24 Configuring Virtualization
The following topics describe how to configure a virtual directory view of repositories:
This chapter also gives an overview of DN Renaming, RDN Changing and Transformations Configurations.
Note:
To use the virtual directory capabilities described here, you must have a valid Oracle Directory Service Plus license.
Note:
You can choose to configure some virtualization elements using dsconfig or Oracle Unified Directory Services Manager (OUDSM).
-
For information about using the
dsconfigcommand, see Managing the Server Configuration Using dsconfig. -
For information about using OUDSM, see Accessing Oracle Unified Directory Using OUDSM.
24.1 Configuring a Virtual Directory View of Your Repositories
You can create and configure a Join workflow element to create a virtual directory view of your repositories by using dsconfig command or OUDSM.
The following topics describe configuring a virtual directory view:
Note:
To use the virtual directory capabilities described here, you must have a valid Oracle Directory Service Plus license.
24.1.1 Prerequisites for Creating the Join Workflow Element
Before creating the Join workflow element, you must configure the participating workflow elements so you can link to them from the Join workflow element configuration.
For example, consider a scenario with two separate Proxy LDAP workflow elements:
-
The first Proxy LDAP workflow element,
we-proxy1, will be linked to the primary participant of the Join workflow element configuration. -
The second Proxy LDAP workflow element,
we-proxy2, will be linked to the secondary participant of the Join workflow element configuration.
Note:
For more information about creating Proxy LDAP workflow elements, see Configuring Proxy LDAP Workflow Elements.
Assume there is an entry in the we-proxy1 data source as follows:
dn:cn=john,cn=users,dc=com1 objectclass:inetorgperson cn:john sn:doe uid:jdoe title:PMTS description: This entry is from we-proxy1
Next, assume there is an entry in the we-proxy2 data source as follows:
dn: sn=doe,cn=employees,dc=com2 empid: jdoe cn:John sn:doe department: Sales manager: userid=smith,cn=users,dc=com2 description: This entry is from we-proxy2 objectclass:inetorgperson
The joined-entry returned from Join Workflow element would be:
dn:cn=john,cn=users,dc=join objectclass:inetorgperson cn:john sn:doe uid:jdoe empid: jdoe title:PMTS description: This entry is from we-proxy1 description: This entry is from we-proxy2 manager: userid=smith,cn=users,dc=join department: Sales
24.1.2 Creating a Join Workflow Element Using the dsconfig Command
You can create and configure a Join workflow element topology, based on the scenario using the two Proxy LDAP workflow elements.
The two Proxy LDAP workflow elements are described in Prerequisites for Creating the Join Workflow Element.
Note:
The following steps assume that you have already created the participating workflow elements.
To configure a Join workflow element topology:
24.1.3 Creating a Join Workflow Element Using OUDSM
You can create a Join workflow element using the OUDSM graphical user interface.
Note:
For information, see Creating a Workflow Element.
24.2 Optimizing Search Results From a Virtual Directory
To help you more efficiently view or retrieve data from virtual data sources, Oracle Unified Directory provides two workflow elements that automatically narrow search results.
You can insert the GetRidOfDuplicate or HideByFilter workflow elements into any workflow chain that returns search results.
This section includes the following topics:
-
Eliminating Duplicate Entries from Search Results Using the GetRidofDuplicate Workflow Element
-
Filtering Search Results Using the HideByFilter Workflow Element
For more information about Oracle Unified Directory workflows, see “OUD Plug-Ins and Workflows" in Oracle Fusion Middleware Developer's Guide for Oracle Unified Directory.
24.2.1 Eliminating Duplicate Entries from Search Results Using the GetRidofDuplicate Workflow Element
The GetRidofDuplicate workflow element removes, from search results for the current search operation, all the entries whose DN has already been returned to the client application. This is useful when a workflow element is likely to return several entries with the same DN.
To eliminate duplicate entries from search operations:
Add the GetRidOfDuplcate workflow element before any workflow element, such as the Join workflow element, that returns duplicate entries.
The following example creates a get-rid-of-duplicate WFE (next WFE=NEXT_WFE).
dsconfig create-workflow-element \
--set enabled:true \
--set next-workflow-element:NEXT_WFE \
--set cache-size:1000000 \
--type get-rid-of-duplicate \
--element-name example \
--hostname locahost \
--port 1444 \
-X \
--bindDN cn=Directory\ Manager \
--bindPasswordFile ****** \
--no-prompt
In this example, a search will return no more than 1000000 unique entries.
