6 Configuring Cloud Native Core Policy Using Cloud Native Core Console
This chapter describes how to configure different services in Oracle Communications CNC Policy and how to create policies and manageable objects in CNC Policy using Oracle Communications Cloud Native Core Console.
Cloud Native Core Console Interface
This section provides an overview of the Oracle Communications Cloud Native Core (CNC) Console, which includes a interface to aid in creating policies and manageable objects in CNC Policy.
- Open a web browser and enter the IP address of the CNC Console system.
The login page opens.
- Enter your Username.
- Enter your Password.
- Click Login.
Tha main page opens.You are logged in. All the Policy related configurations are available in the left navigation menu under Policy.
Figure 6-1 CNC Console Interface

Session Viewer
The Session Viewer displays detailed session information for a specific subscriber. Within the session viewer, you can enter query parameters to render session data for a specific subscriber. This section provides information about viewing the sessions.
To view the sessions:
- From the navigation menu, under Policy, click Session Viewer. The Session Viewer page appears.
- From the
Session Type
drop-down menu, select the service whose sessions you want to view. Possible
values are:
- SM Policy Association
- AM Policy Association
- PA Policy Association
- PCRF-Core Session
- Binding Session
-
- From the Identifier
Type drop-down menu, select the identifier type for the selected
session type. Possible values for SM Policy Association, AM
Policy Association, PA Policy Association, andBinding
Session are:
- SUPI
- GPSI
- IPV4
- IPV6
- POLICY_ASSOC_ID
- MAC
Note:
AM Policy Association and PA Policy Association fetches session data using POLICY_ASSOC_ID (Session ID) only. - From the Identifier Type drop-down menu, select the identifier
type for the selected session type. Possible values for PCRF-Core
Session are:
- DIAMETER_SESSION_ID
- IMSI
- MSISDN
- IPV4
- IPV6
- From the Identifier
Type drop-down menu, select the identifier type for the selected
session type. Possible values for SM Policy Association, AM
Policy Association, PA Policy Association, andBinding
Session are:
- Enter the value in the Identifier Value field for the selected identifier type.
- Click Query. Information about the subscriber session(s) is displayed.
Following screen capture is an example of Query result: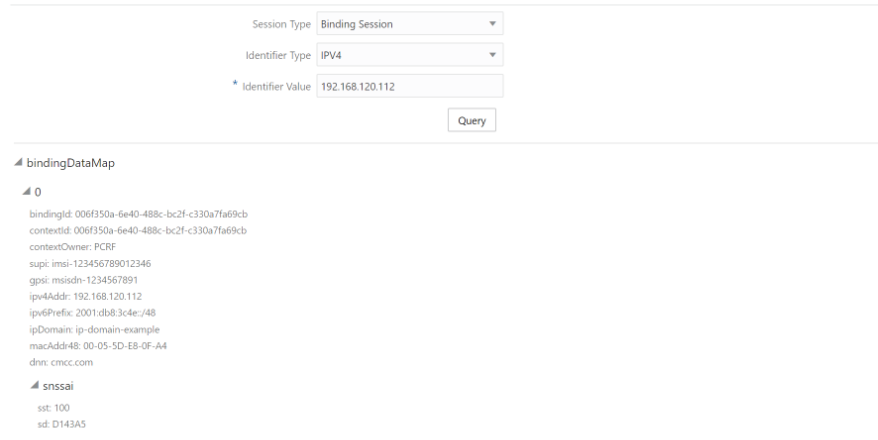
If session data is not available, the error is displayed along with No session found.
General Configurations
You can manage and view the General Configurations from this page.
- From the navigation menu, under
Policy, click General Configurations.
The General Configurations screen appears.
- Click Edit to edit the general configurations.
- Enter the following information:
- Enable Tracing- Specifies whether to enable tracing. The default value is true.
- Enable Metrics- Specifies whether to enable system metrics. The default value is true.
- API Gateway Host- The name of the API gateway host. This field is not used.
- API Gateway Port- The port number of the API gateway (if a port other than the default is being used). The default value is 80. This field is not used.
- Enable TLS- Specifies whether to enable TLS. The default value is false.
- Enable Subscriber Activity Logging- Specifies whether to enable subscriber activity logging. The dafault value is false.
- Click Save.
Service Configurations
You can tailor the Policy services as per network operator's requirements using the Service configuration pages. The configurations include setting up end point addresses, setting up log levels and other debug information like tracing etc. and customizing and/or optimizing NF interactions for example with UDR etc.
Note:
- The NAS Message Maximum Packet Size field is not supported in this release of PCF and will not take effect.
- The Validate User and Query User fields must always be set to false in this release of PCF.
Configuring PCF Session Management Service
- From the navigation menu, under Policy, click Service Configurations,
and then click PCF Session
Management.
The PCF Session Management service screen appears.
- Click Edit to configure the PCF Session Management service.
- Check the default configuration for the fields
available in respective groups and edit as necessary.
The following table describes the fields along with their valid input values under each group:
Field Name Description System Log Level
Indicates the log level of PCF Session Management (SM) service.
Default Value: WARN
Allowed Values: DEBUG, INFO, WARN, ERROR
Component Tracing
Determines if component tracing is enabled. Component tracing is used to evaluate system process latency in detail level.
Default Value: FALSE
Server Root URL Specifies the callback URI for notifications to be received by the user. FQDN
This is the PCF FQDN used by the PCF to register Binding data to BSF. AF may use this FQDN to communicate with PCF on N5 reference point. FQDN needs to be in a standard FQDN format (RFC 1035).
Default Value: pcf-smservice.pcf
Diameter Realm
This is the PCF diameter realm used by the PCF to register Binding data to BSF. Diameter based AF may use this diameter realm to communicate with PCF on Rx reference point.
Default Value: pcf-smservice.svc
Diameter Identity
This is the PCF diameter identity used by the PCF to register Binding data to BSF. Diameter based AF may use this diameter identity to communicate with PCF on Rx reference point.
Default Value: pcf-smservice
Snssai
Used to register Binding data to BSF by PCF.
AF/BSF may use this SNSSAI to discover proper PCF.
Default Value: 0,000000
Enable Metrics
This determines if system metrics is enabled. This will take priority on global metrics configuration. Default Value: True Override Supported Features
Default Value: PRA PRA is only supported in this release.
SMF Terminate Uri Segment Segment in the URI to identify the SM Session TERMINATE operation. Default Value: terminate SMF Update Uri Segment Segment in the URI to identify the SM Session UPDATE operation. To be configured when the SMF uses anything other than the segment string mentioned in the standards. Default Value: update Process 400 as 200 Default Value: False Enable Custom Json This determines if custom JSON is enabled. Default Value: False
User Validate User
When this option is enabled, and the subscriber is not found in the UDR, or PCF is not able to query an available/eligible UDR, PCF shall fail the SM Association creation request with a 400 USER_UNKNOWN error.
When this option is disabled, and the subscriber is not found in the UDR, or PCF is not able to query an available/eligible UDR, PCF shall not fail the SM Association creation request, but continue policy processing.
Default Value: FALSE
Query User
Determines if user query from UDR is enabled. When this option is enabled, PCF shall query the UDR about the subscriber contained in the SM Association create request by sending a GET request for “sm-data” resource on the nudr-dr service.Note:
The PCF User Service caches the subscriber profile when “Subscribe To Notify” option is enabled, in that case, the PCF may not always reach the UDR when the subscriber profile is found in the local cache.Default Value: TRUE
Query User On Update
Determines if user query from UDR on update is enabled. When this option is enabled, PCF shall query the UDR about the subscriber present in the SM Association update request by sending a GET request for “sm-data” resource on the nudr-dr service.Note:
The PCF User Service caches the subscriber profile when “Subscribe To Notify” option is enabled, in that case, the PCF may not always reach the UDR when the subscriber profile is found in the local cache.Default Value : FALSE
Query User On Delete
Determines if user query from UDR on delete is enabled. When this option is enabled, PCF shall query the UDR about the subscriber present in the SM Association delete request by sending a GET request for “sm-data” resource on the nudr-dr service.Note:
The PCF User Service caches the subscriber profile when “Subscribe To Notify” option is enabled, in that case, the PCF may not always reach the UDR when the subscriber profile is found in the local cache.Default Value : FALSE
Query User On Reauth
Determines if user query from UDR on reauth is enabled. When this option is enabled, PCF shall query the UDR about the subscriber, when it receives a Reauthorization request (like an Rx or Policy Authorization request) by sending a GET request for “sm-data” resource on the nudr-dr service.Note:
The PCF User Service caches the subscriber profile when “Subscribe To Notify” option is enabled, in that case, the PCF may not always reach the UDR when the subscriber profile is found in the local cache.Default Value : FALSE
Subscribe to Notify
When this flag is enabled, PCF shall subscribe with the UDR to get notified on changes in subscriber profile.
Default Value: TRUE
Ignore Subs Notification Check
Default Value: FALSE Enable CHF Query All
When this option is enabled, PCF shall fetch the status of Policy Counters (Spending Limit Status Information) and subscribe with the CHF to get notified on change in status by sending a POST request to the nchf-spendinglimitcontrol service. Default Value: FALSE Include Snssai in user query Default Value: true Include Dnn in user query Default Value: true Policy Evaluate This determines if policy evaluate is enabled.
Default Value: TRUE
Policy Control Request Trigger Default Policy Control Request Triggers
Values: PLMN_CH, UE_IP_CH, DEF_QOS_CH, and AC_TY_CH Binding Configuration Binding Operation
Determines if binding operation (register and deregister) to the BSF is enabled.
Default Value: TRUE
Binding Use Local Configured Bsf Always
Whether to use local configured BSF without Always discovering.
Default Value: FALSE
Binding Use Local Configured Bsf When Not Discovered
Whether to use local configured (if having) BSF when not discovered or discover failed. Local configuration can be done using custom yaml.
Default Value: FALSE
Use HTTP2
Determines if using http/2 to communicate with BSF. Otherwise use http/1.1. Default Value : TRUE
QOS Qos Data Id Prefix
This is the prefix of qos data id used by PCF to generate qos data id. For example, prefix is "qosdata_", the generated qos data id is qosdata_0.
Default Value : qosdata_
update Default Pcf Rule With Auth Def Qos
This determines whether to update Qos of default PccRule with the authDefQos of session rule.
Default Value : TRUE
Install Default Qos If Not Requested
This determines whether to install default Qos to the PDU session if UE not requested. Default Value : TRUE
Default Qos 5qi
This is the 5Qi of default Qos which will be applied if no default Qos is requested by UE. Default Value: 9
Default Qos Arp Preempt Cap
This is the ARP Preemption Capability of default Qos which will be applied if no default Qos is requested by UE.
Default Value : MAY_PREEMPT
Default Qos Arp Preempt Vuln
This is the ARP PreemptionVulnerability of default Qos which will be applied if no default Qos is requested by UE.
Default Value : NOT_PREEMPTABLE
Default Qos Arp Priority Level
This is the ARP Priority Level of default Qos which will be applied if no default Qos is requested by UE. Default Value: 1
Rule Install Default Pcc Rule
Default Value : IF_NO_RULE Default PCC Rule Profile Rule Id Prefix
Default Value : 0_ Default Pcc Rule 5qi
This is the 5Qi of default pcc rule. Default Value: 9
Default Pcc Rule Precedence
This is the precedence of default pcc rule.
Default Value : 3000
Default Pcc Rule Arp Preempt Cap
This is the ARP Preemption Capability of qos of default PCC rule.
Default Value : NOT_PREEMPT
Default Pcc Rule Arp Preempt Vuln
This is the ARP PreemptionVulnerability of qos of default pcc rule.
Default Value : PREEMPTABLE
App Rule Precedence Min
This value defines the minimum value for precedence of a PCC rule as authorized by the establishment of an application flow by the AF. If multiple rules are applied to the same packet flow or UE resource (i.e., overlapping rules) a rule with lower precedence value takes the priority over a rule with higher precedence value. The value of -1 is used to not set the precedence of a rule (NOT RECOMMENDED).
Default Value: 400
App Rule Precedence Max
This value defines the maximum value for precedence of a PCC rule as authorized by the establishment of an application flow by the AF. If multiple rules are applied to the same packet flow or UE resource (i.e., overlapping rules) a rule with lower precedence value takes the priority over a rule with higher precedence value. The value of -1 is used to not set the precedence of a rule (NOT RECOMMENDED).
Default Value: 899
Default Pcc Rule Arp Priority Level
This is the ARP Priority Level of qos of default pcc rule The range is 1 to 15. Values are ordered in decreasing order of priority, for example, with 1 as the highest priority and 15 as the lowest priority. Default Value : 15
Switch Flow In To Out Enabled
Default Value: FALSE
Set PacketFilterUsage to true for Preliminary Service Info Default Value: FALSE Charging Charging Data Id Prefix
Default Value: chgdata_
Primary CHF Address
Address of the primary CHF Secondary CHF Address
Address of the secondary CHF Online
Indicates the online charging is applicable to the PDU session. Offline
Indicates the offline charging is applicable to the PDU session. Traffic Control Traffic Control Id Prefix Default Value: tcdata_
IMS Emergency Session Emergency DNNs
Priority Level
Defines the relative importance of a resource request.
Default Value: 1
Preemption Capability
Defines whether a service data flow may get resources that were already assigned to another service data flow with a lower priority level. Default Value: MAY_PREEMPT
Preemption Vulnerability
Defines whether a service data flow may lose the resources assigned to it in order to admit a service data flow with higher priority level. Default Value: NOT_PREEMPTABLE
Audit Enabled Determines whether to send registration request to Audit service or not. Default Value: True
Notification Rate (per second) Defines the number of stale records which Audit service will notify to Session Management (SM) service in one second. Default Value: 50
Policy Association Age (in minutes) Defines the age of a SM policy association after which a record is considered to be stale on PCF and the SMF is queried for presence of such associations. Default Value: 140
Policy Association Maximum Age (in minutes) Defines the maximum age of a SM policy association after which a record is purged from PCF SM database without sending further queries to SM. Default Value: 2880
Minimum Audit Passes Interval (in minutes) Defines the time when next audit for the SM service table will begin after delta time if auditing this table has been finished before this specified time. Default Value: 330
- Click Save.
Configuring PCF Access and Mobility Service
You can configure the PCF access and mobility service from this page.
- From the navigation menu, click .
The PCF Access and Mobility Service screen appears.
- Click Edit to edit the PCF access and mobility service configurations.
- Check the default configuration for
all the fields in all groups and edit as necessary.
The following table describes the input fields available under each group:
Field Name Description System Root Log Level Default Value: WARN
Log Level Use Policy Service
Default Value: true
Use User Service
Default Value: true
Subscribe
Default Value: true
Enable HTTP2.0
Default Value: false
Validate User
Determines if user validate is enabled. HTTP 400 with cause USER_UNK NOWN returns, if this is enabled and user not found in UDR.
Default Value: false
App Default Service Area Restriction
Default Rfsp
Default Triggers
- Click Save.
Configuring PCF Policy Authorization Service
You can configure the PCF policy authorization service from this page.
- From the navigation menu, click .
The PCF Policy Authorization Service screen appears.
- Click Edit to edit the PCF policy authorization service configurations.
- Check the default configuration for
all the fields in all groups and edit as necessary.
The following table describes the input fields displayed under each group:
Field Name Description System Af Direct Reply
Default Value: true Override Supported Features
AF Terminate Uri Segment
Default Value: termination AF Subscriber Notify Segment
Default Value: termination Rx Resource Allocation Partial Failure Report Prefence After PCF triggers a notification to Diameter Connector, the connector generates a RAR message. The partial failed specific action in the RAR message will depend on the priority of the action subscribed in the AAR message. The priority of the actions is INDICATION_OF_FAILED_RESOURCES_ALLOCATION > INDICATION_OF_RELEASE_OF_BEARER > INDICATION_OF_LOSS_OF_BEARER. If you want to assign the action not depend on the priority, you can assign the action in this field. The default configuration is empty, you can choose one action from the below mentioned three options. Once the value is defined in this field, the connector will use the configured action not depend on the priority.
Valid Options are:- INDICATION_OF_FAILED_RESOURCES_ALLOCATION
- INDICATION_OF_RELEASE_OF_BEARER
- INDICATION_OF_LOSS_OF_BEARER
IMS Emergency Session Emergency Service URNs
Reservation Priority Types
Default Value: PRIO_6 - Click Save.
Configuring PCF UE Policy Service
You can configure the PCF UE policy service from this page.
- From the navigation menu, click .
The PCF UE Policy Service screen appears.
- Click Edit to edit the PCF UE policy service configurations.
- In the Notification URI Root field, enter the callback URI for notifications to be received by the PCF UE Policy service (For example, while creating a subscription for the NAS Message Transfer with the AMF)
- Check the default configuration for
all the fields in all groups and edit as necessary.
The following table describes the input fields displayed under each group:
Field Name Description System Log Level
Default Value: WARN Notification URI Root
AMF Enable HTTP/1.1
Default Value: false NAS Message Maximum Packet Size (bytes)
enter a range in [0-65535] number User Validate User
Default Value: false Query User
Default Value: false - Click Save.
Configuring PCF User Connector Service
You can configure the PCF user connector service from this page.
- From the navigation menu, click .
The PCF User Connector Service screen appears.
- Click Edit to edit the PCF user connector service configurations.
- In the Server Root URL field, enter the callback URI for notifications to be received by the User service (For example, while creating a subscription for the user with the UDR)
- Check the default configuration for
all the fields in all groups and edit as necessary.
The following table describes the input fields displayed under each group:
Field Name Description System Log Level
Default Value: WARN Server Root URL
Common Resource Get Subscribe
Default Value: false Request Timeout
Default Value: 1000 DB Keys Precedence
User Index Keys
Indexing Index By Msisdn
Default Value: true Index By Extid
Default Value: true Index By Imsi
Default Value: true Index By Nai
Default Value: true UDR Base Uri
Default Value: /nudr-dr/v1 Supported Features
Default Value: f AM Data Uri
Default Value: /policy-data/ues/{ueId}/am-data UE Policy Set Uri
Default Value: /policy-data/ues/{ueId}/ue-policy-set SM Data Uri
Default Value: /policy-data/ues/{ueId}/sm-data Usage Mon Uri
Default Value: /policy-data/ues/{ueId}/sm-data/{usageMonId} Subs To Notify Uri
Default Value: /policy-data/subs-to-notify Subs To Notify Subs Id Uri
Default Value: /policy-data/subs-to-notify/{subsId} SM Data Subscription Resource Default value would be 1 on selection of "Sm-data" and other value is 2 on selection of "As requested by SM service". Request Timeout
Default Value: 1000 Explode Snssai
Default Value: false Enable HTTP1.1
Default Value: false Enable Discovery On Demand
Default Value: false - Click Save.
Configuring PCRF Core Settings
You can configure the PCRF core settings from this page.
- From the navigation menu, click .
The PCRF Core Settings screen appears.
- Click Edit to edit the PCRF Core settings configuration. This enables the Add button in Advanced Settings group.
- Click Add. The Add Advanced Settings window opens.
- Enter the values in Key and Value fields.
- Click Save.
Policy Engine
You can manage and view the Policy Engine service from this page.
- From the navigation menu, click .
The Policy Engine screen appears. On this page, you can see the list of all the supported services in CNC Policy. Below is a screen capture of Policy Engine page.
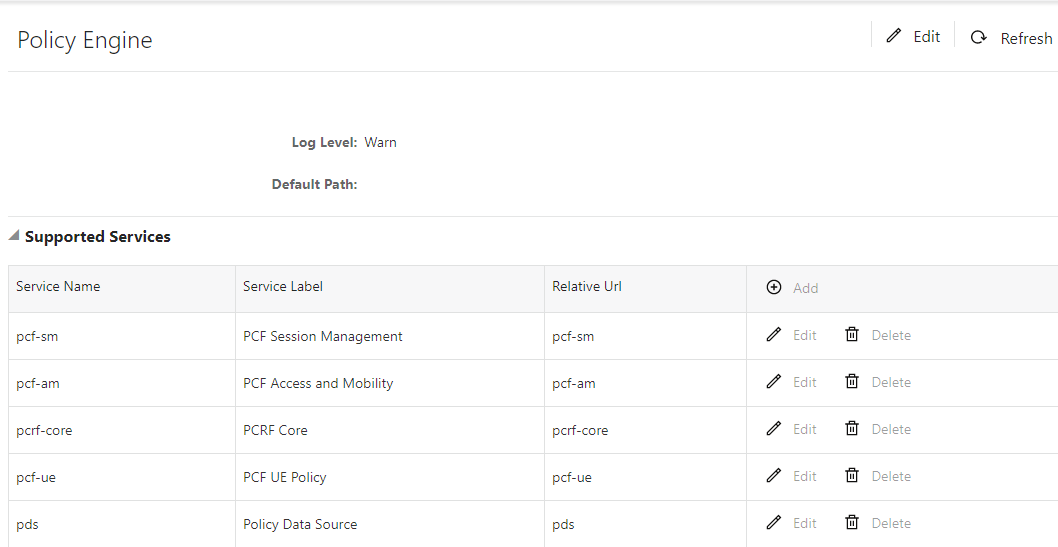
- Click Edit to edit the settings.
- Enter the value in Log Level field. The default value is WARN.
- Click Add in the Supported Services group.
The Add Supported Services screen appears.
- Enter the following information to
create service:
- Service Name: Enter the service name. You should use the same service name as mentioned in the above screen capture under Service Name label. For Example, for SM service, Service Name should be pcf-sm, for PCRF Core service, Service Name should be pcrf-core.
- Service Label: Enter the service label.
- Relative URL: Enter the relative URL.
- Click Save. The services get listed in the Supported Services list.
Note:
Use Edit or Delete buttons available in the next column to update or delete the existing Policy services.Configuring Audit Service
Oracle Communications Cloud Native Core Policy (OCCNCP) signalling services (SM service, AM service, UE service, Binding Management service etc.) are stateless in nature, thereby offloading session state to a centralized database (DB) tier, in this case, it is Oracle MySQL. As the session processing micro-services and the DB tier are different components that communicate over a network there are chances for certain transactions to fail on the transit, for example, in overload situations and/or as a result of code bugs. The OCCNCP solution requires a database audit mechanism to monitor records getting stale and to clean them up so that the database memory does not eventually grow indefinitely. The audit mechanism also notifies the owner services about stale records so that they can trigger signalling messages in certain cases to ensure that the sessions detected as stale by the Audit service is actually released by other consumer NFs. Additionally in certain cases, releasing a session when found to be stale in a NF may require to release associated sessions in the same and/or other NFs. For Example, deleting a stale SM association may require to delete the associated PA sessions.
You can configure the audit service from this page.
- From the navigation menu, under Policy, then under Service Configurations,
click Audit.
The Audit screen appears.
- Click Edit to edit the session management service configurations.
- Check the default configuration for the fields
available and edit as necessary.
The following table describes the input fields displayed under System group:
Field Name Description System Log Level
Indicates the log level of Audit service.
Default Value: Warn
Allowed Values: Debug, Information, Warn, Error
Audit Enabled
Determines if auditing is enabled for all the registered services. Default Value: FALSE
Audit Rate (records per second)
Defines the number of records audited per second.
- Click Save.
Logging in Audit Service
- Database and Table audited
- Number of records found to be stale
- Number of records removed (for DELETE action)
- Number of notifications sent (for NOTIFY action)
- Time taken to complete the audit pass
- Any exceptions occurred
Audit Report {
"database" : "pcf_smservice_161",
"table" : "SmPolicyAssociation",
"staleRecords" : 18869,
"recordsDeleted" : 0,
"timeToCompletePass" : 20,
"recordsEnqueuedForNotification" : 18869,
"exceptions" : [ ]
}Policy Data Configurations
This chapter describes how to create manageable objects in CNC Policy function.
Common
You can configure the common services from this page. To configure the common service, click .
- Policy Table
- Dropdown Blocks
- PCF Presence Reporting Area
- Policy Counter ID
- Match List
- Subscriber Logging
- Custom Attributes
Managing Policy Tables
This chapter describes how to create, modify, delete, and view policy tables, which are independent objects that you can use to capture differences in policy structures.
You can manage multiple policies with small differences by abstracting the differences into tables. The process of modifying the policies, or creating new, similar policies, then becomes a matter of modifying the policy table, which is simpler and less prone to error.
About Policy Tables
In practical use, many policies are very similar, having only small differences between them. A policy table abstracts the differences between related policies. Using a policy table instead of creating many similar policies makes the tasks of adding new policies, modifying existing sets of policies, and checking consistency among related policies simpler and less prone to error
Note:
Policy Table is only supported for the Session Managment service.- Table name
- Table description
- Column definitions
Every column has a definition that contains a name, data type, and indication if the column is a key column. Every entry in the column will be of the same data type as the column. Every table must have atleast one key column.
- Data
The contents of the table cells. (Blank cells are not allowed in a policy table.)
Each row in a policy table can be thought of as a scenario. Substitutions in policy condition and action parameters can include the values in a specified policy table.
Creating a Policy Table
To create a policy table:
Associating a Policy Table with a Policy
To associate a policy table with a new or existing policy, the policy table must already be created.
To associate a policy table with a policy rule:
- From the navigation menu, under Policy Management, click
Policy Projects.
The Policy Projects page displays all the created policies.
- Select the policy.
- Click Open for the selected policy. The policy page is
displayed. The following screen capture shows an example of the SM
Policies policy page:
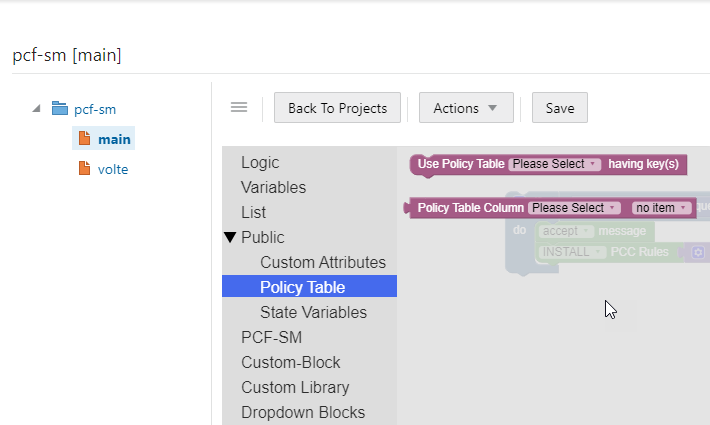
- Under Public section, click Policy Table. Following blocks are
displayed in the work area to create policy rule:
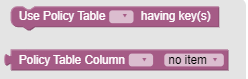
- In the first block, select the policy table from the Policy Table
drop-down and the corresponding key columns are displayed in the key(s).
