AHF Release 24.5
- A New CLI Option to Run an AHF Balance Fleet Report on an Enterprise Manager (EM) Group of Clusters
AHF 24.5 introduces a new CLI option that allows you to run a Balance Fleet Report on an Enterprise Manager (EM) group of clusters. The--em-groupflag is designed to work with the--scope fleetoption. This feature enables administrators to efficiently manage and optimize their cluster resources by generating comprehensive fleet reports. - Oracle Trace File Analyzer Filters Out Small Trace Files from Being Collected
AHF 24.5 introduces enhancements to the Oracle Trace File Analyzer, allowing for more efficient diagnostic collection by filtering out duplicate small trace files that may be redundant or uninformative. - Data Guard Health Report Included in AHF Insights
AHF Insights now includes comprehensive Data Guard Configuration and Health Reports. - System Health Metrics Available on First Failure
AHF can now be configured to automatically collect real-time system health metrics, ensuring they are available at the time of a failure and included within diagnostic collections. These metrics, such as CPU, memory, and IO consumers, are invaluable to Oracle Support for diagnosing Service Requests. - Discovery of Nodes and Switches on Dom0
AHF compliance discovery has been enhanced to automatically detect nodes and switches on Dom0. - Security Checks Section in Oracle Orachk and Oracle Exachk Reports
Beginning with AHF 24.5, Oracle Orachk and Oracle Exachk reports include a new Security section that consolidates all best practice security-related checks. - New Oracle Orachk and Oracle Exachk Best Practice Checks
Release 24.5 includes the following new Oracle Orachk and Oracle Exachk best practice checks.
Parent topic: 2024 AHF Releases
A New CLI Option to Run an AHF Balance Fleet Report on an Enterprise Manager (EM) Group of Clusters
AHF 24.5 introduces a new CLI option that allows you to run a Balance Fleet Report on an Enterprise Manager (EM) group of clusters. The --em-group flag is designed to work with the --scope fleet option. This feature enables administrators to efficiently manage and optimize their cluster resources by generating comprehensive fleet reports.
- Specify the EM Group Name: Use the EM Group name as the fleet name and include the
--em-groupflag in your command. - Existing or New Groups: You can use an existing EM Group or create a new group of clusters. For example, create an EM Group for each data center to run a Balance Fleet report for a specific data center.
For more information about EM Groups, see Managing Groups in the Oracle® Enterprise Manager Cloud Control Monitoring Guide.
Note:
- The
--em-groupflag is mutually exclusive with the--clustersoption. This means you cannot use both flags simultaneously. - The
--em-groupflag must be used with the--scope fleetoption.
ahf analysis create --type impact --scope fleet --name <em-group-name> --em-groupReplace em-group-name with the name of your EM Group. This command will generate a Balance Fleet report, with the EM Group name appearing in the HTML Fleet report as the name of the fleet.
ahf analysis create --type impact --scope fleet --name testgroup --em-group
Starting analysis and collecting data for impact
Report is generated at : /scratch/testuser/view_storage/bagleeso_tfa1/work/oracle.ahf/data/testnode/
diag/balance/user_testuser/fleet_020424_225851580_UTC.htmlRelated Topics
Parent topic: AHF Release 24.5
Oracle Trace File Analyzer Filters Out Small Trace Files from Being Collected
AHF 24.5 introduces enhancements to the Oracle Trace File Analyzer, allowing for more efficient diagnostic collection by filtering out duplicate small trace files that may be redundant or uninformative.
- A new filter,
collection.smallfiles.filter, has been introduced to filter out database foreground and background logs and CRS client logs. - This filter is set to 'OFF' by default. You can enable it by setting it to 'ON' to start filtering out small trace files.
tfactl set collection.smallfiles.filter=ON
tfactl set collection.smallfiles.filter=OFF- You can customize the size threshold for these files using the
collection.smallfile.sizefilterparameter. - The valid range for this parameter is between 8 KB and 1 MB, with a default value of 8 KB.
- If a file's size is greater than or equal to the threshold set by
collection.smallfile.sizefilter, it will be collected. - If a file's size is less than the threshold, only one file among those of similar size will be collected, and the rest will be skipped. Similar size means that the difference between the file sizes is less than 8 bytes.
tfactl set collection.smallfile.sizefilter=10KBFiltering All Foreground Database Logs: You can filter out all foreground database logs, regardless of their size, by using the -nodbforegroundfiles flag in the tfactl diagcollect command.
tfactl diagcollect <other_parameters> -nodbforegroundfilesThese enhancements help reduce the time and space required for Oracle Trace File Analyzer to collect and redact diagnostics, especially when dealing with a large number of small trace files.
Related Topics
Parent topic: AHF Release 24.5
Data Guard Health Report Included in AHF Insights
AHF Insights now includes comprehensive Data Guard Configuration and Health Reports.
Previously, troubleshooting health and performance issues in Data Guard required collecting diagnostics from multiple sources, making the process cumbersome and error-prone. This enhancement simplifies the troubleshooting of Data Guard health and performance issues.
The AHF Insights report within a diagnostic collection for Data Guard includes a new Data Guard section, which shows:
- Configuration
- Metrics
- Log switch interval heatmap
- Archive log size
- Process CPU utilization
tfactl diagcollect -srdc dbdataguardFor more information, see Explore Diagnostic Insights.
Related Topics
Parent topic: AHF Release 24.5
System Health Metrics Available on First Failure
AHF can now be configured to automatically collect real-time system health metrics, ensuring they are available at the time of a failure and included within diagnostic collections. These metrics, such as CPU, memory, and IO consumers, are invaluable to Oracle Support for diagnosing Service Requests.
- Automatic Collection: AHF can capture system health metrics automatically, ensuring that critical data is available immediately upon failure.
- Included in Diagnostic Collections: The collected system health metrics are integrated into diagnostic collections, providing comprehensive data for troubleshooting.
ahf configuration set --property ahf.collectors.enhanced_os_metrics --value onRelated Topics
Parent topic: AHF Release 24.5
Discovery of Nodes and Switches on Dom0
AHF compliance discovery has been enhanced to automatically detect nodes and switches on Dom0.
Previously, users had to manually provide the cluster nodes and switches when running on a KVM host. With this update, compliance simplifies the process by using components already configured using AHF to run checks on Dom0. This ensures that all relevant components are accurately detected and included in compliance checks.
Parent topic: AHF Release 24.5
Security Checks Section in Oracle Orachk and Oracle Exachk Reports
Beginning with AHF 24.5, Oracle Orachk and Oracle Exachk reports include a new Security section that consolidates all best practice security-related checks.
The Security section contains selected controls that may impact the overall security of a system.
Security controls are typically reviewed for impact against Confidentiality, Integrity, and Availability (CIA). The National Institute of Standards and Technology (NIST) definition of CIA is as follows:
- Confidentiality: Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information
- Integrity: Guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity
- Availability: Ensuring timely and reliable access to and use of information
Figure -18 Security checks for Database Server
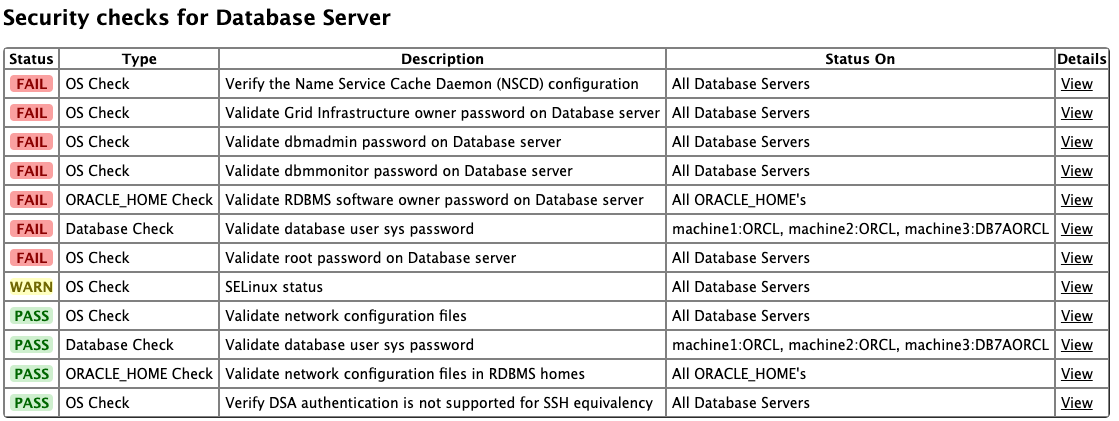
For more information about general security guidelines, refer to Oracle Exadata Database Machine Security FAQ (Doc ID 2751741.1).
Parent topic: AHF Release 24.5
New Oracle Orachk and Oracle Exachk Best Practice Checks
Release 24.5 includes the following new Oracle Orachk and Oracle Exachk best practice checks.
Best Practice Checks Common to Both Oracle Orachk and Oracle Exachk
- Verify clusterware internal patch metadata matches grid home OPatch inventory
- Transport Lag <= 30 Seconds
- Apply Lag <= 30 Seconds
- Data Guard Ready for Failover
- Data Guard Ready for Switchover
All checks can be explored in more detail via the Health Check Catalogs:
Parent topic: AHF Release 24.5