1 About the Salesforce Connector
Oracle Identity Governance is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premises or on the Cloud. Oracle Identity Governance connectors are used to integrate Oracle identity Governance with the external identity- aware applications. The Salesforce connector lets you create and on board Salesforce applications in Oracle Identity Governance
Note:
In this guide, the connector that is deployed using the Applications option on the Manage tab of Identity Self Service is referred to as an AOB application. The connector that is deployed using the Manage Connectoroption in Oracle Identity System Administration is referred to as a CI-based connector (Connector Installer-based connector).From Oracle Identity Governance release 12.2.1.3.0 onward, connector deployment is handled using the application onboarding capability of Oracle Identity Self Service. This capability lets business users to on board applications with minimum details and effort. The connector installation package includes a collection of predefined templates (XML files) that contain all the information required for provisioning and reconciling data from a given application or target system. These templates also include basic connectivity and configuration details specific to your target system. The connector uses information from these predefined templates allowing you to on board your applications quickly and easily using only a single and simplified UI. Application on boarding is the process of registering or associating an application with Oracle Identity Governance and making that application available for provisioning and reconciliation of user information.
The following topics provide a high-level overview of the Salesforce connector:
Certified Components
These are the software components and their versions required for installing and using the Salesforce connector.
Table 1-1 Certified Components
| Component | Requirement for AOB Application | Requirement for CI-Based Connector |
|---|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use any one of the following releases:
|
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
Target Systems |
Salesforce Winter 2012 and later releases |
Salesforce Winter 2012 and later releases |
|
Connector Server JDK |
JDK 1.8.0_131 and later, or JRockit JDK 1.8.0_131 and later |
JDK 1.8.0_131 and later |
|
Connector Server |
11.1.2.1.0 or 12.2.1.3.0 |
11.1.2.1.0 or 12.2.1.3.0 |
Usage Recommendation
These are the recommendations for the Salesforce connector version that you can deploy and use depending on the Oracle Identity Manager version that you are using.
-
If you are using Oracle Identity Governance 12c (12.2.1.3.0) or later, then use the latest 12.2.1.x version of this connector. Deploy the connector using the Applications option on the Manage tab of Identity Self Service.
-
If you are using any of the Oracle Identity Manager releases listed in the “Requirement for CI-Based Connector” column in Table 1-1, then use the 11.1.2.3.0 version of the connector. If you want to use the 12.2.1.x version of this connector, then you can install and use it only in the CI-based mode. If you want to use the AOB application, then you must upgrade to Oracle Identity Governance 12c (12.2.1.3.0) or later.
Note:
If you are using the latest 12.2.1.x version of the Salesforce connector in the CI-based mode, then see Oracle Identity Manager Connector Guide for Salesforce, Release 11.1.1 for complete details on connector deployment, usage, and customization.Certified Languages
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
Supported Connector Operations
These are the list of operations that the connector supports for your target system.
Table 1-2 Supported Connector Operations
| Operation | Supported |
|---|---|
|
User Management |
|
|
Create user |
Yes |
|
Update user |
Yes |
|
Delete user Note: The target does not support the Delete operation, and so the Delete operation from Oracle Identity Governance disables the user on the target. |
Yes |
|
Group Management |
|
|
Create group |
Yes |
|
Remove group |
Yes |
|
Group Grant Management |
|
| Add, Remove | Yes |
|
Territory Grant Management |
|
| Add, Remove | Yes |
|
Permission set Grant Management |
|
| Add, Remove |
Yes |
Connector Architecture
You can configure the Salesforce connector to run in the Target (or account management) and Authoritative (or trusted) mode, and is implemented using the Identity Connector Framework (ICF) component.
The ICF is a component that is required in order to use Identity Connector. ICF provides basic reconciliation and provisioning operations that are common to all Oracle Identity Governance connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as, buffering, time outs, and filtering. ICF is distributed together with Oracle Identity Governance. Therefore, you do not need to configure or modify ICF.
The connector is configured to run in one of the following modes:
-
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this mode, the target system is used as the trusted source and users are directly created and modified on it. During reconciliation, each user record fetched from the target system is compared with existing OIM Users. If a match is found between the target system record and the OIM User, then the OIM User attributes are updated with changes made to the target system record. If no match is found, then the target system record is used to create an OIM User.
-
Account management
Account management is also known as target resource management. In this mode, the target system is used as a target resource and the connector enables the following operations:
-
Provisioning
Provisioning involves creating or updating users on the target system through Oracle Identity Governance. When you allocate (or provision) a Salesforce resource to the OIM User, the operation results in the creation of an account on Salesforce for that user. In the Oracle Identity Governancecontext, the term provisioning also covers updates made to the target system account through Oracle Identity Governance.
-
Target resource reconciliation
In target resource reconciliation, data related to the newly created and modified target system accounts can be reconciled and linked with existing OIM Users and provisioned resources. A scheduled task is used for reconciliation. Salesforce.com provides the details of only the active user accounts.
-
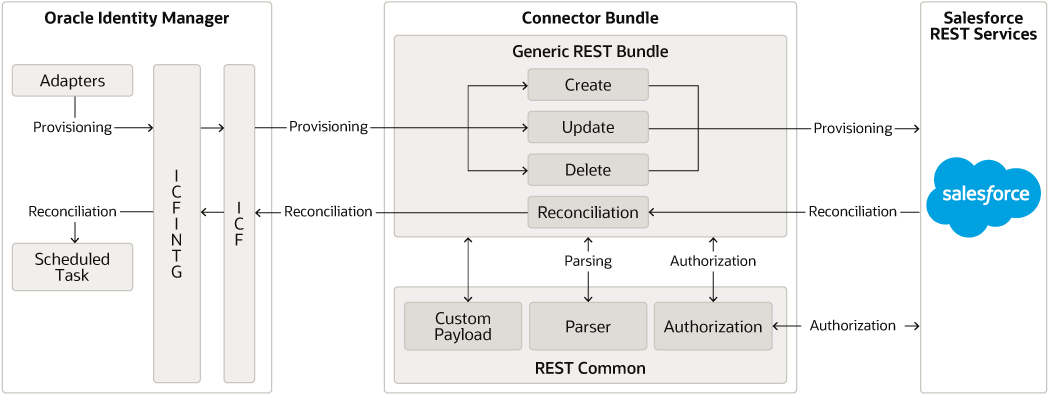
Figure 1-1 Salesforce Connector Architecture
Description of "Figure 1-1 Salesforce Connector Architecture"
As shown in Figure 1-1, Salesforce.com is configured as a target resource of Oracle Identity Governance. Through provisioning operations performed on Oracle Identity Governance, accounts are created and updated on the target system for OIG Users.
Through reconciliation, account data that is created and updated directly on the target system is fetched into Oracle Identity Governance and stored against the corresponding OIM Users.
Identity Connector Framework (ICF) is a component that is required in order to use Identity Connectors. ICF is distributed together with Oracle Identity Governance. You do not need to configure or modify ICF.
During provisioning, the Adapters invoke ICF operation, ICF inturn invokes create operation on Salesforce Identity Connector Bundle and then the bundle calls Salesforce Provisioning API. The Salesforce provisioning API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters.
During reconciliation, a scheduled task invokes ICF operation, ICF inturn invokes create operation on Salesforce Identity Connector Bundle and then the bundle calls Salesforce Reconciliation API. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Governance.
Supported Use Cases
These are common scenarios in which the connector can be used.
-
Salesforce License Management
On Salesforce.com, Profiles are used to manage licences which are in turn associated with user types. So for a particular user type, there is a fixed set of profiles. Using the Salesforce connector, you can reconcile all the profiles from Salesforce and assign them to users without worrying about the user types. Thus, switching the user from one license type to another is accomplished easily with the use of the Salesforce connector. This will arise if one Chatter Free user is promoted to Standard user in Salesforce and can enjoy the privileges that come along with those predefined licenses.
Salesforce Connector is also used to enable specific Salesforce.com profiles for your users, you must choose one profile for each user. A profile is a template that contains a collection of predefined settings and can determine what a user can see and do within the platform. The basic rule of Profiles is whether a given user can see and use each application as well as each tab within the application.
-
One Stop Identity Solution for Multiple Cloud Applications
Salesforce.com can act as a trusted source of identities which can be used to map users against various target cloud applications. In this case, a user from Salesforce can be created in any and every cloud and non-cloud applications that Oracle Identity Governance supports.
Salesforce.com can be used as a trusted source and an organization can use this feature to provide the list of users and further provision the account of these users to a third-party application that has been configured as target source.
-
Evolve Identity and Data Security of Salesforce Beyond the Parameter
Identity management solutions must support more than the traditional parameter-based authentication, and offer a single, simple, and trusted way to manage authentication and authorization of salesforce-based authentications. Enterprises making use of various IT systems (servers, devices, applications etc.) face numerous challenges due to the proliferation of passwords. Any vulnerability for password creates an opportunity for an attacker to acquire password values and consequently impersonate users. Oracle Salesforce Connector helps reduce administrative and help desk costs by enabling self-service password reset and password change.
This following image illustrates about controlling the access that the user has by managing Roles, Groups and Profiles.
Figure 1-2 Manage Roles, Groups, and Profiles to Control Access by the User
Description of "Figure 1-2 Manage Roles, Groups, and Profiles to Control Access by the User"
Supported Connector Features Matrix
Provides the list of features supported by the AOB application and CI-based connector.
Table 1-3 Supported Connector Features Matrix
| Feature | AOB Application | CI-Based Connector |
|---|---|---|
|
Perform Full Reconciliation |
Yes |
Yes |
|
Perform Limited Reconciliation |
Yes |
Yes |
|
Configure validation and transformation of account data |
Yes |
Yes |
|
Support multiple instances and multiple versions of the target system |
Yes |
Yes |
|
Use connector server |
Yes |
Yes |
|
Provide secure communication to the target system through SSL |
Yes |
Yes |
Connector Features
The features of the connector include support for connector server, full reconciliation, limited reconciliation, and transformation and validation of account data.
Support for Full Reconciliation
Full reconciliation involves reconciling all existing user records from the target system into Oracle Identity Governance. After you deploy the connector, you must first perform full reconciliation. A default filter is present in the Full Reconciliation Scheduled Job. This is the default filter which needs to be present while performing full user reconciliation.
If you want to get the frozen users in the Full Reconciliation Scheduled Job use the below Filter ValueFor frozen users:
WHERE+Id+IN+(SELECT+UserId+FROM+UserLogin+WHERE+IsFrozen=false)
For more information, see Performing Full Reconciliation.
Support for Limited Reconciliation
Limited or filtered reconciliation is the process of limiting the number of records being reconciled based on a set filter criteria.
To limit or filter the records that are fetched into Oracle Identity Governance during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled. See Performing Limited Reconciliation.
Transformation and Validation of Account Data
You can configure transformation and validation of account data that is brought into or sent from Oracle Identity Governance during reconciliation and provisioning operations by writing Groovy scripts while creating your application.
For more information, see Validation and Transformation of Provisioning and Reconciliation Attributes in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Support for Cloning Applications and Creating Instance Applications
You can configure this connector for multiple installations of the target system by cloning applications or by creating instance applications.
When you clone an application, all the configurations of the base application are copied into the cloned application. When you create an instance application, it shares all configurations as the base application.
For more information about these configurations, see Cloning Applications and Creating Instance Applications in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Secure Communication to the Target System
To provide secure communication to the target system, SSL is required. You can configure SSL between Oracle Identity Governance and the Connector Server and between the Connector Server and the target system.
If you do not configure SSL, passwords can be transmitted over the network in clear text. For example, this problem can occur when you are creating a user or modifying a user's password.
Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not wish to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements.
For information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Server, see Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance.