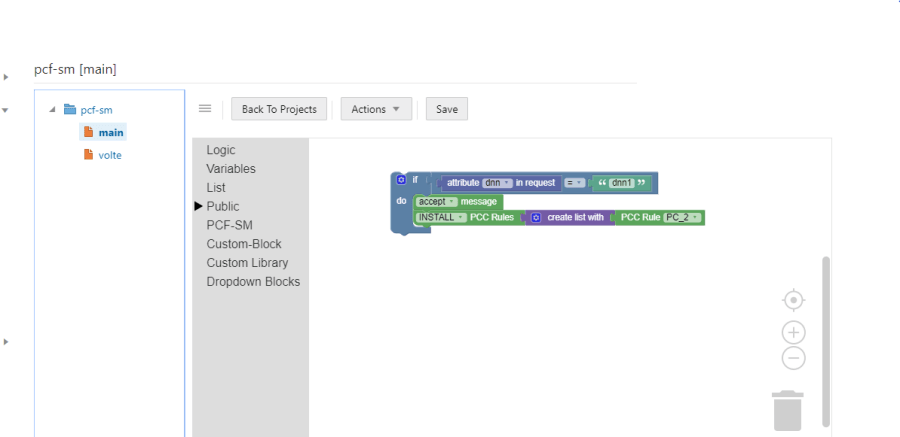
3 About Policies
You can create policies for Session Management, Access and Mobility Management, UE Management, pcrf-core and pds services. For each policy project, multiple interlocking, graphical blocks are predefined and divided into categories. You can combine these blocks in the work area to create policies.
Figure 3-1 Toolbox
Work area allows you to create, edit, save, and delete policies. A policy project execution starts with the main policy. If you want to add more policies to the execution thread, you have to refer to them from the main policy. After the blocks are added to the work area, you can modify them using the context menu available for each block. To view the context menu, right-click the respective block. For more information about the context menu options, see Context Menu Options for All Blocks.
3.1 Creating Policies
3.2 Logic Category
Table 3-1 Logic Category
| Block Icon | Block Name | Description |
|---|---|---|
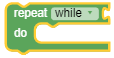 |
repeat |
Runs a code in the block body for the specified number of times. This block provides loop options. You can alter between the following options by clicking the existing option:
|
 |
for each item |
Renders loop variable values from a list, not in a numeric sequence. i indicates a variable that can be set for each item in the list. To change the value of i, or to rename or delete it, click i and choose an appropriate option. |
 |
for each index |
Loops through list provided using an index i. This loop is created to loop custom attributes list using an index value. i indicates a variable that can be set for each index. To change the value of i, or to rename or delete it, click i and choose an appropriate option. |
 |
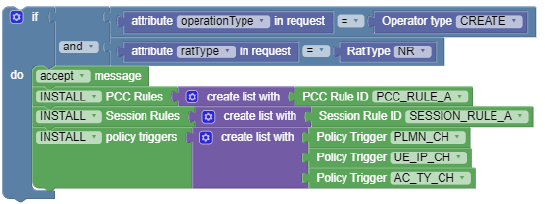
if |
Compares the values of two variables available in another block that is interconnected to it. This block provides options to add appropriate
clauses to a condition. You can click the gear icon (
|
| break out of loop |
Terminates the loop from moving from one phase or iteration to another. If you want to continue the looping from next phase or iteration, then click break out and select the continue with next iteration option from the context menu. Note: This block can be used with the following
blocks only:
|
|
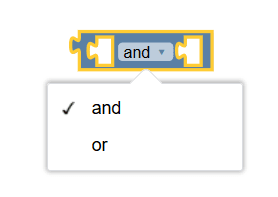 |
and/or |
Returns or produces the true value when the following options are set:
You can alter between the aforementioned options by clicking the existing option. |
| not | Converts the input value of its interconnected block to its opposite value. For example, if this block is interconnected to a block with the input values as true, then the output is false. If no input is provided to this block, then it accepts a true value by default and produces an output with value as false. | |
| inequality |
Performs a non-equal comparison between two values using the available inequality options. You can select an appropriate inequality option from the context menu by clicking the existing option. |
|
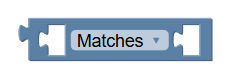 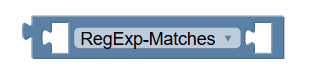 |
comparison | Performs simple wildcard matching for character * and ? when the policy writer selects Matches from the drop-down value. To perform full regular expression matching, select RegExp-Matches from the drop-down list. |
3.3 Variables Category
Table 3-2 Variables Category
| Block Icon | Block Name | Description |
|---|---|---|
| set |
Assigns a value to the variable that matches the value of the input. Also, creates a variable if it does not exist. i indicates a variable that can be set for this block. To rename or delete this variable, click i and choose an appropriate option from the context menu. |
|
| change |
Adds a number to a variable. i indicates a variable that can be set for this block. To rename or delete this variable, click i and choose an appropriate option from the context menu. |
|
| variable |
Returns or produces the value of this variable. i indicates a variable. To rename or delete this variable, click i and choose an appropriate option from the context menu. |
3.4 List Category
Table 3-3 Blocks in List Category
| Block Icon | Block Name | Description |
|---|---|---|
| create empty list | Returns or produces a list of length 0 without any data record. | |
 |
Concat list | Creates lists in loop. See Use case. |
 |
create list with |
Creates a list with any number of items. You can click the gear icon ( |
| contains |
This block takes two lists as an input and check if the contents of the list on the right hand side are present in the list on the left hand side based on the option selected in the drop-down list. Return Type : returns true/false based on match of drop-down option(any,all,none) Drop-down list Options :
|
|
| find |
It has two parameters.
Return Type : array of matched items based on drop-down list (one/any) Drop-down list options :
|
|
|
|
valuelist |
This block matches two value lists as an input and matches the contents of the list on the right hand side with the list on the left hand side based on the option selected in the drop-down list. |
3.5 Public Category
- Customer Attributes
- Policy Table
- State Variables
- Policy Counters (PCF-SM, PCF-AM, PCF-UE, PCRF)
- Operator Specific Data
- User Attributes (PCF-SM, PCF-AM, PCF-UE, PCRF)
- Subscriber Notification (PCF-SM and PCRF only)
- Analytics Data
- Usage Monitoring (PCRF only)
- Observability
Table 3-4 Blocks in Public Category
| Block Icon | Block Name | Description |
|---|---|---|
| number |
Represents a numerical value. To replace the existing value, click the value and type a new value. |
|
| string |
Represents a series of characters and numbers. To add one or a series of characters, click the square symbol embedded between quotation mark and type a character for the string. |
|
| message |
Accepts or rejects a message when interconnected with another block. You can alter between accept and reject options by clicking the existing option. |
|
| End | This block is actually a return statement. | |
| End with | This block is used to return with a value. | |
| request | ||
| response | ||
| String Operations |
It has two parameters and performs (contains, append) between two strings. Both the parameters are strings. Drop-down operators :
|
|
| Call function |
This block executes a function from the policy library with zero or more arguments. Please see the Policy Library section for help with defining functions. A function call with zero arguments can be done like this: |
|
 |
Call policy | This block is used to call a policy inside another. Click the drop-down option next to the Policy block to choose an appropriate option to set the policy. |
 |
Key Value | This block allows policy writers to create
{key:"key",value:"value"} pair.
You may use this block along with map block to create a {key:value} attribute pair. |
| Object expression | This block helps the operator to write a JavaScript
statement. This block can return a value or expression.
For Example: request.request.appSessionContextReqData.ascReqData.medComponents |
|
| Statement expression | This block helps the operator to write a JavaScript
statement. This block does not return anything.
For Example: logger.log("ALWAYS",JSON.stringify(response)) |
|
| Arithmetic |
Performs arithmetic operations on two variables. This block provides multiple arithmetic operations. Click the drop-down option to choose an appropriate option. |
|
| Date Arithmetic Helper |
Performs date arithmetic operations. This block provides multiple units of time. Click the drop-down option to choose an appropriate option. |
|
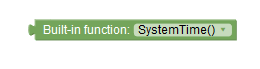 |
built-in function |
Performs built-in functions and produces outputs in predefined formats. For example, a date input can produce outputs in different formats, such as hour, minute, seconds, and so on. This block provides multiple options to set a value of the function. Click the drop-down option to choose an appropriate option. |
| Date and time format |
Produces a selected date in date and time formats. To set a date and time, click the required option and type a value. |
|
| boolean |
Sets a variable value to true or false. To set this block to true or false, click the drop-down option and choose the required option. |
|
| Exist/is null check |
Determines the value of the block at the placeholder. You can set this block to one of the following options:
To set this block to exists or is null, click the drop-down option and choose the required option. |
|
| contains in matchlist |
This block takes matchlist items in right side and any block can be attached in list in left side. There are three options:
|
|
| list includes variable |
This block can be used to find whether a variable is present in the list or not. Left hand side contains List and right hand side is variable which is to be validated for its presence or absence. There are two options:
|
|
| list items contain substring |
This block can be used to find whether all, any, or no substring is present in list items. Left hand side contains List and right hand side is variable/list which is to be validated for its presence or absence. There are three options:
|
|
 |
Convert epoch time to date format | This block can be used to convert epoch time to specified date format. |
| User Attributes | ||
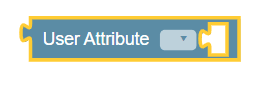 |
User Attributes | This block allows operators to access custom yaml
schemas for suscribers that were imported and tagged as "user"
during the import on the Yaml Schema screen
on CNC Console. The drop-down values in the block are auto-populated
depending on the attribute selected by the operator.
The User Attributes can be used for PCF-SM, PCF-AM, PCF-UE, and PCRF Core policy projects. |
| Customer Attributes | ||
| root | Creates attributes at the root level. | |
| default | Configures the default path of a policy. | |
| custom attributes validation | Produces the value of a selected attribute present in the path provided by the default block. | |
| set custom attributes | Creates custom attributes with the "attributeName" name at the "root" location with a value provided by the Create node block. | |
| remove custom attributes | Removes custom attributes and the attribute name from the root location. | |
| create node | Creates JSON objects. When an attribute is selected, all the fields of that attribute are populated. You must provide values to these attributes by clicking the drop-down options. | |
 |
Create map with | Creates Map object with key value pairs when combined Key Value block. |
| Policy Table | ||
| Fetch Policy Table Row | Fetches "policy Table Row" based on the match with
the key Columns values provided.
This block can be
used to configure Charging Servers. To configure a changing
server:
|
|
| Fetch Policy Table Column | Fetches "Policy Table Column value" based on the row selected in the "Fetch Policy Table Row" Block. | |
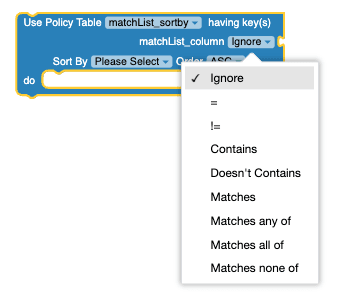 |
Use policy table having key(s) | This block returns multiple matched
rows. It supports sort option, and can be used with the following
operators:
|
| break out of loop | Terminates the loop from moving from one phase or
iteration to another.
If you want to continue the looping from next phase or iteration, then click break out and select the continue with next iteration option from the contex menu. Note: This block can only be used with the blocks listed under the Policy Table category. |
|
| State Variables | ||
  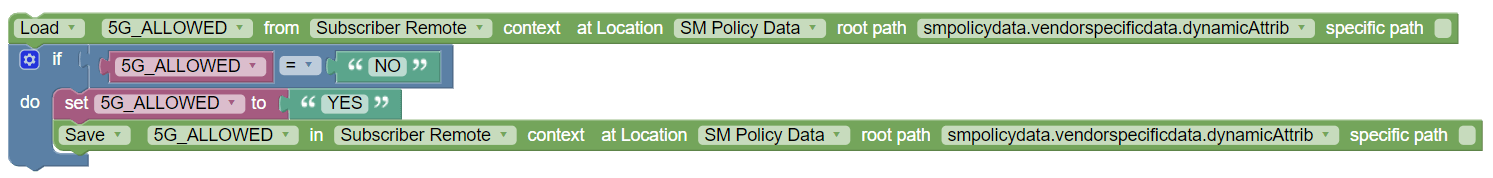 Figure 3-2 Example: Remote SSV for UE Policy 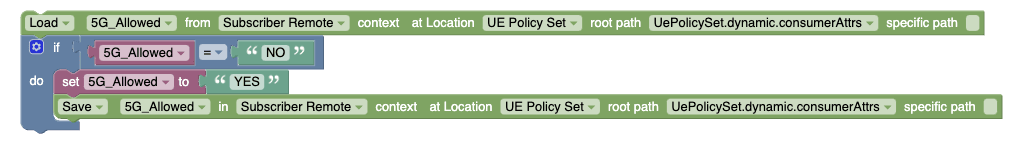 |
save/load/remove state variable(s) | When you use the context as
Policy, Session,
or Subscriber, this block can be used to save
in, load, or remove from the specified state variable
var and the value assigned to it inside
the selected context.
When you select the context as
Subscriber Remote, the block is
automatically populated with the following new fields:
Note: The specific path check box can be used to modify a particular attribute or variable in JSON. In the given policy example, SM receives SMPolicyData and SubscriberStateVariables from PDS. Then, PRE evaluates subscriberStateVariables (5G_ALLOWED), and SM_PRE sends updated information to PDS. It is
important to note that both PRE and SM-PRE refers to
Note:The context list includes the Remote option to create Subscriber Remote State Variables only for SM and UE Services. This option is not available for AM Service. |
  |
remove all variables | Removes all the variables from specified context.
The available options for context drop-down are:
|
|
Figure 3-3 Operator Specific Data  |
Operator Specific Data | Retrieves the values from the schema.yaml files uploaded on the Yaml Schema page on CNC Console for Policy. For more information on how to use Yaml Schema page, see Oracle Communications Cloud Native Core, Converged Policy User's Guide. |
| Policy Counters | ||
 |
Policy Counter Name | Retrieves policy counter names, configured using Policy Data configurations (PolicyPolicy Data ConfigurationsCommonPolicy Counter Id) on the Cloud Native Configuration Console. |
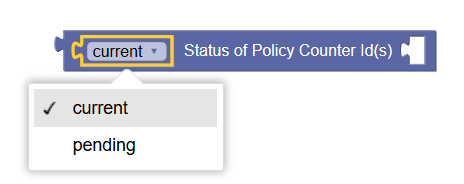 |
Status of Policy Counter ID(s) | Retrieves the current or pending status of specified policy counter IDs. Operators can specify policy counter IDs by using either Policy Counter Name block or string block. |
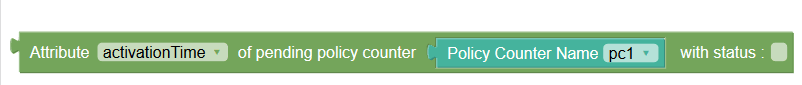 |
Attribute of pending policy counter with status | Selects activationTime attribute of pending policy counter IDs, specified by the operator. The status here is optional. Select the check box for status, and provide its value using a string block. |
 |
Policy Counter IDs | Retrieves all the available policy counter IDs. It is available only in the Public category of PCRF Core policy projects. |
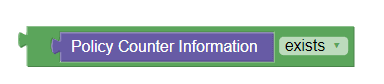 |
Policy Counter Information | Checks if Policy Counter Information exists or not. It is available only in the Public category of PCRF Core policy projects. |
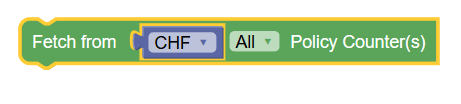 |
Fetch Policy Counters | Retrieves the status of all or specific policy
counters from the CHF or OCS through session management service. If
you want to fetch specific policy counters from CHF or OCS, use
either of the following blocks:
Note: To use this block, make sure that Enable Async CHF Query or Enable Async OCS Query button is enabled on service configurations page on CNC console. (Policy > Service Configurations > PCF Session Management) This block is available under the Public category of PCF Session Management policy projects. |
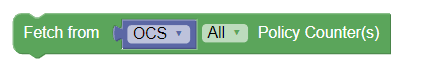 |
Fetch Policy Counters from OCS | Retrieves the status of all or specific policy
counters from the OCS. If operators wish to fetch specific policy
counters from OCS, either of the following can be used:
Note: To use this block, make sure that Async Query switch is enabled on service configurations page on CNC console. (Policy > Service Configurations > PCRF Core > Settings) This block is available under the Public category of PCRF Core policy projects. |
| End All |
You can exit the policy evaluation at any point in time using the End All blockly. This blockly has been added in the Public section for all the services such as PCRF CORE, SM, PDS, and so on. If the End All blockly is
used, the policy evaluation exits from that point and whatever
evaluation has been done till then returns from PRE (policy
runtime). It is used in case the user wants to perform a certain
set of actions and exit from there in some condition without
going and evaluating an entire policy. The following log message
is printed in the policy runtime indicating that policy
evaluation has
exited:
Exit requested from Policy evaluation, hence Exiting from policy!! |
|
| Subscriber Notification | ||
|
Figure 3-4 Send HTTP Notification  |
Send HTTP Notification | This block can be used to send HTTP messages to pre-defined HTTP servers with HTTP header and message body. The HTTP methods supported for sending messages are POST, PUT, GET, and PATCH. |
|
Figure 3-5 Send SMS  |
Send SMS using SMPP protocol |
This action is used to send short text messages as SMS using SMPP Protocol. You must include the MessageBody and the Destination address with User IDs. Note: Currently, this action is supported only for PCRF-Core call flows. For more details on |
|
Figure 3-6 Type of Number  |
Type of Number | Type of Number can be:
|
|
Figure 3-7 SMS Gateway Group  |
SMS Gateway Group | This blockly is used to display the list of SMS Gateways configured in CNC Console. |
|
Figure 3-8 Delivery Receipt  |
Delivery Receipt | The Delivery Receipt can be:
|
|
Figure 3-9 Number Plan Indicator  |
Number Plan Indicator | Number Plan Indicator blockly is used to select the
type of plan such as:
|
| Analytics Data | ||
|
Figure 3-10 Analytics Data |
Analytics Data | This block can be used to select analytic data attributes related to Slice Load Level. |
|
Figure 3-11 Reject Session with Cause 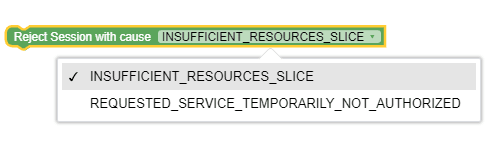 |
Reject Session with Cause | This block can be used to reject a session due to insufficient resources or unauthorized scenario. |
| Usage Monitoring | ||
|
Figure 3-12 Usage Monitoring exists 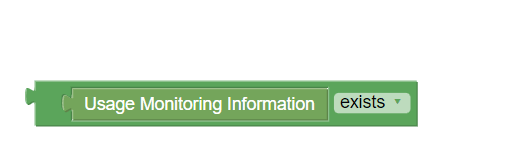 |
Usage Monitoring Information exists | Checks if Usage Monitoring Information exists or not. |
|
Figure 3-13 Monitoring Key for Usage Monitoring Level 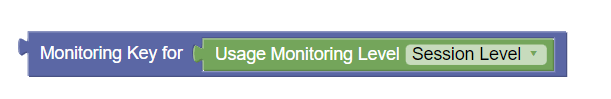 |
Monitoring Key for Usage Monitoring Level | This block can be used to retrieve monitoring key when Usage Monitoring is at session level. |
|
Figure 3-14 Usage Threshold Status for Monitoring Key 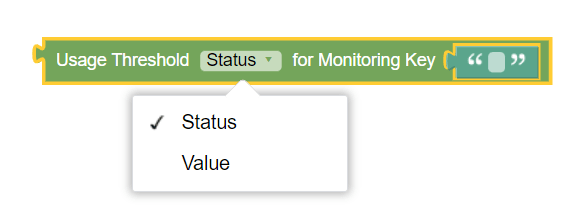 |
Usage Threshold Status for Monitoring Key | This block can be used to retrieve usage threshold status or value for the specified Monitoring Key. |
|
Figure 3-15 Grant Status for Monitoring Key 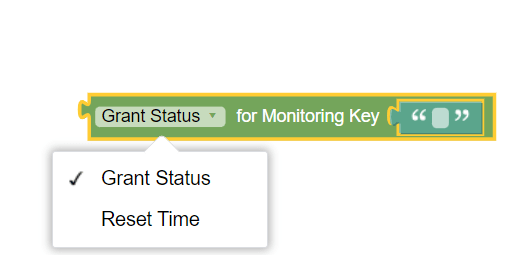 |
Grant Status for Monitoring Key | This block is used to retrieve the grant status or reset time for the specified Monitoring Key. |
|
Figure 3-16 Apply Grant for Monitoring Key  |
Apply Grant for Monitoring Key | This action block can be used to apply Grant for the specified Monitoring Key. |
|
Figure 3-17 Disable Usage Monitoring for Monitoring Key  |
Disable Usage Monitoring for Monitoring Key | This action block can be used to disable Grant for the specified Monitoring Key. |
|
Figure 3-18 Usage Monitoring Level  |
Usage Monitoring Level | This util can be used for specifying that the Usage Monitoring is at session level. |
|
Figure 3-19 Grant Status Approved 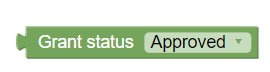 |
Grant status | This util can be used for specifying whether Grant status is approved or denied. |
|
Figure 3-20 Usage Monitoring Information  |
Usage Monitoring Information | This util can be used for retrieving Usage Monitoring Information. |
 |
Forwarded Attribute | Used to access the value of an attribute forwarded by the core service to Usage Monitoring service. |
 |
Reported Usage Data Limits | Used to access the Data Limit Profile names for which usage was reported by the core (such as PGW) in the Session Update (such as CCR-UPDATE) message. |
|
|
Attribute in UM Request |
Provides the following options:
|
 |
Data Limit Profile Attribute |
Used to access the properties of a Usage Monitoring Data Limit Profile configured on the Policy. The Data Limit Profile Attribute provides the following options:
|
 |
UDR Data Limit Attribute |
Used to access the properties of a Usage Monitoring Data Limit provided by UDR. The UDR Data Limit Attribute provides the following options:
|
 |
Usage Data Attribute |
Used to access the properties of a Usage Monitoring Data object. The Usage Data Attribute block provides the following options:
|
 |
Policy Tag | Used to access the Policy Decision Tags provided by Usage Monitoring service to Core Service. |
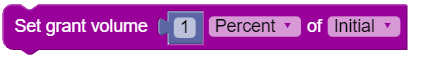 |
Set Grant Volume |
Used to indicate a volume grant value. Units has the following options:
Source options:
|
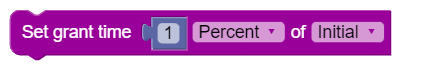 |
Set Grant Time |
Used to indicate a time grant value. Units has the following options:
Source options:
|
 |
Apply Data Limit Profile | Selects a Data Limit Profile from the configured Data Limit Profiles. This blockly also presents the option to use any Data Limits provisioned on the UDR for the subscriber. The provisioned Data Limits can be any top-ups and/or passes. Those data limits can have an option to preempt the currently running data limit. |
 |
Override Attribute |
The Data Limit block represents the attributes inside the UM Data Limit. This block can be used along with Action blocks like "Override Attributes" to indicate which attributes to override. The value selected for this blockly is sent in the PRE response:
|
|
Figure 3-21 PCC Rule Hint  |
PCC Rule Hint |
This attribute is used with the Data Limit Profile block. It allows to access the value of PCCRuleHint from Data limit profile and apply the same in UMPolicyDecision in monitoring key. |
|
Figure 3-22 Volume Grant Params  |
Volume Grant Parameters | Used to configure volume grants at PCC rule level. |
|
Figure 3-23 Time Grant Params  |
Time Grant Parameters | Used to configure time grants at PCC rule level. |
|
Figure 3-24 Active Monitoring Key with PCCRuleHint  |
Active Monitoring Key with PCCRuleHint |
Selects a Monitoring key for the configured PCCRule from usage monitoring policy decision which fulfills the value from active monitoring with PccRuleHint attribute. |
 |
Select Data Limit - Using Data Limit Selection Profile |
Selects a Data Limit from the List of Data Limits provided by the UDR using a Selection Profile. The Override Attributes option allows to override:
|
 |
Sort Data Limits using Data Limit Sorting Profile | Sorts the selected Data Limits using the given sorting profile.. |
 |
Apply UDR Data Limit having |
Selects a Data Limit from the List of Data Limits provided by the UDR using either a plan name. This blockly provides the following options:
|
 |
Apply Tag with name and value | Used to indicate to the core service one or more identifiers (key value pair(s)) to take further actions such as QoS or Charging related decisions. |
|
|
Reset Usage Data | Instructs the Usage Monitoring service to reset the Usage Data for the Profile / Data Limit name mentioned. |
 |
Disable Usage Monitoring | Disable usage monitoring for all or a specific data limit. |
| Observability | ||
 |
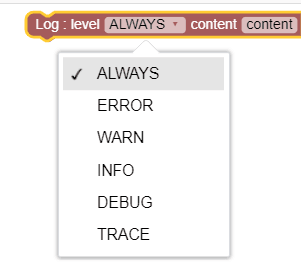
Log level |
This block can be used to set the log level for
Policy services. Users can select any of the following valid
values using the drop-down menu:
The Log level condition block can be used to design policies for PCF-SM, UE, AM, PDS, and PCRF-Core policy projects. Note: For this block, the 'occnp_policy_processing_latency_ms' metric is pegged. For more information see "PRE Metrics" in Oracle Communications Cloud Native Core, Converged Policy User Guide. |
 |
Log Level for content |
This block can be used to set the log level for Policy services and write any string in the Content. In the policy flow, the specified content will be included in the logs of PRE. |
 |
Increment Counter Label | Tracks total number of given custom block is invoked
for corresponding label.
Note: For this block, the 'occnp_block_counter_label' metric is pegged. For more information see "PRE Metrics" in Oracle Communications Cloud Native Core, Converged Policy User Guide. |
 |
Time | Tracks overall time taken by all the blocks captured
as part of this block.
Note: For this block, the 'occnp_block_exec_time_ns' metric is pegged. For more information see "PRE Metrics" in Oracle Communications Cloud Native Core, Converged Policy User Guide. |
3.6 PCF-SM Category
The blocks for this category is available only when you select SM service while configuring the policy project.
Table 3-5 Blocks in SM Service Category
| Block Icon | Block Name | Description | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Constructs | ||||||||||||
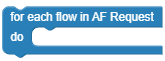 |
For Each AF Flow Request | It loops through the Media Component and SubComponent Blocks comparing with Media Type Block. | ||||||||||
| Conditions | ||||||||||||
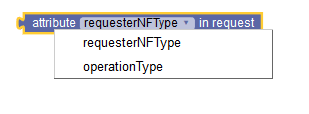 |
Request attributes | Sets the value to one of the JSON paths of drop-down
list options.
Drop-down list options: requesterNFType operationType |
||||||||||
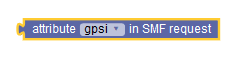 |
Request Attributes in SMF |
Sets the value to one of the JSON paths of drop-down list options. Drop-down list options : requesterNFType, operationType, gpsi, supi, accessType, ratType, pei, subsDefQos.5qi, subsDefQos.arp.priorityLevel, subsDefQos.arp.preemptCap, subsDefQos.arp.preemptVuln, subsDefQos.priorityLevel, dnn. Note: It is recommended to use Request attributes block, described in the next row, if you are selecting requesterNFType or operationType from the drop-down list. |
||||||||||
| Rat Type |
Sets the value to one of the drop-down list options of Rat Type. Drop-down list options : NR, NR_REDCAP, EUTRA, WLAN, VIRTUAL. |
|||||||||||
| app ID | Sets the application ID. | |||||||||||
| Operation Type |
Sets the value to one of the drop-down list options of Operation Type. Drop-down list options : CREATE, MODIFY, TERMINATE, REAUTH. |
|||||||||||
 |
PLMN Id | Compares the plmnId in the User Location Info received in SM Policy Create or Update request. | ||||||||||
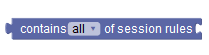 |
Contains session rules | Compares the given list with the list of session rules previously delivered to the SMF and stored in the SM Policy Association. | ||||||||||
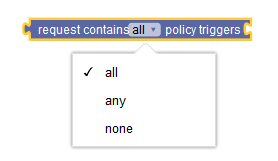 |
Contains policy triggers | Compares the policy triggers received in the SM Policy Update request with the given list of triggers. | ||||||||||
 |
Contain user categories | Compares User Categories attribute fetched from UDR with a list of provided User Categories. | ||||||||||
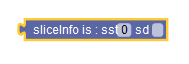 |
sliceInfo | Compares the Slice Information received in SM Policy request. | ||||||||||
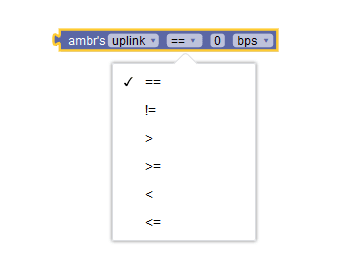 |
AMBR | Compares the AMBR received in the "subsSessAmbr" attribute in SM Policy request from SMF. | ||||||||||
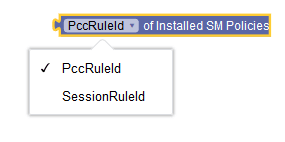 |
Installed SM Policies | Retrieves the list of PCC Rules previously delivered to the SMF and stored in the SM Policy Association. | ||||||||||
 |
Attribute in SM Policy Data | Retrieves data from the SM Policy Data (Subscriber Profile) fetched from UDR for a given S-NSSAI and DNN. | ||||||||||
| Media Componet |
Sets the value to one of the JSON path of drop-down list options. Drop-down list options : AF Application Id, Media Type, Media Component Number, Flow Status. |
|||||||||||
| Media Sub-Component |
Sets the value to one of the JSON path of drop-down list options. Drop-down list options : Flow Usage, Flow Number, Flow Description, Flow Status, ToS Traffic Class. |
|||||||||||
| Media Type |
Sets the value to one of the drop-down list options of Media Type. Drop-down list options : AUDIO, DATA, VIDEO, TEXT,CONTROL, APPLICATION, MESSAGE,OTHERS. |
|||||||||||
| Flow Usage |
Sets the value to one of the drop-down list options of Flow Usage. Drop-down list options: RTCP, NO_INFO. |
|||||||||||
| Flow Status |
Sets the value to one of the drop-down list options of Flow Status. Drop-down list options: ENABLED-UPLINK, ENABLED, ENABLED-DOWNLINK, DISABLED, REMOVED. |
|||||||||||
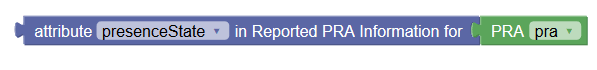 |
Attribute in Reported PRA Information | Retrieves the value of
presenceState attribute in Reported PRA
information for specified PRAs.
Note: Before
accessing the |
||||||||||
 |
NF Type | Allows operators to specify the type of network
function. The following are the available drop-down list values:
|
||||||||||
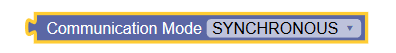 |
Communication Mode | Allows operators to specify mode of communication.
The available drop-down values are:
|
||||||||||
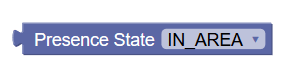 |
Presence State | Allows operators to specify the value for presence
state. The supported values are:
|
||||||||||
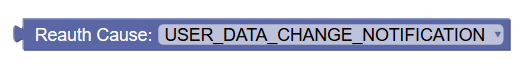 |
Reauthorization Cause | Checks the value of the attribute -
reauthCause of the policy request. The
supported value is "USER_DATA_CHANGE_NOTIFICATION".
|
||||||||||
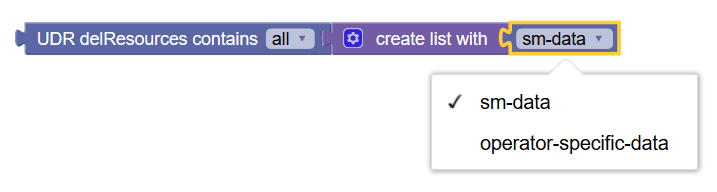 |
UDR delete Resources | Checks the value of the attribute -
policyDataChangeNotification.delResources of
the policy request. The supported values are "sm-data" and "operator-specific-data".
|
||||||||||
| Actions | ||||||||||||
 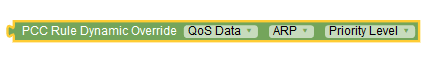 |
PCC Rule Dyanamic Override | This block is used as a key to create a pair of
{attribute: value}to override PCC rule attributes in real-time. This
block is used with the Key Value block.
The drop-down list values, auto-populated in the block, are taken from the PCC Rule configuration Page.PolicyPolicy Data ConfigurationsPCF Session ManagementPCC Rule Currently, operators can use this block to override
the values for the following parameters:
Important: If SM service does
not override attributes provided in the policy:
|
||||||||||
  |
Session Rule Dynamic Override | This block is used as a key to create a pair of
{attribute: value}to override session rule attributes in real-time.
This block is used with Key Value block.
The drop-down list values, auto-populated in the block, are taken from the Session Rule configuration Page.PolicyPolicy Data ConfigurationsPCF Session ManagementSession Rule Currently, operators can use
this block to override the values for the following
parameters:
|
||||||||||
| Apply Session Rule | It modifies the session Rule that is atttached after the "Create list with" Block. | |||||||||||
| Install/Remove Policy Trigger |
This block performs Install / Remove of the Policy Trigger. The Policy Trigger item to install/remove is picked from the set of hardcoded drop-down list values of Policy Trigger Block. |
|||||||||||
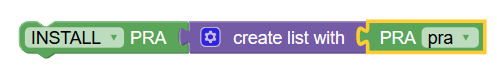
| Install/Remove PRA |
This block performs Install / Remove of the PRA. The PRA item to install/remove is picked from the configuration Page.(PCF→ Policy Configurations → Common → Presence Reporting Area) |
|||||||||||
 Figure 3-25 Install PCC Rule with SRA    |
Install/Update/Remove PCC Rules with Override Attributes |
This block can be used to create, modify, or remove specific PCC Rules. To update or override PCC rule attributes dynamically, you can drag and add create list with block to create pairs of {key:value} attributes using the Key Value block. The PCC rule attributes that you can update dynamically can be selected from the drop-down. You can select SUCC_RES_ALLO for Request Data to install PCC rules with Successful Resource Allocation (SRA) attribute. Note: Override Attributes checkbox is disabled if you select the Remove option from the drop-down. Important: When the PCC rule is initially provisioned, PCF must supply flowInfos or appId attribute. If it supplies appId, then PCF does not update appId attribute later provided by the user. |
||||||||||
  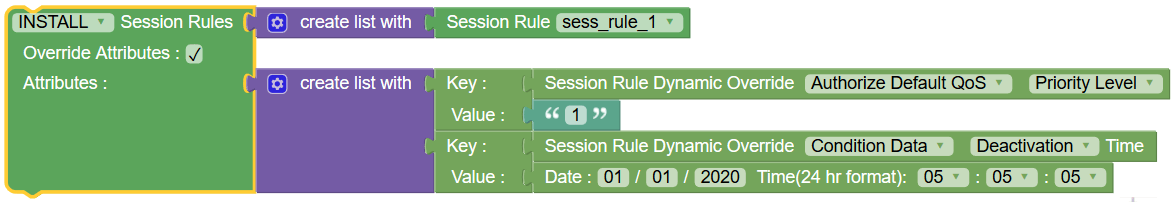 |
Install/Update/Remove Session Rules with Override Attributes |
This block can be used to create, update, and remove specific session rules. To update or override session rule attributes dynamically, you can drag and add create list with block to create pairs of {key:value} attributes using the Key Value block. Note: Override Attributes checkbox is disabled if you select Remove option from the drop-down. The Session rule attributes that you can update dynamically can be selected from the drop-down. |
||||||||||
 |
Apply PCC Rule Profile to flow with Override Attributes | It applies PCC rule with specified PCC Rule Profile. To update or override attributes dynamically, you can drag and add create list with block to create pairs of key:value attributes using the Key block. | ||||||||||
| Remove PCC Rules |
This block removes PCC Rules as per the option selected in drop-down list by the user. Drop-down list options: ALL DYNAMIC PRE_DEFINED NON_CONDITIONED CONDITIONED If you select DYNAMIC from
the drop-down value, SM service removes the following Dynamic
PCC rules:
If you select PRE_DEFINED from the drop-down value, SM service removes the pre-defined PCC rules defined on CM for SM policy data, and installed by previous policy decisions for the specified SM policy association. When removing PCC Rules in bulk, the policy also removes reference data only if the data is not referred by any PCC rule except the ones being deleted. To view all the PCC rules removed as part of a policy action, you can refer to the Info level policy logs. Important: If you are importing policies from older versions (previous to 1.8.0), delete the existing Remove PCC Rules blocks, and drag it from blockly library again after upgrade. |
|||||||||||
| Remove Session Rules |
This block performs Remove of Session Rules as per condition in drop-down list. Drop-down list options: REMOVE_ALL, REMOVE_NON_CONDITIONED, REMOVE_ALL_CONDITIONED. |
|||||||||||
 |
Set Binding Registration | Specifies whether to enable or disable the binding
operation. The supported values are True and
False.
Note: This policy action can read values from a policy table. Note: If Binding Operation flag is disabled on the service configurations page on CNC Console (Policy > Service Configurations > PCF Session Management), no binding operation is performed, irrespective of the value of policy decision. |
||||||||||
 |
Set Binding Registration Mode | Specifies whether to set binding registration mode
as synchronous or asynchronous.
Note: This policy action can read values from a policy table. |
||||||||||
| Policy Trigger |
Sets the value to one of the drop-down list options of Policy Trigger. Drop-down list options: PLMN_CH, RES_MO_RE, AC_TY_CH, UE_IP_CH, UE_MAC_CH, AN_CH_COR, US_RE, APP_STA, APP_STO, AN_INFO, CM_SES_FAIL, PS_DA_OFF, DEF_QOS_CH, SE_AMBR_CH, QOS_NOTIF, NO_CREDIT, PRA_CH, SAREA_CH, SCNN_CH, RE_TIMEOUT, RES_RELEASE, SUCC_RES_ALLO, RAT_TY_CH, REF_QOS_IND_CH, NUM_OF_PACKET_FILTER, UE_STATUS_RESUME, UE_TZ_CH, SCELL_CH. |
|||||||||||
| PCC Rule |
sets the value to one of the drop-down list options of PCC Rule. The drop-down list Values is picked from configuration Page.(PCF→ Policy Configurations → SM Policy → PCC Rule) |
|||||||||||
| PCC Rule Profile |
sets the value to one of the drop-down list options of PCC Rule Profile. The drop-down list Values is picked from configuration Page.(PCF→ Policy Configurations → SM Policy → PCC Rule Profile) |
|||||||||||
| Override PCC Rule |
It appends the "PCC Rule" and "PCC Rule Profile" Block and creates an Object {"pccRuleId": ('geyes-max'), "id":('pc_1')} and returns it. |
|||||||||||
| Session Rule |
sets the value to one of the drop-down list options of Session Rule. The drop-down list Values is picked from configuration Page.(PCF→ Policy Configurations → SM Policy → Session Rule) |
|||||||||||
| Ovverride Session Rule |
It appends the "Session Rule" and "Session Rule Profile" Block and creates an Object {"sessRuleId": 'sm-data', "sessRuleProfileId":('session_rule_profile_2')} and returns it. |
|||||||||||
| Session Rule Profile |
Sets the value to one of the drop-down list options of Session Rule profile. The drop-down list Values is picked from configuration Page.(PCF→ Policy Configurations → SM Policy → Session Rule Profile) |
|||||||||||
| Presence Reporting Area |
Sets the value to one of the drop-down list options of PRA. The drop-down list Values is picked from configuration Page.(PCF→ Policy Configurations → Common → Presence Reporting Area) |
|||||||||||
 |
Release Session | Directs the SM service to trigger session
termination notification and thus releasing a policy association.
When SM service receives this action, it ignores all other
actions.
Note: SM Service only
releases a policy association triggered by
That is, session terminate notification is
triggered based on:
|
||||||||||
|
Figure 3-26 Set Revalidation Time 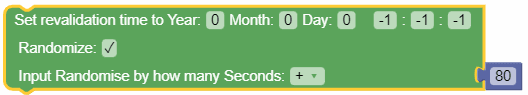 |
Set Revalidation Time |
Revalidation time defines the period within which the Session Management Function (SMF) triggers the PCC rule request towards PCF for an established PDU Session. You can use this action block to set the session revalidation time to a specific year, month, day, or time. In addition, you can check the Randomize checkbox to select a random revalidation time from the defined range. When you select the Randomize checkbox, you need to
define the range for revalidation time. You can define the range
by using the number block (under Public category) for specifying
the seconds and selecting any of the following values from the
dropdown list:
If you select the Randomize option, the following
message is printed in the Policy runtime
logs:
{"messageTimestamp":"2022-01-28T10:56:33.148Z","logLevel":"WARN","pid":9700,"workerId":1,"fileName":"..\\..\\engine\\policies\\pcf-sm\\test1\\main.js","lineNo":"46","message":"Randomization of revalidation time choosen by seconds"} If you input anything other than a number for
randomization, the following error is printed in the
logs:
"message":"Error!! Entered seconds is not a number for randomization !!Please enter number in seconds field." Note: On upgrading to Policy 22.1.0 or higher, the Set revalidation time block is upgraded automatically in the existing policies. |
||||||||||
|
Figure 3-27 Set session revalidation time to earliest of 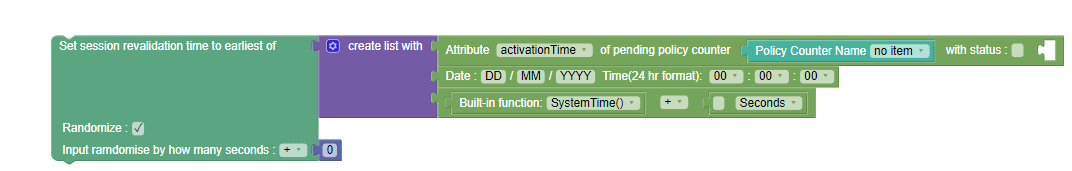 |
Set Session Revalidation time to earliest of |
Set session revalidation time to the earliest of
returns the earliest time from the following list:
This action block is Policy table compliant. In addition, you can check the Randomize checkbox to select a random revalidation time from the time range. You can define the range by using the number block
(under Public category) for specifying the seconds and selecting
any of the following values from the dropdown list:
If you select the Randomize option, the following
message is printed in the Policy runtime
logs:
{"messageTimestamp":"2022-01-25T08:10:41.698Z","logLevel":"WARN","pid":14692,"workerId":2,"fileName":"lib\\services\\sm_core-service.js","lineNo":"25","message":"Applying randomization on earliest time} If you input anything other than a number for
randomization, the following error is printed in the
logs:
"message":"Error!! Entered seconds is not a number for randomization !!Please enter number in seconds field." |
||||||||||
|
Figure 3-28 Reject Session with Error Code and Error Cause Figure 3-29 Example  |
Reject Session with Error Code and Error Cause | Allow to reject the session with a custom error code
and a custom error cause.
Note: If the Error Cause field is empty, only the Error Code will be sent back. |
||||||||||
|
Figure 3-30 Release Sesssion with cause for PCF-SM 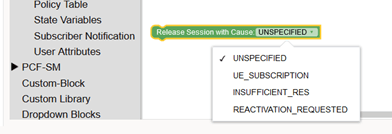 |
Action | Release SM Session with
PolicyAssociationReleaseCause
SMPolicyAssociationReleaseCause can have following
values:
Table 3-6 SMPolicyAssociationReleaseCause
|
||||||||||
3.6.1 PCC/Session Rule Error Report
Table 3-7 Blocks in PCC/Session Rule Error Report
| Block Icon | Block Name | Description |
|---|---|---|
| Constructs | ||
 |
PCC/Session Rule Status | The rule status can be combined with policy conditions "RuleIds" and "Rulereports" to specify rule status "Active" or "Inactive" |
 |
PCC/Session Rule Failure Code | sessRuleFailureCode can be combined with policy conditions "RuleIds" and "Rulereports" to check the failure code values |
 |
PCC/Session Failure Cause | Returns Failure Cause values
["RULE_PERMANENT_ERROR", "RULE_TEMPORARY_ERROR"] used along with two
condition blocks "PCC/Session Rule Ids" and PCC/Session Rule
report".
Checks the cause/failureCause attribute received in errorReport or partialSuccessReport. Checks the sessRuleFailureCode attribute received in sessRuleReports. |
 |
PCC/Session RuleIds from rulereport | Used to get the ruleIds received in ruleReports or sessRuleReports with condition matching for ruleStatus, ruleFailureCode or sessRuleFailureCode and failureCause. |
 |
PCC/Session Rule Report | This condition blockly matches with configured ruleIds, ruleStatus, sessRuleFailureCode and failureCause and returns true or false. |
Figure 3-31 Sample block for PCC/Session
Rule Error Report
3.7 PCF UE Policy
This section describes the blocks that operators can access while configuring PCF UE Policy projects.
Table 3-8 UE Policy Blocks
| Block | Description | ||||||||
|---|---|---|---|---|---|---|---|---|---|
|
Figure 3-32 Attribute in Request Type 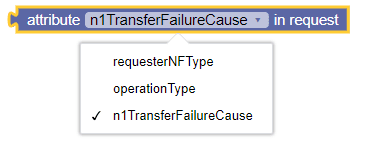 |
Allows the policy writer to retrieve the
following:
|
||||||||
|
Figure 3-33 N1 Transfer Failure Cause |
This blockly allows the policy writer to identify the
N1 transfer failure causes such as
UE_NOT_RESPONDING in the messages.
|
||||||||
|
Figure 3-34 Attribute in AMF Request 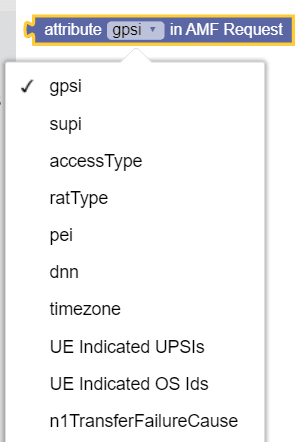 |
Retrieves the specified attribute value from the
incoming request
message.
The available options are:
|
||||||||
|
Figure 3-35 Attributes in UE Policy Set  |
Retrieves the specified attribute value from the UE
Policy Set (as obtained from
UDR).
The available options are:
|
||||||||
|
Figure 3-36 Operation Type |
Allows operators to specify the Operation Type. The supported values are CREATE, UPDATE, TERMINATE, and NOTIFICATION. | ||||||||
|
Figure 3-37 RatType |
Allows operators to specify the value of RAT Type. The supported
values are :
|
||||||||
|
Figure 3-38 AccessType |
Allows operators to specify the Access Type. The supported values are 3GPP Access and Non 3GPP Access. | ||||||||
|
Figure 3-39 PLMN ID |
Allows operators to specify MCC or MNC of plmnid in the following supported values: Serving PLMN Id, EUTRACelld, EUTRA tracking Area Code, NR Celld, NR tracking Area Code, eutraLocation.tai, ecgi, globalNgenbld, nrLocation.tai, ncgi, and globalGnbld. | ||||||||
|
Figure 3-40 UPSI Values |
Allows the operators to specify the value of the UPSI. | ||||||||
|
Figure 3-41 UPSI  |
This block allows the policy writer to select a UPSI configured using the Policy > Policy Data Configurations > PCF UE Policy > UPSI screen. | ||||||||
|
Figure 3-42 URSP |
This block allows the policy writer to select a URSP configured using the Policy > Policy Data Configurations > PCF UE Policy > URSP Rule screen. | ||||||||
| Actions | |||||||||
|
Figure 3-43 Install/Remove UPSI |
Allows the policy writer to install or remove UPSIs
that are already configured in GUI on the UPSI screen
(Policy
>
Policy Data Configurations
>
PCF UE Policy
>
UPSI).
Click the drop-down menu of UPSI block to select desired UPSI Ids. |
||||||||
|
Figure 3-44 Install/Remove UPSIs from UE Policy Set 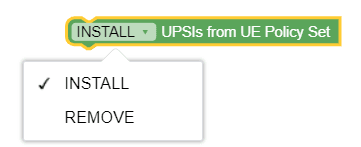 |
Allows the policy writer to install or remove UPSIs
retrieved from the UDR in the UE Policy Set (upsis attribute).
Notes:
|
||||||||
|
Figure 3-45 Install Policy Trigger 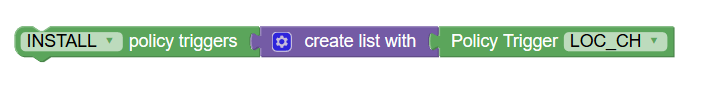 |
This action block allows the policy writer to
install or remove policy triggers. The Policy Trigger value to
install/remove is automatically populated in the form of drop-down
with the Policy Trigger
block.
Note: Currently, the only supported policy trigger value is LOC_CH (change in location). |
||||||||
|
Figure 3-46 Install/Remove URSPs 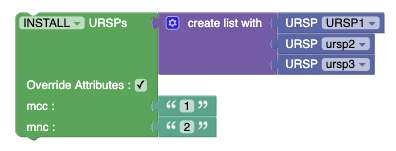 |
Allows the policy writer to install or delete URSP rules for delivery using the fragmentation feature. | ||||||||
|
Figure 3-47 Remove UPSIs  |
Allows the policy writer to remove UPSI from the UDR in the UE Policy Set. | ||||||||
|
Single URSP Figure 3-48 Policy Table Column Blockly  Figure 3-49 Example: Policy Table Column, an URSP 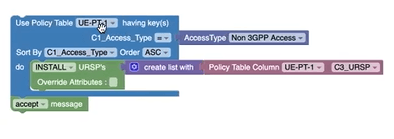 |
This block allows the policy writer to create an
Policy For example: Use Policy Table UE-PT1 whose access type is Non-3GPP Access and Install URSPs with Policy Table UE-PT1 with column c3_URSP (single URSP). |
||||||||
|
URSP List
Figure 3-50 Example: Policy Table Column, URSP List  |
This block allows the policy writer to create an
Policy For example: Use Policy Table UE-PT1 whose access type is Non-3GPP Access and Install URSPs with Policy Table UE-PT1 with column c3_URSP_List (an URSP List). |
||||||||
|
Figure 3-51 Retransmit UPSI |
This blockly allows the policy writer to either re-transmit some of the rejected UPSI or to abort the transmission entirely. | ||||||||
|
Figure 3-52 Skip current fragment  |
This blockly allows the policy writer to skip the current fragment transmission, immediately starting the next fragment transmission or ending the transaction in case there is no next fragment. | ||||||||
|
Figure 3-53 Abort N1 Notify Transmission |
This blockly immediately ends the transaction and won't continue the N1 transmission. | ||||||||
|
Figure 3-54 UPSI List  |
Note: The List blockly is used for setting operation on two lists. It can be used for general cases in addition to the operation on UPSI lists. The List operation is used while finding the delta between the UPSI's ID list that is currently configured in PCF, the UPSI's that are sent on UE Policy Registration and the UPSIs that are on UDR. Allowed values:
|
||||||||
|
Figure 3-55 Retransmit Fragment |
This blockly allows the policy writer to retransmit the whole n1 fragment. | ||||||||
| Condition Blocks | |||||||||
|
Figure 3-56 N1 Notify Message Received 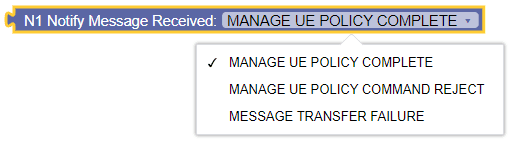 |
This blockly allows the policy writer to identify the
following N1Notify messages:
|
||||||||
|
Figure 3-57 UPSIs attribute path |
UPSI's in VSA: Specify upsi PATH condition returns the UPSIs attribute path in the request. Figure 3-58 UPSI's attribute path in VSA - Example The above example returns the UPSIs attribute path in VSA as:
Note: The PATH text must be either the dotted notation or the array notation and must not mix these two together. |
||||||||
|
Figure 3-59 Get Configured UPSIs/ UPSI Name/ UPSI Index  |
with condition allows to retrieve configured UPSI from PCF, or UPSI name, or UPSI index for the specified attribute (mcc/mnc/upsc/ursp) from the list of UPSIs or individual UPSI plugged in the last section of the blockly. Example for Configured UPSIs and UPSI Name:  In this example, the first part of the blockly will install the "upsc1" upsi if its mcc equals to 123 and mnc equals to 456 and override its PLMN to be 222-333. Similar for the second part, it will assign a variable called attr1 with the attribute of upsc from the UPSI which has the name "upsc2" on the VSA UPSIs list, and if this value is equal to 2, it will remove this UPSI and will override its PLMN to be 222-333. NOTE: In this case, when searching by name, we will check of the list that are on VSA request and if it exist on the PCF Configured UPSIs, it will return the given attribute, so here we check for the UPSI with name "upsc2" which is in the list of the VSA UPSIs and it exists also as a configured UPSI in PCF, then we procced with the validation. Example for UPSI Index:
This example loops on all the UPSIs that are located on AMF request. It allows to access an attribute from specific UPSI on AMF request. This Policy checks if any of the UPSIs on the list has its UPSC as 2. If found, it removes the corresponding UPSI and overrides its PLMN to be 222-333. |
||||||||
| Util Blocks | |||||||||
|
Figure 3-60 Successfully Installed UPSI in N1 Notify Message |
This blockly allows to notify the successfully installed UPSI received in N1N2 notification. The successfully installed UPSI will only be available in the blockly when they are installed using the install UPSIs blockly. |
||||||||
|
Figure 3-61 Rejected UPSI in N1 Notify Message  |
This blockly allows the policy writer to iterate over the rejected UPSI when the N1 Notify message comes as MANAGE UE POLICY COMMAND REJECT. | ||||||||
|
Figure 3-62 Retransmit count for UPSI |
This blockly allows the policy writer to get the current retransmission count for a specific UPSI, allowing the policy writer to control how many times the retransmission has happened. | ||||||||
 |
Installs or removes elements such as PRAs or UPSIs as specified by the operator.
The drop-down values, auto-populated in the block, are taken as per the configuration on PCF Presence Reporting Area page under Common Policy Data Configurations. Note: Currently, Remove all request triggers functionality is not yet supported. |
||||||||
|
Figure 3-63 Install UPSIs  Figure 3-64 Remove UPSIs 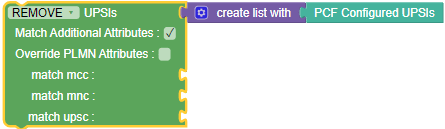 |
Install/Remove UPSIs with/without matching specific attribute of mcc, mnc and upsc. It also supports the checkbox to override PLMN for INSTALL/REMOVE. |
||||||||
|
Figure 3-65 Retransmit count for URSP |
This blockly allows the policy writer to get the current re-transmission count for a specific URSP, allowing the policy writer to control how many times the re-transmission has happened. | ||||||||
|
Figure 3-66 Rejected URSP in N1 Notify Message |
This blockly allows the policy writer to iterate over the rejected URSP when the N1 Notify message comes as MANAGE UE POLICY COMMAND REJECT. | ||||||||
|
Figure 3-67 N1 fragement retransmit count |
This blockly allows the policy writer to get the current re-transmission count of the whole N1 fragment. Using this the policy writer supervises number of retransmission occurrences. | ||||||||
 |
Specifies if it is the PRA Change (PRA_CH) or the Location Change (LOC_CH) action to be mentioned in the PRA report sent by UE Policy Service to AMF upon success Creation or update of the UE Policy Association. | ||||||||
 |
Indicates the presence state of the UE:
|
||||||||
|
|
Sets the value to one of the drop-down list options of PRA. The drop-down list Values is picked from configuration Page. (PCF→ Policy Configurations → Common → Presence Reporting Area) |
||||||||
|
|
Indicates current presence status of the UE in a Presence Reporting Area, and notifies that the UE enters/leaves the Presence Reporting Area. | ||||||||
|
Figure 3-68 PCF Configured UPSIs |
PCF Configured UPSIs utility used with create list with block to generate a list of all configured UPSIs in PCF. |
||||||||
|
Figure 3-69 Convert UPSI Format to 3GPP |
Converts UPSI in format "mcc-mnc-upsc" or UPSI configuration name in PCF such as "upsi01" to 3GPP format. This utility is used with UPSIs in VSA block. For example:
|
||||||||
|
Figure 3-70 UDR delResources contains  |
Checks the value of the attribute -
policyDataChangeNotification.delResources
of the policy request. The supported values are:
For example:
Figure 3-71 Example usage of UDR delResources contains  |
||||||||
|
Figure 3-72 Release Session with cause 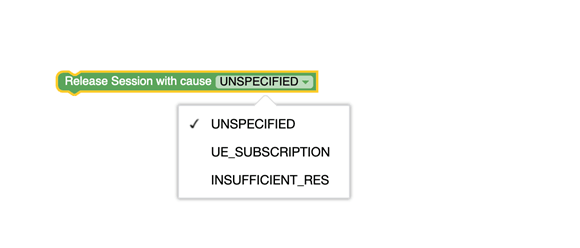 |
PolicyAssociationReleaseCause can have:
Table 3-9 PolicyAssociationReleaseCause
|
||||||||
|
Figure 3-73 Release Session without cause  |
Directs the AM/UE service to trigger session termination notification and thus releasing a policy association. When AM/UE service receives this action, it ignores all other actions. | ||||||||
3.8 PCF-AM Blocks
This section describes the blocks that operators can access while configuring PCF AM Policy projects.
Table 3-10 AM Policy Blocks
| Block | Description |
|---|---|
| Retrieves the value of requester NFType attribute in request. | |
| Retrieves the value of SUPI attribute in AMF request. | |
| Allows operators to specify the value of RAT Type. The supported values are NR, NR_REDCAP, WLAN, EUTRA, and VIRTUAL. | |
| Allows operators to specify the NF Type. The supported values are AMF, SMF, BSF, NEF, AF, UDR, and CHF. | |
| Allows operators to specify the Operation Type. The supported values are CREATE, UPDATE, DELETE, NOTIFICATION, UPDATE_NOTIFY, and TERMINATE_NOTIFY. | |
| Allows operators to specify MCC or MNC of plmnid in the following supported values: eutraLocation.tai, ecgi, globalNgenbld, nrLocation.tai, ncgi, globalGnbld, and negaLocation.n3gppTai. | |
| Allows operators to specify Restriction Type as ALLOWED_AREAS or NOT_ALLOWED_AREAS. | |
 |
Retrieves the service area restriction values, created through Service Area Restriction screen on CNC Console. |
 |
Retrieves the value of presenceState
attribute in Reported PRA information for specified PRAs.
Note: Before accessing |
| Retrieves the PRA values. The supported values are PRA1 and PRA2. | |
| Retrieves the Request Trigger values. The supported values are LOC_CH, PRA_CH, SERV_AREA_CH, and RFSP_CH. | |
| Actions | |
 |
Installs Service Area Restriction, specified by the operator. |
 |
Sets a value for RFSP Index. |
 |
Installs or removes list of PRAs, specified by the operator. The drop-down values, auto-populated in the block, are taken from the PCF Presence Reporting Area configuration Page (Policy > Policy Data Configurations > Common > PCF Presence Reporting Area). |
|
Installs or removes list Request Trigger Actions, specified by the operator. |
|
| Removes all request triggers. | |
3.9 PDS Category
This section provides information about blocks that can be used to write policies for Policy Data Source service.
Table 3-11 PDS Blocks
| Block Image | Description |
|---|---|
| Conditions | |
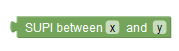 |
Specifies the first value and the last value of a SUPI range. |
| Specifies the first value and the last value of a GPSI range. | |
| Specifies the pattern representing the set of SUPI's belonging to this range. | |
| Specifies the pattern representing the set of GPSI's belonging to this range. | |
 |
Specifies whether the incoming request message is coming from soap connector or PCRF core. |
| Actions | |
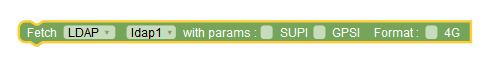   |
This blockly action allows policy writers to retrieve
resourceTypes from specified datasource.
When the user selects LDAP from the drop-down menu, retrieval takes place through LDAP datasource. Use the drop-down menu to select LDAP ID configured on PDS Settings page under Service Configurations in CNC Console. In addition, user can select parameters - SUPI or GPSI to perform the lookup. When the 4G checkbox is selected, the lookup is done using IMSI or MSISDN. When UDR is selected from the drop-down menu, the policy retrieves UDR datasource and the default configurations, configured on PCF User Connector under Service Configurations in CNC Console. In addition, user can use the checkboxes to retrieve multiple resourceTypes at once. When CHF is selected from the drop-down menu, the policy retrieves CHF datasource and the default configurations, configured on PCF User Connector page under Service Configurations in CNC Console. When OCS is selected from the drop-down menu, the policy retrieves OCS datasource and the default configurations, configured using Policy > Diameter Configurations > Peer Nodes page. By default, OCS supports 4G format. |
3.10 PCRF-Core
The policy wizard supports a large number of conditions that can be used for constructing policy rules. To help you find the conditions you want, the conditions are organized into different categories.
The conditions that are included within each of these categories are described in the sections that follow. Within each category, conditions are listed in alphabetical order. The parameters that can be modified within each condition are also detailed.
3.10.1 Conditions
This section provides information on policy conditions available for PCRF Core service.
The enforcement session is one of an IP-CAN session
This policy condition, as shown in the following image, triggers a policy that evaluates the type of the enforcement session.

- an IP-CAN session (default)
- a gateway control session
- a DPI enforcement session
- an S9 sub-session
- an S9 session
Mobile session includes Sponsored Connectivity
The Mobile session includes or does not include Sponsored Connectivity policy condition, as shown in the following image, triggers a policy that evaluates whether or not the mobile session supports sponsored data connectivity. This condition supports sponsored data connectivity for both Gx and Rx requests.

Reauthorization Reason
The Reauthorization Reason policy condition, as shown in the
following image, compares reauthorization reason in request received by PRE with the
value specified in the policy condition.
- REASON_DEFAULT
- REASON_AUDIT
- REASON_TOD
- REASON_LI
- REASON_RELEASE_SESSION
- REASON_POLICY
- REASON_NOTIFICATION
- REASON_RETRY
- REASON_AF
- REASON_OCS_NOTIFICATION
- REASON_RECONCILE
- REASON_USER_SCHEDULED_TASK
- REASON_REVALIDATION_TIMEOUT
- REASON_SY_SESSION_TERMINATION_BY_OCS
request supports feature name
The request supports or does not support feature name policy condition, as shown in the following image, determines whether the request supports or does not support a specified feature respectively.

For the name of the feature, this policy condition supports a comma-delimited list of values.
where the event trigger is one of
This policy condition, as shown in the following image, triggers a policy that is only evaluated for a specific event trigger type.

- SGSN_CHANGE
- QOS_CHANGE
- RAT_CHANGE
- TFT_CHANGE
- PLMN_CHANGE
- LOSS_OF_BEARER
- RECOVERY_OF_BEARER
- IP_CAN_CHANGE
- GW_PCEF_MALFUNCTION
- RESOURCES_LIMITATION
- MAX_NR_BEARERS_REACHED
- QOS_CHANGE_EXCEEDING_AUTHORIZATION
- RAI_CHANGE
- USER_LOCATION_CHANGE
- NO_EVENT_TRIGGERS
- OUT_OF_CREDIT
- REALLOCATION_OF_CREDIT
- REVALIDATION_TIMEOUT
- UE_IP_ADDRESS_ALLOCATE
- UE_IP_ADDRESS_RELEASE
- DEFAULT_EPS_BEARER_QOS_CHANGE
- AN_GW_CHANGE
- SUCCESSFUL_RESOURCE_ALLOCATION
- RESOURCE_MODIFICATION_REQUEST
- UE_TIME_ZONE_CHANGE
- TAI_CHANGE
- ECGI_CHANGE
- CHARGING_CORRELATION_EXCHANGE
- APN_AMBR_MODIFICATION_FAILURE
- USER_CSG_INFORMATION_CHANGE
- USAGE_REPORT
- DEFAULT_EPS_BEARER_QOS_MODIFICATION_FAILURE
- USER_CSG_HYBRID_SUBSCRIBED_INFORMATION_CHANGE
- USER_CSG_HYBRID_UNSUBSCRIBED_INFORMATION_CHANGE
- APPLICATION_START
- APPLICATION_STOP
- ADC_REVALIDATION_TIMEOUT
- ACCESS_NETWORK_INFO_REPORT
- CHANGE_OF_UE_PRESENCE_IN_PRESENCE_REPORTING_AREA_REPORT
- HOTSPOT_SHARE_START
- USAGE_THRESHOLD_REACHED
- SERVICE_FLOW_DETECTION
- CELL_CONGESTED
- CELL_CLEAR
- RAN_NAS_Cause
- SESSION_RECOVERY_VZW
- SESSION_SYNC_VZW
- CREDIT_MANAGEMENT_SESSION_FAILURE
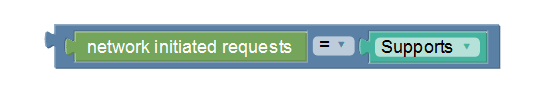
network initiated requests are supported
The network initiated requests policy condition, as shown in the following image, triggers a policy that is only evaluated when network initiated requests are supported. On selecting does not Support from the drop-down field, this condition block triggers a policy that is only evaluated when network initiated requests are not supported.
APN aggregate maximum bitrate
The APN aggregate maximum bitrate condition block, as shown in the following image, selects protocol messages based on the maximum bitrate being requested for an access point name (APN) in a specific direction relative to a numeric value - specified in the string block. The unit of bandwidth is compatible with the Credit Control Request (CCR) message. The APN aggregate maximum bitrate condition block is Policy Table compliant.
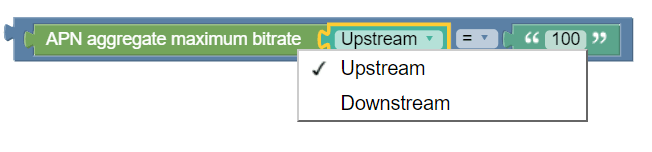
- =
- !=
- <
- <=
- >
- >=
- Matches
- RegExp-Matches
IP-CAN type
The IP-CAN type policy condition, as shown in the following image, triggers a policy that is only evaluated for a protocol message with a specific IP-CAN type.

- 3GPP_GPRS
- 3GPP_EPS
- NON_3GPP EPS
- 3GPP2
- WiMAX
- DOCSIS
- xDSL
The request is
The request is policy condition, as shown in the following image, evaluates whether the request type matches with the specified request.
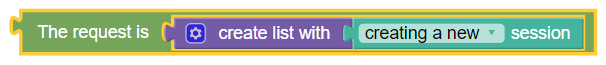
- creating a new session (default)
- modifying an existing session
- re-authorizing an existing session
- terminating an existing session
The RAT type is
The The RAT type is policy condition, as shown in the following image, triggers a policy that is only evaluated for a protocol message with a specific Radio Access Technology (RAT) type.

- GERAN
- UTRAN
- HSPA Evolution
- UMA/GAN
- EUTRAN
- EUTRAN NB IoT
- WLAN
- CDMA2000 1x
- HRPD
- UMB
- eHRPD
- NR_REDCAP
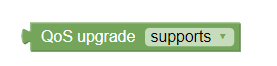
QoS Upgrade
The QoS Upgrade policy condition, as shown in the following image, evaluates if QoS upgrade is supported (supports) or not (does not support).
The session is an enforcement session
The The session is an enforcement session condition block, as shown in the following image, distinguishes between protocol messages that are operating on different sessions.

- an enforcement session (default)
- an application session
- a credit control session
- a radius authorization session
tier
The tier condition block, as shown in the following image, triggers a policy that is evaluated for one or more specific tiers.

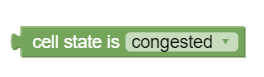
cell state is congested
The cell state is congested policy condition block, as shown in the following image, triggers a policy that is evaluated based on the level of congestion in the cell. The supported values are congested and not congested.
3.10.2 Actions
This section describes the policy actions that can be used to construct policy rules for PCRF Core service.
set Alert with severity level, ID and message
This policy action, as shown in the following image, sends an alert to the system containing the specified severity level and message text. This alert appears in the Active Alerts display for one hour, until cleared, or unless the server fails over, whichever comes first. Alerts generated by policy actions do not affect the HA score of a server, and will not cause a failover. On choosing clear from the drop-down field, the alert containing the specified severity level and message text is cleared from the system.

- Critical (default)
- Major
- Minor
The ID field specifies the alert ID. On selecting Evaluate as expression, the text in the field is evaluated as an arithmetic expression, and the result is used.
Note:
The "set Alert with severity level, ID and message" has been deprecated in 23.4.0. It should not be used.reset all subscriber data
The reset all subscriber data policy action, as shown in the following image, resets all data for the subscriber.
set policy context property name to value
This policy action block, as shown in the following image, sets a subscriber property. The property-name and value accept strings as value.
remove all policy context properties
The remove all policy context properties policy action, as shown in the following image, removes all policy context properties.

Establish Traffic Detection Session for a Peer Node
The Establish Traffic detection session with policy action, as shown in the following image, establishes a traffic detection session with the selected network element identity.

Establish Traffic Detection Session for Peer Node Set
The Establish Traffic detection session with policy action, as shown in the following image, establishes a traffic detection session with the selected network element identity.
Enable Logging with log levels
The public Log: Level block is enabled ALWAYS in the event of various actions, as shown in the following image.
Figure 3-74 Log: level
3.10.3 AF
This section describes the blocks and conditions specific to flows.
3.10.3.1 Conditions
This section describes the conditions specific to flows.
Required-Access-Info
The Required-Access-Info policy condition, as shown in the following image, triggers a policy when the returned access network information, populated in Rx call flow, for that AF session matches the specified value.
Figure 3-75 Policy Condition for Required-Access-Info

- USER_LOCATION (default)
- MS_TIME_ZONE
- USER_LOCATION_AND_MS_TIME_ZONE
the corresponding enforcement session supports feature
The the corresponding enforcement session supports feature name policy condition, as shown in the following image, evaluates the feature name in the enforcement session that correlates to the corresponding application (Rx) request.
![]()
- * (asterisk) character to match zero or more characters
- ? (question mark) character to match exactly one character
where the application session type is Rx
Figure 3-76 Application Session Type Block

Note:
If the application session is not Rx, the policy condition returns unknown.Apply Traffic Profile to Flow(s) whose media type matches one of specified values
This policy condition, as shown in the following image, applies one or more traffic profiles to one or more flows of the specified type media type. It overwrites the corresponding settings in the protocol messages of the specified flows. If multiple traffic profiles are selected, they are applied in the order in which they are specified. If a traffic profile contains settings that are not relevant in the current protocol message, they are ignored. This policy condition is Policy Table compliant.

- Audio
- Video
- Data
- Application
- Control
- Text
- Message
- Other
Specific action
The Specific action policy condition, as shown in the following image, triggers a policy when the value of the Specific-Action AVP field within an Rx RAA message matches the specified value.

