25 Configuring Proxy, Distribution, and Virtualization Deployments
dsconfig command.The following topics describe how to configure a proxy server by using the dsconfig command:
-
Configuring a Distribution with Failover Deployment Between Data Centers
-
Configuring a Union Workflow Element Deployment with Union Partition
Note:
You can also perform these configurations by using dsconfig in interactive mode. For information, see Using dsconfig in Interactive Mode.
Note:
To use the virtual directory capabilities described here, you must have a valid Oracle Directory Service Plus license.
25.1 Configuring a Load Balancing Deployment
You can create and define different objects when configuring a proxy server for simple load balancing with failover on two LDAP servers.
The following topics describe creating and configuring simple load balancing:
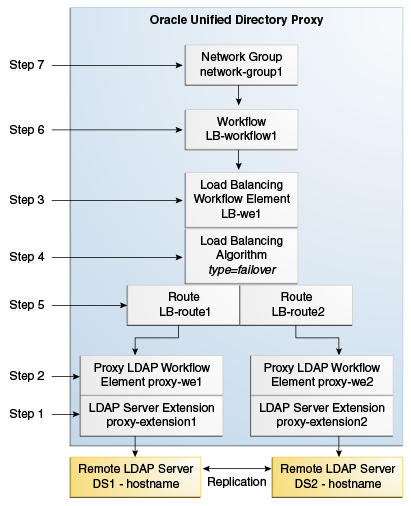
25.1.1 Creating Objects for Simple Load Balancing
The objects that are to be created when configuring a proxy server for simple load balancing are described in this section.
When configuring a proxy server for simple load balancing, you must create the objects shown in Figure 25-1. You must create these objects in the order indicated.
All of the commands in this procedure specify the proxy hostname (-h), the proxy admin port (-p), the bind DN for the initial root user (-D), and the file containing the proxy password (-j). You must also indicate the authentication. If you do not specify authentication, and if the client and server are running in the same instance, then Oracle Unified Directory uses the local authentication configuration.
25.2 Configuring a Distribution Deployment
You can create and define different objects when configuring a proxy server for a simple distribution deployment that is split over two partitions.
This following topics describe creating and configuring a distribution deployment:
Note:
For information about the supported distribution types, see Overview of Data Distribution Using the Proxy.
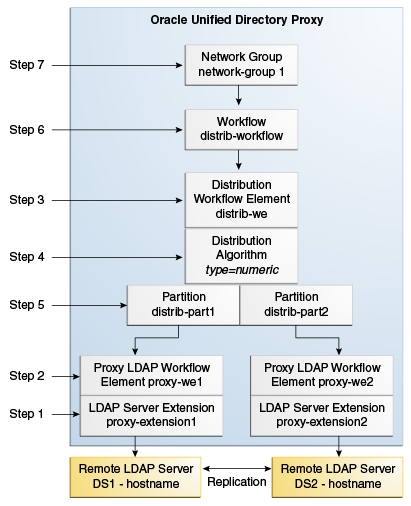
25.2.1 Creating Objects for Simple Distribution
You can create objects when configuring a proxy server for simple distribution.
When configuring a proxy server for simple distribution, you must create the objects shown in Figure 25-2. You must create these objects in the order indicated.
All of the commands in this procedure specify the proxy hostname (-h), the proxy admin port (-p), the bind DN for the initial root user (-D) and the proxy password you want to configure (-w). You must also indicate the authentication. If you do not specify authentication, and if the client and server are running in the same instance, then Oracle Unified Directory uses the local authentication configuration.
25.2.2 Configuring a Simple Distribution Deployment
You can configure a simple distribution deployment by creating a proxy LDAP server extension.
To configure a simple distribution deployment:
-
Create a proxy LDAP server extension.
$ dsconfig -h localhost -p 4444 -D "cn=Directory Manager" -j pwd-file -X \ create-extension \ --extension-name proxy_extension1 \ --type ldap-server \ --set enabled:true \ --set remote-ldap-server-address:DS1_hostname \ --set remote-ldap-server-port:2389
The LDAP server extension is a link to the remote LDAP server. For this task, you need two remote LDAP server instances. Repeat this step, using a different LDAP hostname and port for each server.
-
Create a proxy workflow element for each LDAP server extension.
$ dsconfig -h localhost -p 4444 -D "cn=Directory Manager" -j pwd-file -X \ create-workflow-element \ --element-name proxy-we1 \ --type proxy-ldap\ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy_extension1
You need at least two remote LDAP servers for a distribution architecture. Repeat this step for each server. Use the same LDAP server extension names that you created in step 1.
The property
client-cred-modeindicates the type of authentication used between the proxy and remote LDAP server. The client credential mode can be:use-client-identityoruse-specific-identity. -
Set up distribution by creating a distribution workflow element.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-workflow-element \ --element-name distrib-we \ --type distribution \ --set base-dn:dc=example,dc=com \ --set enabled:true
-
Set the distribution algorithm.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-distribution-algorithm \ --element-name distrib-we \ --type numeric \ --set distribution-attribute:uid
The distribution algorithm types include
capacity,numeric,lexico, ordnpattern. You define the algorithm properties when you create the distribution partitions, in the next step. -
Define the distribution partitions.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-distribution-partition \ --element-name distrib-we \ --partition-name distrib-part1\ --type numeric \ --set lower-bound:0 \ --set upper-bound:1000 \ --set partition-id:1 \ --set workflow-element:proxy-we1
For this task, you must create two partitions. You must use unique partition IDs and partition names for each workflow element. When defining the partitions, you must specify the same type that you used when defining the distribution algorithm.
Note:
The upper boundary is exclusive, which means if you specify
upper-bound:1000as the upper boundary, then the partition only includes values from 0 to 999, inclusive.-
If you created a
capacitydistribution algorithm, then you must create a global index. -
If you created a
lexico,numeric, ordnpatterndistribution algorithm, then creating a global index is optional.
To create a global index:
-
Create a global index catalog.
$ gicadm -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-catalog \ --catalogName gi-catalog
-
Add a global index that indexes the dn attribute to the catalog.
$ gicadm -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ add-index \ --catalogName gi-catalog \ --attributeName dn
-
Associate the global index catalog to the distribution.
$ gicadm -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ associate \ --catalogName gi-catalog \ --distributionWorkflowElement distrib-we
-
-
Create a workflow.
This workflow associates the distribution workflow element with the distribution partition.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-workflow \ --workflow-name distrib-workflow \ --set enabled:true \ --set base-dn:dc=example,dc=com \ --set workflow-element:distrib-we
-
Create the network group.
The network group handles all the requests between the client and the proxy.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-network-group \ --group-name network-group1 \ --set enabled:true \ --set workflow:distrib-workflow \ --set priority:1
25.3 Configuring a Distribution Deployment with Load Balancing
You can create and define different objects when configuring a proxy server for a distribution deployment with load balancing.
The following topics describe creating and configuring distribution with load balancing deployment:
Note:
Although you can add a global index to any distribution deployment, this example does not include instructions for adding a global index.
For information about creating a global index, see Configuring Global Indexes Using the Command Line.
25.3.1 Creating Objects for Distribution with Load Balancing
You can create objects when configuring a proxy server for distribution and load balancing.
When configuring a proxy server for distribution and load balancing, you must create the objects shown in Figure 25-3. You must create these objects in the order indicated.
Figure 25-3 Configuring Distribution and Load Balancing
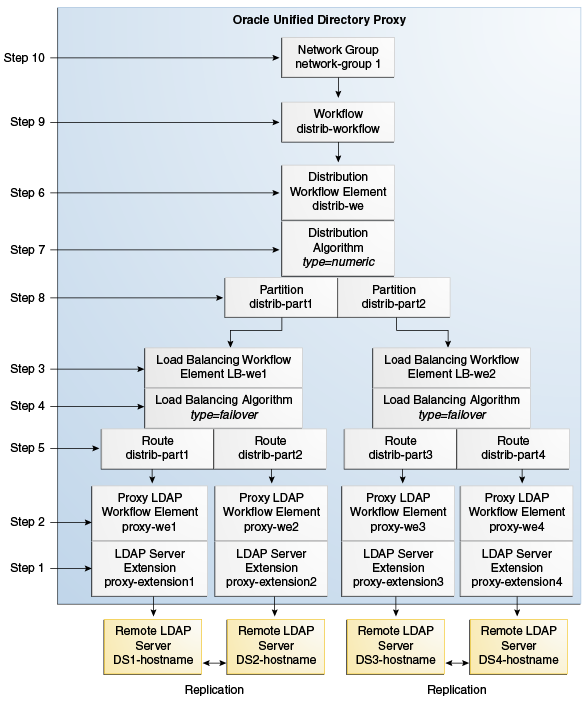
Description of "Figure 25-3 Configuring Distribution and Load Balancing"
This example illustrates a deployment with distribution over two partitions, with each partition load balanced onto two replicated LDAP servers. The example uses a numeric distribution algorithm to partition the data.
All of the commands in this procedure specify the proxy hostname (-h), the proxy admin port (-p), the bind DN for the initial root user (-D), and the file containing the proxy password (-j). You must also indicate the authentication. If you do not specify authentication, and if the client and server are running in the same instance, then Oracle Unified Directory uses the local authentication configuration.
25.3.2 Configuring a Distribution with Load Balancing Deployment
You can use the procedure to configure a distribution with load balancing deployment.
To configure a distribution and load balancing deployment:
-
Create the proxy LDAP server extensions.
$ dsconfig -h localhost -p 4444 -D "cn=Directory Manager" -j pwd-file -X \ create-extension \ --extension-name proxy_extension1 \ --type ldap-server \ --set enabled:true \ --set remote-ldap-server-address:DS1_hostname \ --set remote-ldap-server-port:2389
The LDAP server extension is a link to the remote LDAP server. For this task, you need four remote LDAP server instances. Repeat this step for each remote LDAP server, using a different LDAP hostname and port for each server.
-
Create a proxy workflow element for each LDAP server extension.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-workflow-element \ --element-name proxy-we1 \ --type proxy-ldap\ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy_extension1
For this task, you need four remote LDAP server instances. Repeat this step for each remote server, using the same LDAP server extension names as those created in step 1.
The property
client-cred-modeindicates the type of authentication used between the proxy and remote LDAP server. The client credential mode can be:use-client-identityoruse-specific-identity. -
Create a load balancing workflow element.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-workflow-element \ --element-name LB-we1 \ --type load-balancing \ --set enabled:true
You only need one load balancing workflow element to route requests to either of the two remote LDAP servers. You must create two load balancing workflow elements because you are using two load balancers.
-
Define the load balancing algorithm.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-load-balancing-algorithm \ --element-name LB-we1 \ --type failover
The load balancing algorithm types include
proportional,optimal,saturation,searchfilter, orfailover. You define the load balancing algorithm properties (weight, threshold, or priority) with the load balancing routes, in the next step. For this task, you need two load balancing algorithms. -
Define the load balancing routes for each proxy.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-load-balancing-route \ --element-name LB-we1 \ --route-name LB-route1 \ --type failover \ --set workflow-element:proxy-we1 \ --set add-priority:1 \ --set bind-priority:1 \ --set compare-priority:1 \ --set delete-priority:1 \ --set extended-priority:1 \ --set modify-priority:1 \ --set modifydn-priority:1 \ --set search-priority:1
For this task, you need four load balancing routes. Set two routes per load balancing workflow element (created in step 4). For example, set one route with priority 1 for all operations and set the other route with priority 2 for all operations.
Note:
The properties in this step set the priority for
failoverload balancing. You use different properties forproportionalorsaturationload balancing.For more information on the setting different load balancing types, see Modifying Load Balancing Properties.
-
Set up distribution by creating a distribution workflow element.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-workflow-element \ --element-name distrib-we \ --type distribution \ --set base-dn:dc=example,dc=com \ --set enabled:true
For this task, you need only one distribution workflow element that points to the distribution algorithm.
-
Set the distribution algorithm.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-distribution-algorithm \ --element-name distrib-we \ --type numeric \ --set distribution-attribute:uid
The distribution algorithm types include
capacity,numeric,lexico, ordnpattern. You define the boundaries when you create the distribution partitions, in the next step. -
Define the distribution partitions.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-distribution-partition \ --element-name distrib-we \ --partition-name distrib-part1\ --type numeric \ --set lower-bound:0 \ --set upper-bound:1000 \ --set partition-id:1 \ --set workflow-element:LB-we1
For this task, you must create two partitions. You must use unique partition IDs and partition names for each workflow element and that each partition uses a different load balancing workflow element. When defining the partitions, you must specify the same type that you used when defining the distribution algorithm.
Note:
The upper boundary is exclusive, which means if you specify
upper-bound:1000as the upper boundary, then the partition only includes values from 0 to 999, inclusive.-
If you created a
capacitydistribution algorithm, then you must create a global index. -
If you created a
lexico,numeric, ordnpatterndistribution algorithm, then creating a global index is optional.
To create a global index.
-
Create a global index catalog:
$ gicadm -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-catalog \ --catalogName gi-catalog
-
Add a global index which indexes the dn attribute to the catalog.
$ gicadm -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ add-index \ --catalogName gi-catalog \ --attributeName dn
-
Associate the global index catalog to the distribution.
$ gicadm -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ associate \ --catalogName gi-catalog \ --distributionWorkflowElement distrib-we
-
-
Create a workflow.
This workflow associates the distribution workflow element with the base DN.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-workflow \ --workflow-name workflow \ --set enabled:true \ --set base-dn:dc=example,dc=com \ --set workflow-element:distrib-we
-
Create the network group.
The network group handles all the requests between the client and the proxy.
$ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file \ create-network-group \ --group-name network-group1 \ --set enabled:true \ --set workflow:workflow \ --set priority:1
25.4 Configuring a Failover Deployment Between Data Centers
To set up a failover deployment between two data centers, you need to deploy two levels of load balancers within the proxy.
To set up a failover deployment between two data centers, see Configuration 3: Failover Between Data Centers.
To configure a failover deployment between two data centers, use the following commands:
#Create a proxy LDAP extension for each remote LDAP server dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension1 \ --set enabled:true \ --set remote-ldap-server-address:DS1_hostname \ --set remote-ldap-server-port:3189 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension2 \ --set enabled:true \ --set remote-ldap-server-address:DS2_hostname \ --set remote-ldap-server-port:3289 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension3 \ --set enabled:true \ --set remote-ldap-server-address:DS3_hostname \ --set remote-ldap-server-port:3389 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension4 \ --set enabled:true \ --set remote-ldap-server-address:DS4_hostname \ --set remote-ldap-server-port:3489 #Create a proxy workflow element for each LDAP server extension dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we1 \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension1 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we2 \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension2 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we3 \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension3 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we4 \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension4 # Create a load balancing workflow element for each data center dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name LB-we1 \ --type load-balancing \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name LB-we2 \ --type load-balancing \ --set enabled:true # Define the load balancing algorithm for each data center dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name LB-we1 \ --type proportional dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name LB-we2 \ --type proportional # Define the load balancing routes for each proxy dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we1 \ --route-name LB-route1 \ --type proportional \ --set workflow-element:proxy-we1 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we1 \ --route-name LB-route2 \ --type proportional \ --set workflow-element:proxy-we2 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we2 \ --route-name LB-route3 \ --type proportional \ --set workflow-element:proxy-we3 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we2 \ --route-name LB-route4 \ --type proportional \ --set workflow-element:proxy-we4 # Set failover between the two data centers dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name FO-we \ --type load-balancing \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name FO-we \ --type failover dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name FO-we \ --route-name FO-route1 \ --type failover \ --set workflow-element:LB-we1 \ --set add-priority:1 \ --set bind-priority:1 \ --set compare-priority:1 \ --set delete-priority:1 \ --set extended-priority:1 \ --set modify-priority:1 \ --set modifydn-priority:1 \ --set search-priority:1 \ dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name FO-we \ --route-name FO-route2 \ --type failover \ --set workflow-element:LB-we2 \ --set add-priority:2 \ --set bind-priority:2 \ --set compare-priority:2 \ --set delete-priority:2 \ --set extended-priority:2 \ --set modify-priority:2 \ --set modifydn-priority:2 \ --set search-priority:2 \ # Create workflow dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow \ --workflow-name FO-workflow \ --set enabled:true \ --set base-dn:dc=example,dc=com \ --set workflow-element:FO-we # Create network group dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-network-group \ --group-name network-group1 \ --set enabled:true \ --set workflow:FO-workflow \ --set priority:1
25.5 Configuring a Distribution with Failover Deployment Between Data Centers
To set up a failover deployment between two data centers, you can configure a topology that includes distribution with failover load balancing.
To set up a failover deployment between two data centers, see Configuration 5: Distribution with Failover Between Data Centers.
To configure distribution with failover between two data centers, use the following commands:
#Create the first failover route #Create a proxy LDAP extension for each remote LDAP server dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-1a \ --set enabled:true \ --set remote-ldap-server-address:DS1a_hostname \ --set remote-ldap-server-port:3189 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-2a \ --set enabled:true \ --set remote-ldap-server-address:DS2a_hostname \ --set remote-ldap-server-port:3289 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-1b \ --set enabled:true \ --set remote-ldap-server-address:DS1b_hostname \ --set remote-ldap-server-port:3389 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-2b \ --set enabled:true \ --set remote-ldap-server-address:DS2b_hostname \ --set remote-ldap-server-port:3489 #Create a proxy workflow element for each LDAP server extension dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-1a \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-1a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-2a \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-2a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-1b \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-1b dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-2b \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-2b # Create a load balancing workflow element for each data center dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name LB-we-1a \ --type load-balancing \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name LB-we-1b \ --type load-balancing \ --set enabled:true # Define the load balancing algorithm for each data center dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name LB-we-1a \ --type proportional dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name LB-we-1b \ --type proportional # Define the load balancing routes for each proxy dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-1a \ --route-name LB-route-1a \ --type proportional \ --set workflow-element:proxy-we-1a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-1a \ --route-name LB-route-2a \ --type proportional \ --set workflow-element:proxy-we-2a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-1b \ --route-name LB-route-1b \ --type proportional \ --set workflow-element:proxy-we-1b dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-1b \ --route-name LB-route-2b \ --type proportional \ --set workflow-element:proxy-we-2b # Set failover between the two data centers dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name FO-we1 \ --type load-balancing \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name FO-we1 \ --type failover dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name FO-we1 \ --route-name FO-route-1a \ --type failover \ --set workflow-element:LB-we-1a \ --set add-priority:1 \ --set bind-priority:1 \ --set compare-priority:1 \ --set delete-priority:1 \ --set extended-priority:1 \ --set modify-priority:1 \ --set modifydn-priority:1 \ --set search-priority:1 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name FO-we1 \ --route-name FO-route-1b \ --type failover \ --set workflow-element:LB-we-1b \ --set add-priority:2 \ --set bind-priority:2 \ --set compare-priority:2 \ --set delete-priority:2 \ --set extended-priority:2 \ --set modify-priority:2 \ --set modifydn-priority:2 \ --set search-priority:2 #Create the second failover route #Create a proxy LDAP extension for each remote LDAP server dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-3a \ --set enabled:true \ --set remote-ldap-server-address:DS3a_hostname \ --set remote-ldap-server-port:3189 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-4a \ --set enabled:true \ --set remote-ldap-server-address:DS4a_hostname \ --set remote-ldap-server-port:3289 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-3b \ --set enabled:true \ --set remote-ldap-server-address:DS3b_hostname \ --set remote-ldap-server-port:3389 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-extension \ --type ldap-server \ --extension-name proxy-extension-4b \ --set enabled:true \ --set remote-ldap-server-address:DS4b_hostname \ --set remote-ldap-server-port:3489 #Create a proxy workflow element for each LDAP server extension dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-3a \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-3a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-4a \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-4a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-3b \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-3b dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name proxy-we-4b \ --type proxy-ldap \ --set enabled:true \ --set client-cred-mode:use-client-identity \ --set ldap-server-extension:proxy-extension-4b # Create a load balancing workflow element for each data center dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name LB-we-2a \ --type load-balancing \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name LB-we-2b \ --type load-balancing \ --set enabled:true # Define the load balancing algorithm for each data center dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name LB-we-2a \ --type proportional dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name LB-we-2b \ --type proportional # Define the load balancing routes for each proxy dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-2a \ --route-name LB-route-3a \ --type proportional \ --set workflow-element:proxy-we-3a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-2a \ --route-name LB-route-4a \ --type proportional \ --set workflow-element:proxy-we-4a dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-2b \ --route-name LB-route-3b \ --type proportional \ --set workflow-element:proxy-we-3b dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name LB-we-2b \ --route-name LB-route-4b \ --type proportional \ --set workflow-element:proxy-we-4b # Set failover between the two data centers dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name FO-we2 \ --type load-balancing \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-algorithm \ --element-name FO-we2 \ --type failover dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name FO-we2 \ --route-name FO-route-2a \ --type failover \ --set workflow-element:LB-we-2a \ --set add-priority:1 \ --set bind-priority:1 \ --set compare-priority:1 \ --set delete-priority:1 \ --set extended-priority:1 \ --set modify-priority:1 \ --set modifydn-priority:1 \ --set search-priority:1 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-load-balancing-route \ --element-name FO-we2 \ --route-name FO-route-2b \ --type failover \ --set workflow-element:LB-we-2b \ --set add-priority:2 \ --set bind-priority:2 \ --set compare-priority:2 \ --set delete-priority:2 \ --set extended-priority:2 \ --set modify-priority:2 \ --set modifydn-priority:2 \ --set search-priority:2 # Create distribution to the two failover routes dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --element-name distrib-we \ --type distribution \ --set base-dn:dc=example,dc=com \ --set enabled:true dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-distribution-algorithm \ --element-name distrib-we \ --type numeric \ --set distribution-attribute:uid dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-distribution-partition \ --element-name distrib-we \ --partition-name distrib-part1\ --type numeric \ --set lower-bound:0 \ --set upper-bound:1000 \ --set partition-id:1 \ --set workflow-element:FO-we1 dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-distribution-partition \ --element-name distrib-we \ --partition-name distrib-part2\ --type numeric \ --set lower-bound:1000 \ --set upper-bound:2000 \ --set partition-id:2 \ --set workflow-element:FO-we2 # Create workflow dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-workflow \ --workflow-name Distrib-workflow \ --set enabled:true \ --set base-dn:dc=example,dc=com \ --set workflow-element:distrib-we # Create network group dsconfig -p 4444 -h localhost -D"cn=Directory Manager" -j pwd-file -X -n \ create-network-group \ --group-name network-group1 \ --set enabled:true \ --set workflow:Distrib-workflow \ --set priority:1
25.6 Configuring a Union Workflow Element Deployment with Union Partition
You can create and configure a Union workflow element to aggregate several DITs into a virtual unified DIT by using dsconfig command.
25.6.1 Setting Up OUD Instances to Implement Union Workflow Element Configuration
You must create and configure the OUD (oud1 and oud2) instances to implement the Union workflow element configuration.
Perform the following steps:
-
Run the
oud-setupcommand to create theoud1instance as follows:./oud-setup --cli --baseDN "o=company1" --addBaseEntry --adminConnectorPort 1444 --ldapPort 1389 \ --rootUserDN "cn=Directory Manager" --rootUserPasswordFile pwd.txt --no-prompt --noPropertiesFile -
Run the
oud-setupcommand to create theoud2instance as follows:./oud-setup --cli --baseDN "o=company2" --addBaseEntry --adminConnectorPort 2444 --ldapPort 2389 \ --rootUserDN "cn=Directory Manager" --rootUserPasswordFile pwd.txt --no-prompt --noPropertiesFile
25.6.2 Setting Up OUD Proxy Server to Implement Union Workflow Element Configuration
This topic illustrates how to set up the OUD proxy server to implement Union workflow element configuration.
Run the oud-setup command to create a proxy server instance (oud3):
./oud-proxy-setup --cli --ldapPort 3389 --adminConnectorPort 3444 --rootUserDN "cn=Directory Manager" --rootUserPasswordFile pwd.txt25.6.3 Configuring OUD Proxy Server to Implement Union Workflow Element Configuration
To connect to a remote LDAP directory server, the Oracle Unified Directory proxy needs LDAP server extension and LDAP proxy workflow element.
LDAP Server extensions are the properties required to connect from OUD Proxy oud3 to the remote LDAP servers (oud1 and oud2). You create LDAP Server extensions for oud1 and oud2. You will use these extensions in the workflow configuration later.
In addition, you need to create proxy workflow elements for OUD1 and OUD2. These specify connection details and credentials to the remote LDAP servers.
-
Create an LDAP Server Extension (
LDAPServerExtension1) and that points tooud1../dsconfig create-extension \ --set enabled:true \ --set remote-ldap-server-address:host01.example.com \ --set remote-ldap-server-port:1389 \ --type ldap-server \ --extension-name LDAPServerExtension1 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create an LDAP Proxy workflow element (
ProxyLDAPWorkFlowElement1) that points tooud1../dsconfig create-workflow-element \ --set client-cred-mode:use-client-identity \ --set enabled:true \ --set remote-ldap-server-bind-dn:"cn=directory manager" \ --remote-ldap-server-bind-password:file://pwd-file \ --set ldap-server-extension:LDAPServerExtension1 \ --set remote-root-dn:"cn=directory manager" --set remote-root-password:******** --type proxy-ldap \ --element-name ProxyLDAPWorkFlowElement1 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create an LDAP Server Extension (
LDAPServerExtension2) that points tooud2../dsconfig create-extension \ --set enabled:true \ --set remote-ldap-server-address:host01.example.com \ --set remote-ldap-server-port:2389 \ --type ldap-server \ --extension-name LDAPServerExtension2 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create an LDAP Proxy workflow element (
ProxyLDAPWorkFlowElement2) that points tooud2../dsconfig create-workflow-element \ --set client-cred-mode:use-client-identity \ --set enabled:true \ --set remote-ldap-server-bind-dn:"cn=directory manager" \ --remote-ldap-server-bind-password:file://pwd-file \ --set ldap-server-extension:LDAPServerExtension2 \ --set remote-root-dn:"cn=directory manager" --set remote-root-password:******** --type proxy-ldap \ --element-name ProxyLDAPWorkFlowElement2 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Run the
dsconfigcommand to view the server extensions../dsconfig -h host01.example.com -p 3444 -D "cn=Directory Manager" --bindPasswordFile pwd.txt -X -n list-extensions -
Run the
dsconfigcommand to view the proxy LDAP workflow elements../dsconfig -h host01.example.com -p 3444 -D "cn=Directory Manager" --bindPasswordFile pwd.txt -X -n list-workflow-elements
25.6.4 Creating Union Workflow Element
You can create a Union workflow using dsconfig command.
dsconfig command:
$ ./dsconfig create-workflow-element \ --set base-dn:o=company1 \ --set enabled:true --type union \ --element-name union-we \ --set enabled:true --hostname host01.example.com \ --port 3444 --bindDN "cn=Directory Manager" \ --bindPasswordFile pwd.txt \
You can also edit the properties for the Union workflow element using the dsconfig command-line interactive mode.
See the following example to edit propertied using the dsconfig command in interactive mode.
Oracle Unified Directory Configuration Console Main Menu What do you want to configure? 1) General Configuration 7) Virtualization 2) Authentication and authorization 8) Load Balancing 3) Schema 9) Distribution 4) Replication 10) Integration 5) Local Data Source 11) HTTP 6) Remote Data Source q) quit Enter choice: 9 Distribution Management Menu What would you like to do? 1) Distribution Workflow 3) Global Index Catalogs Shared Cache Element Extension 2) Global Index Catalogs 4) Union Workflow Element Extension b) back q) quit Enter choice [b]: 4 Union Workflow Element management menu What would you like to do? 1) List existing Union Workflow Elements 2) Create a new Union Workflow Element 3) View and edit an existing Union Workflow Element 4) Delete an existing Union Workflow Element 5) >>>> Union Partition management menu b) back q) quit Enter choice [b]: 3 >>>> There is only one Union Workflow Element: "union-we". Are you sure that this is the correct one? (yes / no) [yes]: >>>> Configure the properties of the Union Workflow Element Property Value(s) ---------------------------------------------------------------------- 1) auto-tune-search-option false 2) base-dn "dc=example,dc=com" 3) bind-option bind-first-success 4) cache-size 10000 5) enabled true 6) search-first-match true 7) suppress-entry-duplicates false ?) help f) finish - apply any changes to the Union Workflow Element q) quit Enter choice [f]: ? Component name: Union Workflow Element The Union workflow element is used to aggregate several DITs into a virtual unified DIT. Option Types: r -- Property value(s) are readable w -- Property value(s) are writable m -- The property is mandatory s -- The property is single-valued a -- Administrative action is required for changes to take effect Property Options Syntax -------------------------------------------------- auto-tune-search-option rw-s- BOOLEAN base-dn r-ms- DN bind-option rw-s- OPTION cache-size rw-s- INTEGER enabled rwms- BOOLEAN search-first-match rw-s- BOOLEAN suppress-entry-duplicates rw-s- BOOLEAN ---------------------------------------------------
For more information on the configuration properties of the Union workflow element, see Configuration Parameters for Union Workflow Element.
25.6.5 Configuring Union Workflow Element
You can configure the Union workflow element using dsconfig command.
-
Create a workflow. This workflow associates the Union workflow element with the base DN.
./dsconfig create-workflow \ --set base-dn:o=company1 \ --set enabled:true --set workflow-element:union-we --type generic \ --workflow-name distrib-workflow \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Attach the Union workflow (
distrib-workflow) to the network group../dsconfig set-network-group-prop \ --group-name network-group \ --set workflow:distrib-workflow \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt
25.6.6 Configuring Union Partition
You can create a Union workflow element using dsconfig command.
-
Create the Union Partition for
oud1by running thedsconfig create-workflow-element --type genericcommand:./dsconfig create-union-partition \ --element-name union-we \ --set workflow-element:ProxyLDAPWorkFlowElement1 --type generic \ --partition-name union-part1\ --set priority:1 --set source-base-dn:ou=people,ou=apac,o=comapny1 \ --set relative-base-dn:ou=people \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-promptFor more information on the configuration properties of the Union workflow element, see Configuration Parameters for Union Partition.
-
Create the Union Partition for
oud2by running thedsconfig create-workflow-element --type genericcommand:./dsconfig create-union-partition \ --element-name union-we \ --set workflow-element:ProxyLDAPWorkFlowElement2 --type generic \ --partition-name union-part2\ --set priority:2 --set source-base-dn:ou=people,ou=apac,o=company2 \ --set relative-base-dn:ou=people \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-promptFor more information on the configuration properties of the Union workflow element, see Configuration Parameters for Union Partition.
25.6.7 Validating Union Workflow Element Configuration
Learn to validate the Union workflow element configuration.
-
Run the
ldapmodifycommand to populate the following data for theunion-part1union partition:dn: o=company1 objectclass: top objectclass: organization o: company1 dn: ou=apac,o=company1 objectclass: top objectclass: organizationalunit ou: apac dn: ou=people,ou=apac,o=company1 objectclass: top objectclass: organizationalunit ou: people dn: uid=user.10,ou=people,ou=apac,o=company1 objectclass: top objectclass: inetOrgPerson cn: 10 sn: snof10 uid: user.10 userPassword: 10 -
Run the
ldapmodifycommand to populate theunion-part2union partition:dn: o=company2 objectclass: top objectclass: organization o: company2 dn: ou=apac,o=company2 objectclass: top objectclass: organizationalunit ou: apac dn: ou=people,ou=apac,o=company2 objectclass: top objectclass: organizationalunit ou: people dn: uid=user.20,ou=people,ou=apac,o=company2 objectclass: top objectclass: inetOrgPerson cn: 20 sn: snof20 uid: user.20 userPassword: 20 -
Run the
ldapsearchfor the oud-proxy setup to return all the entries from the partitions:./ldapsearch -h localhost -p 3444 -D "cn=Directory Manager" -j pwd.txt -b "o=company1" -s sub "(objectclass=*)"In response you will get unified data from different partitions. However, the data is present under different base DNs in the partitions.
For the Union workflow element (
union-we), if you have set theauto-tune-search-optionandsearch-first-matchproperties totruethen theldapsearchwill fetch users from both the partitions (union-part1andunion-part2).