6 The Dashboard
The Oracle® Communications Security Shield Cloud Service (Security Shield) Dashboard displays information about the SIP call traffic crossing your telephony network boundary and provides tools to help you manage its security. Some tools are interactive, where you can change certain settings from the Dashboard to quickly respond to traffic conditions. The Dashboard also reports on the state of your network devices, as well as the enforcement actions that the Security Shield applied according to the policies and thresholds you set.
- View detected threats and take action on potential security threats and possible fraud, for example, by specifying thresholds on call activities.
- View specific details about calls that applied enforcement action, for example, blocked calls and re-directed calls.
- View and manage the status of connected devices such as the Session Border Controllers, for example, so you can see which devices are in and out of service.
- View metrics about answered trusted outbound enterprise calls.
- View details about your subscriptions, such as usage and expiration dates.
Topics:
Dashboard Controls and Actions
The Dashboard displays tabs with visual representations of information about Oracle® Communications Security Shield Cloud Service (Security Shield) services and call traffic crossing your telephony network boundary. The information reflects recent activity and refreshes each time you access the Dashboard and periodically refreshes as configured with the Auto Refresh setting.
The tabs on the Dashboard provide you with a complete view of how, why, and when Security Shield protected your telephony network within the last 24 hours. The following screen capture shows an example of the Dashboard including the Answered Outbound Calls scoreboard tab that displays with the optional Trusted Enterprise Calls subscription.
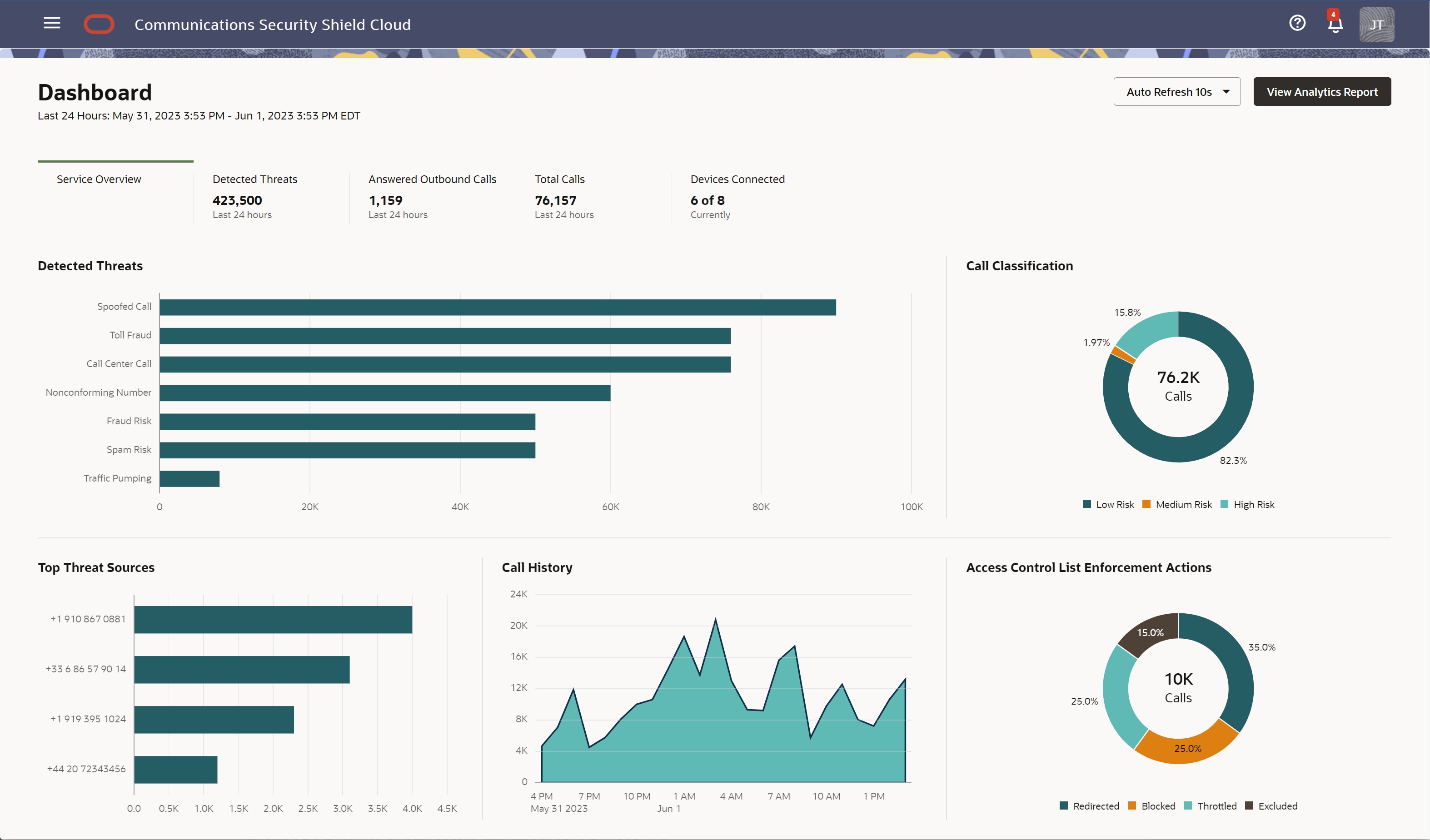
Auto Refresh―While viewing the dashboard, the refresh rate depends on the setting you configure for auto-refresh. To refresh the data while viewing the dashboard, rather than re-launching the dashboard to force the update, you can set the refresh rate at 10, 30, 60, or 90 seconds with the Auto Refresh control. The default is every 10 seconds.
View Analytics Report―When you want to investigate your inbound and outbound call traffic, as well as anomalies, suspicious behavior, and malicious traffic, click Analytics Report.
Last 24 Timestamp―The 24-hour period for which the Dashboard displays data. The Dashboard uses the local date and time where the browser is launched.
Metrics Cards―The Service Overview tab displays interactive metrics cards that provide key performance indicators. When you hover over certain areas of the metrics cards, the Dashboard displays more granular data. The available metric cards depend on the subscription you purchase.
- When you purchase the Trusted Enterprise Calls subscription with either the Standard or Premium subscription, Security Shield adds the Answered Outbound Calls metrics card to the Dashboard along with the others.
- When you purchase only the Trusted Enterprise Calls subscription, the Dashboard displays only the Answered Outbound Calls and Devices Connected metrics cards. Security Shield hides the others.
Note:
No data displays on the Dashboard until you connect the on-premises devices and the Security Shield service starts processing calls.The Service Overview Scoreboard
The Oracle® Communications Security Shield Cloud Service (Security Shield) Service Overview scoreboard displays charts and graphs showing the state of call traffic in your telephony network within the last twenty-four hours.
The following screen capture shows an example of the Service Overview scoreboard with data.
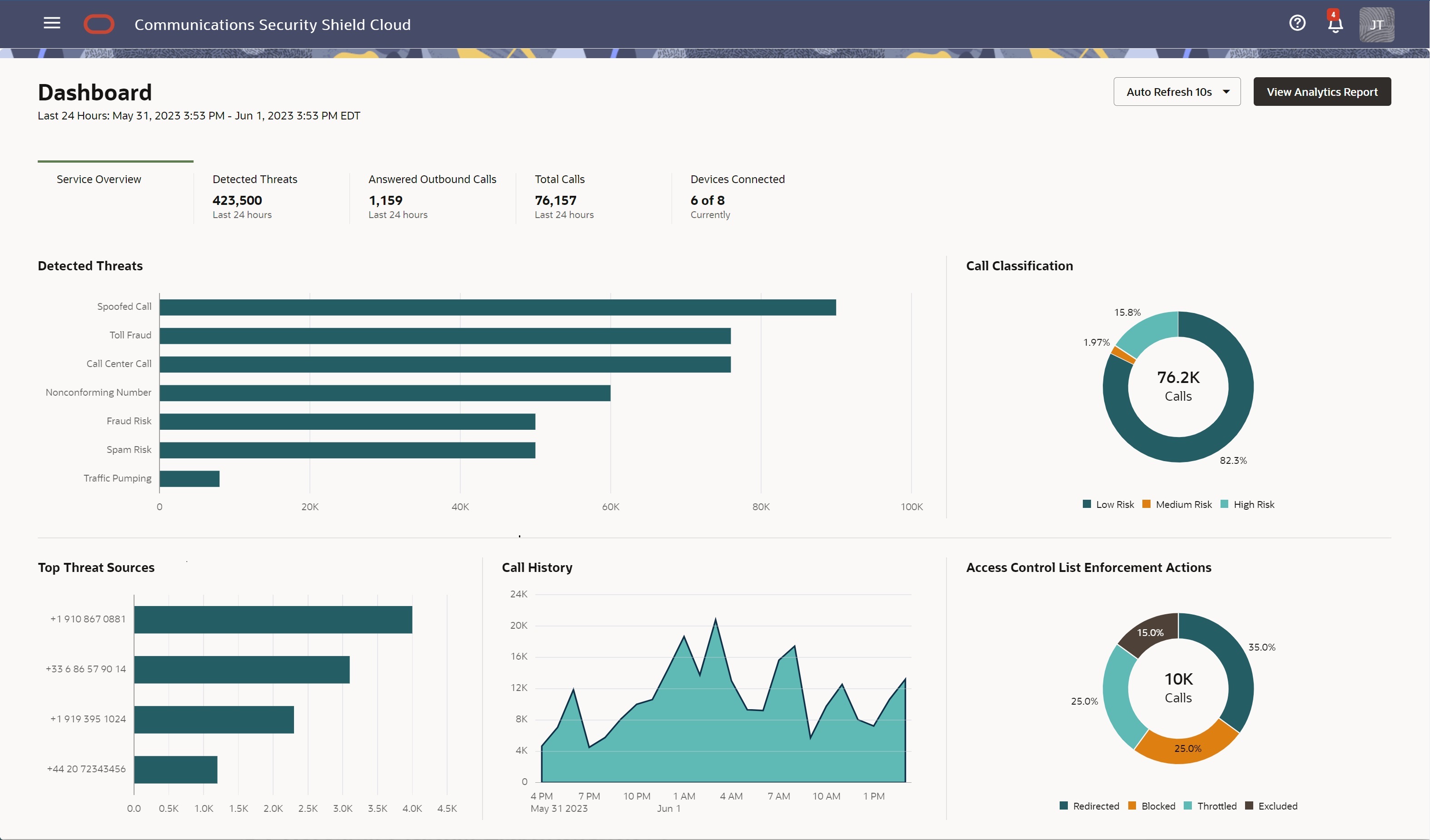
Detected Threats―Shows the number of threats per threat type such as Toll Fraud, Traffic Pumping, Fraud Risk, Spam Risk, Call Center Call, Spoofed Call, Non-conforming Number, High Risk, and Medium Risk calls.
Call Classifications―Shows the number of threats per call classification type such as Low Risk, Medium Risk, and High Risk.
Top Threat Sources―Shows the phone numbers of the top sources of threats in the categories of Allowed, Throttled, Blocked, and Redirected calls.
Call History―Shows the total numbers of calls processed in the last twenty four hours. You can hover over a particular point in time to see more details.
Access Control List Enforcement Actions―Shows the number of calls affected by your Access Control Lists, such as Throttled, Blocked, Redirected, and Excluded calls. When you hover over a section of the chart, the system shows the action taken and the number of call actions for the type.
The Detected Threats Scoreboard Metrics Card
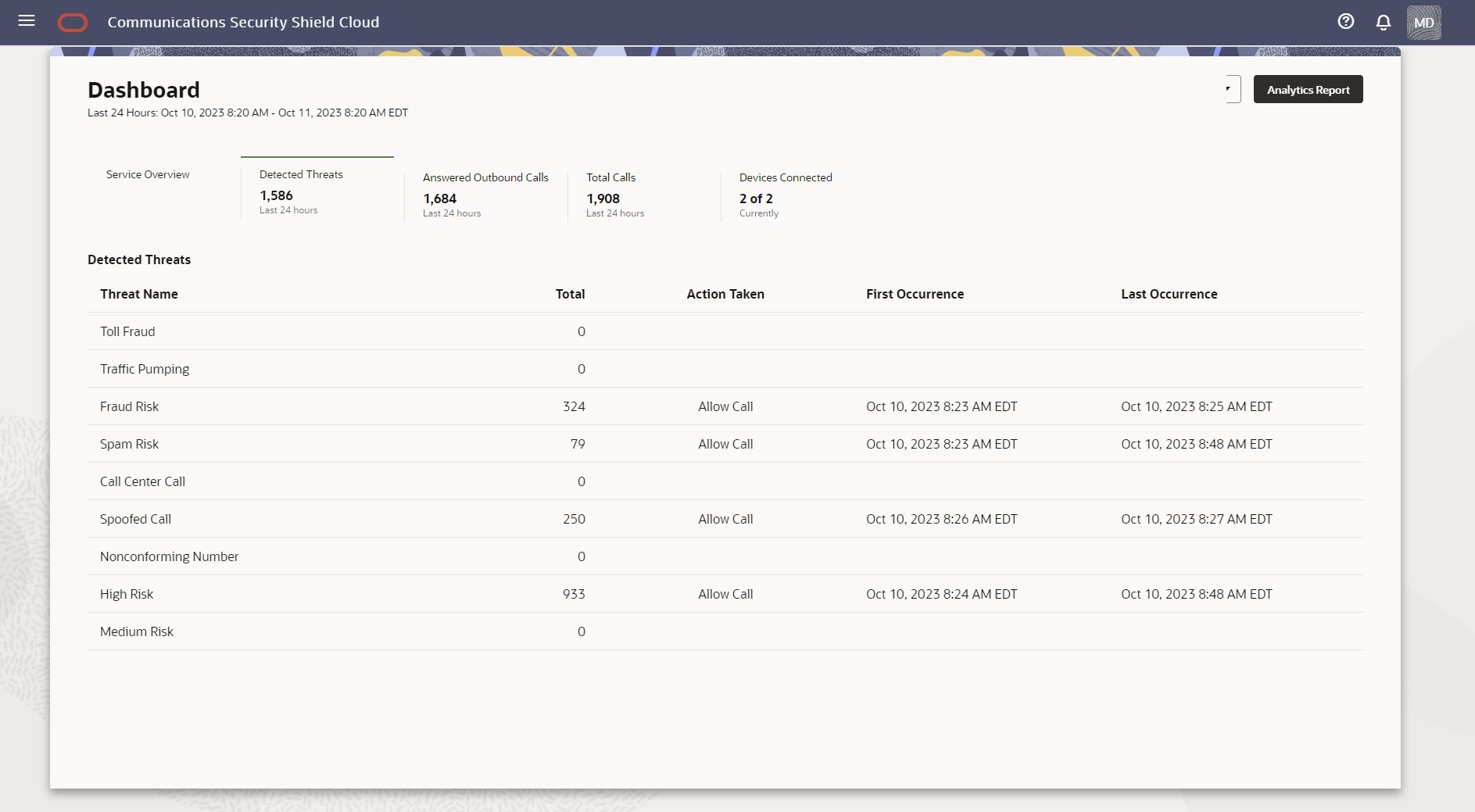
The Detected Threats scoreboard metrics card shows the total number of threats Oracle® Communications Security Shield Cloud Service (Security Shield) detected in the last twenty-four hours. The card displays a breakdown of the number of each threat type detected along with the last action taken and the date and time of the first and last occurrence.
The following screen capture shows the Premium Subscription Detected Threats scoreboard metrics card with sample data.
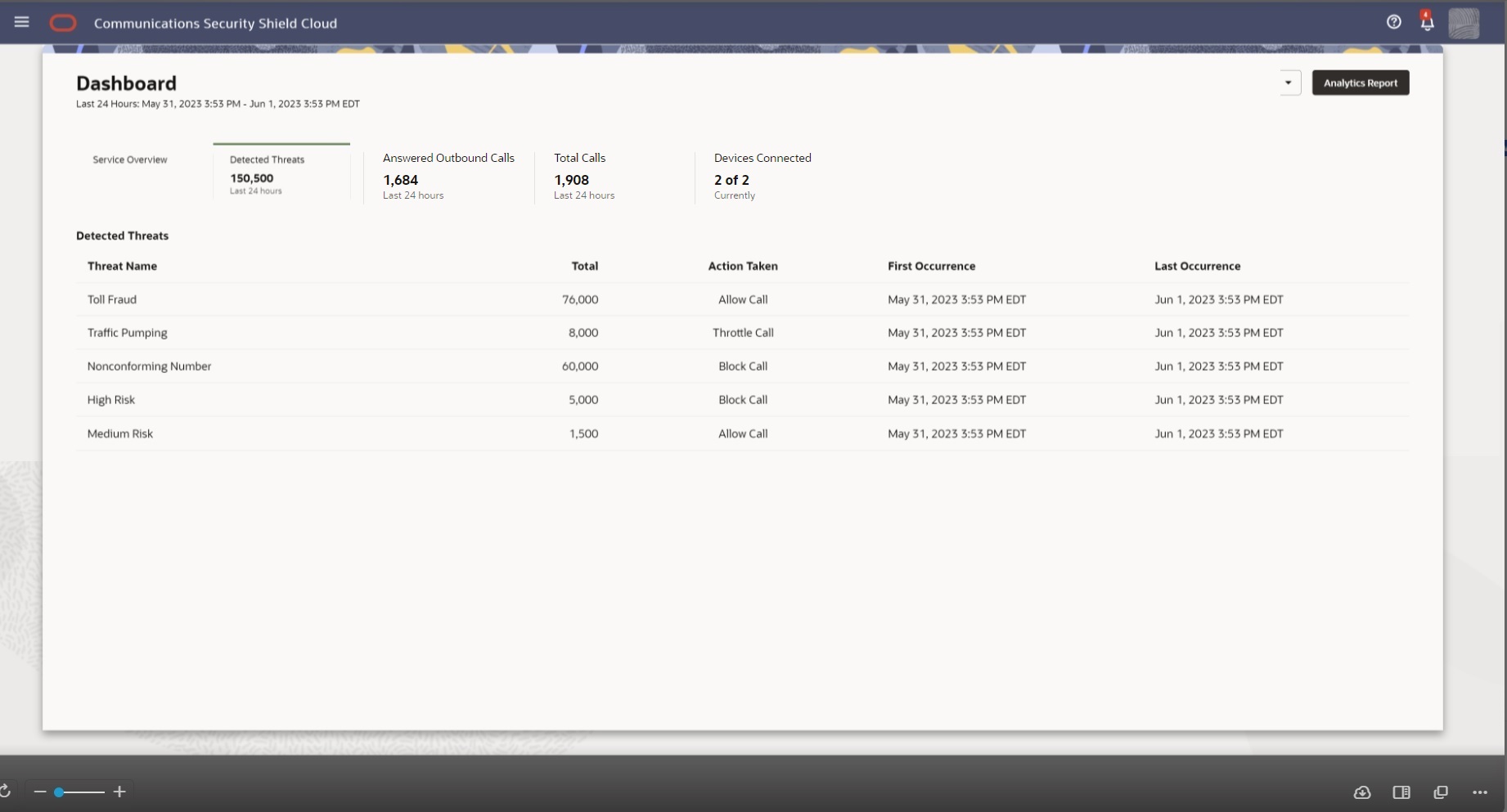
The following screen capture shows the Standard Subscription Detected Threats scoreboard metrics card with sample data.
Note:
The Answered Outbound Calls tab displays only for Trusted Enterprise Calls subscribers.Threat Descriptions
Toll Fraud―Indicates that perpetrators accessed a company's phone lines then used those lines to call premium rate numbers that they have set up. The unsuspecting company must pay the bill. (Standard and Premium)
Traffic Pumping―Indicates calls that exceeded the configured upper threshold of the call attempt rate for five minutes. (Standard and Premium)
Fraud Risk―Indicates high-risk unwanted calls likely originating from entities posing as legitimate callers with malicious intent, such as to defraud you. This is not a call from a Fraud Risk department. (Premium) Security Shield classified the call as a fraud risk, due to association with known scams or dangerous activity. Administrators typically set the enforcement action to Redirect Call for advanced authentication or Block.
Spam Risk―Indicates Spam or other unwanted calls from suspect phone numbers, such as phone numbers that originate large numbers of robocalls. Security Shield classified the call as Spam, due to the caller's patterns indicative of spam calls. Administrators typically set the enforcement action to Block. (Premium)
Call Center Call―Indicates wanted call notifications from direct marketers of goods and services to potential customers. Such calls include verification codes, appointment reminders, school announcements, and so on. Security Shield classified the call as a Call Center Call, due to potential value to the recipients. Administrators typically set the enforcement action to Continue. (Premium)
Spoofed Call―Indicates calls originating from an entity that disguised the caller's identity, hijacked the phone number, used a recently unassigned phone number, and other calls that do not fit into the other classifications. For example, an incorrectly entered phone number might classify as a Spoofed Call. Administrators typically set the enforcement action to Block. (Premium)
Nonconforming Number―Indicates the calling number does not conform to E.164 conventions after number normalization. Possible reasons include errors in one or more normalization rules, incorrect number length, or the number contains prefixes and suffixes. A nonconforming number might also indicate a threat. (Standard and Premium)
High Risk―Indicates that there is no long-term activity and there is activity towards a high number of different phone numbers and unassigned phone numbers. Significant risk factors also include no long-term activity and high short-term activity. (Standard and Premium)
Medium Risk―Indicates activity that is call center-like, sparse, directed towards a high number of premium numbers, or comes from a high number of toll-free numbers. Significant risk factors also include a high number of completed calls and irregular call duration. (Standard and Premium)
Enforcement Actions Taken Descriptions
Block Call―Stops the call from proceeding.
Redirect Call―Directs the call to a number you specify in the Access Control List rule.
Note:
You might see some fluctuation where the actual value sometimes differs from the configured value.Exclude―Allows inbound calls while still evaluating against Traffic Pumping, Spoofing, and Toll Fraud threat detection. Exclude ignores the risk assessment and classifies excluded calls as "Good". The Exclude action does not evaluate against Fraud Risk, Spam Risk, and Call Center call detection.
Allow―Allows the call to proceed under the following conditions:- When the Access Control List enforcement action is set to Allow, Security Shield allows the call regardless of the enforcement action set for the reputation score.
- When the response code from the call look-up is anything but Continue, Security Shield performs the specified action.
- When the response code from the call look-up is set to Continue, the call type is reported and no call enforcement is associated with this detection. Call enforcement depends on other threats detected or the reputation score enforcement and associated settings.
Note:
When there is a conflict between the Call Classification Type action and the Reputation Score Classification action, the Call Classification Type setting takes precedence.
The Answered Outbound Calls Scoreboard Metrics Card
Oracle® Communications Security Shield Cloud Service (Security Shield) adds the Answered Outbound Calls scoreboard metrics card to the Dashboard when you purchase the Trusted Enterprise Calls subscription. The tab displays charts and graphs showing metrics about your attested and unattested outbound calls.
The following screen capture shows the Answered Outbound Calls scoreboard metrics card with sample data.
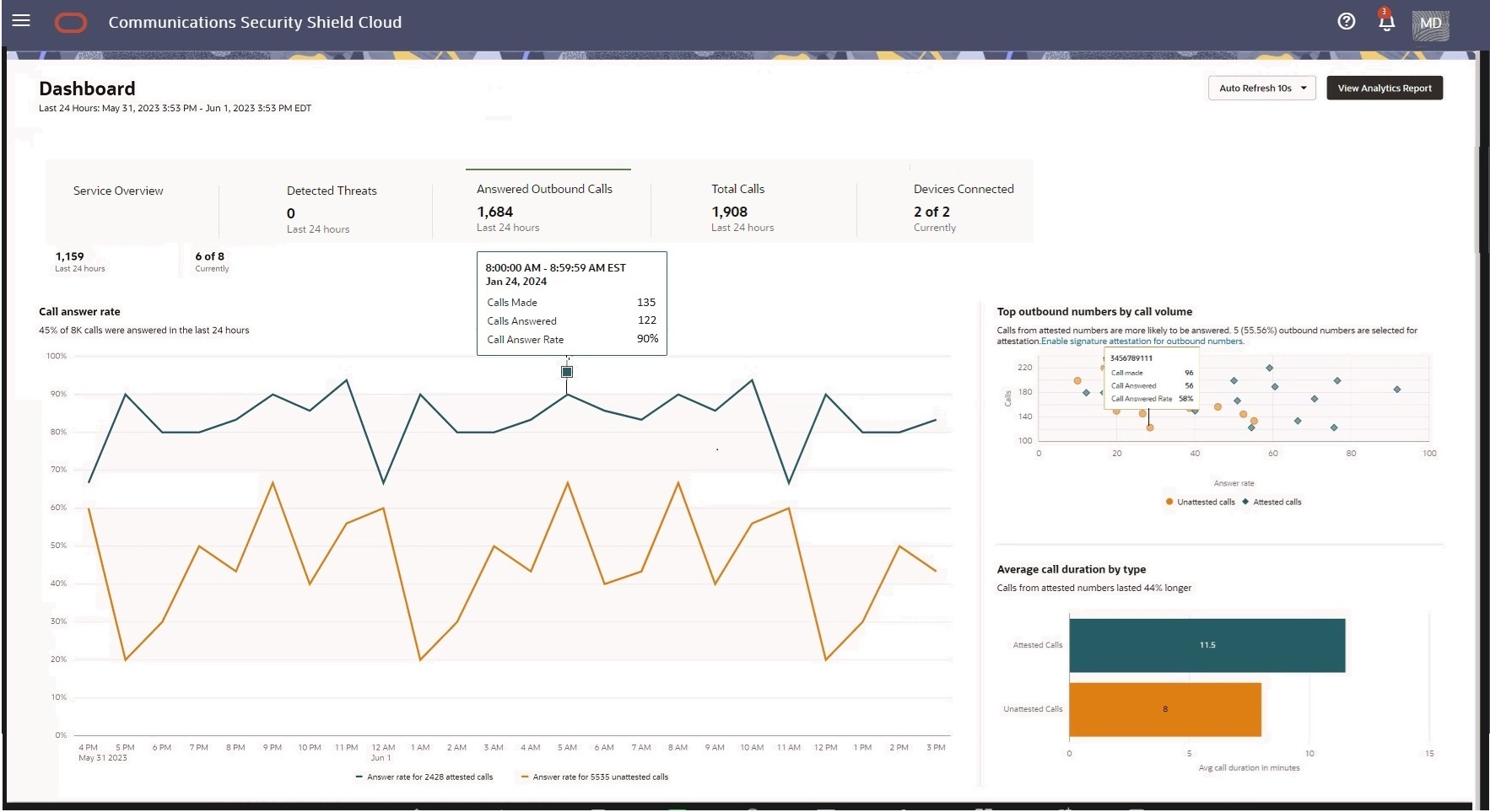
Graph Descriptions
Call Answer Rate—Shows the percentage of the number of outbound calls that were answered in the last twenty-four hours. One line shows the answer rate for attested calls and the other line shows the answer rate for unattested calls. When you hover over any point in time on either line, Security Shield displays the timestamp, number of calls made, number of calls answered, and the call answer rate.
Top Outbound Numbers by Call Volume—Shows the top fifteen attested and unattested outbound phone numbers used in the last twenty-four hours. When you hover over a call bubble (round for unattested calls and diamond shaped for attested calls), Security Shield displays the number of calls made from the selected number, the number of those calls that were answered, and the call answer rate. To enable an unattested phone number for attestation, click the "Enable signature attestation for outbound numbers" link. Security Shield displays the Outbound Number Management page where you can enable the phone number for call signing and attestation. Security Shield logs the change in the Activity Log.
Average Call Duration by Type—Shows the duration of attested and unattested calls in minutes and how much longer attested calls lasted than unattested calls.
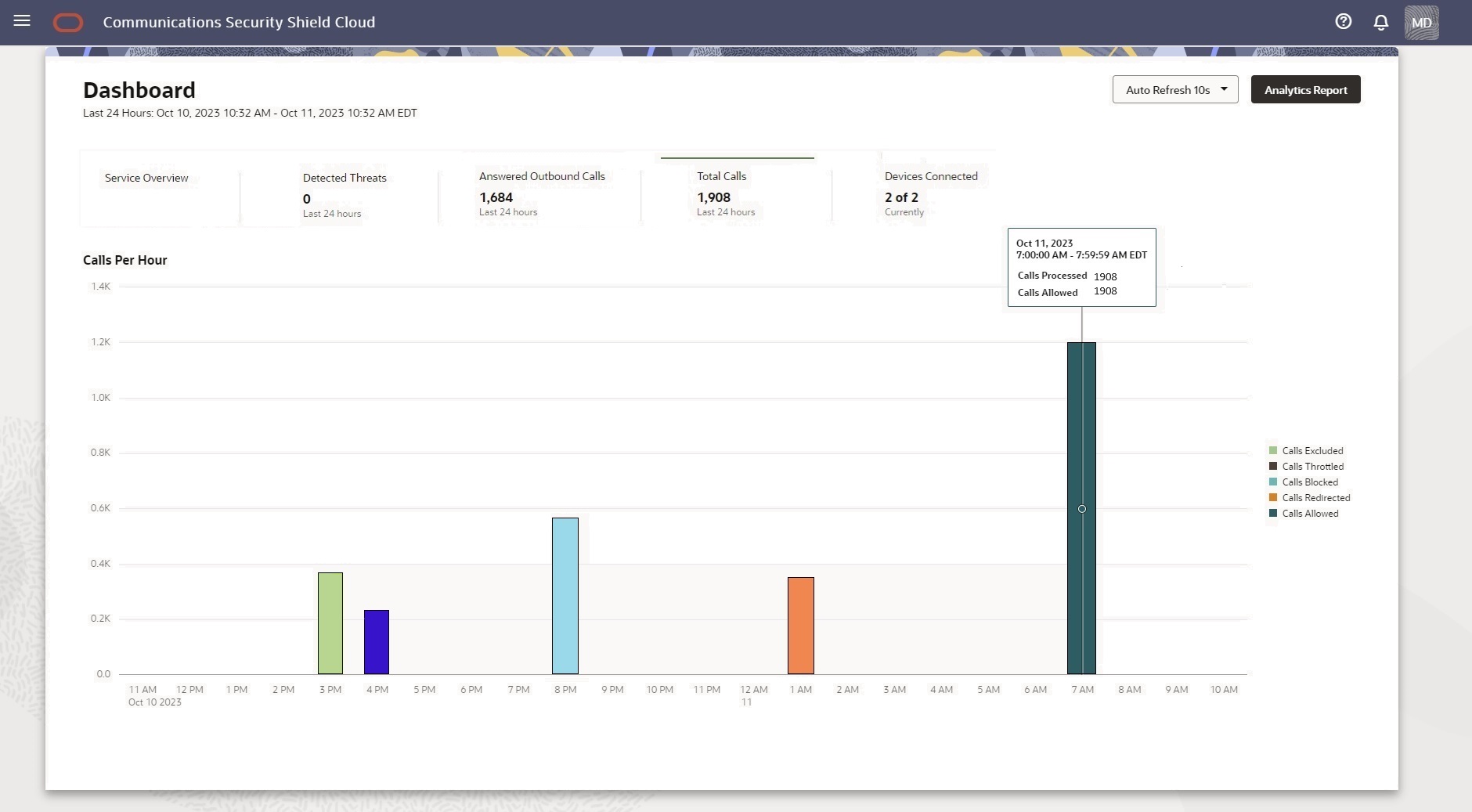
The Total Calls Scoreboard Metrics Card
The Total Calls scoreboard metrics card displays the total number of calls that passed in and out of your telephony network in the last twenty-four hours. When you hover over a time on the horizontal axis, the system displays information about the type of calls received for the time period.
Note:
The Answered Outbound Calls tab displays only for Trusted Enterprise Calls subscribers.Call Total Descriptions
Calls Excluded―The number of inbound calls allowed while still evaluating against Traffic Pumping, Spoofing, and Toll Fraud threat detection. Exclude ignores the risk assessment and classifies excluded calls as "Good". The Exclude action does not evaluate against Fraud Risk, Spam Risk, and Call Center call detection.
Calls Throttled―The number of calls allowed from specified calling and called numbers on the Access Control List per the percentage you set to limit such calls.
Calls Blocked―The number of calls blocked.
Calls Redirected―The number of calls redirected to a specified number.
Calls Allowed―The number of calls allowed.
The Devices Connected Scoreboard Metrics Card
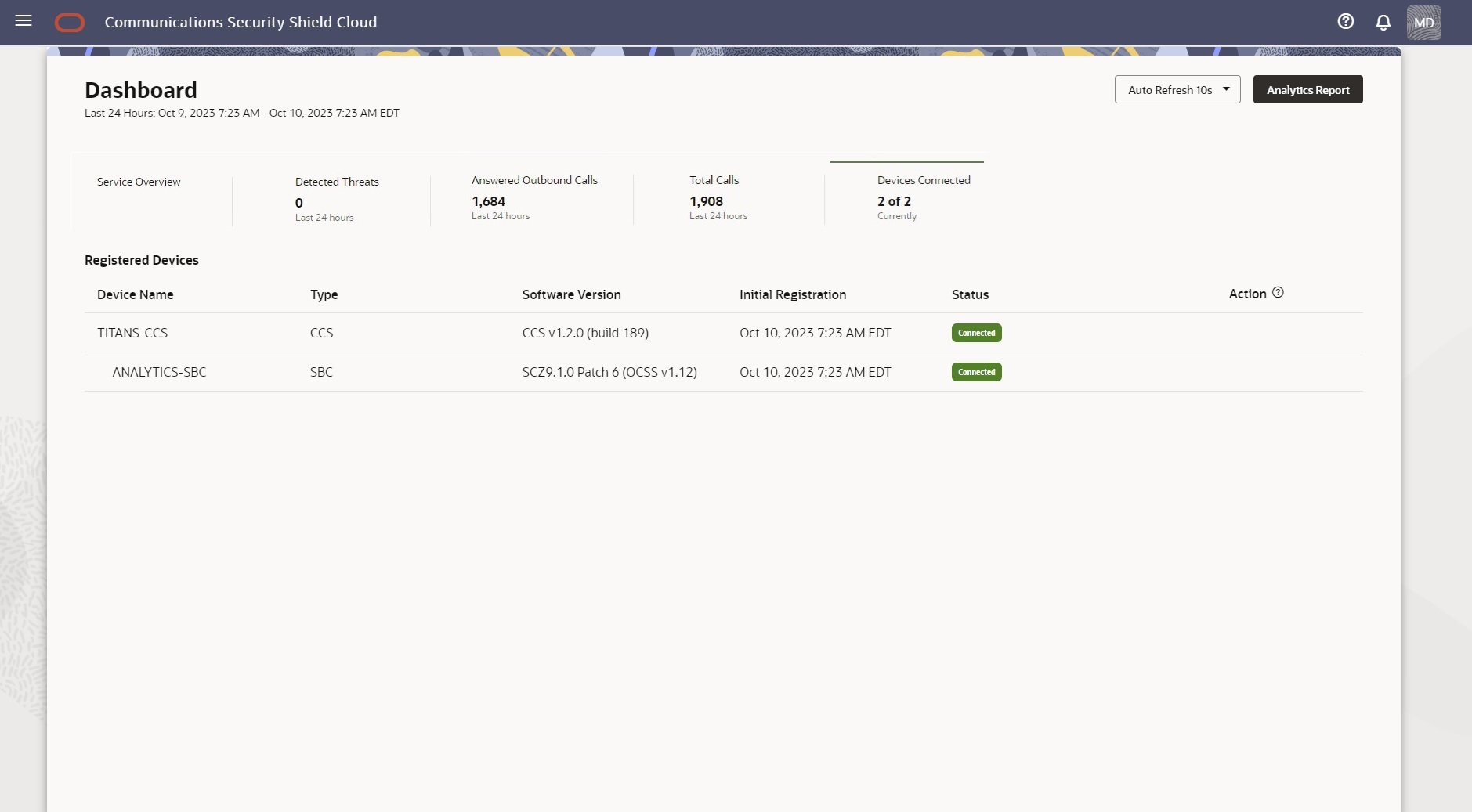
The Devices Connected scoreboard metrics card lists your devices connected to Oracle® Communications Security Shield Cloud Service (Security Shield) and information about their status.
The following screen capture shows the Devices Connected scoreboard metrics card with sample data.
Note:
The Answered Outbound Calls tab displays only for Trusted Enterprise Calls subscribers.Devices include the Cloud Communication Service (CCS) and the Oracle Communications Session Border Controller (SBC). When you configure a device, it automatically starts to register. Device Status also lists the software version running on each device, the date when the device initially registered, and actions taken.
The only interactive function provided is the ability to delete a device with the delete icon, which displays in the Action column. Before deleting a device, you must either take the device offline or disable the configuration that allows it to connect to Security Shield. If you do not, the device will re-register on its own, and will reappear in the device list. You cannot delete a parent device until you delete all of its child devices.