The user can select any of the following valid values from the Specific actions drop-down field:
- SERVICE_INFORMATION_REQUEST (default)
- CHARGING_CORRELATION_EXCHANGE
- INDICATION_OF_LOSS_OF_BEARER
- INDICATION_OF_RECOVERY_OF_BEARER
- INDICATION_OF_RELEASE_OF_BEARER
- INDICATION_OF_ESTABLISHMENT_OF_BEARER
- INDICATION_OF_IP_CAN_CHANGE
- INDICATION_OF_OUT_OF_CREDIT
- INDICATION_OF_SUCCESSFUL_RESOURCES_ALLOCATION
- INDICATION_OF_FAILED_RESOURCES_ALLOCATION
- INDICATION_OF_LIMITED_PCC_DEPLOYMENT
- USAGE_REPORT
- ACCESS_NETWORK_INFO_REPORT
- INDICATION_OF_RECOVERY_FROM_LIMITED_PCC_DEPLOYMENT
- INDICATION_OF_ACCESS_NETWORK_INFO_REPORTING_FAILURE
- PLMN_CHANGE
3.10.3.2 CODEC Conditions
Session Description Protocol (SDP) properties conditions identify any specific SDP attributes and evaluate their value. This includes setting proper bandwidth values on related PCC rules. The following conditions are available.
the local specified SDP property matches one of value(s)
This policy condition, as shown in the following image, checks the Codec type (offer or answer) for a subscriber's device (local, remote or common) for specific values (a comma-delimited list).

- Local—The capabilities of the device for the subscriber.
- Remote—The capabilities of the device for the remote party.
- Common—The capabilities that the local and remote devices have in common.
- Generic
descriptor
Syntax:
sdp.[option]where option is any name (for example, i) or any keyword (for example, a=ptime)
Examples using an SDP generic descriptor:where the local sdp.[i] matches one of *recvonly*where the common sdp.[a=ptime] matches one of 20where the common sdp.[a] matches one of ptime: 20where the common sdp.[u] matches one of http://www.oracle.com:8080/hr/one.htmwhere the common sdp.[u=http://www.oracle.com] matches one of 8080/hr/one.htmwhere the common sdp.[u=http] matches one of //www.oracle.com:8080/hr/one.htmwhere the remote sdp.[xy] matches one of zwhere the remote sdp.[xy=z] matches one of 80
- Media descriptor
Syntax:
sdp.[m.option]where option can be any of the given values - fmt, port, numberofports, media, and proto.
Examples using an SDP media descriptor:where the common sdp.[m.fmt] matches one of 102-
where the common sdp.[m.port] does not match any of 41000,41002 where the remote sdp.[m.media] matches one of audio,video-
where the local sdp.[m.proto] matches one of RTP/AVP
- rtpmap
Syntax:
sdp.[codec-name(codec-name).rtpmap.OPTION]where codec-name specifies a codec name.
where option can be any of the given values - payloadtype, clockrate, and encodingparameters.
Examples using rtpmap:where the common sdp.[ codec-name(AMR-WB).rtpmap] matches one of 104 AMR-WB/160000where the common sdp.[ codec-name(AMR-WB).rtpmap.encodingparameters] matches one of 2-
where the common sdp.[ codec-name(AMR-WB).rtpmap.payloadtype] matches one of 104,102
- fmtp
Syntax:
sdp.[codec-name(codec-name).fmtp.OPTIONS]where codec-name specifies a codec name.
where option can be any of the given values - fmt, profile-level-id, mode-set, packetization-mode, or any other parameter to be conveyed.
Examples using fmtp:where the common sdp.[codec-name(AMR-WB).fmtp.fmt] matches one of 104,102where the common sdp.[codec-name(AMR-WB).fmtp.mode-set] matches one of 2,4-
where the commonsdp.[codec-name(H264).fmtp.profile-level-id] matches one of42e00c
the local specified SDP property exists
This policy condition, as shown in the following image, checks for the existence or non-existence of any SDP property for a subscriber's device (local, remote or common).

- Local—The capabilities of the device for the subscriber.
- Remote—The capabilities of the device for the remote party.
- Common—The capabilities that the local and remote devices have in common.
For information on how to specify the name of SDP property, see Specifying SDP Property.
the local specified SDP property is numerically equal to specified value
This policy condition, as shown in the following image, compares a numerical SDP property for a subscriber's device (local, remote or common) against a specified number (string).

- Local—The capabilities of the device for the subscriber.
- Remote—The capabilities of the device for the remote party.
- Common—The capabilities that the local and remote devices have in common.
Users can select any of the following valid values from the drop-down field for the comparison:
- equal to
- not equal to
- less than
- greater than
- less than or equal to
- greater than or equal to
where the local codec data is an offer
This policy condition, as shown in the following image, checks the Codec type (offer or answer) for a subscriber's device (local, remote, or common).

- Local—The capabilities of the device for the subscriber.
- Remote—The capabilities of the device for the remote party.
- Common—The capabilities that the local and remote devices have in common.
3.10.4 AVP Specific
This section describes conditions and actions specific to Attribute Value Pair (AVP).
3.10.4.1 Conditions
This section describes the conditions specific to AVP. The AVP conditions are Policy Table compliant.
AVP Name exists
This policy condition, as shown in the following image, checks whether the specified third-party AVP exists or does not exist in an incoming Diameter message. This policy condition supports both loaded base Diameter AVPs and third-party AVPs.
![]()
-
name:vendorID - a full path
for the members of the grouped AVPs[avp_name1]:vendorID.[avp_name2]:vendorID…
value of AVP with name contains one or more of specified values
This policy condition, as shown in the following image, compares the specified value of AVP with name with the values or variables from the specified list. The condition is where the request AVP name value matches one of the values. The values can be evaluated for equality as well as inequality. To evaluate an AVP value for inequality, the block contains of must have the value none. This policy condition supports both loaded base Diameter AVPs and third-party AVPs.
-
name:vendorID - a full path
for the members of the grouped AVPs.[avp_name1]:vendorID.[avp_name2]:vendorID…
3.10.4.2 Actions
This section describes the policy actions specific to AVP. The AVP actions are Policy Table compliant.
set custom AVP value to the specified property name
This policy action, as shown in the following image, makes the AVP value accessible throughout the policy context so other policies can access this AVP value as a context property. The context property variable will be set only if this AVP exists in the request and its value is not null.

The property name is a string that represents the policy context property. The Custom AVP name must be an existing AVP name and Vendor ID.
set value to existing or new custom AVP
This policy action, as shown in the following image, adds the third-party non-grouped AVP to the current Diameter session with the specified value. If a third-party AVP value is set in the current Diameter session, it will be sent with the corresponding outgoing message. The value parameter must correspond to the AVP data type; otherwise, the AVP shall not be set. If New is selected as the value for custom AVP, a new AVP is added to the message on every execution of this policy action, without considering that the same AVP name is present in the message.

The value string represents a third-party non-grouped AVP.
- Always
- Unless rejected
- If rejected
Add custom grouped AVP and send Always
This policy action, as shown in the following image, adds or sends new custom grouped AVP to the current reply. A condition can be set specifying that the AVP is always set to send mode. If you are defining a new grouped third-party AVP with members, the grouped AVP has to appear first in the policy. If you are adding a new member AVP that does not have its parent AVP added yet, the policy attempts to locate this grouped AVP in the rest of the policy. To include a grouped AVP multiple times in the same message, users must follow the order in which it appears in the message.

- Always
- Unless rejected
- If rejected
Remove custom AVP from reply Always
This policy action, as shown in the following image, removes the custom AVP name set previously from the reply message.
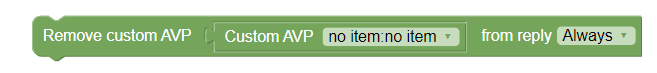
- Always
- Unless rejected
- If rejected
Mark request AVP as failed if exists and send Always
This policy action, as shown in the following image, marks request AVP as failed if it exists.
![]()
- Always
- Unless rejected
- If rejected
3.10.4.3 Use Cases
This section describes use cases for policy conditions specific to AVP.
Use Case - AVP Name exists
The following screen capture shows a sample policy condition that
determines whether the AVP Media-Component-Description is accessible. ![]()
Use Case - Add custom grouped AVP and send Always
In the following sample policy, a third party grouped AVP Custom-Group-AVP:1300 is added to the current Diameter session. It adds the third party non-grouped AVP Custom-Member-AVP2:1300 as a new AVP to the current Diameter session with the specified value 9876 and this AVP can only be send if the policy is not rejected. It adds the third party non-grouped AVP Custom-Member-AVP1:1300 to the current Diameter session with the specified value 4566 and if there are multiple instances of this existing AVP the new value will be set to all of them and this AVP can be sent always regardless of the policy execution outcome.
Custom-Group-AVP (43,VM,v=1300,l=44) =
Custom-Member-AVP2 (1322,V,v=1300,l=16) = 9876
Custom-Member-AVP1 (1311,VM,v=1300,l=15) = 456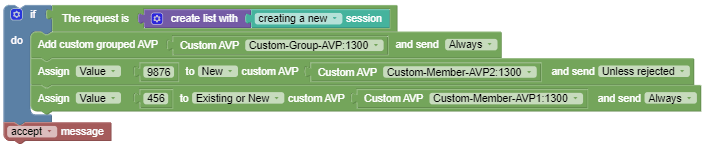
Use Case - Assign value to custom AVP and send response
The following screenshot shows a sample policy for Assign value to custom AVP and send response policy action:
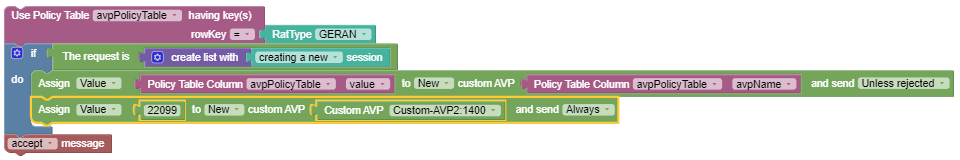
Use Case - Assign custom AVP value to the property
The following screenshot shows a sample policy for Assign custom AVP value to the propert name pname2:
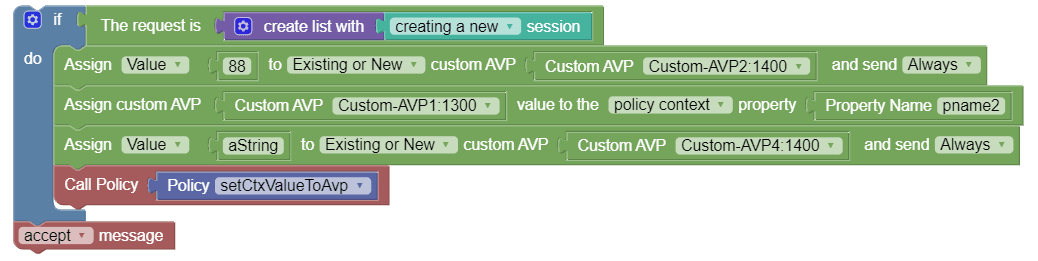
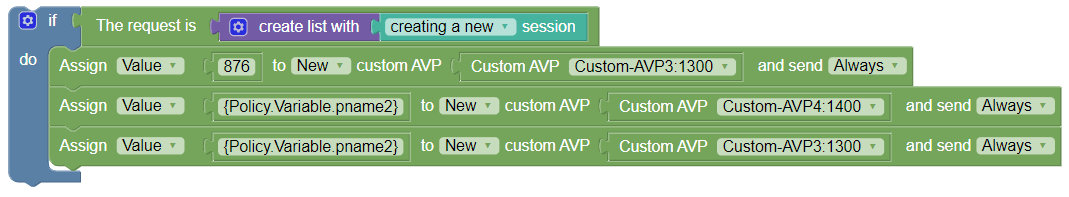
Use Case - Remove custom AVP from reply
The following screenshot shows a sample policy for Remove custom AVP policy action:
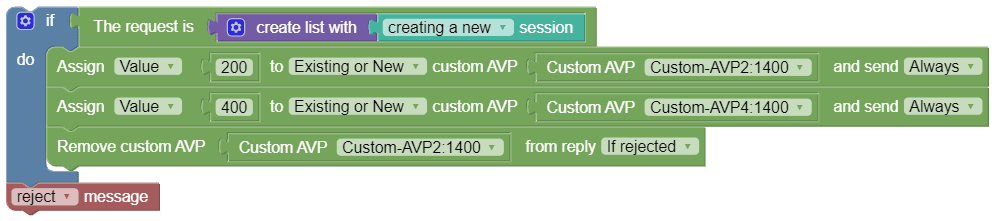
3.10.5 Closed User Group (CSG)
This section describes the Closed User Group (CSG) conditions and use cases for PCRF Core service.
3.10.5.1 Conditions
This section describes the policy conditions that can be used to configure AVP for PCRF Core service.
CSG Id exists
The CSG Id exists policy condition, as
shown in the following image, checks if user CSG id is
present or is null in request.
CSG Id value matches one of specified values
This policy condition, as shown in the following image, evaluates if the CSG Id value in the request matches or does not match with the one or more specified values in the string block.
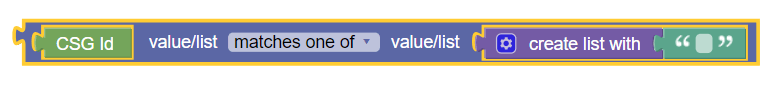
CSG Access Mode is closed
The CSG Access Mode policy condition, as shown in the following image, checks if user CSG Access Mode is equal to the specified value.
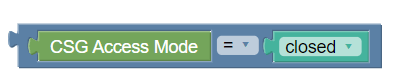
- Closed
- Hybrid
IP-CAN type
The IP-CAN type policy condition, as shown in the following image, triggers a policy that is only evaluated for a protocol message with a specific IP-CAN type.

- 3GPP_GPRS
- 3GPP_EPS
- NON_3GPP EPS
- 3GPP2
- WiMAX
- DOCSIS
- xDSL
Request Attribute present in specified match-list

UE is member of CSG
The UE is member of CSG policy condition, as shown in the following image, checks if UE is a member of CSG and returns a boolean value.

3.10.5.2 Use Cases
This section describes the use cases specific to CSG that can be used to configure AVP for PCRF Core service.
Use Case - CSG Access Mode
In the following sample policy, pccRule is installed if CSG Access Mode returns the
hybrid_mode string value from request. 
Use Case - CSG Id value matches one or more of specified values
In the following sample policy, pccRule is installed if CSG Id does not match with
the list with values ["123", "12"].
Use Case - UE is member of CSG
In the following sample policy, pccRule is installed if UE is not a member of
CSG.
3.10.6 Day/Time
Day and Time conditions, actions, and utils are related to the time at which the policy rules are being executed.
Configuring Local Time
- From the navigation menu, under PCRF, then under Services, click Core Service.
The Core Service screen appears.
- Click Edit to edit the core service configurations.
- In Advance Settings,
click Create.
The Create page appears.
- Enter DB.User.DefaultLocalTimeMode in the Key field.
- Enter True in the Value field.
- Click Save.
If no configuration is provided, the SYSTEM_LOCAL_TIME is considered as default local time.
3.10.6.1 Conditions
This section describes the conditions that can be used to configure day and time for PCRF Core service.
today is the specified day(s) of month in natural order using Configured Local Time
This policy condition, as shown in the following image, triggers a policy based on a day in a month. If current date matches specified number th day (a comma-delimited list of values) of specified months in natural order or reverse order as per the configured time then the condition returns true, otherwise false.

- January (default)
- February
- March
- April
- May
- June
- July
- August
- September
- October
- November
- December
- CONFIGURED_LOCAL_TIME (default)—Calculate the time from the location configured for this MPE device
- SYSTEM_LOCAL_TIME—Calculate the time from the location of this MPE device
- USER_LOCAL_TIME—Calculate the time from the location configured for the user equipment's location
the current time is within the Time Period
This policy condition, as shown in the following image, triggers a policy based on the time period. This condition gets time slots of all the time periods, and compares current time with these time slots. If the current time falls within the range of time slots configured in these time periods then the condition returns true, otherwise false.
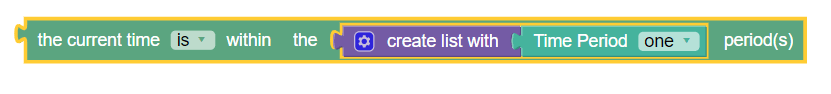
The Time Period drop-down field lists the time periods, configured using the Time Periods page on CNC Console. To navigate to the Time Periods page, click Policy, and then Policy Data Configurations. Select PCRF Core, and then click Time Periods.
the current time is between start time and end time using Configured Local Time
This policy condition, as shown in the following image, triggers a policy based on time. If the present time is between start time and end time then the condition returns true, otherwise false. If start time is greater than end time then the condition is evaluated, where the end time is considered as the next day.

Enter the start time and end time in the format of hh:mm, where hh is a number in the range from 0 to 23.
- CONFIGURED_LOCAL_TIME (default)—Calculate the time from the location configured for this MPE device
- SYSTEM_LOCAL_TIME—Calculate the time from the location of this MPE device
- USER_LOCAL_TIME—Calculate the time from the location configured for the user equipment's location
today is a week day using Configured Local Time
This policy condition, as shown in the following image, triggers a policy based on whether it is a week day or the weekend. If today is week day using the system time (CONFIGURED_LOCAL_TIME) then the condition returns true. If today is not week day using the system time, this policy condition returns false.

- CONFIGURED_LOCAL_TIME (default)—Calculate the time from the location configured for this MPE device
- SYSTEM_LOCAL_TIME—Calculate the time from the location of this MPE device
- USER_LOCAL_TIME—Calculate the time from the location configured for the user equipment's location
today is Day Sunday using Configured Local Time
This policy condition, as shown in the following image, triggers a policy based on the day of the week. If today is Sunday using the system time (CONFIGURED_LOCAL_TIME) then the condition returns true. If today is not Sunday using the system time, this policy condition returns false.
- Sunday (default)
- Monday
- Tuesday
- Wednesday
- Thursday
- Friday
- Saturday
- CONFIGURED_LOCAL_TIME (default)—Calculate the time from the location configured for this MPE device
- SYSTEM_LOCAL_TIME—Calculate the time from the location of this MPE device
- USER_LOCAL_TIME—Calculate the time from the location configured for the user equipment's location
the MSTimezone DST
The the MSTimezone DST policy condition triggers a policy that is only evaluated if the applied Daylight Saving Time offset for the location of a mobile subscriber or mobile station (MS) matches the parameter.
- = (default)
- !=
- <
- <=
- >
- >=
- Matches
- RegExp-Matches
the MSTimezone offset
The the MSTimezone offset policy condition triggers a policy that is only evaluated if the applied time zone for a mobile subscriber or mobile station (MS) matches the parameter.
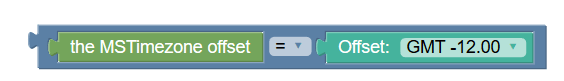
- = (default)
- !=
- <
- <=
- >
- >=
- Matches
- RegExp-Matches
3.10.6.2 Actions
This section describes the actions that can be used to configure day and time for PCRF Core service.
Set session revalidation time to earliest of specified time
- Time in the specified policy counter ID or IDs
- Time defined in the Seconds/Minutes/Hours/Days format from the time when a policy is executed
- Specific time in hh:mm format (limited to 15-minute intervals) on a specific day of the week using either SYSTEM TIME or UTC TIME time-zone.
- Random time between a time range
Figure 3-77 Set session revalidation time to earliest of

This action block is Policy table compliant.
In addition, you can check the Randomize checkbox to select a random revalidation time from the time range.
- "+": It adds the specified seconds to the time entered.
- "-": It subtracts the specified seconds from the time entered.
- "+/-": The range is defined by [ Time entered - specified seconds] to [ Time entered + specified seconds].
{"messageTimestamp":"2022-01-25T08:10:41.698Z","logLevel":"WARN","pid":14692,"workerId":2,"fileName":"lib\\services\\sm_core-service.js","lineNo":"25","message":"Applying randomization on earliest time}
"message":"Error!! Entered seconds is not a number for randomization !!Please enter number in seconds field."
Note: On upgrading to Policy 22.1.0 or later versions, the Set revalidation time to earliest of block is upgraded automatically in the existing policies.
3.10.6.3 Utils
This section describes the utils that can be used to configure day and time for PCRF Core service.
Offset
The Offset util can be combined with policy conditions and actions to specify a time zone.

Time Period
The Time Period util can be combined with policy conditions and actions to specify a time period.
The Time Period drop-down field lists the time periods, configured using the Time Periods page on CNC Console. To navigate to the Time Periods page, click Policy, and then Policy Data Configurations. Select PCRF Core, and then click Time Periods.
Day
The Day util can be combined with policy conditions and actions to specify the day.
- Sunday (default)
- Monday
- Tuesday
- Wednesday
- Thursday
- Friday
- Saturday
3.10.7 Identities/Addresses
The conditions categorized under Identities and Addresses are Policy Table compliant. The conditions can be used to manage policies for PCRF Core service.
3.10.7.1 Conditions
This section describes the conditions specific to user identities and addresses.
where the User IMSI
The where the User IMSI condition block, as shown in the following image, allows operators to identify users based on IMSI, E.164, NAI or SIP URI from the request received by the Policy Rule Engine.
User Equipment
The User Equipment condition block, as shown in the following image, allows operators to evaluate one or more IMEISV or MAC values. The evaluation is based on matching wildcard patterns. On selecting matches one of from the drop-down menu, if the IMEISV/MAC value matches with the address present in the JSON request, then the condition returns true, otherwise false.

Note:
A wildcard match pattern uses the * (asterisk) character to match zero or more characters and the ? (question mark) character to match exactly one character. It can be of form "*-*-56-*-*-D?" or "*:*:56:*:*:D?" and not like "00-*" etc.The Endpoint IP address
In the The Endpoint IP address condition block, as shown in the following image, the The Endpoint IP address child block fetches endpoints IP address from the JSON path, and then compares the retrieved value with the value provided in the string block. It supports both IPv4 and IPv6 addresses.
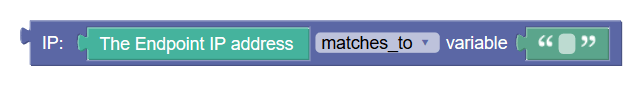
- matches_to - On selecting this value, the block performs a string comparison, and matches the retrieved value with the value provided in the string block.
- is_in_subnet - On selecting this value, the block performs a comparison based on node IP library, and verifies if the retrieved value is in subnet provided in the string block.
3.10.7.2 Use Cases
This section provides information about the use cases related to Identities/Addresses condition blocks.
Use Case - User Equipment
The following policy example shows a create request for a PCC rule when
MAC address matches the specified value, that is, "*:*:56:F2:*:*".
Use Case - The Endpoint IP Address
The following policy example triggers a policy when the endpoint IP
address matches 10.0.3.102:
3.10.8 Location/Presence
This section describes the conditions, actions, and utils specific to user location and presence reporting area.
3.10.8.1 Conditions
This section provides information on Location/Presence conditions available under PCRF Core Service.
The UE is inside/outside/inactive for PRA Area
This policy condition, as shown in the following image, triggers a policy that is only evaluated when the user equipment is or is not inside the subscribed PRA area.
![]()
Operators may select the location of the UE as inside, outside or inactive from the drop-down field.
The subscribed PRA area matches/does not match one or more PRA areas
This policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specific PRA values. If default area is selected as the definition for the parameter pra-areas, the policy is only evaluated if the user equipment is already subscribed to a PRA.
![]()
- CMP defined PRA lists
Select one or more defined PRA lists
- Manual Input
Enter the identifier for the PRA in hexadecimal format or a custom PRA from a subscriber profile in the format {User.CustomField}.
The manual input format for multiple PRAs is:PRA identifier1 [;PRA element list1],PRA identifier2 [; PRA element list2],…The format of PRA identifier and PRA Element List is according to section 8.108 of TS 29.274[9]. It is specified in Hexadecimal format. If only has a PRA identifier then the PRA area is a predefined PRA area. If both PRA identifier and PRA Element List exists, then it is a UE-dedicated PRA Area. The manual input is typically used to input a temporally PRA area. The manual input can also be used to get a PRA area from Custom field of subscriber. For example, {User.Custom4}. If the operator wants to manually input a PRA area they need to get the Hexadecimal value for each. Different vendors/operators should interact or exchange PRA info using the Hexadecimal representation as defined in section 8.108 of TS 29.274[9].
The manual input format for a single PRA is:PRA identifier [, PRA element list] - Default
The PRA to which the user equipment is already subscribed, if any.
The Default option specifies using the default PRA area. The default PRA is the PRA area subscribed or provisioned by the PCRF for the UE during IP-CAN session life cycle. It is either a UE- dedicated or predefined PRA area. It can be a PRA area that is retrieved from the subscriber profile (normally UE-dedicated) or a PRA area defined in the CMP (normally predefined). When used , this Default option means to check whether the UE has subscribed to a PRA area but does not care what the PRA area is.
Routing Area Identifier
The Routing Area Identifier policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specified Routing area identifier values (based on matching wildcard patterns).
Note:
To know more about the format of routing area identifier, see the 3GPP TS 23.003 standard.Serving MCC-MNC
The Serving MCC-MNC policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specific mobile country code (MCC)-mobile network code (MNC) values. A valid value consists of a 3-digit mobile country code and a 2- or 3-digit mobile network code, such as 123045.
Location Area Code
The Location Area Code policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specified Location area code values (based on matching wildcard patterns).
A valid location area code is an integer between 0 and 65535.
Service Area Code
The Service Area Code policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specified Service area code values (based on matching wildcard patterns).
![]()
A valid service area code is an integer between 0 and 65535.
Routing Area Code
The Routing Area Code policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specified Routing area code values (based on matching wildcard patterns).
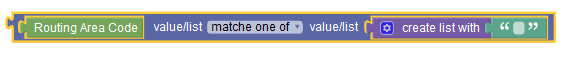
Tracking Area Code
The Tracking Area Code policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specified Tracking area code values (based on matching wildcard patterns).
![]()
E-UTRAN Cell Identifier
The E-UTRAN Cell Identifier policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specific E-UTRAN Cell Identifier values (based on matching wildcard patterns).

The values specified in the string block can be a comma-separated list of values, where each value is a wildcard match pattern that uses the * (asterisk) character to match zero or more characters and the ? (question mark) character to match exactly one character.
Cell Identifier
The Cell Identifier policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specific Cell Identifier values (based on matching wildcard patterns). A valid Cell Identifier is an integer between 0 and 65535.

The values specified in the string block can be a comma-separated list of values, where each value is a wildcard match pattern that uses the * (asterisk) character to match zero or more characters and the ? (question mark) character to match exactly one character.
3.10.8.2 Actions
This section describes the actions specific to Presence Reporting Area, which can be used to create and manage policies for PCRF Core service.
Remove/Install/Subscribe PRA change for PRA Area(s)
This policy action, as shown in the following image, subscribes the user equipment to PRA changes in the specified PRA. If default area is selected as the definition for the parameter pra, subscribes the user equipment to PRA changes in the last subscribedPRA.
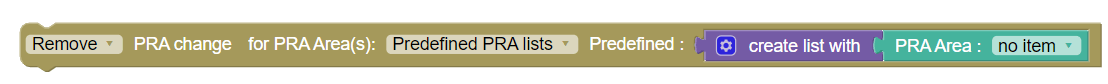
- predefined PRA list — select a defined PRA list
- manual input — enter the identifier for the PRA in hexadecimal format or a custom PRA from a subscriber profile in the format {User.CustomField}.
- default area - the last PRA to which the user equipment was subscribed
PRA Subscription
This policy action, as shown in the following image, enable or disable PRA subscriptions.
3.10.9 Network Device Conditions
Network Device conditions are related to the specific network device for which the policy rule is being evaluated. This includes conditions based on the network device type, as well as those that refer to specific unique identifiers for network devices.
3.10.9.1 Conditions
This section provides information on conditions for Network Devices, available under PCRF Core service.
Enforcement network element type
The enforcement network element type policy condition, as shown in the following image, triggers a policy when enforcement network element type contains any, none or all the specified value of Device type.

- PGW
- GGSN
Enforcement network element name
The Enforcement network element name policy condition, as shown in the following image, triggers a policy when enforcement network element name block contains any, all or none of the specified one or more values in the string block.
Figure 3-78 Policy condition for enforcement network element name

identity of requesting network element
The identity of requesting network element block condition, as shown in the following image, triggers a policy when the identity of networking element, that is, ORIGIN_HOST AVP matches one of or does not match specified values or lists.
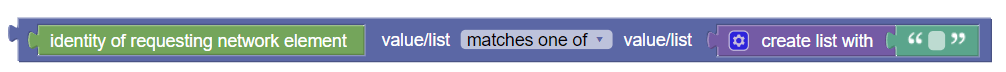
Note:
The wildcards * (asterisk) and ? (question mark) are allowed for entries in the match-list.An-Gw Status
The An-Gw Status policy condition, as shown in the
following image, triggers a policy based on whether the An-Gw status is active or
inactive. It compares the An-Gw status selected from the drop-down field with An-Gw
status read from JSON (which is sent from PCRF-Core to PRE). 
- AN_GW_FAILED
- AN_GW_ACTIVE
Note:
The AN_GW_FAILED value indicates that the AN-Gateway has failed and that the PCRF should refrain from sending policy decisions to the PCEF until it is informed that the AN-Gateway has been recovered. This value shall not be used if the IP-CAN Session Modification procedure is initiated for PCC rule removal only.In place of the dropdown, a string block can also be used, as shown in
the following image:
IP Address of the Serving Gateway
The IP address of the Serving Gateway policy condition, as shown in the following image, triggers a policy that is only evaluated for one or more specific Serving Gateway addresses (based on matching wildcard patterns).

The Serving Gateway addresses in the string block can be a comma-separated list of values, where each value is a wildcard match pattern that uses the * (asterisk) character to match zero or more characters and ? (question mark) character to match exactly one character.
3.10.10 Priority/Emergency
This section describes the policy conditions and actions for multimedia priority support and emergency sessions.
3.10.10.1 Conditions
This section describes the conditions specific to multimedia priority support and emergency sessions.
Media component description reservation priority
This policy condition, as shown in the following image, selects Rx protocol messages
based on the requested media component description reservation priority.
- DEFAULT
- PRIORITY_ONE
- PRIORITY_TWO
- PRIORITY_THREE
- PRIORITY_FOUR
- PRIORITY_FIVE
- PRIORITY_SIX
- PRIORITY_SEVEN
- PRIORITY_EIGHT
- PRIORITY_NINE
- PRIORITY_TEN
- PRIORITY_ELEVEN
- PRIORITY_TWELVE
- PRIORITY_THIRTEEN
- PRIORITY_FOURTEEN
- PRIORITY_FIFTEEN
Media Type
- AUDIO
- DATA
- VIDEO
- TEXT
- CONTROL
- APPLICATION
- MESSAGE
- OTHERS
Figure 3-79 Media Type

AF Application Identifier
This policy condition indicates the particular service that the AF session belongs to. This AVP can be provided at both AF session level, and Media-Component-Descriptionlevel. When provided at both levels, the AF-Application Identifier provided within the Media-Component-Description AVP will have precedence.
Figure 3-80 AF Application Identifier

MCPTT Identifier
This policy condition indicates that the new AF session relates to an MCPTT session with priority call. If PCRF receives the MCPTT-Identifier AVP related to that MCPTT session, PCRF can take specific actions on the corresponding IP-CAN to ensure that the MCPTT session is prioritized.
Figure 3-81 MCPTT Identifier

MCVideo-Identifier
This policy condition indicates that the new AF session relates toan MCVideo session with priority call. If PCRF receives the MCVideo-Identifier AVP related to that MCVideosession, PCRF can take specific actions on the corresponding IP-CAN to ensure that the MCVideo session isprioritized.
Figure 3-82 MCVideo Identifier

Session reservation priority is
This policy condition, as shown in the following image, selects Rx protocol messages based on the requested session reservation priority.

- DEFAULT
- PRIORITY_ONE
- PRIORITY_TWO
- PRIORITY_THREE
- PRIORITY_FOUR
- PRIORITY_FIVE
- PRIORITY_SIX
- PRIORITY_SEVEN
- PRIORITY_EIGHT
- PRIORITY_NINE
- PRIORITY_TEN
- PRIORITY_ELEVEN
- PRIORITY_TWELVE
- PRIORITY_THIRTEEN
- PRIORITY_FOURTEEN
- PRIORITY_FIFTEEN
MPS identifier
The MPS identifier policy condition, as shown in the following image, determines the value of the MPS identifier.

the Service-URN is one of specified value(s)
This policy condition, as shown in the following image, selects Rx protocol messages based on the value of the Service-URN field.
3.10.10.2 Actions
This section describes the actions that can be performed to configure multimedia priority support and emergency sessions.
set GCS ARP to specified Priority Value with Preemption Capability and Preemption Vulnerability enabled
This policy action overrides the default ARP settings for eMPS or GCS ARP. The priority level defines the relative importance of a resource request. Enter a value from 1 to 15. The default is 1.

The Preemption Capability defines whether a service data flow can get resources that were assigned to another service data flow with a lower priority level. Select Enable (default) or Disable from the drop-down field.
The Preemption Vulnerability defines whether a service data flow can release the assigned resources so that a service data flow with a higher priority level can be admitted. Select Enable (default) or Disable from the drop-down field.
set DRMP AVP to specified priority in Re-Authorized Request
This policy action sets the priority level of the Diameter routing message priority (DRMP) AVP for Gx: RAR messages. Select one of the drmp-level values from the drop-down field, where PRIORITY_0 is the highest priority and PRIORITY_15 is the lowest priority.
3.10.11 Roaming
This section describes the policy conditions that can be used to configure policies for roaming scenarios under PCRF Core service.
3.10.11.1 Conditions
This section describes the conditions categorized under Roaming for PCRF Core service.
User is Home
The User is Home policy condition, as shown in the following image, evaluates whether the user is a home user or a visitor.
Current mobile country code
The Current mobile country code policy condition, as shown in the following image, retrieves the current mobile country code of the user from the request received by PRE.

3.10.12 Rules/Flows
This section describes the conditions and actions that can be used to configure rules and flows to manage policies for PCRF Core service.
3.10.12.1 Conditions
This section describes the conditions that can be used to configure rules and flows to manage policies for PCRF Core service.
Rule report contains one of rule name(s) and the rule status is Active
This policy condition, as shown in the following image, triggers a policy when the rule report contains one of the specified rule name(s) and the rule status for the specified rule name is active. This policy condition is policy table compliant.

- ACTIVE
- INACTIVE
- TEMPORARILY_INACTIVE
Rule report contains one of rule name(s) and the rule status is Active and the Final Unit Action is one of specified failure code(s)
This policy condition, as shown in the following image, triggers a policy when the rule report contains one of the specified rule name(s) that is active, and has final unit action as one of the specified values. In place of active rule names, the policy condition can evaluate policy for inactive or temporarily inactive rule names as well.

Instead of Final Unit Action, user can select Rule Failure Code and specify values for policy evaluation.
This policy condition is policy table compliant.
Flow type
The flow type policy condition, as shown in the following image, triggers a policy that is only evaluated for a specific flow type.

- UE_FLOW (default)
- AF_FLOW
- PCC_RULE_FLOW
- ENF_APP_FLOW
Flow request type
The flow request type policy condition, as shown in the following image, triggers a policy that is only evaluated for a specific flow request type.

- TYPE_NOCHANGE (default)
- TYPE_CREATE
- TYPE_MODIFY
- TYPE_DELETE
- TYPE_PROVISION
the name(s) of the installed PCC/ADC rules contains one of specified PCC/ADC rules
This policy condition, as shown in the following image, triggers a policy when the installed PCC or ADC rules contains one of the specified PCC or ADC rules.

3.10.12.2 Actions
This section describes the policy actions that can be applied to configure rules and flows for PCRF Core service.
Apply QoS and Charging Parameter Values
The following policy action can be used to apply the QoS and charging parameter values for a particular session flow:

The following is a sample policy rule to
apply QoS and charging parameters to all the session flows:
The following is a sample policy rule to apply QoS
and charging parameters on a particular session flow:
Apply Traffic Profile to All flows in the request with FlowInfo
This policy action, as shown in the following image, applies one or more traffic profiles to all flows or a specific flow with FlowInfo. It overwrites the corresponding settings in the protocol messages of the specified flows. If multiple traffic profiles are selected, they are applied in the order in which they are specified. If a traffic profile contains settings that are not relevant in the current protocol message, they are ignored. This policy condition is Policy Table compliant.

remove PCC rule for the specified flow
This policy action, as shown in the following image, removes the policy and charging control role from the current flow. Users can select either ENF_APP_FLOW or UE_FLOW from the drop-down list.
Install PCC Rules for specified scope
This policy action, as shown in the following image, installs or removes specified list of PCC Rules for a defined scope.

- SCOPE_SESSION
- SCOPE_FLOW
- SCOPE_ALL
Install PCC Rule with specified Active and Inactive time
The following policy action allows users to install PCC Rules for a specified time duration.
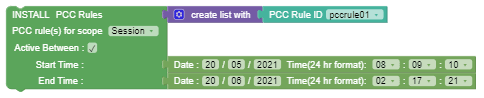
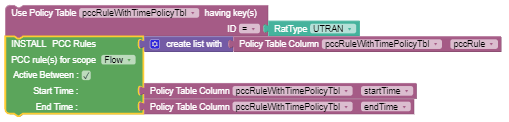
- Start time only - PCC rule becomes active at the
specified time with a null value for the end time.
Note:
To install a rule at the current system time, users are recommended to not use any block to specify the Start Time. Instead, leave the Start Time empty and the Rule-Activation-Time gets installed at the current system time in CCA. - End time only - PCC rule takes current time as start time and gets inactive at the specified time.
- Both Start time and End time - PCC rule remains active between the specified duration.
- Date and time block
- Relative Time
- now
- YYYY-MM-DDThh:mm:ss+UTCoffset
When the Active Between check box is deselected, the PCC rule is installed and becomes active (taking current time as default) with no end time.

The following screenshot shows a
sample policy that installs pccRule2 and sets values for
Rule-Activation-Time and
Rule-Deactivation-Time as Sat Jun 19 16:03:07 UTC
2021 and Fri Aug 20 02:04:54 UTC 2021
respectively.
The installed pccRule2 remains active from
specified start time to end time. It also sets the
Revalidation-Time, which is same as the
Rule-Deactivation-Time.
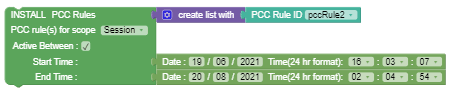
Remove all ADC rules
This policy action, as shown in the following image, removes all the ADC rules from the current flow. Users can select the session scope using the dropdown.
Remove ADC rule for the specified flow
This policy action, as shown in the following image, removes the specified ADC rule from the current flow. Users can select the ADC Rule ID using the dropdown.

Install ADC Rule with specified Active and Inactive time
The following policy action allows users to install ADC Rules for a specified time duration.
- Start time only - ADC rule becomes active at the specified time with a null value for the end time.
- End time only - ADC rule takes current time as start time and gets inactive at the specified time.
- Both Start time and End time - ADC rule remains active between the specified duration.
When the Active Between check box is deselected, the ADC rule is installed and becomes active (taking current time as default) with no end time.

Set values for Charging Server parameters
The following policy action can be used to set values for online or offline charging servers:
- Primary Online
- Secondary Online
- Primary Offline
- Secondary Offline
The Charging Server blocks are Policy Table compliant.
The following is a use case to configure Charging Server using the Policy Table block:
The following screen capture illustrates a charging server Policy Table configured on Policy GUI:
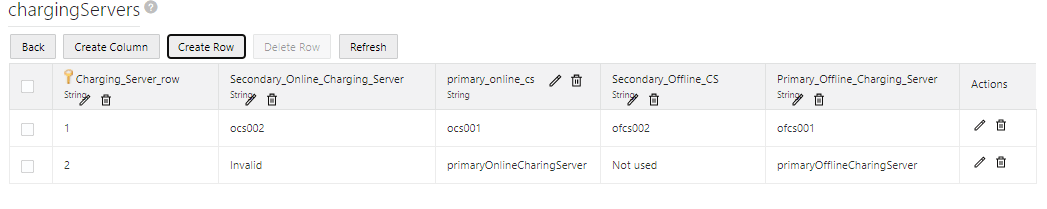
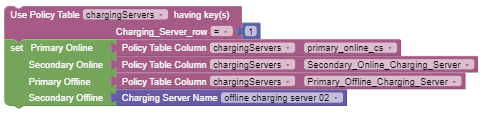
In the above example, the charging server Policy Table is already configured. You can select the particular row from the Policy Table. For more information, see Policy Table.
Add or override Conditional Policy Information with Execution-Time and specified parameters
The following policy action allows users to add a new Conditional-Policy-Information AVP with specified parameter values to the existing list of Conditional-Policy-Information AVPs. By selecting override value, user can replace an existing list of Conditional-Policy-Information AVPs.

- Date and time block
- Relative Time
- now (the local date and time)
- Date and time in the format: YYYY-MM-DDThh:mm:ss+UTCoffset
- Diameter APN-Aggregate-Max-Bitrate-UL
- Diameter APN-Aggregate-Max-Bitrate-DL
- Diameter Default EPS Bearer QCI
- Diameter Default EPS Bearer ARP Priority Level
- Diameter Default EPS Bearer ARP Preemption Capability
- Diameter Default EPS Bearer ARP Preemption Vulnerability
Remove PCC Rules for a Defined Scope
This policy action removes the specified PCC rule for a defined scope as shown in the following image:
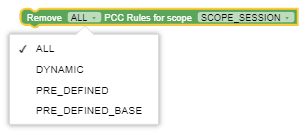
- ALL
- DYNAMIC
- PRE_DEFINED
- PRE_DEFINED_BASE
- SCOPE_SESSION
- SCOPE_FLOW
- SCOPE_ALL
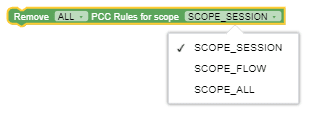
Use case: The following image shows a sample policy when Dynamic is set for Remove field and SCOPE_ALL is set for PCC Rules for scope field:

The return-CCA must include:
Charging-Rule-Remove (1002,VM,v=10415,l=32) = Charging-Rule-Name
(1005,VM,v=10415,l=20) = pccRule1
Use case: The following image shows a sample policy when ALL is selected for the Remove field and PCC Rules for scope is set to SCOPE_ALL:

The return-CCA must include:
Charging-Rule-Remove (1002,VM,v=10415,l=84) = Charging-Rule-Name
(1005,VM,v=10415,l=20) = pccRule1 Charging-Rule-Name (1005,VM,v=10415,l=24) =
predPccRule1 Charging-Rule-Base-Name (1004,VM,v=10415,l=28) =
predPccRuleBase1
3.11 Context Menu Options for All Blocks
The following table provides details about the context menu options for all the blocks:
Table 3-12 Context Menu Options
| Menu Options | Description |
|---|---|
| Duplicate | Creates a copy of this block. |
| Add Comment | Insert comments into the block. |
| Collapse Block | Compresses the elements within the block. |
| Disable Block | Deactivates or disables the block. |
| Delete Block | Removes the block. |
| Help | Opens Google Blockly webpage. |