiple Audit Vault Agents at a time.
Note:
This functionality is applicable for Audit Vault Agents deployed on Linux/Unix/AIX/Solaris platforms only. It is not applicable for Audit Vault Agents deployed on Windows platform.Prerequisite
The Audit Vault Agent must be in RUNNING state.
Follow these steps to enable or disable this functionality:
6.3.12 Check if Audit Vault Agent Has Auto Restart Functionality Enabled
Learn how to check if the Audit Vault Agent is configured for auto restart functionality.
Follow these steps:
6.3.13 Registering and Unregistering the Audit Vault Agent as a Windows Service
Learn about registering and unregistering Oracle Audit Vault Agent as a Windows service.
Note:
The Audit Vault Agent as a Windows Service is not supported in Oracle Audit Vault and Database Firewall release 12.2.0.7.0. Use the console mode to stop or start the Agent.
6.3.13.1 About the Audit Vault Agent Windows Service
Learn about the Audit Vault Agent Windows service.
When you deploy the Audit Vault Agent on a Microsoft Windows host computer, during agent deployment, a Microsoft Windows service named OracleAVAgent is automatically registered. Additionally, you can register and unregister the agent service using the agentctl command.
When the Audit Vault Agent is registered as a Windows service, you can start or stop the service through the Windows Services applet in the Windows Control Panel.
See Also:
6.3.13.2 Registering the Audit Vault Agent as a Windows Service
You can register Audit Vault Agent as a Windows service.
Deploying the Audit Vault Agent on a Windows host automatically registers
a Windows service named agentctl. Use this procedure to register
the Windows service again.
Prerequisite
Ensure to comply with one of the following prerequisites for Oracle AVDF 20.4 and earlier releases:
- Install Visual C++ Redistributable for Visual Studio 2012 Update 4
package from Microsoft on the Windows target machine. Ensure
msvcr110.dllfile is available inC:\Windows\System32directory. - If the
msvcr110.dllfile is not present, then add it to the<Agent Home>/binand<Agent Home>/bin/mswin-x86-64directories.
Ensure to comply with one of the following prerequisites for Oracle AVDF 20.6 and later releases:
- Install Visual C++ Redistributable for Visual Studio 2017 package from
Microsoft on the Windows target machine. Ensure
vcruntime140.dllfile is available inC:\Windows\System32directory. - If the
vcruntime140.dllfile is not present, then add it to the<Agent Home>/binand<Agent Home>/bin/mswin-x86-64directories.
Note:
There is a known issue in Oracle AVDF 20.5 for starting Audit Vault Agent as a service on Windows. See Error When Starting Audit Vault Agent as a Service on Windows in Oracle AVDF 20.5 for complete information. This issue is resolved in release Oracle AVDF 20.6 and later.Registering Audit Vault Agent as a Windows Service
Run the following command on the host machine from the Agent_Home\bin directory:
agentctl registersvc
This adds the Audit Vault Agent service in the Windows services registry.
Note:
- Be sure to set the Audit Vault Agent service to use the
credentials of the Windows OS user account that was used to deploy the Agent
using the
java -jarcommand. Do this in the Service Properties dialog box. - In the Service Properties dialogue, local user name entries in
the This account field should be formatted as in the
following example: user name
jdoeshould be entered as.\jdoe. Refer to Microsoft Windows documentation for procedures to do so.
6.3.13.3 Unregistering the Audit Vault Agent as a Windows Service
You can use two methods to unregister the Oracle Audit Vault Agent as a Windows service.
To unregister the Oracle Audit Vault Agent as a Windows Service, use one of the following methods:
-
Method 1 (Recommended)
On the host machine, run the following command from the
Agent_Home\bindirectory:agentctl unregistersvcThis removes the Oracle Audit Vault Agent service from the Windows services registry.
-
Method 2
If Method 1 fails, then execute the following from the Windows command prompt (Run as Administrator):
cmd>sc delete OracleAVAgentYou can verify that the Audit Vault Agent has been deleted by executing the following query from the Windows command prompt (Run as Administrator):
cmd>sc queryex OracleAVAgent
6.4 Stopping, Starting, and Other Agent Operations
Learn about starting and stopping the agent and other operations.
6.4.1 Stopping and Starting Audit Vault Agent
Learn about stopping and starting Audit Vault Agent.
Topics
Important:
Stop and start the Audit Vault Agent as the same OS user account that you used during installation.
6.4.1.1 Stopping and Starting the Agent on Unix Hosts
Learn about stopping and starting the Agent on Unix hosts.
To start the Audit Vault Agent after initial activation, run the following command
from the Agent_Home/bin
directory on the host machine:
agentctl startTo stop the Audit Vault Agent run the following command from the
Agent_Home/bin directory on
the host machine:
agentctl stopNote:
- After the
agentctl stopcommand, executeagentctl statuscommand to ensure the Agent is inSTOPPEDstate before executing theagentctl startcommand again. - In case the Agent auto start service (Oracle AVDF release 20.7 and onwards) is configured and if the Agent alone is manually stopped, then the Agent is automatically started again. See Configuring Agent Auto Restart Functionality for complete information and run the right commands.
6.4.1.2 Stopping and Starting the Agent on Windows Hosts
Learn about stopping and starting the Agent on Microsoft Windows hosts.
The Audit Vault Agent is automatically registered as a Windows service when you deploy the agent on a Windows host. We recommend that you run the agent as a Windows service so that it can keep running after the user logs out.
See Also: Registering and Unregistering the Audit Vault Agent as a Windows Service
To stop or start the Agent Windows service
Use one of the methods below:
-
In the Windows GUI (Control Panel > Administrative Tools > Services), find the Audit Vault Agent service, and then right-click it to select Start or Stop.
-
Run one of these commands from the
Agent_Home\bindirectory on the host machine:agentctl stopsvcagentctl startsvc
To check that the Windows service is stopped
Run this command:
cmd> sc queryex OracleAVAgentYou should see the Agent Windows service in a STOPPED state.
To stop or start the Agent in console mode
start /b agentctl stop
start /b agentctl start
To forcibly stop the Agent in console mode
agentctl stop -force
Note:
This is not a recommended option to stop the Agent. Use it only in case the Agent goes into an unreachable state for a long time and cannot be restarted or stopped. In such a scenario, use this option to forcibly stop and later restart the Agent.
To restart the Agent use the agentctl start command.
6.4.2 Changing the Logging Level for the Audit Vault Agent
Learn how to change the logging level for Oracle Audit Vault Agent.
The logging level that you set affects the amount of information that Oracle writes to the log files. You may need to take this into account due to disc space limitations.
Log files are located in the Agent_Home/av/log directory.
The following logging levels are listed in the order of the amount of information written to log files, where debug provides the most information:
-
error - Writes only error messages
-
warning - (Default) Writes warning and error messages
-
info - Writes informational, warning, and error messages
-
debug - Writes detailed messages for debugging purposes
Using the Audit Vault Server Console to Change Logging Levels
To change the logging level for the Audit Vault Agent using the Audit Vault Server UI, see "Clearing Diagnostic Logs".
Using AVCLI to Change the Agent Logging Level
To change the logging level for the Audit Vault Agent using the AVCLI utility:
-
Ensure that you are logged into AVCLI on the Audit Vault Server.
-
Run the
ALTER HOSTcommand.The syntax is as follows:
ALTER HOSThost_nameSET LOGLEVEL=av.agent:log_levelIn this specification:
-
host_name: The name of the host where the Audit Vault Agent is deployed.
-
log_level: Enter a value of
info,warn,debug, orerror.
-
6.4.3 Viewing the Status and Details of Audit Vault Agent
Learn about viewing the status and details of Audit Vault Agent.
You can view an Audit Vault Agent's status and details such as activation key, platform, version, location, and other details.
Prerequisite
Log in to the Audit Vault Server console as an administrator. See Using Audit Vault Server Console for more information.
To view the status and details of an Audit Vault Agent:
6.4.4 Deactivating and Removing Audit Vault Agent
Learn about deactivating and removing Audit Vault Agent.
Use this procedure to deactivate and remove Audit Vault Agent.
See Also:
If you have registered the Audit Vault Agent as a Windows service, see Registering and Unregistering the Audit Vault Agent as a Windows Service to unregister the service.
6.5 Updating Audit Vault Agent
Learn about updating Audit Vault Agent.
When you update the Audit Vault Server, the Audit Vault Agent is automatically updated. When you upgrade the Audit Vault Server to a later version, or restart the Audit Vault Agent, you no longer need to restart audit trails manually. The audit trails associated with the Audit Vault Agent automatically restart if you have not explicitly stopped them. If you upgrade the Audit Vault Server, the audit trails associated with the updated Agents will automatically restart if the trails have a single plug-in.
See Also:
Oracle Audit Vault and Database Firewall Installation Guide for information about downloading upgrade software.
6.6 Deploying Plug-ins and Registering Plug-in Hosts
Learn about deploying plug-ins and registering plug-in hosts.
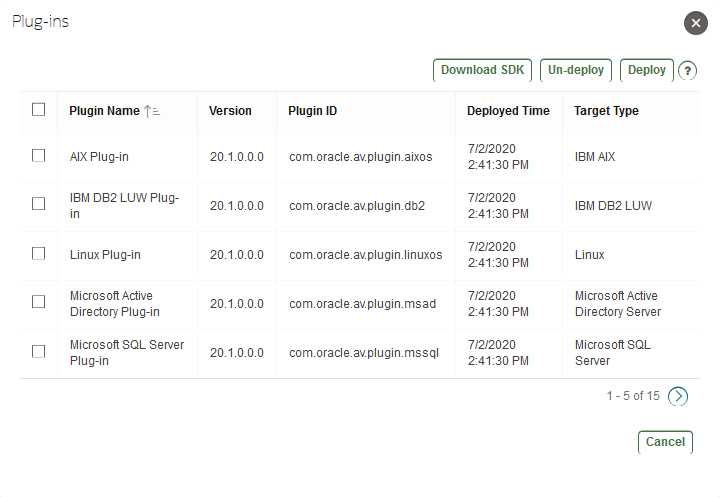
6.6.1 About Plug-ins
Learn about plug-ins for Audit Vault Server.
Each type of target has a corresponding software plug-in in the Audit Vault Server, which enables the Audit Vault Agent to collect audit data. You can deploy more plug-ins, in addition to those shipped with Oracle Audit Vault and Database Firewall, in order to collect audit data from more target types.
A plug-in supports only one target type. However, you may deploy more than one plug-in for the same target type if, for example, you acquired each plug-in from a different developer, or each plug-in supports a specific type of audit trail for the same target type. You can select the specific plug-in to use when you configure audit trail collections.
To start collecting audit data from the target type associated with a plug-in, you must also add the target in the Audit Vault Server, then configure and manually start audit trail collection.
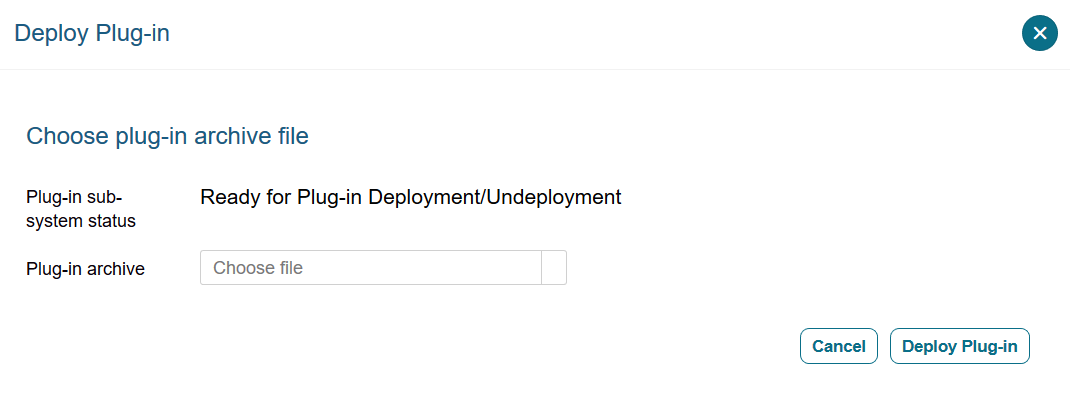
Deploying a plug-in consists of three steps:
6.6.2 Ensuring that Auditing is Enabled in a Target
Learn how to ensure that auditing is enabled in a target.
Ensure that auditing has been enabled in the target. See the target's product documentation for more information.
See Also:
Ensuring that Auditing is Enabled on the Target for information on plug-ins for Oracle Database.
6.6.3 Registering the Plug-in Host in Audit Vault Server
Learn about registering a plug-in host in Audit Vault Server.
To register a host in the Audit Vault Server, see Registering Hosts on the Audit Vault Server.
Oracle AVDF provides out-of-the-box plug-ins for most commonly used trails. See Plug-In Reference for a complete list. You don't need to deploy plug-ins for targets that have existing out-of-the-box plug-ins.
6.6.4 Deploying and Activating the Plug-in
Learn about deploying and activating a plug-in in Audit Vault Server.
To deploy and activate a plug-in: