35.4 SSO Session Linking for OAuth Tokens
In deployment scenarios where a few resources are protected by OAM while some might be accessed with OAuth, to achieve seamless SSO between the different mixes of applications, it is necessary to link the SSO session with the Access Token. SSO Session Linking for OAuth Tokens supports key OAuth deployments requiring 2 legged flows involving native mobile apps and Synchronization of OAuth Tokens with SSO tokens.
Use Case Flow
Figure 35-1 illustrates the use case flow of the SSO Ssession linking.
Figure 35-1 Use case flow for SSO Session Linking for OAuth Tokens
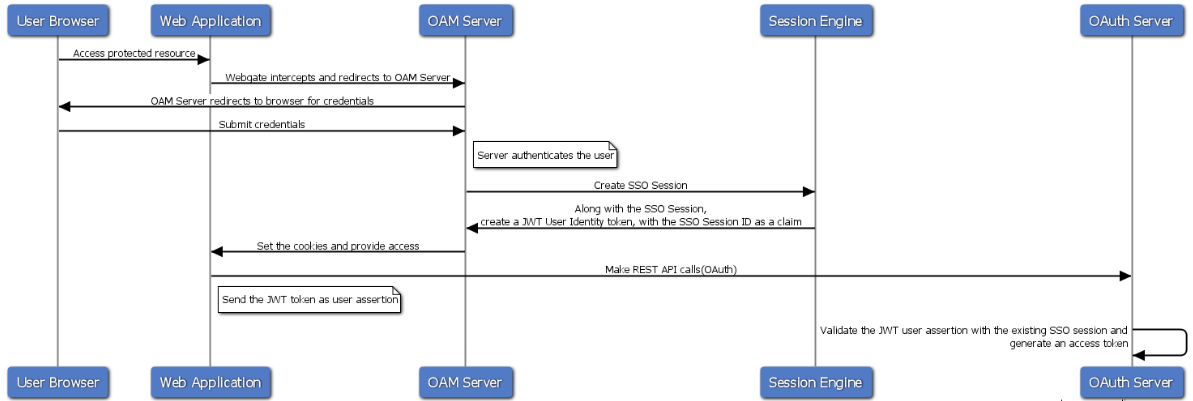
Description of "Figure 35-1 Use case flow for SSO Session Linking for OAuth Tokens"
Server Changes to Link SSO Session
-
When the SSO Session is created, a JWT User Token is also created. The JWT User Token has the SSO "session_id" as part of its claims.
-
Creating this JWT Token is based on configurations. When created, this token can be sent either as a cookie or a header to downstream applications. Currently the configurations are set as challenge parameters at the scheme level.
By default, the SSO link JWT token is set in the cookie.Note:
If theOAUTH_TOKEN_RESPONSE_TYPEisheader, the JWT token is set with the cookie nameJWTAssertion.If the
OAUTH_TOKEN_RESPONSE_TYPEiscookie, the JWT token is set with the cookie nameOAUTH_TOKEN.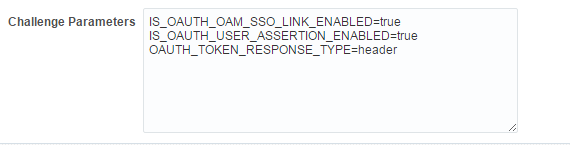
Description of the illustration ssolink_challengparam.png -
Token Signing: On bootstrap a default OAuth key-certificate is boot-strapped into the server. The JWT token will be signed by the Identity Domain private key. When the JWT token is received as an assertion back, the X5T value is retrieved from the header and the associated public key is fetched, which can be used to verify the token.
-
When the token is sent back as part of the JWT Bearer flow in the OAuth Token request, the OAM server retrieves theSSO "session_id" from the token.
-
Check Valid Session: If the JWT Token has a session ID, the server knows this is a SSO Linked JWT Token. It retrieves the "sessionId" claim from the token and checks if the server session with the given ID is still valid.
-
If the session is valid, the subject from the SSO Session is compared with the “sub” field in the JWT Token. If this matches, the access token for this user is generated and returned to the client.
-
In case of an MDC Enabled environment, as part of the JWT Token creation, another claim "mdc_sso_link" is also added to the token. This claim contains the clusterId of the machine on which the session was anchored and the UserIdentityStore reference
-
When the token is sent back as part of the JWT Bearer flow in the OAuth Token request, the OAM server will retrieve the SSO Session ID from the token.
-
Check Valid Session: If the JWT Token has a session ID, the server knows this is a SSO Linked JWT Token. It retrieves the "sessionId" claim from the token and the clusterid from the mdc_sso_link claim and retrieves the session. The normal MDC flows for checking validity of the session are maintained here.
-
If session is valid, the subject from the SSO Session will be compared with the “sub” field in the JWT Token. If this matches, the access token for this user is generated and the returned to the client.
If the session has been idle for more than 15 mins(configured value), when this JWT token is checked for validity it will fail. This ensures that the rules of the session are also applied to the OAuth Access Tokens.