Note:
In this configuration example, the created workflow element is not part of any workflow chain. A full configuration must also define or create the workflow chain, and update the Network group.
The GetRidofDuplicate has one configuration parameter:
cache-size
The cache-size parameter is required. It specifies the maximum number of entries that can be returned to the client during a single search operation.
24.2.2 Filtering Search Results Using the HideByFilter Workflow Element
The HideByFilter workflow element enables you to control in fine detail which entries are returned by searches of a virtual directory.
For example, if you are using Oracle Unified Directory as an address book directory, you can display only the entries for customer service representatives. First you give all customer service representatives an ou value of CSR. Then can use the HideByFilter workflow element with hideFilter set to ou=CSR. When the directory is searched, only the customer service representatives entries are returned.
To filter search results using the HideByFilter workflow element:
Create and link a HideByFilter workflow element. For example:
dsconfig create-workflow-element \
--set enabled:true \
--set next-workflow-element:NEXT_WFE \
--set ldap-filter:ou=CSR \
--type hide-entries-by-filter \
--element-name example1 \
--hostname dosapano \
--port 1444 \
-X \
--bindDN cn=Directory\ Manager \
--bindPasswordFile ****** \
--no-prompt
Table 24-1 summarizes the HideByFilter plug-in configuration parameters:
Table 24-1 HideByFilter Parameters
| Parameter | Description |
|---|---|
|
|
|
|
|
If an entry matches the ldapURL filter then it is returned to the client application only if it's a descendant of the LdapURL base DN. All the other fields of the LDAP filter are ignored. |
|
|
A list of adapters from which the user entry for the dynamic filter is searched. If list is empty, or if the user entry can be found in none of the adapters (including the current adapter) then the dynamic filter is ignored. |
|
|
When set to true, the filtering does apply to admin users. The parameter is optional and the default value is false. |
24.3 Adding the memberof User Attribute to person Entries
You can add the memberof user attribute to person entries. This is useful when you want applications to see group membership, but do not want them to perform secondary searches for those groups.
Note:
For more information, see Understanding Addition of memberof User Attributes to person Entries.
To define a VirtualMemberof workflow element, use the following configuration parameters:
-
searchBase: DN of the base to search for groups containing
personentries. -
explicitRequestOnly: Specify
TrueorFalse-
True (default): Adds the
memberofattribute to the entry only if it is explicitly requested as a returned attribute. -
False: Always adds the
memberofattribute to the entry.
-
-
member-attribute-name: The name of the
memberofattribute to add.Note:
The
memberofattribute has a default value for Oracle Virtual Directory convergence.In Oracle Virtual Directory, the
memberofattribute is auserattribute (not operational). The definition is:attributeTypes: ( 1.2.840.113556.1.2.102 NAME 'memberOf' DESC 'The distinguished name of the groups to which this object belongs' EQUALITY distinguishedNameMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.12 X-ORIGIN 'Microsoft Active Directory' )
24.4 Performing DN Renaming
You can perform DN Renaming configuration. It can be viewed and modified using dsconfig commands.
The following topics describe the DN Renaming configuration:
24.4.1 Configuring DN Renaming
To configure DN renaming, you must first create a DN renaming workflow element and then you can modify the DN renaming properties.
You can modify the following DN renaming properties:
-
client base DN -
source base DN -
next workflow element -
black list attributes -
white list attributes
24.4.2 Creating a DN Renaming Workflow Element
To create a DN renaming workflow element, use the dsconfig create-workflow-element command.
Follow the below given instructions:
$ dsconfig -h localhost -p 4444 -D "cn=Directory Manager" -j pwd-file -X -n \ create-workflow-element \ --type dn-renaming \ --element-name RenameorgDN \ --set client-base-dn:ou=myorg,dc=example,dc=com \ --set next-workflow-element:load-bal-we1 \ --set source-base-dn:ou=people,dc=example,dc=com \ --set enabled:true
where:
-
--set client-base-dnindicates the client base DN, which is the workflow entry point -
--set source-base-dnindicates the base DN which the entries should have after transformation, which is the workflow exit point. -
--set next-workflow-elementindicates the workflow element that will follow the DN renaming workflow element in the proxy architecture. You can specify any type of workflow element here.
24.4.3 Modifying a DN Renaming Configuration
You can view and modify a DN renaming configuration by using the dsconfig commands.
-
To view the current DN renaming properties, use the
dsconfig get-workflow-element-propcommand. -
To modify a DN renaming property, use the
dsconfig set-workflow-element-propcommand. For example,$ dsconfig -h localhost -p 4444 -D "cn=Directory Manager" -j pwd-file -X -n \ set-workflow-element-prop \ --element-name RenameorgDN \ --set source-base-dn:ou=admin,dc=example,dc=com
In the preceding example, only the
source-base-dnis modified. There is no need to specify the old source base DN. Only the new one is required. -
To create a black list of DN attributes that should not be renamed by using, use the
dsconfig set-workflow-element-propcommand. For example,$ dsconfig -h localhost -p 4444 -D "cn=Directory Manager" -j pwd-file -X -n \ set-workflow-element-prop --element-name RenameorgDN \ --set black-list-attributes:manager
The attribute must have a DN type.
24.5 Performing RDN Changing Configuration
You can perform RDN changing configuration, create RDN changing workflow element using dsconfig create-workflow-element command and modify RDN values.
The following topics describe how to perform RDN changing configuration:
24.5.1 Configuring RDN Changing
To change RDNs, you must first create an RDN Changing workflow element, and then you can modify the properties.
Modify the below given required properties:
-
client RDN -
source RDN -
next workflow element -
objectclass -
dn attributes -
replace-value
Note:
To use the virtual directory capabilities described here, you must have a valid Oracle Directory Service Plus license.
24.5.2 Creating an RDN Changing Workflow Element
To create an RDN Changing workflow element, use the dsconfig create-workflow-element command.
Use the following commands to create an RDN changing workflow element:
dsconfig create-workflow-element \
--set client-rdn:cn \
--set enabled:true \
--set next-workflow-element:localproxy \
--set source-rdn:uid \
--type rdn-changing \
--element-name myrdnchangingwfe \
--hostname localhost \
--port "4444" \
--trustAll \
--bindDN cn=directory\ manager \
--bindPasswordFile pwd-file \
--no-prompt
where:
-
--set client-rdnindicates the client base RDN, which is the workflow entry point. -
--set source-rdnindicates the base RDN which the entries should have after transformation, which is the workflow exit point. -
--set next-workflow-element:localproxyindicates the workflow element that will follow the RDN changing workflow element in the proxy architecture. This can be any type of workflow element.Note:
You must create the Proxy LDAP workflow element with the parameters
-
remote-root-dn -
remote-root-password
The RDN Changing workflow element uses these credentials to perform internal searches on the remote server.
-
-
--element-name myrdnchangingwfeindicates the name of the RDN Changing workflow element you are creating.This configuration replaces
uid=user.1,ou=people,dc=example,dc=com with cn=User CN,ou=people,dc=example,dc=com.
24.6 Configuring Transformations
You can configure transformations by using dsconfig and OUDSM.
The following topics explain the transformations configuration model:
Note:
To use the virtual directory capabilities described here, you must have a valid Oracle Directory Service Plus license.
Note:
For more information about transformations, see Understanding the Transformation Framework.
24.6.1 Understanding the Configuration Model
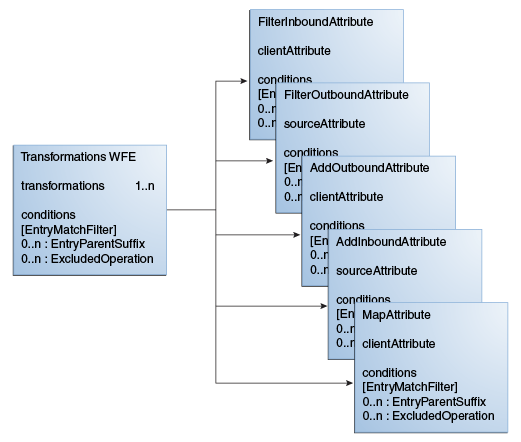
The transformation workflow element and transformations are the backbone entities for configuring transformation.
The transformation workflow element is a container that contains a list of references to transformations. One transformation can be reused by multiple transformation workflow elements. Conditions are properties (attributes) that you can set either on a transformation workflow element or on a transformation.
Note:
For detailed information about the various transformation types, conditions, and parameters that you can configure for a transformation workflow element, see Components of Transformation.
You cannot configure the order in which the transformations should work. For example, you define a transformation workflow element that uses transformation A and transformation B. But, you cannot determine if an entry is first processed by transformation A and then by transformation B. It can be B before A.
If you must define the order in which transformations should occur, for example transformation A should happen before transformation B, then it is recommended that you first create a transformation workflow element that uses transformation A. Next, create another transformation workflow element that uses transformation B. Then, place the second transformation workflow element after the first transformation workflow element.
Figure 24-1 illustrates a high-level configuration model.
24.6.2 Configuring Transformation Using dsconfig
You can create transformations, a workflow element, add transformations, and associate conditions using the dsconfig CLI.
Note:
-
To create a transformations workflow element using OUDSM, see Configuring Transformations Using OUDSM.
-
For more detailed information about transformations, transformation workflow elements, and conditions, see Understanding the Transformation Framework,
To configure transformation:
24.6.3 Configuring Transformations Using OUDSM
You can create, modify, and delete a transformation workflow element for Oracle Unified Directory proxy servers using OUDSM.
Note:
To create a transformation workflow element using dsconfig, see Configuring Transformation Using dsconfig.
This section includes the following topics:
24.6.3.1 Creating Transformations
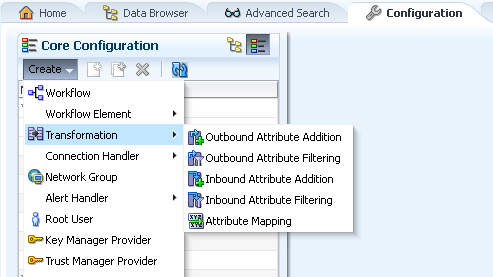
If you are connected to an Oracle Unified Directory Proxy Server, then OUDSM allows you to create five different types of transformations.
For more information about the types of transformations supported, see Overview of Transformation Types.
Note:
If you are connected to an Oracle Unified Directory server instance, then the option to create a new Transformation is not available because transformation functionality is supported by proxy servers only.
To create a transformation using OUDSM:
-
Connect to the directory server from OUDSM, as described in Connecting to the Server Using OUDSM.
-
Select the Configuration tab.
-
Select the Core Configuration view.
-
From the Create menu, select Transformation.
-
From the Transformation submenu, select the desired transformation type.
In this example, consider the following properties for an Outbound Attribute Addition transformation type.
Note:
The properties that appear while creating a transformation vary depending on the type of transformation you create. For more information about each transformation type and the associated properties, see Overview of Transformation Types.
-
In the Name field, type the name for the transformation.
-
In the Conditions region, enter the following information:
Note:
Conditions are optional. However; at runtime, conditions specified here at the transformation level are used with those specified at the transformation workflow element level in the transformation workflow element where the transformation is used. For more information about transformation workflow element, see Configuring Workflow Elements Using OUDSM.
-
In the Entry Matching Filter field, type a valid LDAP filter.
-
In the Entry Parent Suffixes box, click Add to specify the DN that must be an ascendant.
To select an entry, click Select.
In the Entry Picker window, select Tree View to navigate the directory tree and locate the entry, or Search View to search for the entry.
-
From the Excluded Operations list, select the operations that you want to exclude.
-
-
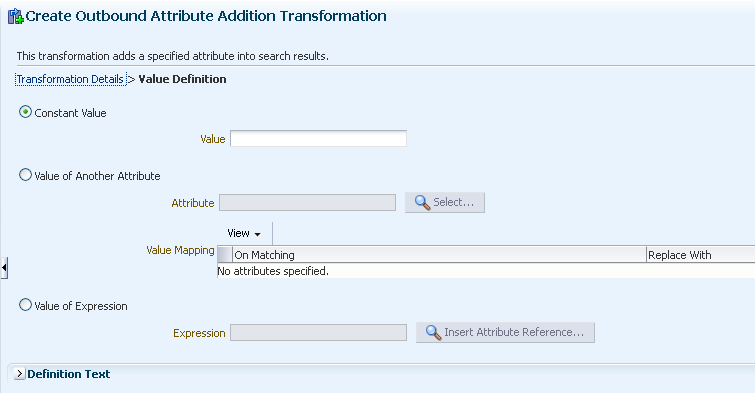
In the Transformation Definition region, enter the following information:
-
In the Client Attribute field, type the name of the client virtual attribute.
To select a client attribute entry, click Select.
In the Attribute Picker window, select locate the desired entry, or Click Search to search for the entry.
-
In the Value Definitions box, click Add to specify the value definitions of the client virtual attribute.
Click Define to enter an appropriate value definition. For more information about specifying value definitions, see Selecting Values from Value Definition Screen.
-
-
From the Conflict Behavior list, select the desired conflict behavior policy.
-
Click Virtual in Source to Yes.
-
Click Create.
24.6.3.2 Modifying Transformations
This section describes how to modify the properties for a transformation.
In this example, modify the properties for an Outbound Attribute Addition transformation type created in Creating Transformations.
To modify a transformation:
24.6.3.3 Deleting Transformations
This section describes the procedure to delete Transformation using OUDSM.
To delete a transformation:
24.6.3.4 Selecting Values from Value Definition Screen
The Value Definition Builder subscreen allows you to define a value for an attribute that is being added, mapped, or deleted by a transformation.
You can specify the following values:
-
Constant value: It is used to enter a constant value.
-
Value of another attribute: It is used to create a new attribute from an existing attribute in the entry that is being processed or to filter a value taken from another attribute.
-
Value of expression: It is used to create an attribute value or to filter an attribute value by manipulating the value of one or more existing attributes.
Figure 24-3 shows the Value Definition screen.
24.7 Configuring SAML XASP
The dsconfig command allows you to create a new SAML XASP workflow element and also edit the properties of an existing workflow element.
24.8 Deploying ForkJoin Workflow Element Configuration Model
The dsconfig command allows you to create and configure a ForkJoin workflow element.
24.8.1 Understanding ForkJoin Workflow Element Configuration Model
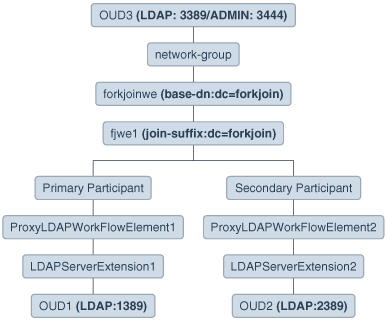
Consider a scenario, where you have two directory servers namely oud1 and oud2. Here, oud1 is the primary participant and oud2 is the secondary participant. Data resides in the both the primary participant and the secondary participant.
For this scenario, assume the following:
-
The primary participant namespace is
dc=example,dc=com. -
The secondary participant namespace is
dc=example,dc=com. -
The ForkJoin workflow element suffix is
dc=forkjoin.
Before creating the ForkJoin workflow element, you must configure the participating workflow elements so that you can link to them from the ForkJoin workflow element configuration. For each directory, you must create a Proxy LDAP workflow element that is associated with a directory to retrieve information from that directory. For example, consider a scenario with two separate Proxy LDAP workflow elements:
-
The first Proxy LDAP workflow element,
ProxyLDAPWorkFlowElement1, is linked to the primary participant of the ForkJoin workflow element configuration. -
The second Proxy LDAP workflow element,
ProxyLDAPWorkFlowElement2, is linked to the secondary participant of the ForkJoin workflow element configuration.
Note:
You can also configure an RDBMS workflow element as a primary or a secondary participant.Assume oud3 is a proxy workflow element, which has a ForkJoin workflow element pointing to the preceding participants through ProxyLDAPWorkFlowElement1 (to oud1) and ProxyLDAPWorkFlowElement2 (to oud2). To learn how to deploy the ForkJoin workflow element configuration, see Implementing ForkJoin Workflow Element Configuration Model.
The following diagram provides a pictorial representation of the ForkJoin workflow element configuration model.
Figure 24-4 ForkJoin Workflow Element Configuration Model
Description of "Figure 24-4 ForkJoin Workflow Element Configuration Model"
The secondary-only-attributes parameter is set to title in ForkJoin workflow element and the join-rule is set as cn=cn. Data in secondary participant as mentioned in the following table, does not have the description attribute.
The following table lists the data that resides in the primary participant and secondary participant.
Table 24-2 Data in Primary Participant and Secondary Participant
| Data in Primary Participant | Data in Secondary Participant |
|---|---|
|
|
|
|
|
|
|
|
24.8.2 Implementing ForkJoin Workflow Element Configuration Model
You can create and configure a ForkJoin workflow element to aggregate data from two data sources at real time by using dsconfig command.
Note:
See Understanding ForkJoin Workflow Element Configuration Model to comprehend the ForkJoin workflow element configuration model.24.8.2.1 Preparing For ForkJoin Workflow Element Configuration
To deploy a ForkJoin workflow element configuration, you need to set up the OUD Directory Server instance and the OUD Proxy Server instance. You need to place a proxy server in front of the data sources that you want to join.
Set up the First OUD Instance (oud1)
-
Run the
oud-setupcommand to create theoud1instance as follows:./oud-setup --cli --baseDN "dc=example,dc=com" --addBaseEntry --adminConnectorPort 1444 --ldapPort 1389 \ --rootUserDN "cn=Directory Manager" --rootUserPasswordFile pwd.txt --no-prompt --noPropertiesFile -
Populate the
oud1directory server instance with sample entries.-
Create an LDIF file
(fj_oud1.ldif) with Data in Primary Participant as described in Understanding ForkJoin Workflow Element Configuration Model. -
Run the
ldapmodifycommand to populate theoud1instance with the entries infj_oud1.ldiffile../ldapmodify --hostname host01.example.com --port 1389 --bindDN "cn=Directory Manager" --bindPasswordFile pwd.txt --defaultAdd --filename fj_oud1.ldif
-
Set up the Second OUD Instance (oud2)
-
Run the
oud-setupcommand to create theoud2instance as follows:./oud-setup --cli --baseDN "dc=example,dc=com" --addBaseEntry --adminConnectorPort 2444 --ldapPort 2389 \ --rootUserDN "cn=Directory Manager" --rootUserPasswordFile pwd.txt --no-prompt --noPropertiesFile -
Populate the
oud2directory server instance with sample entries.-
Create an LDIF file
(fj_oud2.ldif) with Data in Secondary Participant as described in Understanding ForkJoin Workflow Element Configuration Model. -
Run the
ldapmodifycommand to populate theoud2instance with the entries infj_oud2.ldiffile../ldapmodify --hostname host01.example.com --port 2389 --bindDN "cn=Directory Manager" --bindPasswordFile pwd.txt --defaultAdd --filename fj_oud2.ldif
-
Set up the OUD Proxy Server Instance (oud3)
-
Run the
oud-proxy-setupcommand to create a proxy server instance,oud3, as follows:./oud-proxy-setup --cli --ldapPort 3389 --adminConnectorPort 3444 --rootUserDN "cn=Directory Manager" --rootUserPasswordFile pwd.txt
24.8.2.2 Configuring OUD Proxy Server For ForkJoin Workflow Element Configuration
To connect to a remote LDAP directory server, the Oracle Unified Directory proxy needs LDAP server extension and LDAP proxy workflow element.
LDAP Server extensions are the properties required to connect from OUD Proxy oud3 to the remote LDAP servers (oud1 and oud2). You create LDAP Server extensions for oud1 and oud2. You will use these extensions in the workflow configuration later.
In addition, you need to create proxy workflow elements for oud1 and oud2. These specify connection details and credentials to the remote LDAP servers.
-
Create an LDAP Server Extension (
LDAPServerExtension1) and that points tooud1../dsconfig create-extension \ --set enabled:true \ --set remote-ldap-server-address:host01.example.com \ --set remote-ldap-server-port:1389 \ --type ldap-server \ --extension-name LDAPServerExtension1 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create an LDAP Proxy workflow element (
ProxyLDAPWorkFlowElement1) that points tooud1../dsconfig create-workflow-element \ --set client-cred-mode:use-client-identity \ --set enabled:true \ --set ldap-server-extension:LDAPServerExtension1 \ --type proxy-ldap \ --element-name ProxyLDAPWorkFlowElement1 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create an LDAP Server Extension (
LDAPServerExtension2) that points tooud2../dsconfig create-extension \ --set enabled:true \ --set remote-ldap-server-address:host01.example.com \ --set remote-ldap-server-port:2389 \ --type ldap-server \ --extension-name LDAPServerExtension2 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create an LDAP Proxy workflow element (
ProxyLDAPWorkFlowElement2) that points tooud2../dsconfig create-workflow-element \ --set client-cred-mode:use-client-identity \ --set enabled:true \ --set ldap-server-extension:LDAPServerExtension2 \ --type proxy-ldap \ --element-name ProxyLDAPWorkFlowElement2 \ --hostname host01.example.com \ --port 3444 \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Run the
dsconfigcommand to view the server extensions../dsconfig -h host01.example.com -p 3444 -D "cn=Directory Manager" --bindPasswordFile pwd.txt -X -n list-extensions -
Run the
dsconfigcommand to view the proxy LDAP workflow elements../dsconfig -h host01.example.com -p 3444 -D "cn=Directory Manager" --bindPasswordFile pwd.txt -X -n list-workflow-elements
24.8.2.3 Creating ForkJoin Workflow Element
You can create a ForkJoin workflow element using dsconfig command.
-
Create workflow element of type
fork-joinfor join-suffixdc=forkjoin../dsconfig create-workflow-element \ --set enabled:true \ --set join-suffix:dc=forkjoin \ --set populate-joinedentrydn:true \ --set secondary-only-attributes:title \ --type fork-join \ --element-name fjwe1 \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create a workflow of type
genericfor join-suffixdc=forkjoin../dsconfig create-workflow \ --set base-dn:dc=forkjoin \ --set enabled:true \ --set workflow-element:fjwe1 \ --type generic \ --workflow-name forkjoinwf \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt
24.8.2.4 Configuring ForkJoin Workflow Element
You can configure the ForkJoin workflow element using dsconfig command.
-
Create the Primary ForkJoin participant that is the link between the ForkJoin workflow element and
oud1../dsconfig create-primary-fork-join-participant \ --element-name fjwe1 \ --set participant-dn:dc=example,dc=com \ --set participating-workflow-element:ProxyLDAPWorkFlowElement1 \ --type generic \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Create the Secondary ForkJoin participant that is the link between the ForkJoin workflow element and
oud2../dsconfig create-secondary-fork-join-participant \ --element-name fjwe1 \ --set participant-dn:dc=example,dc=com \ --set participating-workflow-element:ProxyLDAPWorkFlowElement2 \ --set participants-join-rule:cn=cn \ --type generic \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Configure the
secondary-only-attributesproperty for the ForkJoin workflow element../dsconfig --hostname host01.example.com --port 3444 --trustAll --bindDN "cn=Directory Manager" \ --bindPasswordFile pwd.txt --no-prompt set-workflow-element-prop --element-name fjwe1 --add secondary-only-attributes:description -
Attach the ForkJoin Workflow element (
forkjoinwf) to the network group../dsconfig set-network-group-prop \ --group-name network-group \ --set workflow:forkjoinwf \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt
24.8.2.5 Configuring ForkJoin Workflow Element Join Policy
ForkJoin workflow element supports standard-join, left-outer-join, and full-outer-join Join policies. Learn to configure the Join policy.
-
Set the join-policy parameter to
full-outer-join../dsconfig set-secondary-fork-join-participant-prop \ --element-name fjwe1 \ --set join-policy:full-outer-join \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Set the join-policy parameter to
standard-join../dsconfig set-secondary-fork-join-participant-prop \ --element-name fjwe1 \ --set join-policy:standard-join \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt -
Set the join-policy parameter to
left—outer-join../dsconfig set-secondary-fork-join-participant-prop \ --element-name fjwe1 \ --set join-policy:left-outer-join \ --hostname host01.example.com \ --port 3444 \ --portProtocol LDAP \ --trustAll \ --bindDN cn=Directory\ Manager \ --bindPasswordFile pwd.txt \ --no-prompt
24.8.2.6 Validating ForkJoin Workflow Element Configuration
Learn to validate the ForkJoin workflow element configuration.
-
To test the
full-outer-joincondition, run theldapsearchcommand as follows:./ldapsearch -h host01.example.com -p 3389 -D "cn=Directory Manager" -j pwd.txt -b "dc=forkjoin" -s sub "|(sn=*e*)(title=*e*)" sn cn titlecn=Rock,dc=forkjoin sn=Anne cn=Rock title=Manager cn=Sandy,dc=forkjoin sn=Ketty cn=Sandy title=SMTS cn=Woods,dc=forkjoin sn=Tent cn=Woods cn=Rivry,dc=forkjoin sn=Rod cn=Rivry title=Trainee cn=Mounty,dc=forkjoin sn=Ret cn=Mounty title=MTS - dept_sec -
To test the
standard-joincondition, run theldapsearchas follows:./ldapsearch -h host01.example.com -p 3389 -D "cn=Directory Manager" -j pwd.txt -b "dc=forkjoin" -s sub "|(sn=*e*)(title=*e*)" sn cn titlecn=Rock,dc=forkjoin sn=Anne cn=Rock title=Manager cn=Sandy,dc=forkjoin sn=Ketty cn=Sandy title=SMTS cn=Woods,dc=forkjoin sn=Tent cn=Woods -
To test the
left—outer-joincondition, run theldapsearchas follows:./ldapsearch -h host01.example.com -p 3389 -D "cn=Directory Manager" -j pwd.txt -b "dc=forkjoin" -s sub "|(sn=*e*)(title=*e*)" sn cn titlecn=Rock,dc=forkjoin sn=Anne cn=Rock title=Manager cn=Sandy,dc=forkjoin sn=Ketty cn=Sandy title=SMTS cn=Woods,dc=forkjoin sn=Tent cn=Woods cn=Rivry,dc=forkjoin sn=Rod cn=Rivry title=Trainee
24.9 Configuring DynamicGroup Workflow Element
You can configure DynamicGroup Workflow Element by using dsconfig.
24.9.1 Understanding DynamicGroup Workflow Element Configuration Model
Learn about the DynamicGroup Workflow Element Configuration.
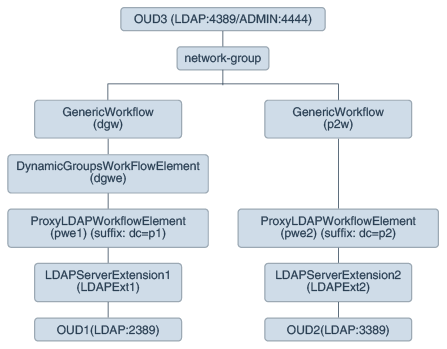
The following diagram illustrates the DynamicGroup Workflow Element configuration:
In the above example, for each backend directory, a ProxyLDAPWorkflowElement is created that retrieves information from the backend directory. Depending on the bind DN, a search would be routed through network-group and forwarded to workflow elements dgw or p2w.The DynamicGroupsWorkflowElement does the conversation with the directory servers that are dependent on the Proxy LDAP Workflow elements.
In this scenario, assume the following:
-
oud1is associated with aProxyLDAPWorkflowElementpwe1with suffixdc=p1. -
oud2is associated withProxyLDAPWorkflowElementpwe2with suffixdc=p2 -
oud3is OUD proxy server which front-endsOUD1andOUD2above usingProxyLDAPWorkflowElementpwe1andpwe2respectively.DynamicGroupsWorkflowElementis configured on top ofProxyLDAPWorkflowElementpwe1in order to handle the processing of Dynamic groups present inoud1. -
LDAPExt1andLDAPExt2areLDAPServerExtensions.
24.9.2 Implementing DynamicGroup Workflow Element Configuration Model
Learn how to implement DynamicGroup Workflow element configuration.
24.9.2.1 Setting up OUD Instances to Configure DynamicGroups Workflow Element
You need to setup OUD proxy and OUD instances to configure dynamic groups.
24.9.2.2 Configuring Proxy LDAP Workflow Element and DynamicGroups Workflow Against First OUD Instance
Learn how to configure the Proxy LDAP Workflow Element and dynamic groups Workflow Element against oud1.
24.9.3 Testing the DynamicGroup Workflow Element Configuration
Learn how to test the dynamic group workflow configuration.
The following sections describe how to test the dynamic groups configuration:
24.9.3.1 Testing DynamicGroups with and without expanding memberURL attribute
Learn how to test dynamic groups with and without expanding memberURL attribute.
memberURL attribute expansion:
Note:
If there is objectclass=groupOfUniqueNames and objectclass=groupOfUrls in the DynamicGroup, then you have to change single-structural-objectclass-behavior:accept parameter using the --advanced option as follows:
./dsconfig set-global-configuration-prop --set single-structural-objectclass-behavior:accept --advanced
To configure the single-structural-objectclass-behavior:accept parameter, see "single-structural-objectclass-behavior" in the Configuration Reference for
Oracle Unified Directory.
24.9.3.2 Testing Group Membership
The Dynamic Groups workflow element detects a membership test query by detecting the presence of both cn and uniqueMember filter terms. When present, the Dynamic Groups workflow processes the query differently by recognizing that the client wants to test a membership assertion. The workflow element modifies the results and returns only the single user being tested as the member.
cn=Jim Ward set in the uniqueMember attribute of the group.