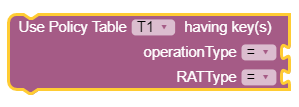
The following screen capture shows an example in which Policy Table T1
has been selected and the OperationType and RatType are the
corresponding key columns in the table T1.
- Select the operator from the operator drop-down and associate the value or
policy condition with the key column. You can select the value or policy
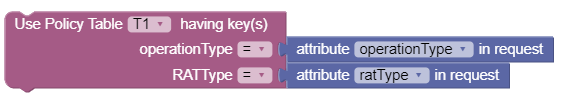
condition from Public and PCF-SM topics. The following screen
capture shows an example of associating policy conditions with the key columns,
OperationType and RatType.
 If all the values associated with the key columns match
its column data from policy table based on the operator used ("="), then it will
return the complete row data.
If all the values associated with the key columns match
its column data from policy table based on the operator used ("="), then it will
return the complete row data.
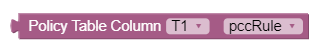
- In the second block, select the policy table from the Policy Table
Column drop-down and the corresponding non-key columns are displayed in
the no itemdrop-down. The following screen capture shows an example in
which policy table T1 is selected and the non-key column, pccRule
is displayed in the drop-down.
 This block returns the value of the non-key column
selected by taking row data as input from the first block.
This block returns the value of the non-key column
selected by taking row data as input from the first block.
- Click Save.
PCF Presence Reporting Area
You can manage, view, import, export and create the PCF Presence Reporting Area using this screen.
Note:
Only administrators can create presence reporting area.To configure the service:
- From the navigation menu, click .
The PCF Presence Reporting Area screen appears with the listing of all the available reports. You can create or import new reports from this page.
Note:
Click Export to download the available reports to your system. - Click Add.
The Create PCF Presence Reporting Area screen appears.
- Enter values for the input fields common to all the
groups available on the screen. .
The following table describes the fields:
Field Name Description Name The unique name assigned to the PRA. Pra Id The unique identifying number of the PRA list. The ID must be numeric value between 0 and 16777125. This field is present if the Area of Interest subscribed or reported is a Presence Reporting Area. - Expand the
Tracking Area
List group.
The expanded window displays the available tracking area lists. To create new lists:
- Click
Add.
The Add Tracking Area List window appears on the screen.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Mnc Defines the Mobile Network Code. Two to three digit number. Mcc Defines the Mobile Country Code. Three digit number. Tac 28-bit string identifying an E-UTRAN Cell Id as specified, in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the Cell Id shall appear first in the string, and the character representing the 4 least significant bit of the Cell Id shall appear last in the string. Pattern: '^[A-Fa-f0-9]{7}$'
Example:
An E-UTRAN Cell Id 0x5BD6007 shall be encoded as "5BD6007".
Note:
Click Cancel to cancel the changes. - Click
Save.
The value gets listed in the Tracking Area List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click
Add.
- Expand the
Ecgi List group.
The expanded window displays the available Eutra Cell Ids. To create new Ids:
- Click
Add.
The Add Ecgi List window appears on the screen.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Mnc Defines the Mobile Network Code of the PLMN. Two to three digit number. Mcc Defines the Mobile Country Code of the PLMN. Three digit number. Eutra Cell Id 28-bit string identifying an E-UTRA Cell Id as specified in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the Cell Id shall appear first in the string, and the character representing the 4 least significant bit of the Cell Id shall appear last in the string.
Pattern: '^[A-Fa-f0-9]{7}$'
Example:
An E-UTRA Cell Id 0x5BD6007 shall be encoded as "5BD6007".
Note:
Click Cancel to cancel the changes. - Click
Save.
The value gets listed in the Ecgi List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click
Add.
- Expand the
Ncgi List group.
The expanded window displays the available Nr Cell Ids. To create new Ids:
- Click
Add.
The Add Ncgi List window appears on the screen.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Mnc Defines the Mobile Network Code of the PLMN. Two to three digit number. Mcc Defines the Mobile Country Code of the PLMN. Three digit number. Nr Cell Id 36-bit string identifying an NR Cell Id as specified in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the Cell Id shall appear first in the string, and the character representing the 4 least significant bit of the Cell Id shall appear last in the string.
Pattern: '^[A-Fa-f0-9]{9}$'
Example:
An NR Cell Id 0x225BD6007 shall be encoded as "225BD6007".
Note:
Click Cancel to cancel the changes. - Click
Save.
The value gets listed in the Ncgi List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click
Add.
- Expand the
Global Ran NodeId
List group.
The expanded window displays the available N3 lwf Ids. To create new Ids:
- Click
Add displayed
in the window.
The Add Global Ran NodeId List window appears on the screen.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Plmn Id Mnc Defines the Mobile Network Code of the PLMN. Two to three digit number. Mcc Defines the Mobile Country Code of the PLMN. Three digit number. N3 lwf Id This field is included if the RAN node belongs to non 3GPP access (i.e a N3IWF).
If included, this field contains the FQDN of the N3IWF.
gNb Id Bit Length Unsigned integer representing the bit length of the gNB ID within the range 22 to 32
gNb Value This represents the identifier of the gNB.
The string shall be formatted with following pattern:
'^[A-Fa-f0-9]{6,8}$'
The value of the gNB ID shall be encoded in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the gNB ID shall appear first in the string, and the character representing the 4 least significant bit of the gNB ID shall appear last in the string.
Examples:
"382A3F47" indicates a gNB ID with value 0x382A3F47
Nge Nb Id This field is included if the RAN Node Id represents a NG-eNB. When present, this field contains the identifier of an NG-eNB. Note:
Click Cancel to cancel the changes. - Click
Save.
The value gets listed under Global Ran NodeId List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click
Add displayed
in the window.
- Click Save.
The Pra details are listed on the PCF Presence Reporting Area screen.
Note:
Click Cancel to cancel the configuration.
Importing the PCF Presence Reports
To import the reports:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload button.
Configuring Policy Counter Id
You can create and manage Policy Counter Ids from the Policy Counter Id screen. The page provides information about the existing Policy Counter Ids. You can create or refresh the Policy Counter Ids from this page.
Note:
Only administrators can create Policy Counter Ids.To configure the service:
- From the navigation menu, click .
The Policy Counter Id screen appears with the listing of all the available rules. You can create or import new data from this page.
Note:
Click the Export button to download the available listings to your system. - Click
Add.
The Create Policy Counter Id screen appears.
- On the
Create Policy Counter
Id screen, enter values for the input fields common to all the groups
available on the screen.
The following table describes the fields:
Field Name Description Policy Counter Id
Policy Counter Id's Name. Name Description
Policy Counter Id's description. Default Status
Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Policy Counter Id screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Policy Counter Id Data
To import the Policy Counter Ids:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring Match Lists
In a wireless network, a match list is a set of defined values that can represent, for example, IDs or Internet addresses. Match lists provide whitelist and blacklist functions in policy rules. Match lists support wildcard matching.
A match list is a set of values in various categories, including access point names (APNs), subscriber IMSIs, location area codes (LACs), service area codes (SACs), Internet addresses, and user equipment identities. A match list can function as a whitelist (listing items to be included) or a blacklist (listing items to be excluded). By using a match list, you can, for example, apply a policy to all subscribers in a set of LACs, or block access to a list of Internet addresses known to be high risk. Match lists support wildcards. Using wildcards, a range of values can be specified compactly.
Creating a Match List
- From the navigation pane, click .
The Match List page opens in the work area.
- Click
Create.
The Create Match List page opens.
- Enter the following
information:
- ID: The ID assigned to the match list.
- Name: The name
assigned to the match list.
The name can only contain the characters A-Z, a-z, 0-9, period (.), hyphen (-), and underline (_). The maximum length is 40 characters.
- Description: Free-form text
- Type: Select
from the following:
- string (default) - The list consists of strings.
- wildcard string - The list consists of wildcard match patterns that use an asterisk (*) to match zero or more characters or a question mark (?) to match exactly one character.
- Items:
- Click Save.
The match list is defined in the database and can now be used in a policy.
Modifying a Match List
- From the navigation pane, click .
The Match List page opens in the work area, displaying the list of defined match lists.
- Select the match list you want to modify.
- Click
Edit.
The Edit Match List page opens.
- Modify match list information as required.
- Click
Save.
The match list is modified.
Deleting a Match List
- From the navigation pane, click .
The Match List page opens in the work area, displaying the list of defined match lists.
- Select the match list you want to delete.
- Click
Delete.
A confirmation message displays.
- Click
OK.
The match list is deleted.
Importing the Match Lists
To import the match lists:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Exporting the Match Lists
You can export the match lists by clicking Export All. The Match Lists will be downloaded in a local machine.
Managing Subscriber Logging
Subscriber logging lets you to define a list of the subscribers (identifier) that you are interested to trace. This allows you to use this functionality to troubleshoot problematic subscribers in production without having to change log levels that can impact all subscribers. Using the subscriber logging, you can trace all the logs related to the subscribers for which the this functionality is enabled.
Note:
This functionality is only supported by Session Management (SM) Associations in this release.Note:
The maximum number of subscribers that can be configured is 100.Note:
You can not modified subscriber information once it is entered. If you need to modify the subscriber information, delete the subscriber information and add it again .To configure a list of subscribers for logging:
- From the navigation menu, under Policy, then
under Policy Data
Configurations, and then under Common, click Subscriber Logging.
The Subscriber Logging screen appears with the listing of subscribers. You can create or import subscribers from this page.
Note:
Click Export to download the available listing on your syatem. - Click Add to add the subscriber
item to the list..
The Create Subscriber Logging screen appears.
- From the Identifier Type drop-down, select the
subscriber identifier type. Supported subscriber identifier type are:
- GPSI
- SUPI
- IPV4
- IPV6
- Enter the subscriber identier value in the Identifier Value field for the selected identifier type.
- Select Enable to enable/disable the subscriber logging functionality for the selected subscriber.
- Click Save.
Note:
Use pencil icon or trash can icon available in the next column to update or delete the subscriber listing.- Subscriber Identification including associated IP Address information
- Message, Container name, Level
- Policy related information (applied for the subscriber session)
- Date and Timestamps for all messages logged
Below screen capture is a log sample (kibana dashboard) with filter
"marker.name:SUBSCRIBER" and fields: message, level, kubernetes.container_name, and
marker.name.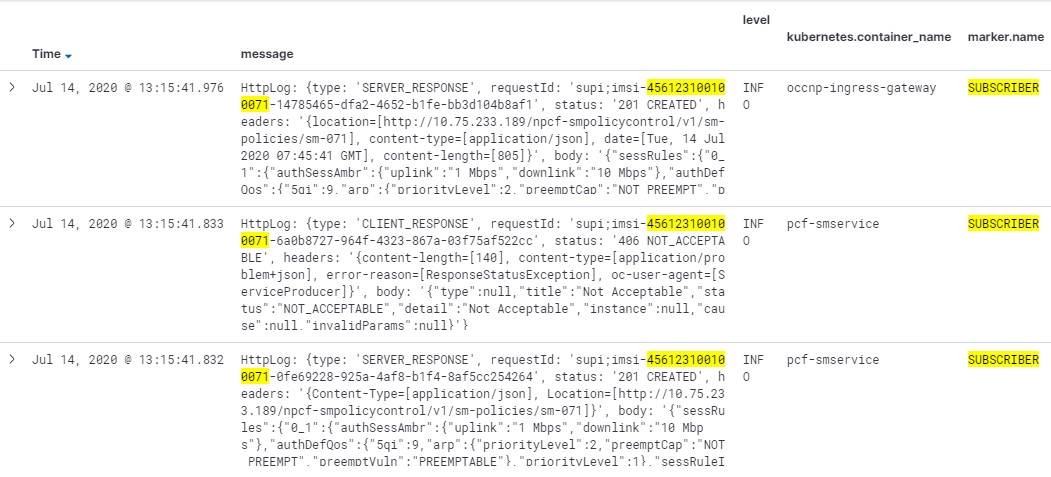
Custom Attributes
Custom attributes lets you to accept the vendor's data that is in custom format, not in the standard format. This data can then be used to construct conditions and actions .
Configuring Custom Schema
Note:
Custom schema yaml file should follow Open API standards.To import a custom schema file:
- Create a custom schema yaml file. Below is a sample yaml
file:
openapi: 3.0.0 info: description: Customer version: "0.0.1" title: Customer paths: /: get: operationId: get summary: get tags: - get responses: '200': description: OK content: application/json: schema: $ref: '#/components/schemas/Customer' components: schemas: Customer: type: object properties: phones: type: array items: type: string name: type: string address: $ref: '#/components/schemas/Address' Address: type: object properties: house: type: string street: type: string city: type: string - Save the yaml file on your system.
- From the navigation menu, click .
The Custom Schema screen appears with the listing of custom schema.
Note:
Click Export to downlaod the available listing on your system. - Click Import to import the custom schema yaml
file.
The File Upload window opens.
- Click Drop Files here or click to upload. Locate the yaml file to be imported.
- Click Import. After the import is complete, the schemas are listed on the Custom Schema page.
You can use this custom schema in creating policy conditions and actions by using blockly interface under the Custom Attributes section in the Public section.
Custom AVP
About Custom AVP
Note:
The Diameter messages listed are examples only. There are many messages associated with Diameter.You can create policy conditions to evaluate the presence of both standard (base) and third-party AVPs in Diameter messages or group AVPs during policy execution. A policy condition can check for the presence of both standard and third-party AVPs in incoming Diameter messages and evaluate their values. A policy action can use standard and third-party AVPs for routing, authentication, authorization, and accounting.
Standard AVPs can be included in third-party AVP conditions and actions. To include a standard (base) AVP in a nonstandard application message, or to use a pre-standard AVP as a standard AVP, define it as a custom AVP.
Charging-Rule-Install ::= < AVP Header: 1001 >
*[ Charging-Rule-Definition ]
*[ Charging-Rule-Name ]
*[ Charging-Rule-Base-Name ]
[ Bearer-Identifier ]
[ Rule-Activation-Time ]
[ Rule-Deactivation-Time ]
[ Resource-Allocation-Notification ]
[ Charging-Correlation-Indicator ]
*[ customAVP ]A Set or Get SPR user attribute value can be set to the defined third-party AVP in Diameter messages. You can also set or remove defined third-party AVPs during the execution point.
name:vendorIdFor example:
- Condition
where the request AVP NEW_AVP3:555 value is numerically equal to 2012- Parameters
- The AVP name and vendor ID. In the example, the vendor ID is 555.
- Description
- A well-defined AVP custom name is referred to if the vendor ID is not specified.
When entering and sending a new third-party AVP definition to an MPE or MRA device, the definition must include the AVP name, code, vendor ID, data type, and an optional AVP flag.
Validation of the AVP code, Name, and vendor ID prohibits a user from overwriting the existing base AVPs.
- Routing
- Authentication
- Authorization
- Accounting
Configuring Custom AVP
- From the navigation menu, click .
The Custom AVP screen appears.
Note:
Click Export to download the available listings to your system. - Click Add.
The Create Custom AVP page opens.
- Enter information as appropriate:
- AVP Name (required) — The name you assign to the AVP.
The name can only contain the characters A–Z, a–z, 0–9, period (.), hyphen (-), and underline (_). The maximum length is 255 characters.
- Description — Free-form text that identifies the AVP. Enter up to 250 characters.
- AVP Code (required) — A unique numeric value assigned to the new AVP.
- Vendor — Select a vendor from the vendor list. To add a vendor to the list, see Custom Vendor.
- Mandatory Flag (optional) —
- Protect Flag (optional) — When checked, specifies the protected AVP values.
- May Encrypt Flag — The AVP is encrypted if the checkbox is specified.
- Vendor Specific Flag — The AVP is vendor specific if the
checkbox is specified.
Note:
This box is checked automatically if the value of the vendor ID is not 0. - AVP Type (required) — Select the data type from the list:
- address
- enumerated
- float32
- float64
- grouped
- id
- int32
- int64
- ipFilterRule
- octetString
- time
- uint32
- uint64
- uri
- utf8String
- Parent AVP — If the AVP is a
member of a grouped AVP, then the parent AVP must be specified.
Select one of the following from the list:
- ADC-Rule-Definition:10415
- ADC-Rule-Install:10415
- ADC-Rule-Remove:10415
- ADC-Rule-Report:10415
- AF-Correlation-Information:10415
- Acceptable-Service-Info:10415
- Access-Network-Charging-Identifier-Gx:10415
- Access-Network-Charging-Identifier:10415
- Access-Network-Physical-Access-ID:10415
- Allocation-Retention-Priority:10415
- Application-Detection-Information:10415
- CC-Money
- Charging-Information:10415
- Charging-Rule-Definition-3GPP2:5535
- Charging-Rule-Definition:10415
- Charging-Rule-Event-Cisco:9
- Charging-Rule-Event-Trigger-Cisco:9
- Charging-Rule-Install-3GPP2:5535
- Charging-Rule-Install:10415
- Charging-Rule-Remove:10415
- Charging-Rule-Report-3GPP2:5535
- Charging-Rule-Report:10415
- Codec-Data-Tmp:10415
- Codec-Data:10415
- Cost-Information
- Default-EPS-Bearer-Qos:10415
- E2E-Sequence
- Envelope:10415
- Event-Report-Indication:10415
- Explicit-Route-Record:21274
- Explicit-Route:21274
- Failed-AVP
- Final-Unit-Indication
- Flow-Description-Info:5535
- Flow-Description:10415
- Flow-Grouping:10415
- Flow-Info:5535
- Flow-Information:10415
- Flow:10415
- G-S-U-Pool-Reference
- Granted-Qos:5535
- Granted-Service-Unit
- Juniper-Discovery-Descriptor:2636
- Juniper-Provisioning-Descriptor:2636
- LI-Indicator-Gx:12951
- LI-TargetMFAddr:12951
- Media-Component-Description:10415
- Media-Sub-Component:10415
- Multiple-Services-Credit-Control
- Offline-Charging:10415
- PCEF-Forwarding-Info:971
- PCEF-Info:971
- PS-Furnish-Charging-Information:10415
- PS-information:10415
- Packet-Filter-Information:10415
- Qos-Information-3GPP2:5535
- Qos-Information:10415
- Qos-Rule-Install:10415
- Qos-Rule-Definition:10415
- Qos-Rule-Remove:10415
- Qos-Rule-Report:10415
- Reachable-Peer:21274
- Redirect-Information:10415
- Redirect-Server
- Requested-Qos:5535
- Requested-Service-Unit
- Service-Information:10415
- Service-Parameter-Info
- Siemens-DL-SDP-Data:4329
- Siemens-UL-SDP-Data:4329
- Subscription Id
- Subscription-Id-3GPP:10415
- Supported-Features:10415
- TDF-Information:10415
- TFT-Packet-Filter-Information:10415
- TMO-Redirect-Server-29168
- Time-Quota-Mechanism:10415
- Trigger:10415
- Tunnel-Header-Filter:10415
- Unit-Value
- Usage-Monitoring-Control:21274
- Usage-Monitoring-Information:10415
- Used-Service-Unit
- User-CSG-Information:10415
- User-Equipment-Info
- User-Location-Info-3GPP:10415
- VZW-Access-Network-Physical-Access-ID:12951
- Vendor-Specific-Application-Id
- Vzw-Trigger:12951
- AVP Name (required) — The name you assign to the AVP.
- Click Save.
- If the AVP name matches the name of a standard AVP, a confirmation message displays. Click OK to overwrite the existing AVP.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.Importing Custom AVP
To import the custom vendor:
- Click Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Custom Vendor
A custom vendor is used to define a vendor in the CNPCRF system. This dictionary includes vendor IDs and text descriptions. You can define custom vendors and add them to the dictionary.
- From the navigation menu, click .
The Custom Vendor screen appears.
Note:
Click Export to download the available listings to your system. - Click Add.
The Create Custom Vendor page opens.
- Enter information as appropriate:
- Vendor Name (required) — The
name you assign to the vendor.
The name can only contain the characters A–Z, a–z, 0–9, period (.), hyphen (-), and underline (_).
- Description — Free-form text
that identifies the vendor.
Enter up to 250 characters.
- Vendor Id — Enter the vendor
ID.
Enter a positive integer.
- Vendor Name (required) — The
name you assign to the vendor.
- Click Save.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.Importing Custom Vendor
To import the custom vendor:
- Click Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
PCF Session Management
The PCF Session Management configurations includes:
Configuring Session Rule
You can create and manage session rules from the Session Rule screen. The page provides information about the existing session rules. You can create or refresh the session rules from this page.
Note:
Only administrators can create session rules.To configure the session rules from this page:
- From the navigation menu, click .
The Session Rule screen appears with the listing of all the available rules. You can create or import new rules details from this page.
Note:
Click the Export button to download the available listings to your system. - Click
Add.
The Create Session Rule screen appears.
- On the
Create Session
Rule screen, enter values for the input fields common to all the groups
available on the screen.
The following table describes the fields:
Field Name Description Session Rule ID Specifies the Session Rule ID. Name Specifies the name assigned to the session rule. Description Free-form text that identifies the session rule. - Under the Authorized Session AMBR
group, add the AMBR details.
- Enter the applicable values in the
input fields available on the window.
The following table describes the fields:
Field Name Description Uplink Bandwidth Specifies the bandwidth in uplink. Downlink Bandwidth Specifies the bandwidth in downlink. Note:
Click Remove to cancel the changes. - Click Add to save changes.
- Enter the applicable values in the
input fields available on the window.
- Select value for Condition Data from the drop down menu.
- Select value for
Authorize Default
Qos from the drop down menu.
Note:
The drop down gets its data from the QoS Information created.Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Session Rule screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Session Rules
To import the session rules:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring Session Rule Profile
You can manage and configure the session rule profiles from this page.
To configure the profile:
- From the navigation menu, click .
The Session Rule Profile screen appears with the listing of all the available rules. You can create or import new profiles from this page.
Note:
Click Export to download the available listings to your system. - Click
Add.
The Create Session Rule Profile screen appears.
- On the
Create Session Rule
Profile screen, enter values for the input fields common to all the groups
available on the screen.
The following table describes the fields:
Field Name Description Session Rule Profile NAME Specifies the name assigned to the session rule profile. Description Free-form text that identifies the session rule profile. - Under the Authorized Session AMBR
group, add the AMBR details:
- Enter the applicable values in the
input fields available on the window.
The following table describes the fields:
Field Name Description Uplink Bandwidth Specifies the bandwidth in uplink. Downlink Bandwidth Specifies the bandwidth in downlink. Note:
Click Remove to cancel the changes. - Click Add to save changes.
- Enter the applicable values in the
input fields available on the window.
- Select value for Condition Data from the drop down menu.
- Select value for
Authorize Default
Qos from the drop down menu.
Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Session Rule Profile screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Session Rule Profiles
To import the session rule profiles:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload button.
Configuring QoS Information
You can manage, view, import, export and create the QoS Information from QoS Information screen.
Note:
Only administrators can create QoS Information data.To configure the QoS Information data:
- From the navigation menu, .
The QoS Information screen appears with the listing of all the available rules. You can create or import the QoS details from this page.
Note:
Click Export to download the available listings to your system. - Click Add.
The Create QoS Information screen appears.
- On the Create QoS Information
screen, enter values for the input fields common to all the groups available on the
screen.
The following table describes the fields:
Field Name Description Name Specifies the name assigned to the QOS information. Description Free-form text that identifies the QOS information. Default 5G QoS Identifier Identifier for the authorized QoS parameters for the service data flow. It shall be included when the QoS information decision is initially provisioned. Priority Level Unsigned integer indicating the 5QI Priority Level, within a range of 1 to 127. Average Window Represents the duration over which the guaranteed and maximum bitrate shall be calculated (NOTE). Max DataBurstVol Denotes the largest amount of data that is required to be transferred within a period of 5GAN PDB (NOTE). - Add arp details in fields listed under ARP group.:
- Enter the applicable values in the
input fields available on the window.
The following table describes the fields:
Field Name Description Priority Level Unsigned integer indicating the ARP Priority Level, within the range 1 to 15. Preemption Capability Defines whether a service data flow may get resources that were already assigned to another service data flow with a lower priority level. Possible values are: - NOT_PREEMPT : Shall not trigger pre-emption.
- MAY_PREEMPT : May trigger pre-emption.
Preemption Vulnerability Defines whether a service data flow may lose the resources assigned to it in order to admit a service data flow with higher priority level. Possible values are: - NOT_PREEMPTABLE : Shall not be pre-empted.
- PREEMPTABLE : May be pre-empted.
Note:
Click the Remove button to cancel the changes. - Click the ADD button to add the
changes.
Note:
Click Cancel to cancel the configuration.
- Enter the applicable values in the
input fields available on the window.
- Click Save.
The value gets listed on the QoS Information screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the QoS Information
To import the session rules:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload button.
Configuring PCC Rule
You can create and manage PCC Rule from the PCC Rule screen. The page provides information about the existing rules. You can create or refresh the PCC rules from this page.
Note:
Only administrators can create PCC rules.To configure the rule:
- From the navigation menu, click .
The PCC Rule screen appears with the listing of all the available rules. You can create or import new rules details from this page.
Note:
Click Export to download the available listings to your system. - Click
Add.
The Create PCC Rule screen appears.
- On the
Create PCC Rule
screen, enter values for the input fields common to all the groups available on
the screen.
The following table describes the fields:
Field Name Description PCC Rule Id Specifies the PCC Rule ID. Name Specifies the name assigned to the PCC rule. Description Free-form text that identifies the PCC rule. Type Select the required type. Possible Values are: - Expand the
Flow Infos group
to add the Flow information:
- Click the
Add icon
displayed in the window.
The Add Flow Infos appears.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Name
Indicates the name for the flow. Flow Description
Indicates the details about flow. Enter a description for the flow.
Pack Filt Id
An identifier of packet filter. Packet Filter Usage
The packet shall be sent to the UE. The default value "FALSE" shall apply, if the attribute is not present and has not been supplied previously. Tos Traffic Class
Contains the Ipv4 Type-of-Service and mask field or the Ipv6 Traffic-Class field and mask field. Spi The security parameter index of the IPSec packet. Flow Label
The Ipv6 flow label header field. Flow Direction
Indicates the flow direction. Select from the following options:
- DOWNLINK
- UPLINK
- BIDIRECTIONAL
- UNSPECIFIED
Ethernet Flow Description Dest Mac Address
A string indicating MAC address. Enter a valid MAC address. For example, 3D-F2-C9-A6-B3-4F Ethernet Type
A two-octet string that represents the Ethertype, in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the ethType shall appear first in the string, and the character representing the 4 least significant bits of the ethType shall appear last in the string.
Flow Description
Indicates the details about flow. Enter a description for the flow. Flow Direction
Indicates the flow direction. Select from the following options:
- DOWNLINK
- UPLINK
- BIDIRECTIONAL
- UNSPECIFIED
Source Mac Address
Enter a MAC Address. For example, 3D-F2-C9-A6-B3-4F Vlan Tags
Customer-VLAN and/or Service-VLAN tags containing the VID, PCP/DEI fields. Each field is encoded as a two-octet string in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the VID or PCF/DEI field shall appear first in the string, and the character representing the 4 least significant bits of the VID or PCF/DEI field shall appear last in the string.
- Click
Add under the
Ethernet Flow
Description group name to expand the group.
The screen displays the available input fields. Enter the applicable values in the input fields.
The following table describes the fields:
Field Name Description Dest Mac Address
A string indicating MAC address. Enter a valid MAC address. For example, 3D-F2-C9-A6-B3-4F Ethernet Type
A two-octet string that represents the Ethertype, in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the ethType shall appear first in the string, and the character representing the 4 least significant bits of the ethType shall appear last in the string.
Flow Description
Indicates the details about flow. Enter a description for the flow. Flow Direction
Indicates the flow direction. Select from the following options:
- DOWNLINK
- UPLINK
- BIDIRECTIONAL
- UNSPECIFIED
Source Mac Address
Enter a MAC Address. For example, 3D-F2-C9-A6-B3-4F Vlan Tags
Customer-VLAN and/or Service-VLAN tags containing the VID, PCP/DEI fields. Each field is encoded as a two-octet string in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the VID or PCF/DEI field shall appear first in the string, and the character representing the 4 least significant bits of the VID or PCF/DEI field shall appear last in the string.
Note:
Click Remove to cancel the changes. - Click Save on the Add Flow Infos
window, under the Flow
Infos group.
The value gets listed on the Create PCC Rule screen.
- Under the
Flow Infos
group, enter values for the rest of the input fields:
Field Name Description App Id
A reference to the application detection filter configured at the UPF. Content Version
Indicates the content version of the PCC rule. Precedence
Determines the order in which this PCC rule is applied relative to other PCC rules within the same PDU session. It shall be included if the "flowInfos" attribute is included or may be included if the "appId" attribute is included when the PCF initially provisions the PCC rule. AF Signalling Protocol
Indicates the protocol used for signalling between the UE and the AF. The default value "NO_INFORMATION" shall apply, if the attribute is not present and has not been supplied previously. Application Relocation
Indication of application relocation possibility. The default value "NO_INFORMATION" shall apply, if the attribute is not present and has not been supplied previously. Qos Data
A reference to the QoSData policy type decision type. Traffic Control Data
A reference to the TrafficControlData policy decision type. Charging Data
A reference to the ChargingData policy decision type. Usage Monitoring Data
A reference to UsageMonitoringData policy decision type. Condition Data
A reference to the condition data.
- Click the
Add icon
displayed in the window.
- Click Save.
The value gets listed on the PCC Rule screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the PCC Rules
To import the session rules:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring PCC Rule Profile
You can create and manage PCC Rule Profile from the PCC Rule Profile screen. The page provides information about the existing profiles. You can create or refresh the profiles from this page.
Note:
Only administrators can create PCC Rule Profile.To configure the PCC Rule Profile:
- From the navigation menu, click .
The PCC Rule Profile screen appears with the listing of all the available rules. You can create or import new profile details from this page.
Note:
Click the Export button to download the available listings to your system. - Click
Add.
The Create PCC Rule Profile screen appears.
- On the
Create PCC Rule
Profile screen, enter values for the input fields common to all the groups
available on the screen.
The following table describes the fields:
Field Name Description Name Specifies the name assigned to the PCC rule profile. Description Free-form text that identifies the PCC rule profile. Type Select the required type. Possible Values are: - Predefined PCC Rule
- Dynamic PCC Rule
If you have selected Dynamic PCC Rule, then go to Step 4 else, go to Step 5.
- Expand the
Flow Infos group
to add the Flow information:
- Click the
Add icon
displayed in the window.
The Add Flow Infos appears.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Name
Indicates the name for the flow. Flow Description
Indicates the details about flow. Enter a description for the flow.
Pack Filt Id
An identifier of packet filter. Packet Filter Usage
The packet shall be sent to the UE. The default value "FALSE" shall apply, if the attribute is not present and has not been supplied previously. Tos Traffic Class
Contains the Ipv4 Type-of-Service and mask field or the Ipv6 Traffic-Class field and mask field. Spi The security parameter index of the IPSec packet. Flow Label
The Ipv6 flow label header field. Flow Direction
Indicates the flow direction. Select from the following options:
- DOWNLINK
- UPLINK
- BIDIRECTIONAL
- UNSPECIFIED
Ethernet Flow Description Dest Mac Address
A string indicating MAC address. Enter a valid MAC address. For example, 3D-F2-C9-A6-B3-4F Ethernet Type
A two-octet string that represents the Ethertype, in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the ethType shall appear first in the string, and the character representing the 4 least significant bits of the ethType shall appear last in the string.
Flow Description
Indicates the details about flow. Enter a description for the flow. Flow Direction
Indicates the flow direction. Select from the following options:
- DOWNLINK
- UPLINK
- BIDIRECTIONAL
- UNSPECIFIED
Source Mac Address
Enter a MAC Address. For example, 3D-F2-C9-A6-B3-4F Vlan Tags
Customer-VLAN and/or Service-VLAN tags containing the VID, PCP/DEI fields. Each field is encoded as a two-octet string in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the VID or PCF/DEI field shall appear first in the string, and the character representing the 4 least significant bits of the VID or PCF/DEI field shall appear last in the string.
- Click
Add under the
Ethernet Flow
Description group name to expand the group.
The screen displays the available input fields. Enter the applicable values in the input fields.
The following table describes the fields:
Field Name Description Dest Mac Address
A string indicating MAC address. Enter a valid MAC address. For example, 3D-F2-C9-A6-B3-4F Ethernet Type
A two-octet string that represents the Ethertype, in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the ethType shall appear first in the string, and the character representing the 4 least significant bits of the ethType shall appear last in the string.
Flow Description
Indicates the details about flow. Enter a description for the flow. Flow Direction
Indicates the flow direction. Select from the following options:
- DOWNLINK
- UPLINK
- BIDIRECTIONAL
- UNSPECIFIED
Source Mac Address
Enter a MAC Address. For example, 3D-F2-C9-A6-B3-4F Vlan Tags
Customer-VLAN and/or Service-VLAN tags containing the VID, PCP/DEI fields. Each field is encoded as a two-octet string in hexadecimal representation. Each character in the string shall take a value of "0" to "9" or "A" to "F" and shall represent 4 bits. The most significant character representing the 4 most significant bits of the VID or PCF/DEI field shall appear first in the string, and the character representing the 4 least significant bits of the VID or PCF/DEI field shall appear last in the string.
Note:
Click Remove to cancel the changes. - Click
Save on the
Add Flow
Infos window, under the
Flow Infos
group.
The value gets listed on the Create PCC Rule screen
- Under the
Flow Infos
group, enter values for the rest of the input fields:
Field Name Description App Id
A reference to the application detection filter configured at the UPF. Content Version
Indicates the content version of the PCC rule. Precedence
Determines the order in which this PCC rule is applied relative to other PCC rules within the same PDU session. It shall be included if the "flowInfos" attribute is included or may be included if the "appId" attribute is included when the PCF initially provisions the PCC rule. AF Signalling Protocol
Indicates the protocol used for signalling between the UE and the AF. The default value "NO_INFORMATION" shall apply, if the attribute is not present and has not been supplied previously. Application Relocation
Indication of application relocation possibility. The default value "NO_INFORMATION" shall apply, if the attribute is not present and has not been supplied previously. Qos Data
A reference to the QoSData policy type decision type. Traffic Control Data
A reference to the TrafficControlData policy decision type. Charging Data:
A reference to the ChargingData policy decision type. Usage Monitoring Data
A reference to UsageMonitoringData policy decision type. Condition Data
A reference to the condition data.
- Click the
Add icon
displayed in the window.
- Click Save.
The value gets listed on the PCC Rule Profile screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the PCC Rule Profiles
To import the session rules:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring QoS Data
You can create and manage QoS Data from the QoS Data screen. The page provides information about the existing QoS Data. You can create or refresh the QoS Data from this page.
Note:
Only administrators can create QoS Data.To configure the QoS Data:
- From the navigation menu, click .
The QoS Data screen appears with the listing of all the available rules. You can create or import new rules details from this page.
Note:
Click Export to download the available listings to your system. - Click
Add.
The Create Qos Data screen appears.
- On the Create QoS Data screen, enter
values for the input fields common to all the groups available on the screen.
The following table describes the fields:
Field Name Description QoS ID Specifies the QoS ID. Name
Specifies the name assigned to the QOS data. Description
Free-form text that identifies the QOS data. Default 5G QoS Identifier
Identifier for the authorized QoS parameters for the service data flow. It shall be included when the QoS data decision is initially provisioned. Maximum Bit Rate UL
Indicates the max bandwidth in uplink. Maximum Bit Rate DL
Indicates the max bandwidth in downlink. Guaranteed Bit Rate UL
Indicates the guaranteed bandwidth in uplink Guaranteed Bit Rate DL
Indicates the guaranteed bandwidth in downlink. QoS Notification Control
Reflective QoS
Indicates whether the QoS information is reflective for the corresponding service data flow. Default value is "FALSE", if not present and has not been supplied previously.
Sharing Key Ul
Indicates, by containing the same value, what PCC rules may share resource in uplink direction. Sharing Key Dl
Indicates, by containing the same value, what PCC rules may share resource in downlink direction. Priority Level
Defines the relative importance of a resource request. Averaging Window
Represents the duration over which the guaranteed and maximum bitrate shall be calculated (NOTE). Maximum Data Burst Volume
Denotes the largest amount of data that is required to be transferred within a period of 5GAN PDB (NOTE). Maximum Packet Loss Rate Dl
Indicates the uplink maximum rate for lost packets that can be tolerated for the service data flow. Max Packet Loss Rate Ul
Indicates the uplink maximum rate for lost packets that can be tolerated for the service data flow. Default QoS Flow Indication
Indicates that the dynamic PCC rule shall always have its binding with the QoS Flow associated with the default QoS rule. Default value is "FALSE", if not present and has not been supplied previously.
- Add the arp details under the ARP group.
- Enter the applicable values in the
input fields available on the window.
The following table describes the fields:
Field Name Description Priority Level Defines the relative importance of a resource request. Preemption Capability Defines whether a service data flow may get resources that were already assigned to another service data flow with a lower priority level. Possible values are: - NOT_PREEMPT
- MAY_PREEMPT
Preemption Vulnerability Defines whether a service data flow may lose the resources assigned to it in order to admit a service data flow with higher priority level. Possible values are: - NOT_PREEMPTABLE
- PREEMPTABLE
Note:
Click Cancel to cancel the configuration.
- Enter the applicable values in the
input fields available on the window.
- Click Save.
The value gets listed on the QoS Data screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the QoS Data
To import the QoS Data:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload button.
Configuring Charging Data
You can manage, view, import, export and create the Charging Data from Charging Data screen.
Note:
Only administrators can create Charging data.To configure the service:
- From the navigation menu, click .
The Charging Data screen appears with the listing of all the available rules. You can create or import new data from this page.
Note:
Click Export to download the available listings to your system. - Click
Create.
The Create Charging Data screen appears.
- On the
Create Charging
Data screen, enter values for the input fields common to all the groups
available on the screen.
The following table describes the fields:
Field Name Description Charging id Specifies the charging id. Name
The name of the Charging Data. Description
The description of the Charging Data. Metering Method
The following options are available
- DURATION
- VOLUME
- DURATION_VOLUME
- EVENT
Defines what parameters shall be metered for offline charging. If the attribute is not present but it has been supplied previously, the previous information remains valid. If the attribute is not present and it has not been supplied previously or the attribute has been supplied previously but the attribute is set to NULL, the metering method preconfigured at the SMF is applicable as default metering method.
Offline
Indicates the offline charging is applicable to the PDU session or PCC rule. The default value "FALSE" shall apply, if the attribute is not present and has not been supplied previously. (NOTE)
Online
Indicates the online charging is applicable to the PDU session or PCC rule. The default value "FALSE" shall apply, if the attribute is not present and has not been supplied previously. (NOTE)
Rating Group
The charging key for the PCC rule used for rating purposes. Reporting Level
The following options are available:
- SER_ID_LEVEL
- RAT_GR_LEVEL
- SPON_CON_LEVEL
Defines on what level the SMF reports the usage for the related PCC rule. If the attribute is not present but it has been supplied previously, the previous information remains valid. If the attribute is not present and it has not been supplied previously or the attribute has been supplied previously but it is set to NULL, the reporting level preconfigured at the SMF is applicable as default reporting level.
Service Id
Indicates the identifier of the service or service component the service data flow in a PCC rule relates to. Sponsor Id
Indicates the sponsor identity. App Svc Prov Id
Indicates the application service provider identity. Af Charging Identifier
Univocally identifies the charging control policy data within a PDU session. Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Charging Data screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Charging Data
To import the session rules:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring Usage Monitoring Data
You can create and manage Usage Monitoring Data from this page. The page provides information about the existing Usage Monitoring Data as well.
Note:
Only administrators can create Usage Monitoring Data.To configure the service:
- From the navigation menu, click .
The Usage Monitoring Data screen appears with the listing of all the available rules. You can create or import new rules details from this page.
Note:
Click Export to download the available listings to your system. - Click
Add.
The Create Usage Monitoring Data screen appears.
- On the
Create Usage
Monitoring Data screen, enter values for the input fields common to all the
groups available on the screen.
The following table describes the fields:
Field Name Description Usage Monitoring id Specifies the usage monitoring id. Name
The name of the Usage Monitoring Data.
Description
The description of the Usage Monitoring Data. Volume Threshold
Indicates a volume threshold. Volume Threshold Uplink
Indicates a volume threshold in uplink. Volume Threshold Downlink
Indicates a volume threshold in downlink. Time Threshold
Indicates a time threshold. Monitoring Time
Indicates the time at which the UP function is expected to reapply the next thresholds (e.g. nextVolThreshold). Next Vol Threshold
Indicates a volume threshold after the Monitoring. Next Vol Threshold Uplink
Indicates a volume threshold in uplink after the Monitoring Time. Next Vol Threshold Downlink
Indicates a volume threshold in downlink after the Monitoring Time. Next Time Threshold
Indicates a time threshold after the Monitoring. Inactivity Time
Defines the period of time after which the time measurement shall stop, if no packets are received. ex Usage PccRule Ids
Contains the PCC rule identifier(s) which corresponding service data flow(s) shall be excluded from PDU Session usage monitoring. It is only included in the UsageMonitoringData instance for session level usage monitoring.
Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Usage Monitoring Data screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Usage Monitoring Data
To import the Usage Monitoring Data:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring Traffic Control Data
You can manage, view, import, export and create the Traffic Control Data from Traffic Control Data screen.
Note:
Only administrators can create traffic control data.To configure the traffic control data:
- From the navigation menu, click .
The Traffic Control Data screen appears with the listing of all the available rules. You can create or import new data from this page.
Note:
Click Export to download the available listings to your system. - Click
Add.
The Create Traffic Control Data screen appears.
- On the Create Traffic Control Data
screen, enter values for the input fields common to all the groups available on the
screen.
The following table describes the fields:
Field Name Description Traffic Control id Specifies the traffic control policy data id. Name
The name of the Traffic Control policy data. Description
The description of the Traffic Control policy data. Flow Status
The following options are available:- ENABLED-UPLINK
- ENABLED-DOWNLINK
- ENABLED
- DISABLED
- REMOVED
Enum determining what action to perform on traffic.
Possible values are: [enable, disable, enable_uplink, enable_downlink] . The default value "ENABLED" shall apply, if the attribute is not present and has not been supplied previously.
- Enter values of the available input fields under Redirect Information group.
The following table describes the fields:
Field Name Description Redirect Enabled Indicates the redirect is enabled. Redirect Address Type This string provides forward-compatibility with future extensions to the enumeration but is not used to encode content defined in the present version of this API. Redirect Server Address Indicates the address of the redirect server. Mute Notification Indicates whether application's start or stop notification is to be muted. The default value "FALSE" shall apply, if the attribute is not present and has not been supplied previously.
Traffic Steering Pol Id Dl Reference to a preconfigured traffic steering policy for downlink traffic at the SMF. Traffic Steering Pol Id Ul Reference to a preconfigured traffic steering policy for uplink traffic at the SMF.
- Expand the
Route To Locs
group.
The expanded window displays the available routes. To create new routes:
- Click
Add in the
window.
The Add Route To Locs window appears on the screen.
- Enter the applicable
values in the input fields available on the window.
The following table describes the fields:
Field Name Description Dnai Identifies the location of the application. Ipv4 Addr Ipv4 address of the tunnel end point in the data network. Ipv6 Addr Ipv6 address of the tunnel end point in the data network. Port Number UDP port number of the tunnel end point in the data network. Route Profile Id Identifies the routing profile Id. Note:
Click Cancel to cancel the changes. - Click
Save.
The value gets listed in the Tracking Area List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click
Add in the
window.
- Enter values of the available input fields the Up Path Chg Event group.
The following table describes the fields:
Field Name Description Notification Uri Defines the notification Uri sent by the SMF. Notification Correlation Id It is used to set the value of Notification Correlation ID in the notification sent by the SMF.
Dnai Change Type The following options are available:
- EARLY
- EARLY_LATE
- LATE
Possible values are
EARLY: Early notification of UP path reconfiguration. -
EARLY_LATE: Early and late notification of UP path reconfiguration. This value shall only be present in the subscription to the DNAI change event.
LATE: Late notification of UP path reconfiguration. This string provides forwardcompatibility with future extensions to the enumeration but is not used to encode content defined in the present version of this API.
- Click Save.
The value gets listed on the Traffic Control Data screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Traffic Control Data
To import the session rules:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring Condition Data
You can create and manage condition data from the Condition Data screen. The page provides information about the existing Condition Data. You can create or refresh the Condition Data from this page.
Note:
Only administrators can create Condition Data.To configure the service:
- From the navigation menu, click .
The Condition Data screen appears with the listing of all the available rules. You can create or import new data from this page.
Note:
Click the Export button to download the available listings to your system. - Click
Add.
The Create Condition Data screen appears.
- On the
Create Condition
Data screen, enter values for the input fields common to all the groups
available on the screen.
The following table describes the fields:
Field Name Description Condition id Specifies the condition data policy data id. Name
The name of the Condition Data policy data. Description
The description of the Condition Data policy data. Activation Time
The time when the decision data shall be activated. Deactivation Time
The time when the decision data shall be deactivated. Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Condition Data screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Condition Data
To import the Condition Datas:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
PCF Access and Mobility
You can configure the PCF Access and Mobility policy services from this page.
The PCF Access and Mobility configuration includes Managing Service Area Restriction.
Configuring Service Area Restriction
You can create and manage service area restrictions from the Service Area Restriction screen. The page provides information about the existing Service Area Restrictions as well.
Note:
Only administrators can create Service Area Restrictions.To configure the service:
- From the navigation menu, click .
The Service Area Restriction screen appears with the listing of all the available rules. You can create or import new data from this page.
Note:
Click Export to download the available listings to your system. - Click
Create.
The Create Service Area Restriction screen appears.
- On the
Create Service Area
Restriction screen, enter values for the input fields common to all the
groups available on the screen.
The following table describes the fields:
Field Name Description Name
Specifies name of the service area restriction. Description
Specifies description of the service area restriction. Restriction Type
Specifies the restriction type. Possible values are: - ALLOWED_AREAS
- NOT_ALLOWED_AREAS
- To create new area details under the
Area group:
- Click the Add button displayed
in the window.
The Add Areas window appears on the screen.
- Enter the applicable values in the
input fields available on the window.
The following table describes the fields:
Field Name Description Tacs Specifies Type Allocation Codes. A decimal number between 0 and 65535. This fields is present if and only if Area Codes is absent. Area Codes Specifies area codes. This fields is present if and only if Tacs is absent. - Click on the Save button.
The value gets listed in the Tracking Area List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click the Add button displayed
in the window.
- Enter value of the
Max Number of
TAs input field.
Note:
Click Cancel to cancel the configuration. - Click Save.
The value gets listed on the Service Area Restriction screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the Service Area Restrictions
To import the Service Area Restrictions:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
PCF UE Policy
You can configure the PCF UE Policy from this page.
The PCF UE Policy configurations includes:
Configuring URSP Rule
You can create and manage URSP Rules from the URSP Rule screen. The page provides information about the existing URSP Rules. You can create or refresh the URSP Rules from this page.
Note:
Only administrators can create URSP Rules.To configure the URSP Rules:
- From the navigation menu, click .
The URSP Rule screen appears with the listing of all the available reports. You can create or import new rules from this page.
Note:
Click the Export button to download the available reports to your system. - Click
Add.
The Create URSP Rule screen appears.
- On the
Create URSP Rule
screen, enter values for the input fields common to all the groups available on
the screen. .
The following table describes the fields:
Field Name Description Name Name of the URSP rule. Precedence Precedence value of the URSP rule. - Under the Traffic Descriptor group,
all available descriptor types are displayed.
To create new types:
- Click Add displayed in
the window.
The Add Traffic Descriptor window appears on the screen.
- Select a value from the Type drop down
menu. Possible values are:
- MATCH_ALL
- OS_ID_OS_APP_ID
- IPV4_REMOTE_ADDRESS
- IPV6_REMOTE_ADDRESS
- PROTOCOL_IDENTIFIER
- SINGLE_REMOTE_PORT
- REMOTE_PORT_RANGE
- Click Save.
The value gets listed under the Traffic Descriptor group.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click Add displayed in
the window.
- The Route Selection Descriptor List group displays the available precedence.
To create new data:
- Click Add displayed in
the window.
The Add Route Selection Descriptor List window appears on the screen.
- Enter the value in the Precedence field.
- Click Add to create a
new Route Selection Descriptor Components in the Route Selection
Descriptor Components group. .
The Add Route Selection Descriptor Components window appears on the screen.
- Select a value from the Type drop down menu.
- Select a value from the SSC Mode drop down menu.
- Click Save.
The value gets listed in the Route Selection Descriptor List.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
- Click Add displayed in
the window.
- Click
Save.
The Pra details are listed on the Presence Reporting Area screen.
Note:
Click Cancel to cancel the configuration.
Importing the URSP Rule
To import the reports:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload.
Configuring UPSI
You can manage, view, import, export and create UPSI from UPSI screen.
Note:
Only administrators can create UPSI.To configure UPSI:
- From the navigation menu, click .
The UPSI screen appears with the listing of all the available rules. You can create or import new profile details from this page.
Note:
Click Export to download the available listings to your system. - Click
Add.
The Create UPSI screen appears.
- On the
Create UPSI
screen, enter values for the input fields common to all the groups available on
the screen.
The following table describes the fields:
Field Name Description Name Name of the UPSI. UPSC Defines UE Policy Section Code. Enter a number between 0 and 65,535. URSP Rules Defines URSP rules. - Enter values of the available input fields under the
PLMN group.
The following table describes the fields:
Field Name Description MCC Defines the Mobile Country Code. Enter a number between 0 and 999. MNC Defines the Mobile Network Code. Enter a number between 0 and 999. - Click Save.
The value gets listed on the UPSI screen.
Note:
Use Edit or Delete buttons available in the next column to update or delete the listing.
Importing the UPSI
To import the UPSIs:
- Click
Import.
The File Upload window appears on the screen.
- Upload the files in required format by clicking Drop Files here or click to upload button.
PCRF Core
This section describes how to use and configure PCRF Core Managed Objects.
Charging Server
Note:
Use pencil icon or trash bin icon available in the next column to edit or update the created charging server.Media Profile
Note:
Media Profiles is a function that is applicable to Cable mode only.To create a media profile:
Note:
Use pencil icon or trash bin icon available in the next column to edit or update the created media profile.Policy Management
- Session Management and Policy Authorization
- Access and Mobility Management
- UE Management
- PCRF Core
- Policy Data Source
For more information on blocks, see Oracle Communications Cloud Native Policy Design Guide. This guide has been made available on MOS.
Policy Projects
You can create and deploy a policy project using Policy Projects page. There are two possible states for the policy project, Prod and Dev. By default, Dev state is assigned to the policy project. Dev Projects will not process any traffic in PRE. Prod projects will process traffic in PRE.
- From the Policy section of the
navigation pane, click .
The Policy Projects screen appears. You can view all the created projects for each service type.
- Choose the service type and click Create to create a new
policy project.
The Create Policy Project window opens.
Note:
If the maximum limit for project is reached per service then an error message is displayed on clicking the Create button. For Example, Maximum number of projects supported in this release is 10. - Enter information as appropriate:
- Name (required) — The name you assign to the policy
project. The name can only contain the characters A–Z, a–z, 0–9, period
(.), hyphen (-), and underscore (_). The maximum length is 32
characters.
Note:
You must assign a unique name to the policy project per service type. The name is case sensitive. - Description — Free-form text that identifies the policy project. The maximum length is 255 characters.
- Name (required) — The name you assign to the policy
project. The name can only contain the characters A–Z, a–z, 0–9, period
(.), hyphen (-), and underscore (_). The maximum length is 32
characters.
- Click Save.
The policy project is created.
Note:
If needed, you can unit test the project. For more information on testing the projects, see Test Policy Projects section int the Oracle Communications Cloud Native Policy Design Guide. - You can change the state of a project. There are two possible
states in this release, Dev and Prod. These states are represented
using the buttons on the page with the Label named as Dev and
Prod. A tick mark and light green color button helps to identify the
current state of a project. Available state button will be in dark green color.
Below screenshot illustrates the different states of a
project.
 When you click on any of the button to change the state, a message
appears asking you to confirm the state change. Click Yes. The project
state will be changed.
When you click on any of the button to change the state, a message
appears asking you to confirm the state change. Click Yes. The project
state will be changed.
Note:
At any point of time there can be only one project in Prod state for a given Service. If you change the state of project to Prod and there is already a project with the Prod state for that service, the Prod state for the existing project will be automatically moved to Dev state. And, the project inDev state will be moved to Prod state. - You can view the last policy project's state with a timestamp by
default. Below screenshot is an example displaying that the project is currently
in Dev state and the last state was Prod with the Exit timestamp.

Below screenshot is an example displaying that the project is just created and is in Dev state and hence it does not have any previous state.

Below screenshot is an example displaying that you can view the full state history by clicking the Previous States link.
- You can filter the projects based on Name and Active State using the Filter.
- Click
 icon to clone the existing policy project. Select an existing policy
project and click Clone icon; the Clone Policy Project window opens. You can
enter the required information and click Save.
icon to clone the existing policy project. Select an existing policy
project and click Clone icon; the Clone Policy Project window opens. You can
enter the required information and click Save.
- Click
 icon to edit the policy project details.
icon to edit the policy project details.
- Click trash
 icon to delete the policy project. When you click on the Delete icon, a
confirmation dialog box appears asking you to confirm the deletion. After
clicking the 'Yes' button, the project and it's associated policies will be
deleted.
icon to delete the policy project. When you click on the Delete icon, a
confirmation dialog box appears asking you to confirm the deletion. After
clicking the 'Yes' button, the project and it's associated policies will be
deleted.
- Click
 icon to open a Blockly editor.
You can construct one or more policies as required using the building blocks provided in the Left Side Panel of the editor.
icon to open a Blockly editor.
You can construct one or more policies as required using the building blocks provided in the Left Side Panel of the editor.Note:
The project in Prod state is not editable you can view the policies but can't modify the project and the policies associated with that project.See Policy Design Guide for more details on the blocks. This guide has been made available on MOS.
Diameter Configurations
You can manage and view the Diameter Configurations from this page. These configurations are a part of PCF mode only for now. For converged and cnPCRF, you have to configure these configurations through Helm Config Map.
Settings
- From the navigation menu, click .
The Settings screen appears.
- Click Edit to edit the settings.
- Enter the following information:
Timer
- Reconnect Delay (sec)- Enter the time frame to delay before attempting to reconnect after a connection failure in seconds. The default is 3 seconds.
- Response Timeout (sec)- Enter the response timeout interval in seconds. The default is 5 seconds.
- Connection Timeout (sec)- Enter the connection timeout interval in seconds. The default is 3 seconds.
- WatchDog Interval (sec)- Enter the watchdog interval in seconds. The default is 6 seconds.
Transport
- Protocol - TCP/SCTP
- Click Save.
Peer Nodes
- From the navigation menu, click .
The Peer Nodes screen appears.
- Click Add to create peer node. The Create Peer Node screen appears.
- Enter the following information:
- Name- Unique Name of the peer node.
- Type- Defines which type of diameter service it should take up. The value can be Application function (af) or diameter routing agent(dra).
- Reconnect Limit (sec) -
- Initiate Connection- Set it to True to initiate a connection for this peer node.
- Port- Enter the port number. Enter a number from 0 to 65535.
- Host- Enter the host name. Enter a FQDN, ipv4 or ipv6 address available for establishing diameter transport connections to the peer node .
- Realm- Enter the realm name, that is, FQDNs to all of that computers that transact diameter traffic.
- Identity- Enter a identity to define a node in a realm.
- Click Save.
Note:
You can import and export the Peer Node configurations by clicking on Import and Export on Peer Nodes Configurations screen.
Configuring Diameter Routing Table
You can define the next hop for Cloud Native Core Policy initiated diameter requests based on Diameter application-id, Destination-Realm and Destination-Host using diameter routing table.You can configure the route entries from this page.
- From the navigation menu, click .
The Diameter Routing Table Configurations screen appears.
- Click Edit to edit the diameter routing table configurations. This enables the Add button in Diamter Routing Table group.
- Click Add. The Add Diamter Routing Table window opens.
-
- Enter the values for the following fields in the Diamter
Routing Table group:
- Priority- Defines the order of use when one or more routes have overlapping criteria. The range is 0-65535.
- Name- Unique name of the diameter routing table.
- Type- The value can be Realm or Host.
- Realms- Realms field is displayed when the Realm is selected in the Type field.
- Hosts
Hosts field is displayed when the Host is selected in the Type field.
- Application ID
Select Rx (default), Gq, Ty, Gx, Gxx, Sy, Gy, Sh, or All.
- Server IdentifierEnter a free-form text.
Note:
* (asterisk) wildcard character is allowed in Hosts, Realms, and Server Identifier fields.Click Save.
- Enter the value for the Server Identifier field in the Default Route group.
- Enter the values for the following fields in the Diamter
Routing Table group:
- Click Save.
Data Source Configurations
Cloud Native Core Policy (CNC Policy) establishes connections with data sources to retrieve information about subscribers from the database. The CNC Policy queries a data source using a key attribute that uniquely identifies a subscriber and stores the results in its cache. A data source uses this key attribute (for example, the phone or account number of the subscriber) to index the information contained in the database.
The CNC Policy supports Lightweight Directory Access Protocol (LDAP) data source. Based on the conditions implemented in PCF system, Policy Data Source (PDS) would retrieve all the relevant information from LDAP data source based on the rules configured in the system through LDAP gateway.
- ldapGatewayEnable
- policydsEnable
LDAP credentails are stored as kubernetes secret along with Authentication DN and LDAP name. You must create a kuberenetes secret to store LDAP credentials before setting a PDS as LDAP data source.
- Create a yaml file with the following
syntax:
apiVersion: v1 kind: Secret metadata: name: ldapsecret labels: type: ocpm.secret.ldap type: Opaque stringData: name: "ldap1" password: "camiant" authDn: "uid=PolicyServer,ou=vodafone,c=hu,o=vodafone"where, name is the configured LDAP server name.
password is the LDAP credential for that data source.
authDN is the authentication DN for that LDAP datsource.
Note:
For different LDAP data sources more entries can be added in above format only the key of the entry should be the ldap name specified in the CNC Policy Graphical User Interface (GUI). - Create the secret by executing the following
command:
kubectl apply -f yaml_file_name -n pcf-namespacewhere:
yaml_file_name is a name of the yaml file that is created in step 1.
pcf-namespace is the deployment namespace used by the helm command.
Data Sources
To set Policy Data Source as LDAP Data Source using CNC Policy GUI:
- Add LDAP data source. To add LDAP data source, From
the navigation menu, under Policy, then under Data
Source Configurations, click Data Sources. The Data
Sources page opens. Click Add to create a data source. On the Create Data
Source page, select LDAP in the Type drop-down list.
The following screen capture shows the example of adding LDAP data source in GUI:
In the above example, LDAP datasource with name LDAP1 is created.
- Create pds service type in PCF
system. To create pds service type, From the navigation menu, under Policy Management, click Settings . On Settings page,
click Add to create pds service type.
The following screen capture shows the example of creating pds service type in GUI:
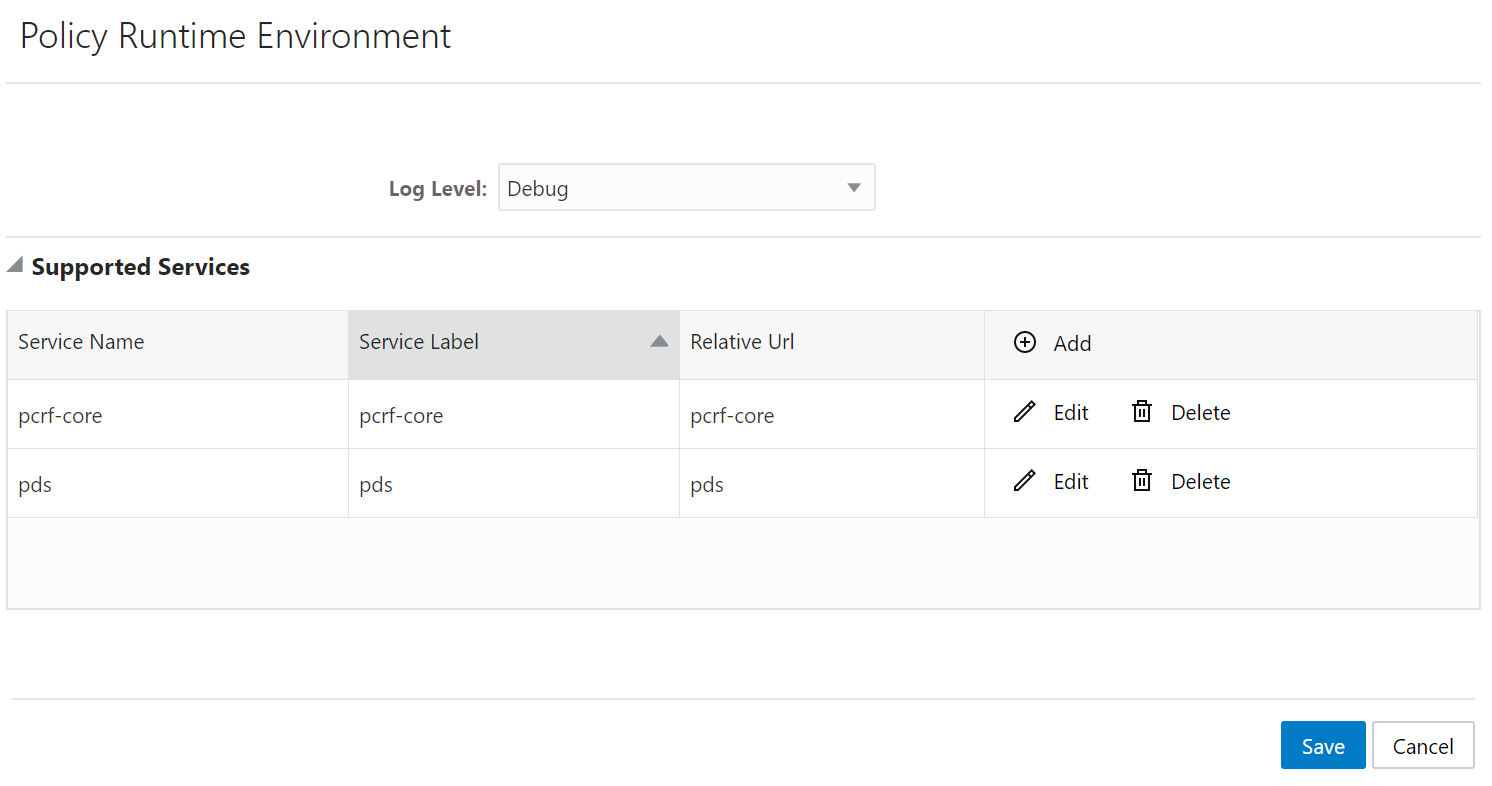 In the above example, pds service type is created.
In the above example, pds service type is created.
Note:
The service name should be entered as pds. - Create Policy Project with pds Service Type. From the
navigation menu, under Policy
Management, click Policy
Projects. On Policy Projects page, click Create to create policy
project. While creating a policy project select pds as a service type.
The following screen capture shows the example of creating policy project with pds service type in GUI:
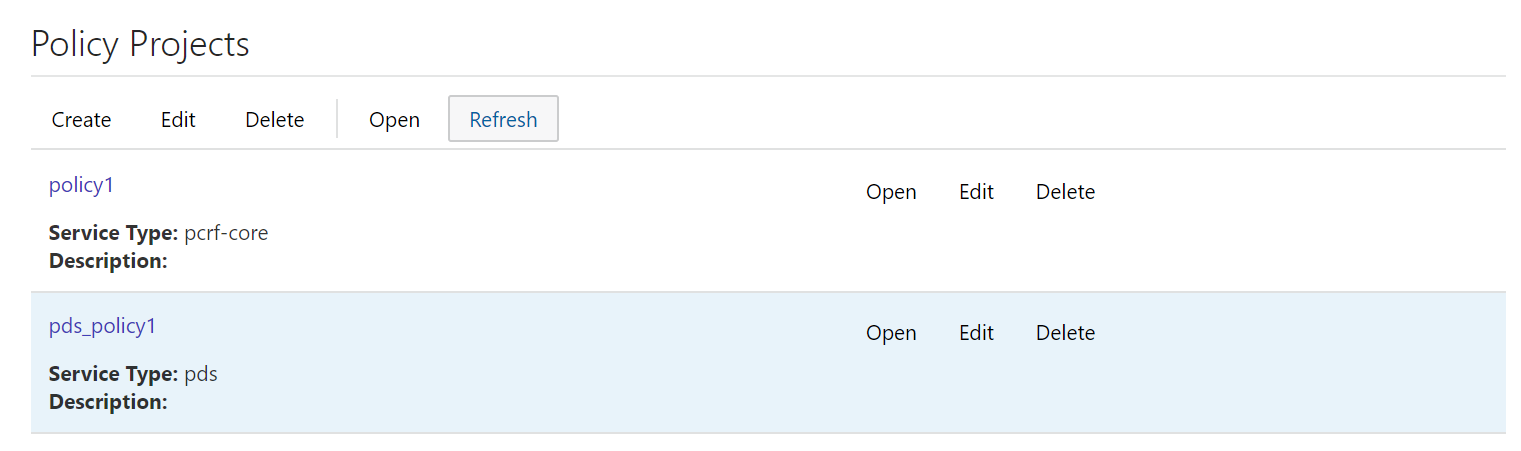 In the above example, s policy project is created with pds service
type.
