Load Data Using Oracle Database Gateway Server Running in Azure VM
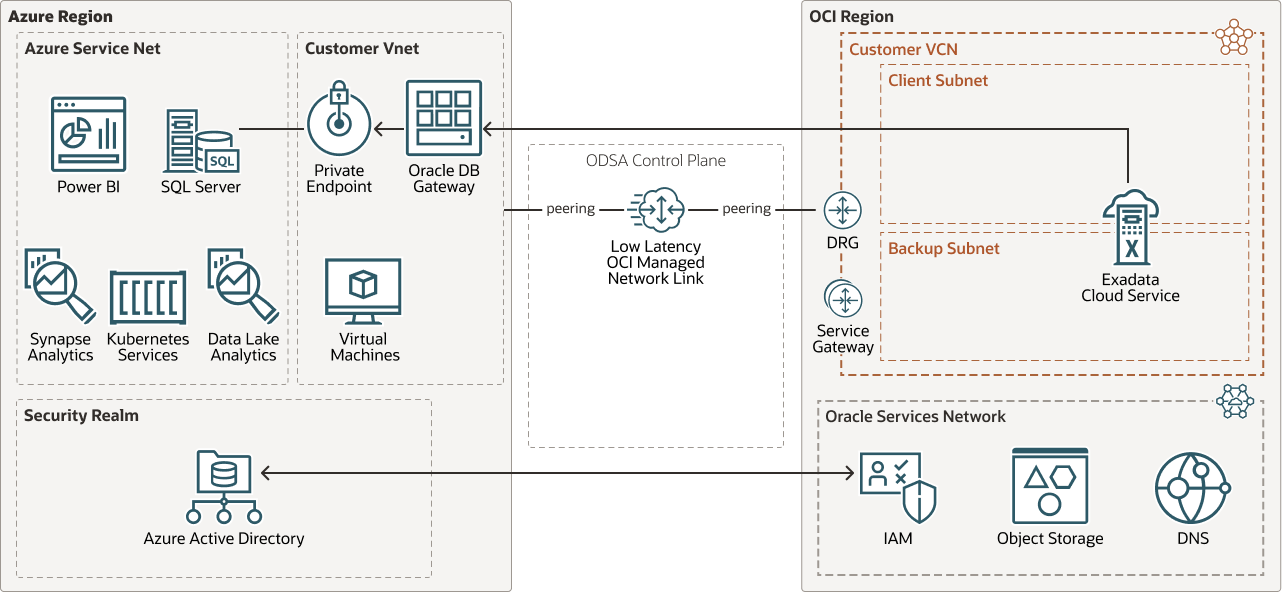
OracleDB for Azure enables Azure applications to load and query data from OCI databases. This architecture describes how an Oracle Exadata Database Service on Dedicated Infrastructure can leverage the infrastructure provided by OracleDB for Azure to load data from an Azure SQL Server using a database link via Oracle Database Gateway for SQL Server software running in an Azure virtual machine.
Architecture
This architecture uses Oracle Database Gateway for SQL Server running in an Azure virtual machine to load data from Azure SQL Server to Oracle Exadata Database Service on Dedicated Infrastructure. Oracle Database Gateway for SQL Server connects to Azure SQL Server using the fast-low latency network link using an Azure private endpoint.
The following diagram illustrates this architecture.
exadata-db-azure-odsa-azure-vm.zip
Note the following about this architecture:
- Oracle Database Gateway for SQL Server software can run on an Azure virtual machine. The number of CPUs, memory, and disk size must be assigned to the Azure virtual machine according to the Oracle Database Gateway for SQL Server requirements and sizing guidelines. See System Requirements for Oracle Database Gateway for SQL Server below for more information.
- Oracle Exadata Database Service on Dedicated
Infrastructure needs to resolve the hostname and IP address of the Azure virtual machine running Oracle Database Gateway. Edit the
/etc/hostsfile on the Oracle Database Gateway server, or configure a Private DNS Zone on the OCI Virtual Cloud Network (VCN) where the Oracle Exadata Database Service on Dedicated Infrastructure is configured. - In Oracle Exadata Database Service on Dedicated
Infrastructure databases, the parameter
global_namesis set toTRUEby default. Therefore, the fully qualified database name must be used when creating the database link to Azure SQL Server.
Before You Begin
Before you begin, check the versions of major software components used in this setup, download the required software package, and review the product documentation for later reference.
Review Software Requirements
These instructions are tested on the following software and hardware versions.
- Oracle Exadata Database Service on Dedicated Infrastructure X8M-2
- Oracle Database 19.16
- Azure SQL Server
Download the following software package:
Review Documentation
-
"Provisioning an Oracle Exadata System in Oracle Database Service for Azure" in Oracle Cloud Infrastructure documentation
- Oracle Database Gateway Installation and Configuration Guide
- Oracle Database Gateway for SQL Server User's Guide
- "System Requirements for Oracle Database Gateway for SQL Server" in Oracle Database Gateway Installation and Configuration Guide
About Required Services and Roles
This solution requires the following services:
- OracleDB for Azure with Oracle Exadata Database Service on Dedicated Infrastructure
- Oracle Cloud Infrastructure
- Azure Virtual Machine
These are the roles needed for each service.
| Service Name: Role | Required to... |
|---|---|
Oracle Exadata Database Service on Dedicated
Infrastructure: sys con |
Configure the database link. |
Oracle Cloud
Infrastructure: VCN Admin |
Add security rules, modify DNS to resolve to Azure endpoint and Azure VM. |
Azure Virtual Machine: root |
Create oracle user to install and configure Oracle Database Gateway software. Modify local firewall to allow connections to port 1521. |
See Learn how to get Oracle Cloud services for Oracle Solutions to get the cloud services you need.
Considerations for Oracle Database Gateway Running in an Azure Virtual Machine
Running the Oracle Database Gateway for SQL Server in an Azure virtual machine is ideal for those customers who are familiar with Azure services, but not very familiar OCI services.
Advantages of Oracle Database Gateway Running in an Azure VM
- Oracle Database Gateway for SQL Server is developed and supported by Oracle.
- No additional third-party software is required to be installed on Oracle Exadata Database Service on Dedicated Infrastructure, making the environment easy to update and maintain.
- Oracle Database Gateway for SQL Server runs on a separate compute instance from Oracle Exadata Database Service on Dedicated Infrastructure, which makes both environments easier to update and maintain. In addition, the solution might be more affordable, as the Oracle Database Gateway software runs on less expensive Azure OCPUs instead of running on the more specialized, higher-priced Oracle Exadata Database Service on Dedicated Infrastructure OCPUs.
- Communication between Oracle Database Gateway Server and Azure SQL Server is encrypted (enforced by Azure SQL Server default configuration).
- Data type conversion and mapping between Oracle Database and Azure SQL Server Database is automatically managed by Oracle Database Gateway software.
- Hostname resolution for the Azure SQL Server is automatically managed by Azure at the Azure virtual machine level.
Disadvantages of Oracle Database Gateway Running in an Azure Virtual Machine
- Additional License for Oracle Database Gateway software may be required.
- Communication between Oracle Exadata Database Service on Dedicated
Infrastructure and Oracle Database Gateway Server is not encrypted by default when configuring the Oracle Database Gateway server. Additional configuration in Oracle Database Gateway
sqlnet.orais required to enforce encryption from Oracle Exadata Database Service on Dedicated Infrastructure to the Oracle Database Gateway server.