Using LDAP with BI Publisher
You can use BI Publisher with an LDAP provider for authentication only or for both authentication and authorization.
Note:
By default, BI Publisher allows every LDAP user to log in to the system even when no BI Publisher-specific roles are assigned to the user. Users cannot perform any functions that require roles, such as creating reports or data models; however if a user is assigned a role that is assigned permissions on catalog objects (such as traverse and open) the user can perform those tasks.
To prevent users from logging in to BI Publisher unless they have a BI Publisher role assigned, see Disabling Users Without BI Publisher-Specific Roles from Logging In.
Configuring BI Publisher to Use an LDAP Provider for Authentication Only
Configure BI Publisher to use an LDAP provider for authentication in conjunction with another security model for authorization.
Configuring BI Publisher to Use an LDAP Provider for Authentication and Authorization
BI Publisher can be integrated with the LDAP provider to manage users and report access.
Create the users and roles within the LDAP server, then configure the BI Publisher server to access the LDAP server.
In the BI Publisher security center module, assign folders to those roles. When users log in to the server, they have access to those folders and reports assigned to the LDAP roles.
Integrating the BI Publisher server with Oracle LDAP consists of three main tasks:
- Set up users and roles in the LDAP provider
- Configure BI Publisher to recognize the LDAP server
- Assign catalog permissions and data access to roles
For information on supported LDAP servers, see System Requirements and Certification for the most up-to-date information on supported hardware and software.
Setting Up Users and Roles in the LDAP Provider
This procedure must be performed in the LDAP provider. See the documentation for the provider for details on how to perform these tasks.
To set up users and roles:
Configuring the BI Publisher Server to Recognize the LDAP Server
To configure the BI Publisher server to recognize the LDAP server, update the Security properties in the BI Publisher Administration page.
Note:
Ensure that you understand your site's LDAP server configuration before entering values for the BI Publisher settings.
To configure the BI Publisher Server for the LDAP Server:
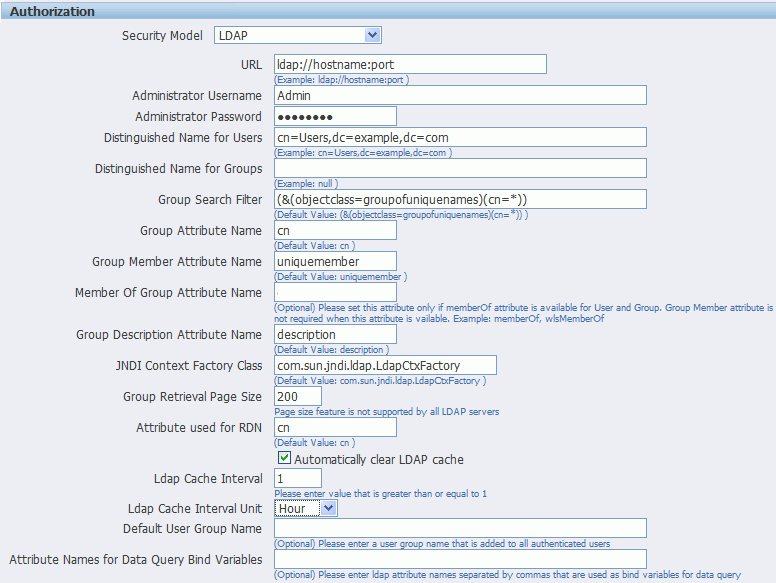
The figure below shows a sample of the LDAP security model entry fields from the Security Configuration page.
If you are configuring BI Publisher to use LDAP over SSL, then you must also configure Java keystore to add the server certificate to JVM. See Configuring BI Publisher for Secure Socket Layer (SSL) Communication.
Disabling Users Without BI Publisher-Specific Roles from Logging In
To disable users without BI Publisher-specific roles from logging in to the BI Publisher server, set a configuration property in the xmlp-server-config.xml file.
The xmlp-server-config.xml file is located at:
$DOMAIN_HOME/bidata/components/bipublisher/repository/Admin/Configuration/xmlp-server-config.xml
In the xmlp-server-config.xml file, add the following property and setting:
<property name="REQUIRE_XMLP_ROLE_FOR_LOGIN" value="true"/>