In the above example, s policy project is created with pds service
type.
- Create policy action and condition in previously
created policy project. Click Open for the selected policy project and you
can see the project is a file. You can create the policy action and condition by
using the different blocks available under Conditions and Actions
under PDS.
The following screen capture shows the example of creating policy action and condition in GUI:
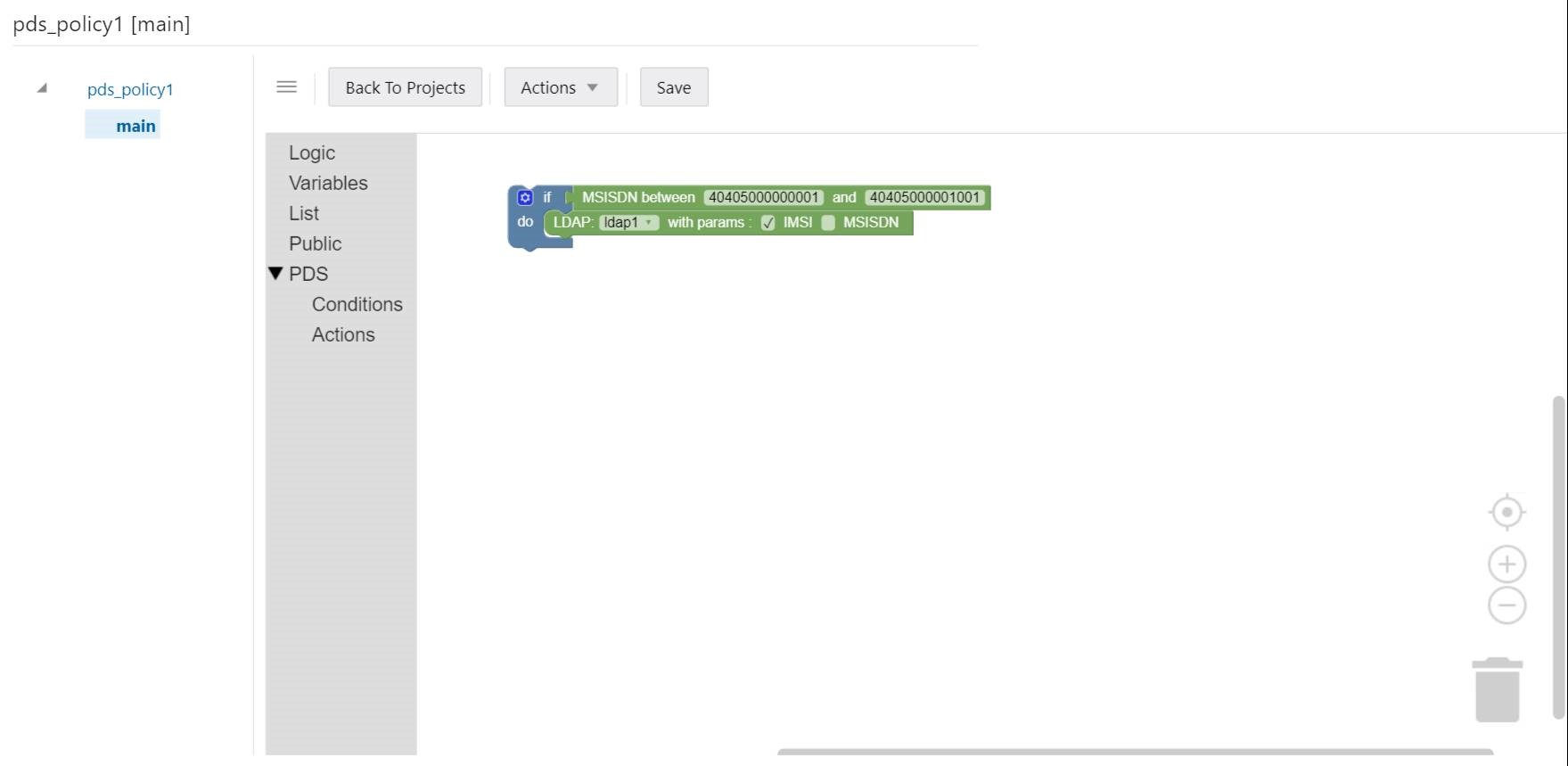
In the above example, if request received for configured IMSI ranges between 404050000000001 and 404050000000001, then PCF will forward request to PDS and PDS will forward the request to LDAP gateway to lookup user information in LDAP1.
Administration
This section describes how to perform administration tasks such as bulk import and bulk export of configurable objects into the system.
Bulk Export
Note:
In Release 1.7.1, bulk export using the GUI for Policy Project is not supported.Note:
In Release 1.7.1, bulk export for the following objects is not supported:- Data Model
- Custom Schema
- Dropdown Blocks
- Using GUI to export the policy configuration data
- Using REST APIs to export the Service Configuration data
- To export policy configuration data using GUI:
- From the navigation pane, click .
The Export All option appears on the screen.
- Click Export All.
A ZIP file, export_configurations.zip, is downloaded to your local computer.
- From the navigation pane, click .
-
To export service configuration data using REST API:
Note:
The below instructions are not needed if you are using the default configuration and can make the changes manually.Prerequisite:
In the CNC Console GUI, From the navigation menu, click Policy, then Service Configurations, and then click PCF Session Management . On the PCF Session Management screen,- Verify the format of snssai is x-y. ( for example, if the value of "snssai" is "0,000000", replace "0,000000" with "0-000000")
- Override Supported Features field should be empty. REST APIs are not compatible with this attribute in Release 1.7.1 .
Use individual REST APIs to fetch the Service Configuration data and save the file as <MO name of the topic 1.6>.json. Following table is an example for the different managed objects:GUI Options GET APIs File name Diameter Configurations→Settings /ocpm/common/v1/configuration/diameter/settings Settings 1.6.json Service Configurations→ Access and Mobility Service /ocpm/pcf/v1/configuration/service/am PCF Access and Mobility 1.6.json Service Configurations→Policy Authorization Service /ocpm/pcf/v1/configuration/service/pa PCF Policy Authorization 1.6.json Service Configurations→Session Management Service /ocpm/pcf/v1/configuration/service/sm PCF Session Management 1.6.json Service Configurations→UE Policy Service /ocpm/pcf/v1/configuration/service/ue PCF UE Policy 1.6.json Service Configurations→User Service /ocpm/pcf/v1/configuration/service/user PCF User Connector 1.6.json Global Configurations /ocpm/pcf/v1/configuration/global General Configurations pcf 1.6.json Policy Management→Policy Table /ocpm/policymanagement/v1/policytables/{serviceName} Policy Tables 1.6.json - Unzip the export_configurations.zip file (created in step 1) and save all the <MO name of the topic 1.6>.json files (created in step 2) in the unzip folder.
- Remove the public.policy.test.json from the folder, as it is not supported in Release 1.7.1 .
- Zip the export_configurations.zip file again. This file is used while importing the data. For importing the data, See Bulk Import.
- POST: /oc-cnpolicyconfiguration/v1/administration/export
- GET: /oc-cnpolicy-configuration/v1/administration/export/{exportResourceId}/status
- GET: /oc-cnpolicy-configuration/v1/administration/export/{exportResourceId}/report
- GET: /oc-cnpolicyconfiguration/v1/administration/export/{exportResource Id}/download
- IN_PROGRESS: If the export is running.
- DONE: If the export is finished. Following are the possible status
if the export is in DONE status:
- SUCCESS : If the export is successful
- FAILED : If the export is failed
- PARTIAL_SUCCESS : If the export is partially successful
For more information on Bulk Export REST APIs, see Oracle Communications Cloud Native Core Policy REST Specification Document.
Bulk Import
This section describes how to perform a bulk import of managed objects into the system.
Note:
Bulk Import using the GUI is not supported in Release 1.7.1. Use REST APIs to bulk import the data that is exported from 1.6.x release stetups. These REST APIs will do conversion and migration to sort out the incompatibility between the releases.Note:
In Release 1.7.1, bulk import for the following objects is not supported:- Data Model
- Custom Schema
- Dropdown Blocks
Importing Managed Object Files Using REST API
- POST: /oc-cnpolicy-configuration/v1/administration/import
- GET: /oc-cnpolicy-configuration/v1/administration/import/{importResourceId}/status
- GET: /oc-cnpolicy-configuration/v1/administration/import/{importResourceId}/report
- Open Swagger UI in the browser and enter http://<IP>:<Port>/swagger-ui.html in the browser.
- Since, Release 1.7.1 is a new install, leave action and managedObjects parameters as blank. Choose the release 1.6.x exported file, export_configurations.zip file in the imporFile parameter.
- Click Execute. See Bulk Export section to create the export_configurations.zip
file. Below screen capture shows how to import the exported file using
swagger:
- Access the status of the import using the
GET:/oc-cnpolicy-configuration/v1/administration/import/{importResourceId}/status
REST API. Below screen caputre shows how to access the status of the
import:
 Below are the status displayed by Bulk import:
Below are the status displayed by Bulk import:- IN_PROGRESS: If the import/export is running.
- DONE: If the import/export is finished.
Following are the possible status if the import/export is in DONE
status:
- SUCCESS : If the import/export is successful
- FAILED : If the import/export is failed
- PARTIAL_SUCCESS : If the import/export is partially successful
- Retrieve the Report of the Import Status using the GET:
/oc-cnpolicy-configuration/v1/administration/import/{importResourceId}/report
REST API. Below screen caputre shows how to retrieve the report of the import
status:
- Access the CNC Console GUI and verify all the records are imported successfully.
For more information on Bulk Import REST APIs, see Oracle Communications Cloud Native Core Policy REST Specification Document.
Importing Managed Object Files Using GUI
To import json or ZIP files:
- From the navigation pane, click .
The bulk import screen appears.
- Click Upload.
Locate the file to be imported.
- Select a processing option
to use to
Handle collisions between imported items and existing items:
- Delete all before
importing The system deletes all objects for each object type matching the
import file before importing the object type json file.
Attention: This import strategy can result in object inconsistency. For example, if you import a ZIP file that only contains traffic profiles, all the traffic profiles are deleted first. However, if existing policies depend on the existing traffic profiles, and the import file does not contain them, the policies can become invalid.
- Overwrite with imported version For each object in the import file, if the object exists in the system, the import updates the object with the configuration contained in the import file. If an object does not exist, the system adds the object to the system.
- Delete all before
importing The system deletes all objects for each object type matching the
import file before importing the object type json file.
- Click Import.
The configuration objects and their configuration settings are imported into the database. After the import is complete, the window reports the results for each json file contained in the ZIP file.
Appendix
This appendix describes the Managed Object that supports the Bulk Import/Export using RESTFul APIs.
| Managed Object | API Import | API Export | API Bulk Import | API Bulk Export |
|---|---|---|---|---|
| Session Viewer | Not Required | |||
| General Configurations | Y | Y | Y | Y |
| Service Configurations | ||||
| PCF Session Management | Y | Y | Y | Y |
| PCF Access and Mobility | Y | Y | Y | Y |
| PCF Policy Authorization | Y | Y | Y | Y |
| PCF UE Policy | Y | Y | Y | Y |
| PCF User Connector | Y | Y | Y | Y |
| PCRF Core | Y | Y | N | N |
| Audit | N | N | N | N |
| Policy Engine | N | N | N | N |
| Policy Data Configurations | ||||
| Common | ||||
| Policy Table | Y | Y | Y | Y |
| Dropdown Block | N | N | N | N |
| PCF Presence Reporting Area | Y | Y | Y | Y |
| Policy Counter Id | Y | Y | Y | Y |
| Match List | N | N | N | N |
| Subscriber Logging | Y | Y | Y | Y |
| Custom Attributes | ||||
| Custom Schema | N | N | N | N |
| Custom AVP | N | N | N | N |
| Custom Vendor | N | N | N | N |
| PCF Session Management | ||||
| Session Rule | Y | Y | Y | Y |
| Session Rule Profile | Y | Y | Y | Y |
| Qos Information | Y | Y | Y | Y |
| PCC Rule | Y | Y | Y | Y |
| PCC Rule Profile | Y | Y | Y | Y |
| QoS Data | Y | Y | Y | Y |
| Charging Data | Y | Y | Y | Y |
| Usage Monitoring Data | Y | Y | Y | Y |
| Traffic Control Data | Y | Y | Y | Y |
| Condition Data | Y | Y | Y | Y |
| PCF Access and Mobility | ||||
| Service Area Restriction | Y | Y | Y | Y |
| PCF UE Policy | ||||
| URSP Rule | Y | Y | Y | Y |
| UPSI | Y | Y | Y | Y |
| PCRF Core | Y | Y | N | N |
| Policy Management | ||||
| Policy Projects | Y | Y | Y | Y |
| Policy Library | N | N | N | N |
| Policy Tests | ||||
| Test Policy Projects | N | N | N | N |
| Data Model | N | N | N | N |
| Diameter Configurations | ||||
| Settings | Y | Y | Y | Y |
| Peer Nodes | Y | Y | Y | Y |
| Routing Table | N | N | N | N |
| Data Source Configurations | ||||
| Data Sources | Y | Y | Y | Y |
| Administration | ||||
| Import | Not Required | |||
| Export | Not Required | |||